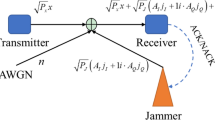
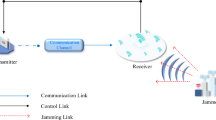
Abstract
With the increasingly fierce competition for electromagnetic spectrum resources and the rapid development in artificial intelligence, frequency-hopping (FH) communication systems are facing serious intelligent jamming attacks. Under this background, game theory has become an effective tool to solve the optimal decision-making problem in communication countermeasures. In this paper, focusing on defending against sweep jamming attacks and considering the inevitable transmission delay of an actual communication system, we propose a multi-step prediction Markov decision process (MPMDP) and set up a multi-step prediction Bellman iterative equation (MPBIE). To solve the MPBIE, multi-step state transition probabilities are derived, and a simplified algorithm is designed. Combing the complete strategy we proposed, the MPMDP strategy to maximize the utility of the FH communication system is obtained. With the assumption that the jammer can learn the MPMDP strategy of the FH communication system, we furtherly study its optional sweep jamming attack strategy. The MPMDP strategy and the optional intelligent sweep jamming attack strategy as a Nash equilibrium of the communication system and the jammer are proved. Lastly, simulation results show that the property and theorems proposed in this paper are valid, and our MPMDP strategy outperforms similar algorithms in terms of the applicable range and performance.











Similar content being viewed by others
References
Pelechrinis, K., Koufogiannakis, C., & Krishnamurthy, S. V. (2009). Gaming the jammer: Is frequency hopping effective? In International conference on modeling and optimization in mobile.
Yu, W. (2018). Research on status and future development of US protected satellite communications system. Radio Communications Technology, 44(3), 236–241.
Ji, Y., Tao, L., & Zhu, Q. (2012). Research on the frequenct hopping communication technology of variable hopping rate and variable interval. Wireless Communication Technology, 4, 25–29.
Gang, C., & Fu-hai, L. (2016). Research on anti-follower jamming performance of variable rate frequency hopping communications. Fire Control and Command Control, 41(7), 107–109.
Dan-tong, N., Wei-kang, Z., & Ying, Z. (2016). Design and analysis of the module for variable rate frequency hopping communications. In Presented at the proceedings of the fourth China command and control conference.
Hlavacek, D., & Chang, J. M. (2014). A layered approach to cognitive radio network security: A survey. Computer Networks, 75, 414–436.
AlSkaif, T., Guerrero Zapata, M., & Bellalta, B. (2015). Game theory for energy efficiency in wireless sensor networks: Latest trends. Journal of Network and Computer Applications, 54, 33–61.
Jia, L., Xu, Y., Sun, Y., Feng, S., & Anpalagan, A. (2018). Stackelberg game approaches for anti-jamming defence in wireless networks. IEEE Wireless Communications, 25(6), 120–128.
Wu, Y., Wang, B., Liu, K. J. R., & Clancy, T. C. (2012). Anti-jamming games in multi-channel cognitive radio networks. IEEE Journal on Selected Areas in Communications, 30(1), 4–15.
Khattab, S., Mosse, D., & Melhem, R. (2008). Jamming mitigation in multi-radio wireless networks: Reactive or proactive? In International conference on security and privacy in communication netowrks.
Anwar, A. H., Kelly, J., Atia, G., & Guirguis, M. (2015). Stealthy edge decoy attacks against dynamic channel assignment in wireless networks. In Military communications conference.
Li, Y., Mehr, A. S., & Chen, T. (2019). Multi-sensor transmission power control for remote estimation through a SINR-based communication channel. Automatica, 101, 78–86.
Wang, B., Yongle, W., Liu, K. J. R., & Clancy, T. C. (2011). An anti-jamming stochastic game for cognitive radio networks. IEEE Journal on Selected Areas in Communications, 29(4), 877–889.
Yao, F., Jia, L., Sun, Y., Xu, Y., Feng, S., & Zhu, Y. (2017). A hierarchical learning approach to anti-jamming channel selection strategies. Wireless Networks, 25(1), 201–213.
Wu, Y. (2010). Game-theoretic strategies for dynamic behavior in cognitive radio networks. Dissertations Theses—Gradworks.
Singh, S., & Trivedi, A. (2012). Anti-jamming in cognitive radio networks using reinforcement learning algorithms. In Ninth international conference on wireless and optical communications networks.
Zappone, A., Sanguinetti, L., & Debbah, M. (2018). Energy-delay efficient power control in wireless networks. IEEE Transactions on Communications, 66(1), 418–431.
Luo, J., Pan, C., Li, R., & Ge, F. (2012). Power control in distributed wireless sensor networks based on noncooperative game theory. International Journal of Distributed Sensor Networks, 8(12), 544–548.
Yang, G., Wang, X., Tan, X., & Li, B. (2015). Adaptive power control algorithm in cognitive radio based on game theory. IET Communications, 9(15), 1807–1811.
Chai, B., Deng, R., Shi, Z., Cheng, P., & Chen, J. (2014). Energy-efficient power allocation in cognitive sensor networks: A coupled constraint game approach. Wireless Networks, 21(5), 1577–1589.
Slimeni, F., Scheers, B., Nir, V. L., Chtourou, Z., & Attia, R. (2016). Learning multi-channel power allocation against smart jammer in cognitive radio networks. In International conference on military communications and information systems.
Liu, H. (2019). SINR-based multi-channel power schedule under DoS attacks: A Stackelberg game approach with incomplete information. Automatica, 100, 274–280.
Yang, D., Xue, G., Zhang, J., Richa, A., & Fang, X. (2013). Coping with a smart jammer in wireless networks: A Stackelberg game approach. IEEE Transactions on Wireless Communications, 12(8), 4038–4047.
Bacci, G., Sanguinetti, L., & Luise, M. J. S. P. M. I. (2015). Understanding game theory via wireless power control. IEEE Signal Processing Magazine, 32(4), 132–137.
Najeh, S., & Bouallegue, A. (2019). Game theory for SINR-based power control in device-to-device communications. Physical Communication, 34, 135–143.
Hu, R., & Lok, T.-M. (2017). Pareto optimality for the single-stream transmission in multiuser relay networks. IEEE Transactions on Wireless Communications, 16(10), 6503–6513.
Adem, N., Hamdaoui, B., & Yavuz, A. (2016). Mitigating jamming attacks in mobile cognitive networks through time hopping. Wireless Communications and Mobile Computing, 16(17), 3004–3014.
Xin, L., Xu, Y., Jia, L., Wu, Q., & Anpalagan, A. J. I. C. L. (2017). Anti-jamming communications using spectrum waterfall: A deep reinforcement learning approach. IEEE Communications Letters, 99, 1–4.
Abu Alsheikh, M., Hoang, D. T., Niyato, D., Tan, H.-P., & Lin, S. (2015). Markov decision processes with applications in wireless sensor networks: A survey. IEEE Communications Surveys and Tutorials, 17(3), 1239–1267.
Hao, X.-C., Yao, N., Li, X.-D., & Liu, W.-J. (2015). Multi-channel allocation algorithm for anti-interference and extending connected lifetime in wireless sensor network. Wireless Personal Communications, 87(4), 1299–1318.
Anwar, A. H., Atia, G., & Guirguis, M. (2018). Adaptive topologies against jamming attacks in wireless networks: A game-theoretic approach. Journal of Network and Computer Applications, 121, 44–58.
Wang, W., Kwasinski, A., Niyato, D., & Han, Z. (2018). Learning for robust routing based on stochastic game in cognitive radio networks. IEEE Transactions on Communications, 66(6), 2588–2602.
Han, G., Liang, X., & Poor, H. V. (2017). Two-dimensional anti-jamming communication based on deep reinforcement learning. In IEEE international conference on acoustics.
Luo, J., Wang, S., & Wang, F. (2019). Joint transmitter–receiver spatial modulation design via minimum Euclidean distance maximization. IEEE Journal on Selected Areas in Communications, 37, 1986–2000.
Zhu, L., Zhu, J., Wang, S., et al. (2019). Adaptive transmit antenna selection based on PCA for millimeter wave LOS MIMO channel. IEEE Access, 7, 12087–12096.
Li, T., Song, T., & Liang, Y. (2018). Wireless communications under hostile jamming security and efficiency.
Wu, Y., Wang, B., & Liu, K. J. R. (2009). Optimal power allocation strategy against jamming attacks using the Colonel Blotto game. In Global telecommunications conference.
Tan, C. K., Sim, M. L., Chuah, T. C., & Su, W. T. (2011). Blotto game-based low-complexity fair multiuser subcarrier allocation for uplink OFDMA networks. EURASIP Journal on Wireless Communications and Networking, 2011(1), 53.
Kim, S. (2015). Cognitive radio anti-jamming scheme for security provisioning IoT communications. KSII Transactions on Internet and Information Systems, 9(10), 4177–4190.
Zhang, H., Du, J., Cheng, J., Long, K., & Leung, V. C. M. (2018). Incomplete CSI based resource optimization in SWIPT enabled heterogeneous networks: A non-cooperative game theoretic approach. IEEE Transactions on Wireless Communications, 17(3), 1882–1892.
Aykin, I., Krunz, M., & Xiao, Y. (2018). Adaptive frequency-hopping schemes for CR-based multi-link satellite networks. International Journal of Satellite Communications and Networking, 36(4), 315–331.
Hanawal, M. K., Abdel-Rahman, M. J., & Krunz, M. (2016). Joint adaptation of frequency hopping and transmission rate for anti-jamming wireless systems. IEEE Transactions on Mobile Computing, 15(9), 2247–2259.
Gao, Y., Xiao, Y., Wu, M., Xiao, M., & Shao, J. (2018). Game theory-based anti-jamming strategies for frequency hopping wireless communications. IEEE Transactions on Wireless Communications, 17(8), 5314–5326.
Arunthavanathan, S., Goratti, L., Maggi, L., de Pellegrini, F., Kandeepan, S., & Reisenfield, S. (2017). An optimal transmission strategy in zero-sum matrix games under intelligent jamming attacks. Wireless Networks, 25(4), 1777–1789.
Dabcevic, K., Betancourt, A., Marcenaro, L., & Regazzoni, C. S. (2014). Intelligent cognitive radio jamming—a game-theoretical approach. EURASIP Journal on Advances in Signal Processing, 2014(1), 171.
Lv, H., Li, P., Yan, Q., & Zhang, H. (2019). Energy-efficient multi-cell resource allocation in cognitive radio-enabled 5G systems. EURASIP Journal on Advances in Signal Processing, 1, 2019.
Torrieri, D. J. (1989). Fundamental limitations on repeater jamming of frequency-hopping communications. IEEE Journal on Selected Areas in Communications, 7(4), 569–575.
Yao, F. Q., & Zhang, Y. (2005). Analysis and application of jamming ellipse. Journal of Pla University of Science, 6(1), 7–10.
Myerson, R. B. (1978). Refinements of the Nash equilibrium concept. International Journal of Game Theory, 7(2), 73–80.
Author information
Authors and Affiliations
Corresponding authors
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix
Appendix
1.1 Proof of Property 1
With action h being adopted, the MPBIE in (5) is expanded as follows:
In (12), \(Q(S_1,A_d^{(h_{\tau })},h)\) is only related to the d-step state transition probabilities \(p(C_{d-\tau +1}|S,A_d^{(h_{\tau })})\) and \(p(J|S,A_d^{(h_{\tau })})\), and the values in the two \([\cdot ]\) are equal for any \(S_1\in \mathbf {S}\) and \(\tau \in \{1,2,\ldots ,k\}\). Subsequently, combining (10) and (11), we find that \(p(C_{d-\tau +1}|S,A_d^{(h_{\tau })})\) and \(p(J|S,A_d^{(h_{\tau })})\) are not related to the initial state \(S_1\), but only related to \(\tau\). Therefore, (13) can be deduced easily:
On the other hand, with action s being adopted, the MPBIE in (5) is expanded as follows:
Similar to the inference of (13), we obtain (15) from (14):
Combining (13), (15), and (5), we obtain (16):
Hence, Property 1 is proven. This property is the basis for the proofs of other theorems.
1.2 Proof of Theorem 1
According to Property 1 and combining (12) and (3), we obtain (17):
By calculating the difference of \(Q(S_1,A_d^{(h_{\tau })},h)\) to \(\tau\), we obtain (18):
In (18), \(p(C_{d-\tau +1}|S,A_d^{(h_{\tau })})\) increases monotonically with \(\tau\), \(R_s(T_h\!-\!T_p)-L_s(T_h\!-\!T_p)\) and \(p(J|C_{d-\tau +1},s)\) are both positive constants. Therefore, \(Q(S_1,A_d^{(h_{\tau })},h)\) increases monotonically with \(\tau\).
According to Property 1 and combining (14) and (3), we obtain (19):
By calculating the difference of \(Q(S_1,A_d^{(h_{\tau })},s)\) to \(\tau\), we obtain (20):
Equation (20) is a recursive expression, which can be proven using the recursive method. With \(\tau =1,2\) and action h being adopted, we obtain (21):
As a result of \(U(C_d,h)>0\) and \(U(J,h)<0\), we obtain (22) form (21):
Similarly, With \(\tau =1,2\) and action s being adopted, we obtain (23):
Similarly, given that \(U(C_d,h)>0\) and \(U(J,h)<0\), we obtain (24):
Combining (22), (24), and (5), we obtain (25):
Substituting (25) back into (20), we obtain (26):
Given that \(Q(S_1,A_d^{(h_{\tau })},h)\) increases monotonically with \(\tau\), we obtain (27):
Substituting (27) back into (20), (28) can be deduced easily:
Continuing the recursive process according to the above rules until \(\tau =d\), we obtain that \(Q(S_1,A_d^{(h_{\tau })},s)>Q(S_1,A_d^{(h_{\tau -1})},s)\) is true for any \(1\le \tau \le d\). \(Q(S_1,A_d^{(h_{\tau })},s)\) increases monotonically with \(\tau\). The first term on the right side of the equation in (20) also increases monotonically with \(\tau\), and its increasing ratio is always greater than that of \(Q(S_1,A_d^{(h_{\tau })},h)\) for any \(\tau\) (reference (18)). Besides, the increasing ratio of the second term on the right side of the equation in (20) is always greater than 0.
In conclusion, both \(Q(S_1,A_d^{(h_{\tau })},s)\) and \(Q(S_1,A_d^{(h_{\tau })},h)\) increase monotonically with \(\tau\), and the increasing ratio of \(Q(S_1,A_d^{(h_{\tau })},s)\) is always greater than that of \(Q(S_1,A_d^{(h_{\tau })},h)\). Therefore, there is at most one intersection \(\tau ^*\) for which \(a_{d+1}=h\) when \(\tau \le \tau ^*\); otherwise, \(a_{d+1}=s\).
Hence, Theorem 1 is proven.
1.3 Proof of Theorem 2
According to (5), we can obtain (29):
Utilizing the property of the second term in (20) is always greater than 0, we find that \(V^*(J,A_d^{(h_{d})})>V^*(J,A_d^{(h_{0})})=V^*(J,A_d^{(s)})\). therefore, (30) can be obtained as follows:
Hence, Theorem 2 is proven.
1.4 Proof of Theorem 3
With action h being adopted and utilizing property 1, we obtain (31) by expanding (5):
The difference \(Q(C_k,A_d^{(s)},h)\) to k is calculated as follows:
In (32), \(Q(C_k,A_d^{(s)},h)\) decreases monotonically with k. In addition, comparing (30) and (31), we obtain (33):
With action s being adopted and utilizing of property 1, we obtain (34) by expanding (5):
The inequality in (34) makes use of the result of (33). In (34), \(U(J,s)<0\) and \(U(C_{k+s},s)>0\), \(p(C_{k+d}|C_k,A_d^{(s)})\) and \(p(J|C_k,A_d^{(s)})\) decreases and increases monotonically with k. Therefore, \(Q(C_k,A_d^{(s)},h)\) decreases monotonically with k. Combining the property that \(Q(C_k,A_d^{(s)},h)\) decreases monotonically with k in (32), we find that \(V^*(C_k,A_d^{(s)})\) decreases monotonically with k.
So far, we have proved that all \(Q(C_k,A_d^{(s)},s)\), \(Q(C_k,A_d^{(s)},h)\), and \(V^*(C_k,A_d^{(s)})\) decrease monotonically with k. However, we have not determined the number of crossings between \(Q(C_k,A_d^{(s)},s)\) and \(Q(C_k,A_d^{(s)},h)\). Therefore, it is necessary to furtherly compare the monotonically decreasing ratio of \(Q(C_k,A_d^{(s)},s)\) and \(Q(C_k,A_d^{(s)},h)\). Calculate the difference of \(Q(C_k,A_d^{(s)},s)\) to k as follows:
The first inequality in (35) utilizes the property that \(V^*(C_{k}|C_k,A_{d}^{(s)})\) decreases monotonically with k. The second inequality in (35) utilizes the property that \(p(C_{k+d}|C_k,A_{d}^{(s)})\) decreases monotonically with k and the result of (33).
Comparing (35) and (32), we find the relationship as (36):
In other words, \(Q(C_k,A_d^{(s)},s)\), \(Q(C_k,A_d^{(s)},h)\), and \(V^*(C_k,A_d^{(s)})\) all decrease monotonically with k, and the decreasing ratio of \(Q(C_k,A_d^{(s)},s)\) is always greater than \(Q(C_k,A_d^{(s)},h)\). Therefore, there is at most one intersection k, such that when \(k>k^*\), \(a_{d+1}=h\); otherwise, \(a_{d+1}=s\) .
Hence, Theorem 3 is proven.
Rights and permissions
About this article
Cite this article
Wei, P., Wang, S., Luo, J. et al. Optimal frequency-hopping anti-jamming strategy based on multi-step prediction Markov decision process. Wireless Netw 27, 4581–4601 (2021). https://doi.org/10.1007/s11276-021-02735-7
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11276-021-02735-7