Abstract
With the increase in point of care services, communication of digital patient records through open network has multi-folded. This digital data is used to obtain the remote medical assistance from the smart healthcare centres. Protecting this data during transmission is a very big challenge. One of the most important medical data is electrocardiogram (ECG) signal which detects the cardiovascular diseases and any alteration in the signal may affect the diagnosis. In this work, an ECG watermarking based on redundant discrete wavelet transform (RDWT) and singular value decomposition (SVD) is developed. First, the ECG signal is converted into 2-D matrix using pan-tompkins algorithm. Then, we use the hybrid of RDWT and SVD to conceal the patient data and logo image into the 2-D ECG image. We also use hybrid of optimization scheme to improve the robustness of the watermark. Preliminary experimental results indicate the optimal invisibility and robustness result is more effective up to 97.89% than the traditional schemes respectively, which makes it suitable for ownership authentication of ECG signal.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
With the advancement in digital communication, it has facilitated the transfer of a large amount of data through the public network in real-time [20]. By applying these emerging technologies, smart healthcare organizations can provide remote medical services to patients [7]. POC services can be beneficial for the remote collection of patient data such as biomedical signals, blood pressure, body temperature, etc. by deploying edge level sensors [1]. At the time of transmission over the open network, different security issues also arise, including preserving data's integrity and privacy along with the source authentication [5]. To date, a variety of guidelines and standards is used to protect patient’s privacy while sharing data for diagnosis or research purposes [5, 9, 21]. Despite several benefits, health data may be redistributed by unauthorized person, which leads to strong security issue. Further, the importance of health data security has increased even more during COVID-19 pandemic [3, 10, 27].
While sending the ECG signal, some information about the patient and the hospital logo can be added as watermarks to resolve any conflict regarding the source in the future. Notably, as the ECG signal is very important for the proper diagnosis, so the watermark should be added in such a way that the degradation of the cover signal will be minimum [29]. Watermarking technique is widely used for bio medical data authentication purposes for its robust nature. In watermarking, the secret digital data is efficiently concealed within the cover to resolve the ownership conflict at any point [6]. Robustness and invisibility are the mutually exclusive properties of any general watermarking system [2]. These requirements need to be balanced to offer high performance. Recently, the concept of watermarking and optimization [4, 16] methods are used together to provide balanced tradeoff among invisibility and robustness efficiently. Optimizations schemes are mainly used to offer optimal gain/embedding value for embedding the secret data into cover [16].
Inspired by these current works, in this article an optimization-based ECG watermarking in RDWT-SVD domain is developed, which are mainly provide balanced tradeoff among invisibility and robustness through optimal embedding/gain value. The contribution of this paper can be summarized from the following aspects:
-
An optimization-based ECG watermarking in RDWT-SVD domain is developed, where main criteria in digital image watermarking are simultaneously improved i.e., quality and robustness. Due to shift invariance nature, RDWT is superior to DWT [7]. Non-fixed orthogonal bases and unidirectional non-symmetrical decomposition properties of SVD make it one of the efficient and popular methods for watermarking [5, 11].
-
Simultaneously embedding of patient details and hospital logo into ECG signal to solve any ownership conflict and offers high robustness with increased embedding capacity [30].
-
Fusion of PSO and firefly optimization (pFIR) concept [8] is used offer the balanced trade-off among invisibility and robustness efficiently.
-
Preliminary experimental results indicate the optimal invisibility and robustness result is more effective than the traditional schemes.
The rest of the paper is arranged in the following way: The related work is detailed in Section 2. Section 3 presents the detail of proposed work. In Section 4, some detail result analysis of the proposed method is carried out. Finally, Section 5 summarizes the work and gives an outlook for future plans.
2 Literature review
Some of the related research works are discussed in this section.
In [29], Sanivarapu et al. proposed a robust watermarking to securely embed patient data within ECG signal. The method used DWT to decompose the cover signal into frequency domain and embed encoded mark into the signal. Compared with the schemes developed by Edward Jero et al. [16], Jero and Ramu [19] and Mathivanan et al. [22], its invisibility is higher. In [16], authors proposed DWT-SVD based secure data hiding technique where embedding and recovery of secret data within cover signal is done using quantization. The performance is improved by utilizing optimization scheme to calculate the value of gain value, which maintains a balance between robustness and visual quality. However, the robustness analysis of this method for different attacks is missing. In [13], Dey et al. described a blind and secure watermarking method to hide data within ECG signal. In this technique, a fusion of RDWT, spread spectrum and quantization method is used to provide source authentication and self-recovery at receiver side. The results show the method is highly invisible and secure with low cost. However, different encoding techniques can also be used to further increase the security. Authors of [18] proposed a blind and secure watermarking using curvelet transform to provide security to patient’s private data. The cover ECG image is decomposed using fast discrete curvelet transform technique. Further, Euclidean distance is used get clusters from the curvelet coefficient points. The patient data is embedded as binary image into these cluster coefficients. The scheme provides more invisibility and robustness when compared with the existing techniques [15, 19, 28].
In [12], authors proposed a quantization based blind watermarking for ECG signal. Here different transform domain techniques are applied on the ECG signal and quantization-based embedding is used to hide the patient’s confidential data. The performance concluded that quantization scheme in DWT and DCT domain gives better result in term of imperceptibility and is useful for medical applications. Bio-medical signals based watermarking which provides data and owner authenticity along with data tracking in [17]. The watermarks are encoded using attribute-based encryption technique which ensures better security. Author used linear-correlation based detection method for robustly encoding the medical data. Another robust watermarking technique is implemented by Dey et al. [14] for authentication of ECG signals. The authors embed hospital logo within the second level DWT coefficients of cover signal using pseudo random sequence and three embedding factors. The values of embedding factors are optimized using cuckoo search optimization to ensure high robustness with minimum distortion. However, the embedding capacity of this technique can further be improved.
Tseng et al. [32] proposed wavelet based watermarking method to ensure secure transmission and authentication of ECG signals. In this approach, the mark is concealed in lower frequency DWT coefficients to provide better robustness. Also, wavelet-based compressed is applied on the watermarked signal to reduce the transmission overhead. In [23], Nambakhsh et al. developed a dual watermarking method to control mismatching of diagnosis report. The authors considered patient data and ECG signal as the watermarks. Multi resolution wavelet decomposition is used to securely embed both the watermarks into PET image. The secure embedding locations for embedding and extraction of marks is computed by applying texture feature extraction algorithm on the host image. The proposed method shows high resistance against various attacks.
Although the proposed watermarking solutions in ECG signals have major advantages, some of the major issues need to be addressed. Most of the discussed techniques are hiding only single watermark, which limits the security and authentication process. This also limits the embedding capacity. Also, an optimized balance between robustness, embedding capacity and visual quality need to be maintained. Further, most of the proposed watermarking techniques need extended robustness analysis.
3 Proposed method
In this section, the overview of our proposed method (see Fig. 1) is presented in detail. We describe the conversion of 1D signal to 2D signal through pan-Tompkins algorithm in Section 3.1. Then, our embedding and extraction design is presented in Section 3.2. Section 3.3 presents the determination of optimal embedding factor by using the pFIR. Specific steps of all these phases are provided in Algorithm 1 to Algorithm 3, respectively, while notations used in the algorithms are summarized in Table 1.
3.1 Conversion of 1D signal to 2D signal
In the pre-processing phase, the QRS region of the ECG signal is extracted and used as 2D carrier image. Since, maximum energy of an ECG signal is concentrated in the QRS region, embedding in this region offers better robustness against different attacks [31]. In the proposed work, pan-tompkins algorithm is implemented to convert ECG signal, ‘Ecg_1D’ into 2D carrier image, ‘Ecg_2D’ [25]. In this process, the powerline interference and high frequency noise is eliminated by passing the input ECG signal through low pass and high pass filters, respectively. Further, the P and T waves are supressed to obtain the QRS region. The complexes are enhanced by applying square and smoothening operations and adaptive threshold method is used to calculate the R wave. Finally, we resize the resulting matrix in desired size. The detailed process of this process is given in Algorithm 1 [29]. Figure 2 shows the original ECG signal and the 2D image of ECG signal containing the QRS region.

3.2 Embedding and extraction of multiple marks
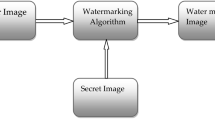
Initially, pan-Tompkins algorithm [23] is implemented to covert carrier ECG signal, ‘Ecg_1D’, into 2D image, ‘Ecg_2D’ using Algorithm 1. Further, sub-sampling is applied on ‘Ecg_2D’ to generate sub-sampled blocks, ‘F1’, ‘F2’, ‘F3’ and ‘F4’. The sub-sampled block with highest entropy value, ‘F_max’, is transformed by second level RDWT and singular matrices, ‘S_H2’ and ‘S_V2’, of the resultant middle frequency sub-bands, ‘H2’ and ‘V2’ are computed. Similar series of RDWT and SVD is applied on the mark images, ‘Waterim1’ and ‘Waterim2’. Finally, the singular value of both watermarks, ‘W_S1’ and ‘W_S2’ are embedded into ‘S_A’ and ‘S_V’, using optimized embedding factor, ‘opt_α’. Lastly, inverse SVD- inverse RDWT are applied to generate the final marked image, ‘Wat_sig’. The stepwise procedure of embedding and recovery of dual marks is given in Algorithm 2. Figure 3 illustrates the middle frequency sub-bands of cover signal before and after embedding of the watermarks. It is observed that there is no significant visual change in the sub-bands before and after embedding procedure. During extraction process, the received signal is reshaped into 2D marked image. Further, reverse of embedding algorithm is applied on marked image to get the watermark images.

3.3 Determination of optimal embedding factor
Robustness and imperceptibility are two main requirements of watermarking technique. Due to their inverse relation, an optimal balance between these requirements needs to be maintained [6]. In the proposed work, embedding and extraction schemes use optimal scaling factor, ‘opt_α’ which is calculated using Fusion of PSO and firefly optimization (pFIR). It offers optimal balance between invisibility and robustness. As shown in Fig. 4, the concept of pFIR is used to calculate the embedding factor. The stepwise procedure for deamination of scaling factor is provided Algorithm 3. The fitness function of our proposed method is calculated as,
Flow diagram of pFIR algorithm [8]
Here peak signal-to-noise ratio (PSNR) and normalized correlation coefficient (NC) are the performance parameters and ‘n’ is the count of considered attacks.

4 Results and analysis
In our experiments, two watermark images including patient’s information [26] and NIT Patna logo [24], each of size 64 × 64, are embedded into the 2D-ECG signal of size 128 × 128 [26]. To verify the proposed method, different parameters including PSNR, Percentage residual difference (PRD), Kullback Leibler (KL) distance and NC are considered [5, 15]. PSNR measures the imperceptibility of the watermarks and PRD shows the percentage of relative squared difference between of original and marked ECG signal [15]. Further, KL divergence measures the difference between the probability density functions of cover and marked ECG signals [15]. NC score is associated with the robustness of the proposed technique which measures the similarity between the original and extracted mark images [5]. It is observed that the scaling factor range from 0.05 to 0.3 gives best result. Figure 5a–d illustrates the original and marked ECG signal, and both watermarks as personal patient data and logo image. It is noticed that there is no significant dissimilarity noticed between the two signals with naked eyes. Also, the ECG signals used for the experimental evaluation of the proposed work are illustrated in Fig. 6.
Sample of different ECG signals [26]
The imperceptibility, robustness and feasibility of the proposed approach are evaluated by considering different experiments. Table 2 summarizes the versatility of the proposed method by considering different ECG signal samples (Fig. 6). The highest value of PSNR obtained is 67.8542 dB implying a good amount of imperceptibility. The NC values for both the watermarks are approaching one which shows the strong robustness. Also, the best value of PRD and KL distance are 0.291% and 0.0025. These small values of PRD and KL distance imply that the proposed method achieves good amount of imperceptibility and shows negligible distortion of the cover signal. Further, the effect on performance parameters for using different sizes of ECG signals is illustrated in Table 3 and Fig. 7. It is observed that in most of the cases we are getting the best results for the size 128 × 128.
Different signal processing attacks are considered to check the robustness of the proposed method and the result is shown in Table 4. NC values of acceptable range, i.e., NC > 0.7, are obtained for most of the attacks except for Gaussian noise and Salt and pepper noise with noise density 0.1. It is observed that our method is robust against the considered attacks. Table 5 represents the comparative analysis of the proposed method with some existing methods. Better results in terms of robustness and imperceptibility are experienced when our technique is compared with the existing state-of-the-art methods [15, 19, 22, 23]. Overall, the objective assessment confirms the promising results, while offered superiority to other competing schemes.
5 Conclusion
This paper presented a RDWT-SVD domain robust ECG watermarking scheme based on optimization, providing both data confidentiality and copyright protection. We first perform pan-tompkins algorithm to convert 1D-ECG signal into 2-D matrix. Then, hybrid of RDWT and SVD is used to invisibly embed the patient data and logo image into cover signal. We also used pFIR scheme to offer good balance between invisibility and robustness. Extensive experimental analysis of the proposed work is further provided. The proposed method provides better scores of PSNR, PRD and KL distance when compared with similar existing methods and incur high visual quality with the best improvement of 97.89%. However, the robustness against Gaussian and salt and pepper noise with high density can further be improved. In future, we can use the concept of machine learning and deep learning to retrieve the watermarks from signal more efficiently.
References
Abuadbba A, Member S, Khalil I, Member S (2016) Walsh-hadamard based 3D steganography for protecting sensitive information in point-of-care. IEEE Trans Biomed Eng 9294(2):1–10. https://doi.org/10.1109/TBME.2016.2631885
Agarwal C, Mishra A, Sharma A, Bedi P (2014) Optimized gray-scale image watermarking using DWT-SVD and firefly algorithm. Expert Syst Appl 41(17):7858–7867. https://doi.org/10.1016/j.eswa.2014.06.011
Almeida BDA, Doneda D, Ichihara MY, Barral-Netto M, Matta GC, Rabello ET, Gouveia FC, Barreto M (2020) Personal data usage and privacy considerations in the COVID-19 global pandemic. Cienc. Saude Coletiva 25:2487–2492. https://doi.org/10.1590/1413-81232020256.1.11792020
Alotaibi SS (2020) Optimization insisted watermarking model: hybrid firefly and Jaya algorithm for video copyright protection. Soft Comput 24(19):14809–14823. https://doi.org/10.1007/s00500-020-04833-8
Anand A, Singh AK (2020) An improved DWT-SVD domain watermarking for medical information security. Comput Commun 152:72–80. https://doi.org/10.1016/j.comcom.2020.01.038
Anand A, Singh AK (2020) Watermarking techniques for medical data authentication: a survey. Multimed Tools Appl. https://doi.org/10.1007/s11042-020-08801-0
Anand A, Singh AK, Lv Z, Bhatnagar G (2020) Compression-then-encryption based secure watermarking technique for smart healthcare system. IEEE Multimed 27(4):133–134. https://doi.org/10.1109/MMUL.2020.2993269
Aydilek İB (2018) A hybrid firefly and particle swarm optimization algorithm for computationally expensive numerical problems. Appl Soft Comput J 66:232–249. https://doi.org/10.1016/j.asoc.2018.02.025
Banerjee S, Singh GK (2021) A new approach of ECG steganography and prediction using deep learning. Biomed Signal Process Control 64(March 2020):102151. https://doi.org/10.1016/j.bspc.2020.102151
Bose B, Dey D, Sengupta A, Mulchandani N (2021) A novel medical image encryption using cyclic coding in covid-19 pandemic situation. J Phys Conf Ser Pap 1797(2021):1–7. https://doi.org/10.1088/1742-6596/1797/1/012035
Chang CC, Tsai P, Lin CC (2005) SVD-based digital image watermarking scheme. Pattern Recognit Lett 26(10):1577–1586. https://doi.org/10.1016/j.patrec.2005.01.004
Chen ST, Guo YJ, Huang HN, Kung WM, Tseng KK, Tu SY (2014) Hiding patients confidential datainthe ECG signal viaa transform-domain quantization scheme topical collection on mobile systems. J Med Syst 38(6):1–8. https://doi.org/10.1007/s10916-014-0054-9
Dey N, Roy AB, Das A, Chaudhuri SS (2012) Stationary wavelet transformation based self-recovery of blind-watermark from electrocardiogram signal in wireless telecardiology. Commun Comput Inf Sci 335:347–357. https://doi.org/10.1007/978-3-642-34135-9_35
Dey N, Samanta S, Yang XS, Das A, Chaudhuri SS (2013) Optimisation of scaling factors in electrocardiogram signal watermarking using cuckoo search. Int J Bio-Inspired Comput 5(5):315–326. https://doi.org/10.1504/IJBIC.2013.057193
Edward Jero S, Ramu P, Ramakrishnan S (2015) ECG steganography using curvelet transform. Biomed Signal Process Control 22:161–169. https://doi.org/10.1016/j.bspc.2015.07.004
Edward Jero S, Ramu P, Swaminathan R (2016) Imperceptibility—robustness tradeoff studies for ECG steganography using continuous ant colony optimization. Expert Syst Appl 49(123–135):2016. https://doi.org/10.1016/j.eswa.2015.12.010
Goudar V, Potkonjak M (2014) Addressing biosignal data sharing security issues with robust watermarking. In: 2014 11th Annual IEEE International Conference on Sensing, Communication, and Networking, SECON 2014, pp 618–626. https://doi.org/10.1109/SAHCN.2014.6990402
Goyal LM et al (2020) Improved ECG watermarking technique using curvelet transform. Sensors (Switzerland). https://doi.org/10.3390/s20102941
Jero SE, Ramu P (2016) Curvelets-based ECG steganography for data security. Electron Lett 52(4):4–5. https://doi.org/10.1137/05064182x
Mathivanan P, Balaji Ganesh A (2019) QR code based color image cryptography for the secured transmission of ECG signal. Multimed Tools Appl 78(6):6763–6786. https://doi.org/10.1007/s11042-018-6471-x
Mathivanan P, Balaji Ganesh A (2021) ECG steganography based on tunable Q-factor wavelet transform and singular value decomposition. Int J Imaging Syst Technol 31(1):270–287. https://doi.org/10.1002/ima.22477
Mathivanan P, Edward Jero S, Ramu P, Balaji Ganesh A (2018) QR code based patient data protection in ECG steganography. Australas Phys Eng Sci Med 41(4):1057–1068. https://doi.org/10.1007/s13246-018-0695-y
Nambakhsh MS, Ahmadian A, Zaidi H (2011) A contextual based double watermarking of PET images by patient ID and ECG signal. Comput Methods Programs Biomed 104(3):418–425. https://doi.org/10.1016/j.cmpb.2010.08.016
NIT Patna: http://www.nitp.ac.in/php/home.php
Pan J, Tompkins WJ (1985) A real-time QRS detection algorithm. IEEE Trans Biomed Eng BME32(3):230–236
“PHYSIOBANK ATM.” https://archive.physionet.org/cgi-bin/atm/ATM
Reyad O, Karar ME (2021) Secure CT—image encryption for COVID - 19 infections using HBBS—based multiple key—streams. Arab J Sci Eng 46(4):3581–3593. https://doi.org/10.1007/s13369-020-05196-w
Roy S, Mittal TKM, Kaushik R, Goyal LM, Verma A, Verma A, Kaur I (2020) Image Watermarking in Curvelet Domain Using Edge Surface Blocks. Symmetry 12:822
Sanivarapu PV, Rajesh KNVPS, Reddy NVR, Reddy NCS (2020) Patient data hiding into ECG signal using watermarking in transform domain. Australas Phys Eng Sci Med. https://doi.org/10.1007/s13246-019-00838-2
Shen H, Chen B (2012) From single watermark to dual watermark: a new approach for image watermarking. Comput Electr Eng 38(5):1310–1324. https://doi.org/10.1016/j.compeleceng.2011.11.012
Sharma N, Anand A, Singh AK (2021) Bio-signal data sharing security through watermarking: a technical survey 103:1883–1917. https://doi.org/10.1007/s00607-020-00881-y
Tseng KK, He X, Kung WM, Chen ST, Liao M, Huang HN (2014) Wavelet-based watermarking and compression for ECG signals with verification evaluation. Sensors (Switzerland) 14(2):3721–3736. https://doi.org/10.3390/s140203721
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sharma, N., Anand, A., Singh, A.K. et al. Optimization based ECG watermarking in RDWT-SVD domain. Multimed Tools Appl 82, 5031–5047 (2023). https://doi.org/10.1007/s11042-021-11519-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-11519-2