Abstract
We model the evolution of preferences guiding behavior in pairwise interactions in group-structured populations. The model uses long-term evolution theory to examine different interaction scenarios, including conditional preference expression upon recognition of the partner’s type. We apply the model to the evolution of semi-Kantian preferences at the fitness level, which combine self-interest and a Kantian interest evaluating own behavior in terms of consequences for own fitness if the partner also adopted this behavior. We seek the convergence stable and uninvadable value of the Kantian coefficient, i.e., the weight attached to the Kantian interest, a quantitative trait varying between zero and one. We consider three scenarios: (a) incomplete information; (b) complete information and incomplete plasticity; and (c) complete information and complete plasticity, where individuals not only recognize the type of their interaction partner (complete information), but also conditionally express the Kantian coefficient upon it (complete plasticity). For (a), the Kantian coefficient generally evolves to equal the coefficient of neutral relatedness between interacting individuals; for (b), it evolves to a value that depends on demographic and interaction assumptions, while for (c) there are generally multiple uninvadable types, including the type whereby an individual is a pure Kantian when interacting with individuals of the same type and applies the Kantian coefficient that is uninvadable under complete information with zero relatedness when interacting with a different typed individual. Overall, our model connects several concepts for analysing the evolution of behavior rules for strategic interactions that have been emphasized in different and sometimes isolated studies.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
This paper is about formalizing natural selection on rules guiding individual behavior in strategic interactions, a central question in evolutionary game theory [28, 70, 71]. By behavior we mean a “strategy”, i.e., “a specification of what an individual will do in any situation in which it may find itself” [70]. In the original evolutionary game theory models, each individual is programmed to play a certain strategy regardless of the strategies used by others in the population. One way to think about this is that the strategy is innate, thus a genetically determined trait. This view led to a vast theoretical literature analysing the genetic evolution of strategies under all sorts of biological scenarios as is illustrated by the studies on the evolution of fighting, cooperation, and life-histories in plants and animals (e.g., the books by [22, 45, 70, 73, 97]). Here, it is the population genetic process alone that determines the “evolutionarily stable strategy” since strategies are inherited from parent to offspring and selected among alternatives by way of differential survival and reproduction.
The view that strategies are innate is restrictive, however, as it rules out situations where individuals have capacities to change their own strategy when interacting with their environment. Such processes have been incorporated into evolutionary game theory through several alternative notions, such as the concepts of “culturally stable” and “developmentally stable” strategies [28, 70]. Here, the behavior of an individual is the outcome of some updating rule(s), typically imitative or experiential, for strategy selection during the individual’s lifespan. In the memorable example detailed by [28], pigs in skinner boxes equilibrate on developmentally stable strategies by action reinforcement in producer-scrounger games, and a large literature has evaluated culturally stable strategies under different sorts of transmission rules (e.g., [20, 23]). This in turn raises the question of what should be the evolutionarily stable rule for individual strategy selection in strategic interactions? While this question was raised early in the history of evolutionary game theory [52, 70], perhaps more controversy than conclusions were initially reached (e.g., [90]), and it is only more recently that this question has gained some renewed theoretical attention in evolutionary biology (e.g., [13, 30, 31, 73]).
In the meantime, however, economists and mathematical game theorists also produced insights about how various individual choice and transmission rules induce change in strategies in populations (e.g., the books by [42, 57, 88, 89, 91, 100, 102]). One obstinate result in this literature is that updating rules of strategies–whether imitative or experiential–relying on payoff tend to converge to Nash equilibria [27, 42, 57]. Hence, in behavioral equilibrium, at the culturally stable or developmentally stable state, it is as if individuals strive to maximize the payoff function at hand and thus as if they are rational decision makers, in the sense that among a set of options they choose the one they prefer, given the others’ strategies [69]. The question of what should be the evolutionarily stable rule for individual strategy selection can thus here be phrased as: if the evolving trait is the payoff function to be maximized, which payoff function is evolutionarily stable? This is the question that the literature on preference evolution for strategic interactions addresses (e.g., [1, 2, 5,6,7, 29, 47, 54, 55, 79, 99]). Because information plays a central role in strategic interactions [43], the formalizations of preference evolution have covered a variety of informational scenarios (e.g., [29, 79, 99]; see [4, 9] for surveys). Focusing on the evolution of preferences gives hope to improve predictions about equilibrium behavior because payoff-based choice rules can otherwise come in endless mechanistic forms—some more biologically and cognitively inspired than others [87, 92] but none empirically fully elucidated (e.g., [59]).
The goal of this paper is to contribute to the literature on the evolution of rules guiding individual behavior in two ways and is thus divided in two parts. In the first part, we connect a number of concepts and results to analyze the long-term evolution (sensu [33, 34]) of behavioral mechanisms for equilibrium action in group-structured populations. This part can thus be read as a methodological review. In the second part, we push forward within this framework the evolutionary analysis of the class of preferences involving a mix between self-interest and an interest in evaluating own behavior in the light of the consequences for own payoff if others adopted this behavior. This is the class of semi-Kantian preferences, which, in the words of [17, p. 191], can be seen as hybrid preferences combining the categorical imperative of Nash with that of Kant. [15] shows that the evolutionarily stable strategy in interactions between siblings could be interpreted as if individuals had such preferences, an interpretation that should hold more generally when interactions occur between related individuals. Semi-Kantian preferences have then indeed been shown to be evolutionarily stable and uninvadable under various transmission rules when population structure results from limited genetic or cultural mixing among interacting individuals, when interacting individuals cannot observe each other’s preferences [7, 8, 11]. However, so far the evolutionary convergence towards semi-Kantian preferences has not been ascertained, and their evolution has not been analyzed under different informational assumptions. Our goal is to analyse convergence stability and uninvadability of semi-Kantian preferences in three different informational scenarios: (a) incomplete information; (b) complete information and incomplete plasticity (interacting individuals can observe each other’s preferences, but an individual’s preferences do not depend on the other’s preferences); and (c) complete information and complete plasticity (interacting individuals can observe each other’s preferences, and an individual’s preferences can depend on the other’s preferences). It will be seen that the different informational and plasticity assumptions lead to quite different evolutionary outcomes, and that we are not always able to reach general conclusions about convergence stability.
Our aim is not to obtain the most general conclusions about the open questions we address, but rather to illustrate how demographic and informational features jointly contribute to the understanding of the long-term evolution of preferences in structured populations. As such, we consider only pairwise interactions and restrict attention to the parametric class of semi-Kantian preferences and the evolution of the Kantian coefficient, a quantitative trait varying between zero and one, which represents the weight attached to the Kantian interest.
2 Evolutionary Invasion Analysis of Behavioral Mechanisms
2.1 Biological Assumptions for Pairwise Interactions
We consider a population of asexually reproducing individuals that are demographically homogeneous (no effective age, stage or sex structure). The population occupies a habitat with an infinite and constant number of groups (or demes, or spatial subdivisions), each of which is occupied by exactly two individuals and so the population is of constant size. Each individual is characterized by a type belonging to a type space \(\Theta \) that affects its phenotype—the collection of any relevant morphological, physiological or behavioral measurable feature of the individual. We consider a demographic process where the population is censused at discrete time steps, between which the following events occur in cyclic order. (a) In each group, the pair of individuals engage in an interaction. Some process (learning, exchange of information, etc) leads to a pair of equilibrium strategies being expressed. The equilibrium strategy pair, which may depend on the individuals’ types as well as the types present in the population at large, determines some outcome (for example, the material payoff of each individual). (b) Each individual in each group produces a large number of juveniles according to the outcome of the pairwise interaction and eventually dies subject to some death process,Footnote 1 which may also depend on the outcome of the pairwise interaction. (c) Juveniles remain in the natal group with some fixed probability. With complementary probability \(m>0\), assumed to be nonzero, they migrate out of their natal group and survive dispersal with a certain probability that may depend on the outcome of the interaction between the juvenile’s parent and its neighbor. (d) In each group, the open reproductive spots vacated by deceased adults are randomly filled up by competing juveniles, who then become adults.
2.2 Invasion and Individual Fitness
We adopt a standard invasion analysis framework and consider a population that is monomorphic for some resident type \(\theta \in \Theta \) in which a mutant type \(\tau \in \Theta \) arises (e.g., [14, 24, 35, 37, 38, 74, 80, 95]). It then follows from applications of invasion analysis to our demographic process assumptions of Sect. 2.1 (see Box 1) that any mutation \(\tau \in \Theta \), which is introduced in a single individual in a monomorphic population with the resident type \(\theta \in \Theta \), eventually goes extinct with probability one if and only if the invasion fitness (the geometric growth ratio) of the mutant type, denoted \(W(\tau ,\theta )\), satisfies
Here, the “1” can be interpreted as the growth ratio of a resident type in a monomorphic resident population, which, owing to the fact that the population is of constant size can, on average, only replace itself (i.e., \(W(\theta , \theta )=1\) for all \(\theta \in \Theta \)).
Invasion fitness can be represented as the individual fitness of a randomly sampled mutant \(\tau \) descending from the individual in which the mutation initially appeared, averaged over the cases where the mutant interacts with another member of the same lineage and those where it interacts with an individual from a different lineage (who is thus of the resident type \(\theta \)):
Here, \(\tilde{w}_i(\tau , \theta )\) is the individual fitness of a mutant when there are \(i\in \{1,2\}\) mutants in its group and the population is otherwise monomorphic for \(\theta \), and \(r(\tau , \theta )\) is the pairwise relatedness between a \(\tau \) mutant and its group neighbor (see Box 1 for a derivation of Eq. (2)). Pairwise relatedness is the probability that, conditional on an individual being of type \(\tau \), the group neighbor belongs to the same ancestral lineage and is thus also of type \(\tau \), whereby both individuals are identical-by-descent [68]; note that since migration is assumed nonzero, we have \(r(\tau , \theta )<1\). Whether relatedness \(r(\tau , \theta )\) depends on both the mutant and the resident type, only on the resident type, or neither, depends on demographic and interaction assumptions. For instance, relatedness is independent of the types for family-structured populations, in which case it is determined only by the pedigree relatedness, e.g. \(r=1/2\) for full-siblings [as implied by the model of [75], which also entails that Eq. (2) applies to sexual reproduction in family-structured populations in the absence of inbreeding].
When \(W(\tau , \theta )\) is differentiable (which is not always the case), a resident type \(\theta ^*\) is locally convergence stable if and only if the first two following conditions hold, while it is locally uninvadable if the first and the third conditions hold [25, 32, 44, 93]:
Here, \(S(\theta )\), \(J(\theta )\), and \(H(\theta )\), stand, respectively, for the selection gradient, the selection Jacobian, and the selection Hessian, evaluated at the resident type \(\theta \). A type satisfying \(S(\theta ^*)=0\) will be called a singular type (or a singularity).Footnote 2 There is a non-trivial relationship between the static conditions (3–5) obtained from invasion fitness and dynamic stability. Namely, for mutants with small effects on the phenotype, i.e. the difference \(\vert \theta -\tau \vert \) is small, a singular type \(\theta ^*\) satisfying conditions (4–5) is a (i) local attractor of the evolutionary dynamics under gradual evolution and (ii) resistant to invasion by small deviations.Footnote 3
2.3 Behavioral Equilibrium
In applications of evolutionary game theory, an individual’s type is often taken to be its strategy to be applied in the interaction at hand. Yet many applications require to decouple types from strategies. In order to do this and obtain a full description of how individual fitness depends on own type and neighbor’s type — a dependence that in Eq. (2) was captured through the mappings \(\tilde{w}_1: \Theta ^2 \rightarrow \mathbb {R}_{+}\) and \(\tilde{w}_2: \Theta ^2 \rightarrow \mathbb {R}_{+}\), without reference to the strategies used by the individuals — we begin by defining individual fitness as a function of the strategies used, and then we introduce notation and assumptions for how the equilibrium strategies depend on the types.
Letting \(\mathcal {X}\) denote the set of strategies that each individual has access to when interacting with its neighbor, the individual fitness function \(w:\mathcal {X}^3\rightarrow \mathbb {R}_{+}\) is defined such that \(w(x_i, x_{j},y)\) gives the expected number of descendants (including the surviving self) produced over one demographic time period by an adult individual i expressing strategy \(x_i\) when matched to a group neighbor j expressing strategy \(x_{j}\), when individuals in the population at large all use strategy y. Note that any individual fitness function is subject to the demographic consistency relation \(w(y,y,y)=1\) for all \(y \in \mathcal {X}\) and an example thereof is provided in Box 2.
Turning now to the equilibrium strategies, in a population with a mutant type \(\tau \) and a resident type \(\theta \ne \tau \), each group either has zero, one, or two mutants. For groups with two residents (resp. two mutants), we denote by \(y^*_\textrm{s}(\theta )\) (resp. \(x^*_\textrm{s}(\tau ,\theta )\)) an equilibrium strategy for each individual, where the subscript “\(\textrm{s}\)” refers to same type (note that we rule out equilibria in which two identical individuals use different strategies). For mixed groups, with one resident and one mutant, let \(x^*_\textrm{d}(\tau ,\theta )\) denote the mutant’s equilibrium strategy and \(y^*_\textrm{d}(\theta ,\tau )\) the resident’s equilibrium strategy, where the subscript “\(\textrm{d}\)” stands for different types. Importantly, throughout we assume that for any type pair \((\theta ,\tau )\in \Theta ^2\) with \(\theta \ne \tau \), there exist unique equilibrium strategies \(y^*_\textrm{s}(\theta )\), \(x^*_\textrm{s}(\tau ,\theta )\), and (\(x^*_\textrm{d}(\tau ,\theta ),y^*_\textrm{d}(\theta ,\tau )\)). In a population with a mutant \(\tau = \theta \) interactions can occur between same and different lineage members having the same type. For this case, we assume that all individuals in all pairs use the same strategy \(y^*_\textrm{s}(\theta )=x^*_\textrm{s}(\theta ,\theta )\) since they have the same type. This implies that the mappings \(\tilde{w}_1\) and \(\tilde{w}_2\) used in Eq. (2) are well defined,Footnote 4 as follows:
and
How do the equilibrium strategies arise? In the evolutionary game theory literature, a variety of processes, or mechanisms, of interdependent strategy expression have been examined, including reactive strategies, behavior response rules, learning rules, or developmental rules (e.g., [1, 12, 30, 62, 70, 72, 73, 94]). In each case, a dynamical system drives strategy expression over time, and under some conditions these behavioral dynamics reach an equilibrium. One way to formalize these mechanisms is to posit that the equilibrium strategies solve a fixed-point problem. Thus, for mixed groups, let there be two mappings, \(M_\textrm{d}:\Theta ^2\times \mathcal {X}^2 \rightarrow \mathbb {R}\) for the mutant type and \(R_\textrm{d}:\Theta \times \mathcal {X}^2 \rightarrow \mathbb {R}\) for the resident type, which capture the process at hand, and which are such that an equilibrium pair of strategies satisfies the fixed-point system of equations:
The mechanism \(M_\textrm{d}\) is parametrized by both the mutant and the resident type, while \(R_\textrm{d}\) is parametrized only by the resident type. This is so because when individuals interact their strategy may depend on (i) their own type and strategy, (ii) the strategy of their interaction partner, and (iii) on strategies in the population at large, which depends only on the resident type when the mutant is rare (see also Eq. 10 below). Solving for \(x^*_\textrm{d}\) and \(y^*_\textrm{d}\) produces the dependence of each strategy on both types, i.e., \(x^*_\textrm{d}=x^*_\textrm{d}(\tau ,\theta )\) and \(y^*_\textrm{d}=y^*_\textrm{d}(\theta ,\tau )\).
For the equilibrium strategy used in mutant–mutant interactions, let there be a mapping \(M_\textrm{s}:\Theta ^2 \times \mathcal {X} \rightarrow \mathbb {R}\) which describes the process whereby a mutant interacts with another mutant as a function of the partner’s strategy. The strategy in equilibrium is then assumed to satisfy the fixed-point equation
The behavioral mechanism \(M_\textrm{s}\) is parametrized by both the mutant and the resident type, because the strategy used in the population at large (which depends on the resident type) may affect the strategy used in a mutant–mutant pair. Hence, the solution of Eq. (9) implicitly defines the equilibrium strategy as a function of both \(\tau \) and \(\theta \), so that we can write \(x^*_\textrm{s}(\tau ,\theta )\). Finally, for the equilibrium strategy in resident-resident interactions, the equilibrium strategy \( y^*_\textrm{s}(\theta )\) is assumed to solve the fixed-point equation
where \(R_\textrm{s}:\Theta \times \mathcal {X} \rightarrow \mathbb {R}\) is the behavioral mechanism characterizing the (same) equilibrium strategy of each individual in a resident pair. By contrast to the equilibrium strategy between two mutants, which depends both on the mutant and the resident type, the equilibrium strategy between two residents depends only on the resident type.
2.4 Nash Equilibrium and Utility Function
Many formalizations of the behavioral fixed points (8–10) consist in assuming that strategies equilibrate by being guided by some payoff function and adopting assumptions such that the dynamics lead to a Nash equilibrium according to this payoff function. In such models, the mappings \(R_\textrm{s}\), \(R_\textrm{d}\), \(M_\textrm{s}\), and \(M_\textrm{d}\) can be thought of as describing the best response functions according to the payoff function. In equilibrium, it is thus as if individuals maximize this payoff function, given the strategy used by the opponent. One class of such models takes the payoff function to be a utility function, which represents an individual’s preferences.Footnote 5 In our setting, given some resident utility function determined by \(\theta \) and some mutant utility function determined by \(\tau \), the strategy \(y^*_\textrm{s}(\theta )\) (resp. \(x^*_\textrm{s}(\tau ,\theta )\)) would be the strategy in \(\mathcal {X}\) that maximizes the utility of a resident (resp. that of a mutant), given that the resident (resp. mutant) with whom it interacts also uses strategy \(y^*_\textrm{s}(\theta )\) (resp. \(x^*_\textrm{s}(\tau ,\theta )\)). Likewise, the strategy \(y^*_\textrm{d}(\theta ,\tau )\) would be the strategy in \(\mathcal {X}\) that maximizes the utility of the resident, given that the mutant with whom it interacts uses strategy \(x^*_\textrm{d}(\tau ,\theta )\), while the strategy \(x^*_\textrm{d}(\tau ,\theta )\) would be the strategy in \(\mathcal {X}\) maximizing the mutant’s utility, given that the resident with whom it interacts uses strategy \(y^*_\textrm{d}(\theta ,\tau )\).
We endorse this approach and rely on results showing that among the set of all continuous utility functions, a utility function representing semi-Kantian preferences emerges as being particularly viable from an evolutionary perspective [7, 11]. For some individual who uses strategy x when it neighbor uses strategy y, and given that strategy \(y^*\) is played at large in the population, this utility function is defined as
where w is the individual fitness function defined above and \(\kappa \in [0,1]\). The first is the individual’s realized fitness, given the strategies used. The second term is the fitness that the individual would realize if—hypothetically—the opponent used the same strategy (x) instead of strategy y; since the individual thereby evaluates what would happen if others were to follow the same course of action as itself, the second term can be interpreted as capturing a form of the first formulation of Kant’s categorical imperative: “act as if the maxims of your action were to become through your will a universal law of nature” [60]. These preferences were dubbed Homo moralis [7], yet they apply regardless of the organism under consideration in our life-cycle assumptions of Sect. 2.1. We will call the parameter \(\kappa \) the Kantian coefficient and our goal is to investigate its evolution under three different scenarios: (a) incomplete information, (b) complete information with incomplete plasticity, and (c) complete information with complete plasticity. Each of these scenarios, together with the utility function (11), defines a specific set of behavioral mechanisms (8–10), detailed in the next section.
3 Evolution of the Kantian Coefficient
For simplicity, we restrict attention to settings where w is twice continuously differentiable and the utility function (11) is strictly concave in its first argument for any \(\theta \in [0,1]\). We further take the strategy space \(\mathcal {X}\) to be an open and convex subset of \(\mathbb {R}\). These assumptions together imply that any equilibrium strategy must satisfy first-order conditions, and this facilitates the analysis. To rule out trivial settings in which an individual’s strategy has no impact on the opponent’s fitness, we also assume that \(\partial w(x,y,z)/\partial y \ne 0\) for all \((x,y,z)\in X^3\). We further assume that the sign of this effect is independent of the strategies used, and by convention, we let \(\partial w(x,y,z)/\partial y > 0\) for all \((x,y,z)\in X^3\), meaning that an increase in the strategy of an individual’s partner enhances the individual’s fitness.Footnote 6 Finally, we assume that \(\partial ^2 w(x,y,z)/\partial y \partial x\) has the same sign for all \((x,y,z)\in X^3\), and we will say that the strategies are strategic complements if \(\partial ^2 w(x,y,z)/\partial y \partial x>0\), strategic substitutes if \(\partial ^2 w(x,y,z)/\partial y \partial x<0\), and strategically neutral if \(\partial ^2 w(x,y,z)/\partial y \partial x=0\).
3.1 Incomplete Information
3.1.1 Behavioral Equilibrium
Under incomplete information, an individual’s type is the value of their Kantian coefficient taking a value in the interval [0, 1], and an individual cannot observe the type of its interaction partner. Still, the individual can have information about the matching distribution in the pairwise interaction, i.e., the probability that the partner belongs to the same lineage. One-shot interactions between perfect strangers are examples of this kind of interaction, as are interactions between family members when the only available information is their degree of kinship. We assume that individuals hold the belief that the probability of being matched with an individual from the same lineage is given by \(r(\tau ,\theta )\), which is a correct belief in the sense that a randomly drawn mutant in the lineage started by the initial mutant, faces the probability \(r(\tau ,\theta )\) of being matched with another mutant. Given these assumptions, an individual can condition its strategy only on the strategy that it expects its partner to use, given the belief on the matching distribution. Since any individual uses the same strategy whether the neighbor has the same or a different type, we simplify the notation by setting \(x^*_\textrm{s}=x^*_\textrm{d}= x^*\) and \(y^*_\textrm{s}=y^*_\textrm{d}= y^*\), where \(x^*\) is the equilibrium strategy of mutants and \(y^*\) that of residents. A strategy pair \((x^*,y^*)\) is a (Bayesian) Nash equilibrium if (a) \(y^*\) is a preferred strategy for a resident, given that other residents use strategy \(y^*\); and (b) \(x^*\) is a preferred strategy for a mutant, given that residents use \(y^*\) and the other mutants use \(x^*\), and given that the mutant applies the belief that the probability of being matched with another mutant is
where on the right-hand side relatedness is expressed in terms of the equilibrium strategies of mutant and resident individuals. Formally \(\tilde{r}:\mathcal {X}^2\rightarrow [0,1]\) so that \(\tilde{r}(x,y)\) is the relatedness of a mutant towards a random group member when mutants play strategy x and residents play strategy y [a concrete example thereof is obtained by setting \(x^*_\textrm{s}=x^*_\textrm{d}= x^*\) and \(y^*_\textrm{s}=y^*_\textrm{d}= y^*\) into the right-hand side of Eq. (B-k) of Box 2]. Thus, \((x^*,y^*)\) solves the fixed point system
which is fully in line with the model in [11, Eqs. 1 and 5] and where the utility functions \(u_{\theta }\) and \(u_{\tau }\) are defined in Eq. (11).Footnote 7 The behavioral fixed point (13) defines the behavioral mechanisms (8–10), which here satisfy \(M_\textrm{d}(\tau ,\theta ,x^*, y^*)=M_\textrm{s}(\tau ,\theta ,x^*)=0\) and \(R_\textrm{d}(\theta ,y^*,x^*)=R_\textrm{s}(\theta ,y^*)=0\), since an individual’s strategy choice cannot be conditioned on the interactant’s type.
Under our mathematical assumptions, the (assumed unique) equilibrium pair of strategies satisfies the necessary first-order conditions for the maximization problems in Eq. (13):
Using Eq. (11), these equations become
where the second equality of the first line shows that the marginal change in utility can be expressed as the sum of the effect of own behavior on own fitness and the fitness of the partner weighted by the Kantian coefficient \(\theta \). The necessary second-order conditions for \((x^*(\tau ,\theta ), y^*(\theta ))\) defined by (14) to be maxima rather than minima are:
These inequalities hold strictly by virtue of the assumption that \(u_{\theta }\) is strictly concave in its first argument. Hence:
This inequality can in turn be used to evaluate how the mutant’s equilibrium strategy would change if the mutant trait value changed. To see this, by applying the implicit function theorem, one obtains by totally differentiating the second line of Eq. (15) with respect to \(\tau \) and solving the resulting linear equation for \(\partial x^*(\tau ,\theta )/\partial \tau \):
This (local) mutant behavioral perturbation, which will be seen to play a central role in the evolutionary analysis, is always positive, i.e., \(\left. \partial x^*(\tau ,\theta )/\partial \tau \right| _{\tau =\theta } >0\) (see Appendix A for a proof). The intuition is that by making the individual attach a greater value to the effect that the strategy would have on self if it was also adopted by the other individual, an increase in \(\tau \) makes the individual internalize the positive externality (\(\partial w(x,y,y^*)/\partial y\)) that the other’s strategy has on self.
3.1.2 Evolutionary Equilibrium
Turning now to the analysis of selection on the Kantian coefficient, invasion fitness writes
which is differentiable (since individual fitness is differentiable so will be \(r(\tau ,\theta )\), see Box 1). Then, substituting Eq. (19) into \(S(\theta )=\left. \partial W(\tau , \theta )/\partial \tau \right| _{\tau =\theta }\), the selection gradient is
because the term multiplying \(\partial r(\tau ,\theta )/\partial \tau \) is \(\left. w(x^*(\tau ,\theta ), x^*(\tau ,\theta ), y^*(\theta ))\right| _{\tau =\theta }-\left. w\!\left( x^*(\tau ,\theta ), y^*(\theta ), y^*(\theta ) \right) \right| _{\tau =\theta }=0\). Selection on the Kantian coefficient thus depends on the (local) mutant behavioral perturbation weighted by the inclusive fitness effect at the strategy level, i.e. the sum of the direct effect, \(\partial w(x,y^*,y^*)/\partial x\), and the indirect effect, \(\partial w(x^*,x,y^*)/\partial x\), on fitness weighted by neutral relatedness. Moreover, since \(\partial w(x,y^*,y^*)/\partial x=-\theta \partial w(y^*,y,y^*)/\partial y\) at \(\tau =\theta \) and \(x^*=y^*\) (see Eq. 15), we obtain that
Since (by assumption) \(\partial w(x,y,y^*)/\partial y \ne 0\) for all \((x,y,y^*)\in X^3\), which also implies that \(\partial x^*(\tau ,\theta )/\partial \tau \ne 0\) (see Eq. 18), this selection gradient shows that the unique singular trait value is
But is \(\theta ^*\) convergence stable and uninvadable?
Let us first consider convergence stability, by determining whether the Jacobian
is strictly negative. Since the term in the square brackets is strictly positive, we immediately obtain that \(\theta ^*=r(\theta ^*,\theta ^*)\) is convergence stable if and only if \(\mathop {}\!\textrm{d}r(\theta ,\theta )/\mathop {}\!\textrm{d}\theta <1\).
What about local uninvadability? To ascertain this, we examine whether the Hessian is strictly negative. Given that \( \partial w(x,y^*,y^*)/\partial x=-\theta \partial w(y^*,x,y^*)/\partial x\) when \(\tau =\theta \) (as noted already above), we obtain:
Since \(K\left( r(\theta ^*,\theta ^*)\right) <0\), the first term is strictly negative. Hence, a sufficient condition for \(\theta ^*=r(\theta ^*,\theta ^*)\) to be (locally) uninvadable is that the local perturbation of relatedness, \(\partial r(\tau , \theta )/\partial \tau \), be nil. The relatedness perturbation can be different from zero, however (for example, see Eq. (B-j) for the expression of \(r(\theta ,\tau )\) for a Moran process), and its sign typically depends on demographic and interaction assumptions in non-trivial ways. Moreover, it does not involve second-order derivatives of individual fitness [78], and thus does not vary systematically according to the strategic substitutability or complementarity of the strategies. Hence, in settings where behavior affects relatedness \(\partial r(\tau , \theta )/\partial \tau \ne 0\), it is challenging to identify general conditions that would guarantee that \(J(\theta ^*)<0\) and \(H(\theta ^*)<0\). Yet, it is known that in certain settings (summarized below) both \(\mathop {}\!\textrm{d}r(\theta ,\theta )/ \mathop {}\!\textrm{d}\theta \) and \(\partial r(\tau , \theta )/\partial \tau \) are negligible. We refer to this as weak trait effects on relatedness. We can then summarize sufficient conditions for the Kantian coefficient to be evolutionarily stable as follows, where
Result 1
When interactions take place under incomplete information, the Kantian coefficient equal to the neutral relatedness, \(\theta ^*=r(\theta ^*,\theta ^*)\), is the unique singular trait value. It is both an evolutionary attractor (convergence stable) and locally uninvadable if trait effects on relatedness are sufficiently weak. More precisely, \(\theta ^*=r(\theta ^*,\theta ^*)\) is convergence stable if and only if \(\mathop {}\!\textrm{d}r(\theta ,\theta )/\mathop {}\!\textrm{d}\theta <1\) and it is locally uninvadable if and only if \(\partial r(\tau , \theta )/\partial \tau <T\) evaluated at \(\theta =\theta ^*\).
While the condition for uninvadability is consistent with the results of [11],Footnote 8 our analysis reinforces those results by identifying a sufficient condition for the Kantian coefficient equal to neutral relatedness to be also convergence stable. When these conditions are satisfied, individuals in a population at the evolutionary equilibrium will thus behave according to Hamilton’s (marginal) rule at the strategy level, i.e., their behavioral equilibrium \(y^*\) satisfies
where the value of relatedness may depend endogenously on the strategy.
Interestingly, many biological scenarios do exhibit weak, or even nil, trait effects on relatedness whereby \(\tilde{r}(y^*,y^*)=\tilde{r}\) is independent of \(y^*\) in Eq. (26).Footnote 9 First, in family-structured populations, which cover a large class of interactions (e.g., parent-offspring interactions, interactions between sibling or cousins, etc...), relatedness is independent of the types (\(\mathop {}\!\textrm{d}r(\theta ,\theta )/\mathop {}\!\textrm{d}\theta = \partial r(\tau , \theta )/\partial \tau = 0\)). Second, relatedness is also independent of the types in spatially-structured populations when selection is weak in the sense that the strategies in the interaction affect fitness only marginally (see, e.g., [11]). Such independence can extend to cases where effects are not so marginal because when the migration probability is exogenous, both \(\mathop {}\!\textrm{d}r(\theta ,\theta )/ d \theta \) and \(\partial r(\tau , \theta )/\partial \tau \) tend to be negligible for several games [78, 98]. Finally, for certain demographic processes, like the Moran process when behavior affects only reproduction, one has \(\mathop {}\!\textrm{d}r(\theta ,\theta )/\mathop {}\!\textrm{d}\theta =0\) and \(\partial r(\tau , \theta )/\partial \tau = 0\) [78], but, as implied by Eq. (B-k) of Box 2, the relatedness perturbation is nonzero in the Moran process when behavior affects survival.
3.2 Complete Information with Incomplete Plasticity
3.2.1 Behavioral Equilibrium
Under complete information individuals have information about the type of their interaction partner, which is here again taken to be the partner’s Kantian coefficient taking values in the interval [0, 1]. However, an individual’s own utility function cannot be conditioned on that information: this is what we mean by incomplete plasticity. Because individuals can observe the type composition of their group, whenever the mutant type differs from the resident type, the distinction between a mutant’s equilibrium strategies \(x^*_\textrm{d}\) and \(x^*_\textrm{s}\), as well as between a resident’s equilibrium strategies \(y^*_\textrm{d}\) and \(y^*_\textrm{s}\), is relevant, as per the behavioral mechanisms (8–10). Hence, the equilibrium strategy \(y^*_\textrm{s}\) used by each resident in an interaction with another resident satisfies
the equilibrium strategy \(x^*_\textrm{s}\) used by each mutant in an interaction with another mutant satisfies
and the equilibrium pair of strategies (\(x^*_\textrm{d},y^*_\textrm{d}\)) used by a mutant and a resident, respectively, in a mutant-resident interaction solves the fixed point system
The fixed point Eqs. (27–29) define the behavioral mechanisms (8–10) under complete information with incomplete plasticity. Note that if \(\tau =\theta \) in Eq. (29), then \(x^*_\textrm{d}(\theta ,\theta )=y^*_\textrm{d}(\theta ,\theta )\) owing to the strict concavity of u in its first argument, which implies that to each strategy played by the opponent there exists a unique best response. Hence, if \(\tau =\theta \),
As in the incomplete information scenario, in the evolutionary analysis we use the expressions that capture how the equilibrium strategies are modified by marginal changes in the mutant trait and the resident trait. To obtain these behavioral perturbations, we first write the necessary first-order conditions for (\(x^*_\textrm{d}, y^*_\textrm{d}\)) to be a Nash equilibrium:
Therein, the monomorphic resident behavioral equilibrium \(y^*_\textrm{s}\) solves
where the second equality shows that the marginal change in utility in the resident population can, as under incomplete information, be expressed as the sum of the effect of own behavior on own fitness and the fitness of the partner weighted by the Kantian coefficient \(\theta \). Since \(u_{\theta }\) is strictly concave in its first argument, the second-order partial derivative of \(u_{\theta }\), evaluated at \(y^*_\textrm{s}(\theta )=y^*_\textrm{d}(\theta ,\theta )\), is strictly negative:
The system of equations in Eq. (31) together implicitly define \(x^*_\textrm{d}\) and \(y^*_\textrm{d}\) as functions of \(\tau \) and \(\theta \). Applying the implicit function theorem, we obtain the following expressions for the behavioral perturbation of the equilibrium strategy of a mutant and of a resident with respect to the mutant trait value, evaluated locally at \(\tau =\theta \):
In the evolutionary analysis, it is the ratio of the resident’s to the mutant’s behavioral perturbation that will matter:
This is well defined, since the assumption \(\partial w(y^*_\textrm{d},y,y^*_\textrm{d})/\partial y\ne 0\) implies \(\partial x^*_\textrm{d}(\tau ,\theta )/\partial \tau \ne 0\), which means that the equilibrium strategy of mutants always changes as a result of a marginal change in the mutant trait value. Because \(\rho (\theta )\) measures the extent to which an individual’s neighbor’s strategy varies with own strategy variation, we follow previous terminology and refer to \(\rho (\theta )\) as the response coefficient [2]. Inserting Eqs. (34) and (35) into Eq. (36), we obtain
implying that the response coefficient has the same sign as \(\partial ^2 w(x,y,y^*_\textrm{d})/\partial x \partial y\), and this will play a role in the analysis of selection on the Kantian coefficient, to which we now turn.
3.2.2 Evolutionary Equilibrium
To begin, note that Eq. (30) implies that we can write invasion fitness (2) as follows:
which is differentiable. Substituting this into the selection gradient \(S(\theta )=\left. \partial W(\tau , \theta )/\partial \tau \right| _{\tau =\theta }\), and simplifying yields (since the term multiplying \(\partial r(\tau ,\theta )/\partial \tau \) is \(\left. w(x^*_\textrm{d}(\tau ,\tau ), x^*_\textrm{d}(\tau ,\tau ), y^*_\textrm{d}(\theta ,\theta ))\right| _{\tau =\theta }-\left. w\!\left( x^*_\textrm{d}(\tau ,\theta ), y^*_\textrm{d}(\theta ,\tau ), y^*_\textrm{d}(\theta ,\theta ) \right) \right| _{\tau =\theta }=0\)):
From Eq. (32), we can write \((1-\theta )\partial w(y,x^*_\textrm{d},y^*_\textrm{d})/\partial y+\theta \partial w(y,x^*_\textrm{d},y^*_\textrm{d})/\partial y+\theta \partial w(x^*_\textrm{d},y,y^*_\textrm{d})/\partial y=0\) at \(\tau =\theta \) where \(x=y=y^*_\textrm{s}=x^*_\textrm{d}=y^*_\textrm{d}\). Therefore, we can replace \(\partial w(x,y^*_\textrm{d},y^*_\textrm{d})/\partial x=\partial w(y,y^*_\textrm{d},y^*_\textrm{d})/\partial y\) by \(-\theta \partial w(x^*_\textrm{d},y,y^*_\textrm{d})/\partial y\) in Eq. (39), to obtain
Comparing Eq. (40) to the selection gradient under incomplete information (see Eq. 21), we see that if the response coefficient is nil, i.e., if \(\rho (\theta )=0\), the two selection gradients are identical, and \(\theta = r(\theta ,\theta )\) is then the unique singularity. This is not surprising since under incomplete information changes in the mutant trait value has no effect on the resident’s equilibrium strategy. We further observe that when \(\theta =1\), then \(\rho (\theta )=0\); using Eq. (34) in Eq. (40), the selection gradient at \(\theta =1\) is thus
Since \(\tilde{K}(1)<0\) and \(r(\theta ,\theta )<1\) for all \(\theta \in [0,1]\), we obtain \(S(1)<0\), which implies that \(\theta =1\) is always counter-selected, and can neither be convergence stable nor uninvadable. By contrast, nothing allows to rule out that \(\theta =0\) could be convergence stable and/or uninvadable. More generally, since \(\partial w(x^*_\textrm{d},y,y^*_\textrm{d})/\partial y \ne 0\) (by assumption), Eq. (40) implies that \(S(\theta )=0\) if and only if
Let \(\tilde{\theta }\) denote a solution to this equation. Since \(r(\theta ,\theta )<1\) for all \(\theta \in [0,1]\), so that \(1-\theta r(\theta ,\theta )>0\) for any \(\theta \in [0,1]\), it follows immediately from Eq. (42) that \(\tilde{\theta }=r(\tilde{\theta })\) if \(\rho (\tilde{\theta })=0\), \(\tilde{\theta }>r(\tilde{\theta })\) if \(\rho (\tilde{\theta })>0\), and \(\tilde{\theta }<r(\tilde{\theta })\) if \(\rho (\tilde{\theta })<0\). Recalling that the sign of \(\rho (\theta )\) depends on the sign of \(\partial ^2 w(x,y,y^*_\textrm{d})/\partial x \partial y\) (see Eq. (37)), and that we restrict the Kantian coefficient to take values between 0 and 1, the following result obtains.
Result 2
Let \(\theta ^*\) denote a singularity for the Kantian coefficient under complete information and incomplete plasticity, and \(\tilde{\theta }\) denote a solution to Eq. (42). Then:
-
(i)
\(\theta ^*=0\) if \(\tilde{\theta }\le 0\), which requires w to be such that strategies are strategic substitutes or strategically neutral;
-
(ii)
\(\theta ^*=\tilde{\theta }\) if \(\tilde{\theta }\in (0,1)\), in which case \(\theta ^*=[r(\theta ^*,\theta ^*)+\rho (\theta ^*)]/[1+ \rho (\theta ^*)r(\theta ^*,\theta ^*) ]\). In particular, \(\theta ^*=r(\theta ^*,\theta ^*)\) if w is such that strategies are strategically neutral, while \(\theta ^*<r(\theta ^*,\theta ^*)\) (resp. \(\theta ^*>r(\theta ^*, \theta ^*)\)) if w is such that strategies are strategic substitutes (resp. complements), and \(\theta ^*= \rho (\theta ^*)\) if \(r(\theta ^*,\theta ^*)=0\).
By contrast to the incomplete information setting where the Kantian coefficient must coincide with the coefficient of relatedness, here it can be either larger or smaller and the behavioral equilibrium \(y^*\) in a population at an evolutionary equilibrium \(\theta ^*\) now satisfies
where relatedness will be independent of the strategies (and types) under weak trait effects on relatedness. Whether the Kantian coefficient exceeds or falls short of relatedness depends on whether the fitness function exhibits, respectively, strategic complementarity or substitutability. The reason that strategic complementarity raises the Kantian coefficient above the value of relatedness stems from the fact that a mutation consisting in an increase in the Kantian coefficient then induces a positive correlated response in the strategy expression by its neighbor, implying that the marginal benefit of the Kantian coefficient is larger than under strategic neutrality (compare Eqs. 21–40). By contrast, under strategic substitutability, a mutation consisting in an increase in the Kantian coefficient has a negative impact on its neighbor’s equilibrium strategy, implying that the marginal benefit of the Kantian coefficient is smaller than under strategic neutrality.
Result 2 further shows that a singular Kantian coefficient can in principle take any value in the range [0, 1) depending on demographic and behavioral parameters. Interestingly, Eq. (42) along with Eq. (36) is identical to the corresponding equation in the model of [6] (see their Eq. (29)), wherein they examine the class of other-regarding utility functions whereby an individual may attach some evolving weight \(\alpha \in (-1,1)\) to the interactant’s individual fitness. Hence, Theorem 1 of this previous work also establishes that whether the exact value of the evolving weight \(\alpha \) exceeds or falls short of relatedness depends on whether the fitness function exhibits strategic substitutability, complementarity, or neutrality.Footnote 10
We now examine whether a Kantian coefficient \(\theta ^*\) of Result 2 is convergence stable and uninvadable. Due to the complexity of the expressions for the Jacobian \(J(\theta ^*)\) and the Hessian \(H(\theta ^*)\) coefficients at \(\theta ^*\) solving \(S(\theta ^*)=0\), presented in Appendix B, we were unable to reach generic answers to these questions, and further assumptions may be needed to reach more definite results. However, we verify that convergence stability and uninvadability can obtain, by resorting to an illustrating example. Consider a Moran demographic process (i.e. individual fitness takes the form of Eq. (B-i)) with constant death rate \(\mu \) and juvenile survival probability s, and that individual face a pairwise interaction such that their expected fecundity (number of offspring produced at stage (b) of the life cycle of Sect. 2.1) is linear-quadratic in the two players’ actions:
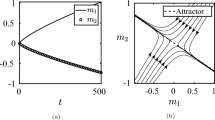
for parameters \(a,b,c \in \mathbb {R}\). Then, substituting Eq. (44) into individual fitness (B-i), we can evaluate the selection gradient (40), the Jacobian (A-10) and the Hessian (A-12) coefficients. Even for this simple example, Eq. (42) is a quartic function that cannot be solved explicitly and so we analyse the selection gradient numerically. Figure 1 displays how for fixed but different values of the backward migration rate \(m_\textrm{b}\) (Eq. B-l), \(\theta ^*\) varies when b is varied. Figure 1 shows that by depending on b, the Kantian coefficient takes a value above or below that of relatedness.
Each curve shows, for the Moran process analyzed in Box 2 with individual fitness (B-i), the singular Kantian coefficient \(\theta ^*\) under complete information and incomplete plasticity, for the linear quadratric fecundity function (44), as a function of parameter b in that function for \(a=0.1\) and \(c=1\). Each of the four lines corresponds to a different value of the “backward migration probability”, which depends on the exogenously given migration probability m (see Eq. (B-l) and the description following it). Starting from the top, the first line, where the Kantian coefficient remains essentially constant at \(\theta ^*=0.98\) is for \(m_\textrm{b}=0.01\) whereby \(r=(1-m_\textrm{b})/(1+m_\textrm{b})\approx 0.98\); the second line is for \(m_\textrm{b}=0.2\) whereby \(r=(1-m_\textrm{b})/(1+m_\textrm{b})\approx 0.66\); the third line for \(m_\textrm{b}=0.4\) whereby \(r=(1-m_\textrm{b})/(1+m_\textrm{b})\approx 0.42\); and the last line, where the Kantian coefficient varies over the range [0, 0.6], is for \(m_\textrm{b}=0.6\) whereby \(r=(1-m_\textrm{b})/(1+m_\textrm{b})=0.25\). By computing the Jacobian (A-10) and the Hessian (A-12) coefficients at these values we checked that all these singular Kantian coefficients are indeed both convergence stable and uninvadable
3.3 Complete Information and Plasticity
3.3.1 Behavioral Equilibrium
The defining assumption of our complete information with complete plasticity scenario is that individuals can not only observe the type of the interaction partner but also condition their preferences on it. Hence, the preferences applied in the interaction become state-specific on the interaction. Specifically, we assume that the type \(\theta =(\theta _{\textrm{d}},\theta _{\textrm{s}})\) of an individual is a two-dimensional quantitative trait (\(\theta \in [0,1]^2\)) such that \(\theta _{\textrm{s}}\) parametrizes an individual’s preference (still given by Eq. (11)) when individuals in a pair have the same type and \(\theta _{\textrm{d}}\) parametrizes an individual’s preference when individuals in a pair have different types.
In terms of the equilibrium strategies, consider some resident type \(\theta =(\theta _{\textrm{d}},\theta _{\textrm{s}})\) and some mutant type \(\tau =(\tau _{\textrm{d}},\tau _{\textrm{s}})\) that is different from \(\theta \) (either because \(\theta _{\textrm{d}}\ne \tau _{\textrm{d}}\), or because \(\theta _{\textrm{s}}\ne \tau _{\textrm{s}}\), or because both \(\theta _{\textrm{d}}\ne \tau _{\textrm{d}}\) and \(\theta _{\textrm{s}}\ne \tau _{\textrm{s}}\)). Then, a resident individual applies the Kantian coefficient \(\theta _{\textrm{s}}\) when interacting with another resident, in which case they both play the equilibrium strategy \(y^*_\textrm{s}\), satisfying
The solution thereof defines the equilibrium strategy as a function of only \(\theta _{\textrm{s}}\) and we write \(y^*_\textrm{s}(\theta _{\textrm{s}})\) when this dependence needs to be made explicit. In mutant–mutant interactions both individuals apply the Kantian coefficient \(\tau _{\textrm{s}}\) and they both use the equilibrium strategy \(x^*_\textrm{s}\), satisfying
This defines the equilibrium strategy as a function of both \(\tau _{\textrm{s}}\) and \(\theta _{\textrm{s}}\) (since \(y^*_\textrm{s}\) depends on \(\theta _{\textrm{s}}\)), which we write \(x^*_\textrm{s}(\tau _{\textrm{s}},\theta _{\textrm{s}})\). Finally, in mutant-resident pairs where \(\tau \ne \theta \), the mutant applies the Kantian coefficient \(\tau _{\textrm{d}}\) while the resident applies the Kantian coefficient \( \theta _{\textrm{d}}\), and the Nash equilibrium strategies \(x^*_\textrm{d}\) and \(y^*_\textrm{d}\) are best responses to each other according to these preferences:
which leads to the dependence of both equilibrium strategies on \(\tau _\textrm{d},\theta _\textrm{d}\), and \(\theta _{\textrm{s}}\) and we write \(x^*_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d},\theta _\textrm{s})\) and \( y^*_\textrm{d}(\theta _\textrm{d},\tau _\textrm{d},\theta _\textrm{s})\). In mutant-resident pairs with the same type, which occurs if individuals from different lineage interact but are of the same type \(\tau =\theta \), then each individual in the pair applies the Kantian coefficient \(\theta _\textrm{s}\) and therefore expresses strategy \(y^*_\textrm{s}(\theta _{\textrm{s}})\).
3.3.2 Evolutionary Equilibrium
The fixed point Eqs. (45–47) define the behavioral mechanisms (8–10) under complete information with complete plasticity and it follows that the invasion fitness can be written as
where
and
Each component of the mutant trait \(\tau =(\tau _{\textrm{d}},\tau _{\textrm{s}})\) thus affects invasion fitness differently. The first trait component, \(\tau _{\textrm{d}}\), only affects the part of invasion fitness \(W_\textrm{d}\) emanating from the interaction of a mutant with a resident. Invasion fitness is not differentiable in trait component \(\tau _\textrm{d}\) because, as emphasized by Eq. (49), there is generally a discrete jump in the equilibrium strategies at \(\tau _\textrm{d}=\theta _\textrm{d}\), from \((x^*_\textrm{d},y^*_\textrm{d})\) to \((y^*_\textrm{s},y^*_\textrm{s})\) since as long as \(\tau \ne \theta \), individuals in mutant-resident pairs play the equilibrium \((x^*_\textrm{d},y^*_\textrm{d})\), while at \(\tau =\theta \) the pair plays \((y^*_\textrm{s},y^*_\textrm{s})\) [see the example below for an illustration]. The second trait component, \(\tau _{\textrm{s}}\), not only affects the part of invasion fitness \(W_\textrm{s}\) emanating from the interaction of a mutant with another mutant, but also \(W_\textrm{d}\), since if \(\tau _\textrm{d}=\theta _\textrm{d}\) the resident applies the value \(\theta _\textrm{d}\) when interacting with a mutant if \(\tau _\textrm{s}\ne \theta _\textrm{s}\) but instead the value \(\theta _\textrm{s}\) if \(\tau _\textrm{s}=\theta _\textrm{s}\). The invasion fitness (48) is thus not differentiable in the mutant type \((\tau _\textrm{d},\tau _\textrm{s})\). Moreover, as will be shown and explained in detail in an example below, there is typically an infinite number of uninvadable types \(\theta \in [0,1]^2\). In spite of these challenges, we have identified two simple sufficient conditions for a type to be uninvadable (but we were unable to conclude on convergence stability).
To state our result, for any \(\theta _\textrm{d},\tau _\textrm{d}, \theta _\textrm{s}\in [0,1]\) define
and
Result 3
A sufficient condition for \(W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d},\theta _\textrm{s})\le 1\) for all \(\tau _\textrm{d}\in [0,1]\) and \(W_\textrm{s}(\tau _\textrm{s},\theta _\textrm{s}) \le 1\) for all \(\tau _\textrm{s}\in [0,1]\) (and thus \(W(\tau , \theta )\le 1\) for all \(\tau =(\tau _\textrm{d},\tau _\textrm{s})\in [0,1]^2\)) is that \(\theta =(\theta _\textrm{d},\theta _\textrm{s})=(\theta _\textrm{d}^*,1)\), where \(\theta _\textrm{d}^*\in [0,1]\) is such that \(\widetilde{W}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1) \ge \widetilde{W}(\tau _\textrm{d},\theta _\textrm{d}^*,1)\) for all \(\tau _\textrm{d}\in [0,1]\).
For a formal proof of this result, see Appendix C. To understand this result, note first that \(\theta _\textrm{s}=1\) guarantees that a mutant cannot achieve a higher fitness when interacting with another mutant, than a resident does when interacting with another resident. This value of the Kantian coefficient indeed implies that both individuals in the interaction act as “social planners”: they choose that strategy which, when chosen by both individuals, maximizes their fitness. Second, note that for \(\tau _\textrm{d}\ne \theta _\textrm{d}\), the system of Eq. (51) is mathematically equivalent to the system of equations that characterizes the equilibrium strategies between a resident and a mutant (see (47)), and \(\widetilde{W}(\tau _\textrm{d},\theta _\textrm{d},\theta _\textrm{s})\) is equivalent to \(W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d},\theta _\textrm{s})\).Footnote 11 Hence, the value \(\theta _\textrm{d}^*\) defined in the result is such that if residents apply \(\theta _\textrm{d}=\theta _\textrm{d}^*\) when interacting with mutants, the residents get a higher fitness than the mutants do in mutant-resident interactions, for any value of \(\tau _\textrm{d}\ne \theta _\textrm{d}\). Thus, \((\theta _\textrm{s},\theta _\textrm{d})=(\theta _\textrm{d}^*,1)\) is a “safe bet” as an uninvadable point.
However, and as mentioned before, there are typically many other uninvadable types. To see why, it is useful to draw a parallel between the function \(\widetilde{W}\), defined in Eq. (52), and the fitness of a mutant under the complete information and incomplete plasticity scenario when relatedness is equal to zero, defined in Eq. (38). These are mathematically equivalent, except that in Eq. (52) individuals in the resident population play strategy \(y_\textrm{s}^*(\theta _\textrm{s})\), where \(\theta _\textrm{s}\) may differ from \(\theta _\textrm{d}\). This parallel allows us to realize that the same arguments as for the derivation of Result 2 can be applied here, to conclude that a relevant candidate value for \(\theta _\textrm{d}^*\) is the one satisfying \(\theta _\textrm{d}^*=\max \{0,\tilde{\rho }(\theta _\textrm{d}^*)\}\) where
From (differentiable) fitness \(\widetilde{W}(\tau _\textrm{d},\theta _\textrm{d},\theta _\textrm{s})\) and following the same arguments as those leading up to Result 2, we know that an uninvadable type satisfying \(\theta _\textrm{d}^*=\tilde{\rho }(\theta _\textrm{d}^*)\) cannot be equal to one, i.e., \(\theta _\textrm{d}^*<1\). Based on the same argument as used in the previous paragraph, we have \(W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d}^*,1)\le \widetilde{W}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1)<\widetilde{W}(1,1,1)=1\). The inequality \(\widetilde{W}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1)<\widetilde{W}(1,1,1)\) follows from the fact that \(\theta _\textrm{s}=1\) implies that both individuals in the interaction act as “social planners” and thus maximize their fitness, and hence interaction partners with \(\theta _\textrm{d}^*<1\) do not act as social planners, thereby choosing a strategy that does not maximise their fitness (see also Appendix C).
We can thus conclude that \(\theta _\textrm{d}=\theta _\textrm{d}^*\) implies that \(W_\textrm{d}(\tau ,\theta )<1\) for any \(\tau _\textrm{d}\ne \theta _\textrm{d}^*\). Hence, we can further conclude that \(\theta =(\theta _\textrm{d},\theta _\textrm{s})=(\theta _\textrm{d}^*,1)\) implies that \(W(\tau ,\theta )<1\) for any \(\tau \ne \theta \). It is this discrete jump between the invasion fitness of any mutant \(\tau \ne \theta \) and the residents’ fitness that opens the door for the multiplicity of uninvadable types. For example, \((\theta _\textrm{d},\theta _\textrm{s})=(\theta _\textrm{d}^*-\varepsilon ,1)\) for some sufficiently small \(\varepsilon >0\) would also be uninvadable: with this resident type, a mutant can achieve a higher fitness than a resident in a mutant-resident interaction, but one can always find \(\varepsilon \) small enough so that this advantage would be too small to overcome the difference \(1-W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d}^*-\varepsilon ,1)\). Likewise, \((\theta _\textrm{s},\theta _\textrm{d})=(1-\varepsilon ,\theta _\textrm{d}^*)\) for some sufficiently small \(\varepsilon >0\) would also be uninvadable: with this resident type, mutants can achieve a higher fitness when interacting with each other than when two residents interact, but one can always find \(\varepsilon \) small enough so that this advantage would be too small to overcome the difference \(1-W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d}^*,1-\varepsilon )\). Note that this example further shows that \(\theta _\textrm{s}=1\) is not necessary for \(\theta \) to be uninvadable.
In order to illustrate Result 3, we work out an example assuming a constant relatedness of 1/2 and an individual fitness function of the form \(w( x_{i},x_{-i},y)=f(x_{i},x_{-i})/f(y,y)\), with fecundity \(f(x_i,x_{-i})=1+a x_i-b x_ix_{-i}-c x_i^{2}\) given by the linear-quadratic function (44). This model could be thought of as interactions between siblings in a family-structured semelparous population. Given these assumptions, the invasion fitness (48) is
with
and
In force of Eq. (45), the (Nash) equilibrium strategy for a resident pair is
while in force of Eq. (47), the strategies for a mutant-resident pair are
and in force of Eq. (46), the equilibrium strategy for a mutant pair is
For this model, we can also write for any \(\tau _\textrm{d},\theta _\textrm{d}\in [0,1]\) that
and the candidate uninvadable Kantian coefficient thus satisfies
which has a relevant root in the interval [0, 1] when \(b<0\) (which implies that the strategies are strategic complements), given by
It is straightforward to check, for instance by computing \(\partial ^2\widetilde{W}(\tau _\textrm{d},\theta _\textrm{d},1)/\partial \tau _\textrm{d}^2\) at \(\tau _\textrm{d}=\theta _\textrm{d}=\theta _\textrm{d}^*\), that there is a range of parameter values where this Kantian coefficient is uninvadable and this is illustrated in panel A of Fig. 2.
Pairwise invasibility plots. Panel A displays the difference \(\widetilde{W}(\tau _\textrm{d},\theta _\textrm{d},1)-\widetilde{W}(\theta _\textrm{d},\theta _\textrm{d},1)\) for all combinations of \(\theta _\textrm{d}\) (x-axis) and \(\tau _\textrm{d}\) (y-axis) values (and thus holding \(\theta _\textrm{s}=1\) fixed), for the parameter values \(a=0.1\), \(b=-0.5\) and \(c=1\) of the linear quadratic game (44) (\(\widetilde{W}(\tau _\textrm{d},\theta _\textrm{d},1\)) is thus defined by (60)). The difference is zero on the diagonal, since \(\tau _\textrm{d}=\theta _\textrm{d}\). The black region depicts all the combinations \((\theta _\textrm{d},\tau _\textrm{d})\) such that the difference is negative, while the white region outside the diagonal depicts all the combinations \((\theta _\textrm{d},\tau _\textrm{d})\) such that the difference is positive. The candidate given by Eq. (62) is \(\theta _\textrm{d}^*\approx 0.22\), which the graph shows is uninvadable. Panel B displays the difference \(W(\tau , \theta )-W(\theta , \theta )\) determined by Eqs. (54–59) of a mutant \(\tau =(\tau _\textrm{d},1)\) in a resident \(\theta =(\theta _\textrm{d},1)\) population for all combinations of resident \(\theta _\textrm{d}\) (x-axis) and mutant \(\tau _\textrm{d}\) (y-axis) trait values (and thus holding \(\theta _\textrm{s}=1\) and \(\tau _\textrm{s}=1\) fixed) for the parameter values \(a=0.1\) \(b=-0.5\) and \(c=1\) of the linear quadratic game (44). On the diagonal, the difference equals zero (and invasion fitness equals one) since \(\tau _\textrm{d}=\theta _\textrm{d}\). The black region depicts all combinations \((\theta _\textrm{d},\tau _\textrm{d})\) such that the difference is negative, i.e., \(W(\tau , \theta )<1\), so that the mutant \(\tau _\textrm{d}\) cannot invade, while the white region outside the diagonal depicts all combinations \((\theta _\textrm{d},\tau _\textrm{d})\) such that the difference is positive, \(W(\tau , \theta )>1\), so that the mutant can invade. The graph thus shows that all values of \((\theta _\textrm{d},1)\) with \(\theta _\textrm{d}\) below approximately 0.6 are uninvadable. There is thus a multiplicity of uninvadable types, which necessarily contains that of Panel A. Note that resident values above approximately \(\theta _\textrm{d}\approx 0.9\) are invadable by any mutation \(\tau _\textrm{d}< \theta _\textrm{d}\), while resident values between approximatively 0.6 and 0.9 are invadable by mutants with \(\tau _\textrm{d}=\theta _\textrm{d}-\delta \) for \(\delta >0\) large enough. C displays \(W(\tau , \theta )-W(\theta , \theta )\) determined by Eqs. (54–59) for a mutant \(\tau =(\tau _\textrm{d},\tau _\textrm{s})\) in a resident \(\theta =(\theta _\textrm{d},\theta _\textrm{s})\) population for all combinations of resident \(\theta _\textrm{s}\) (x-axis) and mutant \(\tau _\textrm{s}\) (y-axis) trait values holding \(\tau _\textrm{d}=\theta _\textrm{d}=\tilde{\rho }(\theta _\textrm{d})\) fixed and given by Eq. (61) under the parameter values \(a=0.1\) \(b=-0.5\) and \(c=1\) of the linear quadratic game (44). As for Panel B, the black region depicts all combinations \((\theta _\textrm{s},\tau _\textrm{s})\) such that the difference is negative, i.e., \(W(\tau , \theta )<1\), so that the mutant \(\tau _\textrm{s}\) cannot invade, while the white region outside the diagonal depicts all combinations \((\theta _\textrm{s},\tau _\textrm{s})\) such that the difference is positive, \(W(\tau , \theta )>1\), so that the mutant can invade. The graph thus shows that all values of \((\theta _\textrm{s},\tilde{\rho }(\theta _\textrm{d}^*))\) with \(\theta _\textrm{s}\) above approximately 0.5 are uninvadable
This example illustrates the two features of Result 3 discussed in general terms above. First, as long as \(\tau \ne \theta \), individuals in mutant-resident pairs play the equilibrium (58), while at \(\tau =\theta \), they play Eq. (57). This makes the strategies discontinuous at \(\tau _\textrm{d}=\theta _\textrm{d}\), which in turn implies that invasion fitness is not differentiable. Despite this discontinuity embedded in fitness \(W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d},\theta _\textrm{s})\) (Eq. 55), Result 3 shows that we can use the function \(\widetilde{W}(\tau _\textrm{d},\theta _\textrm{d},1)\) to straightforwardly calculate \(\theta _\textrm{d}=\theta _\textrm{d}^*=\max \{0,\tilde{\rho }(\theta _\textrm{d}^*)\}\), and then use the Hessian to check that \((\theta _\textrm{s},\theta _\textrm{d})=(1,\theta _\textrm{d}^*)\) is indeed uninvadable. This is illustrated in panel A of Fig. 2. Second, there are multiple uninvadable types; this is illustrated in panels B and C of Fig. 2.
Our formalization of preference evolution under complete information and plasticity makes it difficult to reach any specific conclusion about long-term evolution for two reasons. First, because invasion fitness is not differentiable, a different toolkit than the usual multidimensional convergence stability criterion is needed to characterize the attractor points of the evolutionary dynamic [65]. Second, the multiplicity of uninvadable equilibria compounded with the non-differentiability makes the focus on monomorphic population questionable and a treatment with polymorphic populations appears required. It would thus be relevant to analyze a fully dynamical model of preference evolution with mutation and selection under complete information and plasticity to reach more definite results and also to determine whether the equilibrium \(\theta =(\theta _\textrm{d}^*,1)\) identified in Result 3 plays a special role, for instance whether it is a stochastically stable trait value (sensu [41]).
4 Discussion
By investigating the evolution of semi-Kantian preferences under different informational and behavioral plasticity assumptions in group-structured populations, we have extended the evolutionary viability analysis of this class of preferences. While we restricted attention to pairwise interactions, and preferences characterized by a single evolving quantitative trait, the Kantian coefficient, our model weaves together different threads of the literature and shows how long-term evolution concepts can be used to analyze preferences under gradual evolution. We obtained three main results on the convergence stability and uninvadability of the value of the Kantian coefficient.
First, when interacting individuals have no information about each other’s Kantian coefficient and mutants hold beliefs about the probability of being matched with another randomly sampled mutant from the same lineage, we confirm that an uninvadable Kantian coefficient must equal the coefficient of relatedness [7, 11]. But instead of considering the set of possible utility functions to be the set of all continuous functions as done in this previous work, we focused on the more restricted setting where utility functions are parametrized by a single quantitative trait. This allowed us to cover not only uninvadability in a complementary and less abstract way, but also to cover convergence stability. In Result 1, we show that the Kantian coefficient equal to the coefficient of relatedness is both convergence stable and uninvadable when trait effects on relatedness are sufficiently weak. Thus, we characterize conditions where gradual evolution drives preferences to induce individuals to behave according to Hamilton’s (marginal) rule at the strategy level. One relevant avenue for future research for preference evolution under incomplete information is to consider more realistic demographic scenarios of class structured population (e.g., by sex, age, or stage).
Second, when interacting individuals can observe each other’s type, but each individual has the same preferences regardless of the other’s type, we showed that an uninvadable value of the Kantian coefficient can exceed, fall short of, or equal the coefficient of relatedness. Moreover, we showed that the sign of the discrepancy is determined by whether an individual’s equilibrium strategy is correlated positively, negatively, or not at all with the opponent’s equilibrium strategy. This response coefficient in turn depends on the specifics of the individual fitness function so that the Kantian coefficient will depend on life-history parameters such as survival, migration, etc. [recall the example of the fitness function (B-i)]. Gradual evolution thus now drives preferences to induce individuals to behave according to a context-specific Kantian coefficient, which combines both the relatedness and the response coefficients. This result is fully in line with previous models under complete information and incomplete plasticity, which have all considered other parametric classes of preferences than the one we examined (e.g. [1, 16, 19, 54, 55, 81] for models without relatedness, and [2, 3, 5, 6] for models with relatedness). The dependence of an uninvadable value of the Kantian coefficient on the response coefficient stems from the commitment to a particular behavioral response that an individual’s preferences induces. By being observable, a mutant’s preference type can thus induce a resident to adopt a different strategy than the one adopted in an interaction with another resident, an effect that is absent under incomplete information. Although we established necessary conditions for a Kantian coefficient value to be uninvadable and illustrated uninvadablility and convergence stability under a linear quadratic game (Fig. 1), we did not succeed in identifying simple general sufficient conditions, neither for uninvadability nor for convergence stability. In particular, we cannot rule out evolutionary branching points, which obtain when a singular Kantian coefficient value is convergence stable but not uninvadable (recall footnote 2, and see [44] for a general discussion and [73] for typical evolutionary game theory applications). An avenue for future research on preference evolution under complete information is thus to analyze conditions leading to adaptive polymorphism in preferences.Footnote 12
Finally, we considered the case of complete information with complete plasticity where individuals can both observe the opponent’s type and also condition its preferences on it. This is akin to a green-beard or secret handshake mechanism [46, 49, 83], but at the preference level rather than at the strategy level as in most previous work. Since an individual’s Kantian coefficient may depend on the type of the interaction partner, a type is now a two-dimensional quantitative trait. Compared to the complete information incomplete plasticity scenario, individuals are thus no longer committed to respond according to one and the same Kantian coefficient. Residents are therefore less exploitable by mutants and individuals can be regarded as implementing multiple selves [66] since their preferences and motivations are context-dependent. As we showed, this implies that residents can be pure Kantians when interacting with each other, and still be uninvadable: they can prevent entry by mutants by using the Kantian coefficient equal to the response coefficient when interacting with individuals with a different type than theirs. In such a population, when interacting with each other residents then use the strategy which yields the highest possible individual fitness. In other words, they use the strategy that yields an efficient outcome. This is reminiscent of a result by [29], who showed that a class of “coordination” preferences, which results in efficient strategy profiles, are stable. It is also reminiscent of results obtained by [99] in a model where the search and matching of interacting partners is endogenous but costless: the authors demonstrate the evolutionary stability of a preference for interacting with an individual with the same type as self-combined with play of an efficient strategy profiles. We were, however, not able to characterize convergence stability nor the Kantian coefficient when individuals interact with others with a type different from their own type. Ascertaining this in the non-differentiable setting of complete information with complete plasticity is thus left for future work.
We derived these three results assuming existence of a unique behavioral equilibrium in the resident population and when mutant-resident (or mutant-mutant) interactions occur. Given that it is common that interactions produce a multiplicity of (Nash) equilibria, an important avenue for future research will be to examine the robustness of our results in settings with multiple equilibria. Several questions will need to be addressed. First, one can imagine several alternative formalizations of the interaction between individuals when multiple equilibria are possible. For instance, one could assume that different pairs of individuals in the resident population play different equilibria; such a model would likely require tools from the literature on class-structured populations (since an average individual may then play different equilibria and thus be in different contexts or states, the defining feature of class structured populations e.g., [14]). An alternative would be to assume that the same equilibrium is played in all resident-resident interactions; our formalization should then apply to each equilibrium separately (with implications for possibly different relatedness coefficients depending on the equilibrium being played). The same modeling choices will arise when there exist multiple equilibria in mutant-resident pairs. Second, the definitions of uninvadability and convergence stability may need to be adapted. In particular, for uninvadability, would a preference type be deemed uninvadable only if it is uninvadable for all possible formalizations of interactions in the presence of multiple equilibria? A similar question arises for convergence stability. For existing attempts to address some of these questions, see [7, 8, 10, 11, 29, 79, 99].
Our three results show within the same model how different information and behavioral flexibility assumptions lead to different values of the Kantian coefficient, and thus to different equilibrium strategies. By contrast to strategy evolution models, which predict behavioral patterns for stationary environments, preference evolution models allow to make predictions about behavioral change in a new environment, and can be tested, using either field data or experimental data. A key prediction of our model is that equilibrium behavior at evolutionary equilibrium should be in accordance with Hamilton’s marginal rule expressed at the strategy level only if evolution operated on interactions under incomplete information (recall equation (26)), and that if observed deviations from this rule resulted from interactions taking place under complete information, the deviation from Hamilton’s marginal rule should depend on the specifics of the interaction at hand (recall Eq. 43). In some experiments under incomplete information, humans do appear to conform to behave according to Hamilton’s (marginal) rule at the strategy level ([67]).
Economic games can further be used to discriminate between different preferences in controlled laboratory experiments. For example[21, 40], use dictator games to estimate individuals’ preference parameters assuming other-regarding preferences. More recent studies in this literature have been inspired by results in the evolutionary theory of preferences to design economic games that further allow the researchers to discriminate between other-regarding and semi-Kantian preferences [76], and to estimate the importance of Kantian concerns relative to other-regarding concerns [96]. The latter study indicates that many individuals appear to be driven by a combination of self-interest, semi-Kantian concerns, and other-regard. This finding is in line with evolutionary arguments showing that it is important to distinguish between preferences expressed in terms of fitness consequences and preferences expressed in terms of payoff consequences [11, 63]. The qualitative nature of evolved preferences at the material payoff level indeed differ from that at the fitness level, and this difference depends on demographic properties under genetic evolution and transmission rules under cultural evolution [11]. Payoff and fitness incentives tend to agree in panmictic and family-structured populations, but tend to disagree in spatially structured populations owing to the presence of local competition between individuals. Future research could adopt a similar approach to the one we develop here, by analyzing evolution of preferences expressed at the level of material payoffs under a variety of informational assumptions.
In this paper we have sought to bring together modeling tools from evolutionary biology and from economics in order to investigate the evolution of preferences that guide behavior in strategic interactions. We hope that our formalization has illustrated some of the nuances, intricacies, and richness of research endeavours that seek to analyse more completely the evolutionary dynamics of behavioral mechanisms, and that it will inspire future studies into the many open theoretical and empirical research questions.


Data Availability
Not applicable.
Notes
While we allow for individuals surviving from one demographic time point to the next, the survival probability is assumed independent of age, so that there is no effective age structure in the population.
When invasion fitness is differentiable, the quantities \(S(\theta )\), \(H(\theta )\), and \(J(\theta )\) in fact allow for a complete classification of the singularities of the evolutionary dynamics [44]. Thus, when \(H(\theta ^*)>0\) and \(J(\theta ^*)<0\), a singular type \(\theta ^*\) is an evolutionary branching point; namely, an attractor of the evolutionary dynamics that subsequently splits the population into distinct morphs leading to the coexistence of different types in a protected polymorphism. When \(H(\theta ^*)<0\) and \(J(\theta ^*)>0\) we have a so-called garden of eden state of the evolutionary dynamics, an uninvadable trait value that is unattainable by gradual evolution. Finally, if \(H(\theta ^*)>0\) and \(J(\theta ^*)>0\) then the singular type \(\theta ^*\) is an invadable repellor.
This follows from the fact that under the full evolutionary dynamic process of quantitative traits, the selection gradient \(S(\theta )\) describes the direction of selection on small trait deviations regardless of population genetic states and demographic structures ([86, 84, p. 206] [82]). This entails that any mutant invading the population when rare will eventually substitute the resident and recurrent mutations will drive the trait towards the singularity within its neighborhood when condition (3) is satisfied. This “invasion implies substitution” result was first noted in a special case by [48] and called “a gift from god” [51]. See also [36] for a different line of argument reaching the same conclusions.
Invasion fitness Eq. (2) must be defined for all \(\tau \in \Theta \) including \(\tau =\theta \). In such a monomorphic population, all individuals use strategy \(y^*_\textrm{s}(\theta )=x^*_\textrm{s}(\theta ,\theta )\) and thus the demographic consistency relation \(W(\theta , \theta )=1\) will be verified since \(w(x^*_\textrm{s}(\theta ,\theta ), x^*_\textrm{s}(\theta ,\theta ), y^*_\textrm{s}(\theta ))=w(y^*_\textrm{s}(\theta ), y^*_\textrm{s}(\theta ), y^*_\textrm{s}(\theta ))=1\) for all \(\theta \in \Theta \).
An individual’s utility function is indeed simply a representation of its preferences. For any pair of strategies x and y, an individual’s preferences over available strategies tell whether the individual prefers x, y, or is indifferent between the two. Under certain conditions, such a preference ordering can be fully described by a function that associates a real number to each strategy, namely the utility function (see, e.g., [18, 69]). An individual is assumed to choose a strategy with the highest possible value of the function, since this is the strategy it prefers. Utility maximization is not to be taken literally: it is simply a mathematical tool used to describe behavior that amounts to choosing the preferred item from the strategy set. A pair of strategies then constitutes a Nash equilibrium if each individual uses a strategy which, given the other individual’s strategy, is the one it prefers.
This entails no loss of generality, and simply depends on how one defines the strategy set. For example, if the interaction at hand is a public goods game, then let x and y denote the contributions to the public good. If the interaction at hand is a common pool resource game, then let x and y denote the inverse of contributions to extracting resources.
Note that our model is different from the one in [7], where a resident faces a positive probability of being matched with a mutant. In our model, the mutant trait appears initially in one single individual, and uninvadability obtains if the lineage created by this initial mutant goes extinct in the population (while invadability obtains if the lineage size created by this initial mutant becomes infinite and thus reaches positive frequency in the infinitely large population). During the time the mutant lineage is around in the population there can thus only be a finite number of mutants, and hence residents face a zero probability of being matched with a mutant in this infinitely large population. See Box 1 or [11] for a formal explanation.
This may not be immediately apparent, for the results in [11] (see Propositions 1 and 2) state as a necessary and sufficient condition for a utility function to be uninvadable, that the equilibrium strategy in a population where all individuals have this utility function be an uninvadable strategy (i.e., uninvadable in a setting where the set of traits is the set of strategies, a setting that [11] call strategy evolution). One can check that the condition for \(\theta ^*=r(\theta ^*,\theta ^*)\) to be uninvadable in our setting, i.e., \(H(\theta ^*) <0\) (see Eq. 24), coincides with the condition for the equilibrium strategy \(y^*(\theta ^*)\) to be an uninvadable strategy under strategy evolution. This is so because owing to Eq. (12), \(\partial r(\tau , \theta )/\partial \tau =(\partial \tilde{r}(x, y^*)/\partial x)(\partial x^*(\tau ,\theta )/\partial \tau )\), whereby Eq. (24) becomes \(H(\theta ^*)=\left( \partial x^*(\tau ,\theta )/\partial \tau \right) ^2\left[ K\left( r(\theta ^*,\theta ^*)\right) + 2(\partial \tilde{r}(x, y^*)/\partial x) (\partial w(x^*,y,y^*)/\partial y)\right] \) at \(\tau =\theta \); and under strategy evolution the invasion fitness of mutant type x in a monomorphic resident population y is \(W(x, y)=\left[ 1-\tilde{r}(x, y)\right] w\!\left( x, y, y \right) +\tilde{r}(x, y)\,w(x, x, y)\) and \(\left. \partial ^2 W(x, y)/\partial x^2 \right| _{x=y}\) corresponds to the term in square brackets in \(H(\theta ^*)\).
Because the behavioral perturbations of other-regarding utility functions, and thus \(\rho (\theta )\), typically differ from the ones with the partially Kantian utility function, a singular \(\alpha \) will typically differ from the singular Kantian coefficient, however.
Note that the definition of the function \(\widetilde{W}\) allows us to evaluate \(W_d\) under the hypothesis that the resident would apply the Kantian coefficient \(\theta _\textrm{d}\) even when interacting with another individual with the same type. This is useful for the proof of the result, and for the argument developed in the next paragraph.
To see that polymorphism is likely under preference evolution consider Proposition 1 of [54], which establishes conditions for the evolutionary viability of pessimism or optimism for a particular individual fitness function. Using our notation, these preferences entail the utility function \(u_{\theta _i}(x_i,x_{-i}\mid y^*)=w(x_i,x_{-i}, y^*)+\theta _i x_i\), where \(\theta _i \) is the evolving quantitative trait that can be taken to describe optimism when \(\theta _i>0\) and pessimism when \(\theta _i<0\). It is straightforward to check that the singularity in Proposition 1 of [54] is both convergence stable and uninvadable, as it should under the measure dynamics they consider (e.g.,[26]). However, it is also straightforward to find parameter values of the fitness function they use [54, Eq. 8] such that the singularity is convergence stable and invadable, and thus conducive to an adaptive polymorphism in dispositions, e.g., the coexistence of optimists and pessimists.
References
Akçay E, Van Cleve J (2009) A theory for the evolution of other-regarding motivations integrating proximate and ultimate perspectives. Proc Natl Acad Sci USA 106:19061–19066
Akçay E, Van Cleve J (2012) Behavioral responses in structured populations pave the way to group optimality. Am Natural 179:257–269
Alger I (2010) Public goods games, altruism, and evolution. J Public Econ Theory 12:789–813
Alger I (2023) Evolutionarily stable preferences. Philos Trans R Soc B 378:20210505
Alger I, Weibull JW (2010) Kinship, incentives, and evolution. Am Econ Rev 100:1725–1758
Alger I, Weibull JW (2012) A generalization of Hamilton’s rule–love others how much? J Theor Biol 299:42–54
Alger I, Weibull JW (2013) Homo Moralis: preference evolution under incomplete information and assortative matching. Econometrica 6:2269–2302
Alger I, Weibull JW (2016) Evolution and Kantian morality. Games Econ Behav 98:56–67
Alger I, Weibull JW (2019) Evolutionary models of preference formation. Ann Rev Econ 11:329–354
Alger I, Weibull JW (2023) Evolution and Kantian morality: a correction and addendum. Games Econ Behav 140:585–587
Alger I, Weibull JW, Lehmann L (2020) Evolution of preferences in structured populations: genes, guns, and culture. J Econ Theory 185:1–45
André JB, Day T (2007) Perfect reciprocity is the only evolutionarily stable strategy in the continuous iterated prisoner’s dilemma. J Theor Biol 247:11–22
Arbilly M, Motro U, Feldman MW, Lotem A (2010) Co-evolution of learning complexity and social foraging strategies. J Theor Biol 267:573–81
Avila P, Mullon C (2023) Evolutionary game theory and the adaptive dynamics approach: adaptation where individuals interact. Philos Trans R Soc B 378:615255
Bergstrom T (1995) On the evolution of altruistic ethical rules for siblings. Am Econ Rev 85:58–81
Bester H, Güth W (1998) Is altruism evolutionarily stable? J Econ Behav Organ 34:193–209
Binmore K (1998) Just playing: game theory and the social contract 2. MIT Press, Cambridge
Binmore K (2011) Rational decisions. Princeton University Press, Princeton
Bolle F (2000) Is altruism evolutionarily stable? And envy and malevolence? Remarks on Bester and Güth. J Econ Behav Organ 42:131–133
Boyd R, Richerson PJ (1985) Culture and the evolutionary process. University of Chicago Press, Chicago
Bruhin A, Fehr E, Schunk D (2019) The many faces of human sociality: uncovering the distribution and stability of social preferences. J Eur Econ Assoc 17:1025–1069
Bulmer MG (1994) Theoretical evolutionary ecology. Sinauer Associates
Cavalli-Sforza L, Feldman MW (1981) Cultural transmission and evolution. Princeton University Press
Charlesworth B (1994) Evolution in age-structured populations, 2nd edn. Cambridge University Press, Cambridge
Christiansen FB (1991) On conditions for evolutionary stability for a continuously varying character. Am Natural 138:37–50
Cressman R, Hofbauer J (2005) Measure dynamics on a one-dimensional continuous trait space: theoretical foundations for adaptive dynamics. Theoret Popul Biol 67:47–59
Cressman R, Tao Y (2004) The replicator equation and other game dynamics. Proc Natl Acad Sci USA 11:10810–10817
Dawkins R (1980) Good strategy or evolutionarily stable strategy? In: Barlow GW (ed) Sociobiology: beyond nature/nurture? Westview Press, Boulder
Dekel E, Ely J, Yilankaya O (2007) Evolution of preferences. Rev Econ Stud 74:685–704
Dridi S, Akçay E (2018) Learning to cooperate: the evolution of social rewards in repeated interactions. Am Natural 191:58–73
Dridi S, Lehmann L (2015) A model for the evolution of reinforcement learning in fluctuating games. Anim Behav 104:1–28
Eshel I (1983) Evolutionary and continuous stability. J ot Theoret Biol 103:99–111
Eshel I (1996) On the changing concept of evolutionary population stability as a reflection of a changing point of view in the quantitative theory of evolution. J Math Biol 34:485–510
Eshel I, Feldman M, Bergman A (1998) Long-term evolution, short-term evolution, and population genetic theory. J Theoret Biol 191:391–396
Eshel I, Feldman MW (1984) Initial increase of new mutants and some continuity properties of ESS in two-locus systems. Am Nat 124:631–640
Eshel I, Motro U, Sansone E (1997) Continuous stability and evolutionary convergence. J Theoret Biol 074:222–232
Ferrière R, Gatto M (1995) Lyapunov exponents and the mathematics of invasion in oscillatory or chaotic populations. Theoret Popul Biol 48:126–171
Fisher RA (1930) The genetical theory of natural selection. Clarendon Press, Oxford
Fisher RA (1941) Average excess and average effect of a gene substitution. Ann Human Genet 11:53–63
Fisman R, Kariv S, Markovits D (2007) Individual preferences for giving. Am Econ Rev 97:1858–1876
Foster D, Young HP (1990) Stochastic evolutionary game dynamics. Theoret Popul Biol 38:219–232
Fudenberg D, Levine DK (1998) Theory of learning in games. MIT Press, Cambridge
Fudenberg D, Tirole J (1991) Game theory. MIT Press
Geritz SAH, Kisdi E, Meszéna G, Metz JAJ (1998) Evolutionarily singular strategies and the adaptive growth and branching of the evolutionary tree. Evolut Ecol 12:35–57
Giraldeau L, Caraco T (2000) Social foraging theory. Princeton University Press, Princeton
Grafen A (1990) Do animals really recognize kin? Anim Behav 39:42–54
Güth W (1995) An evolutionary approach to explaining cooperative behavior by reciprocal incentives. Int J Game Theory 24:323–344
Hamilton WD (1964) The genetical evolution of social behaviour, 1. J Theoret Biol 7:1–16
Hamilton WD (1964) The genetical evolution of social behaviour, II. J Theoret Biol 7:17–52
Hamilton WD (1970) Selfish and spiteful behavior in an evolutionary model. Nature 228:1218–1220
Hamilton WD (1988) This week’s citation classic. Curr Contents 40:16
Harley CB (1981) Learning the evolutionary stable strategy. J Theoret Biol 89:611–633
Harris TE (1963) The theory of branching processes. Springer, Berlin
Heifetz A, Shannon C, Spiegel Y (2007) The dynamic evolution of preferences. Econ Theory 32:251–286
Heifetz A, Shannon C, Spiegel Y (2007) What to maximize if you must. J Econ Theory 133:31–57
Hines WGS, Maynard Smith J (1978) Games between relatives. J Theoret Biol 79:19–30
Hofbauer J, Sigmund K (1998) Evolutionary games and population dynamics. Cambridge University Press, Cambridge
Iosifescu M (2007) Finite Markov processes and their applications. Dover, New York
Jeong H, Taylor A, Floeder JR, Lohmann M, Mihalas S, Wu B, Zhou M, Burke DA, Namboodiri VMK (2022) Mesolimbic dopamine release conveys causal associations. Science 378:eabq6740
Kant I (1785) Grundlegung zur Metaphysik der Sitten, Hartknoch, Riga
Karlin S, Taylor HM (1975) A first course in stochastic processes. Academic Press, San Diego
Killingback T, Doebeli M (2002) The continuous prisoner’s dilemma and the evolution of cooperation through reciprocal altruism with variable investment. Am Nat 160:421–438
Lehmann L, Alger I, Weibull JW (2015) Does evolution lead to maximizing behavior? Evolution 69:1858–1873
Lehmann L, Rousset F (2020) When do individuals maximize their inclusive fitness? Am Nat 195:717–732
Leimar O (2009) Multidimensional convergence stability. Evolut Ecol Res 11:191–208
Lester D (2015) On multiple selves. Routledge, London
Levy M, Lo AW (2022) Hamilton’s rule in economic decision-making. Proc Natl Acad Sci USA 119:1–5
Malécot G (1969) The mathematics of heredity. W. H, Freeman and Company, San Francisco
Mas-Colell A, Whinston MD, Green JR (1995) Microecon Theory. Oxford Unversity Press, Oxford
Maynard Smith J (1982) evolution and the theory of games. Cambridge University Press, Cambridge
Maynard Smith J, Price GR (1973) The logic of animal conflict. Nature 246:15–18
McNamara JM, Gasson CE, Houston AI (1999) Incorporating rules for responding into evolutionary games. Nature 401:368–71
McNamara JM, Leimar O (2020) Game Theory in Biology. Oxford University Press
Metz JAJ, Nisbet RM, Geritz SAH (1992) How should we define fitness for general ecological scenarios? Trends Ecol Evolut 7:198–202
Michod R (1980) Evolution of interactions in family-structured populations: mixed mating models. Genetics 96:275–96
Miettinen T, Kosfeld M, Fehr E, Weibull JW (2020) Revealed preferences in a sequential prisoners’ dilemma: a horse-race between six utility functions. J Econ Behav Organ 173:1–25
Moran PAP (1962) The statistical processes of evolutionary theory. Clarendon Press, Oxford
Mullon C, Keller L, Lehmann L (2016) Evolutionary stability of jointly evolving traits in subdivided populations. Am Nat 188:175–195
Ok EA, Vega-Redondo F (2001) On the evolution of individualistic preferences: an incomplete information scenario. J Econ Theory 97:231–254
Parker GA, Maynard Smith J (1990) Optimality theory in evolutionary biology. Science 349:27–33
Possajennikov A (2000) On the evolutionary stability of altruistic and spiteful preferences. J Econ Behav Organ 42:125–129
Priklopil T, Lehmann L (2021) Metacommunities, fitness and gradual evolution. Theoret Popul Biol 142:12–35
Robson AJ (1990) Efficiency in evolutionary games: darwin, nash and the secret handshake. J Evolut Biol 144:379–396
Rousset F (2004) Genetic structure and selection in subdivided populations. Princeton University Press, Princeton
Rousset F (2015) Regression, least squares, and the general version of inclusive fitness. Evolution 69:2963–2970
Rousset F, Billiard S (2000) A theoretical basis for measures of kin selection in subdivided populations: finite populations and localized dispersal. J Evolut Biol 13:814–825
Russell S, Norvig P (2016) Artificial intelligence: a modern approach. Pearson, Edinburgh
Samuelson L (1998) Evolutionary games and equilibrium selection. MIT Press, Cambridge
Sandholm WH (2011) Population games and evolutionary dynamics. MIT Press, Cambridge
Selten R, Hammerstein P (1984) Gaps in Harley’s argument on evolutionarily stable learning rules and in the logic of “tit for tat’’. Behav Brain Sci 7:115–116
Sugden R (1986) Econ rights. Cooperation and welfare. Palgrave Macmillan, New York
Sutton RS, Barto AG (1998) Reinforcement learning. MIT Press, Cambridge
Taylor PD (1989) Evolutionary stability in one-parameter models under weak selection. Theoret Popul Biol 36:125–143
Taylor PD, Day T (2004) Stability in negotiation games and the emergence of cooperation. Proc R Soc Lond Ser B-Biol Sci 271:669–674
Van Cleve J (2023) Evolutionarily stable strategy analysis and its links to demography and genetics through invasion fitness. Philos Trans R Soc B 378:20210496
Van Leeuwen B, Alger I (2022) Estimating social preferences and Kantian morality in strategic interactions. TSE Working Paper 19-1056
Vincent TL, Brown JS (2005) Evolutionary game theory, natural selection, and Darwinian dynamics. Cambridge University Press, Cambridge
Wakano JY, Lehmann L (2014) Evolutionary branching in deme-structured populations. J Theoret Biol 351:83–95
Wang Z, Wu J (2023) Preference evolution under stable matching. SSRN Working Paper 4426394
Weibull JW (1997) Evolutionary game theory. MIT Press, Cambridge
Wolfram Research (2016) Mathematica. Wolfram Research Inc, Champaign
Young HP (1998) Individual strategy and social structure: an evolutionary theory of institutions. Princeton University Press, Princeton
Acknowledgements
We thank Christian Hilbe, Maria Kleshnina and Kateřina Staňková for inviting us to contribute this paper and two reviewers for their helpful comments on it.
Funding
Open access funding provided by University of Lausanne. I.A. acknowledges IAST funding from the French National Research Agency (ANR) under Grant ANR-17-EURE-0010 (Investissements d’Avenir program), and funding from the European Research Council (ERC) under the European Union’s Horizon 2020 research and innovation programme (Grant agreement No 789111 - ERC Evolving Economics).
Author information
Authors and Affiliations
Contributions
L.L. conceived the model, I.A. and L.L. derived the results, L.L. wrote the first draft and both authors finalized the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
All authors declare that they have no conflict of interest
Ethical approval
Not applicable
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Evolutionary Games and Applications” edited by Christian Hilbe, Maria Kleshnina and Kateřina Staňková.
Appendices
Behavioral Perturbation Under Incomplete Information
We here show that the behavioral perturbation (18) is always positive, i.e., \(\left. \partial x^*(\tau ,\theta )/\partial \tau \right| _{\tau =\theta } >0\). We proceed in two steps. First, we evaluate the perturbation of a mutant’s reaction function and show that this is positive. Second, we show that this latter perturbation is sign equivalent to \(\left. \partial x^*(\tau ,\theta )/\partial \tau \right| _{\tau =\theta }\).
For the first step recall from Eq. (13) that a specific mutant’s expected utility is
where the notation \(\mid x^*,y^*\) emphasises that we are here holding the strategies of the other mutant and resident individuals as given. A mutant’s best response to \((x^*,y^*)\) is implicitly defined by the necessary first-order condition:
which, using Eq. (11), is written
This equation implicitly defines the specific mutant’s optimal strategy \(x(\tau , x^*,y^*)\) as a function of \(\tau \), \(x^*\), and \(y^*\) (which depends on \(\theta \)). In other words, it defines this mutant’s reaction function, which specifies its utility-maximizing strategy for each \((x^*,y^*)\) (e.g., [43, p. 14]). We use an index i to denote the partial derivative with respect to the i-th argument of the individual fitness function to rewrite Eq. (A-3) as follows:
which simplifies to
Applying the implicit function theorem holding \((x^*,y^*)\) fixed, we obtain:
where
Strict concavity of \(u_{\tau }\) for all \(\tau \in [0,1]\) implies that \(A<0\) and \(B<0\) and so the denominator of Eq. (A-6) is strictly negative. At equilibrium, and locally at \(\tau =\theta \), we have \(x=x^*=y^*\), implying that the numerator reduces to \(w_2(x,x,y^*)\), which is strictly positive. Hence, the perturbation \(\left. \partial x(\tau , x^*,y^*)/\partial \tau \right| _{\tau =\theta }\), which measures this mutant’s (infinitesimal) change in its reaction function \(x(\tau , x^*,y^*(\theta ))\) when the value of its Kantian coefficient is infinitesimally increased at \(\tau =\theta \), is strictly positive.
We turn now to the second step to show why the result derived in the first step implies that the mutant equilibrium strategy \(x^*\) must increase as a result of an (infinitesimal) increase in the value of \(\tau \) for all mutants. First, note that such an increase in \(\tau \) has no effect on the resident strategy (see Eq. 13), implying that we can indeed hold \(y^*\) fixed, as we did above. Hence, for a given \(\tau \) and \(y^*\), the equilibrium strategy \(x^*(\tau ,\theta )\) is a fixed point of the mutant’s best-response function (see the second line of Eq. 13) and this is a point on the curve described by the reaction function \(x(\tau , x^*,y^*)\) for any given \((\tau , y^*)\). Because \(\left. \partial x(\tau , x^*,y^*)/\partial \tau \right| _{\tau =\theta }\) describes how the response function of one mutant is slightly displaced by the introduction of a small mutant deviation at \(\tau =\theta \), and because we proved above that any such deviation is positive for any strategy \(x^*\) played by other mutants, the equilibrium strategy \(x^*(\tau ,\theta )\) must locally vary with the same sign as the reaction function varies, i.e, \(\left. \partial x^*(\tau ,\theta )/\partial \tau \right| _{\tau =\theta } \propto \left. \partial x(\tau , x^*,y^*)/\partial \tau \right| _{\tau =\theta }\).
Jacobian and Hessian Under Complete Information with Incomplete Plasticity
Differentiating Eq. (40) with respect to \(\theta \) and evaluating at \(\theta ^*\) satisfying \(S(\theta ^*)=0\) yields
Using Eq. (40) at \(S(\theta ^*)=0\) and using Eq. (36) we can express the singular trait value implicitly as
which, on substituting into Eq. (A-8), using \(\rho (\theta )=\left( \partial x^*_\textrm{d}(\tau ,\theta )/\partial \theta \right) /\left( \partial x^*_\textrm{d}(\tau ,\theta )/\partial \tau \right) \) and simplifying produces
The second-order behavioral perturbations \(\partial ^2 x^*_\textrm{d}(\tau ,\theta )/\partial \tau ^2, \partial ^2 x^*_\textrm{d}(\tau ,\theta )/(\partial \tau \partial \theta ), \partial ^2 x^*_\textrm{d}(\tau ,\theta )/\partial \theta ^2\) appearing in this Jacobian can be computed by using implicit differentiation in Eq. (31). The resulting expressions are complicated and lengthy and we were unable to infer some general information from these expressions, although they can be handled easily with a symbolic manipulation system such as Mathematica [101]. A Mathematica notebook with all algebraic computations of the paper is available on request.
Now using invasion fitness (38) to evaluate \(H(\theta )=\left. \partial ^2 W(\tau , \theta )/\partial \tau ^2 \right| _{\tau =\theta }\), we find that
Substituting into this expression \(\partial w(x,y^*_\textrm{s},y^*_\textrm{s})/\partial x=-\theta \partial w(x,y,y^*_\textrm{s})/\partial y\) and Eq. (A-9) yields
A key distinction between the Jacobian \(J(\theta ^*)\) and the Hessian \(H(\theta ^*)\) is that the sign of the Jacobian does not depend directly on fitness derivatives, while the Hessian does. Both expressions remain complicated and we did not manage to obtain general information from them. Hence, they need to be evaluated on a case by case basis.
Proof of Result 3
We first examine mutant–mutant interactions (the term in Eq. (50)) and then turn to mutant-resident interactions (the term in Eq. (49)).
Consider some resident type \(\theta =(\theta _\textrm{d},\theta _\textrm{s})\in [0,1]^2\). For any such type, residents obtain individual fitness \(w(y^*_\textrm{s},y^*_\textrm{s},y^*_\textrm{s})=1\). Visual inspection of the expression in (50) suffices to conclude that, for any value of the resident \(\theta _\textrm{s}\), the most threatening value \(\tau _\textrm{s}\) of any mutant type \(\tau =(\tau _\textrm{d},\tau _\textrm{s})\) against the resident is the one that maximizes \(W_\textrm{s}(\tau _\textrm{s}, \theta _\textrm{s})\), i.e., such that the equilibrium strategy used in a mutant–mutant interaction, \(x^*_\textrm{s}(\tau _\textrm{s},\theta _\textrm{s})\), solves \(\max _{x \in \mathcal {X}} w(x,x,y^*_\textrm{s})\). Given differentiability of w and \(\mathcal {X}= \mathbb {R}\), the strategy \(x^*_\textrm{s}(\tau _\textrm{s},\theta _\textrm{s})\) of the most threatening mutant must thus satisfy the following first-order condition:
Since from Eq. (46), \(x^*_\textrm{s}(\tau _\textrm{s},\theta _\textrm{s})\) must satisfy the following first-order condition for utility maximization by a mutant,
our assumption that \(\frac{\partial w(x,y,z)}{\partial y}\ne 0\) for all \((x,y,z)\in \mathcal {X}^3\) implies that \(\tau _\textrm{s}=1\) is the unique value of \(\tau _\textrm{s}\in [0,1]\) which induces mutants to use the strategy that maximizes \(w(x,x,y^*_\textrm{s})\). Hence, we can conclude that for any resident type \(\theta \), the most threatening mutant type has \(\tau _\textrm{s}=1\). Note further that the argument developed above implies that \(\theta _\textrm{s}=1\) implies \(W_\textrm{s}(\tau _\textrm{s}, \theta _\textrm{s})=1\) if \(\tau _\textrm{s}=1\) and \(W_\textrm{s}(\tau _\textrm{s}, \theta _\textrm{s})<1\) if \(\tau _\textrm{s}<1\). Hence, \(\theta _\textrm{s}=1\) is sufficient for \(W_\textrm{s}(\tau _\textrm{s}, \theta _\textrm{s})\le 1\) for any \(\tau _\textrm{s}\in [0,1]\).
We turn now to the term in Eq. (49), which measures the individual fitness of a mutant in an interaction with a resident. Suppose that the resident type is \(\theta =(\theta _\textrm{d}, \theta _\textrm{s})=(\theta _\textrm{d}^*,1)\), where \(\theta _\textrm{d}^*\) is defined in the statement of the result. By definition of \(\theta _\textrm{d}^*\), \(\widetilde{W}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1) = w(\tilde{y}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1), \tilde{y}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1), y^*_\textrm{s}(1))\ge w(\tilde{x}(\tau _\textrm{d},\theta _\textrm{d}^*,1), \tilde{y}(\theta _\textrm{d}^*,\tau _\textrm{d},1), y^*_\textrm{s}(1)) \) for all \(\tau _\textrm{d}\ne \theta _\textrm{d}^*\). Since \(w(y, y, y^*_\textrm{s}(1)) \) is strictly concave in y (owing to our assumption that the utility function is strictly concave in its first argument), which achieves its maximum for y satisfying (A-13), it follows that the value of \(\kappa \in [0,1]\) that would maximize the function \(w(\tilde{y}(\kappa ,\kappa ,1), \tilde{y}(\kappa ,\kappa ,1), y^*_\textrm{s}(1)) \) is \(\kappa =1\). Together with the preceding inequality, we can thus conclude that \(w(\tilde{x}(\tau _\textrm{d},\theta _\textrm{d}^*,1), \tilde{y}(\theta _\textrm{d}^*,\tau _\textrm{d},1), y^*_\textrm{s}(1)) \le w(\tilde{x}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1), \tilde{y}(\theta _\textrm{d}^*,\theta _\textrm{d}^*,1), y^*_\textrm{s}(1)) \le w(\tilde{x}(1,1,1), \tilde{y}(1,1,1), y^*_\textrm{s}(1)) =1\). In other words, for any \(\tau _\textrm{d}\ne \theta _\textrm{d}^*\), \(W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d}^*,1) \le 1\).
The preceding conclusions, namely that \(W_\textrm{s}(\tau _\textrm{s}, 1)\le 1\) and \(W_\textrm{d}(\tau _\textrm{d},\theta _\textrm{d}^*,1) \le 1\), imply that whatever is the value of relatedness \(r(\tau ,\theta )\), if the resident type is \((\theta _\textrm{d},\theta _\textrm{s})=(\theta _\textrm{d}^*,1)\), then \(W(\tau , \theta )\le 1\) for any \(\tau \ne \theta \). \(\square \)
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Alger, I., Lehmann, L. Evolution of Semi-Kantian Preferences in Two-Player Assortative Interactions with Complete and Incomplete Information and Plasticity. Dyn Games Appl 13, 1288–1319 (2023). https://doi.org/10.1007/s13235-023-00521-y
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s13235-023-00521-y