Abstract
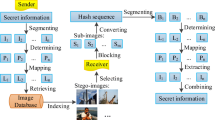
Most of the coverless information hiding approaches use a set of cover images as stego-images which make them unsuitable for real-time applications. Moreover, the parameters that affect the hiding capacity and the robustness against image processing attacks are not explicitly studied. This paper explores the effectiveness of coverless information hiding using only one cover image to transmit secret information based on eigen decomposition. The proposed approach performs coverless information hiding by establishing mapping relationships between the hash codes of the image blocks and the characters of the secret message. The hash code is calculated by splitting the block into 9 sub-blocks and then comparing the largest eigenvalues of the sub-blocks according to four arrangements. To speed up the embedding process, we build a lookup table to store the pre-computed hash codes with the corresponding block locations. The approach has three important parameters: overlapping blocks, arrangements of sub-blocks, and block sizes. Several experiments are conducted to analyze the effect of these parameters on performance. The results of the analyses indicate that the overlapping between image blocks is necessary to generate a sufficient number of unique hash codes. Otherwise, the embedding process could not be completed using a single image. The arrangement between sub-blocks has a lower impact on the number of unique hash codes and the resilience against image processing attacks. The block size is another important parameter. As the block size increases, the hiding capacity decreases and the resilience against image processing attacks improves. Compared with other coverless information hiding approaches, the proposed approach has a higher hiding capacity and better resilience against image processing attacks. Moreover, the approach has short execution time and better resistance to detecting tools.






Similar content being viewed by others
References
Bishop CM (2006) Pattern recognition and machine learning. Springer
Fridrich J, Kodovsky J (2012) Rich models for steganalysis of digital images. IEEE Transactions on Information Forensics and Security 7(3):868–882
Guo Y, Li C, Liu Q (2019) R2n: a novel deep learning architecture for rain removal from single image. CMC-Computers Materials and Continua 58 (3):829–843
Hu D, Wang L, Jiang W, Zheng S, Li B (2018) A novel image steganography method via deep convolutional generative adversarial networks. IEEE Access 6:38303–38314
Huang F, Huang J, S Y-Q (2012) New channel selection rule for jpeg steganography. IEEE Transactions on Information Forensics and Security 7(4):1181–1191
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on lsb matching revisited. IEEE Transactions on information forensics and security 5(2):201–214
Luo Y, Qin J, Xiang X, Tan Y, Liu Q, Xiang L (2020) Coverless real-time image information hiding based on image block matching and dense convolutional network. J Real-Time Image Proc 17(1):125–135
McKeon RT (2007) Strange fourier steganography in movies. In: IEEE international conference on electro/information technology, pp 178–182
Muhuri PK, Ashraf Z, Goel S (2020) A novel image steganographic method based on integer wavelet transformation and particle swarm optimization. Appl Soft Comput 92:1–26
Paillier P (1999) Public-key cryptosystems based on composite degree residuosity classes. In: International conference on the theory and applications of cryptographic techniques. Springer, pp 223–238
Sahu AK, Swain G (2019) A novel n-rightmost bit replacement image steganography technique. 3D Research 10(2):1–18
Sahu AK, Swain G (2020) Reversible image steganography using dual-layer lsb matching. Sensing and Imaging 21(1):1–21
Wu D-C, Tsai W-H (2003) A steganographic method for images by pixel-value differencing. Pattern Recogn Lett 24(9-10):1613–1626
Yuan C, Xia Z, Sun X (2017) Coverless image steganography based on sift and bof. Journal of Internet Technology 18(2):435–442
Zhang X, Wang S (2005) Steganography using multiple-base notational system and human vision sensitivity. IEEE Signal Processing Letters 12(1):67–70
Zhang X, Peng F, Long M (2018) Robust coverless image steganography based on dct and lda topic classification. IEEE Transactions on Multimedia 20 (12):3223–3238
Zheng S, Wang L, Ling B, Hu D (2017) Coverless information hiding based on robust image hashing. In: International conference on intelligent computing (ICIC). Springer, pp 536–547
Zhili Z, Cao Y, Wang M (2019) Faster-rcnn based robust coverless information hiding system in cloud environment. IEEE Access
Zhiwei K, Jing L, Yigang H (2007) Steganography based on wavelet transform and modulus function. J Syst Eng Electron 18(3):628–632
Zhou Z, Sun H, Harit R, Chen X, Sun X (2015) Coverless image steganography without embedding. In: International conference on cloud computing and security. Springer, pp 123–132
Zhou Z, Cao Y, Sun X (2016) Coverless information hiding based on bag-of-words model of image. J Appl Sci 34(5):527–536
Zhou Z, Wu QJ, Yang CN, Sun X, Pan Z (2017) Coverless image steganography using histograms of oriented gradients-based hashing algorithm. Journal of Internet Technology 18(15):1177–1184
Zhou Z, Wu Q, Sun X (2018) Encoding multiple contextual clues for partial-duplicate image retrieval. Pattern Recogn Lett 109:18–26
Zhou Z, Mu Y, Wu Q (2019) Coverless image steganography using partial-duplicate image retrieval. Soft Comput 23(13):4927–4938
Zou L, Sun J, Gao M, Wan W, Gupta BB (2019) A novel coverless information hiding method based on the average pixel value of the sub-images. Multimedia Tools and Applications 78(7):7965–7980
Acknowledgements
The author would like to thank Mustansiriyah University / Baghdad / Iraq for its support in the present work.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of Interests
The author declares that she has no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Abdulsattar, F.S. Towards a high capacity coverless information hiding approach. Multimed Tools Appl 80, 18821–18837 (2021). https://doi.org/10.1007/s11042-021-10608-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10608-6