Abstract
This paper studies the problem of differentially private bipartite output consensus in continuous-time heterogeneous multi-agent systems (MASs) characterized by antagonistic interactions. A novel hybrid privacy-preserving event-triggered impulsive consensus protocol is introduced to protect the agent’s initial information from disclosure, which involves a discrete-time information transmission based on an event-triggering mechanism. Using stochastic Lyapunov method, sufficient conditions have been obtained to achieve mean square bipartite output consensus with a guaranteed level of privacy. Furthermore, the differential privacy of competitive agent pairs is exclusively secured by the proposed control scheme by injecting Laplace noise. The protocol also effectively prevents Zeno behavior by imposing a lower bound for impulsive intervals under all event-triggered conditions. A simulation example is provided to validate the effectiveness of the theoretical result.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
Introduction
With recent advancements in networking technology and wireless communication, the consensus problem of multi-agent systems (MASs) has received tremendous research interest from various fields, such as mobile-robot systems [1], wide-area networks [2], autonomous underwater vehicles [3], etc. In practice, agents often exhibit both antagonistic and cooperative relationships in many multi-agent networks, which can be represented in terms of signed graphs. In this case, the problem of bipartite consensus was introduced as an important issue in the field of MASs, and several research works have been obtained on this topic [4, 5]. It should be noted that previous results on bipartite consensus have focused on homogeneous agents. However, the dynamics of real-world systems are often different, and the bipartite output consensus problem of heterogeneous MASs deserves further attention. In this regard, a unified framework for bipartite output synchronization of linear heterogeneous agents was investigated in [6]. In [7], the bipartite output consensus of heterogeneous linear MASs was studied through the integration of event-triggered and adaptive control strategies, under both fixed and switching topologies. Further, to improve the convergence rate, finite-time event-triggered bipartite output consensus for heterogeneous linear MASs was discussed in [8]. In [9], a distributed reduced-dimensional observer was designed to estimate leader states and system matrices, and an edge-based adaptive protocol was proposed to ensure bipartite output synchronization. A bipartite output formation control problem was considered in [10], where an adaptive distributed dynamic event-triggered controller was proposed without requiring any global information about the network. The above research has made great contributions to the development of bipartite output consensus, but they do not take into account the issue of privacy leakage within these problems.
Information sharing among agents to reach agreement throughout the network is an essential element in solving consensus problems. However, directly sharing agent states can compromise privacy and lead to the leakage of sensitive information. As a result, privacy-preserving problems have become crucial in consensus algorithm design. In recent years, several techniques, including homomorphic encryption [11], state decomposition [12], output mask [13], differential privacy [14] and monodirectional information exchange [15], have been employed to ensure privacy in consensus problems. Among these methods, differential privacy is particularly notable due to its strong mathematical guarantees and no assumptions regarding background knowledge of the adversary [16, 17]. Numerous studies have applied differential privacy to consensus problems in MASs. A differential private average consensus algorithm with an event-triggered scheme is designed in [18] for discrete-time MASs. In [19], the problem of resilient consensus with faulty agents over digraphs is considered by employing a differentially private mean-subsequence-reduced(MSR) method. In [20], the author addressed the differentially private consensus problem for general multivariable discrete-time MASs. A differentially private consensus problem for cooperative–competitive MASs was investigated in [21] where privacy only works for competitive agents. By using Rényi divergence, a distributed differentially private algorithm based on Gaussian noises was developed in [22] to solve the output consensus problem. In addition, the differentially private consensus problem has been further developed in [23] for discrete-time MASs over switching networks. The author first addressed the differentially private average consensus of MASs with positive agents in [24] using non-decaying positive Gaussian noises. Very recently, by injecting time-varying noises, a differentially private bipartite consensus was investigated in [25]. However, little attention has been paid to the privacy-preserving bipartite output consensus problem of heterogeneous MASs so far.
It is noteworthy that the majority of existing literature on differential private consensus has primarily focused on discrete-time models, with less focus on continuous-time MASs. Impulsive control [26], a method for converting continuous dynamics into discrete form, has been extensively studied [27, 28]. However, these studies typically depend on fixed or predetermined impulse sequences, which can be conservative. Recent work [29] of differential private average output consensus in continuous-time MASs combining periodic sampling with hybrid control to reduce communication loads, yet this discrete-time interaction scheme still requires time-triggering, which may result in a high communication burden among agents. To overcome this issue, the event-triggered impulsive control (ETIC) method was proposed. The primary advantage of ETIC is intelligent sampling and transmission inside the communication network since the impulsive sequence is determined by a well-designed event-triggered mechanism. Leaderless quasi-synchronization of heterogeneous MASs was investigated in [30] using centralized and distributed ETIC control strategies. In the case of leader-following consensus problems, quasi-consensus with random packet loss has been examined in [31] based on Lyapunov theory. Building upon the ETIC method, the leader-following problem for unknown nonlinear MASs was considered in [32] with an improved event-triggering function to reduce resource utilization. Moreover, leader-following mean square consensus for stochastic MASs with randomly occurring uncertainties and nonlinearities was discussed in [33]. A general ETIC method was used to solve the bipartite tracking output consensus problem for MASs with a dynamic leader in [34] under switching topology and non-zero control inputs. A two-layer distributed control scheme, which includes an ETIC method and a fault-tolerant controller, was provided in [35] to solve the containment control problem of linear MASs with deception attacks and actuator faults. To the best of our knowledge, the problem of differentially private bipartite consensus for continuous-time MASs under the ETIC method has not yet been addressed.
Based on a hierarchical hybrid framework, this paper investigates the bipartite output consensus of continuous-time heterogeneous MASs with differential privacy requirements. The main contributions of this work are as follows. First, we design a novel privacy-preserving algorithm for output average consensus in heterogeneous cooperative-competitive MASs. Compared with [25, 36] only considering homogeneous MASs, we consider the heterogeneous MASs. Second, the development and implementation of an impulsive controller that employs an event-triggered mechanism is introduced. This novel method performs very efficiently in terms of lower transmission and computation costs. Moreover, a fixed lower bound on impulsive intervals was proposed to prevent Zeno behavior. Compared with [22, 29], we design a control scheme that is a combination of impulsive control and event-triggered control, which can effectively save resources and generalize continuous-time systems to discrete-time systems. Additionally, the communication topologies are generalized from unsigned graphs [14, 19, 20] to signed graphs in our study. Finally, we demonstrate that our algorithm ensures mean square convergence, with privacy preservation only applied to competitive agents.
The structure of this article is as follows. The preliminaries and problem formulation are given in “Preliminaries” and “Problem formulation” sections, respectively. The main results are given in “Main results” section, which includes the design of the hybrid controller, and the analysis of consensus and privacy. The simulation result is given in “Numerical examples” and “Conclusion” sections concludes this article.
Preliminaries
Notations
Denote the set of real numbers by \(\mathbb {R}\), the set of n- dimensional real vectors by \(\mathbb {R}^n\), and the set of \(n\times n\) real matrices by \(\mathbb {R}^{n\times n}\). \(I_n\in \mathbb {R}^{n\times n}\) is identity matrix. Denote \(\otimes \) as the Kronecker product. \(\textrm{diag}(\cdot )\) represents a diagonal matrix. \(\textrm{col}(\cdot )\) represents a concatenation. \(\textrm{sign}(\cdot )\) denotes a sign function. \(||x||_1\) and ||x|| denote 1-norm and 2-norm of vector x, respectively. For matrix A, ||A|| denotes the 2-norm of A, \(\rho (A)\) denotes the spectral radius of A. For a random variable \(X\in \mathbb {R}\), \(\mathbb {E}[X]\) and Var[X] denotes the expectation and variance. We denote by \(X\sim \textrm{Lap}(0,b)\) a zero mean random variable with Laplace distribution and variance \(2b^2\), and its probability density function is given by \(\mathcal {L}(x;b)=\frac{1}{2b}e^{-\frac{|x|}{b}}\). For a random vector \(Y\in \mathbb {R}^n\), cov(Y) represents the covariance matrix.\(\mathcal {R}(H)\) denotes the range space of function H.For a set \(\Omega \), \(\mathcal {B}(\Omega )\) denotes the Borel \(\sigma \)-algebra of \(\Omega \). For a subset P of real numbers, inf(P) denotes the greatest real number that is less than or equal to all numbers in P.
Graph theory
Let \(\mathcal {G}=(\mathcal {V},\mathcal {E},A)\) be a signed digraph, where \(\mathcal {V}=\{1,2,\ldots ,N\}\) is the set of vertices representing agents. \(\mathcal {E}\subseteq \mathcal {V} \times \mathcal {V}\) denotes the set of edges, and \(A=[a_{ij}]\in \mathbb {R}^{N\times {N}}\) is the adjacency matrix of G, where \(a_{ij}\not =0\Leftrightarrow (v_i,v_j)\in \mathcal {E}\) and \(a_{ij}=0\Leftrightarrow (v_i,v_j)\notin \mathcal {E}\). Specifically, the interactions between agent i and j is cooperative if \(a_{ij}>0\) and competitive if \(a_{ij}<0\). It is assumed that the digraph with no self-loops, i.e., \(a_{ii}=0, i\in \{1\ldots ,n\}\) and satisfies the digon sign-symmetry property \(a_{ij}a_{ji}\ge 0\). Let \(\mathcal {N}_i\) denote the neighbor set of the node i, that is, \(\mathcal {N}_i=\{j|(v_j,v_i\in \mathcal {E})\}\). The cardinality of \(\mathcal {N}_i\) is \(|\mathcal {N}_i|\). A directed path from agent i to agent j is a sequence of ordered edges \(\{(v_i,v_{i_1}), (v_{i_1},v_{i_2}),\ldots ,(v_{i_l},v_j)\}\). A signed directed graph is said to contain a directed spanning tree if there is at least one agent, which has a directed path to every other agent. The in-degree and out-degree of agent i can be separately defined as \(d^i_{in}=\sum _{j\in \mathcal {N}_i}|a_{ij}|\) and \(d^i_\mathrm{{out}}=\sum _{j\in \mathcal {N}_i}|a_{ji}|\). A signed digraph \(\mathcal {G}\) is balanced if \(d^i_{in}=d^i_\mathrm{{out}}=d_i\) for \(i\in \{1\ldots ,N\}\). For a balanced digraph, we denote the smallest degree as \(d_{\min }={\min }\{d_{i}, i\in \mathcal {V}\}\). A signed Laplacian matrix \(L=[l_{ij}]\in \mathbb {R}^{N\times N}\) is defined as \(L=D-A\), where \(D=\textrm{diag}(d^1_{in},\ldots ,d^N_{in})\).
Definition 1
A signed digraph is structurally balanced if there exists a bipartition of nodes \(\mathcal {V}_1\) and \(\mathcal {V}_2\) satisfying \(\mathcal {V}_1\cup \mathcal {V}_2=\mathcal {V}\) and \(\mathcal {V}_1\cap \mathcal {V}_2=\emptyset \), such that \(a_{ij}>0, i,j\in \mathcal {V}_q(q\in 1,2)\) and \(a_{ij}<0, i\in \mathcal {V}_q, j\in \mathcal {V}_{3-q}\).
Related lemmas
Lemma 1
[37] The signed digraph is structurally balanced if and only if there exists a gauge matrix \(S=\textrm{diag}(s_1,\ldots ,s_N)\) with \(s_i\in \{\pm 1\}\) such that \(\mathcal {A}_s=S\mathcal {A}S\), where \(\mathcal {A}_s=[|a_{ij}|]\in \mathbb {R}^{N\times N}\) is a non-negative matrix and all off-diagonal entries of \(L_s=SLS\) are non-positive.
Lemma 2
[38] If the symmetry matrix \(B\in \mathbb {R}^{n\otimes n}\) is positive definite or positive semi-definite, then for an arbitrary matrix \(A\in \mathbb {R}^{n\otimes m}\), the following inequality holds
Problem formulation
Consider a MAS consisting of N continuous-time heterogeneous agents with the following dynamics:
where \(x_i\in \mathbb {R}^{n_i}\), \(u_i\in \mathbb {R}^{m_i}\) and \(y_i\in \mathbb {R}^{l}\) represent the system state, the control input, and the measurement output, respectively. \(A_i, B_i\), and \(C_i\) are system matrices with compatible dimensions.
Definition 2
The heterogeneous MASs (2) can achieve mean square bipartite output consensus if there exists a random variable \(y^*\) such that
The objective of this article is to develop a distributed controller that enables the system (2) to achieve mean square bipartite output consensus while guaranteeing differential privacy.
In what follows, we introduce the definitions of differential privacy used in this article.
Definition 3
[39] For any given vector \(\sigma \in \mathbb {R}^l\), two initial states \(y(0)=\textrm{col}(y_1(0),y_2(0),\ldots ,y_N(0))\in \mathbb {R}^{Nl}\) and \(y^{'}(0)=\textrm{col}(y_1^{'}(0),y_2^{'}(0),\ldots ,y^{'}_N(0))\in \mathbb {R}^{Nl}\) are said to be \(\sigma \)-adjacent if there exists an integer \(i_0\in \mathcal {V}\) such that
Definition 4
[20] (Differential privacy) Given \(\epsilon >0\), \(\sigma >0\) and any two \(\sigma \)-adjacent initial states y(0), \(y^{'}(0)\), a randomized mechanism \(\mathbb {R}^{Nl}\rightarrow \mathcal {R}(\mathcal {M})\) is \(\epsilon \)-differentially private for any \(\mathcal {O}\in \mathcal {B}(\mathcal {R}(\mathcal {M}))\), if
where \(\epsilon \) is the privacy level.
Throughout this paper, the following assumptions should be satisfied.
Assumption 1
The directed signed graph \(\mathcal {G}\) is structurally balanced and contains a directed spanning tree.
Assumption 2
All the matrices \((A_i,B_i), i=1,\ldots ,N\), are stabilizable.
Assumption 3
All the matrices \((A_i,C_i), i=1,\ldots ,N\) are detectable.
Assumption 4
For \(i\in \mathcal {V}\), there exists solution \((\Pi _i,\Gamma _i)\), satisfying the following equations:
Main results
Hybrid event-triggered impulsive controller design
To achieve bipartite output consensus of (2), we design a hybrid controller based on the approach in [29, 40] as follows:
with
where \(\zeta _i(t)\in \mathbb {R}^l\) is the reference state with \(\zeta _i(0)=y_i(0)\). \(\gamma \) is the impulsive gain, \(K_{1i}\) and \(K_{2i}\) and are the control parameters to be designed. \(\delta (\cdot )\) is the Dirac function, and \(t_k\) are the event-triggered impulsive instants for \(k=1,2,\ldots ,\) which satisfy \(0<t_1<t_2<\cdots<\) with \(\lim _{k\rightarrow \infty }t_k=+\infty \). \(\eta _j(t_k)\in \mathbb {R}^l\) is a random vector with each entry to be independent and identically distributed (i.i.d.) Laplace distribution.
The MASs under the event-triggered impulsive control strategy can be rewritten as
Remark 1
It is evident that each agent only receives information from its neighbors at the impulsive time instant. This implies that information transfer between agents only occurs at these discrete trigger times.
Denote \(A=\textrm{diag}(A_1,\ldots ,A_N)\), \(B=\textrm{diag}(B_1,\ldots ,B_N)\), \(K_1=\textrm{diag}(K_{11},\ldots ,K_{1N})\), \(\Pi =\textrm{diag}(\Pi _1,\ldots ,\Pi _N)\), \(\Gamma =\textrm{diag}(\Gamma _1,\ldots ,\Gamma _N)\). Then, define the consensus error and the following error as \(\bar{\zeta }_i(t)=\zeta _i(t)-\frac{1}{N}\sum _{i=1}^{N}s_is_j\zeta _j(t)\), \(\bar{x}_i(t)=x_i(t)-\Pi _i\zeta _i(t)\). Moreover, define \(\bar{\zeta }(t)=\textrm{col}(\bar{\zeta }_1(t),\ldots , \bar{\zeta }_N(t))\), \(\bar{x}(t)=\textrm{col}(\bar{x}_1(t),\ldots ,\bar{x}_N(t))\) and \(\eta (t)=\textrm{col}(\eta _1(t), \ldots ,\eta _N(t))\). Substituting (7) and (8) in (2), for \(t\in (t_k,t_{k+1})\), we have
Under Assumption 4 and \(K_{2i}=\Gamma _i-K_{1i}\Pi _i\), it holds that
Let \(M=I_N-\frac{1}{N}ss^T\), for \(t=t_k\), from Eq. (9), we have
and
From (10)–(13), the closed-loop system with respect to \(\bar{\zeta }(t)\) and \(\bar{x}(t)\) can be rewritten as
Denote \(\hat{A}=A+BK_1\), \(\mathcal {A}^*=\mathcal {A}-\mathcal {A}_s\), it follows from (14) that \(\bar{\zeta }(t^-_{k+1})=\bar{\zeta }(t_k)\) and \(\bar{x}(t^-_{k+1})=e^{\hat{A}(t_{k+1}^{-}-{t_k})}\bar{x}(t_k)\), then
Consensus analysis
In this subsection, we first prove that the output of each heterogeneous system converges to the average of the reference states in the mean square. Then, we prove that heterogeneous MASs are able to achieve mean square bipartite output average consensus.
Theorem 1
Under Assumptions 1–4, suppose there exists positive definite matrix \(P\in \mathbb {R}^{Nl\times Nl}\), positive definite matrix \(Q\in \mathbb {R}^{n^*\times n^*}\) with \(n^*=\sum _{i=1}^{N}n_i\) such that the following inequalities
hold, then
and the event-triggered condition is designed as:
where \(\bar{X}^T_{\zeta }(t)=\begin{bmatrix}\bar{\zeta }^T(t)&\bar{x}^T(t)\end{bmatrix}^T\), \(W(t)=\begin{bmatrix}W_1&{}0\\ W_2&{}W_3(t)\end{bmatrix}\), \(W_1=(I_N-\gamma L)\otimes I_l\), \(W_2=\gamma \Pi (L\otimes I_l)\), \(W_3(t_{k+1}^-)=e^{\hat{A}(t_{k+1}^{-}-t_k)}\), \(T_u>0\) is an upper bound of impulsive interval and can be chosen large enough, \(\Delta t>0\) is a constant, \(0<\beta <1\), \(U\in \mathbb {R}^{N^*\times N^*}\) with \(N^*=\sum _{i=1}^{N}n_i+Nl\) is a symmetric positive definite matrix such that \(W^T(t+\Delta t)UW(t+\Delta t)-U<0\).
Proof
From (15), we have:
and the compact form of the above system can be described by
where \(R=\begin{bmatrix}R_1&R_2\end{bmatrix}^T\), \(R_1=\frac{\gamma }{2}(M\mathcal {A}^*\otimes I_l)\), \(R_2=-\frac{\gamma }{2}\Pi (\mathcal {A}^*\otimes I_l)\).
Since conditions (16) and (17) hold, \(\rho (W_1)<1\) and \(\rho (W_3(t_k+\Delta t))<1\), which means that \(\rho (W(t_k+\Delta t))<1\) and there must exist the symmetric positive definite matrix U such that \(W^T(t_k+\Delta t)UW(t_k+\Delta t)-U<0\).
Let \(V(k)=\bar{X}^T_{\zeta }(t_k)U\bar{X}_{\zeta }(t_k)\), then we have \(\Delta V(k)=V(k+1)-V(k)\), and the expectation of \(\Delta V(k)\) is
Let \(\Delta V_1(k)=\bar{X}^T_{\zeta }(t_k)(W^T(t_{k+1}^-)UW(t_{k+1}^-)-U)\bar{X}_{\zeta }(t_k)\) and according to Lemma 2, we have
Then, enumerating and calculating the sums of both sides in Eq. (23), we have as \(k\rightarrow \infty \)
Using Schur complement, according to condition (16), condition (17) and event-triggered condition (19), we have \(\Delta V_1(k)<0\) when \(t_{k+1}-t_k>\Delta t\). Then, we have \(\mathbb {E}[\Delta V_1(k)]<0, \mathbb {E}[V(k)]\ge 0\). From (24), we can further get that \(\mathbb {E}[V(k)]\) and \(\mathbb {E}[\Delta V_1(k)]\) are both bounded. Consequently, there must exist a positive real number \(0<r<1\) such that
As \(k\rightarrow \infty \), the contribution of the first term in (25) converge to 0, and in the second term we have \(\sum _{i=1}^{N}\sum _{z=1}^{l}E[\eta _{i,z}^T (t^-_{k+1})\eta _{i,z}(t^-_{k+1})]=2\sum _{i=1}^{N}c^2_iq^{2k}_iI_l\) which also converge to 0. Therefore, we conclude that \(\mathbb {E}[V(k)]=0\) as \(k\rightarrow \infty \).
Since \(U>0\) and \(\mathbb {E}[V(k)]=0\), we have \(\lim _{k\rightarrow \infty }\mathbb {E}[\bar{X}_{\zeta }(t_k)]=0\), which means that \(\lim _{k\rightarrow \infty }\mathbb {E}[\bar{\zeta }(t_{k})]=0\) and \(\lim _{k\rightarrow \infty }\mathbb {E}[\bar{x}(t_{k})]=0\). Then,
The proof is completed. \(\square \)
Theorem 2
Suppose Assumptions 1–4 hold and \(A_i+B_iK_{1i}\) is Hurwitz, the heterogeneous multi-agent system (2) will achieve mean square bipartite output average consensus and \(\lim _{t\rightarrow \infty }\mathbb {E}||y_i(t)-s_iy^*||^2=0\), where \(y^*\) is a random vector, \(\mathbb {E}[y^*]=\frac{1}{N}(\mathbf{{1}}^T_NS\otimes I_l)y(t_0)\).
Proof
Based on Assumption 1, we have \(\mathbf{{1}}^T_{N}S{L}=\textbf{0}\). Accordingly, it is derived from (9) that
By taking iterations, we can obtain that
which
According to Theorem 1, we have
with \(y^*=\frac{1}{N}\sum _{i\in \mathcal {V}}s_i\xi _i(t_0)+\frac{\gamma }{2N}\sum _{p=1}^{\infty }\sum _{i\in \mathcal {V}}\sum _{j\in \mathcal {N}_i}\tilde{a}_{ij}\eta _i (t^-_p)\), \(\tilde{a}_{ij}=(s_i-s_j)|a_{ij}|\). By the fact that \(\eta _i(t^-_h)\) are i.i.d., we have
\(\square \)
Remark 2
Because in Theorem 1 there exists a constant \(\Delta t>0\) such that \(t_{k+1}-t_k>\Delta t\), then the Zeno behavior can be naturally excluded.
Remark 3
Compared to the work in [15], which proposed an alternating direction method of multiplier (ADMM) to solve the consensus problem of reflection coefficients, the event-triggered impulsive control strategy proposed in this paper can mitigate limited communications resources. In addition, compared with the monodirectional information exchange method to safeguard information privacy, the implementation of differential privacy in this paper is independent of a specific network structure or communication model, making it more flexible to different systems.
Privacy analysis
In this subsection, we analyze the \(\epsilon _i\) privacy of the proposed algorithm. First, we consider the initial states of an individual agent’s output \(y(0)=\textrm{col}(y_1(0),y_2(0),\ldots ,y_N(0))\) as the private data. We then denote the sequence of reference states \(\chi (y(0), O)=\{\zeta _i(t_k),i\in \mathcal {V},k=0,1,\ldots \}\) as the trajectory of the system, and the sequence of transmitted states \(O=\{\varphi _i(t_k),i\in \mathcal {V},k=0,1,\ldots \}\) as the observation of the system. Define the randomized mechanism \(\mathcal {M}(\cdot )\) as a stochastic map from the private data y(0) to an observation sequence O.
Theorem 3
If the agent and its neighbors are in a competitive relationship, the proposed algorithm can preserve \(\epsilon _i\)-differential privacy for agent \(i\in \mathcal {V}\) with
Proof
Because the observations \(O=\{\varphi _i(t_k^-),i\in \mathcal {V},k=1,2,\ldots \}\) for y(0) and \(y^{'}(0)\) are the same, based on Eq. (9), we have
and
Therefore,
Define \(R=\{\chi (y(0),O),O\in \mathcal {O}\}\) and \(R^{'}=\{\chi (y^{'}(0),O), O\in \mathcal {O}\}\) are the set of possible in the observation set \(\mathcal {O}\). Meanwhile, let \(f(y(0),\chi (y(0), O))\) and \(f(y^{'}(0),\chi (y^{'}(0), O))\) as the probability density function of the trajectories, respectively. Given initial states y(0), the observation sequence \(O=\{\varphi _i(t_k^-),i\in \mathcal {V},k=1,2,\ldots \}\) is unique defined by the noise sequence \(\{\eta _i(t^-_k),i\in \mathcal {V},k=0,1,\ldots \}\) according to (9). Then, the probability density function of observation sequence O is given as follows
For a pair of private datasets, since they have the same observation up to time T, there exists a bijection \(h(\cdot ):R\rightarrow R^{'}\) such that for \(\chi (y(0),O)\in R\), \(\chi (y^{'}(0),O)\in R^{'}\), it has \(h(\chi (y(0),O))=\chi (y^{'}(0),O)\). Then, from (37) and using the bijection \(h(\cdot )\), one can get
Subsequently, integrating both sides of (37) and letting \(k\rightarrow \infty \) yields
where \(i_0\) can be any agent in the network. The proof is now complete. \(\square \)
Remark 4
Theorem 3 reveals that the privacy level \(\epsilon _i\) is related to the parameter \(c_i\), \(q_i\), and the degree \(d_i\). According to (32), we find that greater \(c_i\), \(q_i\), and \(d_i\) give a smaller \(\epsilon _i\), which may lead to better privacy protection.
Numerical examples
Example 1
Consider a MAS with six agents over a signed graph \(\mathcal {G}\) (see Fig. 1), where the red dashed lines and the blue solid lines separately indicate the antagonistic and cooperative interactions. Since \(\mathcal {G}\) is structural balanced, \(\mathcal {V}_1=\{v_1,v_2,v_3\}\) and \(\mathcal {V}_2=\{v_4,v_5,v_6\}\) are two competitive groups. The dynamics of (2) are provided as follows:
Based on (6), we can get the solution of that \(\Pi _1=\Pi _3=\Pi _5=[-1,1]^T\), \(\Gamma _1=\Gamma _3=\Gamma _5=1\) and \(\Pi _2=\Pi _4=\Pi _6=[1,0,0]^T\), \(\Gamma _2=\Gamma _4=\Gamma _6=-1\). Then, we select the feedback gain matrices \(K_{11}=[4.3,-1.32], K_{12}=[5.7,-3.4], K_{13}=[14,-35],K_{14}=[37.2,35.94,8.5], K_{15}=[106,68.7,12.3],K_{16}=\) [176.4, 97.6, 15.2] such that \(A_i+B_iK_{1i}\) are Hurwitz matrices.
The initial states are randomly selected from the interval [0, 10] and let \(c_i=0.8, q_i=0.95\), \(\Delta t=0.02, \gamma =0.15, \beta =0.7\). The corresponding results are presented in Figs. 2, 3, 4 and 5. Figure 2 shows the output trajectories \(y_i(t)\) of all agents, demonstrating that outputs \(y_1(t), y_2(t)\) and \(y_3(t)\) in subgroup \(\mathcal {V}_1\) converge to consensus, while outputs \(y_4(t), y_5(t)\) and \(y_6(t)\) in subgroup \(\mathcal {V}_2\) converge to the opposite value. Figure 3 depicts the triggered instants for agents 1-6. We can observe that the triggering instants of each agent are finite, which verifies the exclusion of Zeno behavior. As depicted in Fig. 4, the output errors of all agents asymptotically converge to zero, thereby confirming that the proposed control strategy achieves bipartite output consensus for the heterogeneous MASs. Figure 5 reveals the relation between privacy level \(\epsilon _i\) and the parameter set (\(c_i\), \(q_i\), \(d_i\)) for \(\gamma =0.15\). It shows that \(\epsilon _i\) decreases as \(c_i\), \(q_i\), and \(d_i\) increase, which implies stronger privacy protection for agents with more neighbors.
Triggering instants under the proposed controller (7)
Example 2
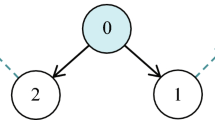
Consider a MAS with four agents over a signed graph \(\mathcal {G}\) (see Fig. 6), where the red dashed lines and the blue solid lines separately indicate the antagonistic and cooperative interactions. Since \(\mathcal {G}\) is structural balanced, \(\mathcal {V}_1=\{v_1,v_2\}\) and \(\mathcal {V}_2=\{v_3,v_4\}\) are two competitive groups. The dynamics of (2) are provided as follows:
Triggering instants under the proposed controller (7)
Based on (6), we can get the solution of that \(\Pi _1=[1,0]^T\), \(\Pi _2=[1,0]^T\), \(\Pi _3=[1,-1]^T\), \(\Pi _4=[0,2]^T\) and \(\Gamma _1=-1\), \(\Gamma _2=-0.5\), \(\Gamma _3=-2\), \(\Gamma _=-2\). Then, we select the feedback gain matrices \(K_{11}=[6.3,9.92], K_{12}=[7.2,13.8], K_{13}=[7.6,12.95],K_{14}=[10.25,-3.65]\) such that \(A_i+B_iK_{1i}\) are Hurwitz matrices.
The initial states are randomly selected from the interval \([-5,5]\) and let \(c_i=0.8, q_i=0.95\), \(\Delta t=0.02, \gamma =0.2, \beta =0.5\). The corresponding results are presented in Figs. 7, 8 and 9. Figure 7 shows the output trajectories \(y_i(t)\) of all agents, demonstrating that outputs \(y_1(t), y_2(t)\) in subgroup \(\mathcal {V}_1\) converge to consensus, while outputs \(y_3(t), y_4(t)\) in subgroup \(\mathcal {V}_2\) converge to the opposite value. Figure 8 depicts the triggered instants for agents 1–4. We can observe that the triggering instants of each agent are finite, which verifies the exclusion of Zeno behavior. As depicted in Fig. 9, the output errors of all agents asymptotically converge to zero, thereby confirming that the proposed control strategy achieves bipartite output consensus for the heterogeneous MASs. Figure 10 reveals the relation between privacy level \(\epsilon _i\) and the parameter set (\(c_i\), \(q_i\), \(d_i\)) for \(\gamma =0.2\). It shows that \(\epsilon _i\) decreases as \(c_i\), \(q_i\), and \(d_i\) increase, which implies stronger privacy protection for agents with more neighbors.
Conclusion
In this paper, a differentially private bipartite output consensus problem for continuous-time heterogeneous MASs over signed topology is addressed. To handle this problem, a novel hybrid impulsive controller is designed, where the event-triggered mechanism is taken into account. In contrast to the current time-triggered approach, a significant reduction in control accuracy and communication costs can be achieved. Besides, the proposed control strategy avoids Zeno behavior by enforcing a fixed lower bound on time intervals. A formal analysis of the \(\epsilon _i\)-differential privacy of the system is also provided. Future work will focus on differentially private bipartite output consensus with dynamic event-triggered control, switching topology, and privacy preservation of cell-free networks. Moreover, privacy preservation in practice, including protecting the privacy of traffic analysis and health research, will be further studied to extend our proposed control scheme.
References
Montero EE, Mutahira H, Pico N, Muhammad MS (2024) Dynamic warning zone and a short-distance goal for autonomous robot navigation using deep reinforcement learning. Complex Intell Syst 10: 1149–1166
Wang Q, Hu J, Wu Y, Zhao Y (2023) Output synchronization of wide-area heterogeneous multi-agent systems over intermittent clustered networks. Inf Sci 619:263–275
Chen B, Hu J, Zhao Y, Ghosh BK (2022) Finite-time velocity-free rendezvous control of multiple AUV systems with intermittent communication. IEEE Trans Syst Man Cybern Syst 52(10):6618–6629
Hu J, Wu Y, Li T, Ghosh BK (2018) Consensus control of general linear multiagent systems with antagonistic interactions and communication noises. IEEE Trans Autom Control 64(5):2122–2127
Xu C, Xu H, Guan Z, Ge Y (2023) Observer-based dynamic event-triggered semiglobal bipartite consensus of linear multi-agent systems with input saturation. IEEE Trans Cybern 53(5):3139–3152
Yaghmaie FA, Su R, Lewis FL, Olaru S (2017) Bipartite and cooperative output synchronizations of linear heterogeneous agents: a unified framework. Automatica 80:172–176
Zhang H, Cai Y, Wang Y, Su H (2020) Adaptive bipartite event-triggered output consensus of heterogeneous linear multiagent systems under fixed and switching topologies. IEEE Trans Neural Netw Learn Syst 31(11):4816–4830
Zhao L, Wu H, Cao J (2022) Finite/fixed-time bipartite consensus for networks of diffusion PDEs via event-triggered control. Inf Sci 609:1435–1450
Liang Q, Wu Y, Hu J, Zhao Y (2020) Bipartite output synchronization of heterogeneous time-varying multi-agent systems via edge-based adaptive protocols. J Frankl Inst 357(17):12808–12824
Zhang J, Zhang H, Sun S (2024) Adaptive dynamic event-triggered bipartite time-varying output formation tracking problem of heterogeneous multiagent systems. IEEE Trans Syst Man Cybern Syst 54(1):12–22
Hadjicostis CN, Domínguez-García AD (2020) Privacy-preserving distributed averaging via homomorphically encrypted ratio consensus. IEEE Trans Autom Control 65(9):3887–3894
Zhang K, Li Z, Wang Y, Louati A, Chen J (2022) Privacy-preserving dynamic average consensus via state decomposition: case study on multi-robot formation control. Automatica 139:110182
Altafini C (2020) A system-theoretic framework for privacy preservation in continuous-time multiagent dynamics. Automatica 122:109253
Huang Z, Mitra S, Dullerud G (2012) Differentially private iterative synchronous consensus. In: Proceedings of the 2012 ACM workshop on privacy in the electronic society, pp 81–90
Xu W, An J, Li H, Gan L, Yuen C (2024) Algorithm-unrolling-based distributed optimization for RIS-assisted cell-free networks. IEEE Internet Things J. 11:944–957
Dwork C (2006) Differential privacy. In: Automata, languages and programming: 33rd international colloquium, ICALP 2006, Venice, Italy, July -10–14, 2006, proceedings, part II 33. Springer, pp 1–12
Xu C, Mei X, Liu D, Zhao K, Ding AS (2023) An efficient privacy-preserving point-of-interest recommendation model based on local differential privacy. Complex Intell Syst 9(3):3277–3300
Gao L, Deng S, Ren W (2018) Differentially private consensus with an event-triggered mechanism. IEEE Trans Control Netw Syst 6(1):60–71
Fiore D, Russo G (2019) Resilient consensus for multi-agent systems subject to differential privacy requirements. Automatica 106:18–26
Wang Y, Lam J, Lin H (2022) Consensus of linear multivariable discrete-time multiagent systems: differential privacy perspective. IEEE Trans Cybern 52(12):13915–13926
Ma J, Hu J (2022) Safe consensus control of cooperative-competitive multi-agent systems via differential privacy. Kybernetika 58(3):426–439
Liu X, Wang Y, Xiao J, Chi M, Liu Z (2022) Concentrated differentially private average consensus algorithm for a discrete-time network with heterogeneous dynamics. J Frankl Inst 359(4):1655–1676
Wan X, Guo Y, Wu X (2023) Differentially private consensus for multi-agent systems under switching topology. IEEE Trans Circ Syst II Exp Briefs 70(9):3499–3503
Wang Y, Lam J, Lin H (2023) Differentially private average consensus for networks with positive agents. IEEE Trans Cybern https://doi.org/10.1109/TCYB.2023.3267145
Wang J, Ke J, Zhang J-F (2024) Differentially private bipartite consensus over signed networks with time-varying noises. IEEE Trans Autom Control https://doi.org/10.1109/TAC.2024.3351869
Wang Y, Liu X, Xiao J, Shen Y (2018) Output formation-containment of interacted heterogeneous linear systems by distributed hybrid active control. Automatica 93:26–32
Liu Z-W, Wen G, Yu X, Guan Z-H, Huang T (2019) Delayed impulsive control for consensus of multiagent systems with switching communication graphs. IEEE Trans Cybern 50(7):3045–3055
Hu Z, Mu X (2023) Impulsive consensus of stochastic multi-agent systems under semi-Markovian switching topologies and application. Automatica 150:110871
Liu X, Zhang J, Wang J (2020) Differentially private consensus algorithm for continuous-time heterogeneous multi-agent systems. Automatica 122:109283
Sun W, Zheng H, Guo W, Xu Y, Cao J, Abdel-Aty M, Chen S (2020) Quasisynchronization of heterogeneous dynamical networks via event-triggered impulsive controls. IEEE Trans Cybern 52(1):228–239
Chen R, Peng S (2023) Leader-follower quasi-consensus of multi-agent systems with packet loss using event-triggered impulsive control. Mathematics 11(13):2969
Tang W, Liang C, Wu J, Xie Y (2023) Distributed impulsive control consensus for a class of unknown nonlinear multi-agent systems based on event-triggered scheme. Nonlinear Anal Hybrid Syst 49:101352
Zhang Z, Peng S, Liu D, Wang Y, Chen T (2020) Leader-following mean-square consensus of stochastic multiagent systems with ROUs and RONs via distributed event-triggered impulsive control. IEEE Trans Cybern 52(3):1836–1849
Zhang L, Li Y, Lu J, Lou J (2022) Bipartite event-triggered impulsive output consensus for switching multi-agent systems with dynamic leader. Inf Sci 612:414–426
Li W, Sader M, Zhu Z, Liu Z, Chen Z (2023) Event-triggered fault-tolerant secure containment control of multi-agent systems through impulsive scheme. Inf Sci 622:1128–1140
Zuo Z, Tian R, Han Q, Wang Y, Zhang W (2022) Differential privacy for bipartite consensus over signed digraph. Neurocomputing 468:11–21
Altafini C (2012) Consensus problems on networks with antagonistic interactions. IEEE Trans Autom Control 58(4):935–946
Wu Y, Liang Q, Zhao Y, Hu J, Xiang L (2021) Adaptive bipartite consensus control of general linear multi-agent systems using noisy measurements. Eur J Control 59:123–128
Luo Q, Liu S, Wang L, Tian E (2022) Privacy-preserved distributed optimization for multi-agent systems with antagonistic interactions. IEEE Trans Circ Syst I Reg Pap 70:1350–1360
Su Y, Huang J (2011) Cooperative output regulation of linear multi-agent systems. IEEE Trans Autom Control 57(4):1062–1066
Acknowledgements
This work was partially supported by the National Key Research and Development Program of China under Grant 2022YFE0133100, and the Sichuan Science and Technology Program under Grant 24NSFSC1362.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
No potential conflict of interest was reported by the authors.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Ma, J., Hu, J. Privacy-preserving bipartite output consensus for continuous-time heterogeneous multi-agent systems via event-triggered impulsive control. Complex Intell. Syst. 10, 5127–5137 (2024). https://doi.org/10.1007/s40747-024-01430-2
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40747-024-01430-2