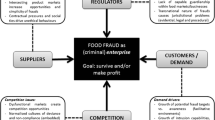
Abstract
Major food fraud scandals of the last decade have created awareness of the need to strengthen companies’ ability to combat fraud within their own organizations and across their supply chains. The scandals compelled food companies and the food industry as a whole to take action and to protect companies and industries against the threat of food fraud. Stakeholders expect food companies to act proactively to mitigate food fraud risks. Certification schemes expect food producers to consider food fraud and to undertake food fraud vulnerability assessments and prepare control plans to mitigate fraud risks. This paper examines how vulnerability for food fraud on company level and supply chain level can be assessed using criminological theory. First, the paper discusses how such theory can be applied for assessing motivations and opportunities for internal and external actors to commit food fraud and assessing existing control measures to mitigate these vulnerabilities. Second, the paper discusses the SSAFE-tool in which these elements have been used in a survey for assessing food fraud vulnerability of companies in food supply chains. Third, the paper evaluates the results of the application of the SSAFE-tool to several food supply chain and tiers, including milk, spices, extra olive oil, organic foods and the food service industry.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Major food fraud scandals of the last decade have created awareness of the need to strengthen companies’ ability to combat fraud within their own organizations and across their supply chains. The scandals compelled food companies and the food industry as a whole to take action and to protect companies and industries against the threat of food fraud, besides bringing challenges to food safety regulators and law enforcement agencies to detect and deter food fraud (Gussow, 2020). All stakeholders expect food companies to act proactively to mitigate food fraud risks. However, the professional field of food safety and quality management was not geared for crime prevention. Food safety management systems are not specifically designed for fraud detection or mitigation. Current risk/hazard assessments focus primarily on unintentional and accidental food quality malpractices and food defense issues. However, few consider intentional food quality issues.
A recurring idea in the calls for the mitigation of food fraud, was to ‘Think like a criminal’.Footnote 1 The UK’s Food Standards Agency called for nationwide testing of beef products for horse DNA, but experts in the food industry viewed this as an outdated way of thinking about food adulteration. ‘We tested for horse DNA but what if next time it was turkey? You need to think like a criminal’.Footnote 2 ‘Think like a criminal to prevent food fraud’ was a take away message at the global food safety conference after the Horsemeat and Melamine scandals.Footnote 3
Thinking like a criminal suggests a criminological perspective, as criminology offers insights into offender motivations and their perceptions of criminogenic opportunities. Criminology is the academic discipline that is studying criminal behavior and criminal decision-making – including fraud. And it is the basis of crime prevention theory (Welsh & Farrington, 2012). Crime prevention has been included before in corporate compliance management systems, such as anti-money laundering procedures in the financial industry. Food fraud prevention is, however, rather new to the world of food safety and quality management (Spink, 2019).
Therefore, in the aftermath of the horsemeat scandal, the Global Food Safety Initiative (GFSI) added new requirements in its standards for which certification schemes need to consider food fraud in addition to food safety and food defense. Food companies were expected to undertake food fraud vulnerability assessments and prepare control plans to mitigate fraud risks (GFSI, 2018). A food fraud vulnerability assessment can identify areas in the food chain where vulnerabilities might exist. It can also determine the key drivers and enablers of the vulnerability in supply chains (Soon et al., 2019; Spink et al., 2016). Food fraud vulnerability assessments tools differ from conventional purely food safety hazard analysis or risk assessment tools as food fraud vulnerability assessments also requires consideration of a number of socio-economic factors (Manning & Soon, 2019). Several tools have been developed, including the Vulnerability Assessment and Critical Control Points, the NSF Fraud Protection Model, the Food Fraud Mitigation Guidance Document, the Food Fraud Initial Screening Model, the CARVER + Shock tool and the SSAFE Food Fraud Vulnerability Assessment tool (Spink et al., 2016). These tools can help companies to conduct a food fraud vulnerability assessment, while the results can also inform about the vulnerability to food fraud of food supply chains and types of companies in those chains. All available tools have strengths and weaknesses. The tools differ in scope and depth, usage capability (online/offline, payable/for free), and in flexibility and applicability to different products, business sizes and regions (Manning & Soon, 2019).
Although food fraud vulnerability assessments have now been globally implemented in the food industry, criminological insights in the various aspects of the assessments would substantiate its use. Therefore, the current paper tries to answer the following research question: how can vulnerability for food fraud on company level and supply chain level be assessed and what criminogenic motivations, opportunities and (lack of) control measures does such assessment show? To answer this question, this paper focuses on the SSAFE-tool (SSAFE, 2016). For the SSAFE-tool, the authors of this paper prepared a science-based survey for self-assessment of a company’s food fraud vulnerability profile to provide a basis to develop company-specific intervention strategies. The survey-questions on food fraud vulnerability sectors were based state-of-the-art research in criminology, food authenticity and food quality management. The assessment consists of 50 survey-questions and associated three level answering grids (low-medium-high vulnerability). Each question relates to the previously identified fraud factors: 9 for opportunities, 20 for motivations, and 21 for control measures. The assessment was developed and tested through an extensive, interactive and iterative process with representatives from the global food industry, retail, authorities and scientific community (van Ruth et al., 2017).
Food fraud assessment tools are primarily designed as a management tool for individual companies. However, this paper will illustrate how a food fraud vulnerability assessment tool can be based on criminological theory and research, while it also shows that such a tool can be used on aggregated level to study food fraud vulnerability of food supply chains and commodities. The following section will first explore how criminological theory and research, besides food science, can be used to assess food fraud vulnerability. Secondly, the SSAFE-tool tool for which criminological theory has been used for such purpose will be introduced. Thirdly, the results of the application of the SSAFE-tool to several food supply chain and tiers will be presented. Finally, the contribution of food fraud vulnerability assessments for understanding the causation of food fraud will be discussed.
Criminological theory and food fraud vulnerability
Many criminological theories have been develop to explain crime and criminal behavior. Taken together, these theories focus on three types of explanatory factors: motivations, opportunities and controls. In other words, offenders need to be willing to commit their crimes and they need to be able to do so, having the opportunity and not being restrained by external actors or factors. Some theories have tried to integrate these explanatory factors, such as the influential Routine Activities Theory, which presents crime as the outcome of the convergence of motivated offenders suitable target and absence of guardianship in time and place (Felson & Cohen, 1980). While this theory takes the presence of motivated offenders as given and focuses on understanding opportunity and control, criminological research on particular types of crime often focuses on particular offender profiles and motivations for these particular types of crime.
In criminology, fraud is generally seen as a form of white-collar crime, as it is committed in the context of a legitimate occupation or business context (Benson & Simpson, 2018). However, some cases of serious forms of fraud – such as VAT frauds – are presented as forms of organized crime, as the criminal collaboration is purely aimed at illegal gain. While this upperworld-underworld divide is contested, the question to perceive food fraud as either being white-collar crime or organized crime is relevant for understanding underlying causes and risk factors.
In early reports on current cases, food fraud was presented as organized crime, compared to other types of organized crime such as human trafficking and drug trafficking (Elliot, 2014). Also, law enforcement agencies such as Europol have expressed their concerns about the influence of organized crime groups in certain food supply chains.Footnote 4 From a criminological opportunity perspective, Lord et al. (2017), however, concluded that food fraud is likely to be an endogenous problem within the food industry, rather than an exogenous problem of organized crime. They allege that criminal opportunities arise under conducive conditions as part of legitimate actors’ routine behaviors in food supply chains. Also, in handbooks on white-collar crime, food fraud is presented as a form of corporate crime (Croall, 2001; Friedrichs, 2009). Corporate crime refers to crimes committed either by a corporation (i.e., a business entity having a separate legal personality from the natural persons that manage its activities), or by individuals acting on behalf of a corporation or other business entity (Benson & Simpson, 2018). Prior research indicates with regard to food fraud that, as with many white-collar crime offenders, the offender could be a legitimate entrepreneur, either working for a corporation or owning a company in a food supply chain (Cheng, 2012; Manning et al., 2016; Spink & Moyer, 2011).
What both white-collar crime and organized crime have in common, is economic gain as a main motivation. And while there are competing definitions of food fraud, they agree that it is an economically motivated crime. Although the argument of Lord et al. (2017) that legitimate occupational positions, organizational settings and business practices create criminal opportunities and provide ‘ready-made’ markets and networks through which to conceal illicit behaviors and for which insiders are best positioned is convincing, this does not exclude the potential empirical reality that organized criminal are drawn to the lure to exploit such opportunities (Kleemans & Van de Bunt, 2008). Apart from this, control measures such as tracking and tracing ingredients and produce through the supply chain – from farm to fork – will prevent illicit food stuff entering the chain as well as being produced in the chain. In a Dutch sample of criminal cases of food fraud, Gussow (2020) found that while the offenders did not appear to be traditional organized crime, and most offenders were regular companies in food supply chains, some offenders were outsiders to the food industry.
Notwithstanding similarities, framing food fraud as either an endogenous problem or an exogenous threat is relevant for vulnerability assessments, as motivations, opportunities and controls of insiders and outsiders may differ. Gussow’s finding illustrate that a vulnerability assessment should include both types of risks. While it is more comforting to expect and arm against external threats, companies also need to acknowledge weaknesses within their own operating procedures and business cultures.
Furthermore, criminogenic incentives may differ for the various tiers in production and distribution chains (Simpson, 2011). Studies of fraud in markets and industries show that structural power rests primarily at the top of the distribution chain. Consequently, pressures and constraints are mainly pushed downward. So the structure of markets and supply chains affect the risk of fraud. Simpson refers to this as ‘criminogenic tiers’: “Each tier is situated in a competitive environment with its own distinct characteristics and pressure […] Different kinds of occupational crime emerge at different levels in response to the motivations and opportunities for crime.”(Simpson, 2011, 493). This would imply that primary producers, food manufacturers, wholesalers and retailers or caterers experience different motivations and opportunities for food fraud and therefore need different kinds of controls.
The above shows that, like all business related crimes, food fraud is the result of a complex interplay of an array of distal (e.g. industry structures, political systems) and proximal (e.g. individual propensities, organizational cultures) factors, that interact to generate motivations and opportunities for fraud (Huisman, 2016). The challenge for a food fraud vulnerability assessment tool, like any model for the empirical analysis of crime, is to bring this complex of interacting factors down to a limited set of tangible indicators of motivations and opportunities for food fraud. Using the Routine Activities Theory formula, the application of criminology to food fraud vulnerability assessments could be conducted by looking for motivations, opportunities and controls by actors within food supply chains. These three elements affecting criminal behavior and their aggregation have been the topic of extensive study and theory testing in criminology in general and in white-collar crime and organized crime research in particular. We will now elaborate these elements for food fraud.
Motivations for food fraud
Fraud can be committed by individual offenders (working in a company or operating in organized networks) as well as by corporate offenders (companies operating in the chain). Fraud offenders can be both actors in the chain as well as external actors trying to infiltrate or to manipulate this chain. Economic motivation assumes the pursuit of individual material success or some kind of business advancement. Depending on both the offender and the situation, this economic motivation can take different forms: profit maximization or loss minimization. In other words greed versus need: the drive for more material gain versus law breaking being perceived as unavoidable for economic survival. Both have been found to be strong drivers for business related crimes (Shover & Hochstetler, 2006. Furthermore, additional factors such as organizational strategy, business culture, level of competition, relationships with supplier(s), etc. can drive motivations to commit food fraud (Huisman, 2016).
Opportunities for food fraud
Suitable targets provide opportunities. In mainstream criminology, such targets are homes to burgle and victims to attack. In the case of food fraud, suitable targets can be food ingredients and products, which are – by the nature of their composition, qualities, geographical or production origin – attractive for adulteration, mislabeling or counterfeiting. Typical opportunity features of white-collar crime are the superficial appearance of legitimacy of the business activities, the legitimate access of the offender to the target or crime location and the distance between offender and victim in time and place (Simpson and Benson, 2018). These all apply to food fraud: the purpose of adulteration, mislabeling or counterfeiting is to mimic the genuine product, it is committed in the context of regular food production and potential harms to consumers will present themselves later and will be difficult to trace back to the adulteration. Food products and food production procedures can differ strongly in vulnerability to adulteration (Evershed & Temple, 2016).
Control measures for food fraud prevention
Chain actors can implement control measures in their systems to detect or prevent fraud and intervene in case of deviations. In criminology, informal guardians are distinguished from formal guardians, while exercising guardianship (control) is the formal and professional duty of the latter (Reynald, 2018). From a company perspective, formal internal guardians can be food quality and safety officers, while the national Food Safety Authority exercises formal external guardianship. Informal guardians can be employees, suppliers, customers and other stakeholders, while suppliers and customers ca also act as formal guardians when conducting mandatory tests.. The most appropriate system to exercise guardianship is the food safety management system, which should include measures to mitigate the risk on fraud such as detection systems, and/or preventive measures, in the form of both hard and soft controls (Spink, 2019).
Towards a food fraud vulnerability assessment tool
The criminological framework laid out above has been suggested as starting point for the concept of food fraud vulnerability assessments (Spink, 2019; van Ruth et al., 2017). The three elements are the main factors determining a company’s vulnerability to food fraud. The elements are producing risks in the following manner: Opportunities and motivations are created by the company’s internal and external environment and are here defined as the potential fraud risk factors. The potential risk resulting from these two elements can be mitigated by the third element: the control measures due to the company’s food safety management system and/or external controls in the chain/industry network and/or legal frameworks.
Companies operating in a high fraud risk environment (e.g. due to opportunities, drivers or motives inherent to the environment) will require advanced and specific fraud monitoring systems and preventive measures to limit their vulnerability to food fraud. Contingency measures may be required in addition to mitigation measures to limit damage in case fraud issues occur in the company or in its environment. Food fraud vulnerability factors inherent to the internal and or external environment may change over time and are dynamic. Therefore, food fraud vulnerability assessment requires both regular usage and updating.
The three elements are at the core of the SSAFE food fraud vulnerability assessment tool that was designed to assist food companies with the evaluation of their vulnerability to food fraud. The assessment diagnoses the company’s potential vulnerability to food fraud and provides a profile of the vulnerabilities resulting from the opportunity- and motivations-related fraud risk factors, and existing control and contingency measures. It can serve as input for further in-depth analysis and/or the development of company specific interventions to enhance mitigation of fraud vulnerability. If high vulnerabilities are identified, additional and existing instruments may be employed for a more detailed and in-depth analysis these particular vulnerabilities. For instance, when the ethical business culture is perceived as low, and therefore crate a vulnerability to unethical behavior, the Ethical Virtues Model for diagnosing the ethical business culture may be applied (Kaptein, 2008).
It is recommended that companies that use the SSAFE tool integrate it into their food safety management system, as various food safety management system certification schemes prescribe. The criminological framework provides the managerial challenge of being receptive to external threats as well as to the dark side of one’s own organization. The tool provides an overall evaluation of a company’s food fraud vulnerability. The tool is not designed to detect fraud nor predict future food fraud incidents.
The core of the tool is a questionnaire of fifty questions for food fraud vulnerability self-assessment, and it is structured in two dimensions. The first dimension involves the elements affecting criminal behavior, i.e. motivations, opportunities, and control measures. These elements are sub-divided into economic drivers, cultural and behavioral drivers, technical opportunities, opportunities in time and place within the supply chain, technical control measures (hard controls) and managerial control measures (soft controls) (van Ruth et al., 2017). The second dimension concerns the level at which these vulnerability indicators are located: the company and the layers of its external environment, i.e. its direct suppliers/customers, the chain/industry network, and the (inter)national governance environment. Along this dimension of environmental layers, the span of control of the company to manage motivations, opportunities and controls decreases. Similarly the company’s ability to obtain reliable data on the three motivations, opportunities and controls decreases along the axis.
The motivations section comprises twenty indicators for organizational aspects, business culture, historical offences, and economic conditions of the company, that can perform as drivers creating motivations for fraud. These indicators are assessed related to the company itself, to the direct suppliers/customers, to the wider chain/industry network, and at the (inter)national level. The opportunities section includes eleven indicators related to product and process characteristics, features of the chain/industry network, and historical evidence of fraud with particular food products and ingredients. The control measures section consists of nineteen indicators for mitigation and contingency control measures. A sub-division is provided for the environmental layers, i.e. for the internal hard controls, internal soft controls, and external controls at the level of the direct suppliers/customers and the wider environment.
For each opportunity and motivations indicator, three descriptions are provided which reflect three vulnerability levels (low, moderate, high). These operationalizations were based on available research and theory on these items (see for details, SSAFE, 2016). Similarly for each control indicator, three descriptions are provided, reflecting the level of control (from simple to advanced and tailored for fraud). The description that reflects the company situation needs to be selected for each indicator. The answers to the questions, selected by the businesses, are transformed to a score system. For opportunities and motivations, a score of 3, 2, and 1 is assigned to high, medium, and low vulnerability situations, respectively. For control measures the reversed order is used.
The SSAFE-tool was transformed into a user-friendly and freely downloadable app by PwC.Footnote 5 From its launch in 2016 until the end of 2019, the tool was downloaded 75.000 times from the SSAFE website. According to Manning and Soon, key strengths of the SSAFE tool are its flexibility and applicability, its versatility and accessibility, and its inclusion of intrinsic and extrinsic risk factors (Manning & Soon, 2019).
Like other FFVA-tools, the SSAFE tool was initially designed as a management tool for individual companies. However, as anonymized results were registered, the usage of the SSAFE tool allows for aggregated level analysis van Ruth and Nillesen (2021) analyzed self-assessments using the SSAFE tool of 8021 companies, active in 20 industry segments and located in five continents. Their results show that a company’s industry segment (chain and tier) affects its perceived fraud vulnerability greatly and to a larger extent than the size of the business. The effect of industry segment on fraud vulnerability appears fairly similar across continents, whereas the effect of business size exhibits large geographical variation. The results demonstrate that those involved in animal product supply chains and end of chain nodes (catering & retail) feel most vulnerable, and so are larger businesses, and businesses located in Africa and Asia (van Ruth & Nillesen, 2021).
Also unlike other tools, the SSAFE-tool has been used in a number of academic studies assessing fraud vulnerability in various food supply chains and food business tiers. While the development of fraud vulnerability assessment tools as such and the extent of their usage have been academically critiqued (Manning & Soon, 2019), the outcomes of using these tools were not yet published. So far, there is hardly any research comparing food fraud vulnerability of different supply chains and food business tiers using the same methodology. In the next section the results of studies using the SSAFE tool will be discussed.
Assessing fraud vulnerability in food supply chains
Some commodities seem to be more associated with food fraud than others. An inventory of reports in the existing three global food fraud databasesFootnote 6 over the period 2008 to 2013 revealed that the six most frequently reported commodity groups were spices and herbs, olive oil, seafood, dairy products, meat, and other oils and fats (Weesepoel & van Ruth, 2015). In a series of research projects, the SSAFE food fraud vulnerability assessment tool was used to assess fraud vulnerabilities in the following food supply chains: milk (Yang et al., 2019; Yang et al., 2020), olive oil (Yan et al., 2020a; 2020b), and spices (Silvis et al., 2017). Also using the SSAFE tool, businesses in supply chains of six commodities were assessed and compared for their fraud vulnerabilities: fish, meat, milk, olive oil, organic bananas, and spice supply chains. Furthermore, this study examined differences and similarities between commodity supply chains, as well as between groups factors (tiers) across chains (e.g. processors, wholesalers and retailers) (van Ruth et al., 2018). Besides the ‘vertical’ approach of studying particular food supply chains, also a ‘horizontal’ approach was used of studying actors in the upper tiers across food supply chains: the food service industry consisting of restaurants and catering (besides retailers such as supermarkets and shops) (van Ruth et al., 2020). Finally, the tool has been used to assess perceived fraud vulnerability of various organic foods.
In all these research projects, the questionnaire of the SSAFE tool was used. To fit the scope of the research, some of the questions were left out. For instance, questions on counterfeiting were not used when they did not apply to the commodity chains examined, such as milk. For exploratory analysis, multiple correspondence analysis (MCA) and agglomerative hierarchical clustering (AHC) was applied. Throughout these studies, a significance level of p < 0.05 was applied. Opportunities and motivations related fraud factors were considered prime drivers and enhancers if their scores exceeded the average for either the opportunities or motivations group.
Milk
Yang et al. (2019) studied the perception of fraud vulnerability of the general milk supply chain in the Netherlands and its tiers (farmers, processors, retailers), as well as the differences in perceived fraud vulnerability of farmers producing organic milk, green intermediate ‘pasture milk’ and conventional milk. They surveyed 38 companies in the three tiers included in the study: 30 farmers, 4 milk processors and 4 retailers. MCA was used to investigate the association between groups. The three tier groups showed major similarities in motivation related fraud factors, and large differences in fraud opportunities and controls. The processors and retailers perceive a higher vulnerability to milk fraud than the farmers. Yet, farmers believed that the technical opportunities for adulteration contributed considerably to fraud vulnerability. There were also differences observed between the organic and non-organic farmers, with organic farmers reporting slightly more vulnerability than their non-organic counterparts. From this study it appears that perception of vulnerability to fraud in the milk supply chain in the Netherlands is low to medium, but the key factors contributing to the perceived vulnerability differ between the tiers.
Yang et al. also studied food fraud vulnerability in milk supply chain in China (Yang et al., 2020). In this study, 90 Chinese dairy farmers and 14 milk processors were surveyed with the SSAFE tool. MCA was applied for exploratory analysis, and non-parametric Kruskal-Wallis tests were applied for the group comparisons and Mann-Whitney U-tests for pairwise comparisons. Overall, actors perceived the milk supply chain as low to medium vulnerable to food fraud. Farmers reported significantly more vulnerablility than processors due to enhanced opportunities and motivations, and less adequate controls. Both geographical location of the farms and their size affected their perceived fraud vulnerability significantly. Compared to the situation of the milk chain in the Netherlands, the overall perceived fraud vulnerability seems fairly similar in China. There are differences between the perspectives of the tier groups in the two countries. The processors consider themselves more vulnerable in the Netherlands, while in China farmers perceive to be most vulnerable to milk fraud.
Extra virgin olive oil
As a high value commodity on the market, extra virgin olive oil is a suitable target for food fraud. To understand differences in perceived fraud vulnerability between tier groups across the extra virgin olive oil supply chain and to disclose underlying factors, Yan examined the perceived fraud vulnerability of 28 companies using the SSAFE tool (Yan, 2020; Yan et al. 2020). Amongst these companies were seven olive oil producers, seven business-to-business companies, seven food manufacturers and seven retailers. Producers were located in Spain, Portugal, Greece and France; the other companies were located in the Mediterranean as well or in the Netherlands. The similarities and differences in perceived fraud vulnerabilities according to group characteristics (the role, the scale and the location of the company) were evaluated. Non-parametric Kruskal-Wallis tests were applied for group comparisons due to the ordinal data in this study. The pairwise comparisons were carried out using the Mann-Whitney U tests. The score data were subjected to MCA to investigate the association between groups.
Eight fraud factors related to opportunities and motivations scored high in the supply chain indicating their importance as potential fraud drivers and enablers. These were five technical opportunity factors: three relating the complexity, the availability of technology and knowledge and the detectability of adulterating raw materials and two relating the availability of technology and knowledge and the detectability of adulterating final products. Motivational factors were all economic drivers: the supply and pricing of raw materials, the presence of valuable components or attributes in raw materials and the level of competition in the branch of industry. Four factors related to control measures are perceived as creating high vulnerability for fraud with extra virgin olive oil: the lack of a whistle blowing scheme within the company, the lack of a fraud control system of suppliers and the industry as a whole and the lack of law enforcement in the supply chain.
The vulnerability to fraud in the extra virgin olive oil supply chain across all actors is perceived as high level on average. In decreasing contribution to the overall perceived fraud vulnerability, the fraud factor categories were ranked as follows: technical opportunities, a lack of managerial controls, a lack of technical controls, economic drivers, cultural and behavioural drivers and opportunities in time and place. Among the tier groups, the retailers and business-to-business companies experienced higher levels of perceived vulnerability than olive oil producers and food manufacturers due to the additional vulnerability related to the opportunities in time and place and greatest lack of control measures. Furthermore, the perceived fraud vulnerability of the company was not only determined by the tier group, but also impacted by the scale and location of the company.
Spices
Spices rank high among food stuffs most susceptible to food fraud (Weesepoel & van Ruth, 2015). Silvis et al. (2017) examined the perceived fraud vulnerabilities of various actors in the spices supply chain, using the SSAFE tool. Eight companies participated in the study: a trader, two importers, two business to business companies and three business-to- business/business-to-consumer companies. Based on frequency analysis of the scores on the 50 items, Silvis et al. concluded that the various actors perceived the general level of food fraud vulnerability in the spices chain as medium vulnerable. The ease to adulterate spices combined with the complexity of fraud detection create considerable opportunities to commit fraud, resulting in high vulnerability, whereas opportunities associated with supply chain transparency and fraudulent incidences in the past were judged as medium vulnerable. The high competition level in the sector together with the high added value of spices are perceived as important economic motivations to commit fraud, also creating high vulnerability. Ethical business culture was considered to contribute to the actual fraud vulnerability to a lesser extent. The implementation of both the hard and soft control measures varied widely among the actors. Fraud specific measures are merely lacking or are at a very basic level. For soft control measures of the own company, the scores were higher.
Comparing six supply chains
Besides individual commodities and their supply chains, companies in supply chains of six commodities were assessed and compared for their fraud vulnerabilities (van Ruth et al., 2018). The companies included wholesalers and processors. Wholesale included traders, importers, distributors, and auctions, i.e. all organizations that did not process the products but just passed them on in the chain. Processors included companies processing the primary product, such as olive oil, but also complex food manufacturers. In this study, primary producers, such as farmers or fishermen were not involved. To investigate the specific differences between the supply chains and the subsequent tiers (retails, wholesale, processor), a multi-factor analysis of variance (ANOVA; chain x actor) was carried out with subsequent post-hoc tests (Fisher’s Least Significant difference tests: Fisher’s LSD test).
The study identified 13 prime opportunities and motivations which seem to contribute highly to the perceived fraud vulnerability of the assessed chain actors. The control measures vary a lot across supply chains and tiers. Often technical control measures are to some extent in place, but managerial (soft) controls which counteract motivations-related fraud factors are less extensively present. Managerial controls at the wider environment level, i.e. social control and food policy and enforcement, are perceived as lacking or insufficient in many cases. Perceived fraud vulnerability was shown to be determined by both the commodity chain and the position of the actor in that chain: half of the fraud factors were significantly impacted by the type of commodity chain and one out of seven of the fraud factors by the tier.
The study further demonstrated that the spices chain ranked highest in perceived fraud vulnerability; subsequently followed by olive oil, meat, fish, milk and organic banana. The wholesalers group is considered as most vulnerable among the tiers, they were followed by the retailers, and processors.
Organic food
Besides the supply chain of a particular commodity or the tier within supply chains, another focus for assessing food fraud vulnerability is looking at food products containing certain qualities, as a result of the way they are produced and that may therefore carry a certain label. Such as organic and halal foods. Organic foods are frequently targeted by fraudsters (Ferreira et al., 2021; Manning & Kowalska, 2021). van Ruth and Pagter-de Witte (2020) examined the fraud vulnerability of five actors from each of four chains with the SSAFE tool: the organic banana, egg, olive oil and pork supply chains. Significant differences between the scores of actors in the four commodity supply chains were assessed by analysis of variance (ANOVA). To explore patterns in these frequency data, principal component analysis (PCA) was carried out on the frequency data. To assess correlations between ethical business culture vulnerability levels and criminal offences, Spearman’s rank correlation tests were performed on all related scores and Spearman’s rho (rs) was calculated. Agglomerative hierarchical cluster (AHC) analysis was applied to examine similarities in scores patterns of individual actors.
Contrary to Yang et al.’s finding regarding organic milk presented above, the organic chains perceived fraud vulnerability appeared slightly less than conventional chains due to fewer observed opportunities for fraud and the more adequate controls being present. On the other hand, organic chains were associated with enhanced vulnerability resulting from cultural and behavioral drivers. Across chains, but most prevalent in the pork industry, there was a group that scored high on previous offending and on perceiving an unethical business culture with the company, with suppliers and in the wider industry. This may refer to a group of cheaters or free riders who aim to profit from the premium of the organic label but who do not share the normative motivations of producing organic food.
Generally, actors in the organic olive oil and pork chains scored higher on perceived vulnerability than those from the banana and egg chains. However, high vulnerability actors were not limited to particular chains. Across the whole group of actors in organic chains, three groups in terms of cultural/behavioral drivers were distinguished: a low vulnerability group, a group facing more external threats and a group presenting fraud vulnerability in general and in particular from within their own company. Ethical business culture and criminal history scores of businesses correlated significantly (rs = 0.376; p = 0.003: van Ruth & Pagter-de Witte, 2020). This implies that the climate in a company is an important factor to consider when estimating the exposure of businesses to food fraud and that not all companies involved in organic food are driven by environmental benefits.
The food service industry
Instead of looking ‘vertical’ up or down specific food supply chains and their subsequent tiers, van Ruth et al. (2020) looked ‘horizontally’ at three upper tiers of four product groups. They examined and compared between 15 casual dining restaurants, fine dining restaurants and mass caterers for four product groups. These companies at the end of the chain can be victims of food fraud committed down a supply chain. However, they can be offenders as well, when they for instance sell horse steak as beef steak or serve pollack as cod. Perceived vulnerability was assessed by an adapted version of the SSAFE tool, tailored to the food service sector situation. Significance of differences in scores and frequencies between groups were assessed by multi-factor analysis of variance (MANOVA), with post-hoc Fisher’s Least Significant Difference tests. Although the scores are ordinal data, MANOVA was applied to get insights into the influence of the two individual factors as well as their interactions. It allowed also a direct comparison with previous data from other nodes in the chain (van Ruth et al., 2018).
The 15 food service operators rated high vulnerability for 40% of the fraud indicators. This is considerably more than food manufacturers, wholesalers and retailers did in the studies discussed above. In particular, more opportunities and fewer controls were noted. Overall fraud vulnerability perception was more determined by the type of food service operator than by the type of food product. Casual dining restaurants felt most vulnerable, followed by fine dining restaurants. Mass caterers seemed the least vulnerable operators, because they had more adequate food fraud controls in place. Considering its high vulnerability, authors recommended urgent reinforcement of mitigation measures in the food service industry.
Conclusion and discussion
Recent food fraud scandals have not only raised concern with food safety regulators and consumers, but first and foremost with companies in the food supply chains. Companies are called upon to assess their vulnerability to food fraud, both as victim of external or internal actors and as potential perpetrator. Using criminological theory and results from criminological research on white-collar crime and organized crime, the SSAFE tool has been developed for the assessment of the vulnerability of individual companies and food supply chains for food fraud. This tool has extensively been used by companies but – partly adjusted to fit the research scope – by food scientists as well in an effort to examine and compare food fraud vulnerability in food supply chain and between tiers within those chains. These studies show that the survey-tool is able to find differences and that the different risk scores for motivation, opportunities and controls make sense. Multivariate data analysis allows for finding groups of companies with similar risk profiles and similar characteristics, pointing at underlying potential causal factors. A supply chain is usually determined by the type of product, and products exhibit traits that can be manipulated for illicit gain according to their supply chain actors. Nevertheless, the tool is also able to differentiate between geographical location, conventional and organic produce, and the tiers within supply chains.
The studies using the tool confirmed the need to include endogenous and exogenous risks factors in the vulnerability assessment. Across chains particular groups had high scores for victimization and reported offending by both suppliers and customers. Such groups seem particularly vulnerable to becoming a victim of external fraud according to these factors. However, also across chains groups of companies score high on having a history of offending and reporting an unethical business culture. Moreover, it appears that actors see fairly consistent technical opportunities and economic drivers to adulterate their product across chains, pointing at endogenous risks. Ethical business culture, the climate within a company, appears to be a very important factor of food fraud vulnerability and requires sufficient attention in fraud mitigation plans.
As food fraud vulnerability assessments tools measure perceived food fraud vulnerabilities by food businesses, conclusions about actual prevalence and underlying causal factors cannot be deducted from the outcomes of their use. However, looking at the result of the studies using the SSAFE tool, the perceptions of these vulnerabilities seem partly consistent across food supply chains and continents. This finding indicates that individual perceptions of vulnerability to food fraud may be susceptive to particular organizational environments where opportunities are generated in relation to social-structural patterns of business activity. Also, the aggregate findings may point at wider structural driver effects shaping perceived opportunities and motivations for food fraud. The outcomes may be related to studies looking at criminogenic structures within certain industries (Bradshaw, 2014) or food fraud being part of a broader palette of inflated rates of economic crimes in particular regions and settings (Alibux, 2016).
In conclusion, food fraud vulnerability assessment tools, such as the SSAFE tool can provide a better understanding of how companies in food supply chains perceive vulnerability to fraud and in turn insight into how these perceptions vary across sectors, products and geographies. In return, the applications of the tool offer rich data that offers potential for further analysis. And as such, the tool offers a novel example of the integration of social science, natural science and practice, and also demonstrates the potential for the development of new databases on perceptions of fraud vulnerabilities within food systems. For understanding the prevalence and causation of food fraud, food fraud vulnerability assessments provide only a piece of the complex puzzle of crime.
Limitations
Notwithstanding these benefits, the SSAFE tool – and potentially similar tools for food fraud vulnerability assessment – has limitations. A first limitation is the broad scope and required usability of the tool. The survey includes 50 questions covering a wide array of topics, concerning both company characteristics and the business environment, which leads to quite rough measurements of some of the key elements. For instance the Ethical Virtues Model served as inspiration for assessing the ethical business culture (Kaptein, 2008). However, the Corporate Ethical Virtues scale and measures eight corporate virtues, using 58 survey-items. In the SSAFE-tool this was brought down to tool brought down to one question. A much more refined and valid way to assess ethical business culture is of course using the full scale (Kangas et al., 2014).
Further, the company’s home country ranking on the TI corruption perception index was used as a proxy for the prevalence of financial and economic crime – including fraud – in that country. As for the lack of – equal – measurements of financial and economic crime in most countries, this may the best there is, but is not optimal.
Also, there may be a bias in the sample of businesses likely to complete the survey. Those that are otherwise compliant, and those that have therefore the information needed to answer the survey questions in order, may be over-represented to those businesses that have difficulties in meeting regulatory requirements or that occasionally find themselves on a slippery slope towards fraud. Businesses where there is a predetermined and pre-planned approach to systematic frauds, may decline from participating in the survey. As such, the tool suffers from the same limitation as self-reporting surveys used in criminology for measuring the prevalence of crimes that are hard to measure using crime statistics and victim surveys. However, the SSAFE does not measure prevalence of food fraud, but it assesses perceived vulnerabilities.
More generally, the reliability of answers and qualification of risk scores may be dependent on the respondents’ educational level, working experience, knowledge about food fraud, etc. It is unknown whether self-perceptions of vulnerability reflect actual vulnerabilities. Although the SSAFE tool requires a team approach (e.g. security, finance, quality assurance), Manning and Soon point out that a lack of skills and understanding of how to use the tool and variable scopes of assessments may result in inconsistency in vulnerability scoring. They call for more industry level cohesiveness and consistency in how food fraud vulnerability assessments are undertaken to address both intrinsic and extrinsic food fraud vulnerability (Manning & Soon, 2019).
Finally, the tool is not correlated for actual prevalence of food fraud within most of the examined supply chains and companies. An exemption is the study on milk fraud in China, that was able to find a correlation between survey-results and reported fraud prevalence (Yang et al., 2020). Also, the vulnerability profiles of the supply chains assessed with the SSAFE-tool match with previous rankings of food supply chains in food fraud databases (Weesepoel & van Ruth, 2015). Nevertheless, the presumably high dark figure in the detection of food fraud (Gussow, 2020) prevents testing the correlation between high vulnerability and high prevalence of food fraud and assessing the validity and predictive value of current tools for assessing food fraud vulnerability. As such, ‘risky business’ does not only refer to the vulnerability to food fraud, but also to the validity of food fraud vulnerability assessments and mitigation tools.
Notes
See also: Hines, T., & Murphy, L. (2016). Combatting Food Fraud With Intelligent Due Diligence. World Food Regulation Review, 25(8), 20.
http://www.foodnavigator.com/Market- Trends/Think-like-a-criminal-to-beat-food-fraud-says- Danone-expert
USP Food Fraud database, NCFDP EMA Incident database & RASFF database.
References
Alibux, A. N. R. N. (2016). Criminogenic conditions, bribery and the economic crisis in the EU: A macro level analysis. European Journal of Criminology, 13(1), 29–49.
Benson, M. L., & Simpson, S. S. (2018). White-collar crime: An opportunity perspective (3rd ed.). Taylor & Francis.
Bradshaw, E. A. (2014). “Obviously, we’re all oil industry”: The criminogenic structure of the offshore oil industry. Theoretical Criminology, 19(3), 376–395.
Cheng, H. (2012). Cheap capitalism A sociological study of food crime in China. British Journal of Criminology, 52(2), 254–273.
Croall, H. (2001). Understanding white collar crime. McGraw-Hill Education (UK).
Elliot, C. (2014) Elliott review into the integrity and Assurance of Food Supply Networks – Final report. A National Food Crime Prevention Framework, London: HM Government.
Evershed, R., & Temple, N. (2016). Sorting the beef from the bull: The science of food fraud forensics. Bloomsbury Sigma.
Felson, M., & Cohen, L. E. (1980). Human ecology and crime: A routine activity approach. Human Ecology., 8(4), 389–406.
Ferreira, G., J. Tucker, E. Rakola & S.R. Skorbiansky (2021) Fraud in organic foods, in: Hellberg, R.S., K. Everstine & S.A. Sklare, Food Fraud, Academic Press, 335–350.
Friedrichs, D. (2009). Trusted criminals: White collar crime in contemporary society. Cengage Learning.
GFSI (2018) Tackling food fraud through food safety management, https://mygfsi.com/wp-content/uploads/2019/09/Food-Fraud-GFSI-Technical-Document.pdf
Gussow, K. (2020). Finding food fraud: Explaining the detection of food fraud in the Netherlands, dissertation. Vrije Universiteit.
Huisman, W. (2016). Criminogenic organizational properties and dynamics. In S. R. van Slyke, M. L. Benson, & F. T. Cullen (Eds.), The Oxford handbook of white-collar crime (pp. 435–462). Oxford University Press.
Kangas, M., Feldt, T., & Huhtala, M. (2014). The corporate ethical virtues scale: Factorial invariance across organizational samples. Journal of Business Ethics, 124, 161–171.
Kaptein, M. (2008). Developing and testing a measure for the ethical culture of organizations: The corporate ethical virtues model. Journal of Organizational Behavior, 29(7), 923–947.
Kleemans, E. R., & Van de Bunt, H. G. (2008). Organised crime, occupations and opportunity. Global Crime, 9(3), 185–197.
Lord, N., Flores Elizondo, C. J., & Spencer, J. (2017). The dynamics of food fraud: The interactions between criminal opportunity and market (dys)functionality in legitimate business. Criminology & Criminal Justice. https://doi.org/10.1177/1748895816684539
Manning, L., & Kowalska, A. (2021). Considering fraud vulnerability associated with credence-based products such as organic food. Foods, 10(8), 1879. https://doi.org/10.3390/foods10081879
Manning, L., Smith, R., & Soon, J. M. (2016). Developing an organizational typology of criminals in the meat supply chain. Food Policy, 59, 44–54.
Manning, L., & Soon, J. M. (2019). Food fraud vulnerability assessment: Reliable data sources and effective assessment approaches. Trends in Food Science & Technology, 91, 159–168.
Reynald, D.M. (2018) Guardianship, in: Gerben J.N. Bruinsma and Shane D. Johnson, The Oxford Handbook of Environmental Criminology, Oxford: OUP, 716–73.
van Ruth, S. M., Huisman, W., & Luning, P. A. (2017). Food fraud vulnerability and its key factors. Trends in Food Science & Technology, 67, 70–75. https://doi.org/10.1016/j.tifs.2017.06.017
van Ruth, S. M., Luning, P. A., Silvis, I. C. J., Yang, Y., & Huisman, W. (2018). Differences in fraud vulnerability in various food supply chains and their tiers. Food Control, 84(Supplement C), 375–381. https://doi.org/10.1016/j.foodcont.2017.08.020
van Ruth, S. M., van der Veeken, J., Dekker, P., Luning, P. A., & Huisman, W. (2020). Feeding fiction: Fraud vulnerability in the food service industry. Food Research International, 133, 109158. https://doi.org/10.1016/j.foodres.2020.109158
van Ruth, S. M., & de Pagter Witte, L. (2020). Integrity of organic foods and their suppliers: Fraud vulnerability across chains. Foods, 9(188), 1–11.
van Ruth, S. M., & Nillesen, O. (2021). Which company characteristics make a food business at risk for food fraud? Foods, 10, 842. https://doi.org/10.3390/foods10040842
Shover, N. L., & Hochstetler, A. (2006). Choosing white-collar crime. Cambridge, University Press.
Silvis, I. C. J., van Ruth, S. M., van der Fels-Klerx, H. J., & Luning, P. A. (2017). Assessment of food fraud vulnerability in the spices chain: An explorative study. Food Control, 81, 80–87. https://doi.org/10.1016/j.foodcont.2017.05.019
Simpson, S. (2011). Making sense of white collar crime: Theory and research. The Ohio State Journal of Criminal Law, 8, 481–502.
Soon, J. M., Krzyzaniak, C., Shuttlewood, Z., Smith, M., & Jack, L. (2019). Food fraud vulnerability assessment tools used in food industry. Food Control, 10(2019), 225–232.
Spink, J., & Moyer, D. C. (2011). Defining the public health threat of food fraud. Journal of Food Science, 76(9), R157–R163.
Spink, J., Moyer, D. C., & Whelan, P. (2016). The role of the public private partnership in food fraud prevention—Includes implementing the strategy. Current Opinion in Food Science, 10, 68–75. https://doi.org/10.1016/j.cofs.2016.10.002
Spink, J. (2019). Food fraud prevention. Introduction, implementation, and management. Springer.
SSAFE. (2016). Food fraud vulnerability assessment tool. http://www.ssafe-food.org/our-projects/.
Weesepoel, Y., & van Ruth, S. (2015). Inventarisatie van voedselfraude: mondiaal kwetsbare productgroepen en ontwikkeling van analytische methoden in Europees onderzoek. https://edepot.wur.nl/360164.
Welsh, B. C., & Farrington, D. P. (2012). The Oxford handbook of crime prevention. OUP.
Yan, J. (2020). Fraud investigation in the extravirgin olive oil supply chain: Identification of vulnerable points and development of novel fraud detection methods. Dissertation. Wageningen University. https://doi.org/10.18174/516130.
Yan, J., Erasmus, S. W., Aguilera, T. M., Huang, H., & van Ruth, S. M. (2020). Food fraud: Assessing fraud vulnerability in the extra virgin olive oil supply chain. Food Control, 111, 107081.
Yang, Y., Huisman, W., Hettinga, K. A., Zhang, L., & van Ruth, S. M. (2020). The Chinese milk supply chain: A fraud perspective. Food Control, 113, 107211. https://doi.org/10.1016/j.foodcont.2020.107211
Yang, Y., Huisman, W., Hettinga, K. A., Liu, N., Heck, J., Schrijver, G. H., Gaiardonia, L., & van Ruth, S. M. (2019). Fraud vulnerability in the Dutch milk supply chain: Assessments of farmers, processors. Food Control, 95(1), 308–317.
Availability of data and material (data transparency)
N.A.
Code availability (software application or custom code)
N.A.
Author information
Authors and Affiliations
Contributions
Both author provided equal and original contributions.
Corresponding author
Ethics declarations
Conflicts of interest/competing interests (include appropriate disclosures)
No conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Huisman, W., van Ruth, S. Risky business: food fraud vulnerability assessments. Crime Law Soc Change 78, 559–576 (2022). https://doi.org/10.1007/s10611-021-10008-9
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10611-021-10008-9