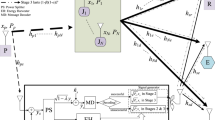
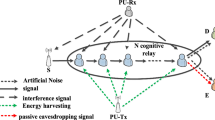
Abstract
EHONs (Energy Harvesting Overlay Networks) satisfy stringent design requirements such as high energy-and-spectrum utilization efficiencies. However, due to open access nature of these networks, eavesdroppers can emulate cognitive radios to wire-tap legitimate information, inducing information security to become a great concern. In order to protect legitimate information against eavesdroppers, this paper generates artificial noise transmitted simultaneously with legitimate information to interfere eavesdroppers. Nonetheless, artificial noise cannot be perfectly suppressed at legitimate receivers as for its primary purpose of interfering only eavesdroppers. Moreover, channel information used for signal detection is hardly estimated at receivers with absolute accuracy. As such, to quickly evaluate impact of channel estimation-and-artificial noise cancellation imperfection on secrecy performance of secondary/primary communication in ANaEHONs (Artificial Noise-aided EHONs), this paper firstly proposes precise closed-form formulas of primary/secondary SOP (Secrecy Outage Probability). Then, computer simulations are provided to corroborate these formulas. Finally, various results are illustrated to shed insights into secrecy performance of ANaEHON with key system parameters from which optimum parameters are recognized. Notably, secondary/primary communication can be secured at different levels by flexibly adjusting various parameters of the proposed system model.












Similar content being viewed by others
Notes
[24] investigated the same system model as [14] and [15]. Nonetheless, the energy source which the secondary transmitter scavenges is not RF signals, significantly simplifying the analysis in [24]. Furthermore, [24] ignored artificial noise. Consequently, references such as [24] are not related works for survey.
References
Yu, L., Liu, Z., Wen, M., Cai, D., Dang, S., Wang, Y., & Xiao, P. (2021). Sparse code multiple access for 6G wireless communication networks: Recent advances and future directions. IEEE Communications Standards Magazine, 5(2), 92–99.
Li, W., Wang, N., Jiao, L., & Zeng, K. (2021). Physical layer spoofing attack detection in MmWave massive MIMO 5G networks. IEEE Access, 9, 60419–60432.
De Alwis, C., Kalla, A., Pham, Q. V., Kumar, P., Dev, K., Hwang, W. J., et al. (2021). Survey on 6G frontiers: Trends, applications, requirements, technologies and future research. IEEE OJCS, 2, 836–886.
Motz, C., Paireder, T., & Huemer, M. (2021). Low-complex digital cancellation of transmitter harmonics in LTE-A/5G transceivers. IEEE OJCS, 2, 948–963.
Savic, M., Lukic, M., Danilovic, D., Bodroski, Z., Bajović, D., Mezei, I., et al. (2021). Deep learning anomaly detection for cellular IoT with applications in smart logistics. IEEE Access, 9, 59406–59419.
Ali, M., Qaisar, S., Naeem, M., Ejaz, W., & Kvedaraite, N. (2020). LTE-U WiFi HetNets: Enabling spectrum sharing for 5G/beyond 5G systems. IEEE Internet of Things Magazine, 3(4), 60–65.
Tian, Z., Yi, S., Zhiwen, P., Nan, L., & Xiaohu, Y. (2021). Matching theory based physical layer secure transmission strategy for cognitive radio networks. IEEE Access, 9, 46201–46209.
Fakharian, M. M. (2021). RF energy harvesting using high impedance asymmetric antenna array without impedance matching network. Radio Science, 56(3), 1–10.
Eltresy, N. A., Abd Elhamid, M., Elsheakh, D. M., Elhennawy, H. M., & Abdallah, E. A. (2021). Silver sandwiched ITO based transparent antenna array for RF energy harvesting in 5G mid-range of frequencies. IEEE Access, 9, 49476–49486.
Gunasinghe, D., & Baduge, G. A. A. Performance analysis of SWIPT for intelligent reflective surfaces for wireless communication. IEEE Communications Letters. https://ieeexplore.ieee.org/document/9404225
Le, Q. N., Yadav, A., Nguyen, N. P., Dobre, O. A., & Zhao, R. (2021). Full-duplex non-orthogonal multiple access cooperative overlay spectrum-sharing networks with SWIPT. IEEE Transactions on Green Communications and Networking, 5(1), 322–334.
Sadique, J. J., Ullah, S. E., Islam, M. R., Raad, R., Kouzani, A. Z., & Mahmud, M. P. (2021). Transceiver design for full-duplex UAV based zero-padded OFDM system with physical layer security. IEEE Access, 9, 59432–59445.
Shang, X., Yin, H., Wang, Y., Li, M., & Wang, Y. (2021). Secure multiuser scheduling for hybrid relay-assisted wireless powered cooperative communication networks with full-duplex destination-based jamming. IEEE Access, 9, 49774–49787.
Su, R., Wang, Y., & Sun, R. (2019). Secure cooperative transmission in cognitive AF relay systems with destination-aided jamming and energy harvesting. Proc (pp. 1–5). Turkey: IEEE PIMRC.
Su, R., Wang, Y., & Sun, R. (2018). Destination-assisted jamming for physical-layer security in SWIPT cognitive radio systems. Proc (pp. 1–6). Spain: IEEE WCNC.
Wang, D., Zhou, F., & Leung, V. C. (2020). Primary privacy preserving with joint wireless power and information transfer for cognitive radio networks. IEEE Transactions on Cognitive Communications and Networking, 6(2), 683–693.
Xu, M., Jing, T., Fan, X., Wen, Y., & Huo, Y. (2018). Secure transmission solutions in energy harvesting enabled cooperative cognitive radio networks. Proc (pp. 1–6). Spain: IEEE WCNC.
Ho-Van, K., & Do-Dac, T. Overlay networks with jamming and energy harvesting: Security analysis. Arabian Journal for Science and Engineering. https://doi.org/10.1007/s13369-021-05492-z
Dang-Ngoc, H., Ho-Quoc, B., & Ho-Van, K. (2020). Key secrecy performance metrics of overlay networks with energy scavenging and artificial noise. In Proc. IEEE SigTelCom, Vietnam, 28-29 Aug. (pp. 77–81).
Pham-Thi-Dan, N., Ho-Quoc, B., Ho-Van, K., Do-Dac, T., Nguyen-Huu, P., Vo-Que, S., Pham-Ngoc, S., & Pham-Hong, L. (2020). Secrecy throughput analysis of energy scavenging overlay networks with artificial noise. In Proc. IEEE ATC, Vietnam, 8-10 Aug (pp. 90–94).
Dang-Ngoc, H., Ho-Van, K., & Do-Dac, T. Secrecy analysis of overlay mechanism in radio frequency energy harvesting networks with jamming under Nakagami-m fading. Wireless Personal Communications. https://doi.org/10.1007/s11277-021-08468-2
Wang, D., & Tellambura, C. (2020). Performance analysis of energy beamforming WPCN links with channel estimation errors. IEEE OJ-CS, 1, 1153–1170.
Li, M., Yin, H., Huang, Y., Wang, Y., & Yu, R. (2018). Physical layer security in overlay cognitive radio networks with energy harvesting. IEEE Transactions on Vehicular Technology, 67, 11274–11279.
Chen, L., Huang, L., Xu, H., Yang, C., Sun, Z., & Wang, X., (2015). Primary secrecy is achievable: Optimal secrecy rate in overlay CRNs with an energy harvesting secondary transmitter. Proc (pp. 1–6). USA: ICCCN.
Kazmi, S. A. A., & Coleri, S. (2020). Optimization of full-duplex relaying system with non-linear energy harvester. IEEE Access, 8, 201566–201576.
Tran, T. N., Vo, T. P., Fazio, P., & Voznak, M. SWIPT model adopting a PS framework to Aid IoT networks inspired by the emerging cooperative NOMA technique. IEEE Access, accepted.
Ho-Van, K., & Do-Dac, T. (2019). Security analysis for underlay cognitive network with energy scavenging capable relay over Nakagami-m fading channels. Wireless Communications and Mobile Computing, 2019, 1–16.
Nguyen-Huu, P., Ho-Van, K., & Bao, V. N. Q. (2019). Secrecy outage analysis of energy harvesting two-way relaying networks with friendly jammer. IET Communications, 13(13), 1877–1885.
Ge, L., Chen, G., Zhang, Y., Tang, J., Wang, J., & Chambers, J. A. (2020). Performance analysis for multihop cognitive radio networks with energy harvesting by using stochastic geometry. IEEE IoT Journal, 7(2), 1154–1163.
Gradshteyn, I. S., & Ryzhik, I. M. (2000). Table of integrals, series and products (6th ed.). Academic.
Acknowledgements
This research is funded by Vietnam National University HoChiMinh City (VNU-HCM) under Grant Number B2021-20-01. We would like to thank Ho Chi Minh City University of Technology (HCMUT), VNU-HCM for the support of time and facilities for this study.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ho-Van, K., Do-Dac, T. Impact of channel estimation-and-artificial noise cancellation imperfection on artificial noise-aided energy harvesting overlay networks. Telecommun Syst 78, 273–292 (2021). https://doi.org/10.1007/s11235-021-00808-8
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-021-00808-8