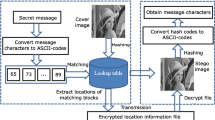
Abstract
Data hiding, also known as information hiding and digital watermarking, refers to the technology of hiding secret information in publicly available media and making it difficult for people to feel its existence. According to the survival result of the hidden information when the stego media is processed, this technology can be divided into robust, semi-fragile, and fragile watermarking. Strong robust digital watermarking is technically difficult to achieve, so it is unrealistic to apply it for digital copyright protection at present. In contrast, fragile (and semi-fragile) watermarking has good feasibility and has been used for authentication and tamper localization of the stego media. However, the existing technology has limitations. To improve the sensitivity and positioning accuracy of tampering, some algorithms embed excessive data, which greatly reduces the fidelity of stego media. To prevent third parties from bypassing integrity authentication and tamper localization, some algorithms add complex encryption algorithms to achieve the confidentiality of hidden data, which not only greatly increases the computational cost, but also destroys the blindness of data extraction. To overcome these shortcomings, this paper proposes a lightweight large-capacity image data-hiding technology. Both the data hiding and data extraction are based on looking up a shared codebook table, so the computational cost on both sides is low. The codebook table can be flexibly customized according to the agreement of the sender and receiver of the stego image. It not only ensures the fidelity of stego image but also naturally provides the confidentiality of hidden data. The experimental results and analysis show that its comprehensive performance, including imperceptibility, capacity, complexity, security, and customizability, is better than various state-of-the-art fragile watermarking techniques. Thus, the proposed technique has obvious advantages when used in image authentication, tampering localization, source tracing, and steganography. The proposed technique can be flexibly extended to hide data in other media.












Similar content being viewed by others
Data availability
The datasets generated during and/or analyzed during the current study are available from the corresponding author on reasonable request.
References
Abdel Raouf A (2021) A new data hiding approach for image steganography based on visual color sensitivity. Multimed Tools Appl 80:23393–23417. https://doi.org/10.1007/s11042-020-10224-w
Akgul A, Kacar S, Aricioglu B (2017) A new two-level data hiding algorithm for high security based on a nonlinear system. Nonlinear Dynam 90:1123–1140. https://doi.org/10.1007/s11071-017-3714-8
Akhtarkavan E, Majidi B, Mandegari A (2023) Secure Medical Image Communication Using Fragile Data Hiding Based on Discrete Wavelet Transform and Lattice Vector Quantization. IEEE Access 11:9701–9715. https://doi.org/10.1109/ACCESS.2023.3238575
Alshehri L, Hussain M, Aboalsamh H, at al. (2020) Fragile watermarking for image authentication using BRINT and ELM. Multimed Tools Appl 79:29199–29223. https://doi.org/10.1007/s11042-020-09441-0
Anand A, Singh AK (2022) SDH: Secure Data Hiding in Fused Medical Image for Smart Healthcare. IEEE Trans Comput Soc Syst 9(4):1265–1273. https://doi.org/10.1109/TCSS.2021.3125025
Asad NM, Salameh HI (2012) A Modification of Odd and Even Digital Watermark Technique. Asian J Inform Technol 11(4):151–152
Basu S, Debnath A, Basu A et al (2022) An image data hiding technique using Differential Evolution. Multimed Tools Appl 81:39995–40012. https://doi.org/10.1007/s11042-022-12557-0
Bose A, Maity SP (2022) Secure sparse watermarking on DWT-SVD for digital images. J Inform Sec Appl 68. https://doi.org/10.1016/j.jisa.2022.103255
Chan C-K, Cheng L-M (2004) Hiding data in images by simple LSB substitution. Pattern Recogn 37(1):469–474
Chang J-C, Lu Y-Z, Wu H-L (2017) A separable reversible data hiding scheme for encrypted JPEG bit streams. Signal Process 133:135–143
Chen Y-Y, Chi K-Y (2019) Cloud image watermarking: high quality data hiding and blind decoding scheme based on block truncation coding. Multimedia Systems 25:551–563. https://doi.org/10.1007/s00530-017-0560-y
Chen Y-Y, Hsia C-H, Jhong S-Y et al (2018) Data hiding method for AMBTC compressed images, Journal of Ambient Intelligence and Humanized. Comput. https://doi.org/10.1007/s12652-018-1048-0
Chen B, Yin X, Lu W et al (2023) Reversible data hiding in encrypted domain by signal reconstruction. Multimed Tools Appl 82:1203–1222. https://doi.org/10.1007/s11042-022-13266-4
Dragoi IC, Coltuc D (2021) On the Security of Reversible Data Hiding in Encrypted Images by MSB Prediction. IEEE Trans Inform Foren Sec 16:187–189. https://doi.org/10.1109/TIFS.2020.3006382
Huang H-S (2015) A combined image steganographic method using multi-way pixel value differencing, the Sixth International Conference on Graphic and Image Processing, ICGIP 2015. Int Soc Optics Phot 2015:315–319
Jhong C-L, Wu H-L (2022) Grayscale-Invariant Reversible Data Hiding Based on Multiple Histograms Modification. IEEE Trans Circuits Syst Video Technol 32(9):5888–5901. https://doi.org/10.1109/TCSVT.2022.3164013
Jung K-H (2010) High-capacity steganographic method based on pixel-value differencing and LSB replacement methods. Imaging Sci J 58(2010):213–221
Jung K-H, Yoo K-Y (2015) Steganographic method based on interpolation and LSB substitution of digital images. Multimed Tools Appl 74(2015):2143–2155
Kamili A, Hurrah NN, Parah SA et al (2021) DWFCAT: Dual Watermarking Framework for Industrial Image Authentication and Tamper Localization. IEEE Trans Industr Inform 17(7):5108–5117. https://doi.org/10.1109/TII.2020.3028612
Khadse DB, Swain G (2022) Data Hiding and Integrity Verification based on Quotient Value Differencing and Merkle Tree. Arab J Sci Eng. https://doi.org/10.1007/s13369-022-06961-9
Khan LS, Khan M, Hazzazi MM et al (2023) A novel combination of information confidentiality and data hiding mechanism. Multimed Tools Appl 82:6917–6941. https://doi.org/10.1007/s11042-022-13623-3
Khodaei M, Faez K (2012) New adaptive steganographic method using least significant bit substitution and pixel-value differencing. IET Image Process 6(2012):677–686
Kim HW, Choi D, Kim T (2010) Selective correlation detector for additive spread spectrum watermarking in transform domain. Signal Process 90(8):2605–2610
Kim D-S, Yoon E-J, Kim C et al (2018) Reversible data hiding scheme with edge-direction predictor and modulo operation. J Real-Time Image Proc 14:137–145. https://doi.org/10.1007/s11554-015-0548-9
Kumar S, Gupta A, Walia GS (2022) Reversible data hiding: A contemporary survey of state-of-the-art, opportunities and challenges. Appl Intell 52:7373–7406. https://doi.org/10.1007/s10489-021-02789-2
Leelavathi R, Prasad MNG (2022) A high capacity reversible data hiding scheme in efficient LZW compression. Multimed Tools Appl. https://doi.org/10.1007/s11042-022-13765-4
Lefèvre P, Carré P, Fontaine C et al (2022) Efficient image tampering localization using semi-fragile watermarking and error control codes. Signal Process 190. https://doi.org/10.1016/j.sigpro.2021.108342
Li F, Mao Q, Chang C-C (2018) Reversible data hiding scheme based on the Haar discrete wavelet transform and interleaving prediction method. Multimed Tools Appl 77:5149–5168. https://doi.org/10.1007/s11042-017-4388-4
Li Y, Chang C-C, He M (2020) High Capacity Reversible Data Hiding for VQ-Compressed Images Based on Difference Transformation and Mapping Technique. IEEE Access 8:32226–32245. https://doi.org/10.1109/ACCESS.2020.2973179
Lin Y-K (2014) A data hiding scheme based upon DCT coefficient modification. Comput Stand Inter 36(5):855–862
Liu J-L, Lou D-C, Tso H-K (2006) A robust watermarking scheme using self-reference image. Comput Stand Interf 28(3):356–367
Liu Z, Huang Y, Huang J (2019) Patchwork-Based Audio Watermarking Robust Against De-Synchronization and Recapturing Attacks. IEEE Trans Inform Forensics Sec 14(5):1171–1180
Luo Y, Li L, Liu J, at al.. (2021) A multi-scale image watermarking based on integer wavelet transform and singular value decomposition. Expert Syst Appl 168. https://doi.org/10.1016/j.eswa.2020.114272
Malik A, Singh S, Kumar R (2018) Recovery based high capacity reversible data hiding scheme using even-odd embedding. Multimed Tools Appl 77(2018):15803–15827
Mandal J, Das D (2017) Steganography using adaptive pixel value differencing (APVD) of gray images through exclusion of overflow/underflow. Signal Process 122(2017):234–244
Moad MS, Kafi MR, Khaldi A (2022) A wavelet based medical image watermarking scheme for secure transmission in telemedicine applications. Microprocess Microsyst 90. https://doi.org/10.1016/j.micpro.2022.104490
Mohammad AA, Ali A-H, Farfoura M (2019) An improved capacity data hiding technique based on image interpolation. Multimed Tools Appl 78:7181–7205. https://doi.org/10.1007/s11042-018-6465-8
Mukherjee DP, Maitra S, Acton ST (2004) Spatial domain digital watermarking of multimedia objects for buyer authentication. IEEE Trans Multim 6(1):1–15
Patel R, Lad K, Patel M et al (2021) A hybrid DST-SBPNRM approach for compressed video steganography. Multimedia Systems 27:417–428. https://doi.org/10.1007/s00530-020-00735-9
Prasad S, Pal AK (2020) Hamming code and logistic-map based pixel-level active forgery detection scheme using fragile watermarking. Multimed Tools Appl 79:20897–20928. https://doi.org/10.1007/s11042-020-08715-x
Raj NR, Shreelekshmi R (2022) Fragile watermarking scheme for tamper localization in images using logistic map and singular value decomposition. J Visual Commun Imag Represent 85. https://doi.org/10.1016/j.jvcir.2022.103500
Roselin Kiruba R, Sharmila TS (2023) A novel data hiding by image interpolation using edge quad-tree block complexity. Vis Comput 39:59–72. https://doi.org/10.1007/s00371-021-02312-1
Singla D, Syal R (2012) Data Security Using LSB & DCT Steganography In Images. Int J Comput Engin Res 2(2):359–364
Sisaudia V, Vishwakarma VP (2022) A secure gray-scale image watermarking technique in fractional DCT domain using zig-zag scrambling. J Inform Sec Appli 69. https://doi.org/10.1016/j.jisa.2022.103296
Tsai C-S, Zhang Y-S, Weng C-Y (2022) Separable reversible data hiding in encrypted images based on Paillier cryptosystem. Multimed Tools Appl 81:18807–18827. https://doi.org/10.1007/s11042-022-12684-8
Wang Y, Pearmain A (2004) Blind image data hiding based on self reference. Pattern Recogn Lett 25(15):1681–1689
Wang Z-H, Chang C-C, Li M-C (2012) Optimizing least-significant-bit substitution using cat swarm optimization strategy. Inf Sci 192(2012):98–108
Wang J, Zhang L-Y, Chen J et al (2019) Compressed Sensing Based Selective Encryption With Data Hiding Capability. IEEE Trans Indust Inform 15(12):6560–6571. https://doi.org/10.1109/TII.2019.2924083
Xia Z, Zhang W, Duan H et al (2022) Fragile watermarking scheme in spatial domain based on prime number distribution theory. Multimed Tools Appl 81:6477–6496. https://doi.org/10.1007/s11042-021-11704-3
Yadav GS, Mangal P, Parmar G et al (2023) Genetic algorithm and hamilton path based data hiding scheme including embedding cost optimization. Multimed Tools Appl. https://doi.org/10.1007/s11042-022-14322-9
Yang H, Sun X, Sun G (2019) A high-capacity image data hiding scheme using adaptive LSB substitution. Radio Eng 18(2009):509–516
Yi S, Zhou Y (2019) Separable and Reversible Data Hiding in Encrypted Images Using Parametric Binary Tree Labeling. IEEE Trans Multimed 21(1):51–64. https://doi.org/10.1109/TMM.2018.2844679
Yin Z, Xiang Y, Zhang X (2020) Reversible Data Hiding in Encrypted Images Based on Multi-MSB Prediction and Huffman Coding. IEEE Trans Multimed 22(4):874–884. https://doi.org/10.1109/TMM.2019.2936314
Yu M, Yao H, Qin C et al (2023) Reversible Data Hiding in Palette Images. IEEE Trans Circuits Syst Video Technol 33(2):648–660. https://doi.org/10.1109/TCSVT.2022.3207270
Zaid AO, Makhloufi A, Bouallegue A (2009) Improved QIM-based watermarking integrated to JPEG2000 coding scheme. Sign, Image Video Proc 3(2009):197–207
Zhang H, Sun S, Hu L et al (2022) A novel data hiding scheme based on improved diamond encoding in IWT domain. Multimed Tools Appl. https://doi.org/10.1007/s11042-022-14235-7
Acknowledgment
The authors are grateful to anonymous reviewers for useful suggestions. This research was sponsored by the Key R&D Program of Hubei Province, China (Grant number 2021BAA039). Thank Prof. Xiaochuan Shi, who works at the School of Cyber Science and Engineering of Wuhan University, for helping to obtain the funding.
Author information
Authors and Affiliations
Corresponding authors
Ethics declarations
Conflict of interest
We declare that we have no financial and personal relationships with other people or organizations that can inappropriately influence our work, and there is no professional or other personal interest of any nature or kind in any product, service, and/or company that could be construed as influencing the position presented in, or the review of, the manuscript entitled.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ding, W., Zhang, H., Reulke, R. et al. Large-capacity image data hiding based on table look-up. Multimed Tools Appl 82, 44123–44146 (2023). https://doi.org/10.1007/s11042-023-15514-7
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-023-15514-7