Abstract
Energy harvesting-aided non-orthogonal multiple access (NOMA) meets critical requirements of modern wireless networks in terms of spectral efficiency, communication reliability, and energy efficiency. However, information security for it has not received greatly attentions from both industry and academia. This paper proposes jammer selection to meliorate its security performance. To promptly assess the efficacy of the proposed jammer selection, we propose explicit formulas of connection/secrecy throughput and outage probability for both far and near users accounting for non-linear feature of energy harvesters. These formulas are corroborated by Monte-Carlo simulations and quickly generate innumerable results to reveal a significant/slight influence of energy harvesting nonlinearity on communications reliability/information security. In addition, there exist limits on target data/secrecy rates to avoid complete connection outage (i.e. connection outage probability is one) and achieve complete security (i.e. secrecy outage probability is one). Additionally, the proposed (NOMA-and-proposed jammer selection) scheme significantly outperforms its counterparts (NOMA-and-random jammer selection and orthogonal multiple access-and-proposed jammer selection) in terms of both security and reliability. Nevertheless, there is a trade-off between reliability and security. Notably, the proposed scheme obtains optimum security/reliability performance with proper selection of time/power splitting coefficient.







Similar content being viewed by others
Data availability
Data is contained within the article.
Notes
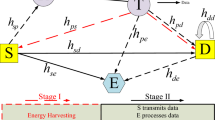
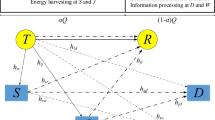
We study NOMA for each cluster of two users owing to the extensively-acknowledged reality that accreting a quantity of users in each cluster is complex and inefficient [51, 52]. Additionally, the two-user NOMA case was recommended for the 3GPP-LTE-A [53, 54]. Notwithstanding, how to cluster two users is outside the scope of our work (please refer to [6, 29, 36, 42, 55] for deep comprehension on NOMA user grouping).
Although that all jammers jam E simultaneously generates higher amount of jamming power to secure better the desired communications, the current paper does not consider this scenario. This is because of the increasing complexity. Indeed, in order to cancel all jamming signals from J jammers from the desired signals at N and F, they need to synchronize these jamming signals. As such, the higher J, the more complex the synchronization. Accordingly, the jammer selection proposed in this paper reduces the complexity of the synchronization significantly.
This paper researches the case that N implements the detection of \(x_n\) solely if N has restored \(x_f\) accurately. The condition to specify whether N has detected \(x_f\) exactly will be presented in the sequel. Consequently, the interference remained after suppressing \(x_f\) out of \({\tilde{y}_n}\) is neglected.
Due to the high number of curves in Fig. 2, the asymptotic analytical results in Subsections 3.1.3 and 3.2.3 are not presented here. Nevertheless, we double-checked the agreement between the asymptotic analytical results and the simulated results at high P, which exposes the precision of the analysis in Subsections 3.1.3 and 3.2.3.
References
Guo H et al Multi-UAV cooperative task offloading and resource allocation in 5G advanced and beyond. IEEE Trans Wire Commun. To appear
Fall M et al (2023) Towards sustainable 5G networks: A proposed coordination solution for macro and pico cells to optimize energy efficiency. IEEE Access 11:50794–50804
Lee H et al (2023) Towards 6G hyper-connectivity: Vision, challenges, and key enabling technologies. JCN 25(3):344–354
Ngo et al QT Physical layer security in IRS-assisted cache-enabled satellite communication networks. IEEE Trans Green Commun Netw. To appear
Li Y et al NOMA assisted two-tier VR content transmission: A tile-based approach for QoE optimization. IEEE Trans Mob Comp. To appear
Zhang X et al Generalized approximate message passing based Bayesian learning detectors for uplink grant-free NOMA. IEEE Trans Veh Tech. To appear
Srinath HG et al An efficient NB-IoT compatible GF-NOMA PHY mechanism for mMTC. IEEE IoT J. To appear
Hu B et al (2023) A self-powered rectifier-less series-synchronized switch harvesting on inductor (S-SSHI) interface circuit for flutter-based piezoelectric energy harvesters. IEEE Instrument Measure Mag 26(3):5–13
Halimi MA et al (2023) Rectifier design challenges for wireless energy harvesting/wireless power transfer systems: Broadening bandwidth and extended input power range. IEEE Micro Mag 24(6):54–67
Halimi MA et al (2023) Rectifier circuits for RF energy harvesting and wireless power transfer applications: A comprehensive review based on operating conditions. IEEE Micro Mag 24(1):46–61
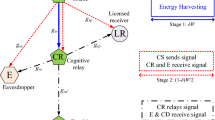
Pham-Thi-Dan N et al (2019) Security analysis for cognitive radio network with energy scavenging capable relay over Nakagami-m fading channels. Ho Chi Minh City, Vietnam, IEEE ISEE, pp 68–72
Wang D et al (2020) Primary privacy preserving with joint wireless power and information transfer for cognitive radio networks. IEEE Trans Cog Commun Netw 6(2):683–693
Ge L et al (2020) Performance analysis for multihop cognitive radio networks with energy harvesting by using stochastic geometry. IEEE IoT J 7(2):1154–1163
Bouabdellah M et al (2019) Cooperative energy harvesting cognitive radio networks with spectrum sharing and security constraints. IEEE Access 7:173329–173343
Ghosh S et al On the performance of end-to-end cooperative NOMA-based IoT networks with wireless energy harvesting. IEEE IoT J. To appear
Zhu Z et al (2021) Robust beamforming designs in secure MIMO SWIPT IoT networks with a nonlinear channel model. IEEE IoT J 8(3):1702–1715
Solanki S et al (2020) Performance analysis of Piece-Wise linear model of energy harvesting-based multiuser overlay spectrum sharing networks. IEEE OJCS 1:1820–1836
Babaei M et al (2020) BER performance of full-duplex cognitive radio network with nonlinear energy harvesting. IEEE Trans Green Commun Netw 4(2):448–460
Wang D et al (2020) Performance analysis and resource allocations for a WPCN with a new nonlinear energy harvester model. IEEE OJCOMS 1:1403–1424
Ni L et al (2019) Outage-constrained secrecy energy efficiency optimization for CRNs with non-linear energy harvesting. IEEE Access 7:175213–175221
Wang F et al Secure resource allocation for polarization-based non-linear energy harvesting over 5G cooperative CRNs. IEEE Wire Commun Lett. To appear
Salman H et al PLS-IoT enhancement against eavesdropping via spatially distributed constellation obfuscation. IEEE Wire Commun Lett. To appear
Cao K et al Physical layer security for intelligent reflecting surface aided wireless powered communication systems. IEEE IoT J. To appear
Loukil MH et al Physical layer security at a point-to-point MIMO system with 1-Bit DACs and ADCs. IEEE Wirel Commun Lett. To appear
Katsuki Y et al (2023) Noncoherent massive MIMO with embedded one-way function physical layer security. IEEE Trans Info Forensics Secur 18:3158–3170
Amini C et al (2023) Relay-aided based physical layer security in VLC system with improved noise model. IEEE Trans Commun 71(7):4193–4203
Zheng TX et al (2016) Optimal power allocation for artificial noise under imperfect CSI against spatially random eavesdroppers. IEEE Trans Veh Tech 65(10):8812–8817
Hu J et al (2017) Artificial-noise-aided secure transmission scheme with limited training and feedback overhead. IEEE Trans Wirel Commun 16(1):193–205
Khazali A et al (2022) Energy efficient uplink transmission in cooperative mmWave NOMA networks with wireless power transfer. IEEE Trans Veh Tech 71(1):391–405
Singh CK et al (2022) Energy harvesting in overlay cognitive NOMA systems with hardware impairments. IEEE Sys J 16(2):2648–2659
Shukla AK et al (2021) Performance analysis of energy harvesting-assisted overlay cognitive NOMA systems with incremental relaying. IEEE OJCOMS 2:1558–1576
Liu Y et al (2020) Outage performance analysis for SWIPT-based incremental cooperative NOMA networks with non-linear harvester. IEEE Commun Lett 24(2):287–291
Le QN et al (2021) Full-duplex non-orthogonal multiple access cooperative overlay spectrum-sharing networks with SWIPT. IEEE Trans Green Commun Netw 5(1):322–334
Ma L et al (2021) On the performance of full-duplex cooperative NOMA with non-linear EH. IEEE Access 9:145968–145976
Aswathi V et al (2021) Outage and throughput analysis of full-duplex cooperative NOMA system with energy harvesting. IEEE Trans Veh Tech 70(11):11648–11664
Si Q et al (2021) Cooperative SM-based NOMA scheme with SWIPT. IEEE Trans Veh Tech 70(6):6195–6199
García CE et al (2022) Low-complexity PSO-based resource allocation scheme for cooperative non-linear SWIPT-enabled NOMA. IEEE Access 10:34207–34220
Tran TN et al (2021) SWIPT model adopting a PS framework to aid IoT networks inspired by the emerging cooperative NOMA technique. IEEE Access 9:61489–61512
Liu X et al (2022) Simultaneous wireless information and power transfer based on symbol allocation for GFDM-NOMA cooperative communications. IEEE Wirel Commun Lett 11(2):333–337
Do DT et al (2021) User grouping and energy harvesting in UAV-NOMA system with AF/DF relaying. IEEE Trans Veh Tech 70(11):11855–11868
Agrawal K et al (2020) NOMA with battery-assisted energy harvesting full-duplex relay. IEEE Trans Veh Tech 69(11):13952–13957
Li X et al (2021) Cooperative wireless-powered NOMA relaying for B5G IoT networks with hardware impairments and channel estimation errors. IEEE IoT J 8(7):5453–5467
Bisen S et al (2021) On performance of energy harvested cooperative NOMA under imperfect CSI and imperfect SIC. IEEE Trans Veh Tech 70(9):8993–9005
Zhai C et al (2022) Nonorthogonal multiple access with energy harvesting-based alternate relaying. IEEE Sys J 16(1):327–338
Lei R et al (2021) Secrecy outage performance analysis of cooperative NOMA networks with SWIPT. IEEE Wirel Commun Lett 10(7):1474–1478
Li X et al (2020) Performance analysis of impaired SWIPT NOMA relaying networks over imperfect Weibull channels. IEEE Sys J 14(1):669–672
Aldababsa M et al (2022) Joint transmit-and-receive antenna selection system for MIMO-NOMA with energy harvesting. IEEE Sys J 16(3):4139–4148
Lyu B et al (2022) IRS-assisted downlink and uplink NOMA in wireless powered communication networks. IEEE Trans Veh Tech 71(1):1083–1088
Wu Q et al (2021) IRS-assisted wireless powered NOMA: Do we really need different phase shifts in DL and UL? IEEE Wirel Commun Lett 10(7):1493–1497
Zhang D et al (2021) Throughput maximization for IRS-assisted wireless powered hybrid NOMA and TDMA. IEEE Wirel Commun Lett 10(9):1944–1948
Ardakani FD et al (2022) Joint device pairing, reflection coefficients, and power control for NOMA backscatter systems. IEEE Trans Veh Tech 71(4):4396–4411
Zhao F et al (2022) Integrated satellite-terrestrial networks with coordinated C-NOMA and relay transmission. IEEE Sys J 16(4):5270–5280
Study on Downlink Multiuser Superposition Transmission for LTE (2015) 3GPP. Shanghai, China
Chen G et al (2020) On the performance of cluster-based MIMO NOMA in multi-cell dense networks. IEEE Trans Commun 68(8):4773–4787
Ding Z et al (2016) Impact of user pairing on 5G nonorthogonal multiple-access downlink transmissions. IEEE Trans Veh Tech 65:6010–6023
Fang B et al (2016) Precoding and artificial noise design for cognitive MIMOME wiretap channels. IEEE Trans Veh Tech 65(8):6753–6758
Nguyen VD et al (2016) Joint information and jamming beamforming for secrecy rate maximization in cognitive radio networks. IEEE Trans Info Forensics Secur 11(11):2609–2623
Hu X et al (2016) Secure transmission via jamming in cognitive radio networks with possion spatially distributed eavesdroppers. In: Proceedings of the IEEE PIMRC, Valencia, Spain, pp 1–6
Wu Y et al (2015) Secure beamforming for cognitive radio networks with artificial noise. In: Proceedings of the IEEE WCSP, Nanjing, China, pp 1–5
Zou Y (2017) Physical-layer security for spectrum sharing systems. IEEE Trans Wirel Commun 16(2):1319–1329
Li Z et al (2015) Cooperative jamming for secure communications in MIMO cooperative cognitive radio networks. In: Proceedings of the IEEE ICC, London, UK, pp 7609–7614
Abramowitz M et al (1972) Handbook of mathematical functions with formulas, graphs, and mathematical tables, Tenth printing ed., Washington, DC, USA: U.S. Government Printing Office
Funding
This research is funded by Vietnam National University HoChiMinh City (VNU-HCM) under Grant Number B2023-20-08.
Author information
Authors and Affiliations
Contributions
Khuong Ho-Van contributes the whole manuscript.
Corresponding author
Ethics declarations
Ethics approval
Not applicable.
Consent for publication
Khuong Ho-Van consents to publish this manuscript on Peer-to-Peer Networking and Applications.
Conflict of interest
The author declares no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the Topical Collection: 1- Track on Networking and Applications
Guest Editor: Vojislav B. Misic
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Ho-Van, K. Jammer selection for energy harvesting-aided non-orthogonal multiple access: Performance analysis. Peer-to-Peer Netw. Appl. 16, 2438–2455 (2023). https://doi.org/10.1007/s12083-023-01542-5
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12083-023-01542-5