Abstract
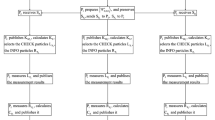
A multi-party semi-quantum key agreement (SQKA) protocol based on delegating quantum computation (DQC) model is proposed by taking Bell states as quantum resources. In the proposed protocol, the participants only need the ability of accessing quantum channel and preparing single photons {|0〉, |1〉, |+〉, |−〉}, while the complicated quantum operations, such as the unitary operations and Bell measurement, will be delegated to the remote quantum center. Compared with previous quantum key agreement protocols, this client-server model is more feasible in the early days of the emergence of quantum computers. In order to prevent the attacks from outside eavesdroppers, inner participants and quantum center, two single photon sequences are randomly inserted into Bell states: the first sequence is used to perform the quantum channel detection, while the second is applied to disorder the positions of message qubits, which guarantees the security of the protocol.




Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: Public-key distribution and coin tossing. In: Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, pp 175–179. IEEE Press, New York (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661 (1991)
Hillery, M., Bužek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829–1834 (1999)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. Phys. Rev. Lett. 83(3), 648 (1999)
Deng, F.G., Long, G.L., Liu, X.S.: Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys. Rev. A 68(4), 042317 (2003)
Liu, W.J., Chen, H.W., Ma, T.H., Li, Z.Q., Liu, Z.H., Hu, W.B.: An efficient deterministic secure quantum communication scheme based on cluster states and identity authentication. Chin. Phys. B 18(10), 4105–4109 (2009)
Liu, Z.H., Chen, H.W.: Cryptanalysis and improvement of quantum broadcast communication and authentication protocol with a quantum one-time pad. Chin. Phys. B 25(8), 080308 (2016)
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A-Math. Theor. 42(5), 055305 (2009)
Liu, W.J., Liu, C., Liu, Z.H., Liu, J.F., Geng, H.T.: Same initial states attack in Yang others.’s quantum private comparison protocol and the improvement. Int. J. Theor. Phys. 53(1), 271–276 (2014)
Liu, W.J., Liu, C., Chen, H. W., Li, Z.Q., Liu, Z.H.: Cryptanalysis and improvement of quantum private comparison protocol based on Bell entangled states. Commun. Theor. Phys. 62(2), 210–214 (2014)
Liu, W.J., Liu, C., Wang, H.B., Liu, J.F., Wang, F., Yuan, X.M.: Secure quantum private comparison of equality based on asymmetric W state. Int. J. Theor. Phys. 53(6), 1804–1813 (2014)
Liu, W.J., Wang, F., Ji, S., Qu, Z.G., Wang, X.J.: Attacks and improvement of quantum sealed-bid auction with EPR pairs. Commun. Theor. Phys. 61(6), 686–690 (2014)
Liu, W.J., Wang, H.B., Yuan, G.L., Xu, Y., Chen, Z.Y., An, X.X., Ji, F.G., Gnitou, G.T.: Multiparty quantum sealed-bid auction using single photons as message carrier. Quantum Inf. Process. 15(2), 869–879 (2016)
Liu, W.J., Chen, Z.F., Liu, C., Zheng, Y.: Improved deterministic N-to-one joint remote preparation of an arbitrary qubit via EPR pairs. Int. J. Theor. Phys. 54 (2), 472–483 (2015)
Wang, H.B., Zhou, X.Y., An, X.X., Cui, M.M., Fu, D.S.: Deterministic joint remote preparation of a four-qubit cluster-type state via GHZ states. Int. J. Theor. Phys. 55(8), 3588–3596 (2016)
Zhou, N., Zeng, G., Xiong, J.: Quantum key agreement protocol. Electron. Lett. 40(18), 1149–1150 (2004)
Chong, S.K., Tsai, C.W., Hwang, T.: Improvement on quantum key agreement protocol with maximally entangled states. Int. J. Theor. Phys. 50(6), 1793–1802 (2011)
Chong, S.K., Hwang, T.: Quantum key agreement protocol based on BB84. Opt. Commun. 283(6), 1192–1195 (2010)
Shen, D.S., Ma, W.P., Wang, L.L.: Two-party quantum key agreement with four-qubit cluster states. Quantum Inf. Process. 13(10), 2313–2324 (2014)
Huang, W., Wen, Q.Y., Liu, B., Gao, F., Sun, Y.: Quantum key agreement with EPR pairs and single-particle measurements. Quantum Inf. Process. 13(3), 649–663 (2014)
Shukla, C., Alam, N., Pathak, A.: Protocols of quantum key agreement solely using Bell states and Bell measurement. Quantum Inf. Process. 13(11), 2391–405 (2014)
Shi, R.H., Zhong, H.: Multi-party quantum key agreement with bell states and bell measurements. Quantum Inf. Process. 12(2), 921–932 (2013)
Liu, B., Gao, F., Huang, W., Wen, Q.Y.: Multiparty quantum key agreement with single particles. Quantum Inf. Process. 12(4), 1797–1805 (2013)
Sun, Z.W., Zhang, C., Wang, B., Li, Q., Long, D.: Improvements on multiparty quantum key agreement with single particles. Quantum Inf. Process. 12 (11), 3411–3420 (2013)
Sun, Z.W., Huang, J.W., Wang, P.: Efficient multiparty quantum key agreement protocol based on commutative encryption. Quantum Inf. Process. 15(5), 2101–2111 (2016)
Broadbent, A.: Delegating private quantum computations. Can. J. Phys. 93(9), 941–946 (2015)
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Information. Cambridge University Press (2000)
Fisher, K.A., Broadbent, A., Shalm, L.K., Yan, Z.: Quantum computing on encrypted data. Nat. Commun. 5(2), 3074 (2013)
Sun, Z.W., Yu, J., Wang, P., Xu, L.: Symmetrically private information retrieval based on blind quantum computing. Phys. Rev. A 91(5), 052303 (2015)
Li, Q., Chan, W.H., Zhang, S.Y.: Semiquantum key distribution with secure delegated quantum computation. Sci. Rep. 6, 19898 (2016)
Shen, J., Shen, J., Chen, X., Huang, X., Susilo, W.: An efficient public auditing protocol with novel dynamic structure for cloud data. IEEE Trans. Inf. Forens. Secur. doi:10.1109/TIFS.2017.2705620 (2017)
Liu, Q., Cai, W.D., Shen, J., Fu, Z.J., Liu, X.D., Linge, N.: A speculative approach to spatial-temporal efficiency with multi-objective optimization in a heterogeneous cloud environment. Securi. Commun. Netw. 9(17), 4002–4012 (2016)
Fu, Z.J., Shu, J.G., Wang, J., Liu, Y.L., Lee, S.Y.: Privacy-preserving smart similarity search based on simhash over encrypted data in cloud computing. J. Int. Technol. 16(3), 453–460 (2015)
Fu, Z., Huang, F., Sun, X., Vasilakos, A.V., Yang, C.-N.: Enabling semantic search based on conceptual graphs over encrypted outsourced data. IEEE Trans. Serv. Comput. doi:10.1109/TSC.2016.2622697 (2016)
Fu, Z.J., Huang, F.X., Ren, K., Weng, J., Wang, C.: Privacy-preserving smart semantic search based on conceptual graphs over encrypted outsourced data. IEEE Trans. Inf. Forens. Secur. 12(8), 1874–1884 (2017)
Xia, Z.H., Wang, X.H., Sun, X.M., Wang, Q.: A secure and dynamic multi-keyword ranked search scheme over encrypted cloud data. IEEE Trans. Parallel Distrib. Syst. 27(2), 340–352 (2016)
Fu, Z.J., Wu, X.L., Guan, C.W., Sun, X.M., Ren, K.: Toward efficient multi-keyword fuzzy search over encrypted outsourced data with accuracy improvement. IEEE Trans. Inf. Forens. Secur. 11(12), 2706–2716 (2016)
Shen, J., Liu, D., Shen, J., Liu, Q., Sun, X.: A secure cloud-assisted urban data sharing framework for ubiquitous-cities. Pervasive Mob. Comput. doi:10.1016/j.pmcj.2017.03.013 (2017)
Fu, Z.J., Ren, K., Shu, J.G., Sun, X. M., Huang, F.X.: Enabling personalized search over encrypted outsourced data with efficiency improvement. IEEE Trans. Parallel Distrib. Syst. 27(9), 2546–2559 (2016)
IBM quantum computing platform (2016). http://research.ibm.com/ibm-q/qx/. Online accessed 12-April-2017
Acknowledgements
The authors would like to thank the anonymous reviewers and editor for their comments that improved the quality of this paper. This work is supported by the National Nature Science Foundation of China (Grant Nos. 61373131, 61502101 and 61672290), the Six Talent Peaks Project of Jiangsu Province (Grant No. 2015-XXRJ-013), Natural Science Foundation of Jiangsu Province (Grant No. BK20140823, BK20171458), Natural science Foundation for colleges and universities of Jiangsu Province (Grant No.16KJB520030), and the Priority Academic Program Development of Jiangsu Higher Education Institutions (PAPD).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, WJ., Chen, ZY., Ji, S. et al. Multi-party Semi-quantum Key Agreement with Delegating Quantum Computation. Int J Theor Phys 56, 3164–3174 (2017). https://doi.org/10.1007/s10773-017-3484-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-017-3484-6