Abstract
One of the areas in which wireless networks based on visible light communication (VLC) are considered superior to traditional radio-based communication is security. The common slogan summarizing VLC security features is: WYSIWYS—”What You See Is What You Send”. However, especially in the case of infrastructure downlink communication, security with respect to data snooping, jamming and modification must be carefully provided for. This paper examines the physical layer aspects of VLC networks with respect to possible disruptions caused by rogue transmitters. We present the theoretical system model that we use in simulations to evaluate various rogue transmission scenarios in a typical indoor environment. We use estimated bit error rate as a measure of the effectiveness of jamming and rogue data transmission. We find that it is quite easy to disrupt, and in some cases to even hijack legitimate transmission.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
Visible light communication (VLC) is a wireless optical communication technology through which baseband signals are modulated on the light emitted by an LED: [1,2,3]. The decreasing cost and hence rapid adaptation of LED-based light make VLC a promising communication technique and a significant alternative to radio-based wireless communication. As user demand for data transmission throughput and availability continues to increase, “traditional” radio-based communication systems, such as Wi-Fi, Bluetooth, ZigBee, etc. fail to deliver because of their bounded channel capacity and transmission rates due to the limited radio spectrum available. VLC data transmission networks provide an attractive alternative to traditional wireless techniques.
VLC systems have been proposed and implemented both for indoor and outdoor applications—see [2] and [4]. Indoor applications include a range of communication facilities provided today by radio-based WLAN and Personal Area Networks (PAN), and range from: office communication [5], multimedia conferencing [6], peer-to-peer data exchange, data broadcasting—especially multimedia such as home-audio and video streams, see: [7,8,9], to positioning: [10, 11]. VLC systems also provide a safe alternative to electromagnetic interference from radio frequency communications in hazardous environments such as mines and petrochemical plants, and in applications where traditional WLAN communication may interfere with specialized equipment, for example in healthcare—especially in RF-restricted zones like emergency rooms and intensive care units [12, 13]—and in aeronautics [14].
VLC is also starting to be considered as a way of augmenting or even replacing RF networks; for example, a wide range of techniques aimed at VLC based multimedia networks was developed under “hOME Gigabit Access” project (OMEGA) [7] sponsored by the European Union. The usage of smartphone cameras and light sensors brings VLC to the field of mobile computing and sensing. VLC has the potential to evolve into a general WLAN standard in [15] with the OpenVLC platform, the authors have demonstrated that it is relatively easy with current software defined radio (SDR) toolkits to implement the TCP/IP suite on the VLC medium.
One of the areas in which VLC techniques are considered superior to traditional radio-based communication is security. The directivity and high obstacle impermeability of optical signals are considered to provide a secure way to transmit data within an indoor environment, making the data difficult to intercept from outside. The common slogan summarizing VLC security features is: WYSIWYS—”What You See Is What You Send” [16]. As the recent history of IT technological progress has taught us, a common mistake in the development of novel communication techniques has been to ignore or marginalize security issues. Such was the case with the IPv4 internet protocol suite, fiber-optics based networks, and more recently, with early adopted WLAN technologies. Currently, the VLC industry seems to be on the same path again: the indubitable “pro-security” physical characteristics of visual light communication have steered the developers’ focus away from the security track.
The shared nature of the medium allows wireless networks to be easily monitored and broadcast on. Attackers may not only easily monitor communication but also launch jamming (denial of service) attacks. Attacks on the physical level that disregard MAC-level protocols can effectively block the network and are not remedied by traditional security mechanisms. A risk assessment of VLC communication with respect to the communicating parties of three basic classes: mobile (smartphones, tablets, wearables, etc.), fixed (PCs, peripherals, and appliances) and infrastructure (fixed in-room transmitters) was conducted in [17]. By analyzing basic physical characteristics of the VLC communication channel, it was shown that particularly in the case of infrastructure downlink communication, security with respect to data snooping, jamming and modification must be carefully provided for. In order to ensure the dependability of VLC networks, we must better understand the physical layer mechanisms of executing a hostile-transmitter type attack.
In this paper, we focus on possible disruptions caused by rogue transmitters in VLC networks. Our main contributions can be concisely stated as follows:
-
We adapt existing VLC theoretical models to our needs–namely to compute bit error rate (BER) as a measure of rogue transmitter influence on “legitimate” data transmission.
-
We design and evaluate possible attack scenarios in a two-step approach:
-
we use a specialized CAD tool to design a realistic indoor VLC lighting infrastructure
-
we conduct simulations to establish the influence of rogue transmitter(s) on the VLC system as a whole.
-
The structure of this work is as follows: in Sect. 2, we will describe the current state of VLC security research; in Sect. 3, we will present the theoretical system model which we will use in subsequent simulations to evaluate various rogue transmission scenarios; in Sect. 4, we will describe the physical properties of evaluation scenarios; in Sect. 5, we will show and discuss simulation results; and in Sect. 6, we will summarize the paper and outline areas of future research.
2 Current State of VLC Security Research
2.1 Confidentiality and Data Snooping
A common assumption in VLC, as stated for example in the IEEE 802.15.7 standard [18], is that: “Because of directionality and visibility, if an unauthorized receiver is in the path of the communication signal, it can be recognized”. However, this is not always true; let us consider a case of communication with an “infrastructure” transmitter. Both in the case of the NLOS channel and LOS, an unauthorized receiver may be easily introduced into the environment without being recognized. Snooping on VLC transmission is, of course, limited by high obstacle impermeability and is more difficult than Wi-Fi snooping, but there is no obvious reason why it should not be possible. In [19], it was shown experimentally that eavesdropping on VLC transmission is indeed possible. The equipment used, based on a standard low-cost SDR design, was able to achieve acceptable BER rates in a range of different scenarios. The authors evaluated different room configurations and were able to decode high-order modulated 64-QAM VLC signals outside of the room, via door gaps, key holes and windows protected by special “privacy” coatings.
Up till now, the confidentiality of VLC communication has mainly been tackled on the information-theory level, referring to the discrete memoryless wiretap channel and the metric of the channel’s secrecy capacity, as originally introduced by Wyner [20]. In [21], the authors proposed to use the MIMO technique and beam-forming (similar to BF/MIMO implemented in Wi-Fi networks) to establish a secure channel between the transmitter and the receiver located in a particular physical location. The bit error rate (BER) was minimized at the receiver’s location, while it remained unacceptably high in the rest of the area. In this way, a potential eavesdropper physically located some distance from the legitimate receiver was unable to properly decode the data. This was attained without significant influence on the lighting characteristics and was therefore unobservable to the users. A similar approach was proposed in [22] using the multiple input single output (MISO) technique, together with null-steering and artificial noise—an achievable secrecy rate was calculated numerically. In a related work [23], this approach was also in part verified in a real environment.
2.2 Jamming and Data Modification
Let us consider the possible schemes for introducing a signal jamming or data-modifying device into the VLC infrastructure channel. The attacker may choose to use both a directed-Line of Sight (LOS) or non-directed Non-Line of Sight (NLOS) transmitter–receiver arrangement; but, due to power considerations, a LOS model will be preferred. In general, the attacker’s aim is to achieve a higher illumination at the receiver than that provided by the legitimate transmitter.
The major practical concern from the attacker’s point of view is to ensure that the illumination provided by the rogue transmitter remains undetected by users. Hence, the attacker may introduce his own (preferably) highly directed transmitter or “hijack” a part of the legitimate infrastructure. VLC infrastructure networks consist of numerous independent transmitters to provide adequate coverage and capacity. Multi-transmitter “femtocell” VLC networks are also studied as an extension of traditional Wi-Fi and cellular networks [24]. In such environments, the installation of a rogue transmitter may easily pass undetected. A second possibility is hijacking a part of the legitimate VLC infrastructure via a wired or wireless channel. In a large installation, such malicious intervention may easily pass undetected.
Many different attack strategies that a wireless jammer can perform in order to interfere with other communications have been proposed in the literature (see for example [25]). In the most commonly accepted classification of these attack strategies, four general ones are described:
-
Constant jammer—continually emits a signal consisting of a random bit sequence.
-
Deceptive jammer—instead of sending out random bits, the deceptive jammer constantly injects regular packets into the channel without any gap between subsequent packet transmissions.
-
Random jammer—alternates between sleeping and jamming.
-
Reactive jammer—stays quiet when the channel is idle, but starts transmitting a radio signal as soon as it senses activity on the channel. A reactive jammer targets the reception of a message.
Since in this work we address the physical level of communication, and we do not consider the abstraction of data packets, we can assume that the rogue transmission that we model best matches the constant or deceptive jammer strategies.
3 The System Model
The system components are an LED transmitter, consisting of multiple light sources, and a photodiode receiver. The received signal depends on the physical characteristics of the transmitting LED, the receiver, and channel characteristics which, in turn, are determined by a room’s physical properties (dimensions, wall reflectivity). We use ray optics to calculate signal and noise levels and to derive adequate metrics. We assume the multiple input single output (MISO) model with multiple luminaires, each consisting of multiple transmitting LEDs (both legitimate and rogue) and one photodiode detector. A single transmitting LED is characterized by a half-power semi-angle and center luminous intensity (measured in cd). The receiver is a simple non-imaging photodetector with an optical filter, optical concentrator and a single photodiode element. Its characteristics are as follows: the field of view (FOV) angle, the gain (being a product of filter and concentrator gains), the photodetector area and the conversion efficiency (measured in A/W).
The metric that we use to measure the impact of the rogue transmitter is the bit error rate (BER), which depends on the signal to noise ratio (SNR) and modulation scheme, for M-PAM modulation:
where M is the number of signal levels and the Q-function is defined in a standard way (the tail probability of the standard normal distribution). The approximation in (1) results from the assumption that only one bit error occurs in Gray coding [26].
We calculate SNR as follows:
where \(s_{data}^{{}}\) is the data signal, \(s_{rogue}^{{}}\) is the signal transmitted by “rogue” (interfering) luminaires, and N is noise.
We want to test the influence of the rogue data source on the legitimate transmitter, as well as the opposite: how the legitimate transmitter influences the signal quality of the rogue one. Hence, we also want to calculate the BER and SNR assuming that the rogue signal is data and that the legitimate signal is treated as noise:
The problem of noise in VLC environments has been studied in detail [27]. In general, the following noise sources should be considered: background and transmitting LED shot noise, thermal noise in the detector and the influence of inter symbol interference (ISI):
where N is the total noise variance and \(\sigma_{shot}^{{}}\), \(\sigma_{thermal}^{{}}\), \(\sigma_{ISI}^{{}}\) is the standard variance of shot, thermal and ISI respectively. Proper estimation of noise in VLC environments is crucial in studying maximum attainable transfer rates under various conditions and modulation schemes. The input-referred noise variance depends on the signal data rate; for data rates of interest in our scenario (105–107 bits/s), the dominating noise factors are ISI and background shot noise. Hence, we will consider only these sources:
where q is the electronic charge, R is the responsivity of the photodiode, B is the equivalent noise bandwidth, P is the received power, I bg is the background current; and where for a p-i-n/FET receiver, we assume I2 = 0.56. In the multi-luminaire study that we conduct in this paper, the dominant noise factor is the interfering signal from neighboring luminaires and not physical noise itself.
Now we will present an analytical model of the optical wireless channel, which will let us derive SNR and BER measures for different physical scenarios.
A single LED is a Lambertian emitter—its radiation intensity is a cosine function of the viewing angle and is given by:
where \(\theta\) is the irradiance angle, \(P_{t}\) is the transmitted power and m is the order of Lambertian emission which is given by the irradiance semi-angle \(\theta_{1/2}\) (the half-power angle):
Light propagates from the LED to the receiver via a channel which is modeled by the direct channel transfer function h d :
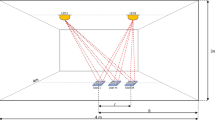
where \(\theta\) is the irradiance angle, \(\varphi\) is the angle of incidence, A is the receiver’s area, \(R\left( \psi \right)\) is the receiver’s gain, d is the distance from the LED to the receiver and \(\theta_{FOV}\) is the receiver’s field-of-view semi-angle. The geometric model of this simple line of sight (LOS) case is shown in Fig. 1.
To make the model more realistic, we will also consider the effect of first reflections from the walls; the channel transfer function for the reflection path—h r is:
where \(\theta\) is the irradiance angle, \(\psi\) is the angle of incidence, A is the receiver’s area, \(R\left( \varphi \right)\) is the receiver’s gain, \(d_{1}^{{}}\) is the distance from the LED to a reflective point, \(d_{2}^{{}}\) is the distance from a reflective point to the receiver, \(\rho\) is the reflectance factor, dA w is a reflective area surface element, α is the angle of irradiance to a reflective point and β is the angle of irradiance to the receiver. The geometric model of this case is shown on Fig. 1.
For a single source, the output signal of the LED transmitter is given by the following general formula:
where: \(P_{t}\) is the power transmitted from a single LED, µ is the modulation index, and x(t) is the modulating signal. Assuming that the receiver is DC blocked, we get the following general formula for the received signal:
Considering the “legitimate” and “rogue” sets of transmitters, we obtain the following:
We use (14) and (15) in a numeric model to calculate the BER as given in (2) and (4) for our scene.
4 The Simulated Scene
4.1 The Simulated Environment
For our numerical simulations, we will use a standard “office environment” arrangement, akin to the ones typically used in similar work [1, 21,22,23,24]. However, we have decided to adopt a larger room size than was considered in the above mentioned work, as in our opinion it better fits real-world environments. We have also considered realistic luminaire arrangements used with typical off-the shelf lighting products. We have designed a single room scene illustrated in Fig. 2. The room’s dimensions are: 7 m × 7 m × 2.8 m. The detector’s photodiode at the reference plane is set at the “desk level”—0.85 m. The room and VLC system’s parameters are given in Tables 1, 2 and 3. We have tested several different scenarios of luminaire placement with different arrangements of legitimate and rogue transmitters. To design and verify luminaire arrangement, we used a two-step approach: in the first step, a specialized CAD tool [28] was used. This allowed us to set-up realistic scenarios based on standard luminaire components. The scene was initially designed to provide ergonomic lighting conditions which meet current standardsFootnote 1 [29]. A sample scene as modeled in the CAD tool is shown in Fig. 3. The light power levels, the SNR and BER, for different luminaire placement scenarios were calculated numerically according to formulas (2), (4), (14) and (15)—as described in Sect. 5.
We have simulated three luminaire placement scenarios:
-
(1)
G1—a 3 × 4 recessed luminaire grid—Fig. 4,
-
(2)
G2—a 2 × 4 recessed luminaire grid with an additional 1 × 3 array of “downlight” lower power elements—Fig. 5,
-
(3)
GC—a 2 × 3 luminaire grid surrounded by a circular arrangement of lower power “downlight” elements—Fig. 6.
The first scenario is the most common, standard solution for office spaces. The second scenario is a typical light placement for office spaces (meeting rooms, open spaces, etc.), with downlights providing additional illumination in recessed areas which are further from natural sources of light, such as corridors, etc. The third scenario provides a more uniform light distribution in the room perimeter, which is a favorable feature for VLC communication. In scenario G1, one type of luminaire is used—a square 60 × 60 cm panel module with a 70 deg. radiation semi-angle. In scenarios G2 and GC, two types of luminaires are used: a square 60 × 60 cm panel module with a 70 deg. radiation semi-angle and lower-power luminaires with a more narrow radiation semi-angle of 30 deg. In all cases, we have introduced rogue transmitters.
4.2 Rogue Transmitter Choice and Placement
We have tested various scenarios of rogue transmitter placement, taking into account the practical possibility of an attacker modifying the VLC infrastructure. We have only considered scenarios in which a whole set of LEDs constituting a luminaire is taken over by an attacker. This is a realistic assumption taking into account the fact that all LEDs in the luminaire are driven by a single amplifier and modulator, and it is not technically feasible to hack “a part” of the luminaire. Scenario G1 corresponds to the case where one of the luminaires was physically modified or replaced (Fig. 4)—one out of 12 luminaries is a rogue one. Two different rogue transmitter placement options were tested here—central and peripheral. In scenario G2—Fig. 5, we considered the possibility of an attack where one or all 3 of the downlight luminaires are taken over. In scenario GC—Fig. 6, we tested the possibility of taking over all 10 (the full “circle”) or 5 (half of the “circle”) of the downlight luminaires.
5 Simulation Results
In all the scenarios, we show the logarithmic plots of the computed Bit Error Rate achievable for legitimate and rogue data transmission: BER s (2) and BER r (4). We assume that a maximum BER level of 10−3 is required for effective transmission.
Scene G1—in this scenario, we test an arrangement with one rogue transmitter placed in two locations: centrally and peripherally. With the rogue placed centrally, legitimate transmission is jammed in 11% of the total room area—Fig. 7; with peripheral placement, legitimate transmission is jammed in 18% of the area—Fig. 8. With the BER r not lower than 10−1, effective rogue transmission is not possible in this scenario—Figs. 9, 10.
Scene G2—in this scenario, we test two sub-arrangements: with one and with three rogue transmitters. In the case of one rogue transmitter placed centrally in the downlight row—legitimate transmission is jammed in 10% of the total room area—Fig. 11. Rogue transmission is possible in a very limited area directly under the transmitter (less than 1% of the total area)—Fig. 12. With three rogue downlight luminaires legitimate transmission is jammed in an area of 42%—Fig. 13, while rogue transmission is possible in an area of 10%—Fig. 14.
In this scenario we have also tested the impact of an irradiance semi-angle on the BER, increasing \(\varphi_{1/2}\) from the default value 30o deg. to 45o, for all type “d” (rogue) luminaires (transmitted power remains constant). As the semi-angle is increased, the BER r increases to values in the range of 10−1, making rogue transmission infeasible—Figs. 15 and 16. With an increase in the rogue transmitter semi-angle, the area of jammed legitimate transmission (BERs above 10−3) increases from 10 to 25% (comparing with results shown on Fig. 11).
Scene GC—in this scenario, we also test two sub-scenarios: with 5 and 10 rogue transmitters. In the first case, half of downlight luminaire “circle” is rogue; in the second sub-scenario, whole downlight “circle” consists of rogue luminaires. With 5 rogue luminaires, legitimate transmission is possible in an area of 50%, while rogue transmission again is attainable only in small recessed areas (less than 2.5% of the total area)—Figs. 17 and 18. With 10 rogue luminaires on the perimeter, jamming is very effective -legitimate transmission is possible only in an area of 25%—Fig. 19, while rogue transmission is feasible only in the recessed room areas (less than 5% of the total area)—Fig. 20.
To summarize—depending on the arrangement of the luminaires, with the take-over of only one out of 12 transmitters, it is possible to jam communication in a relatively large area (up to 18% of the total area). In the second scenario, with access to three low power luminaires out of the total of 19 transmitters, it is possible to block almost half of the whole area. In the last scenario, controlling half of the peripheral low-power luminaires blocks legitimate transmission in 50% of the area, while if all the low-power luminaires are rogue, transmissions are blocked in 75% of the area. On the other hand, depending on the scenario, effective rogue transmission is possible on up to 10% of the whole area.
6 Summary
VLC networks are currently considered as a means of augmenting traditional radio-based WLANs. However, the issues of VLC security are only beginning to be tackled. As with radio-based networks, the shared nature of optical medium allows adversaries to generate jamming attacks. In this work, we have presented a numerical study of a VLC system with rogue transmitters. To the best of our knowledge, it is the first time the problem of interfering legitimate and illegal VLC transmission has been considered. Our simulation “scenes” have been designed and verified with a CAD planning tool to ensure relevance to real-world environments. We have numerically calculated the Bit Error Rates of interfering legitimate and rogue transmission in various office room scene arrangements. We have concluded that it is feasible, with limited access to the transmitter infrastructure, to jam transmission in a large area of up to 75% of the whole scene. It is also possible to introduce illegal transmission on limited areas of up to 10% of the whole scene. In our opinion, this study brings forward the issue with the security of VLC based wireless LANs with respect to rogue transmission.
As a next step, the possibility of hostile data modification in VLC networks should be considered. This may be attained with reactive jamming techniques. As was demonstrated in [25], real time reactive jamming is easily in reach of attackers with the use of SDR technology. In the above-mentioned work, ZigBee (IEEE 802.15.4) protocol devices were used. It is worth noting the MAC level similarities of ZigBee and the VLC 802.15.7 standard. Detecting the presence of a jamming attack in VLC networks also remains an open issue. In [30], various “consistency checking” methods for detecting a wireless radio jammer have been proposed; the adoption of these techniques for VLC systems and the development of new rogue transmitter detection methods dedicated to VLC would also be interesting areas for future research.
As WYSIWYS—”What You See Is What You Send” remains mostly a slogan, appropriate security mechanisms must be implemented in the data-link layer (and/or higher network layers) to cope with the possible introduction of rogue access points.
Notes
Although some controversy remains as to the proper light-level standards for office workers, we have assumed an optimal level of 500 lx and not less than 300 lx for the desk surface.
References
Nakagawa, M. (2007). Visible light communications. In Proceedings conference on Lasers and Electro-Optics/Quantum electronics and laser science conference and photonic applications systems technologies, Baltimore. doi: 10.1109/CCNC.2012.6181092
Elgala, H., Mesleh, R., & Haas, H. (2011). Indoor optical wireless communication: Potential and state-of-the-art. IEEE Communications Magazine, 49(9), 56–62.
Tsiatmas, A., Baggen, C. P. A., Willems, F. M., Linnartz, J. P., & Bergmans, J. W. (2014). An illumination perspective on visible light communications. Communications Magazine IEEE, 52(7), 64–71.
Samsung Electronics, ETRI, VLCC, University of Oxford (2008). Visible light communication: Tutorial. http://www.ieee802.org/802_tutorials/2008-03/15-08-0114-02-0000-VLC_Tutorial_MCO_Samsung-VLCC-Oxford_2008-03-17.pdf
Rahaim, M. B., Vegni, A.M. & Little, T. D. (2011). A hybrid radio frequency and broadcast visible light communication system. In Proceedings IEEE global communications conference (GLOBECOM) Workshops (pp. 792–796).
Chen, L.B., et al. (2014). Development of a dual-mode visible light communications wireless digital conference system. In Consumer electronics (ISCE 2014), The 18th IEEE international symposium on (pp. 1–2).
Javaudin, J. P., Bellec, M., Varoutas D., & Suraci, V (2008). OMEGA ICT project: towards convergent gigabit home networks In Proceedings international symposium on personal, indoor and mobile radio communications (PIMRC), Cannes, France
Langer, K.D., et al (2008). Optical wireless communications for broadband access in home area networks. In Proceedings international conference on transparent optical networks, ICTON ( pp. 149–154). doi: 10.1109/ICTON.2008.4598756
O’Brien, D.C., et al (2009). Gigabit optical wireless for a home access network. In Proceedings IEEE 20th international symposium on personal, indoor and mobile radio communications,( pp. 1–5).
Yoshino, M., Haruyama S. & Nakagawa, M. (2008). High-accuracy positioning system using visible LED lights and image sensor. In Radio and Wireless Symposium, IEEE (pp. 439–442, 22–24).
Ren, Z. X., Zhang, H. M., Wei, L. & Guan, Y. (2014). A high precision indoor positioning system based on VLC and smart handheld. In Applied mechanics and materials (vol. 571, pp. 183–186).
Cheong, Y.-K., Ng, X., & Chung, W.-Y. (2013). Hazardless biomedical sensing data transmission using VLC. IEEE Sensors Journal, 13(9), 3347–3348.
Shoaiba, M., et al. (2016). Visible light communication applications in healthcare. Technology and Health Care, 24(1), 135–138.
GBI Research. (2011). Visible light communication (VLC)—A potential solution to the global wireless spectrum shortage Tech. Rep. London: GBI Research.
Wang, Q., Giustiniano D., & Puccinelli, D. (2014) OpenVLC: Software-defined visible light embedded networks. In Proceedings of the 1st ACM MobiCom workshop on visible light communication systems, September. (pp. 15–20)
Conti, J. P. (2008). What you see is what you send. Engineering and Technology, 3, 66–67.
Blinowski, G. (2016). Practical aspects of physical and MAC layer security in visible light communication systems. International Journal of Electronics and Telecommunications, 62(1), 7–13.
IEEE (2011). IEEE standard for local and metropolitan area networks–part 15.7: Short-range wireless optical communication using visible light. IEEE Std 802.15.7-2011, https://standards.ieee.org/findstds/standard/802.15.7-2011.html
Classen, J., Chen, J., Steinmetzer, D., Hollick, M. & Knightly, E. (2015). The spy next door: Eavesdropping on high throughput visible light communications. In Proceedings of the 2nd ACM MobiCom Workshop on Visible Light Communication Systems, ser. VLCS (Vol. 15)
Wyner, A. D. (1975). The wire-tap channel. The Bell System Technical Journal, 54, 1355–1387.
Le Minh, H. Pham, A. T., Ghassemlooy Z. & Burton, A. (2014) Secured communications-zone multiple input multiple output visible light communications. In Proceedings Globecom Workshop—Optical Wireless Communications,
Mostafa, A., & Lampe, L. (2014). Physical-layer security for indoor visible light communications,” In Proceedings IEEE ICC 2014—optical networks and systems
Chow, C.-W. (2015). Secure communication zone for white-light LED visible light communication. Optics Communications, 344, 81–85.
Cui, K., Quan, J., & Xu, Z. (2013). Performance of indoor optical femtocell by visible light communication. Optics communication, 298, 59–66.
Pelechrinis, K., Iliofotou, M., & Krishnamurthy, S. V. (2011). Denial of service attacks in wireless networks: The case of jammers. IEEE Communications Surveys and Tutorials, 13(2), 245.
Xiong, F. (2006). Digital Modulation Techniques, Second Edition, Boston. Norwood: Artech House. ISBN 978-1-58053-864-0.
Agarwal, A., & Garima, S. (2014). “SNR Analysis for Visible Light Communication Systems,” International journal of engineering research and technology, Vol. 3. No. 10 October 2014. ESRSA Publications.
Relux Suite, Relux Informatik AG, http://www.relux.biz
EU Standard EN 12464-1:2011, Light and lighting. Lighting of work places. Indoor work places, 2011
Wilhelm‚ M., Martinovic‚ I., Schmitt, J. B. & Lenders, V (2011). Reactive jamming in wireless networks: how realistic is the threat?” In Proceedings of the fourth ACM conference on wireless network security. ACM (pp. 47–52)
Acknowledgements
This work was supported by the Statutory Grant of the Polish Ministry of Science and Higher Education, given to the Institute of Computer Science, Warsaw University of Technology.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
Open Access This article is distributed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits unrestricted use, distribution, and reproduction in any medium, provided you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license, and indicate if changes were made.
About this article
Cite this article
Blinowski, G.J. The Feasibility of Launching Rogue Transmitter Attacks in Indoor Visible Light Communication Networks. Wireless Pers Commun 97, 5325–5343 (2017). https://doi.org/10.1007/s11277-017-4781-3
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-017-4781-3