Abstract
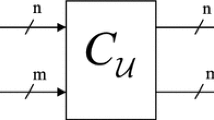
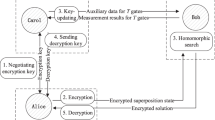
Suppose some data have been encrypted, can you compute with the data without decrypting them? This problem has been studied as homomorphic encryption and blind computing. We consider this problem in the context of quantum information processing, and present the definitions of quantum homomorphic encryption (QHE) and quantum fully homomorphic encryption (QFHE). Then, based on quantum one-time pad (QOTP), we construct a symmetric QFHE scheme, where the evaluate algorithm depends on the secret key. This scheme permits any unitary transformation on any \(n\)-qubit state that has been encrypted. Compared with classical homomorphic encryption, the QFHE scheme has perfect security. Finally, we also construct a QOTP-based symmetric QHE scheme, where the evaluate algorithm is independent of the secret key.
Similar content being viewed by others
References
Rivest, R.L., Adleman, L., Dertouzos, M.L.: On data banks and privacy homomorphisms. Found. Secur. Comput. 4(11), 169 (1978)
Feigenbaum, J.: Encrypting problem instances. Advances in cryptology. In: Proceedings of Crypto’85, p. 477. Springer, Berlin (1985)
Abadi, M., Feigenbaum, J., Kilian, J.: On hiding information from an oracle. J. Comput. Syst. Sci. 39(1), 21 (1989)
Brickell, E., Yacobi, Y.: On privacy homomorphisms. Advances in cryptology. In: Proceedings of Eurocrypt’87, p. 117. Springer, Berlin (1987)
Gentry, C.: A fully homomorphic encryption scheme. PhD thesis, Stanford University (2009)
Gentry, C.: Computing arbitrary functions of encrypted data. Commun. ACM 53(3), 97 (2010)
Castelluccia, C., Chan, A.C., Mykletun, E., Tsudik, G.: Efficient and provably secure aggregation of encrypted data in wireless sensor networks. ACM Trans. Sens. Netw. 5(3), 20 (2009)
Hessler, A., Kakumaru, T., Perrey, H., Westhoff, D.: Data obfuscation with network coding. Comput. Commun. 35(1), 48–61 (2012)
Armknecht, F., Augot, D., Perret, L., Sadeghi, A.R.: On constructing homomorphic encryption schemes from coding theory. In: Chen, L.Q. (ed.) Cryptography and Coding. Springer, Berlin (2011)
Bennett, C.H., Brassard, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems, and Signal Processing, p. 175. IEEE, New York (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661 (1991)
Tamaki, K., Koashi, M., Imoto, N.: Unconditionally secure key distribution based on two nonorthogonal states. Phys. Rev. Lett 90, 167904 (2003)
Childs, A.M.: Secure assisted quantum computation. Quantum Inf. Comput. 5, 456 (2005)
Arrighi, P., Salvail, L.: Blind quantum computation. Int. J. Quantum Inf. 4, 883 (2006)
Aharonov, D., Ben-Or, M., Eban, E.: Interactive proofs for quantum computations. In: Proceeding of Innovation in Computer Science, p. 453. Tsinghua University Press, Beijing (2010)
Broadbent, A.J., Fitzsimons, F., Kashefi, E.: Universal blind quantum computation. In: Proceedings of the 50th Annual IEEE Symposium on Foundations of Computer Science, p. 517. IEEE Computer Society, Los Alamitos (2009)
Sueki, T., Koshiba, T., Morimae, T.: Ancilla-Driven Universal Blind Quantum Computation. Available via http://arxiv.org/abs/1210.7450
Barz, S., Kashefi, E., Broadbent, A., Fitzsimons, J.F., Zeilinger, A., Walther, P.: Demonstration of blind quantum computing. Science 335, 303 (2012)
Vedral, V.: Moving beyond trust in quantum computing. Science 335(6066), 294 (2012)
Morimae, T., Fujii, K.: Blind topological measurement-based quantum computation. Nat. Commun. 3, 1036 (2012)
Morimae, T.: Continuous-variable blind quantum computation. Phys. Rev. Lett. 109, 230502 (2012)
Morimae, T., Dunjko, V., Kashefi, E.: Ground state blind quantum computation on AKLT state. Available via http://arxiv.org/abs/1009.3486
Fitzsimons, J.F., Kashefi, E.: Unconditionally verifiable blind computation. Available via http://arxiv.org/abs/1203.5217
Rohde, P.P., Fitzsimons, J.F., Gilchrist, A.: Quantum walks with encrypted data. Phys. Rev. Lett. 109(15), 150501 (2012)
Giovannetti, V., Lloyd, S., Maccone, L.: Quantum private queries. Phys. Rev. Lett. 100(23), 230502 (2008)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11(2), 373–384 (2012)
Lin, S., Sun, Y., Liu, X.F., Yao, Z.Q.: Quantum private comparison protocol with d-dimensional Bell states. Quantum Inf. Process. 12(1), 559–568 (2013)
Guo, F.Z., Gao, F., Qin, S.J., Zhang, J., Wen, Q.Y.: Quantum private comparison protocol based on entanglement swapping of d-level Bell states. Quantum Inf. Process. 12(3), 1–10 (2013)
Li, Y.B., Qin, S.J., Yuan, Z., Huang, W., Sun, Y.: Quantum private comparison against decoherence noise. Quantum Inf. Process. 12(6), 2191–2205 (2013)
Liu, B., Gao, F., Jia, H.Y., Huang, W., Zhang, W.W., Wen, Q.Y.: Efficient quantum private comparison employing single photons and collective detection. Quantum Inf. Process. 12(2), 887–897 (2013)
Boykin, P.O., Roychowdhury, V.: Optimal encryption of quantum bits. Phys. Rev. A 67(4), 042317 (2003)
Ambainis, A., Mosca, M., Tapp, A., Wolf, R.: Private quantum channels. In: Proceedings of the 41st IEEE Annual Symposium on Foundations of Computer Science, p. 547. IEEE Computer Society, Los Alamitos (2000)
Nielsen, M., Chuang, I.: Quantum Computation and Quantum Information. Cambridge University Press, Cambridge (2000)
Liang, M., Yang, L.: Universal quantum circuit of near-trivial transformations. Sci. China-Phys. Mech. Astron. 54(10), 1819–1827 (2011)
Dupuis, F., Nielsen, J.B., Salvail, L.: Secure two-party quantum evaluation of unitaries against specious adversaries. Advances in cryptology. In: Proceedings of Crypto 2010, pp. 685–706. Springer, Berlin (2010)
Dupuis, F., Nielsen, J.B., Salvail, L.: Actively secure two-party evaluation of any quantum operation. Advances in cryptology. In: Proceedings of Crypto 2012, pp. 794–811. Springer, Berlin (2012)
Ambainis, A., Smith, A.: Small pseudo-random families of matrices: derandomizing approximate quantum encryption. In: Jansen, K., Khanna, S., Rolim, J.D.P., Ron, D. (eds.) Approximation, Randomization, and Combinatorial Optimization. Springer, Berlin (2004)
Liang, M., Yang, L.: Public-key encryption and authentication of quantum information. Sci. China-Phys. Mech. Astron. 55, 1618 (2012)
Author information
Authors and Affiliations
Corresponding author
Appendix
Appendix
This section lists some commutation rules about the operators \(X,Y,Z,H, CNOT, R_z(\theta ),R_y(\theta )\). Here, \(j,k,l,m\) are single-bit numbers.
Rights and permissions
About this article
Cite this article
Liang, M. Symmetric quantum fully homomorphic encryption with perfect security. Quantum Inf Process 12, 3675–3687 (2013). https://doi.org/10.1007/s11128-013-0626-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-013-0626-5