Abstract
In the last decade, the risk evaluation and the investment decision are among the most prominent issues of efficient project management. Especially, the innovative financial sources could have some specific risk appetite due to the increasing return of investment. Hence, it is important to uncover the risk factors of fintech investments and investigate the possible impacts with an integrated approach to the strategic priorities of fintech lending. Accordingly, this study aims to analyze a unique risk set and the strategic priorities of fintech lending for clean energy projects. The most important contributions to the literature can be listed as to construct an impact-direction map of risk-based strategic priorities for fintech lending in clean energy projects and to measure the possible influences by using a hybrid decision making system with golden cut and bipolar q-rung orthopair fuzzy sets. The extension of multi stepwise weight assessment ratio analysis (M-SWARA) is applied for weighting the risk factors of fintech lending. The extension of elimination and choice translating reality (ELECTRE) is employed for constructing and ranking the risk-based strategic priorities for clean energy projects. In this process, data is obtained with the evaluation of three different decision makers. The main superiority of the proposed model by comparing with the previous models in the literature is that significant improvements are made to the classical SWARA method so that a new technique is created with the name of M-SWARA. Hence, the causality analysis between the criteria can also be performed in this proposed model. The findings demonstrate that security is the most critical risk factor for fintech lending system. Moreover, volume is found as the most critical risk-based strategy for fintech lending. In this context, fintech companies need to take some precautions to effectively manage the security risk. For this purpose, the main risks to information technologies need to be clearly identified. Next, control steps should be put for these risks to be managed properly. Furthermore, it has been determined that the most appropriate strategy to increase the success of the fintech lending system is to increase the number of financiers integrated into the system. Within this framework, the platform should be secure and profitable to persuade financiers.
Similar content being viewed by others
Introduction
The costs of clean energy projects are quite expensive compared to fossil fuels. Consequently, investors are becoming less interested in clean energy projects. This situation leads to a decrease in environmentally friendly energy projects. To prevent this problem, clean energy investors must be provided with cost advantages. A fintech lending system can significantly aid in resolving this problem. It is an alternative source of financing for commercial enterprises and consumers in need of capital. Therefore, fintech loan is a next-generation funding system that contributes to the expansion of investments in countries (Chao et al. 2022). Thanks to innovative financial products, investors will have easier access to the necessary financial resources. However, an additional critical issue in this context is the need to effectively analyze ongoing risks (Coşkun and Ibhagui 2022). Otherwise, questions may arise regarding the developed financial products, jeopardizing the projects’ sustainability. In summary, the types of risks in the fintech lending system must be clearly identified. Then, the appropriate measures must be implemented to effectively manage these risks.
The regulatory risk is crucial to this process. Countries can create new regulations for fintech applications (Hai et al. 2022). These new applications may increase the expenses of fintech companies, such as new taxes (Lorenzo and Arroyo 2022). In addition, the new regulations that will be implemented may make it more difficult to enter the sector. This case will diminish the motivation of investors who build the platform toward these practices. Another type of risk in the fintech system is information systems security risk. The fintech platform conducts all transactions over the internet. This increases the risk to security. Moreover, Internet-based attacks by third parties on the fintech platform can cause severe issues (Amarasekara et al. 2022). Because of the security problem in this system, the fintech company’s reputation will suffer significantly. Fintech companies will have difficulty acquiring new customers because of this situation, which will increase their anxiety (Chaudhry et al. 2022). Technology risk should also be considered in this framework (Liu et al. 2022). In the fintech system, where every application is submitted online, a technological glitch may result in customer dissatisfaction (Paramati et al. 2022).
An effective risk management is essential to increase the performance and effectiveness of fintech companies. In this context, fintech companies must take precautions against all types of risk. Meanwhile, each control measure against these risks will increase the companies’ expenses (Thakor et al. 2020). Therefore, it is extremely difficult for fintech companies to take comprehensive precautions against all types of risks. In other words, for fintech companies to become financially efficient, they may need to take some risks. Within this framework, a priority analysis must be conducted for these risk types (Knight and Wojcik 2020). Thanks to this circumstance, we can determine which risks pose the greatest threat to the efficiency of the fintech system. Thus, fintech companies will be better able to implement the risk management procedure, which in turn will not negatively affect the financial performance of these companies.
This study aims to evaluate significant risks and identify the strategic priorities of fintech lending for clean energy projects. Hence, the primary research question is to determine which risks play a more significant role in the effectiveness of the fintech platform. With a comprehensive literature review, this framework defines four distinct risks: regulatory, financial, security, and technological. Therefore, the main hypothesis of this study is that these four risks have a substantial effect on the performance of the fintech platform. This study develops a model to analyze a unique risk set and the strategic priorities of fintech lending for clean energy projects. The risk factors of fintech lending are examined with multi-stepwise weight assessment ratio analysis (M-SWARA) methodology. Furthermore, strategic priorities are evaluated using the elimination and choice translating reality (ELECTRE) method. In this process, the models are integrated with golden cut and bipolar q-rung orthopair fuzzy sets (q-ROFSs). In addition to this concern, all calculations are performed utilizing intuitionistic fuzzy sets (IFSs) and Pythagorean fuzzy sets (PFSs).
This study’s most important contributions to the literature are to construct an impact-direction map of risk-based strategic priorities for fintech lending in clean energy projects and to measure the possible influences using a hybrid decision-making system with golden cut and bipolar q-ROFSs. The analysis enables us to identify more important risks associated with fintech lending. These issues can be extremely useful for defining appropriate risk mitigation strategies for this system. Accordingly, the fintech platform’s effectiveness can be enhanced. Therefore, financial system of the countries can be developed significantly because of a more effective fintech system. Moreover, this situation positively affects the development of environmentally friendly energy projects.
The proposed model has some advantages by comparing with other ones. This study uses enhancements to the classic SWARA system to create a new method called M-SWARA. This new method identifies the impact-relation degrees of the factors. This circumstance provides an important superiority for this model by comparing the previous models in the literature. In other models in that considered SWARA, analytical hierarchy process, or analytical network process, only the weights of criteria can be determined. Due to the operation of the models, the causal relationship could not be identified in these models. Complex and crucial is the issue of evaluating the risk-based strategic priorities of fintech lending for clean energy projects. Thus, the risks can have a substantial impact on one another. For example, regulation risk can impact other risks, such as technological and information security risks. Therefore, to generate appropriate strategies, influenced and influential factors should be defined. Accordingly, M-SWARA methodology is more appropriate for this subject than the other approaches.
Furthermore, golden cut is considered by calculating the degrees in q-ROFSs to increase the appropriateness of the findings. These concerns contribute positively to the originality of the proposed model. Moreover, q-ROFSs consider a wider space by comparing with PFSs and IFSs (Kamacı and Petchimuthu 2022; Lin et al. 2020; 2021). Therefore, more comprehensive evaluations are possible (Li et al. 2020; Garg and Chen 2020; Akçetin and Kamacı 2022). Numerous complexities are involved in evaluating the risk-based strategic priorities of fintech lending for clean energy projects. In this framework, all risks are quite important, so their relative weights of importance are quite close. Due to this issue, identifying more significant risks is extremely challenging. To answer this question, a comprehensive examination must be conducted. Therefore, q-ROFSs are more appropriate for this topic than PFSs and IFSs, since a larger space can be considered during the analysis process (Sahu et al. 2021; Riaz and Fariz 2022). Therefore, these fuzzy sets enable more nuanced assessments.
In addition to q-ROFSs, PFSs and IFSs are used to test the validity of the findings alongside q-ROFSs. The effectiveness of the fintech lending system for clean energy projects is reliant on the identification of more crucial risks. In order to verify the consistency of the analysis results, it is essential to conduct a comparative evaluation using other fuzzy sets. Lastly, the compensation among the factors and the normalization procedure can be avoided by employing the ELECTRE method in the evaluation procedure (Nasution et al. 2020; Biluca et al. 2020). With the aid of this issue, the original data cannot be manipulated, thereby enhancing the applicability of the findings. This is not the case for other comparable techniques described in the literature, such as technique for order preference by similarity to ideal solution (TOPSIS) (Vojinović et al. 2022). In addition, when employing bipolar fuzzy sets, both negative and positive sets can be considered to obtain more comprehensive data by comparing with other fuzzy sets (Akram and Arshad 2020; Riaz and Tehrim, 2020; Shumaiza et al., 2019). Thus, it is possible to achieve more precise results (Akram and Al-Kenani 2020; Akram et al. 2019; Akram and Arshad 2019; Alghamdi et al. 2018).
In Sect. 2, the literature on risks in fintech lending is explained. Methods are described in detail in Sect. 3. The model’s results are presented in Sect. 4. In Sects. 5 and 6, conclusions and discussions are presented.
Literature for risks in fintech lending
This section contains a literature review on the risks associated with fintech lending systems. In evaluating the literature, the two most recent studies are considered. The studies are selected from the social science citation index-indexed journals. A unique paragraph is created for each type of the risk. Information systems security risk is an important type of risk that has an impact on the effectiveness of the fintech lending process. The fintech platform conducts all operations via the internet, which increases the platform’s information security risks (Hwang et al. 2021). As a result of these risks not being effectively managed, serious system problems may arise (Miyauchi 2021). Since the fintech company is responsible for the platform’s security, it is also responsible for any security-related issues that may arise (Hussain et al. 2021). Therefore, the problems that will arise due to the lack of security will result in significant losses for the fintech company (Maiti and Ghosh 2021). Within this framework, fintech firms must define all risks in detail (Meng et al. 2021). The next step is identifying and implementing the necessary control measures for these risks. Najib et al. (2021) investigated the influence of fintech systems on economic growth. They underlined that security conditions should be satisfied. Le (2021) evaluated the fintech system after COVID-19 period and identified that necessary actions should be taken to address security issues.
Technology risk is another important type of risk for the efficient development of fintech lending processes. The fintech lending process is conducted entirely online. Therefore, in order for this system to function properly, a robust technological infrastructure is required (Yusuf 2021). Without adequate technology, the fintech platform will be plagued by persistent bugs (Wang et al. 2022). Consequently, customer discontent will increase. This will result in the loss of customers for the fintech company (Chaudhry et al. 2022). Consequently, fintech firms must prioritize technological investment (Coffie et al. 2021). In this manner, the technological risk on the platform will be reduced to an absolute minimum. Setiawan et al. (2021) examined the Indonesian fintech system. For the effectiveness of the fintech lending system, they emphasized the need for necessary technological development. Sheng (2021) studied the performance of the fintech system for different country groups and determined the increase in customer dissatisfaction with technological problems in the system.
Financial risk is another type of risk that must be considered to improve the performance of the fintech lending system. Financial risk is the possibility that a fintech company will be unable to meet its obligations due to insufficient assets (Banna et al. 2021). Companies with funds on the fintech platform and those in need of funds are brought together on the internet (Zhao et al. 2022). In this context, the associated fund is made available as a loan to customers (Sakarya and Aksu 2021). The creditworthiness of the customers must be high (Al Janabi 2021). If the loans given to individuals with low creditworthiness are not repaid, the fintech company is exposed to financial risk. Liu (2021) examined methods for enhancing the efficacy of the fintech system. Therefore, fintech companies should conduct an effective customer credibility analysis. Katsiampa et al. (2022) evaluated the fintech system in China and determined that financial risks must be effectively managed to enhance the system.
Regulation risk should also be considered for a fintech lending system to be effective. This risk refers to the possibility that a change in laws and regulations will significantly affect the fintech company. Countries are able to enact new rules for the fintech system (Ebrahim et al. 2021). These new applications may also increase the expenses of fintech firms. In addition, new regulations may discourage investors from entering the market (Xu et al. 2021). For instance, the additional taxes imposed on fintech applications can substantially increase investor costs (Wojcik 2021). This situation endangers the sustainability of this system because it will negatively impact profitability (Omarova 2021). Omarini (2021) focused on the critical issues for enhancing the fintech system’s performance. To achieve this objective, fintech companies should primarily consider regulatory risks. Huibers (2021) examined the fintech credit system in the Netherland and pointed out that necessary actions should be taken regarding the regulation risks for the success of this system.
The results of the literature review indicate that the fintech lending system is subject to a variety of risks. Therefore, businesses must take precautions for each type of risk. However, the measures taken for each type of risk incur additional business expenses. Therefore, fintech companies cannot take comprehensive precautions against all potential threats. In this context, it is necessary to establish risk priorities for the fintech system to identify the most important issues. However, only a few studies in the literature have focused on the analysis with respect to the risks in the fintech lending system. Accordingly, the present study aims to assess significant risks and determine the strategic priorities of fintech lending for clean energy projects. By focusing on this topic, this study is believed to contribute to the existing body of knowledge.
Methodology
Bipolar q-ROFSs, SWARA and ELECTRE are detailed in this part.
Bipolar q-ROFSs with golden cut
Atanassov (1999) generated IFSs with membership and non-membership (MGS and NGS) degrees (\(\mu_{I} , n_{I} )\) in Eq. (1).
Equation (2) includes the requirement.
PFSs are introduced by Yager (2013) with degrees (\(\mu_{p} , n_{p} )\) as in Eq. (3).
Equation (4) states the requirement.
Also, q-ROFSs are developed by Yager (2016) with the extension of PFSs and IFSs as in Eq. (5).
The requirement is given in Eq. (6).
Zhang (1994) generated bipolar fuzzy sets to better reflect uncertainties. Equation (7) describes them, where \(\mu_{B}^{ + }\) states the satisfaction degree and satisfaction of the same element is shown by \(\mu_{B}^{ - }\).
Bipolar fuzzy sets can be adopted to IFSs, PFSs and q-ROFSs as in Eqs. (8–13).
where \(\mu_{{B_{I} }}^{ + } ,\mu_{{B_{P} }}^{ + } ,\mu_{{B_{Q} }}^{ + } , n_{{B_{I} }}^{ + } ,n_{{B_{P} }}^{ + } ,n_{{B_{Q} }}^{ + } :U \to \left[ {0,1} \right]\) and define the positive member and non-membership degrees. \(\mu_{{B_{I} }}^{ - } ,\mu_{{B_{P} }}^{ - } ,\mu_{{B_{Q} }}^{ - } , n_{{B_{I} }}^{ - } ,n_{{B_{P} }}^{ - } ,n_{{B_{Q} }}^{ - } :U \to \left[ { - 1,0} \right]\) and are the negative member and non-membership degrees for bipolar IFS, PFS, and q-ROFS respectively. For bipolar q-ROFS, \(q\) is defined as odd number. The details are illustrated in Fig. 1.
Operations are given in Eqs. (14–17).
\(B_{Q1} = \left\{ {\vartheta , \mu_{{B_{Q1} }}^{ + } \left( \vartheta \right),n_{{B_{Q1} }}^{ + } \left( \vartheta \right),\mu_{{B_{Q1} }}^{ - } \left( \vartheta \right),n_{{B_{Q1} }}^{ - } \left( \vartheta \right)/\vartheta \varepsilon U} \right\}\) and
Equations (18–20) are used for defuzzification.
This study considers golden cut (\(\varphi )\) to calculate the degrees. Equation (21) details this by denoting large and small quantities by a and b (Hu et al. 2020).
Equation (22) includes the arithmetical illustration.
Equation (23) states the degrees (\(\mu_{{G_{{B_{Q} }} }}\), \(n_{{G_{{B_{Q} }} }}\)).
Equations (24)-(26) include the adopted on golden cut to bipolar fuzzy sets.
M-SWARA method with bipolar q-ROFSs
Keršuliene et al. (2010) developed SWARA to compute the weights of the factors. In this method, the expert team can select the priorities. Equation (27) provides details about the relationship matrix.
Score functions and bipolar fuzzy sets are created. Equations (28–30) explain the values of comparative significance ratio (\(s_{j} )\), coefficient (\(k_{j} )\), recomputed weight (\(q_{j} )\), and weight (\(w_{j}\)).
Stable matrix is constructed by limiting and taking transpose of the matrix with the power of 2t + 1.
ELECTRE with bipolar q-ROFSs
Benayoun et al. (1966) developed ELECTRE by considering binary superiority comparisons to rank the items. Equation (31) includes the decision matrix.
This matrix is normalized by Eq. (32).
In this framework, if \(X_{ij}\) is equal to “0” for all i and j, then \(r_{ij}\) will be undefined because of the value of “0/0”. The values are weighted with Eq. (33).
Equations (34–39) explain the calculation of concordance and discordance (C and D) interval matrices.
Equations (40–47) include the creation of the concordance E, discordance F and aggregated G index matrixes.
In this scope, \(e_{ab}\), \(f_{ab}\), and \(g_{ab}\) refer to the sets of concordance, discordance, and aggregated index matrixes, respectively. Also, the net superior \(c_{a}\), inferior \(d_{a}\), and overall \(o_{a}\) values are computed by the following equations:
Analysis
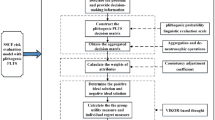
Clean energy projects have high initial cost that is accepted as the main drawback of these projects. Thus, innovative financial technology products play a crucial role in these endeavors. Consequently, the purpose of this study is to analyze a distinct risk set and the strategic priorities of fintech lending for clean energy projects. In order to analyze a unique risk set and the strategic priorities of fintech lending for clean energy projects, a model is developed in this study. This proposed model consists primarily of two distinct phases. First, the investor risks associated with fintech lending for clean energy projects are quantified. Second, the risk-based strategic priorities of fintech lending for clean energy projects are ranked. All phases are explained in Fig. 2.
Stage 1 Weighting the investors’ risks for the fintech lending in clean energy projects.
Step 1 Determine the investor risks for the fintech lending.
The investor risks associated with fintech lending are outlined in Table 1. These factors represent the dangers for businesses that develop fintech lending platforms to attract clean energy investors.
Regulation risk plays a significant role in the fintech lending system. It is defined as regulatory changes that negatively impact the fintech lending system. Financial risk indicates that fintech lending companies lack the liquid assets necessary to meet their obligations. Security risk refers to the possibility of unauthorized access to the information technology (IT) systems of the fintech platform. Technological risk provides information about the disruption of processes caused by a lack of technological expertise during research and development by fintech companies. Table 2 contains the scales and degrees utilized in the calculations, where PDG and NDG stand for positive and negative degrees, respectively.
Step 2 Collect the linguistic evaluations.
Table 3 displays evaluations of risks. For this purpose, an expert team is created with three different decision-makers. This group has a minimum of 24 years of experience in financial technology. They serve as senior executives for various fintech companies. They have worked in various departments of financial technology companies until now. Thus, they were able to gain a variety of experiences with financial technology applications. Therefore, these experts have sufficient knowledge to make an assessment on this subject.
Step 3 Determine the average values of positive and negative membership and non-membership degrees for the risks.
Average values are indicated in Table 4.
Step 4 Compute the score function values.
The values of score functions are calculated in Table 5.
Step 5 Compute sj, kj, qj, and wj values.
SWARA approach is extended in this study by the name of M-SWARA. Within this context, some improvements are made, such as computing sj, kj, qj, and wj values with the help of Eqs. (28–30). In this framework, \(k_{j}\) refers to the coefficient value, \(q_{j}\) shows the recalculated weight, \(s_{j}\) indicates the comparative importance rate and \(w_{j}\) represents the weights of the criteria. These values are computed to define the criteria relationship degrees. The specifics of these values are detailed in Table 6.
Step 6 Construct the relation matrix.
Relation matrix is generated in Table 7.
Step 7 Determine the stable matrix.
Stable matrix is developed for computing the weights of the items in Table 8.
Step 8 Compare weighting priorities.
The causal relationship among the risk factors is identified in Fig. 3.
Security is affected by three other risk factors. Additionally, security influences the financial realm. This calculation is also performed using IFSs and PFSs. Table 9 provides a summary of all conclusions.
The most important risk factor for a fintech lending system is security. Moreover, financial has the second-best rank for this issue. Financial and technological risks carry less weight. Figure 4 depicts the specifics of the risk weighting priorities.
Stage 2 Ranking the risk-based strategic priorities of fintech lending for clean energy projects.
Step 9 Collect the linguistic evaluations for the strategies.
In the second stage of the proposed model, the risk-based strategic priorities of fintech lending for clean energy projects are ranked based on their strategic importance. Table 10 displays a selection of strategic priorities based on risk.
Cost refers to the decrease in operational expenses as a result of fewer personnel and physical inputs. In addition, time includes the short-term matching of fund suppliers with fund demanders. Furthermore, volume means providing a wide set of finance providers for the different projects. The information presents the project data and the rating of investors clearly. Table 11 depicts evaluations of strategies.
Step 10 Define the average values for the strategies.
Table 12 includes average values.
Step 11 Compute the score functions.
Table 13 calculates the score function values of the strategies.
Step 12 Normalize the decision matrix.
Table 14 gives information about the normalized matrix.
Step 13 Compute the weighted decision matrix.
Table 15 presents the weighted matrix.
Step 14 Determine concordance and discordance interval matrixes.
Concordance and discordance interval matrixes (CCM and DCM) are created in Table 16.
Step 15 Compute aggregate index matrixes.
Aggregate index matrixes are demonstrated in Table 17.
Step 16 Calculate net superior, inferior, and overall values for ranking the strategies.
Net superior, inferior, and overall values are computed in Table 18 for ranking the strategies.
Ranking results are summarized in Table 19.
The most important risk-based strategy for fintech lending is found to be volume. Secondly, cost should also be a top priority in this case. Time and data play the least important role. Figure 5 explains the ranking results in detail.
The results are validated using TOPSIS, and a sensitivity analysis is performed by altering the weights of the criteria in four separate cases. The comparative results are presented in Table 20.
In a number of instances, the comparative results of the extended M-SWARA and TOPSIS are remarkably similar. Consequently, it is possible to conclude that the proposed model is valid and that the weighting results are consistent with the shifting order.
Discussions
Investors primarily take measures to mitigate the risk of unauthorized access to the IT systems of the fintech platform. The fintech lending system is conducted entirely online. Because all transactions on this platform are integrated over the internet network, there is a substantial IT risk associated with this system. Unavoidable IT risks will negatively impact the financing and functionality of fintech companies. These businesses must take the necessary cyber security precautions. Therefore, fintech companies will be accountable for any security issues that arise on this platform. This results in substantial financial losses for these companies. Meanwhile, fintech companies will suffer a significant loss of reputation due to this issue. Customers will not trust fintech companies with inefficient IT systems, thus threatening the continuity of fintech investments because it will result in customer defections.
In this context, fintech companies must take certain precautions to manage the security risk effectively. First, the primary threats to IT must be identified. In this context, all applications on the platform must be evaluated, and what risks exist and when they may manifest must. These risks must then be examined in depth. The probability of risk occurrence and their potential consequences should be determined during this step. Thus, it will be possible to rank the risks against one another. Next, control measures must be implemented to effectively manage these risks. These measures should be tailored to each type of risk. Finally, it must be determined if these measures effectively mitigate risks. In this context, security tests must be conducted for the implemented controls.
Numerous researchers have explained the significance of this situation in the literature. For instance, Iqbal et al. (2021), Ryu (2018), and Jagtiani and John (2018) concurred that fintech firms should take the necessary steps to effectively manage security risks. With the assistance of this issue, the risk management process can be conducted more efficiently, which positively impacts the companies' profitability. On the other hand, there are also studies in the literature with contradictory findings. For instance, Katsiampa et al. stated that the effectiveness of the fintech lending system should primarily take financial performance risks into account. In addition, Huibers (2021) highlighted the significance of regulation risk in this framework. It is determined that country-specific legal regulations should be considered in the design of this system.
It has been determined that increasing the number of financiers integrated into the system is the most effective strategy for boosting the success of the fintech lending system. This will allow for the ability to serve more customers. In this context, the fintech lending company must enter contracts with additional financiers. To convince these financiers, the platform must be safe, and the procedure must be profitable. Otherwise, investors will lack confidence in this platform and refuse to be integrated into the system. This will negatively impact the fintech system’s profitability. Similarly, Firmansyah and Anwar (2019), Acar and Çıtak (2019), and Sheikh et al. (2019) argued that reaching many financiers is essential for the effectiveness of fintech systems.
Conclusions
This study evaluates significant risks and identifies the strategic priorities of fintech lending for clean energy projects. It developed a model to analyze a distinct set of risks and the strategic priorities of fintech lending for clean energy projects. M-SWARA methodology is used to analyze the risk factors of fintech lending. Furthermore, strategic priorities are evaluated using the ELECTRE method. These models are integrated with golden cut and bipolar q-ROFSs during this procedure. In addition to this issue, IFSs and PFSs are used for all calculations. Findings reveal that three additional risk factors affect security. Additionally, security influences the financial realm. Meanwhile, security is identified as the greatest risk factor for fintech lending systems, followed by financial. Financial and technological risks have lower significance. Volume is found as the most critical risk-based strategy for fintech lending. Moreover, cost should also be a top priority in this regard. Time and data play the least important role. Therefore, these companies must take the necessary cyber security precautions. In this framework, these companies can establish a new risk management department, which aims to identify the most significant threats to IT. The likelihood of occurrence and potential consequences of the risks should then be determined. Based on these findings, the necessary precautions should be taken to effectively manage these risks.
Constructing an impact-direction map of risk-based strategic priorities for fintech lending in clean energy projects and measuring the possible influences using a hybrid decision-making system with golden cut and bipolar q-ROFS are the most significant contributions to the literature. In this study, all risks associated with the fintech platform are included in the scope of the review. These risks could be addressed in a specific manner in a subsequent study. For instance, it is believed that a more comprehensive examination of IT risks would be advantageous. This application can be implemented for all types of risk. Additionally, the model developed for this study can be enhanced. In this context, the reliability of the model’s results can be tested by considering various fuzzy numbers.
Availability of data and materials
Not applicable.
Abbreviations
- ELECTRE:
-
Elimination and choice translating reality
- SWARA:
-
The stepwise weight assessment ratio analysis
References
Acar O, Çıtak YE (2019) Fintech integration process suggestion for banks. Proc Comput Sci 158:971–978
Akçetin E, Kamacı H (2022) Three-valued soft set and its multi-criteria group decision making via TOPSIS and ELECTRE. Sci Iran 28(6):3719–3742
Akram M, Al-Kenani AN (2019) Multiple-attribute decision making ELECTRE II method under bipolar fuzzy model. Algorithms 12(11):226
Akram M, Al-Kenani AN (2020) Multi-criteria group decision-making for selection of green suppliers under bipolar fuzzy PROMETHEE process. Symmetry 12(1):77
Akram M, Arshad M (2019) A novel trapezoidal bipolar fuzzy TOPSIS method for group decision-making. Group Decis Negot 28(3):565–584
Akram M, Arshad M (2020) Bipolar fuzzy TOPSIS and bipolar fuzzy ELECTRE-I methods to diagnosis. Comput Appl Math 39(1):1–21
Akram M, Al-Kenani AN, Alcantud JCR (2019) Group decision-making based on the VIKOR method with trapezoidal bipolar fuzzy information. Symmetry 11(10):1313
Al Janabi MA (2021) Systematic market and asset liquidity risk processes for machine learning: robust modeling algorithms for multiple-assets portfolios. Internet of Things. Springer, Cham, pp 155–188
Alghamdi MA, Alshehri NO, Akram M (2018) Multi-criteria decision-making methods in bipolar fuzzy environment. Int J Fuzzy Syst 20(6):2057–2064
Amarasekara C, Iyke BN, Narayan PK (2022) The role of R&D and economic policy uncertainty in Sri Lanka’s economic growth. Financ Innov 8(1):1–19
Atanassov KT (1999) Intuitionistic fuzzy sets. In: Intuitionistic fuzzy sets, Physica, Heidelberg, pp 1–137
Banna H, Hassan MK, Rashid M (2021) Fintech-based financial inclusion and bank risk-taking: evidence from OIC countries. J Int Finan Markets Inst Money 75:101447
Benayoun R, Roy B, Sussman B (1966) ELECTRE: Une méthode pour guider le choix en présence de points de vue multiples. Note de travail 49:2–120
Biluca J, de Aguiar CR, Trojan F (2020) Sorting of suitable areas for disposal of construction and demolition waste using GIS and ELECTRE TRI. Waste Manage 114:307–320
Chao X, Ran Q, Chen J, Li T, Qian Q, Ergu D (2022) Regulatory technology (Reg-Tech) in financial stability supervision: taxonomy, key methods, applications and future directions. Int Rev Financ Anal 80:102023
Chaudhry SM, Ahmed R, Huynh TLD, Benjasak C (2022) Tail risk and systemic risk of finance and technology (FinTech) firms. Technol Forecast Soc Chang 174:121191
Coffie CPK, Hongjiang Z, Mensah IA, Kiconco R, Simon AEO (2021) Determinants of FinTech payment services diffusion by SMEs in Sub-Saharan Africa: evidence from Ghana. Inf Technol Dev 27(3):539–560
Coşkun S, Ibhagui O (2022) Technology shocks and covered interest parity deviations in emerging market economies. Empir Econ. https://doi.org/10.1007/s00181-021-02164-7
Ebrahim R, Kumaraswamy S, Abdulla Y (2021) FinTech in banks: opportunities and challenges. In: Innovative strategies for implementing fintech in banking, pp 100–109
Firmansyah EA, Anwar M (2019) Islamic financial technology (FINTECH): its challenges and prospect. In: Achieving and sustaining SDGs 2018 conference: harnessing the power of frontier technology to achieve the sustainable development goals (ASSDG 2018), Atlantis Press, pp 52–58
Garg H, Chen SM (2020) Multiattribute group decision making based on neutrality aggregation operators of q-rung orthopair fuzzy sets. Inf Sci 517:427–447
Hai B, Yin X, Xiong J, Chen J (2022) Could more innovation output bring better financial performance? The role of financial constraints. Financ Innov 8(1):1–26
Hu J, Liu D, Du C, Yan F, Lv C (2020) Intelligent energy management strategy of hybrid energy storage system for electric vehicle based on driving pattern recognition. Energy 198:117298
Huibers F (2021) Regulatory response to the rise of fintech credit in The Netherlands. J Risk Financ Manag 14(8):368
Hussain M, Nadeem MW, Iqbal S, Mehrban S, Fatima SN, Hakeem O, Mustafa G (2021) Security and privacy in FinTech: a policy enforcement framework. In: Research anthology on concepts, applications, and challenges of FinTech, IGI Global, pp 372–384
Hwang Y, Park S, Shin N (2021) Sustainable development of a mobile payment security environment using fintech solutions. Sustainability 13(15):8375
Iqbal S, Hussain M, Munir MU, Hussain Z, Mehrban S, Ashraf MA (2021) Crypto-currency: future of FinTech. In: Research anthology on blockchain technology in business, healthcare, education, and government, IGI Global, pp 1915–1924
Jagtiani J, John K (2018) Fintech: the impact on consumers and regulatory responses. J Econ Bus 100:1–6
Kamacı H, Petchimuthu S (2022) Some similarity measures for interval-valued bipolar q-rung orthopair fuzzy sets and their application to supplier evaluation and selection in supply chain management. Environ Dev Sustain 1–40. https://doi.org/10.1007/s10668-022-02130-y
Katsiampa P, McGuinness PB, Serbera JP, Zhao K (2022) The financial and prudential performance of Chinese banks and Fintech lenders in the era of digitalization. Rev Quant Finan Account. https://doi.org/10.1007/s11156-021-01033-9
Keršuliene V, Zavadskas EK, Turskis Z (2010) Selection of rational dispute resolution method by applying new step-wise weight assessment ratio analysis (SWARA). J Bus Econ Manag 11(2):243–258
Knight E, Wojcik D (2020) FinTech, economy and space: Introduction to the special issue. Environ Plan: Econ Space 52(8):1490–1497
Le MT (2021) Examining factors that boost intention and loyalty to use Fintech post-COVID-19 lockdown as a new normal behavior. Heliyon 7(8):e07821
Li Z, Wei G, Wang R, Wu J, Wei C, Wei Y (2020) EDAS method for multiple attribute group decision making under q-rung orthopair fuzzy environment. Technol Econ Dev Econ 26(1):86–102
Lin M, Huang C, Chen R, Fujita H, Wang X (2021) Directional correlation coefficient measures for Pythagorean fuzzy sets: their applications to medical diagnosis and cluster analysis. Complex Intell Syst 7(2):1025–1043
Liu H, Zhang Z, Zhang T (2022) Shale gas investment decision-making: Green and efficient development under market, technology and environment uncertainties. Appl Energy 306:118002
Liu C (2021) FinTech and its disruption to financial institutions. In: Research anthology on blockchain technology in business, healthcare, education, and government, IGI Global, pp 1679–1699
Lorenzo L, Arroyo J (2022) Analysis of the cryptocurrency market using different prototype-based clustering techniques. Financ Innov 8(1):1–46
Maiti M, Ghosh U (2021) Next generation Internet of Things in fintech ecosystem. IEEE Internet Things J. https://doi.org/10.1109/JIOT.2021.3063494
Meng S, He X, Tian X (2021) Research on Fintech development issues based on embedded cloud computing and big data analysis. Microprocess Microsyst 83:103977
Miyauchi Y (2021) New risks from Fintech (1) cyber security. In: The economics of Fintech, Springer, Singapore, pp 189–198
Najib M, Ermawati WJ, Fahma F, Endri E, Suhartanto D (2021) FinTech in the small food business and its relation with open innovation. J Open Innov: Technol Mark Complex 7(1):88
Nasution N, Febriadi B, Mahalisa G, Hijriana N, Rasyidan M, Sinaga DM, Raharjo MR (2020) Application of ELECTRE algorithm in skincare product selection. J Phys: Conf Ser 1471(1):012066
Omarini A (2021) FinTech and regulation: from start to boost: a new framework in the financial services industry. Where is the market going? too early to say. In: Disruptive technology in banking and finance, Palgrave Macmillan, Cham, pp 241–262
Omarova ST (2021) Fintech and the limits of financial regulation: a systemic perspective. In: Routledge handbook of financial technology and law, Routledge, pp 44–61
Paramati SR, Shahzad U, Doğan B (2022) The role of environmental technology for energy demand and energy efficiency: evidence from OECD countries. Renew Sustain Energy Rev 153:111735
Riaz M, Fariz HMA (2022) Picture fuzzy aggregation approach with application to third-party logistic provider selection process. Rep Mechan Eng 3(1):318–327
Riaz M, Tehrim ST (2020) Cubic bipolar fuzzy set with application to multi-criteria group decision making using geometric aggregation operators. Soft Comput 24(21):16111–16133
Ryu HS (2018) What makes users willing or hesitant to use Fintech?: the moderating effect of user type. Ind Manag Data Syst. https://doi.org/10.1108/IMDS-07-2017-0325
Sahu R, Dash SR, Das S (2021) Career selection of students using hybridized distance measure based on picture fuzzy set and rough set theory. Decis Mak: Appl Manag Eng 4(1):104–126
Sakarya Ş, Aksu M (2021) Fintech ecosystem in Turkey: an evaluation in terms of financial markets and financial stability. In: The impact of artificial intelligence on governance, economics and finance, Vol. I, Springer, Singapore, pp 11–31
Setiawan B, Nugraha DP, Irawan A, Nathan RJ, Zoltan Z (2021) User innovativeness and fintech adoption in indonesia. J Open Innov: Technol Mark Complex 7(3):188
Sheikh A, Ghanbarpour T, Gholamiangonabadi D (2019) A preliminary study of fintech industry: a two-stage clustering analysis for customer segmentation in the B2B setting. J Bus Bus Mark 26(2):197–207
Sheng T (2021) The effect of fintech on banks’ credit provision to SMEs: evidence from China. Financ Res Lett 39:101558
Thakor AV (2020) Fintech and banking: what do we know? J Financ Intermed 41:100833
Vojinović N, Stević Ž, Tanackov I (2022) A novel IMF SWARA-FDWGA-PESTEL analysis for assessment of healthcare system. Operat Res Eng Sci: Theor Appl 5(1):139–151
Wang X, Wu Z, Shen S (2022) Financial technology risk management and control in the big data era. In: International conference on cognitive based information processing and applications (CIPA 2021), Springer, Singapore, pp 368–374
Wójcik D (2021) Financial geography II: the impacts of FinTech–Financial sector and centres, regulation and stability, inclusion and governance. Prog Hum Geogr 45(4):878–889
Xu Y, Bao H, Zhang W, Zhang S (2021) Which financial earmarking policy is more effective in promoting FinTech innovation and regulation? Indu Manag Data Syst. https://doi.org/10.1108/IMDS-11-2020-0656
Yager RR (2016) Generalized orthopair fuzzy sets. IEEE Trans Fuzzy Syst 25(5):1222–2123
Yager RR (2013) Pythagorean fuzzy subsets. In: 2013 joint IFSA world congress and NAFIPS annual meeting (IFSA/NAFIPS), IEEE, pp 57–61
Yusuf TO (2021) The risks of islamic Fintech. In: Islamic FinTech, Palgrave Macmillan, Cham, pp 367–384
Zhang WR (1994) Bipolar fuzzy sets and relations: a computational framework for cognitive modeling and multiagent decision analysis. In: NAFIPS/IFIS/NASA'94. proceedings of the first international joint conference of the north american fuzzy information processing society biannual conference. The industrial fuzzy control and intellige, IEEE, pp 305–309
Zhao J, Li X, Yu CH, Chen S, Lee CC (2022) Riding the FinTech innovation wave: FinTech, patents and bank performance. J Int Money Financ 122:102552
Acknowledgements
Not applicable
Funding
This work was the Key Scientific Research Project of Colleges and Universities in Henan Province “Research on the key role of Investment in the Optimization and upgrading of Industrial structure in Henan Province” (22A790014) and National scientific research project cultivation fund project "Research on the Endogenous Mechanism, Performance Evaluation and Optimization Path of Science and Technology Finance Boosting China's High quality Economic Development" (XKPY-2022030).
Author information
Authors and Affiliations
Contributions
QW participated in the design of the study and performed the statistical analysis and conceived of the study and participated in its design and coordination and helped to draft the manuscript. XM participated in the design of the study and performed the statistical analysis and conceived of the study and participated in its design and coordination and helped to draft the manuscript. CW participated in the design of the study and performed the statistical analysis and conceived of the study and participated in its design and coordination and helped to draft the manuscript. HD participated in the design of the study and performed the statistical analysis. SY conceived of the study and participated in its design and coordination and helped to draft the manuscript. All authors read and approved the final manuscript.
Corresponding authors
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Wan, Q., Miao, X., Wang, C. et al. A hybrid decision support system with golden cut and bipolar q-ROFSs for evaluating the risk-based strategic priorities of fintech lending for clean energy projects. Financ Innov 9, 10 (2023). https://doi.org/10.1186/s40854-022-00406-w
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s40854-022-00406-w