Abstract
Seafood fraud is a global concern. High-value products with a diversity of species, production methods and fishery origins provide a business environment that is both conducive to criminality and financially lucrative. However, there is scarce empirical evidence on the nature of seafood fraud. This study aims to increase the understanding of deceptive practices in the seafood industry, the crime commission process and to identify possible intervention points. Ten case studies that had resulted in successful prosecutions were analysed using performed crime scripts to understand the actors, resources, processes, fraud techniques, conditions and the payment, sale and distribution of illicit products through legitimate supply chains. The crime scripts for each fraud were created using open-source intelligence, including media sources, publicly available court filings and company records. Similar to other white-collar offences, fraud opportunity was facilitated by leveraging existing resources, relationships and industry reputation to enable and conceal fraudulent practices. In all cases, fraud was perpetrated by senior management, undermining internal control mechanisms. Other fraud enablers included the availability and pricing of substitute products, lack of end-to-end traceability and the inability of supply chain actors, including consumers, to detect fraud. Also notable was the extent of employee involvement, so this paper considers impediments to external disclosure, particularly for migrant workers. The study enriches the food fraud literature by using crime script analysis to understand preparation, execution, and opportunity structures of seafood fraud. By emphasising the nature of fraudulent activities in specific markets, rather than solely focusing on perpetrators, it offers a more comprehensive approach to understanding environmental and situational influences. These insights, scarce in the current literature, are vital for shaping effective intervention strategies.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Seafood ranks high on the list of commodities most susceptible to food fraud (Beia et al., 2020; Europol, 2021; Tähkäpää et al., 2015). Seafood supply chain networks are high-value, complex and opaque, providing an environment that is both profitable and conducive to criminal behaviour. Food fraud can be defined as the practice of misleading consumers or customers about a product for financial gain (Robson et al., 2021) and deceptive practices in this sector are well evidenced (Fox et al., 2018; Kroetz et al., 2020; Pardo et al., 2016). Techniques include species substitution, usually for a lower-priced or more abundant species (Bosko et al., 2018; Kitch et al., 2023; Sameera et al., 2021, misrepresentation of origin – by fishery, production, or catch method (Lawrence et al., 2022; Miller et al., 2012) and the addition of undeclared ingredients to increase volume, quality, or production (Love et al., 2011; Niederer et al., 2019; Rahman et al., 2016). Seafood fraud has a wide impact. It creates a market for illegal fishing, depriving the legitimate supply chain of between $9 bn and $17 bn of trade per year (Sumaila et al., 2020), undermines marine biodiversity and sustainable fisheries management (Kroetz et al., 2020; Sameera et al., 2021) and has implications for public health (Cohen et al., 2009; Li et al., 2022; Pigłowski, 2023). As with all food frauds, businesses caught up in a scandal face reputational risk, revenue impacts and financial impacts from recalls and regulatory penalties (Bindt, 2016; Cox et al., 2020).
Several studies have investigated the incidence (Fox et al., 2018; Pardo et al., 2016; Reilly, 2018; Silva et al., 2021; Lawrence et al., 2022) and vulnerability (Wagner, 2015) of the seafood sector to food fraud. However, as acknowledged in other food fraud research (Gussow & Mariët, 2022; Lord et al., 2021; Smith et al., 2022), there is minimal investigation into the empirical nature of seafood fraud. Crime script analysis (CSA) is used to inform situational crime prevention to understand how criminal relationships, behaviours and processes influence fraud opportunity by mapping out the specific sequential steps, skills and resources required for such a crime to take place (Cornish, 1994; Cornish & Clarke, 2002). Its applicability to white-collar crime is evidenced in the literature (Donegan, 2019; Jordanoska & Lord, 2019; Junger et al., 2020; Kennedy et al., 2018). Food fraud, a non-violent, financially motivated offence typically committed by individuals or organisations in business or professional settings is commonly referred to in the literature as a form of corporate or white-collar crime, committed by either business owners, or by employees of a food business operator (Huisman & van Ruth, 2022; Lord et al., 2017a; Smith et al., 2017). CSA is emerging as a methodology to analyse food fraud and the structural conditions that facilitate illegal behaviour in the food system. Examples include the analysis of counterfeit alcohol investigations (Bellotti et al., 2020), the examination of the black market in poached meats (Goodall, 2019) and to propose local and macro-level intervention strategies to prevent illegal, unreported and unregulated (IUU) fishing (Petrossian & Pezzella, 2018).
This study aims to comprehensively understand criminal activities in the seafood sector by examining the structured sequences of events and actions of large-scale seafood frauds and the conditions in place to facilitate them using CSA. The analysis has two broad aims. The first objective is to provide new insights into how food crime is prepared and conducted. It considers the actors, decisions, processes and resources required to commit each fraud and the opportunity structures that facilitate it. Second, by employing CSA, a structured framework that maps the distinct criminal stages of fraud within the food system, it becomes possible to identify common situational elements across different crimes and identify possible opportunities for intervention. In this study, Open-Source Intelligence (OSINT) was collated from the media, publicly available court records from the US and company records. Subsequently, CSA was used to construct the scripts of 10 distinct fraudulent activities in the UK and the US. Research using CSA to analyse food fraud is still relatively scarce, so this paper contributes to exploring the use of CSA as a framework to study food-related criminality and to broaden the crime types analysed by the methodology. Moreover, this represents the most extensive investigation employing CSA to analyse illicit activities within traditional and legitimate segments of the food industry.
Theoretical framework
Commonly referenced in the literature are the components of an anti-fraud strategy; prevent, detect, deter and disrupt (Soon et al., 2019; Spink, 2019; Spink et al., 2017). These components are closely interlinked, and each plays its own significant role in combatting criminality and creating a hostile environment for fraudsters to operate in. Prevention and mitigation exist in the prevent, detect and deter components of this strategy, and a consensus is forming in the food fraud literature that it is more effective to prevent than to pursue and prosecute (Barrere et al., 2020; Lord et al., 2017b; Soon et al., 2019; Spink, 2019; van Ruth et al., 2017), a central theme underpinning the Elliott Review into the integrity and assurance of food supply networks (Elliott, 2014).
Prevention and mitigation are the anticipation, recognition and appraisal of a crime risk and the initiation of action to remove (prevent) or reduce (mitigate) it (Welsh & Farrington, 2012). Prevention aims to eradicate the risk; mitigation assumes prevalence and aims to reduce the negative consequences (Spink, 2019). The literature on crime prevention is vast; in the context of food crime, it has been explored by numerous authors, primarily in the context of situational crime prevention (Lord et al., 2017b; Manning & Soon, 2016; Spink, 2019; Spink et al., 2017; van Ruth et al., 2017). Situational crime prevention aims to reduce crime by taking a systematic approach to minimise the opportunities and incentives to commit crime by manipulating the environment within which the crime is situated to increase the risks and costs of being caught and reduce the benefits (Cornish, 1994). It is particularly relevant for food crime, as the types of criminals (Manning & Soon, 2016; Spink et al., 2013) and methods of fraud (Robson et al., 2021) are so varied that it is easier to focus on reducing situational risk than to target offenders through individual crime profiling (Spink, 2019). Situational crime prevention also allows resources to shift from law enforcement to public and private interventions (Spink et al., 2016).
Food fraudsters are described in the literature as ‘intelligent, resilient, clandestine, and good at stealthily avoiding detection’ (Spink & Moyer, 2011, p. 161). This premise is reinforced in multiple research papers (van Ruth et al., 2017; Spink et al., 2017), as is the concept of entrepreneurship (Lord et al., 2017a, b), framing food fraud as an enterprise crime and concealing illegal activity behind legal businesses and markets. Often perpetrated by legitimate market actors who are seeking to maximise profit or manage supply, demand and competitive pressures (FSA & FSS 2020; Gussow, 2020), it is proposed that food frauds are ‘situated actions, shaped by contingent enterprise conditions’ (Lord et al., 2017b, p. 483), i.e., influenced by the internal and external environment of the businesses within which they occur. Criminal advantage is provided by actors’ legitimate business processes, relationships and resources, a concept well recognised in white-collar crime (Benson et al., 2009; Benson & Simpson, 2018), food fraud literature (Lord et al., 2017a; Spencer et al., 2018) and by regulators, where ‘food crime is committed by those with an existing role in the food and drink economy, and the access to markets which this provides is clearly an asset to those criminals’ (FSA and FSS, 2020, p.6).
The seafood industry encompasses a variety of species, production methods and attributes, actors, supply chain nodes and geographies, making it more complex than other areas of the food system (Anderson et al., 2018) and consequently challenging to monitor and regulate. Fraud is perpetrated via numerous techniques (Fox et al., 2018; Lawrence et al., 2022) and can be confined to one part of the supply chain or incorporate multiple network actors working in collusion. For example, the UK’s black fish scandal, a large-scale fraud, was worth almost £63 million in Northeastern Scotland through the illegal landing of undeclared fish between 2002 and 2006, involving approximately half of all pelagic fishing vessels from the area. The fraud involved actors across the fishing community, including skippers, factories and agents, enabling criminal activity to be concealed within legitimate business processes through the ability to falsify logbooks, conduct false accounting, manipulate weight recording and offload fish directly to processing factories to avoid fish markets and public scrutiny (Smith, 2015).
White collar criminals, in this case, food system actors engaging in criminality, find opportunity in their legitimate organisational practices and processes (Benson et al., 2009; Lord et al., 2017b), their occupational resources provide a facilitating asset (FSA & FSS, 2020) and the ability to conceal criminal activity behind their routine, everyday practices (Levi & Lord, 2017). Detection and proof of white-collar offences are often more challenging to detect and prove than for other types of crime (Gottschalk, 2021; Gottschalk & Gunnesdal, 2018) because such offences are often ‘invisible’, covert, apparently legitimate, physically distant and without immediate impact (Benson et al., 2009; Croall, 1999). As offenders have legitimate access to the space where the crime occurs (for example the harvesting and processing of seafood), criminological approaches that focus on the characteristics of crime rather than the offender may be more effective in supporting interventions (Eck & Clarke, 2019).
Crime script analysis (CSA)
Underpinned by these theories and introduced by Derek Cornish (Cornish, 1994), CSA is increasingly used as a technique to explore the procedural aspects of criminal activity (Dehghanniri & Borrion, 2021), the modus operandi of fraudsters and the context within which crimes occur. A systematic approach deconstructs crime into component parts to establish a chronological sequence of activities, skills, processes and resources required for a given crime.
CSA has been used to analyse a wide range of offences; examples include ‘traditional’ crimes such as homicide (Osborne & Capellan, 2017; de Korte & Kleemans, 2022), sexual offences (Brayley et al., 2011; Chiu & Leclerc, 2021; Cook et al., 2019) and white-collar crimes including financial fraud (Donegan, 2019; Gilmour, 2014; Junger et al., 2020), cybercrime (Hutchings & Holt, 2015; Loggen & Leukfeldt, 2022; van Nguyen, 2021) and corruption (Rowe et al., 2013). It has also been used as a tool to explore wildlife crime and potential disruption strategies (Lemieux & Bruschi, 2019; Moreto & Clarke, 2013; Skidmore, 2021; Sosnowski et al., 2020; Viollaz et al., 2021), In the context of food fraud, specific information on the crime commission process is more fragmented with a relatively small selection of studies (Bellotti et al., 2020; Goodall, 2019; Petrossian & Pezzella, 2018), that demonstrate the applicability of this type of analysis to inform situational prevention for food supply chains.
Practical application
In this study, CSA helps to explore how illicit products move through legitimate and illegitimate supply chains, opportunities for co-offending, methods of misrepresentation and concealment and the situational conditions and actors that facilitate criminal activity. In addition to the ‘why’ of traditional criminological theories, CSA gives an understanding of the ‘how’ of committing crime, which offer more tangible opportunities for interventions. Focusing on the ‘how’ of crime events provides procedural information that is key to developing comprehensive prevention strategies and also to sense check mitigation tools such as food fraud vulnerability assessments, commonly used by the food industry and regulators to pinpoint potential weak spots in a supply chain (van Ruth et al., 2017). By delving into how such crimes are carried out and considering historical contexts conducive to criminal activities, crime script analysis helps to validate the “why factors” considered in vulnerability assessments, which advocate adopting a criminal mindset (van Ruth et al., 2017). CSA provides a detailed examination of specific criminal activities to engage in such critical thinking and although these insights are limited to information on crimes that are known, provide empirical information on existing criminal activity.
By identifying recurring patterns and modus operandi used by offenders and understanding how crimes are committed, food industry actors can strengthen internal control systems. It allows regulators and law enforcement to focus their efforts on key points within criminal activities, such as vulnerable stages in a process or specific locations prone to certain types of crimes. This targeted approach can optimise resource allocation and enhance the effectiveness of enforcement actions.
Several methods exist for crime scripting practice and there are no specific guidelines about the data collection or the creation of scripts themselves (Dehghanniri & Borrion, 2021). Presented initially as a nine-step process by Cornish, it has been adapted in some subsequent studies. Tompson and Chainey (2011) simplified the process into four steps (preparation, pre-activity, activity and post-activity so that the language was more widely understood, and the process streamlined (Chainey & Berbotto, 2022), a methodology that has been employed by other studies (Ambagtsheer & Bugter, 2022; Berbotto & Chainey, 2021; Skidmore, 2021).Multiple sources of data are used for creating scripts (Brayley et al., 2011; Dehghanniri & Borrion, 2021). These include interviews with law enforcement, subject matter experts or victims, police and court records and OSINT (Hutchings & Holt, 2015; Hutchings & Pastrana, 2019; Peters, 2020), intelligence gathered from openly available information on the internet or elsewhere.
Methodology
This study uses OSINT to collect data for the crime scripts. This could include resources such as media sources, social media grey literature, mapping, imagery, commercial databases and books (National Police Chief’s Council, 2020). Although widely acknowledged as an invaluable intelligence resource (Sampson, 2016; Wells & Gibson, 2017), care must be taken to ensure data quality and reliability, as there are minimal constraints on who can produce and distribute open-source data (de Busser, 2014). The methodology is therefore based on the structured method proposed by Chainey and Berbotto (2022), that uses document analysis and a coding process to ensure that the data gathered from open sources is validated as much as possible.
In contrast to a broad overview, this study adopts a case study approach, aligning with Benson et al.‘s (2009) recommendation for detailed appraisal. Given the number of changeable variables for seafood crimes (seafood product, fraud type, actor, supply chain node), the decision was made not to pursue a singular crime script but to take a crime-specific approach (Cornish, 1994) and script each crime individually, a method that has been used to provide comparative analyses of individual cases (Ambagtsheer & Bugter, 2022). This approach allows for an in-depth consideration and analysis of historical situational factors that enabled diverse fraudulent practices.
Scripting individual crimes entails a significant amount of data, so each crime event was simplified to one ‘act or facet’ that demotes seafood mislabelling. This approach was taken in a previous study on IUU fishing (Petrossian & Pezzella, 2018) and by certain authors to script wildlife crimes (Skidmore, 2021; Sosnowski et al., 2020; Viollaz et al., 2018, 2021).
The crime script was broken down into scenes (the stages of the crime event), cast (individuals and organisations) and conditions, which include the prerequisites, (equipment, resources, information that needs to be in place before the crime is initiated), facilitators (rewards, risks and costs) and enforcement conditions (legislation, permits/licences and regulators). Systematically scripting out the conditions allows for some consideration of the wider drivers and environmental factors that propel offenders into criminality, essential information to fully understand offender decision-making, particularly for white-collar crime (Jordanoska & Lord, 2019). The data from each case were carefully analysed to identify the actors and main events specific to each crime. The crime commission process was compared among sources to ensure reliability and then the data were analysed and coded by hand to organise the data to a scene, using Tompson and Chainey’s (2011, p. 88) simplified scene typology: preparation (the opportunities and conditions in place in place for illegal activity to take place in the food system), pre-activity (the logistical or transactional steps that need to be carried out prior to the activity), (this relates to the actual food fraud activity), or post-activity (the logistical or transactional steps necessary to exit from the illegal activity). The data were also coded according to cast (offenders and legitimate businesses) and conditions (prerequisites, facilitators and enforcement conditions), creating a performed script for each crime (Borrion, 2013). These scripts were compared to identify common themes across the data.
Data sources
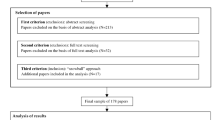
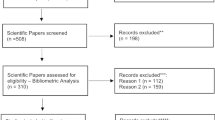
Case study criteria were legitimate seafood companies that had occurred or been prosecuted between 2015 and 2023, were of a significant scale, had resulted in a conviction and had enough data to create a meaningful script. Relevant cases were initially identified via a keyword search of media sources, using Nexis UK and the terms: ‘seafood fraud or fish fraud or seafood mislabelling or fish mislabelling or (food fraud and seafood) or (food fraud and fish)’ under the topic ‘crime, law enforcement and corrections’.
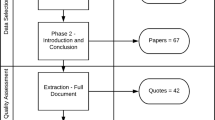
Additional searches of the grey literature were conducted via Google to identify additional cases, further information on the cases identified and information on specific seafood chains. Certain cases were excluded; blue crab (US Department of Justice (DOJ), 2020) and spiny lobster (Department of Justice (DOJ), 2023), frauds with very similar crime scripts to Cases 5, 6 and 7 and two cases of complex organised fraud with wide-ranging timelines (Oceana, 2018; Sharpe, 2017) that were too extensive to script for this study. Although the search criteria was not limited by country, the search strategy resulted in ten cases for analysis, eight from the US and two from the UK. For the US cases, the validity of the data identified in media sources was checked by viewing indictments, judgements and summaries of judiciary proceedings via Public Access to Court Electronic Records (PACER), a service that provides electronic public access to federal court records, available at https://pacer.uscourts.gov. In the UK, the relevant courts for each case were contacted. However, there was no publicly available information on the cases. Companies House was used to verify company directors and filings. (https://www.gov.uk/government/organisations/companies-house). The sources used for each case are listed in supplementary information (appendix 2) Table A.2.
Limitations
This study is subject to various limitations. Open-source data are a valuable tool for crime scripting because they provide a wide breadth of easily accessible data. However, data may not be accurate, or up to date and key details may be omitted, some parts of the crime script may be more comprehensively covered. In some cases, there were gaps in the data. For example, in cases 7 and 10, post-activity data is still needed as there was only information up to export. To make this clear, the authors have explicitly stated our lack of knowledge in the script of these cases. Data from media outlets may contain bias, as media sources may have specific agendas or perspectives that limit the crime script’s accuracy and credibility. Where possible, information was retrieved on each case from multiple sources (including US judiciary records) to try and mitigate bias and inaccuracy as much as possible and provide a comprehensive understanding of criminal activity in these cases. Using open-source data, each case’s details can be transparently scripted and made available to all to provide a comprehensive picture of the crime commission process.
The selection of cases only includes crimes that have been detected and prosecuted, so the data are subject to selection bias. Many food crimes go unnoticed and those that succeed in evading detection may have more complex methods of concealment than those that are identified. The search criteria also only revealed large-scale cases from the UK and US, likely due to the use of English language sources and a broader geographical spread would have been more desirable. However, the aim is to provide valuable insights on previous criminality in the sector, rather than an exhaustive account of all seafood crime and, in the absence of expert or confidential data sources, is based on the best publicly available information. Combining CSA with other methods of analysis, such as food fraud vulnerability assessments, allows for the assessment of both known and unknown risks in the food system and demonstrates the necessity of using multiple tools in the measurement, prediction, prevention and mitigation of food fraud.
Results
Table 1 contains key information on each fraud, including company name, supply chain node, location, description and scale of fraud. Supplementary information, (Appendix 1) Table A.1 contains the crime scripts of each fraud, including relevant actors (cast) and categorised by act and conditions into four stages: preparation, pre-activity, activity and post-activity, based on the open-source information available.
Cast
Lead offenders
All the companies for whom it was possible to gather business size data were classed as small, according to their number of employees. In all cases, fraud was carried out by senior leadership, in most cases, CEOs or directors of legitimate seafood companies. The directors were also company owners, meaning that the company benefits of fraudulent activity were also of direct personal benefit. Where fraud was initiated by company employees (Case 1), it was with the approval and at senior leadership’s behest. Cases 2, 4 and 6 were familial associates, including father and sons, cousins and brothers. Family firms are generally considered to act more ethically than non-family firms (Ding & Wu, 2014), affording more value to non-financial attributes such as employee satisfaction, loyalty and trust than non-family businesses (Zellweger et al., 2013). However, internal control mechanisms may be weaker than in non-family firms due to the corporate culture operating based on trust, contributing to an environment where illicit behaviour is facilitated by weak governance.
Support offenders
It is notable that, as far as is possible to assess from the data available, there was little collusion across supply chain networks, with offending occurring at one node and product received by legitimate supply actors and absorbed into the legitimate supply chain network. Cases 3 and 4 used support offenders; seafood customers who knowingly received illegally imported siluriformes and a fishing captain who was a licenced vessel operator to source IUU fish.
Legitimate actors
Legitimate actors were active primarily in the post-activity phase, where illicit or mislabelled products entered legitimate supply chains, but they were also active in preparation, where offenders purchased legitimate products (e.g., Asian crab) but misrepresented them at sale. These actors included post- harvest nodes of the seafood supply chain; processors, wholesalers, restaurants and supermarkets.
Implications
Corporate culture
In all cases, fraud was perpetrated from the top. Senior leadership is responsible for setting the tone at the top of the organisation and is considered to have a critical influence in shaping the corporate culture, attitudes and behaviour of others within the organisation (Ewelt-Knauer et al., 2022; Warren et al., 2015). A lack of moral leadership and permissive attitudes can contribute to fraud pervading throughout a corporation, an acceptance of unethical practices and an environment that is inconducive for employees to speak out on wrongdoing (Soltani, 2014).
Guardian offender overlap
Chan and Gibbs (2022, p. 326) explore the concept of guardian offender overlap in the context of financial fraud; when individuals who should have guardianship responsibilities within an organisation choose to offend, it has far-reaching implications in the context of organisational control structures ‘if guardians are motivated to offend, in theory they can exploit their legitimate access to the accounting and reporting process to do so. If such guardian-offender overlap were pervasive, specialized access and the potential to circumvent the guardianship structures will render controls inadequate’. This can similarly be observed in the context of food fraud; if fraud is perpetrated at the management level, internal control systems are undermined. When individuals who should have guardianship responsibilities within an organisation choose to offend, it has far-reaching implications in the context of organisational control structures. For example, in Case 6, the vice president was employed by the company (also the CEO’s son) and responsible for sales, marketing and logistics. He also had technical responsibilities; for ensuring compliance with regulations and was the designated Hazard Analysis and Critical Control Points (‘HACCP’) coordinator. If fraud is committed by those with technical responsibilities, internal control systems are effectively undermined and the layer of food fraud prevention that sits within a food business is removed. These types of offenders have both specialised access to food business systems, processes and networks, but are also tasked with guardianship and have the access and knowledge to bypass internal food fraud and safety management systems. In cases 3 and 4, where customers and suppliers were also complicit, this has even more serious implications for guardian/offender overlap as controls upstream or downstream in the supply chain are also undermined.
Preparation, pre-activity, activity and post-activity
Preparation
Act
Using an intricate knowledge of the seafood industry, offenders identified potential markets for illicit products. Cases 1, 3, 4, 5, 6, 7 and 8 were from existing customer relationships, while cases 2, 9 and 10 identified new markets. Illicit products were sourced. In some cases, these were products already supplied to the businesses (Cases 3, 5, 10); in other cases, they were sourced specifically for the purpose of criminal behaviour (Cases 1, 2, 4, 7, 8, 9). Case 6 sourced both new products and used existing imported products.
Conditions
All lead offenders owned legitimate seafood businesses through which these frauds were conducted, with resources and relationships already in place that could be used for both legal and illicit behaviour. Resources included access to facilities including docking and weighing, cold storage, company-owned transport and packaging. Existing relationships were used for identifying markets, using existing suppliers and customers. In all cases, the fraudulent behaviour was conducted within the structures, normal business processes and networks of their legitimate businesses, with complex concealment strategies that facilitated the illicit behaviour and the ability to ‘launder’ illicit products into legitimate supply chains. Offenders’ routine business activities created effective opportunity structures for crime to occur. For example, in the case of US crab and shrimp mislabelling, the companies already purchased domestic wild-caught products and imported foreign products as part of legitimate business arrangements. Mispresenting one for the other, for example, could conceivably have occurred as a small act of deception, as a one-off solution to fulfil an order during a supply shortfall, but escalates gradually into a much more significant fraud - the ‘slippery slope effect’, a concept explored by Lord et al. (2017a).
As part of his job, ‘A.P’ bought and sold shrimp on behalf of Alphin Brothers. ‘A.P’ bought and sold both domestic shrimp…. also shrimp that had been imported into the United States from other countries, such as Mexico, Venezuela and Ecuador. ‘A.P’ sold shrimp to customers in the United States, including other wholesalers as well as retail operations and arranged for transportation of shrimp to customers. (United States of America v. Alphin Brothers Inc., 2014).
As part of its business, CAPT. NEILL’S purchased live domestic blue crab. CAPT NEILL’S employed workers to steam, pick, and process the meat from the domestic blue crab…. As part of its business, CAPT. NEILL’s also purchased crab meat from species other ‘than blue crab, including crab indigenous to, and exported from, South America… As part of its business, CAPT. NEILL’S sold crab meat to wholesale member stores, grocery store chains, and retail establishments. (United States of America v. Capt. Neill’s Seafood, Inc & Phillip R. Carawan, 2019).
Many companies were well trusted within the industry, with longstanding reputations that enabled them to initiate illegal activity without question. Case 5, for example, had a 30-year reputation in the seafood industry and despite having repackaged 42,855 lbs. of foreign jumbo crab in 2015 (DOJ, 2020) received an excellent rating in their SQF food safety certification in July 2015 (SQF Institute, 2023), which would have provided additional reassurance to buyers that products meet safety, regulatory and quality standards.
A condition key to preparation for most of these crimes was a demand for products with certain attributes, volatility in supply and/or pricing of these products and the availability and pricing of potential substitutes. In the UK, for example, sea bass prices increased in 2011 due to reduced supply (FAO, 2011), partly attributed to the financial crisis in Europe (Dove, 2011), with producers scaling back production from previous years (Towers, 2012). In addition, wild seabass stocks suffered a decline from 2009 onwards (Williams & Carpenter, 2015) and consumer demand in the UK increased by 10% between 2011 and 2012 as it replaced overfished species such as cod and haddock. During this period, the seabass market was characterised by significant price swings as it is subject to seasonality (Towers, 2012); industry fragmentation and a lack of intra-industry cooperation made production forecasting difficult, meaning that it was difficult to sell seabass on contract to reduce price uncertainty. The media reports surrounding Case 9 cited these price increases as an initial motivator to source a cheaper product.
In the US, domestic blue crab is native to the western Atlantic and the Gulf of Mexico. 50% originates from Chesapeake Bay, providing the area with an annual economic value between $46 and $103 million (Huang, 2015). The blue crab harvest supports coastal communities and ecosystems and is of cultural and culinary significance (Paolisso, 2007), but yields are in decline due to overfishing, disease and environmental pressures, particularly in the Chesapeake fishery (Hedgpeth, 2022). Crab meat is still primarily extracted via process-intensive manual labour, often by Mexican immigrants (Paolisso, 2007). To bridge the dwindling supply, make use of cheap and abundant foreign crab meat and create a year-round product, food businesses began to import crab from Asia and South America, used predominantly for processed products such as crab cakes (Daub, 2006). Selling imported crab ‘Maryland style’, while it may be misleading to some consumers, is not considered fraud; restaurants are not regulated by country-of-origin labelling regulation (COOL) and ‘Maryland style’ refers to the cooking or seasoning of such dishes (Oceana, 2015). However, it could be argued that the easy availability and acceptance of such substitutes precipitated ‘industrial drift’ and a slippery slope to food fraud and several high-profile court cases have followed, where products are stated as local. A study in 2015 found that 38% of crab cakes advertised as blue local crabs contained cheaper imported (often swimming) crabs from the Indo-Pacific region and the Mexican Pacific coast (Oceana, 2015). It is estimated that 10 to 45% of crab imported into the US from these countries originates from IUU fishing (Pramod et al., 2014).
The substitutions observed in these cases include cheaper fillets of white fish for sea bass, foreign processed crab meat substituted for local, farm-raised shrimp sold as ‘wild-caught’, processed octopus sold and IUU catch sold as legitimate. In most cases, they feature a less abundant, more expensive species being substituted for a cheaper species with a plentiful supply. When fish are processed and morphological features are moved, it can be very difficult to distinguish between visually similar species (Reilly, 2018).
Similarly, it is impossible to verify the production method visually, or if seafood has been caught legitimately. Therefore, the availability of cheap substitutes that are only distinguishable from the intended product with sophisticated testing or sold without end-to-end traceability data is a key condition for most of these offences. The offenders’ intricate knowledge of local demand for premium products, alongside the availability of substitutes that would go undetected, allowed them to benefit from substantial price differentials between legitimate and illicit products.
Implications
The CSA revealed that these large-scale food frauds were primarily characterised by opportunistic decision-making within legitimate and well-regarded seafood enterprises, rather than organised or independently planned crimes. The crimes were mostly perpetrated through existing supply chain networks, using established trading relationships to launder illicit products. This contrasts with previous studies of seafood fraud that warn against complex and opaque supply chains (Fox et al., 2018; Lawrence et al., 2022; Pramod et al., 2014) and signals that there is also vulnerability for locally produced and distributed goods, a phenomenon recently observed in a UK report on food fraud drivers (Elahi et al., 2022a).
In many of these cases, shortfalls in supply and plentiful availability of visually similar cheap substitutes were key motivators and facilitators of criminality. Food systems have been placed under recent strain due to a myriad of factors, including Brexit (Ranta & Mulrooney, 2021), COVID-19 (Ahmed & Azra, 2022; Alabi & Ngwenyama, 2023; Soon-Sinclair et al., 2023), the war in Ukraine (Ben Hassen & El Bilali, 2022; Jagtap et al., 2022), the cost-of-living crisis (Benton et al., 2022) and face future climate change-related impacts (Godde et al., 2021; Guzmán-Luna et al., 2022; Scanes & Byrne, 2023). Price volatility and fluctuations in supply are considered key drivers of food fraud vulnerability (van Ruth et al., 2017) and care should be taken to ensure the integrity of such products, particularly if the cost deviates from the prevailing market pricing. Horizon scanning and fraud predictor models, including AI-based predictive analytics, may offer possibilities for the food industry and regulators to track such price differentials and identify anomalies and patterns that may indicate fraudulent activity in the supply chain (Soon, 2022; Ulberth, 2020).
Pre-activity
Act
Illicit products were purchased. All cases, except 4 and 10 were imported from overseas, usually for a farmed, cheaper product. In case 4, the fish was not local, but IUU and in case 10, the origin of the salmon was not disclosed. Each offence was facilitated by document fraud, defined as ‘making, using or possessing false documents with the intent to sell or market a fraudulent or substandard product’ (FSA, 2023). In most cases, the original labelling and packaging were removed and new labels were applied. Additional information, such as an expiry date, was applied to make the packaging more realistic. In most cases, the mislabelling facilitated the substitution of species or fishery origin to sell a lower-priced product for a higher price. In Case 9, the misrepresentation of the communication from Trading Standards to the processor and retailer enabled the supply of a substandard product. In Case 3, siluriformes banned for import were mislabelled as permitted species, facilitating their entry to the US.
Due to the scale of some of these frauds, employees were required to repackage and mislabel the products and were actively engaged in wrongdoing. In the US blue crab and shrimp mislabelling cases, employees were directed to unpack foreign containers and repack the products from them into domestically branded packaging, a request that carries little ambiguity as to its lawfulness.
A.P. directed ALPHIN BROTHERS employees… to repack approximately 13,450 pounds of farm-raised shrimp that had been imported into the United Sates from Ecuador and elsewhere, into boxes bearing the brand name Uncle Jock and falsely labeled as wild-caught product of the United States’ (United States of America v. Alphin Brothers, 2014).
In Case 9, the fraudulent e-mail pertaining to communicate Trading Standards permission to sell Japanese sea bass was sent from an employee’s computer.
Conditions
Offenders used existing food control systems for complex concealment strategies to ‘launder’ illicit products into legitimate supply chains. For example, in Case 4, they had the necessary dealer permits to account for fish purchased from commercial fishing vessels and in Case 7, wholesale saltwater products licences allowing them to purchase and sell domestic spiny lobster. Customs brokers used for their legitimate business prepared the necessary airway bills, labels, invoices and documents. In Case 8, the company provided services to vessels that unloaded at its dock, including the preparation of state ‘trip tickets’ and records of shrimp landings required by Texas law. To prepare the state trip ticket, the company had their own forms called unloading tickets, which contained information such as vessel name, licence number, vessel captain, pallet number and pallet weight. These tickets accompanied shrimp when transported across state lines to substantiate the origin of the seafood if inspected by highway patrol or agricultural authorities. Company personnel trucked illicit product to the companys’ legitimate docking facility, re-weighted and wrapped it to appear that it had been caught by a local fishing vessel, a Texas-Licensed shrimper, ‘The Regio’, which was docked at a facility next to the LO’s own facility. Using their legitimate unloading tickets, they created false bills of landing and documentation that read ‘Product of U.S.A., Wild-caught Gulf Shrimp.’ Case 10 involved the use of false identification marks, false health and pre-export certificates.
Implications
Document fraud was used in all cases to facilitate the sale of illicit products. The reliance of the food industry on documentation, often paper-based, to verify the origin and authenticity of products, is a key vulnerability that fraudsters can exploit. Additionally, food industry workers are not routinely trained to identify fraudulent documentation and where legitimate corporate documents are used (as in many of these cases), it may not differ from the expected documentation. Fenoff and Lee (2023) propose that a document fraud review should be added to corporate food fraud vulnerability assessments so that organisations understand where they may be at risk. The increasing digitisation of control systems and associated documentation should contribute to making document fraud more difficult.
In the food fraud literature and industry certification guidelines (BRCGS, 2018; Moy, 2018; Soon & Manning, 2017), there is (correctly) much focus placed on the importance of corporate whistleblowing systems that provide confidential, anonymous and independent reporting lines for disclosures of wrongdoing. However, where crime is perpetrated from within the company and by higher-ranking personnel, particularly if the deceptive behaviour is ‘normalised as sharp practice’ (Etienne et al., 2020, p. 26), internal reporting lines will be rendered ineffective, which underlines the importance of external whistleblowing resources alongside mechanisms that might increase external reporting. In the UK, for example, employees, contractors, trainees, or agency staff in the food industry who wish to make a qualified disclosure are protected by the Public Interest Disclosure Act 1998 (FSA, 2018), but its effectiveness in encouraging external reporting has been questioned, as the legislative structure is more favourable to that report internally first (Etienne et al., 2020; Hyde & Savage, 2015; Lewis, 2008). Anonymous reporting via hotlines or e-mail, such as the UK’s FSA’s Food Crime Confidential (FSA, 2023) may help lower the inhibition threshold for external reporting. However, if communication channels are only one-way and the whistleblower chooses to omit contact details, the ability to gather further intelligence is limited. Several suggestions to increase external reporting have been put forward in the literature, including law enforcement campaigns, financial support for reporters, the use of trade unions and food enforcement officers to act as contact points for potential reporters (Etienne et al., 2020).
The likelihood of reporting may be affected by labour force characteristics. Power imbalances between employers and staff within the global food industry exist due to concentrations of power and a reliance on low-wage labour, including migrant and seasonal workers (Davies, 2018; Palumbo et al., 2022; Scott et al., 2012). These groups of employees may be discouraged from whistleblowing for fear of retaliation, job loss, or harassment, particularly if they lack access to legal support and resources. A study on barriers to reporting in the UK’s food industry (Etienne et al., 2020) found that the characteristics of the UK’s food industry labour workforce made reporting less likely as workers were likely to be in zero hours or temporary contracts, regularly changing jobs and easily replaced. Similarly, the US blue crab and shrimp processing industries have historically struggled to attract and retain workers (traditionally African American women) due to the seasonality of employment, repetitive and tedious labour, payment by piece and risk of injury. To solve this labour gap, they have employed several strategies; for example, hiring non-immigrant workers on the H2B visa program (Bier, 2021; Griffith, 1997), immigrant workers hired through temporary work agencies, international students through the e J-1 visa program and undocumented workers (Castellanos Contreras et al., 2016). These hiring practices can limit employees’ ability to report wrongdoing; they are often linguistically and culturally isolated (Straut-Eppsteiner, 2016), lack access to legal resources and, as their visas are tied to their contracts, face immigration-related vulnerability in terms of legal status and employment.
‘As most supervisors at the crab houses do not speak Spanish, and the women rarely speak English, communicating basic questions or concerns is a significant challenge. Fear of being fired and sent back to Mexico makes the workers hesitant to ask questions or express concerns. They also fear that should they speak out about working conditions, they would not be recruited in future years’ (Washington College of Law International Human Rights Law Clinic and Centro de los Derechos del Migrante, 2013, p. 30).
Suggested solutions to encourage reporting include ensuring that workers are aware of their legal rights and protections, including the right to report wrongdoing without fear of retaliation from the start of their employment, ensuring workers have knowledge of and access to appropriate legal resources, strengthening immigration protection for whistleblowers and ensuring that whistleblowing protection legislation is not limited to those with a domestic employment contract. (Berg et al., 2023; Sinclair, 2022; Washington College of Law International Human Rights Law Clinic and Centro de los Derechos del Migrante, 2013).
Activity
Act
The products were sold to retailers, wholesalers, wholesale member clubs, seafood stores, markets, grocery stores and restaurants. As far as it is possible to ascertain from the available information, customers of the lead offenders were generally unaware that products were misrepresented or mislabelled and bought the product in good faith, often from suppliers that they had existing relationships with and who had longstanding reputations in the industry. Cases 3, 4, 7,8 and 10 used relatively sophisticated counterfeit documentation (shipping documentation, fish dealer reports, vessel trip reports (VTRs), health and export certificates, false unloading documents and bills of landing) to facilitate the crimes.
Conditions
Lead offenders perceived that the risk of checks or sampling was low, and that the product was not visually different from the authentic product. In case 9, for example, the fraud relied on the processor and retailer not independently checking the legislation and taking at face value the doctored e-mail from Trading Standards sent by the offender, an omission for which the judge criticised the processor and retailer at the prosecution, ‘“Both Iceland and Kirwin Brothers are to be criticised for not checking the relevant regulations and permitting the mislabelling of the food product for sale to the public’ (Former Royal Navy chef jailed over £1m ‘fake’ sea bass scam, 2015). In cases 1,2,5,6 and 8, where crab, shrimp and squid were substituted for other species, confirmation of fraud would have required onsite analysis (if the customer had appropriate fraud screening capabilities) or sent off for laboratory analysis. The crimes also relied on customers not verifying documentation. This would require the customer to be familiar with both the required documentation and regulations; for example, in Case 8, shrimp were accepted where the landing documentation (that guarantees the authenticity of domestically caught seafood) was not signed by the vessel owner; this should have raised a red flag.
Cases 3 and 4 relied on the absence of external verification. Case 3 relied on an absence of checks by border control for species included in the shipping consignment with the species of fish listed on the shipping documentation that were not subject to the Federal Meat Inspection Act (FMIA). Case 4 was based on the assumption that the National Oceanic and Atmospheric Administration (NOAA) could not identify the fraudulent VTR and dealer reports. Where the supply chain is vertically integrated and companies control both the fishing and distribution nodes of the supply chain, this represents a vulnerability. Fish dealers must report their purchases to NOAA via a dealer report, which includes information such as date of landing, port of landing, catch vessel, corresponding VTR number, commercial grade, species, price, and weight (NOAA, 2023). These reports corroborate the information submitted in the VTRs by vessel captains and it indicates a possibility of fraud if there is a mismatch. However, if both reports are falsified, this control is invalidated.
Implications
The success of many of these frauds relied on the traceability concept of one step forward and one step back; food business operators should be able to identify the immediate supplier of a product (one step back) and the immediate customer to whom a product is supplied (one step forward). Designed with food safety in mind, the principle allows food to be accurately traced and recalled in the event of a food safety issue. For the UK, this was set out in EU Regulation (EC) No 178/2002, now replaced by the UK Food Information (Amendment) (EU Exit) Regulations 2019 and in the US, it is covered under the Food Safety Modernization Act (FSMA), 2011. However, particularly as many products were processed and it is not possible to visually distinguish one species from another, other techniques are required to ensure that fraudulent products do not contaminate legitimate supply chains, putting businesses and consumers at risk. It underlines the necessity of rigorous supplier verification, including food fraud vulnerability assessments, regular (unannounced) audits, mass balance checks and product testing, including DNA sampling, to ensure safety and quality standards. However, the victims in these crime scripts included smaller supply chain actors, such as grocery stores or areas of the supply chain, such as food service who may not have and face challenges in implementing these levels of supplier verification.
Practical and cost-effective strategies to mitigate the risk of food fraud for these companies are essential. and efforts that support smaller companies or those without technical resources to achieve certification, such as GFSI’s Global Markets (GFSI, 2022), BRCGS START! (BRCGS, 2022), or MSC’s extension of its certification to retailers, fishmongers and restaurants are all initiatives that help strengthen the supply chain. Immutable sea-to-plate traceability systems that include authentication tools such as distributed ledger technologies, e.g., blockchain, also present opportunities to reduce information asymmetries, decrease management costs and share data among diverse actors in a supply chain via immutable transactions (Tolentino-Zondervan et al., 2023). Research and initiatives already promote and support the adoption of traceability systems by SMEs (Hamdan et al., 2022; Katsikouli et al., 2021; OECD, 2019), although ongoing challenges regarding cost, interoperability, scalability, data governance regulation are acknowledged (Astill et al., 2019; Chiaraluce et al., 2024).
Post-activity
Act
For most scripts, at this point, the product is transported to the final customer and placed on the market. At this point, it has been successfully incorporated into the legitimate supply chain. Opportunities to identify fraud and determine where it occurred become more difficult as food travels along the supply chain, particularly if it does not have end-to-end traceability.
Conditions
All frauds ultimately end up with the consumer. For certain frauds, e.g., the laundering of IUU fish into legitimate supply chains and the illegal importation of siluriformes, it would be impossible for the consumer to identify based on the appearance or taste of the product. However, certain frauds, particularly where one species has been substituted for another, for example, Asian crab for domestic blue crab or Asian farmed prawn for wild-caught domestic, rely on consumer inability to tell the difference. If the product is processed, then it is less likely that concerns will be raised, as if morphological features are removed and flavouring is introduced, then it can be very difficult to distinguish certain species from each other (Reilly, 2018). As observed by the judge in Case 2, ‘Equally likely is that defendants realized that they could make more money for less work by claiming that the squid was octopus because it sells at a higher price, reasoning that most, if not all, frozen seafood consumers could not tell the difference. They then mislabelled the squid and reaped a larger profit’ (United States of America v. Anchor Foods, Inc., Advanced Frozen Foods, Inc., Roy Tuccillo, Sr. & Roy Tuccillo, Jr., 2020).
Implications
In the cases studied, the frauds were often longstanding and relied on the criminality not being detected, either internally from within the supply chain network or externally from regulators. However, at the final stage, the frauds also relied on the consumers’ inability to distinguish legitimate from illicit products. The concept of consumers as guardians of food fraud is uncomfortable. If consumers discover fraud, then it has already occurred and travelled to the end of the supply chain. However, many of these frauds were perpetrated over several years and relied on the inability of the consumer to distinguish between genuine and illicit products. Cusa et al. (2021, p. 1315) explored the concept of ‘seafood literacy…the knowledge required for consumers to make informed purchasing and feeding choices concerning personal health, environmental impact, and ethical standards’. Their study found only a 30% accuracy rate among European consumers, and consumers in the UK only correctly identified 18% of species, indicating the unfamiliarity attributed to globalised supply chains and urbanisation. Global trade means consumers are no longer restrained by location and seasonality (Anderson et al., 2018) and modern lifestyles are detaching consumers from the source of their food. Ready-to-cook products are more popular than whole fish (Menozzi et al., 2020); products lack morphological features and are also purchased through large retailers rather than fishmongers and local markets.
At the same time, consumers are increasingly making conscious decisions about the seafood they purchase and are willing to pay more for specific production methods or premium attributes (Menozzi et al., 2020; Zander & Feucht, 2018). A recent study indicated that consumers who were more aware of seafood fraud would increase demand for independently verified products (Ryburn et al., 2022), in line with other research on food fraud (Charlebois et al., 2016; Kendall et al., 2019) and that they would pay a premium for traceability systems that ensure attributes such as assured safety control (Hoque et al., 2022). Possible interventions to improve consumer guardianship could include increasing awareness of seafood fraud generally, driving consumer demands for initiatives that track the seafood supply chain from catch to consumer, advising consumers to buy from sources who are transparent about their sourcing practices and, most importantly can demonstrate that their products are legal and sustainable, potentially through the use of third-party certification such as the Marine Stewardship Council (MSC) or the Aquaculture Stewardship Council (ASC) and providing clear channels for reporting to the relevant authorities if consumers suspect fraud. However, it is essential to ensure adequate regulation with increasing numbers of certification standards (Danley, 2021), as the associated credence attributes and consequent price premiums (Asche & Bronnmann, 2017; Fonner & Gill, 2015) can also be drivers of fraud (van Ruth et al., 2017).
Finally, it is worth noting that these frauds were large-scale, generating substantial illegal profits. This prompts questions about whether the frauds were facilitated by other accomplices, for example, company accountants and suggests an additional intervention point post-activity. Unusually elevated profits, financial discrepancies or inconsistencies, unusual payment patterns, inconsistent payment schedules, or large cash deposits could indicate suspicious activity for tax authorities, auditors and banks. While automated auditing software is commonly utilised in the financial services sector, its adoption in the food industry remains limited (Jack, 2014), despite its potential application (Elahi et al., 2022b; Jack, 2014; Onarinde et al., 2023). Forensic accounting presents an effective opportunity to combat fraud, to complement traditional food fraud vulnerability assessments for supplier profiling (Jack, 2014) and by the regulators for to support detection, as well as proceeds of crime investigations.
Conclusion
The aim of this review was to comprehensively understand and break down the criminal process of conducting seafood fraud into a process of sequential acts using CSA. This provided a framework to identify the actors, decisions, processes and resources involved in the criminal process and surface opportunity structures and common characteristics that facilitated the fraudulent behaviour. The overarching aim is to identify points in the sequence where various actors could apply intervention strategies to deter fraud.
The studied crime scripts showed that for most frauds, criminal activity was perpetrated at the top of small companies where the owners were also CEOs or presidents and benefited directly from illicit activity. Those individuals who should have been guardians had become offenders, a phenomenon that contributes to fraud becoming pervasive throughout an organisation (Chan & Gibbs, 2022). Importantly, this completely undermines corporate control mechanisms, as the offenders have specialised access to food business risk management systems, processes and networks. These offenders used legitimate food business premises and facilities, transport and packaging to conduct their illegitimate activities. Regular suppliers and customers provided supply and demand for illicit products and company documentation such as labels, invoices and landing documentation concealed the crimes and assured recipients of their legality. Understanding how fraud manifests within legitimate businesses allows for a better understanding of how structural market conditions facilitate criminal opportunities for deceptive practice, insights more common in other white collar-crime literature, for example in the financial industry (Jordanoska & Lord, 2019; Snaphaan & van Ruitenburg, 2024).
In many of the cases, senior leadership directed employees to carry out deceptive acts such as repacking and mislabelling products. There is scarce information on how these food frauds were finally detected, so we are unable to ascertain for certain if any employees made disclosures. However, these particular frauds were longstanding (over several years) and therefore reliant on remaining unreported and undetected, at least for the duration of the reported criminality. Labour force characteristics in the food industry may contribute to workers’ motivation to report, as well as differing legislation on whistleblower protection (Etienne et al., 2020).Within the food industry, customers demanded no further traceability other than ‘one step back’ and did not conduct regular testing or audits. Many of the customers were small-scale food businesses that took at face value the suppliers’ longstanding industry reputations and trading relationships. Research exploring the motivation, difficulties, and barriers to more stringent controls exist in the food safety domain (Macheka et al., 2013; Lee et al., 2021), but future research to comprehend these factors in relation to food fraud is required. By mapping the sequence of actions and decisions across the crime commission process, supply chain weaknesses and potential areas of intervention were identified. These include the recognition of potential vulnerabilities from local networks, ensuring whistleblowing legislation provides robust protection, particularly for external reporting and non-immigrant and migrant workers and increasing the capabilities of consumers as food fraud guardians. The extensive use and apparent ease of document fraud suggests a requirement for increased security, scrutiny and digitisation and underlines the need for a transparent food system that ensures immutable traceability from sea to plate. For the food industry and regulators, certification, supplier assessment and horizon scanning provide different forms of assurance that known and unknown food fraud risks are being identified and mitigated (Soon-Sinclair et al., 2023). Increased support to ensure that smaller businesses and those outside manufacturing, particularly food service and retail, have knowledge and access to these countermeasures may help safeguard their supply chains against rogue operators.
Data availability
The data that support the findings of this study are available from Nexis (https://www.lexisnexis.co.uk/) and PACER (https://pacer.uscourts.gov/). Restrictions apply to the availability of the data from Nexis, which were used under license for this study. The data are, however, available from the authors upon reasonable request and with the permission of the database providers.
References
Ahmed, N., & Azra, M. N. (2022). Aquaculture production and value chains in the COVID-19 pandemic. Current Environmental Health Reports, 9(3), 423–435. https://doi.org/10.1007/s40572-022-00364-6.
Alabi, M. O., & Ngwenyama, O. (2023). Food security and disruptions of the global food supply chains during COVID-19: Building smarter food supply chains for post COVID-19 era. British Food Journal, 125(1), 167–185. https://doi.org/10.1108/BFJ-03-2021-0333.
Ambagtsheer, F., & Bugter, R. (2022). The organization of the human organ trade: A comparative crime script analysis. Crime Law and Social Change. https://doi.org/10.1007/s10611-022-10068-5.
Anderson, J. L., Asche, F., & Garlock, T. (2018). Globalization and commoditization: The transformation of the seafood market. Journal of Commodity Markets, 12, 2–8. https://doi.org/10.1016/j.jcomm.2017.12.004.
Asche, F., & Bronnmann, J. (2017). Price premiums for ecolabelled seafood: MSC certification in Germany. Australian Journal of Agricultural & Resource Economics, 61(4), 576–589. https://doi.org/10.1111/1467-8489.12217.
Astill, J., Dara, R. A., Campbell, M., Farber, J. M., Fraser, E. D. G., Sharif, S., & Yada, R. Y. (2019). Transparency in food supply chains: A review of enabling technology solutions. Trends in Food Science & Technology, 91, 240–247. https://doi.org/10.1016/j.tifs.2019.07.024.
Barrere, V., Everstine, K., Théolier, J., & Godefroy, S. (2020). Food fraud vulnerability assessment: Towards a global consensus on procedures to manage and mitigate food fraud. Trends in Food Science & Technology, 100, 131–137. https://doi.org/10.1016/j.tifs.2020.04.002.
Beia, S. I., Bran, M., Petrescu, I., & Beia, V. E. (2020). Food fraud incidents: Findings from the latest rapid alert system for food and feed (RASFF) report. Scientific Papers: Management Economic Engineering in Agriculture & Rural Development, 20(2), 45–52. https://managementjournal.usamv.ro/pdf/vol.20_2/Art5.pdf.
Bellotti, E., Spencer, J., Lord, N., & Benson, K. (2020). Counterfeit alcohol distribution: A criminological script network analysis. European Journal of Criminology, 17(4), 373–398. https://doi.org/10.1177/1477370818794870.
Ben Hassen, T., & El Bilali, H. (2022). Impacts of the Russia-Ukraine war on global food security: Towards more sustainable and resilient food systems? Foods, 11(15), 2301. https://doi.org/10.3390/foods11152301.
Benson, M. L., & Simpson, S. (2018). White-collar crime: An opportunity perspective (3rd ed.). Routledge.
Benson, M. L., Madensen, T. D., & Eck, J. E. (2009). White-collar crime from an opportunity perspective. In S. S. Simpson & D. Weisburd (Eds.), The Criminology of White-Collar Crime (pp. 175–193). Springer New York. https://doi.org/10.1007/978-0-387-09502-8_9.
Benton, T. G., Froggatt, A., Wellesley, L., Grafham, O., King, R., Morisetti, N., Nixey, J., & Schroder, P. (2022). The Ukraine war and threats to food and energy security. Chatham House. https://doi.org/10.55317/9781784135225.
Berbotto, A. A., & Chainey, S. P. (2021). Theft of oil from pipelines: An examination of its crime commission in Mexico using crime script analysis. Global Crime, 22(4), 265–287. https://doi.org/10.1080/17440572.2021.1925552.
Berg, L., Farbenblum, B., & Verma, S. (2023). Breaking the Silence Migrant Justice Institute. https://www.migrantjustice.org/s/Feb-23-Breaking-the-Silence-Proposal-for-Whistleblower-Protections-xtna.pdf. Accessed 15 July 2023.
Bier, D. (2021). H–2B Visas: The complex process for nonagricultural employers to hire guest workers Cato Institute. https://www.cato.org/publications/policy-analysis/h-2b-visas-complex-process-nonagricultural-employers-hire-guest-workers. Accessed 15 July 2023.
Bindt, V. (2016). Costs and benefits of the food fraud vulnerability assessment in the Dutch food supply chain. https://edepot.wur.nl/390258. Accessed 10 June 2023.
Borrion, H. (2013). Quality assurance in crime scripting. Crime Science, 2(1), 6. https://doi.org/10.1186/2193-7680-2-6.
Bosko, S. A., Foley, D. M., & Hellberg, R. S. (2018). Species substitution and country of origin mislabeling of catfish products on the U.S. commercial market. Aquaculture, 495, 715–720. https://doi.org/10.1016/j.aquaculture.2018.06.052.
Brayley, H., Cockbain, E., & Laycock, G. (2011). The value of crime scripting: Deconstructing internal child sex trafficking. 5(2), 132–143. https://doi.org/10.1093/police/par024.
BRCGS (2018). Global standard food safety (Issue 8) https://www.brcgs.com/product/global-standard-for-food-safety-issue-8/p-616. Accessed 8 August 2023.
BRCGS (2022). BRCGS Start!https://www.brcgs.com/our-standards/start/. Accessed 8 August 2023.
Castellanos Contreras, D., Rebert, T., & Bhattacharjee, S. (2016). S. Raising the floor for supply chain workers: US seafood supply chains, 2016. https://www.ituccsi.org/IMG/pdf/nga_raising_the_floor_for_supply_chain_workers_2016.pdf. Accessed 10 June 2023.
Chainey, S. P., & Berbotto, A. A. (2022). A structured methodical process for populating a crime script of organized crime activity using OSINT. Trends in Organized Crime, 25(3), 272–300. https://doi.org/10.1007/s12117-021-09428-9.
Chan, F., & Gibbs, C. (2022). When guardians become offenders: Understanding guardian capability through the lens of corporate crime. Criminology, 60, https://doi.org/10.1111/1745-9125.12300.
Charlebois, S., Schwab, A., Henn, R., & Huck, C. W. (2016). Food fraud: An exploratory study for measuring consumer perception towards mislabeled food products and influence on self-authentication intentions. Trends in Food Science & Technology, 50, 211–218. https://doi.org/10.1016/j.tifs.2016.02.003.
Chiaraluce, G., Bentivoglio, D., Finco, A., et al. (2024). Exploring the role of blockchain technology in modern high-value food supply chains: Global trends and future research directions. Agricultural Economics, 12, 6. https://doi.org/10.1186/s40100-024-00301-1.
Chiu, Y. N., & Leclerc, B. (2021). Scripting stranger sexual offenses against women. Sexual Abuse: A Journal of Research & Treatment (Sage), 33(2), 223–249. https://doi.org/10.1177/1079063219889055.
Cohen, N. J., Deeds, J. R., Wong, E. S., Hanner, R. H., Yancy, H. F., White, K. D., Thompson, T. M., Wahl, M., Pham, T. D., Guichard, F. M., Huh, I., Austin, C., Dizikes, G., & Gerber, S. I. (2009). Public health response to puffer fish (tetrodotoxin) poisoning from mislabeled product [Article]. Journal of Food Protection, 72(4), 810–817. https://doi.org/10.4315/0362-028X-72.4.810.
Cook, A., Reynald, D. M., Leclerc, B., & Wortley, R. (2019). Learning about situational crime prevention from offenders: Using a script framework to compare the commission of completed and disrupted sexual offenses. Criminal Justice Review (Sage Publications), 44(4), 431–451. https://doi.org/10.1177/0734016818812149.
Cornish, D. (1994). The procedural analysis of offending and its relevance for situational prevention, in Clarke, R.V. (Ed.), Crime Prevention Studies, Vol. 3, Criminal Justice Press, Monsey, NY, pp. 151–196.
Cornish, D., & Clarke, R. V. (2002). Analyzing organized crimes. In A. Piquero, & S. Tibbetts (Eds.), Rational choice and criminal behaviour. Routledge.
Cox, A., Wohlschlegel, A., Jack, L., & Smart., E. (2020). The cost of food crime https://www.food.gov.uk/sites/default/files/media/document/the-cost-of-food-crime.pdf. Accessed 23 March 2023.
Croall, H. (1999). White-collar crime: an overview and discussion. In P. Davies, P. Francis, & V. Jupp (Eds.), Invisible Crimes: Their Victims and their Regulation (pp. 29–53). Palgrave Macmillan UK. https://doi.org/10.1007/978-1-349-27641-7_2.
Cusa, M., Falcão, L., De Jesus, J., Biolatti, C., Blondeel, L., Bracken, F. S. A., Devriese, L., Garcés-Pastor, S., Minoudi, S., Gubili, C., Acutis, P. L., & Mariani, S. (2021). Fish out of water: Consumers’ unfamiliarity with the appearance of commercial fish species. Sustainability Science, 16(4), 1313–1322. https://doi.org/10.1007/s11625-021-00932-z.
Danley, S. (2021). July 27). IFT FIRST: Demand for sustainability certifications is growing. Food Business News. https://www.foodbusinessnews.net/articles/19192-ift-first-demand-for-sustainability-certifications-is-growing.
Daub, T. (2006). Most Maryland crabs come from Asia. Foreign Policy https://foreignpolicy.com/2006/05/01/most-maryland-crabs-come-from-asia/.
Davies, J. (2018). From severe to routine labour exploitation: The case of migrant workers in the UK food industry. Criminology & Criminal Justice, 19(3), 294–310. https://doi.org/10.1177/1748895818762264.
de Busser, E. (2014). Open source data and criminal investigations: Anything you publish can and will be used against you. Groningen Journal of International Law, 2(2), 90–114. https://doi.org/10.21827/5a86a843e5c9d.
de Korte, L. R., & Kleemans, E. R. (2022). Contract killings: A crime script analysis. Trends in Organized Crime, 25(1), 130–143. https://doi.org/10.1007/s12117-021-09411-4.
Dehghanniri, H., & Borrion, H. (2021). Crime scripting: A systematic review. European Journal of Criminology, 18(4), 504–525. https://doi.org/10.1177/1477370819850943.
Department of Justice (DOJ) (2020). Seafood processor pleads guilty to selling foreign crabmeat falsely labeled as blue crab from USA. https://www.justice.gov/opa/pr/seafood-processor-pleads-guilty-selling-foreign-crabmeat-falsely-labeled-blue-crab-usa.
Department for Business, Energy and Industrial Strategy (BEIS) (2019). Business population estimates for the UK and regions: 2019 statistical release https://www.gov.uk/government/statistics/business-population-estimates-2019/business-population-estimates-for-the-uk-and-regions-2019-statistical-release-html. Accessed 15 July 2023.
Department of Justice (DOJ). (2023). ). Keys lobster company and its president pled guilty to exporting falsely labeled product. U.S. Attorney’s Office, Southern District of Florida. https://www.justice.gov.
Ding, S., & Wu, Z. (2014). Family ownership and corporate misconduct in U.S. small firms. Journal of Business Ethics, 123(2), 183–195.
Donegan, M. (2019). Crime script for mandate fraud. Journal of Money Laundering Control, 22(4), 770–781. https://doi.org/10.1108/JMLC-03-2019-0025.
Dove, C. (2011, August 24). Spain’s farmed bream, bass prices rise. SeafoodSource. https://www.seafoodsource.com/news/supply-trade/spain-s-farmed-bream-bass-prices-rise.
Eck, J. E., & Clarke, R. V. (2019). Situational crime prevention: Theory, practice and evidence. In M. Krohn, N. Hendrix, P. Hall, & G. Lizotte, A. (Eds.), Handbook on crime and Deviance. Springer. Handbooks of Sociology and Social Research https://doi.org/10.1007/978-3-030-20779-3_18.
Elahi, S., Elliott, C., Spink, J., & Points, J. (2022a). Report for Defra: Food fraud project 25069, phase 1: Food fraud drivers publication version. Accessed 15 August 2023. https://randd.defra.gov.uk/ProjectDetails?ProjectId=20179.
Elahi, S., Elliott, C., Spink, J., & Points, J. (2022b). Report for Defra: Food fraud project 25069, Phase 2: Food fraud mitigation tools - publication version. Accessed 23 February 2024. https://randd.defra.gov.uk/ProjectDetails?ProjectId=20179.
Elliott, C. (2014). Elliott review into the integrity and assurance of food supply networks—Final report (a national food crime prevention framework). https://www.gov.uk/government/publications/elliott-review-into-the-integrity-and-assurance-of-food-supply-networks-final-report.
Etienne, J., Campbell, L., Jager, E., Verstraeten, Y., Rigoni, M., & McEntaggart, K. (2020). Barriers to and enablers of the reporting of intelligence regarding food crime ICF Consulting Services Limited for Food Standards Agency and National Food Crime Unit. https://www.food.gov.uk/sites/default/files/media/document/food-crime-intelligence-reporting-barriers-and-enablers.pdf.
Europol (2021). Opson IX. https://www.europol.europa.eu/publications-events/publications/operation-opson-ix-%E2%80%93-analysis-report. Accessed 25 July 2023.
Ewelt-Knauer, C., Schwering, A., & Winkelmann, S. (2022). Doing good by doing bad: How tone at the top and tone at the bottom impact performance-improving noncompliant behavior. Journal of Business Ethics, 175(3), 609–624. https://doi.org/10.1007/s10551-020-04647-6.
Fenoff, R., & Lee, B. (2023). February 6). Food Documents as Food Fraud Facilitators. Food Safety Magazine https://www.food-safety.com/articles/8333-food-documents-as-food-fraud-facilitators.
Fonner, F., & Gill, S. (2015). Willingness to pay for multiple seafood labels in a niche market. Marine Resource Economics, 30(1), 51–70. https://doi.org/10.1086/679466.
Food and Agriculture Organisation (FAO) (2011). European Seabass and Gilthead seabream - August 2011. https://www.fao.org/in-action/globefish/market-reports/resource-detail/en/c/338057/. Accessed 25 July 2023.
Food Standards Agency (FSA) (2018). Handling disclosures https://www.food.gov.uk/about-us/handling-disclosures. Accessed 15 July 2023.
Food Standards Agency (FSA) (2023). Report a food crime https://www.food.gov.uk/contact/businesses/report-safety-concern/report-a-food-crime. Accessed 9 July 2023.
Food Standards Agency and Food Standards Scotland (FSA & FSS) (2020). Food Crime Strategic Assessment 2020. https://www.food.gov.uk/sites/default/files/media/document/food-crime-strategic-assessment-2020_2.pdf. Accessed 15 July 2023.
Former Royal Navy chef jailed over £1m (2015, January 30). ‘fake’ sea bass scam The Telegraph https://www.telegraph.co.uk/news/uknews/crime/11378898/Former-Royal-Navy-chef-jailed-over-1m-fake-sea-bass-scam.html.
Fox, M., Mitchell, M., Dean, M., Elliott, C., & Campbell, K. (2018). The seafood supply chain from a fraudulent perspective. Food Security: The Science Sociology and Economics of Food Production and Access to Food, 10(4), 939. https://doi.org/10.1007/s12571-018-0826-z.
GFSI (2022). Participate: Strategic Review of the Global Markets Programme. https://mygfsi.com/how-to-implement/global-markets/. Accessed 15 July 2023.
Gilmour, N. (2014). Understanding money laundering: a crime script approach. The European Review of Organised Crime 1(2), 2014, 35–56.
Godde, C. M., Mason-D’Croz, D., Mayberry, D. E., Thornton, P. K., & Herrero, M. (2021). Impacts of climate change on the livestock food supply chain; a review of the evidence. Global Food Security, 28, 100488. https://doi.org/10.1016/j.gfs.2020.100488.
Goodall, O. (2019). Beyond wildlife crime: Realist social relations crime scripts of the illegal taking of deer [unpublished doctoral dissertation] University of Cardiff.
Gottschalk, P. (2021). Filling the gap in white-collar crime detection between government and governance: The role of investigative journalists and fraud examiners. Journal of White Collar and Corporate Crime, 2(1), 36–46. https://doi.org/10.1177/2631309X20925818.
Gottschalk, P., & Gunnesdal, L. (2018). White-Collar Crime Detection. In P. Gottschalk & L. Gunnesdal (Eds.), White-collar crime in the shadow economy: Lack of detection, investigation and conviction compared to social security fraud, pp. 111–134. Springer International Publishing. https://doi.org/10.1007/978-3-319-75292-1_10.
Griffith, D. (1997). New immigrants in an old industry: Mexican h-2b workers in the mid-Atlantic blue crab processing industry, University of Delaware, Newark, DE. https://migration.ucdavis.edu/cf/more.php?id=148. Accessed 7 August 2023.
Gussow, K. E. (2020). Finding food fraud: Explaining the detection of food fraud in the Netherlands. PhD-Thesis - Research and graduation internal, Vrije Universiteit Amsterdam]. Accessed 15 July 2023.
Gussow, K. E., & Mariët, A. (2022). The scope of food fraud revisited. Crime Law and Social Change, 78(5), 621–642. https://doi.org/10.1007/s10611-022-10055-w.
Guzmán-Luna, P., Mauricio-Iglesias, M., Flysjö, A., & Hospido, A. (2022). Analysing the interaction between the dairy sector and climate change from a life cycle perspective: A review. Trends in Food Science & Technology, 126, 168–179. https://doi.org/10.1016/j.tifs.2021.09.001.
Hamdan, I. K. A., Aziguli, W., Zhang, D., Sumarliah, E., & Usmanova, K. (2022). Forecasting blockchain adoption in supply chains based on machine learning: Evidence from Palestinian food SMEs. British Food Journal, 124(12), 4592–4609. https://doi.org/10.1108/BFJ-05-2021-0535.
Hedgpeth, D. (2022, May 22). Blue crab population in Chesapeake Bay hits record low. The Washington Post. https://www.washingtonpost.com/dc-md-va/2022/05/25/blue-crabs-chesapeake-bay-record-low/.
Hoque, M. Z., Akhter, N., & Chowdhury, M. S. R. (2022). Consumers’ preferences for the traceability information of seafood safety. Foods, 11(12). https://doi.org/10.3390/foods11121675.
Huang, P. (2015). An inverse demand system for the differentiated blue crab market in Chesapeake Bay. Marine Resource Economics, 30(2), 139–156. https://doi.org/10.1086/679971.
Huisman, W., & van Ruth, S. (2022). Risky business: Food fraud vulnerability assessments. Crime Law Soc Change, 78, 559–576. https://doi.org/10.1007/s10611-021-10008-9.
Hutchings, A. and Pastrana, S. (2019). Understanding eWhoring. IEEE European Symposium on Security and Privacy (EuroS&P) https://doi.org/10.1109/EuroSP.2019.00024.
Hutchings, A., & Holt, T. J. (2015). A crime script analysis of the online stolen data market. The British Journal of Criminology, 55(3), 596–614. https://doi.org/10.1093/bjc/azu106.
Hyde, R., & Savage, A. (2015). Whistleblowing without borders: the risks and rewards of transnational whistleblowing networks. In D. Lewis, & W. Vandekerckhove (Eds.), Developments in whistleblowing research 2015. International Whistleblowing Research Network. https://nottingham-repository.worktribe.com/output/981352.
Jack, L. (2014, September 5). Food fraud is still hard to detect – so follow the money. The Conversation https://theconversation.com/food-fraud-is-still-hard-to-detect-so-follow-the-money-31322.
Jagtap, S., Trollman, H., Trollman, F., Garcia-Garcia, G., Parra-López, C., Duong, L., Martindale, W., Munekata, P. E. S., Lorenzo, J. M., Hdaifeh, A., Hassoun, A., Salonitis, K., & Afy-Shararah, M. (2022). The Russia-Ukraine conflict: Its implications for the global food supply chains. Foods, 11(14), 2098–2098. https://doi.org/10.3390/foods11142098.
Jordanoska, A., & Lord, N. (2019). Scripting the mechanics of the benchmark manipulation corporate scandals: The ‘guardian’ paradox. European Journal of Criminology, 17(1), 9–30. https://doi.org/10.1177/1477370819850124.
Junger, M., Wang, V., & Schlömer, M. (2020). Fraud against businesses both online and offline: Crime scripts, business characteristics, efforts, and benefits. Crime Science, 9(1), 13. https://doi.org/10.1186/s40163-020-00119-4.
Katsikouli, P., Wilde, A. S., Dragoni, N., & Høgh-Jensen, H. (2021). On the benefits and challenges of blockchains for managing food supply chains. Journal of the Science of Food and Agriculture, 101(6), 2175–2181. https://doi.org/10.1002/jsfa.10883.
Kendall, H., Clark, B., Rhymer, C., Kuznesof, S., Hajslova, J., Tomaniova, M., Brereton, P., & Frewer, L. (2019). A systematic review of consumer perceptions of food fraud and authenticity: A European perspective. Trends in Food Science & Technology, 94, 79–90. https://doi.org/10.1016/j.tifs.2019.10.005.
Kennedy, J. P., Haberman, C. P., & Wilson, J. M. (2018). Occupational pharmaceutical counterfeiting schemes: A crime scripts analysis. Victims & Offenders, 13(2), 196–214. https://doi.org/10.1080/15564886.2016.1217961.
Kitch, C. J., Tabb, A. M., Marquis, G. E., & Hellberg, R. S. (2023). Species substitution and mislabeling of ceviche, poke, and sushi dishes sold in Orange County, California. Food Control, 146. https://doi.org/10.1016/j.foodcont.2022.109525.
Kroetz, K., Luque, G. M., Gephart, J. A., Jardine, S. L., Lee, P., Chicojay Moore, K., Cole, C., Steinkruger, A., & Donlan, C. J. (2020). Consequences of seafood mislabeling for marine populations and fisheries management. Proceedings of the National Academy of Sciences of the United States of America, 117(48), 30318–30323. https://doi.org/10.1073/pnas.2003741117.
Lawrence, S., Elliott, C., Huisman, W., Dean, M., & van Ruth, S. (2022). The 11 sins of seafood: Assessing a decade of food fraud reports in the global supply chain. Comprehensive Reviews in food Science and food Safety, 21(4), 3746–3769. https://doi.org/10.1111/1541-4337.12998.
Lee, J. C., Daraba, A., Voidarou, C., Rozos, G., Enshasy, H. A. E., & Varzakas, T. (2021). Implementation of food safety management systems along with other management tools (HAZOP, FMEA, Ishikawa, Pareto). The Case Study of Listeria monocytogenes and correlation with Microbiological Criteria. Foods, 10(9), 2169. https://doi.org/10.3390/foods10092169.
Lemieux, A. M., & Bruschi, N. (2019). The production of jaguar paste in Suriname: A product-based crime script. Crime Science: An Interdisciplinary Journal, 8(1). https://doi.org/10.1186/s40163-019-0101-4.
Levi, M., & Lord, N. (2017). White-Collar and Corporate Crime in the Oxford Handbook of Criminology. Oxford University Press.
Lewis, D. (2008). Ten years of public interest disclosure legislation in the UK: Are whistleblowers adequately protected? Journal of Business Ethics, 82(2), 497–507. https://doi.org/10.1007/s10551-008-9899-5.
Li, A., Tang, Q., Kearney, K. E., Nagy, K. L., Zhang, J., Buchanan, S., & Turyk, M. E. (2022). Persistent and toxic chemical pollutants in fish consumed by asians in Chicago, United States. Science of the Total Environment, 811, 152214. https://doi.org/10.1016/j.scitotenv.2021.152214.
Loggen, J., & Leukfeldt, R. (2022). Unraveling the crime scripts of phishing networks: An analysis of 45 court cases in the Netherlands. Trends in Organized Crime, 1–21. https://doi.org/10.1007/s12117-022-09448-z.
Lord, N., Flores Elizondo, C. J., & Spencer, J. (2017a). The dynamics of food fraud: The interactions between criminal opportunity and market (dys)functionality in legitimate business. Criminology & Criminal Justice, 17(5), 605–623. https://doi.org/10.1177/1748895816684539.
Lord, N., Spencer, J., Albanese, J., & Flores Elizondo, C. (2017b). In pursuit of food system integrity: The situational prevention of food fraud enterprise. European Journal on Criminal Policy and Research, 23(4), 483–501. https://doi.org/10.1007/s10610-017-9352-3.
Lord, N., Flores Elizondo, C., Davies, J., & Spencer, J. (2021). Fault lines of food fraud: Key issues in research and policy. Crime Law and Social Change: An Interdisciplinary Journal, 1. https://doi.org/10.1007/s10611-021-09983-w.
Love, D., Rodman, S., Neff, R., & Nachman, K. (2011). Veterinary drug residues in seafood inspected by the European Union, United States, Canada, and Japan from 2000 to 2009. Environmental Science & Technology, 45, 7232–7240. https://doi.org/10.1021/es201608q.
Macheka, L., Manditsera, F. A., Ngadze, R. T., Mubaiwa, J., & Nyanga, L. K. (2013). Barriers, benefits and motivation factors for the implementation of food safety management system in the food sector in Harare Province, Zimbabwe. Food Control, 34(1), 126–131. https://doi.org/10.1016/j.foodcont.2013.04.019.
Manning, L., & Soon, J. M. (2016). Food safety, food fraud, and food defense: A fast evolving literature. Journal of Food Science, 81(4), R823–R834. https://doi.org/10.1111/1750-3841.13256.
Menozzi, D., Nguyen, T. T., Sogari, G., Taskov, D., Lucas, S., Castro-Rial, J. L. S., & Mora, C. (2020). Consumers’ preferences and willingness to pay for fish products with health and environmental labels: Evidence from five European countries. Nutrients, 12(9), 2650. https://doi.org/10.3390/nu12092650.
Miller, D., Jessel, A., & Mariani, S. (2012). Seafood mislabelling: Comparisons of two western European case studies assist in defining influencing factors, mechanisms and motives. Fish and Fisheries, 13(3), 345–358. https://doi.org/10.1111/j.1467-2979.2011.00426.x.
Moreto, W. D., & Clarke, R. V. (2013). Script analysis of the transnational illegal market in endangered species. In B. Leclerc, & R. Wortley (Eds.), Cognition and crime: Offender decision making and script analyses (pp. 209–220). Routledge.
Moy, G. G. (2018). The role of whistleblowers in protecting the safety and integrity of the food supply. NPJ Science of food, 2, 8. https://doi.org/10.1038/s41538-018-0017-5.
National Oceanic and Atmospheric Administration (NOAA) (2023). Vessel trip reporting in the Greater Atlantic region. https://www.fisheries.noaa.gov/new-england-mid-atlantic/resources-fishing/vessel-trip-reporting-greater-atlantic-region. Accessed 22 August.
National Police Chief’s Council (2020). Internet intelligence and investigations strategy https://library.college.police.uk/docs/NPCC/Internet-Intelligence-and-Investigation-v1.5.pdf. Accessed 17 May.
Niederer, M., Lang, S., Roux, B., Stebler, T., & Hohl, C. (2019). Identification of nitrite treated tuna fish meat via the determination of nitrous oxide by head space-gas chromatography/mass spectrometry. F1000Research, 8, 711. https://doi.org/10.12688/f1000research.19304.2.
Oceana (2015). Oceana reveals mislabeling of iconic Chesapeake blue crab https://oceana.org/reports/oceana-reveals-mislabeling-iconic-chesapeake-blue-crab/. Accessed 17 May 2023.
Oceana (2018). The rise and fall of the Codfather, North America’s most notorious fishing criminal. https://oceana.ca/en/blog/rise-and-fall-codfather-north-americas-most-notorious-fishingcriminal/#:~:text = The%20charges%20against%20him%20include,it%20is%20harming%20the%20oceans. Accessed 17 May 2023.
OECD (2019). Blockchain for SMEs and entrepreneurs. https://www.oecd.org/cfe/SMEs/blockchainSMEs.htm. Accessed 14 August 2023.
Onarinde, B., Manning, L., Skoczylis, J., Cowen, N., Oyeyinka, S., Thompson, M., MacLeod, A., & James, C. (2023). What works to prevent food fraud. https://doi.org/10.46756/sci.fsa.lzy803.
Osborne, J. R., & Capellan, J. A. (2017). Examining active shooter events through the rational choice perspective and crime script analysis. Security Journal, 30(3), 880–902. https://doi.org/10.1057/sj.2015.12.
Palumbo, L., Corrado, A., & Triandafyllidou, A. (2022). Migrant labour in the agri-food system in Europe: Unpacking the social and legal factors of exploitation. European Journal of Migration and Law, 24(2), 179–192. https://doi.org/10.1163/15718166-12340125.
Paolisso, M. (2007). Taste the traditions: Crabs, crab cakes, and the Chesapeake Bay blue crab fishery. American Anthropologist, 109(4), 654–665. https://doi.org/10.1525/AA.2007.109.4.654.
Pardo, M. Á., Jiménez, E., & Pérez-Villarreal, B. (2016). Misdescription incidents in seafood sector. Food Control, 62, 277–283. https://doi.org/10.1016/j.foodcont.2015.10.048.
Peters, B. C. (2020). Nigerian piracy: Articulating business models using crime script analysis. International Journal of Law Crime and Justice, 62, 100410. https://doi.org/10.1016/j.ijlcj.2020.100410.
Petrossian, G. A., & Pezzella, F. S. (2018). IUU fishing and seafood fraud: Using crime script analysis to inform intervention. The ANNALS of the American Academy of Political and Social Science, 679(1), 121–139. https://doi.org/10.1177/0002716218784533.
Pigłowski, M. (2023). Hazards in seafood notified in the Rapid Alert System for Food and feed (RASFF) in 1996–2020. Water, 15, 548. https://doi.org/10.3390/w15030548.
Pramod, G., Nakamura, K., Pitcher, T. J., & Delagran, L. (2014). Estimates of illegal and unreported fish in seafood imports to the USA. Marine Policy, 48, 102–113. https://doi.org/10.1016/j.marpol.2014.03.019.
Rahman, S., Majumder, M. A. A., Ahasan, R., Ahmed, S. M. M., Das, P., & Rahman, N. (2016). The extent and magnitude of formalin adulteration in fish sold in domestic markets of Bangladesh: A literature review. International Journal of Consumer Studies, 40(2), 152–159. https://doi.org/10.1111/ijcs.12238.
Ranta, R., & Mulrooney, H. (2021). Pandemics, food (in)security, and leaving the EU: What does the Covid-19 pandemic tell us about food insecurity and Brexit. Social Sciences & Humanities Open, 3(1). https://doi.org/10.1016/j.ssaho.2021.100125.
Reilly, A. (2018). Overview of food fraud in the fisheries sector, by Alan Reilly Rome, Italy Fisheries and Aquaculture Circular No. 1165. https://www.fao.org/documents/card/en/c/I8791EN/. Accessed 10 June 2023.
Robson, K., Dean, M., Haughey, S., & Elliott, C. (2021). A comprehensive review of food fraud terminologies and food fraud mitigation guides. Food Control, 120. https://doi.org/10.1016/j.foodcont.2020.107516.
Rowe, E., Akman, T., Smith, R., & Tomison, A. (2013). Organised crime and public sector corruption: A crime scripts analysis of tactical displacement risks. Trends & issues in crime and criminal justice, No. 444. https://www.aic.gov.au/publications/tandi/tandi444.
Ryburn, S. J., Ballantine, W. M., Loncan, F. M., Manning, O. G., Alston, M. A., Steinwand, B., & Bruno, J. F. (2022). Public awareness of seafood mislabeling. PeerJ, 10, e13486. https://doi.org/10.7717/peerj.13486.
Sameera, S., Jose, D., Harikrishnan, M., & Ramachandran, A. (2021). Species substitutions revealed through genotyping: Implications of traceability limitations and unregulated fishing. Food Control, 123, 107779. https://doi.org/10.1016/j.foodcont.2020.107779.
Sampson, F. (2016). Intelligent evidence: Using open source intelligence (OSINT) in criminal proceedings. The Police Journal, 90(1), 55–69. https://doi.org/10.1177/0032258X16671031.
Scanes, E., & Byrne, M. (2023). Warming and hypoxia threaten a valuable scallop fishery: A warning for commercial bivalve ventures in climate change hotspots. Global Change Biology, 29(8), 2043–2045. https://doi.org/10.1111/gcb.16606.
Scott, S., Craig, G., & Geddes, A. (2012). Experiences of forced labour in the UK food industry. https://www.jrf.org.uk/sites/default/files/jrf/migrated/files/forced-labour-food-industry-full.pdf. Accessed 17 July 2023.
Sharpe, M. (2017, December 30). Guilty pleas end fish fraud trial Manawatu Standard https://www.pressreader.com/new-zealand/manawatu-standard/20171230/281728384894558.
Silva, A. J., Hellberg, R. S., & Hanner, R. H. (2021). Chapter 7 - Seafood fraud. Food Fraud, 109–137. https://doi.org/10.1016/B978-0-12-817242-1.00008-7. https://doi-org.queens.ezp1.qub.ac.uk/.
Sinclair, J. (2022). Is it time for a whistleblower visa?https://freemovement.org.uk/is-it-time-for-a-whistleblower-visa/. Accessed 10 August 2023.
Skidmore, A. (2021). Using crime script analysis to elucidate the details of Amur tiger poaching in the Russian Far East. Crime Science, 10(1), 16. https://doi.org/10.1186/s40163-021-00150-z.
U.S. Small Business Administration (SBA) (2023). Size standards. https://www.sba.gov/size-standards/index.html.
Smith, R. (2015). Documenting the UK Black Fish scandal as a case study of criminal entrepreneurship. International Journal of Sociology and Social Policy, 35(3/4), 199–221. https://doi.org/10.1108/IJSSP-02-2014-0018.
Smith, R., Manning, L., & McElwee, G. (2017). Critiquing the inter-disciplinary literature on food-fraud. International Journal of Rural Criminology, 3(2), 250–270. https://doi.org/10.18061/1811/81045
Smith, R., Manning, L., & McElwee, G. (2022). The anatomy of ‘So-Called Food-Fraud scandals’ in the UK 1970–2018: Developing a Contextualised understanding. Crime Law and Social Change, 78(5), 535–558. https://doi.org/10.1007/s10611-021-10000-3.
Snaphaan, T., & van Ruitenburg, T. (2024). Financial Crime Scripting: An analytical method to generate, organise and systematise knowledge on the financial aspects of profit-driven crime. Eur J Crim Policy Res. https://doi.org/10.1007/s10610-023-09571-9.
Soltani, B. (2014). The anatomy of corporate fraud: A comparative analysis of high profile American and European corporate scandals. Journal of Business Ethics, 120(2), 251–274. https://doi.org/10.1007/s10551-013-1660-z.
Soon, J. M. (2022). Chapter 34 - food fraud countermeasures and consumers: A future agenda. Future Foods, 597–611. https://doi.org/10.1016/B978-0-323-91001-9.00027-X. https://doi-org.queens.ezp1.qub.ac.uk/.
Soon, J. M., & Manning, L. (2017). Whistleblowing as a countermeasure strategy against food crime. British Food Journal, 119(12), 2630–2652. https://doi.org/10.1108/BFJ-01-2017-0001.
Soon, J. M., Manning, L., & Smith, R. (2019). Advancing understanding of pinch-points and crime prevention in the food supply chain. Crime Prevention and Community Safety, 21. https://doi.org/10.1057/s41300-019-00059-5.
Soon-Sinclair, J. M., Nyarugwe, S., & Jack, L. (2023). Food fraud and mitigating strategies of UK food supply chain during COVID-19. Food Control, 148, 109670. https://doi.org/10.1016/j.foodcont.2023.109670.
Sosnowski, M. C., Weis, J. S., & Petrossian, G. A. (2020). Using crime script analysis to understand the illegal harvesting of live corals: Case studies from Indonesia and Fiji. Journal of Contemporary Criminal Justice, 36(3), 384–402. https://doi.org/10.1177/1043986220910295.
Spencer, J., Lord, N., Benson, K., & Bellotti, E. (2018). C’ is for commercial collaboration: Enterprise and structure in the ‘middle market’ of counterfeit alcohol distribution. Crime Law and Social Change, 70(5), 543–560. https://doi.org/10.1007/s10611-018-9781-z.
Spink, J. W. (2019). Food Fraud Prevention: Introduction, Implementation, and Management (1st 2019. ed.) [eBook]. Springer New York.
Spink, J., & Moyer, D. C. (2011). Defining the Public Health Threat of Food Fraud. Journal of Food Science, 76(9), R157–R163. https://doi.org/10.1111/j.1750-3841.2011.02417.x.
Spink, J., Moyer, D. C., Park, H., & Heinonen, J. A. (2013). Defining the types of counterfeiters, Counterfeiting, and Offender Organizations. Crime Science, 2, 1–10. https://doi.org/10.1186/2193-7680-2-8.
Spink, J., Moyer, D. C., & Whelan, P. (2016). The role of the public private partnership in Food Fraud prevention—includes implementing the strategy. Current Opinion in Food Science, 10, 68–75. https://doi.org/10.1016/j.cofs.2016.10.002.
Spink, J., Ortega, D. L., Chen, C., & Wu, F. (2017). Food fraud prevention shifts the food risk focus to vulnerability. Trends in Food Science & Technology, 62, 215–220. https://doi.org/10.1016/j.tifs.2017.02.012.
SQF Institute (2023). SQF Certified Site Directory. https://go.sqfi.com/assessment-database/sqf-certified-site-directory/. Accessed 18 August 2023.
Straut-Eppsteiner, H. (2016). Coming and going: Mexican women guestworkers in the US crab industry. Latino Studies, 14(4), 482–503. https://doi.org/10.1057/s41276-016-0013-3.
Sumaila, U. R., Zeller, D., Hood, L., Palomares, M. L. D., Li, Y., & Pauly, D. (2020). Illicit trade in marine fish catch and its effects on ecosystems and people worldwide. Science Advances, 6(9), eaaz3801. https://doi.org/10.1126/sciadv.aaz3801.
Tähkäpää, S., Maijala, R., Korkeala, H., & Nevas, M. (2015). Patterns of food frauds and adulterations reported in the EU rapid alert system for food and feed and in Finland. Food Control, 47, 175–184. https://doi.org/10.1016/j.foodcont.2014.07.007.
Tolentino-Zondervan, F., Ngoc, P. T. A., & Roskam, J. L. (2023). Use cases and future prospects of blockchain applications in global fishery and aquaculture value chains. Aquaculture, 565, 739158. https://doi.org/10.1016/j.aquaculture.2022.739158.
Tompson, L., & Chainey, S. (2011). Profiling illegal waste activity: Using crime scripts as a data collection and analytical strategy. European Journal on Criminal Policy and Research, 17(3), 179–201. https://doi.org/10.1007/s10610-011-9146-y.
Towers, L. (2012, April 15). European seabass and gilthead seabream markets 2011. thefishsite.com. https://thefishsite.com/articles/european-seabass-and-gilthead-seabream-markets-2011.
Ulberth, F. (2020). Tools to combat food fraud – a gap analysis. Food Chemistry, 330, 127044. https://doi.org/10.1016/j.foodchem.2020.127044.
United States of America v. Alphin Brothers, Inc (2014). ‘‘Criminal Information’ (court filing), E.D.N.C., Vol. No. 5:14-CR-287-1H, NO. Docket 1, 12, December 2014, via PACER.
United States of America v. Anchor Foods, Inc., Advanced Frozen Foods, Inc., Roy Tuccillo, Sr. and Roy Tuccillo (2020). Jr. Report and recommendation, (court filing), E.D.N.Y., Vol. 2:18-cr-00522, no. Docket 47, 10 May, 2020, via PACER.
United States of America v. Capt. Neill’s Seafood Inc. &, Philip, R., & Carawan (2019). ‘Criminal information’, (Court filing), Vol 2:19-CR-12-1FL, no Docket 1, 26 June, 2019, via PACER.
van Nguyen, T. (2021). The modus operandi of transnational computer fraud: A crime script analysis in Vietnam. Trends in Organized Crime, 1–22. https://doi.org/10.1007/s12117-021-09422-1.
van Ruth, S. M., Huisman, W., & Luning, P. A. (2017). Food fraud vulnerability and its key factors. Trends in Food Science & Technology, 67, 70–75. https://doi.org/10.1016/j.tifs.2017.06.017.
Viollaz, J., Graham, J., & Lantsman, L. (2018). Using script analysis to understand the financial crimes involved in wildlife trafficking. Crime Law and Social Change: An Interdisciplinary Journal, 69(5), 595. https://doi.org/10.1007/s10611-017-9725-z.
Viollaz, J., Long, B., Trung, C. T., Kempinski, J., Rawson, B. M., Quang, H. X., Hiền, N. N., Liên, N. T. B., Dũng, C. T., Huyền, H. T., McWhirter, R., Dung, N. T. T., & Gore, M. L. (2021). Using crime script analysis to understand wildlife poaching in Vietnam. Ambio, 50(7), 1378–1393. https://doi.org/10.1007/s13280-020-01498-3.
Wagner, S. (2015). When tuna still isn’t always tuna: Federal food safety regulatory regime continues to inadequately address seafood fraud. Ocean and Coastal Law Journal, 20(1), 111–140.
Warren, D. E., Peytcheva, M., & Gaspar, J. P. (2015). When ethical tones at the top conflict: Adapting priority rules to reconcile conflicting tones. Business Ethics Quarterly, 25(4), 559–582. https://doi.org/10.1017/beq.2015.40.
Washington College of Law International Human Rights Law Clinic and Centro de los Derechos del Migrante (2013). Picked apart: The hidden struggles of migrant worker women in the Maryland crab industry https://fairlaborrecruitment.files.wordpress.com/2013/01/pickedapart-1.pdf.
Wells, D., & Gibson, H. (2017). OSINT from a UK perspective: considerations from the law enforcement and military domains. Proceedings Estonian Academy of Security Sciences, 16: From Research to Security Union. Estonian Academy of Security Sciences, 84–113.
Welsh, B., & Farrington, D. P. (2012). The Oxford handbook of crime prevention. Oxford University Press.
Williams, C., & Carpenter, G. (2015). NEF working paper on sea bass (Dicentrarchus labrax) and article 17 of the reformed Common Fisheries Policy (CFP). New Economics Foundation, 2015.
Zander, K., & Feucht, Y. (2018). Consumers’ willingness to pay for sustainable seafood made in Europe. Journal of International Food & Agribusiness Marketing, 30(3), 251–275. https://doi.org/10.1080/08974438.2017.1413611.
Zellweger, T. M., Nason, R. S., Nordqvist, M., & Brush, C. G. (2013). Why do family firms strive for nonfinancial goals? An organizational identity perspective. Entrepreneurship Theory and Practice, 37(2), 229–248. https://doi.org/10.1111/j.1540-6520.2011.00466.x.
Acknowledgements
This work is supported by the Department for the Economy NI (DfE) as part of a PhD studentship for the first author.
Author information
Authors and Affiliations
Contributions
All authors contributed to the study conception and design. Material preparation, data collection and analysis were performed by Sophie Lawrence. The first draft of the manuscript was written by Sophie Lawrence and all authors commented on previous versions of the manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
Wim Huisman is Editor-in-Chief for Crime Law and Social Change. The other authors have no relevant financial or non-financial interests to disclose.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Lawrence, S., van Ruth, S., Elliott, C. et al. Characteristics and situational aspects of seafood fraud: a comparative crime script analysis. Crime Law Soc Change (2024). https://doi.org/10.1007/s10611-024-10149-7
Accepted:
Published:
DOI: https://doi.org/10.1007/s10611-024-10149-7