Abstract
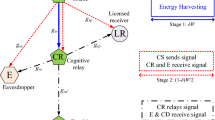
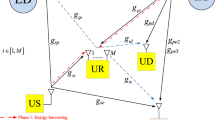
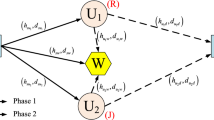
This paper adopts a relay among available secondary relays and exploits non-selected relays as jammers to maintain and secure legitimate secondary source-to-destination communications in energy harvesting underlay cognitive networks (EHUCNs) as their direct communications is in outage. All relays harvest radio frequency energy in signals transmitted by primary and secondary transmitters and consume the harvested energy for their jamming-and-relaying operations. Under Rayleigh fading, peak transmission power restriction, interference power restriction, primary interference and power splitting-based energy scavenging method, we propose exact closed-form formulas of outage and intercept probabilities to promptly assess both security and reliability performances of the suggested relay-and-jammers selection in EHUCNs. The suggested expressions are corroborated by computer simulations. Numerous results indicate the efficacy of the relay-and-jammers selection in improving both security and reliability for source–destination communications. Moreover, the security and reliability performances are saturated at large maximum transmit/interference powers and considerably degraded by the primary interference. Furthermore, the reliability performance can be optimized by splitting appropriately the received power for information decoding and energy harvesting at the relays.






Similar content being viewed by others
Notes
A link is a multi-hop communication link through which the secondary source connects the secondary destination via several secondary relays, each on one hop.
The connection outage probability indicates the probability that the received SNR subceeds a threshold.
The intercept outage probability signifies the probability that the SNR at the eavesdropper subceeds a threshold.
It is obvious that this paper completely differs [24] because the former proposes the relay selection while the latter proposed the link selection.
\(h_{\texttt {mn}}\sim {{\mathcal {CN}}}(0,\mu _{\texttt {mn}})\) denotes a zero-mean \(\mu _{\texttt {mn}}\)–variance complex Gaussian random variable.
\(\text {E}\) can apply other signal combining techniques (e.g., equal gain combining and maximum ratio combining) for better performance but with higher complexity [40].
References
Tian, Z.; et.al.: Matching theory based physical layer secure transmission strategy for cognitive radio networks. IEEE Access, accepted.
Ho-Van, K.: Outage analysis in cooperative cognitive networks with opportunistic relay selection under imperfect channel information, AEU - Inter. J. Elec. Commun. 69(11), 1700–1708 (2015)
Ho-Van, K.; et al.: Exact outage analysis of underlay cooperative cognitive networks over Nakagami-m fading channels. IET Commun. 7(12), 1254–1262 (2013)
Alexandropoulos, G.; et al.: Symbol error probability of DF relay selection over arbitrary Nakagami-m fading channels. J. Eng. 325045, 1–6 (2013)
Bai, W.; et al.: Joint optimization of computation offloading, data compression, energy harvesting, and application scenarios in fog computing. IEEE Access, accepted.
Wang, Y.; et al.: Energy efficient data and energy integrated management strategy for IoT devices based on RF energy harvesting. IEEE IoT J., accepted.
Tang, X.; et al.: Self-sustainable long range backscattering communication using RF energy harvesting. IEEE IoT J., accepted.
Nourredine, O.; et al.: A new stochastic petri nets modeling for dual cluster heads configuration in energy-harvesting WSNs. In: Proceedings of IHSH, pp. 142–147. Algeria (2021)
Ni, L.; et al.: Outage-constrained secrecy energy efficiency optimization for CRNs with non-linear energy harvesting. IEEE Access 7, 175213–175221 (2019)
Lei, H.; et al.: On secure underlay MIMO cognitive radio networks with energy harvesting and transmit antenna selection. IEEE Trans. Green Commun. Netw. 1(2), 192–203 (2017)
Wang, X.; et al.: Energy efficiency optimization for NOMA-based cognitive radio with energy harvesting. IEEE Access 7, 139172–139180 (2019)
Ghosh, S.; et al.: Secrecy capacity in CRN with malicious energy harvester using game theoretic techniques. IEEE Trans. Cogn. Commun. Netw. 3(3), 343–360 (2017)
Zhou, F.; et al.: Resource allocation for secure MISO-NOMA cognitive radios relying on SWIPT. In: Proceedings of IEEE ICC, pp. 1–6. USA (2018)
Tan, R.; et al.: Secrecy performance of cognitive radio sensor networks with an energy-harvesting based eavesdropper and imperfect CSI. In: Proceedings of AsianHOST, pp. 80–85. Hong-Kong (2018)
Ho-Van, K.; et al.: Security performance of underlay cognitive relaying networks with energy harvesting. Wirel. Per. Commun. 110(2), 829–846 (2020)
Shi, H.; et al.: Physical layer security in an untrusted energy harvesting relay network. IEEE Access 7, 24819–24828 (2019)
Bouabdellah, M.; et al.: Cooperative energy harvesting cognitive radio networks with spectrum sharing and security constraints. IEEE Access 7, 173329–173343 (2019)
Pham-Thi-Dan, N.; et al.: Security analysis for cognitive radio network with energy scavenging capable relay over Nakagami-m fading channels. In: Proceedings of IEEE ISEE, pp. 68–72. Vietnam (2019)
Ji, B.; et al.: Secrecy performance analysis of UAV assisted relay transmission for cognitive network with energy harvesting. IEEE Trans. Veh. Technol. 69(7), 7404–7415 (2020)
Maji, P.; et al.: Physical layer security with non-linear energy harvesting relay. In: Proceedings of IEEE ICCCNT, pp. 1–6. India (2019)
Zhao, W.; et al.: Security energy efficiency maximization for two-way relay assisted cognitive radio NOMA network with self-interference harvesting. IEEE Access 7, 74401–74411 (2019)
Banerjee, A.; et al.: On outage secrecy minimisation in an energy harvesting relay assisted cognitive radio networks. IET Commun. 12(18), 2253–2265 (2018)
Maji, P.; et al.: Secrecy outage of a cognitive radio network with selection of energy harvesting relay and imperfect CSI. Wirel. Per. Commun. 100(2), 571–586 (2018)
Hieu, T.D.; et al.: Performance enhancement for harvest-to-transmit cognitive multi-hop networks with best path selection method under presence of eavesdropper. In: Proceedings of IEEE ICACT, pp. 323–328. Korea (2018)
Ho-Van, K.; et al.: Security enhancement for energy harvesting cognitive networks with relay selection. Wirel. Commun. Mobile Comput. 2, 1–13 (2020)
Pham-Thi-Dan, N.; et al.: Energy harvesting cooperative cognitive networks: relay selection for information security. In: Proceedings of IEEE ISEE, pp. 93–96. Vietnam (2019)
Gurjar, D.S.; et al.: Performance of wireless powered cognitive radio sensor networks with nonlinear energy harvester. IEEE Sens. Lett. 3(8), 1–4 (2019)
Bletsas, A.; et al.: A simple Cooperative diversity method based on network path selection. IEEE JSAC 24(3), 659–672 (2006)
Chakraborty, P.; et al.: Secrecy performance of an idle receiver assisted underlay secondary network. IEEE Trans. Veh. Technol. 66(10), 9555–9560 (2017)
Su, R.; et al.: Secure cooperative transmission in cognitive AF relay systems with destination-aided jamming and energy harvesting. In: Proceedings of IEEE PIMRC, pp. 1–5. Turkey (2019)
Wang, D.; et al.: Primary privacy preserving with joint wireless power and information transfer for cognitive radio networks. IEEE Trans. Cog. Commun. Netw. 6(2), 683–693 (2020)
Zou, Y.: Physical-layer security for spectrum sharing systems. IEEE Trans. Wirel. Commun. 16(2), 1319–1329 (2017)
Hu, X.; et al.: Secure transmission via jamming in cognitive radio networks with Possion spatially distributed eavesdroppers. In: Proceedings of IEEE PIMRC, pp. 1–6. Spain (2016)
Li, Z.; et al.: Cooperative jamming for secure communications in MIMO Cooperative Cognitive Radio Networks. In: Proceedings of IEEE ICC, pp. 7609–7614. UK (2015)
Shu, Z.; et al.: On Physical layer security for cognitive radio networks. IEEE Netw. 27(3), 28–33 (2013)
Wu, Y.; et al.: Secure beamforming for cognitive radio networks with artificial noise. In: Proceedings of IEEE WCSP, pp. 1–5. China (2015)
Fang, B.; et al.: Precoding and artificial noise design for cognitive MIMOME wiretap channels. IEEE Trans. Veh. Technol. 65(8), 6753–6758 (2016)
Nguyen, V.D.; et al.: Joint information and jamming beamforming for secrecy rate maximization in cognitive radio networks. IEEE Trans. Info. Forensics Secur. 11(11), 2609–2623 (2016)
Wang, F.; Wirel. Commun. Lett., accepted.
Simon, M.K.; et al.: Digital Communication over Fading Channels, 2nd edn. Wiley, Hoboken (2005)
Gradshteyn, I.S.; et al.: Table of Integrals, 6th edn. Series and ProductsAcademic Press, San Diego (2000)
Ho-Van, K.: Exact outage probability analysis of proactive relay selection in cognitive radio networks with MRC receivers. J. Commun. Netw. 18(3), 288–298 (2016)
Acknowledgements
This research is funded by Vietnam National Foundation for Science and Technology Development (NAFOSTED) under grant number 102.04-2019.318. We would like to thank Ho Chi Minh City University of Technology (HCMUT), VNU-HCM for the support of time and facilities for this study.
Author information
Authors and Affiliations
Corresponding author
Appendix: Asymptotic Results when \(I_t \rightarrow \infty \)
Appendix: Asymptotic Results when \(I_t \rightarrow \infty \)
When primary receivers tolerate any interference level from secondary transmitters, the case of \(I_t \rightarrow \infty \) holds. For instance, secondary transmitters are distant from primary receivers so that interference caused by secondary transmitters upon primary receivers is negligible, and then, the interference power restriction relating to \(I_t\) is relaxed. Another example is that secondary transmitters operate in the non-cognitive mode, and then, the interference power restriction is ignored.
This appendix shows asymptotic results for IP and OP when \(I_t \rightarrow \infty \). In this asymptotic region, \(P_s\) in (23), \(P_{r_b}\) in (24) and \({\bar{P}}_s\) in (25) become \(P_{sm}\), \(P_{r_bm}\) and \(P_{sm}\), respectively. Therefore, (55) is approximated as
where \(I_{22}\) is given by (49).
\(I_1^{\mathrm{asym}}\) is obtained from \(I_{1t}\) in (29) with the substitution of \(P_s\) with \(P_{sm}\), i.e.,
Similarly, \(I_{2111}^{\mathrm{asym}}\) is obtained from (38) with the substitution of \(P_{r_b}\) with \(P_{r_bm}\), i.e.,
In the asymptotic region, (71) is approximated as
where \(O_2^{\mathrm{asym}}\) is computed in the same way as \(I_1^{\mathrm{asym}}\), resulting in
With the substitution of \(P_s\) with \(P_{sm}\), the event \(\left\{ {{P_s} > \frac{{{{{\bar{\gamma }} }_d}}}{{{\phi _{{r_b}}}}}} \right\} \) in (58) is equivalent to \(\left\{ {{\phi _{{r_b}}} > \frac{{{{{\bar{\gamma }} }_d}}}{{{P_{sm}}}}} \right\} \). Therefore, \(O_1\) in (58) is approximated as
where \(O_{11}\) is given by (64).
Rights and permissions
About this article
Cite this article
Ho-Van, K., Do-Dac, T. Relay-and-Jammers Selection for Performance Improvement of Energy Harvesting Underlay Cognitive Networks. Arab J Sci Eng 47, 2649–2661 (2022). https://doi.org/10.1007/s13369-021-05935-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-021-05935-7