Abstract
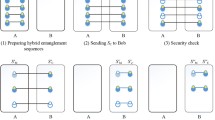
In this paper, a multi-party quantum private comparison (MQPC) scheme is suggested based on entanglement swapping of Bell entangled states within d-level quantum system, which can accomplish the equality comparison of secret binary sequences from n users via one execution of scheme. Detailed security analysis shows that both the outside attack and the participant attack are ineffective. The suggested scheme needn’t establish a private key among n users beforehand through the quantum key distribution (QKD) method to encrypt the secret binary sequences. Compared with previous MQPC scheme based on d-level Cat states and d-level Bell entangled states, the suggested scheme has distinct advantages on quantum resource, quantum measurement of third party (TP) and qubit efficiency.

Similar content being viewed by others
References
Yao, A.C.: Protocols for secure computations. In: Proceedings of 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82), p. 160, Washington, DC (1982)
Boudot, F., Schoenmakers, B., Traor’e, J.: A fair and efficient solution to the socialist millionaires’ problem. Discret. Appl. Math. (Special Issue on Coding and Cryptology). 111(1–2), 23–36 (2001)
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A : Math. Theor. 42, 055305 (2009)
Chen, X.B., Xu, G., Niu, X.X., Wen, Q.Y., Yang, Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283, 1561–1565 (2010)
Yang, Y.G., Xia, J., Jia, X., Shi, L., Zhang, H.: New quantum private comparison protocol without entanglement. Int. J. Quantum Inf. 10, 1250065 (2012)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11, 373–384 (2012)
Wang, C., Xu, G., Yang, Y.X.: Cryptanalysis and improvements for the quantum private comparison protocol using EPR pairs. Int. J. Quantum Inf. 11, 1350039 (2013)
Yang, Y.G., Xia, J., Jia, X., Zhang, H.: Comment on quantum private comparison protocols with a semi-honest third party. Quantum Inf. Process. 12, 877–885 (2013)
Zhang, W.W., Zhang, K.J.: Cryptanalysis and improvement of the quantum private comparison protocol with semi-honest third party. Quantum Inf. Process. 12, 1981–1990 (2013)
Chen, X.B., Su, Y., Niu, X.X., Yang, Y.X.: Efficient and feasible quantum private comparison of equality against the collective amplitude damping noise. Quantum Inf. Process. 13, 101–112 (2014)
Ji, Z.X., Ye, T.Y.: Quantum private comparison of equal information based on highly entangled six-qubit genuine state. Commun. Theor. Phys. 65, 711–715 (2016)
Ye, T.Y.: Quantum private comparison via cavity QED. Commun. Theor. Phys. 67(2), 147–156 (2017)
Ye, T.Y., Ji, Z.X.: Two-party quantum private comparison with five-qubit entangled states. Int. J. Theor. Phys. 56(5), 1517–1529 (2017)
Chang, Y.J., Tsai, C.W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 12, 1077–1088 (2013)
Liu, W., Wang, Y.B., Wang, X.M.: Multi-party quantum private comparison protocol using d-dimensional basis states without entanglement swapping. Int. J. Theor. Phys. 53, 1085–1091 (2014)
Wang, Q.L., Sun, H.X., Huang, W.: Multi-party quantum private comparison protocol with n-level entangled states. Quantum Inf. Process. 13, 2375–2389 (2014)
Hung, S.M., Hwang, S.L., Hwang, T., Kao, S.H.: Multiparty quantum private comparison with almost dishonest third parties for strangers. Quantum Inf. Process. 16(2), 36 (2017)
Ye, T.Y.: Multi-party quantum private comparison protocol based on entanglement swapping of Bell entangled states. Commun. Theor. Phys. 66(3), 280–290 (2016)
Ji, Z.X., Ye, T.Y.: Multi-party quantum private comparison based on the entanglement swapping of d-level Cat states and d-level Bell states. Quantum Inf. Process. 16(7), 177 (2017)
Ye, T.Y., Ji, Z.X.: Multi-user quantum private comparison with scattered preparation and one-way convergent transmission of quantum states. Sci. China Phys, Mech. Astron. 60(9), 090312 (2017)
Ye, C.Q., Ye, T.Y.: Circular multi-party quantum private comparison with n-level single-particle states. Int. J. Theor. Phys. 58(4), 1282–1294 (2019)
Li, C.Y., Zhou, H.Y., Wang, Y., Deng, F.G.: Secure quantum key distribution network with Bell states and local unitary operations. Chin. Phys. Lett. 22(5), 1049 (2005)
Li, C.Y., Li, X.H., Deng, F.G., Zhou, P., Liang, Y.J., Zhou, H.Y.: Efficient quantum cryptography network without entanglement and quantum memory. Chin. Phys. Lett. 23(11), 2896 (2006)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems and Signal Processing, Bangalore, pp. 175–179 (1984)
Shor, P.W., Preskill, J.: Simple proof of security of the BB84 quantum key distribution protocol. Phys. Rev. Lett. 85(2), 441–444 (2000)
Gao, F., Qin, S.J., Wen, Q.Y., Zhu, F.C.: A simple participant attack on the Bradler-Dusek protocol. Quantum Inf. Comput. 7, 329 (2007)
Funding
Funding by the National Natural Science Foundation of China (Grant No.62071430) and Zhejiang Gongshang University, Zhejiang Provincial Key Laboratory of New Network Standards and Technologies (No. 2013E10012) is gratefully acknowledged.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interest
The authors declare that they have no conflicts of interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ye, TY., Hu, JL. Multi-Party Quantum Private Comparison Based on Entanglement Swapping of Bell Entangled States within d-Level Quantum System. Int J Theor Phys 60, 1471–1480 (2021). https://doi.org/10.1007/s10773-021-04771-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-021-04771-7