Abstract
A multicarrier continuous-variable quantum key distribution (CVQKD) protocol uses Gaussian subcarrier quantum continuous variables (CVs) for the transmission. Here, we define an iterative error-minimizing secret key adaption method for multicarrier CVQKD. The proposed method allows for the parties to reach a given target secret key rate with minimized error rate through the Gaussian sub-channels by a sub-channel adaption procedure. The adaption algorithm iteratively determines the optimal transmit conditions to achieve the target secret key rate and the minimal error rate over the sub-channels. The solution requires no complex calculations or computational tools, allowing for easy implementation for experimental scenarios.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
Continuous-variable quantum key distribution (CVQKD) represents an important practical manifestation of the fundamentals of quantum mechanics [1, 2, 4,5,6, 11,12,13,14,15,16,17, 19,20,21, 37, 49, 50, 58, 59]. CVQKD does not require single-photon sources and detectors and can be implemented in an experimental scenario by standard devices [29,30,31, 39, 43,44,45,46, 48, 57, 60]. In a CVQKD setting, the information is carried by a continuous-variable quantum state that is defined in the phase space via the position and momentum quadratures. In an experimental CVQKD scenario, the CV quantum states have a Gaussian random distribution, and the quantum channel between the sender (Alice) and receiver (Bob) is also Gaussian, because the presence of an eavesdropper (Eve) adds a white Gaussian noise into the transmission [3, 7,8,9,10, 25, 26, 35, 40,41,42, 51, 54, 61,62,63].
The relevant performance attributes of experimental CVQKD (i.e., secret key rates, transmission distances, tolerable excess noise, etc.) still require significant improvements [6, 11,12,13,14, 17, 49, 58, 59]. The multicarrier CVQKD has been recently introduced through the adaptive quadrature division modulation (AMQD) [15]. The multicarrier CVQKD scheme injects several additional degrees of freedom into the transmission, which are not available for a standard (single carrier) CVQKD setting [15, 17, 18, 20,21,22,23,24, 27,28,29,30,31, 64, 65]. These results also made possible to utilize several significant phenomena for CVQKD that are unavailable in a standard CVQKD protocol [16,17,18, 21,22,23, 28, 29]. The secret key rates of multicarrier CVQKD confirm the multimode bounds of [7] (see the results on fundamental rate-loss scaling in quantum optical communications in [7]). Further information on the bounds of private quantum communications can be found in [8].
Here, a secret key adaption method is defined for multicarrier CVQKD. The proposed secret key adaption successively utilizes private rate curves for the sub-channels. The curves also define an adaption region for each sub-channel. Particularly, the adaption region provides a base for the iterative, private rate increment method utilized by our secret key rate adaption algorithm. The iterative sub-channel selection procedure depends on the actual target private rate and the noise levels of the sub-channels. We demonstrate the results through the framework of AMQD and also extend the results to the multiple-access multicarrier CVQKD.
The novel contributions of our manuscript are as follows:
- 1.
We define an iterative error-minimizing secret key adaption method for multicarrier CVQKD. The proposed secret key adaption algorithm iteratively determines the optimal transmit conditions at a given target secret key rate to realize minimal error transmission over the sub-channels.
- 2.
The proposed method allows for the parties to reach a given target secret key rate with minimized error rate through the Gaussian sub-channels by a sub-channel adaption procedure.
- 3.
At a given transmission rate of private classical information (private rate), the method determines and selects that sub-channel from the set of available sub-channels for the transmission of the quadratures which sub-channel provides a minimal error rate.
- 4.
The scheme provably yields a minimized error rate transmission for all sub-channels while achieving the selected target secret key rate.
- 5.
The solution requires no complex calculations or computational tools, allowing for easy implementation for experimental CVQKD scenarios.
This paper is organized as follows. In “Preliminaries”, preliminary findings are summarized. Section “Secret Key Rate Adaption with Minimized Error Rate” discusses the iterative secret key adaption scheme. Section “Secret Key Rate Adaption in Multiuser Multicarrier CVQKD” extends the results to a multiuser setting. In “Numerical Evidence”, a numerical evidence is proposed. Finally, Section “Conclusions” concludes the results. Supplemental material is included in the Appendix.
Preliminaries
The notations and basic terms of multicarrier CVQKD can be found in [15]. A brief summary is also included in Appendix 1.
Multiuser quadrature allocation (MQA)
In an MQA multiple access multicarrier CVQKD [20], a given user \(U_{k} ,k=0,\ldots ,K-1\), where K is the number of total users, is characterized via m subcarriers, formulating an \({\mathcal {M}}_{U_{k} } \) logical channel of \(U_{k} \),
where \({\mathcal {N}}_{U_{k} ,i} \) is the ith sub-channel of \({\mathcal {M}}_{U_{k} } \). For a detailed description of MQA for multicarrier CVQKD, see [20].
Private Classical Rate Curves
The secret key adaption method utilizes \(r+2\) rate curves for the sub-channels, defined via set
Specifically, for all sub-channels \({\mathcal {N}}_{i} \), \(i=0,\ldots ,l-1\) a given rate curve is selected from \({\mathcal {S}}\) (2) according to the sub-channel conditions.
In particular, a \(R\left( q\right) \) rate curve refers to the transmission rate of private classical information (private rate) over \({\mathcal {N}}_{i} \), with the relation
where \(R\left( q\right) \) is referred to as the target private rate at an \(R\left( q-1\right) \) actual private rate in an iteration procedure.
Assuming a reverse reconciliation [6], a given target private rate \(R\left( q\right) \) is defined as
where \(P\left( {\mathcal {N}}_{i} \right) \) is the private classical capacity of \({\mathcal {N}}_{i} \) [2, 34], and \(\chi _\mathrm{AB} \left( {\mathcal {N}}_{i} \right) \) and \(\chi _\mathrm{BE} \left( {\mathcal {N}}_{i} \right) \) are the Holevo information of Alice (transmitter) and Bob (receiver), and Bob and Eve (eavesdropper), respectively.
Secret Key Rate Adaption with Minimized Error Rate
Theorem 1
A given target secret key rate \(S^{\mathrm{*}} \left( {\mathcal {N}}\right) =\sum _{i=0}^{l-1}R_{i} \left( {\mathcal {N}}_{i} \right) \), where \(R_{i} \left( {\mathcal {N}}_{i} \right) \) is the private rate of sub-channel \({\mathcal {N}}_{i}\), can be achieved over the l sub-channels such that the error rate of all sub-channels is minimized.
Proof
The proof focuses on a single sub-channel \({\mathcal {N}}_{i} \) for the private transmission of a single quadrature component \(x_{i} \) (or \(p_{i} \)), which refers to a \(x_{i} \in {{\mathcal {N}}}\left( 0,\sigma _{\omega }^{2} \right) \) position or a \(p_{i} \in {{\mathcal {N}}}\left( 0,\sigma _{\omega }^{2} \right) \) momentum quadrature of the ith subcarrier, respectively.
Let
of the ith, \(i=0,\ldots ,l-1\) sub-channel \({\mathcal {N}}_{i} \).
Let \(R_{\min } \left( {\mathcal {N}}_{i} \right) \) and \(R_{\max } \left( {\mathcal {N}}_{i} \right) \) be the minimal and maximal private classical information transmission rates selected for \({\mathcal {N}}_{i} \). The private rates are referring to the transmission of a given quadrature \(x_{i} \).
These rate curves, \(R\left( q\right) >R\left( q-1\right) \), allow us to reach a target secret key rate \(S^{\mathrm{*}} \left( {\mathcal {N}}\right) \) over the sub-channels with a minimized error rate in a multicarrier CVQKD setting. Specifically, it requires a rigorously defined iterative condition on the selection of the sub-channels for each target rate \(R\left( q\right) \).
From \(R_{\min } \left( {\mathcal {N}}_{i} \right) \) and \(R_{\max } \left( {\mathcal {N}}_{i} \right) \), an adaption region \(\mathrm{A}\) can be characterized with r rate curves inside the region. Define r rate curves for the transmission of \(x_{i} \) in the region of \(\mathrm{A}\)
as
such that (3) holds.
Precisely, at a given private rate \(R\left( {\mathcal {N}}_{i} \right) \), (5) is referred to as \(\nu _{i} \left( R\left( {\mathcal {N}}_{i} \right) \right) \),
where \(\sigma _{R\left( {\mathcal {N}}_{i} \right) }^{2} \) is the noise variance of \({\mathcal {N}}_{i} \) at \(R\left( {\mathcal {N}}_{i} \right) \), while \(F\left( T\left( R\left( {\mathcal {N}}_{i} \right) \right) \right) \) is the transmittance coefficient of \({\mathcal {N}}_{i} \) at \(R\left( {\mathcal {N}}_{i} \right) \). Note that in function of (8), after a scaling the rate curves of (7) are almost parallel to \(R_{\min } \left( {\mathcal {N}}_{i} \right) \). By theory, at \(R\left( {\mathcal {N}}_{i} \right) =0\) (8) is directly defined from \(\sigma _{{\mathcal {N}}_{i} }^{2} \) is the noise variance and \(T_{i} \left( {\mathcal {N}}_{i} \right) \) is the transmittance coefficient of \({\mathcal {N}}_{i} \), as given in (5).
In function of \(\nu _{i} \left( R\left( {\mathcal {N}}_{i} \right) \right) \), the SNR of \({\mathcal {N}}_{i} \) at a given \(R\left( {\mathcal {N}}_{i} \right) \) is expressed as [55]
To step forward, we have to focus on the behavior of parameter \(\nu _{i} \left( \cdot \right) \) at an increased transmission rate.
Particularly, let \(\mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{i} \right) \) be the current private rate and \(R\left( {\mathcal {N}}_{i} \right) \) be the target private rate for a sub-channel \({\mathcal {N}}_{i} \), such that \(\mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{i} \right)<R\left( {\mathcal {N}}_{i} \right) <\tilde{R}\left( {\mathcal {N}}_{i} \right) \). Then, let \(\delta _{\nu _{i} } \left( R\left( {\mathcal {N}}_{i} \right) \right) \) identify the cumulative \(\nu _{i} \left( R\left( {\mathcal {N}}_{i} \right) \right) \) parameter of \({\mathcal {N}}_{i} \) at an increased (target) private rate \(R\left( {\mathcal {N}}_{i} \right) \), evaluated via the following iteration:
where \(\Delta _{\nu _{i} } \) identifies the difference of \(\nu _{i} \) at \(R\left( {\mathcal {N}}_{i} \right) \) and \(\tilde{R}\left( {\mathcal {N}}_{i} \right) \) as
the iteration (10) at no transmission, \(R\left( {\mathcal {N}}_{i} \right) =0\), identifies \(\nu _{i} \left( {\mathcal {N}}_{i} \right) \) as
while for any \(R\left( {\mathcal {N}}_{i} \right)>\mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{i} \right) >0\),
To conclude, from (10) follows that a rate increment from \(\mathop {R}\limits _{\smile }( {\mathcal {N}}_{i} ) \) to \(R\left( {\mathcal {N}}_{i} \right) \) also increases \(\delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{i} \right) \right) \) by \(\Delta _{\nu _{i} } \left( R\left( {\mathcal {N}}_{i} \right) ,\tilde{R}\left( {\mathcal {N}}_{i} \right) \right) \), thus for any \(R\left( {\mathcal {N}}_{i} \right) >\mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{i} \right) \), the following relation holds [55]:
Let us then define r private transmission curves in the adaption region \(\mathrm{A}\) of \({\mathcal {N}}_{i} \). The aim of the iterative secret key adaption scheme is to provide a rate increment in each step by selecting that sub-channel \({\mathcal {N}}_{i} \), for which (10) is minimal. Specifically, it is a convenient approach because this sub-channel provides the best condition for the transmission.
As we show, using this sub-channel, the increased rate \(\tilde{R}\) can be achieved with a minimized error rate, but at the same time, it keeps the target secret key rate. Therefore, applying the sub-channel selection procedure with respect to the iterative condition of (10), a desired target secret key rate can be achieved such that the transmission is adapted to not just the sub-channel conditions, but also to yield a minimized error rate for all sub-channels.
Applying (10) for a \(R_{\min } \left( {\mathcal {N}}_{i} \right) \) private rate is as follows. An \(R_{\min } \left( {\mathcal {N}}_{i} \right) \) target private rate over \({\mathcal {N}}_{i} \), \(\delta _{\nu _{i} } \left( R_{\min } \left( {\mathcal {N}}_{i} \right) \right) \) is yielded via \(\nu _{i} \left( {\mathcal {N}}_{i} \right) \) and \(\Delta _{\nu _{i} } \left( R_{\min } \left( {\mathcal {N}}_{i} \right) ,R\left( 0\right) \right) \) derived from \(R\left( 0\right) \in \mathrm{A}\) as
Applying (10) to the r rate curves \(R\left( q\right) \in \mathrm{A}\), \(q=0\ldots r-2\) at a target rate \(R\left( q\right) \) results in \(\delta _{\nu _{i} } \left( R\left( q\right) \right) \) as
Specifically, in each step for a given target \(R\left( q\right) \), the method selects that \({\mathcal {N}}_{i} \), for which (36) is minimal, because that sub-channel provides the best conditions. Thus, the secret key adaption is an iterative process and depends on the \(\delta _{\nu _{i} } \left( R\left( q-1\right) \right) \) parameter obtained at \(R\left( q-1\right) \) and on \(\Delta _{\nu _{i} } \left( R\left( q\right) ,R\left( q+1\right) \right) \).
In particular, for \(q=0\), (16) yields
where \(R\left( 1\right) \in \mathrm{A}\). While, for \(q=r-1\), (10) results in
where \(R\left( k\right) \in \mathrm{A}\), \(k=0\ldots r-2\). For \(R_{\max } \left( {\mathcal {N}}_{i} \right) \), by definition \(\delta _{\nu _{i} } \left( R_{\max } \left( {\mathcal {N}}_{i} \right) \right) =+\infty \) [55].
The distribution of a sample set \(\delta _{\nu _{i} } \left( R\left( q\right) \right) \) for m sub-channels, \(i=0,\ldots ,m-1\), in a low-SNR CVQKD scenario is illustrated in Fig. 1a. The SNR in Fig. 1b is derived from the \(\delta _{\nu _{i} } \left( R\left( q\right) \right) \) set of the m sub-channels as \(\mathrm{SNR}\left( \nu _{i} \left( R\left( q\right) \right) \right) =10\log _{10} \left( {1/ \left( \nu _{i} \left( R\left( q\right) \right) \right) } \right) \).
Next, we show that for an arbitrary target private rate \(R\left( {\mathcal {N}}_{i} \right) >0\), the iterative condition on \(\delta _{\nu _{i} } \left( R\left( {\mathcal {N}}_{i} \right) \right) \) (see (16)) provides a minimized error rate over the selected \({\mathcal {N}}_{i} \).
Let \({\mathcal {B}}\) be the bit error rate (BER), and let \({\mathcal {B}}\left( R\left( q\right) _{\delta _{\nu _{i} } \left( R\left( q-1\right) \right) } \right) \) refer to the bit error rate of \({\mathcal {N}}_{i} \) at target private rate \(R\left( q\right) \), at an actual rate \(R\left( q-1\right) \), and \(\delta _{\nu _{i} } \left( R\left( q-1\right) \right) \). Then, at a given \(R\left( q\right) \), selecting that \({\mathcal {N}}_{i} \), \(i=0,\ldots ,l-1\) from the total l, for which \(\delta _{\nu _{i} } \left( R\left( q-1\right) \right) \) is minimal, as
yields a minimized bit error rate at a given \(R\left( q\right) \) over the selected \({\mathcal {N}}_{i} \) as
where \({\mathcal {B}}\left( R_{\min } \left( {\mathcal {N}}_{i} \right) _{\delta _{\nu _{i} } \left( R\left( q-1\right) \right) } \right) \) is defined as
where function \({\mathcal {F}}\left( \cdot \right) \) is evaluated as
where \(\mathrm{SNR}\left( \nu _{i} \left( R\left( x\right) \right) \right) =10\log _{10} \left( {1/ \left( \nu _{i} \left( R\left( x\right) \right) \right) } \right) \), while \(\text {erfc}\left( \cdot \right) \) is the complementary error function
The aim of the error minimization procedure is to achieve (20) for all \(R\left( \cdot \right) \) via the selection of that \({\mathcal {N}}_{i} \) for which \(\delta _{\nu _{i} } \left( R\left( q-1\right) \right) \) is minimal.
Let \(R\left( k+1\right) _{\delta _{\nu _{i} } \left( R\left( k\right) \right) } \) refer to a private rate \(R\left( k+1\right) \) over at \(\delta _{\nu _{i} } \left( R\left( k\right) \right) \) with respect to the transmission of a single quadrature component \(x_{i} \) (or \(p_{i} \)).
First, we apply (19) to the minimal rate \(R_{\min } \left( {\mathcal {N}}_{i} \right) \) by the selection of that \({\mathcal {N}}_{i} \), for which \(\nu _{i} \left( {\mathcal {N}}_{i} \right) \) is minimal, thus
which yields
Similarly, at \(R\left( 0\right) \), that sub-channel is selected for the \(R\left( 0\right) \) rate transmission, for which \(\delta _{\nu _{i} } \left( R_{\min } \left( {\mathcal {N}}_{i} \right) \right) \) is minimal.
In particular, due to the iterative determination of \(\delta _{\nu _{i} } \left( R_{\min } \left( {\mathcal {N}}_{i} \right) \right) \), the corresponding \({\mathcal {B}}\left( R\left( 0\right) _{\xi \left( R_{\min } \left( {\mathcal {N}}_{i} \right) \right) } \right) \) is yielded as
Precisely, for \(R\left( q\right) \), \(q=1\ldots r-1\), therefore, in each step, that sub-channel selected for the transmission, for which \(\xi \left( R\left( q-1\right) \right) \) is minimal, ensures that the resulting \({\mathcal {B}}\left( R\left( q\right) _{\xi \left( R\left( q-1\right) \right) } \right) \) is evaluated as
Putting the pieces together, the utilization of (27) for \(q=1\) is as
while for \(q=r-1\),
and, finally, for \(R_{\max } \left( {\mathcal {N}}_{i} \right) _{\xi \left( R\left( r-1\right) \right) } \), the corresponding error rate is
The \({\mathcal {B}}\) bit error rates at private rates, \(R_{\min } \left( {\mathcal {N}}_{i} \right) ,R\left( 0\right) ,\ldots ,R_{\min } \left( r-1\right) ,R_{\max } \left( {\mathcal {N}}_{i} \right) \), for a given sub-channel \({\mathcal {N}}_{i} \) in function of \(\nu _{i} \) (low-SNR scenario) are summarized in Fig. 2 for the range \(\nu _{i} =\left[ 0.1,0.3\right] \) (Fig. 2a), and \(\nu _{i} =\left[ 0.3,0.9\right] \) (Fig. 2b).
The \({\mathcal {B}}\) bit error rates at \(R_{\min } \left( {\mathcal {N}}_{i} \right) ,R\left( 0\right) ,\ldots ,R\left( r-1\right) ,R_{\max } \left( {\mathcal {N}}_{i} \right) \) in a low-SNR scenario for a given sub-channel \({\mathcal {N}}_{i} \) at a \(\nu _{i} =\left[ 0.1,0.3\right] \) and b \(\nu _{i} =\left[ 0.3,0.9\right] \)
The iterative secret key adapting method with the error minimization is detailed in Algorithm 1.
The proof is concluded here. \(\square \)

The resulting \({{\mathcal {B}}}\) bit error rates of the secret key rate adapting method for a given sub-channel \({\mathcal {N}}_{i} \) in function of \(\nu _{i} \) are summarized in Fig. 3. Parameter \(\nu _{i} \) is scaled for the SNR with \(5\; {\mathrm{dB}}\) steps in the range of \(\left[ 15,-5\right] \) as \(\nu _{i} \left( R_{i} \left( x\right) \right) =10^{-{{\mathrm{SNR}}\left( \nu _{i} \left( R\left( x\right) \right) \right) / 10} }. \)
The \({\mathcal {B}}\) bit error rate of secret key adapting for a sub-channel \({\mathcal {N}}_{i} \) in function of \({{\nu }_{i}}\left( {{R}_{i}}\left( x \right) \right) ={{10}^{-{\text {SNR}\left( {{\nu }_{i}}\left( R\left( x \right) \right) \right) }/{10}\;}}\). The adaption is made via r rate curves \(R\left( q\right) \), \(q=0\ldots r-1\), \(R_{\min } \left( {\mathcal {N}}_{i} \right)<R\left( 0\right) \ldots<R\left( r-1\right) <R_{\max } \left( {\mathcal {N}}_{i} \right) \) in the \(\mathrm{A=}\left[ R_{\min } \left( {\mathcal {N}}_{i} \right) ,R_{\max } \left( {\mathcal {N}}_{i} \right) \right] \) adaption region (shaded area)
Secret Key Rate Adaption in Multiuser Multicarrier CVQKD
This section extends the results for a multiuser multicarrier CVQKD [20] scenario.
Lemma 1
The secret key adaption can be extended to a \(U_{k} ,k=0,\ldots , K-1\) multiuser setting, where K is the number of users, to achieve target secret key rate \(S^{\mathrm{*}} \left( {\mathcal {M}}_{U_{k} } \right) \) with minimized error rate over the m sub-channels of \({\mathcal {M}}_{U_{k}}\) of \(U_{k}\), for \(\forall k\).
Proof
The proof focuses on a given logical channel \({\mathcal {M}}_{U_{k} } =\left[ {\mathcal {N}}_{U_{k} ,0} ,\ldots ,{\mathcal {N}}_{U_{k} ,m-1} \right] ^\mathrm{T} \) of a user \(U_{k} \), where \({\mathcal {N}}_{U_{k} ,i} \), \(i=0,\ldots ,m-1\) is the ith sub-channel.
Let K be the number of transmit users and select a given \(U_{k} ,k=0,\ldots ,K-1\). Let \(S^{\mathrm{*}} \left( {\mathcal {M}}_{U_{k} } \right) \) be the target secret key rate of users over \({\mathcal {M}}_{U_{k} } \), and let \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) \) be the private rate of \({\mathcal {N}}_{U_{k} ,i} \). The steps of the extension are summarized as follows.
Let
where \(\sigma _{{\mathcal {N}}_{U_{k} ,i} }^{2} \) is the noise variance of \({\mathcal {N}}_{U_{k} ,i} \), while \(T_{i} \left( {\mathcal {N}}_{U_{k} ,i} \right) \) is the transmittance coefficient of \({\mathcal {N}}_{U_{k} ,i} \). At a given rate curve \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) >0\),
where \(\sigma _{R\left( {\mathcal {N}}_{U_{k} ,i} \right) }^{2} \) is the noise variance at \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) \), while \(T_{i} \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) is the transmittance coefficient of \({\mathcal {N}}_{U_{k} ,i} \) at \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) \), respectively. Apply the secret key rate adaption method over the set \({\mathcal {M}}_{U_{k} } \) of m \({\mathcal {N}}_{U_{k} ,i} \), sub-channels of \({\mathcal {M}}_{U_{k} } \), until
Apply the steps for all transmit users \(U_{k} \) for their \({\mathcal {M}}_{U_{k} } \) sets of m sub-channels. Therefore, one can utilize (27) at a given \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) =R_{i} \left( q\right) \), where \(R_{i} \left( q\right) \) refers to the \(R\left( q\right) \) curve of \({\mathcal {N}}_{U_{k} ,i} \), and from (12) follows \(\delta _{\nu _{i} } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) =0\right) =\nu _{i} \left( {\mathcal {N}}_{U_{k} ,i} \right) \), which yields the error rate for \({\mathcal {N}}_{U_{k} ,i} \) of \({\mathcal {M}}_{U_{k} } \) as
\(\square \)
Variance Adaption for an Equalized Error Rate
In this section, we propose a modulation variance adaption method to achieve an equally minimized error rate for the sub-channels of a given user. The results can be extended to an arbitrary number of users.
Theorem 2
For all \(U_{k} \), \(k=0,\ldots ,K-1\), the error rate of the \({\mathcal {N}}_{U_{k} ,i} \), \(i=0,\ldots ,m-1\) sub-channels of \({\mathcal {M}}_{U_{k}}\) of user \(U_{k}\) can be equally minimized via a \(\tilde{\sigma }_{\omega }^{2} =\sigma _{\omega }^{2} +\Delta _{\sigma _{\omega _{i} }^{2}}\) modulation variance correction, where \(\Delta _{\sigma _{\omega _{i} }^{2} } >0\).
Proof
Let
and \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) \) be the target private rate,
where \(R_{i} \left( q\right) \) refers to the \(R\left( q\right) \) curve of \({\mathcal {N}}_{U_{k} ,i} \), with relation to \(R_{i} \left( q-1\right) <R_{i} \left( q\right) \), and let us identify \(R_{i} \left( -1\right) =R_{\min } \left( {\mathcal {N}}_{U_{k} ,i} \right) \) and \(R_{i} \left( r\right) =R_{\max } \left( {\mathcal {N}}_{U_{k} ,i} \right) \).
Precisely, for a given \(U_{k} \) at \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) \), the minimal \(\delta _{\nu _{i} } ( \mathop {R}\limits _{\smile }( {\mathcal {N}}_{U_{k} ,i} ) ) \) parameter for the \({\mathcal {N}}_{U_{k} ,i} \), \(i=0,\ldots ,m-1\) sub-channels of the set \({\mathcal {M}}_{U_{k} } \)is evaluated as
Let \(\sigma _{\omega }^{2} \) refer to the input modulation variance of the ith subcarrier of \(U_{k} \). Specifically, using the expression of \(\xi _{U_{k} } \) in (37), the \(\sigma _{\omega }^{2} \) modulation variance of the ith subcarrier is corrected by \(\Delta _{\sigma _{\omega _{i} }^{2} } \) as
yielding a modulation variance increment
for the input of \({\mathcal {N}}_{U_{k} ,i} \).
In particular, using (39), the \(\varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) resulting \(\delta _{\nu _{i} } \) parameter for \({\mathcal {N}}_{U_{k} ,i} \) at a target rate \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) \) is, therefore,
from which the \(\Delta _{\mathrm{SNR}} \left( \varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \right) \) SNR increment of \({\mathcal {N}}_{U_{k} ,i} \) at a given \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) =R\left( q\right) \) is as
where \({\mathcal {F}}\left( \cdot \right) \) is specified in (22).
Therefore, the \({\mathcal {B}}( R\left( {\mathcal {N}}_{U_{k} ,i} \right) _{\xi _{U_{k} } } ) \) error rate for all \({\mathcal {N}}_{U_{k} ,i} \) at an arbitrary \(R\left( {\mathcal {N}}_{U_{k} ,i} \right) _{\delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) } \) is equally minimized by \(\xi _{U_{k} } \) via (21) as
The formula of (42) proves the minimal error rate at arbitrary \(S^{\mathrm{*}} \left( {\mathcal {M}}_{U_{k} } \right) \) over \({\mathcal {M}}_{U_{k} } \)for all \({\mathcal {N}}_{U_{k} ,i} \) sub-channels of \(U_{k} \).
Without loss of generality, the results can be extended for all K users to achieve minimized equalized error rate over all \({\mathcal {M}}_{U_{k} } \), \(k=0,\ldots ,K-1\) logical channels.
In a single user setting, e.g., \(K=1\), the method provides an equal, minimized error rate over the l sub-channels.
The proof is concluded here. \(\square \)
Numerical Evidence
This section proposes numerical evidence to demonstrate the results through a multiuser multicarrier CVQKD environment (AMQD-MQA [20]). The numerical evidence serves demonstration purposes.
Parameters
To demonstrate the results of Section 4.1, let \(U_{k} \) be a given user with m sub-channels. The parameters of the numerical evidence are summarized as follows.
The single-carrier inputs of user \(U_{k} \),
have a modulation variance of \(\sigma _{\omega _{0} }^{2} \) and formulate a d-dimensional input vector \(\mathbf {x}_{U_{k} } \).
The jth single carrier is dedicated to a single-carrier channel \({\mathcal {N}}_{U_{k} ,j} \). The single-carrier channel transmittance coefficient is depicted by \(T\left( {\mathcal {N}}_{U_{k} ,j} \right) \), \(j=0,\ldots ,d-1\), where d is the dimension of the input vector.
The single carriers are granulated into m subcarriers, where the ith subcarrier is
and has a modulation variance of \(\sigma _{\omega }^{2} \).
The m sub-channels,
formulate the \({\mathcal {M}}_{U_{k} } \) logical channel of user \(U_{k} \),
The \(\Delta _{x_{i} } \in {\mathcal {N}}\left( 0,\sigma _{{\mathcal {N}}_{U_{k} ,i} }^{2} \right) \) noise of \({\mathcal {N}}_{U_{k} ,i} \) is added to the subcarriers, where \(\sigma _{{\mathcal {N}}_{U_{k} ,i} }^{2} \) is the noise variance of \({\mathcal {N}}_{U_{k} ,i} \).
For a given sub-channel \({\mathcal {N}}_{U_{k} ,i} \) of \(U_{k} \), parameters \(\nu _{i} \left( {\mathcal {N}}_{U_{k} ,i} \right) \) and \(\nu _{i} \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) are evaluated via (31) and (32), such that the \(T\left( {\mathcal {N}}_{U_{k} ,i} \right) \) sub-channel transmittance coefficients are estimated in a pre-communication phase via the subcarrier spreading technique [30].
The \(\delta _{\nu _{i} } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) of \({\mathcal {N}}_{U_{k} ,i} \) parameters are determined from \(\nu _{i} \left( {\mathcal {N}}_{U_{k} ,i} \right) \) for all sub-channels via the iterative method of Theorem 2.
Modulation Variance Adaption
The analysis focuses on a low-SNR CVQKD scenario. An initial low-SNR set of \(\delta _{\nu _{i} } ( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) ) \), \(i=0,\ldots ,m-1\) of user \(U_{k} \) from a low-SNR scenario is illustrated in Fig. 4a. The minimum of the set is \(\xi _{U_{k} } = \min \limits _{\forall i\in {\mathcal {M}}_{U_{k} } } \delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \), from which the modulation variance correction for \({\mathcal {N}}_{U_{k} ,i} \) is \(\Delta _{\sigma _{\omega _{i} }^{2} } =\delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) -\xi _{U_{k} } \). The corresponding \(\Delta _{\sigma _{\omega _{i} }^{2} } \) (see (38)), \(i=0,\ldots ,m-1\) values determined from the \(\delta _{\nu _{i} } ( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) ) \) elements are depicted in Fig. 4b.
An initial low-SNR set of \(\delta _{\nu _{i} } ( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) ) \) of user \(U_{k} \), \(i=0,\ldots ,m-1\), \(m=1000\). a The minimum of set \(\delta _{\nu _{i} } ( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) ) \) (red solid line). b The resulting \(\Delta _{\sigma _{\omega _{i} }^{2} } \) variance correction, \(i=0,\ldots ,m-1\), \(m=1000\) determined from the \(\delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) elements
In a low-SNR setting due to the value range of \(\delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \), \(i=0,\ldots ,m-1\), the required \(\Delta _{\sigma _{\omega _{i} }^{2} } \) variance correction for the subcarriers is, therefore, negligible.
The \(x_{U_{k} ,i} \), \(i=0,\ldots ,m-1\) input quadratures of user \(U_{k} \) with a constant variance \(\sigma _{\omega }^{2} \) are illustrated in Fig. 5a. Applying the result of \(\Delta _{\sigma _{\omega _{i} }^{2} } \), the \(\tilde{x}_{U_{k} ,i} \), \(i=0,\ldots ,m-1\) input quadratures of user \(U_{k} \) at the \(\tilde{\sigma }_{\omega _{i} }^{2} =\sigma _{\omega }^{2} +\Delta _{\sigma _{\omega _{i} }^{2} } \) increased variance are depicted in Fig. 5b.
a The \(x_{U_{k} ,i} \), \(i=0,\ldots ,m-1\), \(m=1000\) input quadratures of user \(U_{k} \) at a constant variance \(\sigma _{\omega }^{2} =64\). b The \(\tilde{x}_{U_{k} ,i} \), \(i=0,\ldots ,m-1\), \(m=1000\) input quadratures of user \(U_{k} \) at increased variance \(\tilde{\sigma }_{\omega _{i} }^{2} =\sigma _{\omega }^{2} +\Delta _{\sigma _{\omega _{i} }^{2} } \)
The variance adaption of \(x_{U_{k} ,i} \), \(i=0,\ldots ,m-1\) requires only a moderate \(\Delta _{\sigma _{\omega _{i} }^{2} } \) for all subcarriers to achieve an equalized, significantly lower error rate through the sub-channels.
SNR Differences
The effects of the \(\Delta _{\sigma _{\omega _{i} }^{2} } \) variance correction and the resulting \(\varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) can be expressed in terms of the resulting SNR change.
The \(\Delta _{\mathrm{SNR}} \left( \tilde{\sigma }_{\omega _{i} }^{2} \right) =\mathrm{SNR}\left( \tilde{\sigma }_{\omega _{i} }^{2} \right) -\mathrm{SNR}\left( \sigma _{\omega }^{2} \right) \), \(i=0,\ldots ,m-1,\) SNR difference for the input quadratures \(\left\{ x_{U_{k} ,i} ,\tilde{x}_{U_{k} ,i} \right\} \) at \(\sigma _{\omega }^{2} \) and \(\tilde{\sigma }_{\omega _{i} }^{2} =\sigma _{\omega }^{2} +\Delta _{\sigma _{\omega _{i} }^{2} } \) is depicted in Fig. 6a. The \(\Delta _{\mathrm{SNR}} \left( \varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \right) \) SNR differences (see (41)) achieved at a given \(\varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \), \(i=0,\ldots ,m-1,\) are illustrated in Fig. 6b.
a The \(\Delta _{\mathrm{SNR}} \left( \tilde{\sigma }_{\omega _{i} }^{2} \right) \), \(i=0,\ldots ,m-1\), \(m=1000\) parameter for \(\left\{ x_{U_{k} ,i} ,\tilde{x}_{U_{k} ,i} \right\} \) at \(\sigma _{\omega }^{2} \) and \(\tilde{\sigma }_{\omega _{i} }^{2} \). b The \(\Delta _{\mathrm{SNR}} \left( \varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \right) \) parameter, \(i=0,\ldots ,m-1\), \(m=1000\)
The \(\Delta _{\mathrm{SNR}} \left( \tilde{\sigma }_{\omega _{i} }^{2} \right) \) input SNR difference results in an improved \(\Delta _{\mathrm{SNR}} \left( \varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \right) \) parameter via \(\varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) for all i.
Error Rate Minimization
The BER values for the initial low-SNR set and for the set of \(\varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \) are compared in Fig. 2. The BER of \({\mathcal {N}}_{U_{k} ,i} \) at the initial low-SNR set of \(\delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \), \(i=0,\ldots ,m-1,\) is illustrated in Fig. 7a. The BER of the m sub-channels \({\mathcal {N}}_{U_{k} ,i} \), \(i=0,\ldots ,m-1,\) at \(\varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) \), is depicted in Fig. 7b.
a The BER for the initial low-SNR set \(\delta _{\nu _{i} } \left( \mathop {R}\limits _{\smile }\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) ,i=0,\ldots ,m-1,m=1000\) (the minimum of the set is depicted by the green solid line). b The BER values for \(\varphi _{\delta _{\nu _{i} } } \left( R\left( {\mathcal {N}}_{U_{k} ,i} \right) \right) ,i=0,\ldots ,m-1,m=1000\)
As follows, as \(\xi _{U_{k} } \) is determined and applied in the iteration procedure, the resulting BER is equally minimized for all \({\mathcal {N}}_{U_{k} ,i} \) sub-channels of user \(U_{k} \).
Conclusions
We defined an iterative secret key adaption method for multicarrier CVQKD. The scheme provides a minimized error rate using the utilization of an adaptive private classical information transmission through the sub-channels. The private classical transmission is realized through pre-defined private rate curves, which characterize an adaption region for each sub-channel to find the best conditions for the transmission at a given private classical rate. The method allows us to reach a given target secret key rate with optimal transmit conditions and minimized error rate for all sub-channels.
Data Availability
This work does not have any experimental data.
Abbreviations
- AMQD:
-
Adaptive multicarrier quadrature division
- AWGN:
-
Additive white Gaussian noise
- BER:
-
Bit error rate
- CV:
-
Continuous variable
- CVQFT:
-
Continuous-variable quantum Fourier transform
- CVQKD:
-
Continuous-variable quantum key distribution
- DV:
-
Discrete variable
- FFT:
-
Fast Fourier transform
- ICVQFT:
-
Inverse CVQFT
- IFFT:
-
Inverse fast Fourier transform
- MQA:
-
Multiuser quadrature allocation
- QFT:
-
Quantum Fourier transform
- QKD:
-
Quantum key distribution
- SNR:
-
Signal-to-noise ratio
References
Adcock MRA, Hoyer P, Sanders BC. Limitations on continuous-variable quantum algorithms with Fourier transforms. N J Phys. 2009;11:103035.
Gyongyosi L, Imre S, Nguyen HV. A survey on quantum channel capacities. IEEE Commun Surv Tut. 2018;99:1. https://doi.org/10.1109/COMST.2017.2786748.
Biamonte J, et al. Quantum machine learning. Nature. 2017;549:195–202.
Garcia-Patron R, Cerf NJ. Unconditional optimality of gaussian attacks against continuous-variable quantum key distribution. Phys Rev Lett. 2006;97:190503.
Grosshans F. Collective attacks and unconditional security in continuous variable quantum key distribution. Phys Rev Lett. 2005;94:20504.
Grosshans F, Cerf NJ, Wenger J, Tualle-Brouri R, Grangier P. Virtual entanglement and reconciliation protocols for quantum cryptography with continuous variables. Quant Inf Comput. 2003;3:535–52.
Pirandola S, Laurenza R, Ottaviani C, Banchi L. Fundamental limits of repeaterless quantum communications. Nat Commun. 2017;8:15043. https://doi.org/10.1038/ncomms15043.
Pirandola S, Braunstein SL, Laurenza R, Ottaviani C, Cope TPW, Spedalieri G, Banchi L. Theory of channel simulation and bounds for private communication. Quantum Sci Technol. 2018;3:35009. https://doi.org/10.1088/2058-9565/aac394.
Pirandola S. Capacities of repeater-assisted quantum communications. 2016.arXiv:1601.00966.
Pirandola S. End-to-end capacities of a quantum communication network. Commun Phys. 2019;2:51.
Pirandola S, Braunstein SL, Lloyd S. Characterization of collective gaussian attacks and security of coherent-state quantum cryptography. Phys Rev Lett. 2008;101:200504.
Pirandola S, Garcia-Patron R, Braunstein SL, Lloyd S. Direct and reverse secret-key capacities of a quantum channel. Phys Rev Lett. 2009;102:50503.
Pirandola S, Mancini S, Lloyd S, Braunstein SL. Continuous-variable quantum cryptography using two-way quantum communication. Nat Phys. 2008;4:726–30.
Pirandola S, Serafini A, Lloyd S. Correlation matrices of two-mode bosonic systems. Phys Rev A. 2009;79:52327.
Gyongyosi L, Imre S. Adaptive multicarrier quadrature division modulation for long-distance continuous-variable quantum key distribution, In: Proc. SPIE 9123 Quantum Information and Computation XII, “912307;” from Conference Volume 9123 Quantum Information and Computation XII, Baltimore, Maryland, USA 2014. https://doi.org/10.1117/12.2050095.
Gyongyosi L, Imre S. Diversity space of multicarrier continuous-variable quantum key distribution. Int J Commun Syst. 2019. https://doi.org/10.1002/dac.4003.
Gyongyosi L, Imre S. Gaussian quadrature inference for multicarrier continuous-variable quantum key distribution. Quantum Stud Math Found. 2019. https://doi.org/10.1007/s40509-019-00183-9.
Gyongyosi L, Imre S. Statistical quadrature evolution by inference for multicarrier continuous-variable quantum key distribution. Quantum Stud Math Found. 2019. https://doi.org/10.1007/s40509-019-00202-9.
Gyongyosi L, Imre S. Geometrical analysis of physically allowed quantum cloning transformations for quantum cryptography. Inf Sci. 2014;285:1–23. https://doi.org/10.1016/j.ins.2014.07.010.
Gyongyosi L, Imre S. Multiple access multicarrier continuous-variable quantum key distribution. Chaos, Solitons Fractals. 2018;114:491–505. https://doi.org/10.1016/j.chaos.2018.07.006.
Gyongyosi L, Imre S. Secret key rate proof of multicarrier continuous-variable quantum key distribution. Int J Commun Syst. 2018. https://doi.org/10.1002/dac.3865.
Gyongyosi L. Singular value decomposition assisted multicarrier continuous-variable quantum key distribution. Theor Comput Sci. 2019. https://doi.org/10.1016/j.tcs.2019.07.029.
Gyongyosi L, Imre S. Secret key rates of free-space optical continuous-variable quantum key distribution. Int J Commun Syst. 2019. https://doi.org/10.1002/dac.4152.
Gyongyosi L, Imre S. Proceedings volume 8997 advances in photonics of quantum computing, memory, and communication “VII;” “89970C;”. 2014. https://doi.org/10.1117/12.2038532.
Gyongyosi L, Imre S. Long-distance continuous-variable quantum key distribution with advanced reconciliation of a gaussian modulation. In: Proceedings of SPIE Photonics West OPTO. 2013; 2013.
Gyongyosi L, Imre S. Low-dimensional reconciliation for continuous-variable quantum key distribution. Appl Sci. 2018. https://doi.org/10.3390/app8010087 (ISSN 2076-3417).
Gyongyosi L. Diversity extraction for multicarrier continuous-variable quantum key distribution. In: Proceedings of the 2016 24th European Signal Processing Conference (EUSIPCO 2016), 2016.
Gyongyosi L, Imre S. Eigenchannel decomposition for continuous-variable quantum key distribution. In: Proceedings Volume 9377 advances in photonics of quantum computing, memory, and communication “VIII;” 937711. 2015. https://doi.org/10.1117/12.2076532.
Gyongyosi L, Imre S. Singular layer transmission for continuous-variable quantum key distribution. In: IEEE Photonics Conference (IPC) 2014 IEEE. 2014. https://doi.org/10.1109/IPCon.2014.6995246.
Gyongyosi L, Imre S. Adaptive Gaussian quadrature detection for continuous-variable quantum key distribution. In: SPIE advances in photonics of quantum computing memory and communication IX, 2016.
Gyongyosi L, Imre S. Gaussian quadrature inference for multicarrier continuous-variable quantum key distribution. In: SPIE quantum information and computation XIV, 17–21 Apr 2016 Baltimore, Maryland, USA. 2016.
Gyongyosi L, Bacsardi L, Imre S. A survey on quantum key distribution. Infocommun J. 2019;XI(2):14–21.
Heinzel G, Rudiger A, Schilling R. Spectrum and spectral density estimation by the Discrete Fourier transform (DFT), including a comprehensive list of window functions and some new at-top windows. 2002. http://hdl.handle.net/11858/00-001M-0000-0013-557A-5.
Imre S, Gyongyosi L. Advanced quantum communications–an engineering approach. New Jersey: Wiley-IEEE Press; 2012 (ISBN-10: 1118002369 ISBN-13: 978-11180023).
Imre S, Balazs F. Quantum computing and communications—an engineering approach. Hoboken: Wiley; 2005 (ISBN 0-470-86902-X).
Jahromi OS. Multirate statistical signal processing. Berlin: Springer; 2007 (ISBN-10 1–4020-5316-9).
Jouguet P, Kunz-Jacques S, Leverrier A, Grangier P, Diamanti E. Experimental demonstration of long-distance continuous-variable quantum key distribution. 2012. arXiv:1210.6216v1.
Kay S. Fundamentals of statistical signal processing, vol. I-III. Upper Saddle River: Prentice Hall; 2013 (ISBN-13: 978-0133457117).
Kiktenko EO, Pozhar NO, Anufriev MN, Trushechkin AS, Yunusov RR, Kurochkin YV, Lvovsky AI, Fedorov AK. Quantum-secured blockchain. Quantum Sci Technol. 2018;3:35004.
Kimble HJ. The quantum Internet. Nature. 2008;453:1023–30. https://doi.org/10.1038/nature07127.
Laudenbach F, Pacher C, Fred Fung C-H, Poppe A, Peev M, Schrenk B, Hentschel M, Walther P, Hubel H. Continuous-variable quantum key distribution with gaussian modulation—the theory of practical implementations. Adv Quantum Technol. 2018;1(1):1–37.
Laurenza R, Pirandola S. General bounds for sender-receiver capacities in multipoint quantum communications. Phys Rev A. 2017;96:32318.
Lloyd S. Capacity of the noisy quantum channel. Phys Rev A. 1997;55:1613–22.
Lloyd S, Mohseni M, Rebentrost, P. Quantum algorithms for supervised and unsupervised machine learning. 2013. arXiv:1307.0411.
Lloyd S, Mohseni M, Rebentrost P. Quantum principal component analysis. Nat Phys. 2014;10:631.
Lloyd S, Shapiro JH, Wong FNC, Kumar P, Shahriar SM, Yuen HP. Infrastructure for the quantum Internet. ACM SIGCOMM Comput Commun Rev. 2004;34:9–20.
Middlet, D. An introduction to statistical communication theory: an IEEE Press Classic Reissue, Hardcover, IEEE, ISBN-10: 780311787 ISBN-13: 978-0780311787 1960.
Muralidharan S, Kim J, Lutkenhaus N, Lukin MD, Jiang L. Ultrafast and fault-tolerant quantum communication across long distances. Phys Rev Lett. 2014;112:250501.
Navascues M, Acin A. Security bounds for continuous variables quantum key distribution. Phys Rev Lett. 2005;94:20505.
Navascues M, Grosshans F, Acin A. Optimality of Gaussian attacks in continuous-variable quantum cryptography. Phys Rev Lett. 2006;97:190502.
Petz D. Quantum information theory and quantum statistics. Heidelberg: Springer-Verlag; 2008 Hiv: 6.
Press WH, Teukolsky SA, Vetterling WT, Flannery BP. Numerical recipes in C: the art of scientific computing. Cambridge: Cambridge University Press; 1993 ISBN : 0-521-43108-5.
Shieh W, Djordjevic I. OFDM for optical communications. Amsterdam: Elsevier; 2010. p. 456 (Hardcover ISBN: 9780123748799, eBook ISBN: 9780080952062).
Shor PW. Scheme for reducing decoherence in quantum computer memory. Phys Rev A. 1995;52:R2493–6.
Rohling H, Fellenberg C. Successive bit loading concept. OFDM concepts for future communication systems. Berlin: Springer; 2011.
Tse D, Viswanath P. Fundamentals of wireless communication. Cambridge: Cambridge University Press; 2005 ISBN-13: 978-0521845274, ISBN-10: 521845270.
Van Meter R. Quantum networking. Hoboken: Wiley; 2014. p. 368 ISBN-13: 978-1848215375, ISBN-10: 9781848215375.
Weedbrook C, Pirandola S, Lloyd S, Ralph T. Quantum cryptography approaching the classical limit. Phys Rev Lett. 2010;105:110501.
Weedbrook C, Pirandola S, Garcia-Patron R, Cerf NJ, Ralph T, Shapiro J, Lloyd S. Gaussian quantum information. Rev Mod Phys. 2012;84:621.
Gyongyosi L, Imre S. Decentralized base-graph routing for the quantum internet. Phys Rev A Am Phys Soc. 2018. https://doi.org/10.1103/PhysRevA.98.022310.
Gyongyosi L, Imre S. Entanglement-gradient routing for quantum networks. Sci Rep. 2017. https://doi.org/10.1038/s41598-017-14394-w.
Gyongyosi L, Imre S. Entanglement availability differentiation service for the quantum internet. Sci Rep Nat. 2018. https://doi.org/10.1038/s41598-018-28801-3.
Bacsardi L. On the way to quantum-based satellite communication. IEEE Commun Mag. 2013;51(08):50–5.
Zhang H, Mao Y, Huang D, Li J, Zhang L, Guo Y. Security analysis of orthogonal-frequency-division-multiplexing-based continuous-variable quantum key distribution with imperfect modulation. Phys Rev A. 2018;97:52328.
Zhao W, Liao Q, Huang D, et al. Performance analysis of the satellite-to-ground continuous-variable quantum key distribution with orthogonal frequency division multiplexed modulation. Quant Inf Proc. 2019;18:39. https://doi.org/10.1007/s11128-018-2147-8.
Acknowledgements
Open access funding provided by Budapest University of Technology and Economics (BME). The research reported in this paper has been supported by the National Research, Development and Innovation Fund (TUDFO/51757/2019-ITM, Thematic Excellence Program). This work was partially supported by the National Research Development and Innovation Office of Hungary (Project No. 2017-1.2.1-NKP-2017-00001), by the Hungarian Scientific Research Fund—OTKA K-112125 and in part by the BME Artificial Intelligence FIKP grant of EMMI (BME FIKP-MI/SC).
Funding
We have no competing financial interests.
Author information
Authors and Affiliations
Contributions
LGY designed the protocol and wrote the manuscript. LGY and SI analyzed the results. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of Interest
We have no competing interests.
Ethical Approval
This work did not involve any active collection of human data.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Parts of this work were presented in [15].
Appendix
Appendix
Multicarrier CVQKD
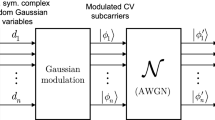
First, we summarize the basic notations of AMQD [15]. The following description assumes a single user, and the use of n Gaussian sub-channels \({\mathcal {N}}_{i} \) for the transmission of the subcarriers, from which only l sub-channels will carry valuable information.
In the single-carrier modulation scheme, the jth input single-carrier state \({\left| \varphi _{j} \right\rangle } ={\left| x_{j} +\mathrm{i}p_{j} \right\rangle } \) is a Gaussian state in the phase space \({\mathcal {S}}\), with i.i.d. Gaussian random position and momentum quadratures \(x_{j} \in {\mathcal {N}}\left( 0,\sigma _{\omega _{0} }^{2} \right) \), \(p_{j} \in {\mathcal {N}}\left( 0,\sigma _{\omega _{0} }^{2} \right) \), where \(\sigma _{\omega _{0} }^{2} \) is the modulation variance of the quadratures. (For simplicity, \(\sigma _{\omega _{0} }^{2} \) is referred to as the single-carrier modulation variance, throughout.) Particularly, this Gaussian single carrier is transmitted through a Gaussian quantum channel \({\mathcal {N}}\). In the multicarrier scenario, the information is carried by Gaussian subcarrier CVs, \({\left| \phi _{i} \right\rangle } ={\left| x_{i} +\mathrm{i}p_{i} \right\rangle } \), \(x_{i} \in {\mathcal {N}}\left( 0,\sigma _{\omega }^{2} \right) \), \(p_{i} \in {\mathcal {N}}\left( 0,\sigma _{\omega }^{2} \right) \), where \(\sigma _{\omega }^{2} \) is the modulation variance of the subcarrier quadratures, which are transmitted through a noisy Gaussian sub-channel \({\mathcal {N}}_{i} \). Each \({\mathcal {N}}_{i} \) Gaussian sub-channel is dedicated for the transmission of one Gaussian subcarrier CV from the n subcarrier CVs. (Note: index i refers to the subcarriers, while index j to the single carriers throughout the manuscript.) The single-carrier state \({\left| \varphi _{j} \right\rangle } \) in the phase space \({\mathcal {S}}\) can be modeled as a zero-mean, circular symmetric complex Gaussian random variable \(z_{j} \in {\mathcal {CN}}\left( 0,\sigma _{\omega _{z_{j} } }^{2} \right) \), with variance \(\sigma _{\omega _{z_{j} } }^{2} ={\mathbb {E}}\left[ \left| z_{j} \right| ^{2} \right] \), and with i.i.d. real and imaginary zero-mean Gaussian random components \(\text {Re}\left( z_{j} \right) \in {\mathcal {N}}\left( 0,\sigma _{\omega _{0} }^{2} \right) \), \(\text {Im}\left( z_{j} \right) \in {\mathcal {N}}\left( 0,\sigma _{\omega _{0} }^{2} \right) \).
In the multicarrier CVQKD scenario, let n be the number of Alice’s input single-carrier Gaussian states. The n input coherent states are modeled by an n-dimensional, zero-mean, circular symmetric complex random Gaussian vector
where each \(z_{j} \) can be modeled as a zero-mean, circular symmetric complex Gaussian random variable
Specifically, the real and imaginary variables (i.e., the position and momentum quadratures) formulate n-dimensional real Gaussian random vectors, \(\mathbf {x}={{\left( {{x}_{1}},\ldots , {{x}_{n}} \right) }^\mathrm{T}}\) and \(\mathbf {p}={{\left( {{p}_{1}},\ldots , {{p}_{n}} \right) }^\mathrm{T}}\), with zero-mean Gaussian random variables with densities \(f(x_{j})\) and \(f(p_{j})\) as
where \({{\mathbf {K}}_{\mathbf {z}}}\) is the \(n\times n\) Hermitian covariance matrix of \(\mathbf {z}\):
while \({{\mathbf {z}}^{\dagger }}\) is the adjoint of \(\mathbf {z}\).
For vector \(\mathbf {z}\),
holds, and
for any \(\gamma \in \left[ 0,2\pi \right] \). The density of \(\mathbf {z}\) is as follows (if \({{\mathbf {K}}_{\mathbf {z}}}\) is invertible):
A n-dimensional Gaussian random vector is expressed as \(\mathbf {x}=\mathbf {As}\), where \(\mathbf {A}\) is an (invertible) linear transform from \({\mathbb {R}}^{n} \) to \({\mathbb {R}}^{n} \), and \(\mathbf {s}\) is an n-dimensional standard Gaussian random vector \({\mathcal {N}}\left( 0,1\right) _{n} \). This vector is characterized by its covariance matrix \({{\mathbf {K}}_{\mathbf {x}}}=\mathbb {E}\left[ \mathbf {x}{{\mathbf {x}}^\mathrm{T}} \right] =\mathbf {A}{{\mathbf {A}}^\mathrm{T}} \), and has density
The Fourier transformation \(F\left( \cdot \right) \) of the n-dimensional Gaussian random vector \(\mathbf {v}=\left( v_{1}, \ldots , v_{n} \right) ^\mathrm{T} \) results in the n-dimensional Gaussian random vector \(\mathbf {m}={{\left( {{m}_{1}},\ldots , {{m}_{n}} \right) }^{T}}\), as:
In the first step of AMQD, Alice applies the inverse FFT (fast Fourier transform) operation to vector \(\mathbf {z}\) (see (47)), which results in an n-dimensional zero-mean, circular symmetric complex Gaussian random vector \(\mathbf {d}\), \(\mathbf {d}\in \mathcal {CN}\left( 0,{{\mathbf {K}}_{\mathbf {d}}} \right) \), \(\mathbf {d}={{\left( {{d}_{1}},\ldots , {{d}_{n}} \right) }^\mathrm{T}}\), as
where
where \(\sigma _{\omega _{d_{i} } }^{2} ={\mathbb {E}}\left[ \left| d_{i} \right| ^{2} \right] \) and the position and momentum quadratures of \({\left| \phi _{i} \right\rangle } \) are i.i.d. Gaussian random variables
where \({{\mathbf {K}}_{\mathbf {d}}}=\mathbb {E}\left[ \mathbf {d}{{\mathbf {d}}^{\dagger }} \right] \), \(\mathbb {E}\left[ \mathbf {d} \right] =\mathbb {E}\left[ {{e}^{i\gamma }}\mathbf {d} \right] =\mathbb {E}{{e}^{i\gamma }}\left[ \mathbf {d} \right] \), and \(\mathbb {E}\left[ \mathbf {d}{{\mathbf {d}}^{T}} \right] =\mathbb {E}\left[ {{e}^{i\gamma }}\mathbf {d}{{\left( {{e}^{i\gamma }}\mathbf {d} \right) }^\mathrm{T}} \right] =\mathbb {E}{{e}^{i2\gamma }}\left[ \mathbf {d}{{\mathbf {d}}^\mathrm{T}} \right] \), for any \(\gamma \in \left[ 0,2\pi \right] \).
The \(\mathbf {T}\left( \mathcal {N} \right) \) transmittance vector of \({\mathcal {N}}\) in the multicarrier transmission is
where
is a complex variable, which quantifies the position and momentum quadrature transmission (i.e., gain) of the ith Gaussian sub-channel \({\mathcal {N}}_{i} \), in the phase space \({\mathcal {S}}\), with real and imaginary parts
and
Particularly, the \(T_{i} \left( {\mathcal {N}}_{i} \right) \) variable has the squared magnitude of
where
The Fourier-transformed transmittance of the ith sub-channel \({\mathcal {N}}_{i} \) (resulted from CVQFT operation at Bob) is denoted by
The n-dimensional zero-mean, circular symmetric complex Gaussian noise vector \(\Delta \in {\mathcal {CN}}\left( 0,\sigma _{\Delta }^{2} \right) _{n} \) of the quantum channel \({\mathcal {N}}\), is evaluated as
where
with independent, zero-mean Gaussian random components
and
with variance \(\sigma _{{\mathcal {N}}_{i} }^{2} \), for each \(\Delta _{i} \) of a Gaussian sub-channel \({\mathcal {N}}_{i} \), which identifies the Gaussian noise of the ith sub-channel \({\mathcal {N}}_{i} \) on the quadrature components in the phase space \({\mathcal {S}}\).
The CVQFT-transformed noise vector can be rewritten as
with independent components \(F\left( \Delta _{x_{i} } \right) \in {\mathcal {N}}\left( 0,\sigma _{F\left( {\mathcal {N}}_{i} \right) }^{2} \right) \) and \(F\left( \Delta _{p_{i} } \right) \in {\mathcal {N}}\left( 0,\sigma _{F\left( {\mathcal {N}}_{i} \right) }^{2} \right) \) on the quadratures, for each \(F\left( \Delta _{i} \right) \). It also defines an n-dimensional zero-mean, circular symmetric complex Gaussian random vector \(F\left( \Delta \right) \in {\mathcal {CN}}\left( 0,\mathbf {K}_{F\left( \Delta \right) } \right) \) with a covariance matrix
where \(\mathbf {K}_{F\left( \Delta \right) } =\mathbf {K}_{\Delta } \), by theory. At a constant subcarrier modulation variance \(\sigma _{\omega _{i} }^{2} \) for the n Gaussian subcarrier CVs, the corresponding relation is
where \(\sigma _{\omega _{i} }^{2} \) is the modulation variance of the quadratures of the subcarrier \({\left| \phi _{i} \right\rangle } \) transmitted by sub-channel \({\mathcal {N}}_{i} \). Assuming l good Gaussian sub-channels from the n with constant quadrature modulation variance \(\sigma _{\omega _{i} }^{2} \), where \(\sigma _{\omega _{i} }^{2} =0\) for the ith unused sub-channel
In particular, from the relation of (73), for the transmittance parameters the following relation follows at a given modulation variance \(\sigma _{\omega _{0} }^{2} \), precisely,
where \(\left| T\left( {\mathcal {N}}\right) \right| ^{2} \) is the transmittance of \({\mathcal {N}}\) in a single-carrier scenario, and
For the method of the determination of these l Gaussian sub-channels, see [15]. Alice’s ith Gaussian subcarrier is expressed as
A.2 Notations
The notations of the manuscript are summarized in Table 1.
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Gyongyosi, L., Imre, S. Secret Key Rate Adaption for Multicarrier Continuous-Variable Quantum Key Distribution. SN COMPUT. SCI. 1, 33 (2020). https://doi.org/10.1007/s42979-019-0027-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-019-0027-7