Abstract
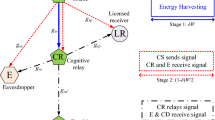
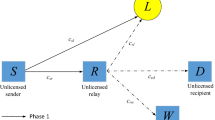
We propose a system model for energy harvesting-based underlay relaying networks with transmit antenna selection and jamming where a multi-antenna unlicensed relay performs multiple tasks [received signal combining, transmit antenna selection (TAS), energy harvesting] to save energy consumption, ensure continuous connection of an unlicensed source to an unlicensed destination, and secure transmission against a wire-tapper. Moreover, to guarantee security for source-to-relay transmission, we propose embedding jamming signal into secret information at the source to reduce the wire-tapper’s capability of decoding source message. To swiftly illustrate security-and-reliability trade-off of the proposed system model as well as compare with its counterparts so as to highlight our contributions, we propose closed forms of intercept and outage probabilities at the wire-tapper and the destination, correspondingly, under licensed interference and restraints of peak transmit/interference powers. We found from various results that (1) the proposed TAS scheme achieved the best reliability-and-security trade-off in comparison with previous schemes; (2) reliability saturation occurs at high peak transmit/interference power; (3) licensed interference and time for energy harvesting drastically enhance security yet mitigate reliability; (4) distributing power properly to secret and jamming signals at the source brings better security; (5) increasing the number of antennas at the relay dramatically improves both security and reliability for the proposed TAS scheme.







Similar content being viewed by others
Notes
System models in this paper and [34] are completely different. Therefore, performance comparison between them is not feasible and fair.
References
Li, C.; et al.: Secure transmission rate of short packets with queueing delay requirement. IEEE Trans. Wire. Commun. (2021). https://doi.org/10.1109/TWC.2021.3094615
Khalid, W.; et al.: RIS-aided physical layer security with full-duplex jamming in underlay D2D networks. IEEE Access 9, 99667–99679 (2021)
Tuan, V.P.; et al.: Enhancing secrecy performance for NOMA systems with intelligent reflecting surface: analysis and optimization. IEEE Access 9, 99060–99072 (2021)
He, H.; et al.: Secure transmission in multiple access wiretap channel: cooperative jamming without sharing CSI. IEEE Trans. Info. Forensics Secur. 16, 3401–3411 (2021)
Tang, X.; et al.: Securing wireless transmissions with RIS-receiver coordination: passive beamforming and active jamming. IEEE Trans. Veh. Tech. 70(6), 6260–6265 (2021)
Shang, X.; et al.: Secure multiuser scheduling for hybrid relay-assisted wireless powered cooperative communication networks with full-duplex destination-based jamming. IEEE Access 9, 49774–49787 (2021)
Thameur, H.B.; et al.: SDR implementation of a real-time testbed for spectrum sensing under MIMO time-selective channels for cognitive radio applications. IEEE Sensors Lett. 5(8), 1–4 (2021)
Gamal, S.; et al.: Multiple access in cognitive radio networks: from orthogonal and non-orthogonal to rate-splitting. IEEE Access 9, 95569–95584 (2021)
Pandey, A.; et al.: Joint impact of nodes mobility and imperfect channel estimates on the secrecy performance of cognitive radio vehicular networks over nakagami-m fading channels. IEEE Open J. Veh. Tech. 2, 289–309 (2021)
Ho-Van, K.; et al.: Relay-and-jammers selection for performance improvement of energy harvesting underlay cognitive networks. Arab. J. Sci. Eng. (2021). https://doi.org/10.1007/s13369-021-05935-7
Ho-Van, K.; et al.: Relay selection for security improvement in cognitive radio networks with energy harvesting. Wire. Commun. Mobi. Comp. (2021). https://doi.org/10.1155/2021/9921782
Gao, X.; et al.: Cooperative scheme for backscatter-aided passive relay communications in wireless-powered D2D networks. IEEE IoT J. (2021). https://doi.org/10.1109/JIOT.2021.3096652
Shukla, A.K.; et al.: Performance analysis of energy harvesting-assisted overlay cognitive NOMA systems with incremental relaying. IEEE Open J. Commun. Soc. 2, 1558–1576 (2021)
Iqbal, A.; et al.: cDERSA: cognitive D2D enabled relay selection algorithm to mitigate blind-spots in 5G cellular networks. IEEE Access 9, 89972–89988 (2021)
Muhammad, S.; et al.: A dual-band ambient energy harvesting rectenna design for wireless power communications. IEEE Access 9, 99944–99953 (2021)
Williams, A.J.; et al.: Survey of energy harvesting technologies for wireless sensor networks. IEEE Access 9, 77493–77510 (2021)
Amini, M.R.; et al.: Performance analysis of URLL energy-harvesting cognitive-radio IoT networks with short packet and diversity transmissions. IEEE Access 9, 79293–79306 (2021)
Jung, E.M.; et al.: A Wideband, Quasi-Isotropic, Ambient RF energy harvester combining UHF-TV and FM. IEEE Antennas Wire. Prop. Lett. 20(10), 1854–1858 (2021)
Khodeir, M. A.; et al.: Secrecy outage performance with EH and TAS for realistic underlay cognitive radio networks using MIMO systems, In: Proc. IEEE ICICS, 24-26 May 2021, Valencia, Spain, pp. 405-410 (2021)
Shi, H.; et al.: Physical layer security in an untrusted energy harvesting relay network. IEEE Access 7, 24819–24828 (2019)
Ho-Van, K.; et al.: Impact of channel estimation-and-artificial noise cancellation imperfection on artificial noise-aided energy harvesting overlay networks. Telecommun. Sys. 78, 273–292 (2021)
Ho-Van, K.; et al.: Impact of artificial noise on security capability of energy harvesting overlay networks, Wire. Commun. Mobi. Comp, pp. 1-12, (2021)
Dang-Ngoc, H.; et al.: Secrecy Analysis of Overlay Mechanism in Radio Frequency Energy Harvesting Networks with Jamming under Nakagami-m fading. Wire. Per. Commun. 110(2), 829–846 (2020)
Ho-Van, K.; et al.: Overlay networks with jamming and energy harvesting: security analysis. Arab. J. Sci. Eng. 46, 9713–9724 (2021)
Wang, D.; et al.: Primary privacy preserving with joint wireless power and information transfer for cognitive radio networks. IEEE Trans. Cogn. Commun. Netw. 6(2), 683–693 (2020)
Pham-Thi-Dan, N.; et al.: Security for jamming-aided energy harvesting cognitive radio networks, In: Proc. IEEE ISEE, HCM City, Vietnam, 15-16, pp. 125-128, (2021)
Ho-Van, K.; et al.: Security improvement for energy harvesting based overlay cognitive networks with jamming-assisted full-duplex destinations. IEEE Trans. Veh. Tech. (2021). https://doi.org/10.1109/TVT.2021.3118329
Ho-Van, K.; et al.: Security enhancement for energy harvesting cognitive networks with relay selection, Wire. Commun. Mob. Comp., vol. 2020, pp. 1-13
Ji, B.; et al.: Secrecy performance analysis of UAV assisted relay transmission for cognitive network with energy harvesting. IEEE Trans. Veh. Tech. 69(7), 7404–7415 (2020)
Ho-Van, K.; et al.: Security performance of underlay cognitive relaying networks with energy harvesting. Wire. Per. Commun. 110(2), 829–846 (2020)
Ho-Van, K.; et al.: Security analysis for underlay cognitive network with energy scavenging capable relay over Nakagami-m fading channels. Wire. Commun. Mob. Comp. (2019). https://doi.org/10.1109/ISEE2.2019.8920857
Ho-Van, K.; et al.: Relaying communications in energy scavenging cognitive networks: secrecy outage probability analysis. Wire. Commun. Mob. Comp. 2019, 1–13 (2019)
Ho-Van, K.; et al.: Eavesdropping-decoding compromise in spectrum sharing paradigm with ES-capable AF relay. Wire. Netw. 26(3), 1937–1948 (2020)
Bouabdellah, M.; et al.: Cooperative energy harvesting cognitive radio networks with spectrum sharing and security constraints. IEEE Access 7, 173329–173343 (2019)
Bletsas, A.; et al.: A simple cooperative diversity method based on network path selection. IEEE JSAC 24(3), 659–672 (2006)
Simon, M.K.; et al.: Digital Communication over Fading Channels, 2nd edn Wiley, Hoboken, New Jersey (2005)
Wang, F.; et al.: Secure resource allocation for polarization-based non-linear energy harvesting over 5G cooperative CRNs. IEEE Wire. Commun. Lett. (2020). https://doi.org/10.1109/LWC.2020.3028585
Ho-Van, K.; et al.: On the outage performance of reactive relay selection in cooperative cognitive networks over Nakagami-m fading channels. Wire. Per. Commun. 96(1), 1007–1027 (2017)
Gradshteyn, I.S.; et al.: Table of Integrals, 6th edn Series and Products, Academic Press, San Diego, CA, USA (2000)
Press, W.H.; et al.: Numerical recipes in C: the art of scientific computing, 2nd edn Cambridge University Press (1992)
Acknowledgements
We would like to thank Ho Chi Minh City University of Technology (HCMUT), VNU-HCM for the support of time and facilities for this study.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Le-Thanh, T., Ho-Van, K. Security-and-Reliability Trade-off of Energy Harvesting-Based Underlay Relaying Networks with Transmit Antenna Selection and Jamming. Arab J Sci Eng 47, 13711–13727 (2022). https://doi.org/10.1007/s13369-021-06413-w
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13369-021-06413-w