Abstract
Security threats are always there if the human intruders are not identified and recognized well in time in highly security-sensitive environments like the military, airports, parliament houses, and banks. Fog computing and machine learning algorithms on Gait sequences can prove to be better for restricting intruders promptly. Gait recognition provides the ability to observe an individual unobtrusively, without any direct cooperation or interaction from the people, making it very attractive than other biometric recognition techniques. In this paper, a Fog Computing and Machine Learning Inspired Human Identity and Gender Recognition using Gait Sequences (FCML-Gait) are proposed. Internet of things (IoT) devices and video capturing sensors are used to acquire data. Frames are clustered using the affinity propagation (AP) clustering technique into several clusters, and cluster-based averaged gait image(C-AGI) feature is determined for each cluster. For training and testing of datasets, sparse reconstruction-based metric learning (SRML) and Speeded Up Robust Features (SURF) with support vector machine (SVM) are applied on benchmark gait database ADSC-AWD having 80 subjects of 20 different individuals in the Fog Layer to improve the processing. The performance metrics, for instance, accuracy, precision, recall, F-measure, C-time, and R-time have been measured, and a comparative evaluation of the projected method with the existing SRML technique has been provided in which the proposed FCML-Gait outperforms and attains the highest accuracy of 95.49%.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Biometrics are a human's distinguishing feature [1]. Recognizing a human biometric aspect requires distinctive feature vectors obtained from the physiological and/or behavioral traits of an individual [2]. Human recognition by biometrics from a range without human interference is in emerging demand in a variety of critical security applications. Human identification/recognition utilizing gait biometric systems has become much more attractive in real-time applications. Biometric traits are classified into two types: behavioral and physiological [3]. Iris, Deoxy-ribose Nucleic Acid (DNA), fingerprint, face, palm print, etc., are physiological, and behavioral characteristics include gait, written signature, and voice. A biometric scheme is a pattern-recognition scheme that identifies a human based on a feature vector obtained from a particular physiological or behavioral attribute that the human possesses [4]. The feature vector is generally kept in a database for classification. Gender recognition and human identification from gait sequences are an emerging and efficient technique [5].
1.1 The motivation of this study
As there are many situations where gender recognition and human identity play their role for security purposes like in gender base mall entry [6], entries in parks [7], detection of intruders, and identifying the movement of humans near the line of control (LOC) and borders [8]. In this study, we projected a fog computing-based Human Identification and Gender Recognition using SRML and SVM with SURF from Gait sequences, which will improve its accuracy in real time. It takes less computing time and performs faster than previous algorithms as there is localization for data storage and processing among distributed fog nodes. Several applications mostly for analytics and Big Data need together Fog localization and Cloud globalization in a single system.
1.2 Main contributions of this article
The main contribution of this article is as follow:
-
A Fog Computing and Machine Learning model for Human Identity and Gender Recognition using SRML and SVM with SURF from gait sequences has been proposed for fast processing and high accuracy at the fog level of the system. Real-time alerts are also generated for unauthorized humans. Parallel processing concept at fog and cloud level to make it more effective.
This article is organized into various sections. Section 2 presents an overview of some of the key studies in the area of gait recognition systems. Section 3 discusses in detail gait recognition and some of the related concepts used in this study. Section 4 describes in detail the proposed methodology for Gait recognition in the fog layer using SURF, SRML, and SVM. Section 5 discusses the FCML-Gait implementations and performance analysis, as well as the results. Lastly, section 6 concludes the work with some observations and future research directions.
2 Related work
Jiwan Lu et al. [9] addressed the issues raised in identifying a human and recognizing gender from gait series with random walking. Most datasets assume that humans walk or move along a static route or a pre-defined pathway, which is impractical. To address this issue, a new gait dataset known as ADSC-AWD (Advanced Digital Sciences Center-Arbitrary Walking Directions) is generated in which humans walk freely and openly. Human silhouettes are extracted from each gait series and then clustered. As a feature, a C-AGI is determined for each cluster. SRML is used to differentiate gait character abstraction. They attained a rate comparable to existing gait-based gender recognition systems.
Jeevan et al. [10] developed earlier gait representations that collect both moving and looking details and are sensitive to changes in various circumstances such as bag holding and fashion style. Shannon Entropy calculates the variability in the silhouette. It understands general moving details and reacts to situations that affect appearance. Pal and Pal Entropy are proposed as solutions to this problem. CASIA datasets A, B, and C were used to demonstrate the effectiveness of the projected gait illustration. They obtained reasonably good results on a large database, such as CASIA datasets B and C, indicating the technique's suitability for large datasets.
Arun Joshi et al. [3] used SVM and back propagation neural networks to explain an efficient and easy method for automatic human recognition from body silhouette. Just two kinds of features were obtained in this method: the length and width of the silhouette.
Xiaohui Zhao et al. [11] demonstrated a gait-based strategy for humans moving in random directions. In a broad sense, the monitor equipment's view angle in situations of the detector matter is proposed using an angle estimation scheme. The drawback of the ACM (Appearance Conversion Machine) is that good-quality exchange results are only achieved for like posture. To compensate for this drawback, modified ACM generates a better recognition outcome for distant stances.
Lopez Fernandez et al. [12] proposed a new approach for multi-view gait recognition for humans moving on uncontrolled routes. Considering the participant's mobility into account, a unique walking invariant gait representation focused on the angular evaluation of 3D objects is used. The supermajority strategy is used to enhance classifier performance. The moving gait sequences are classified using a support vector machine. The efficiency for gait recognition is demonstrated on uncontrolled routes.
Daigo Muramatsu et al. [13] presented a gait recognition system that improves correctness in situations where views are divergent. The view transformation technique is used to generate multiple joint gait features for changing gaits. Multiple scores are computed to measure the stability of the attribute and a possibility ratio from the results. The result shows that good calibration and discrimination outcomes are achieved. However, because this strategy is considered on view challenges of gait recognition, other aspects such as clothing, possessions, and gait speed may influence the recognition rate.
Sruti Das Choudhury and TardiTjahjadi [14] proposed a gait recognition system that is unaffected by various gait identification challenges, such as unusual variability in handling and clothing.
Xin Chen et al. [15] discussed how human gait is influenced when walking with different types of individuals. A prototype referred to as a latent conditional random field is used to generate various features, and the model is built using a support vector machine template. The results revealed that this approach outperforms for gait recognition while moving with different participants.
Derlatka Marcin [16] described a method focused on ground reaction forces (GRF) to enhance the efficiency of gait recognition for women going in varying footwear such as high-heeled shoes and sports shoes. The expertise of moving in high-heeled shoes has a significant impact on results.
Cheng Fengjiang et al. in [17] have projected an efficient and speedy person gait recognition system. It was built with a Kinect sensor and MATLAB software in combination with great mathematical computing power. They attained two innovations in this approach. The experimental outcomes showed that the system is competent for gait recognition and will be very supportive in the area of identification and security.
Munish Kumar et al. [18] have discussed various vision-based techniques for gait recognition. In this, all the aspects related to data capturing and environmental factors influencing gait recognition are considered. SVM is used for gender recognition to provide faster responses and higher accuracy.
Muhammad Hassan Khan et al. [19] described a method that directly works on videos instead of working on the silhouette. Spatiotemporal is used to find the local descriptors as a feature, and then, the linear SVM classifier is used. The method is applied to five different gait datasets.
Hidalgo et al. in [20] have projected a cloud-based gait analysis on mobile devices by applying the K-Nearest Neighbor (K-NN) for classification and generated their dataset.
Batool et al. in [21] have discussed an IoT-cloud-based technique for gait analysis using a machine learning technique and also effectively addressed major threats like imitation attacks. The cloud-level processing is not preferred for real-time applications as having more delay.
3 GAIT recognition and related concepts
3.1 Human gait recognition
Gait recognition and identification are a technique to know a person, by the smartness of their walking [22]. It is a sign-less unobtrusive technique for biometric recognition which proposes the opportunity to identify and recognize humans from a distance without any participation or assistance by the subject side, due to this property, it is so attractive technique for recognition or identification [23].
The attention to gait recognition as an emerging biometric technique is strongly provoked by the requirement for automatic recognition for visual observation, monitoring, and controlling applications. Nowadays, the utilization of human gait for individual identification in observation applications has magnetized researchers or inventors from computer vision [24]. The appropriateness of gait recognition or identification for observation systems emerges due to the reality that gait sequences can be obtained from the distance in addition to their non-invasive character [25].
Gait recognition is more appealing because physiological and other behavioral characteristics require human collaboration and do not produce better results in low-resolution image data. [26].
3.2 Gait metric learning algorithm
3.2.1 Sparse reconstruction-based metric learning (SRML)
Sparse reconstruction-based metric learning is a distance metric that simultaneously reduces intra-class sparse reconstruction inaccuracies while increasing inter-class sparse reconstruction inaccuracies. Indeed, discriminative details are used to recognize gaits [9]. Multiple C-AGI features are computed for each gait series using pre-processing and feature-based metrics, and all of these C-AGIs are used to describe specific gait from different poses and viewpoints.
The projected SRML algorithm is concluded as:

The author’s experimental results in [9] demonstrated that the approach produces a significantly higher recognition rate than other metric learning techniques commonly used for gait recognition. It investigates point-to-set distance measures, which effectively model massive intra-class viewing variability even with a small amount of training data.
3.3 Speeded up robust features (SURF)
Speeded Up Robust Features (SURF) are a confined keypoint indicator and descriptor that can be applied for item identification or certification or cataloging or 3D rebuilding [27]. It is partially motivated using the scale-invariant feature transform (SIFT) [28]. Typical edition of SURF is faster than SIFT and as declared by its writer to be extra strong beyond diverse image transformations than SIFT.
Speeded-Up Robust Features method provides finding of interest points, description feature vectors [29], and matching. Initially, Herbert Bay suggested the SURF algorithm in 2006 and is autonomous for scale and rotation [30]. It is comparable to Scale Invariant Feature Transform, however, faster than SIFT as of utilizing Integral images. SURF generates blob-like formations on the bends of items lying on the images. These blobs are found through the determinant of Hessian (DoH) matrix having altered second-order Gaussian derivative which is standardized with the discrepancy of Gaussian [30]. A native maximum is determined in whichever regions of the image while Gxx and Gyy derivations are normally positive and Gxy is negative.
In the SURF detector, the DoH filter is utilized for convolving the input image. Secondly, search the local maxima among neighbor pixels, and each local maximum point found is understood. Lastly, for each key point, values for x, y, and DoH are computed. The SURF descriptor's primary goal is to provide precise pixel details over the local neighborhood [30]. Since the SURF descriptor is required to recognize key point direction, pixels in its neighborhood region were convolved with lateral and vertical Haar Wavelet reactions [31]. The SURF descriptor is applied to a region that is divided into 4 × 4 subregions. These subregions are identified by wavelet estimated values as dx for horizontal and dy for vertical. The wavelet responses are then computed by sampling each subregion 5 × 5 times. The fundamental view of each subarea known as vector v is defined as v = {Ʃdx, Ʃ|dx|, Ʃdy,Ʃ |dy|}. Concatenation 4 × 4 subareas result in 16 × 1 vector for every key point as the descriptor [31]. Integral image is utilized for getting better the processing time as calculations are performed by traversing the original image simply one time [30]. The integral image I(x) is an image in which every point p(x) = (x, y)T holds the addition of every pixel of a rectangular area under consideration between 0 origin and x point.
The hessian matrix-supported detector is used to locate the key points, resulting in high accuracy and a short computing time [30]. The Hessian matrix determinant expresses the magnitude of the response. Equation (2) denotes the Hessian matrix, where m = (x; y) is a key point, σ is a scale, and Dxx(m, σ) is the Gaussian second-order derivative convolution similar to Dxy(x, σ) and Dyy(x, σ).
where
and
SURF technique is the speeded-up edition of SIFT, having a better encouragement in real time [31]. The recognition system's efficiency is further improved by using the fused feature vector obtained from SURF and other techniques [32, 33]. SURF and SIFT methods are applied broadly for the recognition and tracking of objects to maximize recognition accuracy [34].
3.4 Classifier for gait-based human recognition
A support vector machine, as explained below, performs human recognition:
3.4.1 Support vector machines (SVMs)
Support vector machine (SVM) is an advanced classification method established by Boser, Guyon, and Vapnik in 1992 [35]. SVM classifiers are broadly applied in bioinformatics (and other disciplines) because they are extremely correct and are capable of computing and manipulating high-dimensional data like gene expression and elasticity to model different data sources [36, 37]. SVM fits into the universal category of kernel schemes.
SVMs have managed knowledge models with related learning algorithms that examine the information and are used to identify arrangements for categorization and regression investigation [38, 39]. Taking a group of training examples, everyone is considered as a member of one of the two classes, SVM training method constructs a model that allots fresh examples into one class or another. The SVM classifier is normally employed as an element of bioinformatics (and contrasting orders) due to its high accuracy and processes the high-spatial details, for example, gene interpretation [40]. SVM fits in with the universal class of portion schemes. A portion scheme is a computation that depends on the information immediately through spot items. Using SVM efficiently necessitates a comprehensive understanding of its features and functions. When organizing an SVM, the specialist may wish to settle various options as to how to pre-process the information and data, on which bits to start operating, and lastly, establishing and initializing the dimensions for support vector machines.
SVM is based on the system risk minimization principle, which optimizes the training data set to produce machine learning models. For a training phase of instance-label pairs: (ai, bi), i = 1, 2, 3……, l where ai ϵ Rn and bi ϵ {1, − 1}i (n and l denote the space dimensions and size of training data set). Here if ‘a’ belongs to one group then bi = 1; if ‘a’ belongs to the other group then bi = − 1. In our data set, there are 80 different videos for ‘a’ and 20 different human values as male and female for ‘b.’
SVM primarily focuses on determining the best hyperplane for classification by finding solutions to the quadratic optimization model shown below [39]:
where w and ξi represent the weight vector for learned decision hyperplane and slack variable. K is the penalty factor for balancing the classification correctness. In our approach, K is set to one. SVM categorizes the test instance, x using the decision function shown below [39]:
where sv, \(\beta i\),b and M(xi, x) denote support vectors, Lagrange multipliers, model bias, and kernel function. We used linear kernel SVM in this case, so M(xi, x) equals xi • x.
Like in this case, we intend to provide the viewer with a common overview of entire verdicts and to offer overall rules and procedures. Each process was undertaken using the PyML (Machine Learning in Python) which focused on SVM portioning strategies.
3.5 Fog-cloud computing
Over the last five years, moving data to the cloud for analysis and computing has been the focusing part to handle real-time applications. However, due to new innovative technology like IoT, the cloud computing paradigm is encountering growth challenges [41]. Latency restraints, network bandwidth restraints, resource-constrained devices, continual services without Internet access, and novel security challenges in IoT require new computing and network paradigm termed Fog computing [41].
Fog computing platforms permit the application to run anywhere. It reduces the requirement of specified applications dedicated particularly for Cloud or edge devices. It enables applications from different sources to execute on the same platform without any combined intervention. Moreover, the fog computing platform provides general lifecycle supervision for all applications.
4 FCML-gait: fog computing and machine learning inspired human identity and gender recognition model
The correct and accurate recognition rate is very important factors for indicating the performance of gait recognition techniques as well as for the correct recognition of humans especially in sensitive applications where errors are required to be kept as minimal as possible.
From the literature review conducted in previous section II, it was observed that previously many Gait-based recognition techniques were introduced by researchers across the globe. However, the majority of them were very time-consuming and give low accuracy due to inefficient classifiers, fewer parameters, or performing processing at the cloud which takes more time.
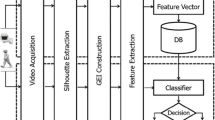
To overcome and address the above issues, we have presented FCML-Gait, a Fog Computing and Machine Learning Inspired Human Identity and Gender Recognition Model using Gait Sequences. FCML-Gait uses SRML and SVM with SURF for improved accuracy and performance. The technique comprises added parameters that enhance the overall efficiency of the proposed work. The layered arrangement of the projected model is shown in Fig. 1.
In the proposed framework, the binary human silhouette from each frame of the input video of the walking person is detected by subtracting the background. Features such as cycle lengths, length of step size, the center of mass, and arm movement are extracted and selected using various image processing operations. Frames are clustered using the AP clustering technique, into several clusters, and then, the C-AGI feature is computed for each cluster. For each subject, a distance metric SRML feature is computed for all gait sequences.
4.1 Dataset used
A publicly available benchmark gait dataset Advanced Digital Sciences Center-Arbitrary Walking Direction (ADSC-AWD) [9] is used in the proposed method which is collected indoors. In the ADSC-AWD dataset, there are a total of 20 individuals (13 males and 7 females) and every individual has four different videos. Figure 2 indicates a portion of the example images of the ADSC-AWD dataset.
In a real-time application, the outdoor datasets are collected via IoT devices in the data acquisition layer as depicted in Fig. 3.
The accuracy, precision, recall, F-measure, C-time, and R-time performance metrics have been measured, and relative analysis of the projected (FCML-Gait) method with the existing (SRML) technique has been performed.
The IoT-based gait recognition architecture is divided into four (4) distinct layers as depicted in Fig. 3. In the data acquisition layer, real-time gait sequences are captured using IoT devices or image capturing sensors. Feature vector extraction and classification using SURF, SRML and SVM are performed in the Fog layer to improve the performance and real-time alerts are generated for intruders. Decision-making like gender ratio prediction and image record storage is performed efficiently in the cloud. We can apply this model for gender base mall entry, entries in parks, and to identify the movement of humans near the line of control (LOC) and borders.
The working of the FCML-Gait is explained in detail using the following working algorithm.

The complete flow chart of the projected framework is shown in Fig. 4, where the flow is categorized as a training sequence and testing sequence.
Step 1 Design a GUI(Graphical User Interface) for the simulation of the FCML-Gait for Human Identity and Gender Recognition from Gait Sequences where SURF, SRML, and SVM are used. The GUI for the projected approach is shown in Fig. 5. It comprises two sections, a testing section, and a training section. In the training section, a database of gait sequences for the proposed work has been uploaded for matching purposes. Training is done by using algorithms named sparse reconstruction-based metric learning (SRML) and support vector machine (SVM). SVM classifies the extracted features obtained from C-AGI and SURF.
Step 2 Develop a code for uploading the video data for training and testing of proposed work from the ADSC-AWD database of gait. There are 80 videos for twenty different subjects four for each subject. Preprocessing on the uploaded video is applied to ensure that the video used for recognition is compatible with the proposed framework. In the pre-processing step, we have applied filtering (background subtraction), resizing, conversion (into gray and binary form), to make the uploaded video useful.
Step 3 Clustering of the pre-processed frames using the affinity propagation (AP) technique. The code for C-AGI is also developed to act as the gait feature for every cluster. For the given gait series, suppose there are Nj frames in the jth cluster, then the feature C-AGI is computed as in Eq. (8). Figure 6a, b represents the primitive component, i.e., the cluster of frames and their average, respectively, of the uploaded video which helps in the feature extraction process where SURF is used.
Step 4 The code for SRML is developed for machine learning and a distance matrix (W) is found which is used for training and testing. SRML is applied to detect the region of the frames to be considered for feature extractions and to calculate distance metric (W). Figure 7 presents the notation of each component of the uploaded video and is marked by a red color rectangle which helps in the feature extraction process by using several components.
Step 5 Develop a code for extracting features from the strokes using the SURF descriptor. The Extracted Features of the uploaded video as key points are shown in Fig. 8. It provides findings of interest points, description feature vectors, and matching. SURF descriptor is applied to a concerned region which is splitted into 4 × 4 subregions so that maximum key features of the frame are considered. In the feature extraction technique, the way of walking such as differences in consecutive frames, the distance between hands, and style of gait cycle has been calculated. Primitive components of video frames after applying the feature extraction technique have been displayed in circles.
Step 6 Initialize the SRML and SVM for the training of data according to feature for classification. Save Training Data and simulate with test data and find appropriate results for proposed work with a combination of SRML and SVM.
Step 7 After the training of data, we have tested the gait video to verify the proposed work using the training dataset. In this learning, we have used the combination of SVM and SRML as a classifier to classify the test data according to the training set. Firstly, the features are trained using the SRML, after that the output of SRML acts as the input of SVM and creates a better training structure to achieve better accuracy of the proposed gait recognition system. In the classification process, both humans, as well as their gender, are recognized.
Step 8 The performance metrics like precision, recall, F-measure, R-time, C-time, and accuracy are calculated as shown in Fig. 9 and are analyzed.
5 Discussion on results
The results obtained after simulating the code in the MATLAB environment have been discussed and analyzed in the current section.
Table 1 depicts the parameters for performance of the projected (FCML-Gait) system. The computational time for training is much higher than the recognition time in our proposed approach. However, in most cases, training is done offline, and only recognition is done online. As a result, the increased computational complexity will have no effect on the practical implementation of our suggested approach (Tables 2, 3, 4, 5, 6).
5.1 Comparison of existing (SRML) work with (FCML-gait) proposed system
Further, we relate the accuracy of the suggested work with the previous SRML technique. We analyze the accuracy results based on database training. There is a total of three phases in which training of the proposed FCML-Gait Recognition system has been done.
-
(a)
Training for dataset of Size: 25%
-
(b)
Training for dataset of Size: 50%
-
(c)
Training for dataset of Size: 75%
Tables 2, 4, and 6 depict the comparison of accuracies for ten different iterations after training the FCML-Gait system for datasets of size 75%, 50%, and 25%, respectively, with the previous (SRML).
The average accuracy values for three considered cases: (i) when Training Set Size: 75% as shown in Table 3, (ii) Training Set Size: 50% as shown in Table 5, and (iii) Training Set Size: 25% as shown in Table 7 are obtained as 95.49%, 93.07%, and 92.82%, respectively, which are higher than the previous (SRML)work.
In the proposed system, there is parallel processing in the fog level and cloud level which improves the time complexity. At the fog level, SURF, SRML and SVM are used for features extraction and classification, each having a time complexity of O(n3) as in [9] [42]; therefore, the time complexity of the proposed system is O(n3), where n is the number of instances for training the system.
From the analysis shown in Table 8 and Fig. 10, it is clear that the recognition time of existing methods [9] is more than the proposed FCML-Gait work, and hence, it is also clear that by using SURF, SRML, and SVM, the accuracy of the gait recognition system has improved as SVM is best for binary classification. The proposed model is implemented on hardware that comprises a 2.4-GHz CPU and 4 GB RAM, and its performance will be further improved for more high-end available processors. The computational time of the projected system is greater than the previsions existing methods as shown in Table 8, but it will not affect the performance as the training of the system is performed offline and only the testing is accomplished online efficiently as has less recognition time than the existing methods.
The proposed FCML-Gait approach is cost-effective as it is non-invasive and gives good results even for low-quality datasets. For its implementation minimum hardware infrastructure is required as 2.4-GHz CPU, 4 GB RAM, cameras, or IoT devices for real-time data capturing and producing good results. Further, there is parallel processing at the fog and cloud level which makes it more effective.
A comparative analysis of the proposed work with the earlier studies is performed based on parameters, namely datasets used, algorithm/technique used, Internet of things (IoT), fog computing (FC), cloud computing (CC), accuracy/recognition rate (RR) as shown in Table 9.
6 Conclusion and future work
The human gait is forthcoming behavioral excellence, and many related learning methods have proved that it has exceptional potential for biometric identification and recognition using IoT and fog computing. This research study demonstrated a simple yet efficient fog-based technique (FCML-Gait) for personal identification and gender recognition from gait sequences. We have used SURF, SRML, and SVM at the fog layer to achieve better recognition accuracy in the real-time instance. We have extracted the feature vectors using the SURF feature descriptor, and for verification of the system, an SRML and SVM-based classifier has been used at the fog layer. The accuracy of the proposed FCML Gait-based recognition system outperforms the previous SRML and other techniques as well. The average accuracy values of different samples (for the training set having n = 75%, n = 50%, and n = 25%) are obtained as 95.49%, 93.07%, and 92.82%, respectively, which are higher than previous (SRML) also an alert is generated for an unauthorized human. Further, in terms of recognition time which is another crucial performance metric in recognition systems, the proposed FCML-based recognition system can achieve an average recognition time of 0.0834 s, which is very less than other existing methods available in the literature. In the cloud, records are kept for future use like decision making, prediction of gender ratio, and alert generation. Despite the benefits of the proposed system, it has some limitations as the dataset used is collected indoor, collection and use of outdoor data via IoT devices is needed. It is not implemented in real-world scenarios as having diversity in the datasets and security threats as well which are not taken into consideration. Qualitative features are not considered and have scope to improve the performance further via the concept of fused feature vectors with other advanced classifiers. In the future, we would like to address all the limitations as testing the performance of the FCML-Gait using multiple databases containing different scenarios like collected from dark, fog environment, underwater, walking in a group with different types of persons. Furthermore, we look forward to improving the performance of FCML-Gait by using advanced and more efficient feature extraction methods with fused feature concepts. Additionally, both quantitative and qualitative features can be considered in the future to strengthen the recognition technique. The proposed approach can also be used for the detection of intruders in various real-time applications, recognitions of infected humans during pandemics like COVID-19 in public places as in [43] and is not limited to humans only.
References
Reid, D.A., Nixon, M.S.: Imputing human descriptions in semantic biometrics. In: Proceedings of the 2nd ACM workshop on Multimedia in Forensics, Security &Intelligence, pp. 25–30 (2010).
Agrafioti, F., Bui, F.M., Hatzinakos, D.: Enabling continuous or instantaneous identity recognition of a large group of people based on physiological biometric signals obtained from members of a small group of people. ed: Google Patents (2017).
Joshi, A., Bhushan, S., Kaur, M.J.: Gait Recognition of human using SVM and BPNN classifiers. Int. J. Comput. Sci. Mobile Comput. 3(1), 281–290 (2014)
Ellavarason, E., Guest, R., Deravi, F., Sanchez-Riello, R., Corsetti, B.: Touch-dynamics based behavioural biometrics on mobile devices–a review from a usability and performance perspective. ACM Comput. Surveys (CSUR) 53(6), 1–36 (2020)
Ahmed, K., Doegar, A.: A review on human identity and gender recognition from gait sequences. Int. J. Res. Electron. Comput. Eng. 5(4), 85–91 (2017)
Arroyo, R., Yebes, J.J., Bergasa, L.M., Daza, I., Almazán, J.: Expert video-surveillance system for real-time detection of suspicious behaviors in shopping malls. Expert Syst. Appl. 42(21), 7991–8005 (2015)
Buciu, I., Gacsadi, A.: Biometrics systems and technologies: a survey. Int. J. Comput. Commun. Control 11(3), 315–330 (2016)
Labati, R.D., Genovese, A., Muñoz, E., Piuri, V., Scotti, F., Sforza, G.: Biometric recognition in automated border control: a survey. ACM Comput. Surveys (CSUR) 49(2), 1–39 (2016)
Lu, J., Wang, G., Moulin, P.: Human identity and gender recognition from gait sequences with arbitrary walking directions. IEEE Trans. Inf. Forensics Secur. 9(1), 51–61 (2013)
Jeevan, M., Jain, N., Hanmandlu, M., Chetty, G.: Gait recognition based on gait pal and pal entropy image. In: IEEE International Conference on Image Processing (2013).
Zhao, X., Jiang, Y., Stathaki, T., Zhang, H.: Gait recognition method for arbitrary straight walking paths using appearance conversion machine. Neurocomputing 173, 530–540 (2016)
Fernández, D.L., MadridCuevas, F.J., Poyato, A.C., Muñoz-Salinas, R., Carnicer, R.M.: A new approach for multi-view gait recognition on unconstrained paths. J. Vis. Commun. Image Represent. 38, 396–406 (2016)
Muramatsu, D., Makihara, Y., Yagi, Y.: Cross-view gait recognition by fusion of multiple transformation consistency measures. IET Biometrics 4(2), 62–73 (2015)
Choudhury, S.D., Tjahjadi, T.: Clothing and carrying condition invariant gait recognition based on rotation forest. Pattern Recogn. Lett. 80, 1–7 (2016)
Chen, X., Weng, J., Lu, W., Xu, J.: Multi-gait recognition based on attribute discovery. IEEE Trans. Pattern Anal. Mach. Intell. 40(7), 1697–1710 (2017)
Marcin, D.: Human gait recognition based on ground reaction forces in case of sport shoes and high heels. In: 2017 IEEE International Conference on INnovations in Intelligent SysTems and Applications (INISTA), pp. 247–252 (2017).
Fengjiang, C., Muqing, D., Cong, W.: Kinect-based gait recognition system design via deterministic learning.In: 29th Chinese Control and Decision Conference (CCDC), pp. 5916–5921 (2017).
Kumar, M., Singh, N., Kumar, R., Goel, S., Kumar, K.: Gait recognition based on vision systems: a systematic survey. J. Vis. Commun. Image Represent. (2021).
Khan, M.H., Farid, M.S., Grzegorzek, M.: Spatiotemporal features of human motion for gait recognition. SIViP 13(2), 369–377 (2019)
Hidalgo, M.N., Pastor, F.J.F., Sarabia, R.J.V., Pascual, J.M., Chamizo, J.M.G.: Gait analysis using computer vision based on cloud platform and mobile device. Hindawi Mobile Inf. Syst. Ambient Assisted Living Ambient Intell. Health 2018 (2018).
Batool, S., Hassan, A., Saqib, N.A., Khattak, M.A.K.: Authentication of remote IoT users based on deeper gait analysis of sensor data. IEEE Access 8, 101784–101796 (2020)
Elharrouss, O., Almaadeed, N., Al-Maadeed, S., Bouridane, A.: Gait recognition for person re-identification. J. Supercomput. 1–20 (2020).
Seifert, A., Amin, M.G., Zoubir, A.M.: Toward unobtrusive in-home gait analysis based on radar micro-Doppler signatures. IEEE Trans. Biomed. Eng. 66(9), 2629–2640 (2019)
Khamsemanan, N., Nattee, C., Jianwattanapaisarn, N.: Human identification from freestyle walks using posture-based gait feature. IEEE Trans. Inf. Forensics Secur. 13(1), 119–128 (2017)
“Neural Networks For Non-Intrusive Biometric Recognition,” http://www.advancedsourcecode.com/gaitrecognition.asp. Accessed on 4 June 2020.
Rida, I., Almaadeed, N., Almaadeed, S.: Robust gait recognition: a comprehensive survey. IET Biometrics 8(1), 14–28 (2018)
Khachikian, S., Emadi, M.: A review of detector descriptors’ on object tracking. Electronic Resource (2016).
Gao, J., Huang, X., Peng, G., Wang, M., Wu, Z.: Simplified SIFT feature point detecting method. Appl. Res. Comput. 7 (2008).
Bay, H., Ess, A., Tuytelaars, T., Gool, V.: Speeded-up robust features (SURF). Computer vision and image understanding (CVIU). In: Proceedings of the 9th European conference on computer vision. Springer, Austria (2006).
Pedersen, J. T.: Study group SURF: feature detection & description. In Department of Computer Science, Aarhus University (2011).
Bay, H., Ess, A., Tuytelaar, T., Gool, L.V.: Speeded-up robust features (SURF). Comput. Vis. Image Underst. 110(3), 346–359 (2008)
Bansal, M., Kumar, M., Sachdeva, M., Mittal, A.: Transfer learning for image classification using VGG19: Caltech-101. J. Ambient Intell. Hum. Comput. (2021).
Bansal, M., Kumar, M., Kumar, M.: 2D object recognition: a comparative analysis of SIFT,SURF and ORB feature descriptors. Multimedia Tools Appl. (2021).
Gupta, S., Thakur, K., Kumar, M.: 2D-human face recognition using SIFT and SURF descriptors of face’s feature regions. Vis. Comput. Int. J. Comput. Graph. (2020).
Steel, S.J., Hechter, G.K.: Application of Support Vector Machines in a Life Assurance Environment, pp. 458–465. Springer, Berlin (2005)
Pradhan, N., Singh, A. S.: Machine learning architecture and framework. In: Machine Learning and Cognitive Computing for Mobile Communications and Wireless Networks, pp. 1–24. Wiley, Hoboken (2020).
Sharma, S., Lone, F. R., Lone, M. R.: Machine learning for enhancement of security in internet of things based applications. In: Security and Privacy in the Internet of Things. Chapman and Hall/CRC, Boca Raton (2020).
Saini, A., Singh, H.: Enhanced human identity and gender recognition from gait sequences using SVM and MDA. Int. J. Comput. Appl. 119(2) (2015).
Ng, H., Tong, H., Tan, W., & Abdullah, J.: Gait classification by support vector machine. Commun. Comput. Inf. Sci. 623–636 (2011).
Byvatov, E., Schneider, G.: Support vector machine applications in bioinformatics. Appl. Bioinform. 2(2), 67–77 (2003)
Nandyala, C.S., Kim, H.: From cloud to fog and IoT-based real-time U-healthcare monitoring for smart homes and hospitals. Int. J. Smart Home 10(2), 187–196 (2016)
Abdiansah, A., Wardoyo, R.: Time complexity analysis of support vector machines(SVM) in LibSVM. Int. J. Comput. Appl. 128(3), 28–34 (2015)
Singh, S., Ahuja, U., Kumar, M., Kumar, K., Sachdeva, M.: Face mask detection using YOLOv3 and faster R-CNN models: COVID-19 environment. Multimedia Tools Appl. 80, 19753–19768 (2021)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Ahmed, K., Saini, M. FCML-gait: fog computing and machine learning inspired human identity and gender recognition using gait sequences. SIViP 17, 925–936 (2023). https://doi.org/10.1007/s11760-022-02217-z
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11760-022-02217-z