Abstract
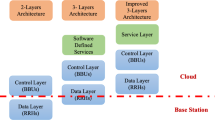
In this article, we present relay selection policies in applications with secrecy requirements which are of interest in the fifth generation (5G) of wireless networks. More specifically, we provide a classification of relays based on their distinct communication attributes, such as processing, multiple antennas, storage, channel estimation, density and security level. In addition, we discuss the level of efficiency exhibited by each relay class, regarding their impact in delay-critical applications and green communications applications, while aiming at a specific security level at the physical layer. Then, relay selection policies are proposed taking into consideration the goals set by each application. Numerical evaluation of the proposed policies in terms of the average secrecy rate, average delay and power reduction show improved performance compared to other state-of-the-art solutions.









Similar content being viewed by others
References
Demestichas, P., Georgakopoulos, A., Karvounas, D., Tsagkaris, K., Stavroulaki, V., Lu, J., et al. (2013). 5G on the Horizon: Key challenges for the radio-access network. IEEE Vehicular Technology Magazine, 8(3), 47–53.
Pandit, S., & Singh, G. (2013). Throughput maximization with reduced data loss rate in cognitive radio network. Springer Telecommunication Systems. doi:10.1007/s11235-013-9858-z.
Mach, P., Bestak, R., & Becvar, Z. (2013). Optimization of association procedure in WiMAX networks with relay stations. Springer Telecommunication Systems, 52(3), 1697–1704.
Zhou, L. (2013). Green service over Internet of Things: A theoretical analysis paradigm. Springer Telecommunication Systems, 52(2), 1235–1246.
Horizon 2020—Work programme 2014–2015, http://ec.europa.eu/research/participants/portal/doc/call/h2020/common/1587758-05i._ict_wp_2014-2015_en.pdf.
Papapostolou, A., Friderikos, V., Yahiya, T. A., & Chaouchi, H. (2013). Path selection algorithms for fault tolerance in wireless mesh networks. Springer Telecommunication Systems, 52(4), 1831–1844.
Nieto, A., & Lopez, J. (2013). Analysis and taxonomy of security/QoS tradeoff solutions for the future internet. Wiley Online Library, Security and Communication Networks. doi:10.1002/sec.809.
Varalakshmi, L. M., Florence Sudha, G., & Jaikishan, G. (2013). A selective encryption and energy efficient clustering scheme for video streaming in wireless sensor networks. Springer Telecommunication Systems, 56(3), 357–365.
Zheng, K., Hu, F., Wang, W., Xiang, W., & Dohler, M. (2012). Radio resource allocation in LTE-advanced cellular networks with M2M communications. IEEE Communications Magazine, 50(7), 184–192.
Riihonen, T., Werner, S., & Wichman, R. (2011). Mitigation of loopback self-interference in full-duplex MIMO relays. IEEE Transactions on Signal Processing, 59(12), 5983–5993.
Nomikos, N., Charalambous, T., Krikidis, I., Skoutas, D. N., Vouyioukas, D., & Johansson, M. (2013). Buffer-aided successive opportunistic relaying with inter-relay interference cancellation. In IEEE international symposium on personal, indoor and mobile radio communications (pp. 1321–1325).
Bletsas, A., Khisti, A., Reed, D., & Lippman, A. (2006). A simple cooperative diversity method based on network path selection. IEEE Journal on Selected Areas in Communications, 24, 659–672.
Michalopoulos, D. S., & Karagiannidis, G. K. (2008). Performance analysis of single relay selection in Rayleigh fading. IEEE Transactions on Wireless Communications, 7, 3718–3724.
Kharchenko, V., Gorbenko, A., Sklyar, V., & Phillips, C. (2013). Green computing and communications in critical application domains: Challenges and solutions. In: IEEE workshop on green and safe computing and communication (pp. 191–197).
El Maliki, T., & Seigneur, J. M. (2013). Security adaptation based on autonomic and trust systems for ubiquitous mobile network and green IT. In: IARIA conference on mobile ubiquitous computing, systems, services and technologies (pp. 152–158).
Aleksic, S. (2013). Energy-efficient communication networks for improved global energy productivity. Springer Telecommunication Systems, 54, 183–199.
Olsson, M., Cavdar, C., Frenger, P., Tombaz, S., Sabella, D., & Jantti, R. (2013). 5GrEEn: Towards green 5G mobile networks. In wireless and mobile computing. In IEEE internationsl conference on wireless and mobile computing, networking and communications (pp. 212–216).
Samdanis, K., Kutscher, D., & Brunner, M. (2010). Self-organized energy efficient cellular networks. In IEEE international symposium on personal, indoor and mobile radio communications (pp. 1665–1670).
Antonopoulos, A., Verikoukis, C., Skianis, C., & Akan, O. (2013). Energy efficient network coding-based MAC for cooperative ARQ wireless networks. Elsevier Ad Hoc Networks, 11(1), 190–200.
Krikidis, I., Charalambous, T., & Thompson, J. S. (2012). Stability analysis and power optimization for energy harvesting cooperative networks. IEEE Signal Processing Letters, 19(1), 20–23.
Mekikis, P. V., Lalos, A. S., Antonopoulos, A., Alonso, L., & Verikoukis, C. (2014). Wireless energy harvesting in two-way network coded cooperative communications: A stochastic approach for large scale networks. IEEE Communications Letters, 18(6), 1011–1014.
Ke, F., Fenf, S., & Zhuang, H. (2010). Relay selection and power allocation for cooperative network based on energy pricing. IEEE Communications Letters, 14(5), 396–398.
Panigrahi, B., Panda, B. S., & Luk, J. D., (2010). Energy-efficient greedy forwarding protocol for wireless sensor networks. In IEEE Vehicular Technology Conference (pp. 1–5).
Antonopoulos, A., & Verikoukis, C. (2014). Multi-player game theoretic MAC strategies for energy efficient data dissemination. IEEE Transactions on Wireless Communications, 13(2), 592–603.
Hauser, C. H., Bakken, D. E., Dionysiou, I., Gjermundrod, K. H., Irava, V., Helkey, J., et al. (2008). Security, trust, and QoS in next-generation control and communication for large power systems. Critical Infrastructures, 4(1), 3–16.
Son, K., Kim, H., Yi, Y., & Krishnamachari, B. (2011). Base station operation and user association mechanisms for energy-delay tradeoffs in green cellular networks. IEEE Journal on Selected Areas in Communications, 29(8), 1525–1536.
Ho, C. Y., & Huang, C. Y. (2011). Energy-efficient subcarrier power allocation and relay selection scheme for OFDMA-based cooperative relay networks. IEEE International Conference on Communications (pp. 1–6).
Ikki, S. S., Ubaidulla, P., & Aissa, S. (2013). Regenerative cooperative diversity networks with co-channel interference: Performance analysis and optimal energy allocation. IEEE Transactions on Vehicular Technology, 62(2), 896–902.
Yu, H., Lee, I. H., & Stuber, G. L. (2012). Outage probability of decode-and-forward cooperative relaying systems with co-channel interference. IEEE Transactions on Wireless Communications, 11(1), 266–274.
Rankov, B., & Wittneben, A. (2007). Spectral efficient protocols for half-duplex fading relay channels. IEEE Journal on Selected Areas in Communications, 25(2), 379–389.
Nomikos, N., Skoutas, D. N., Vouyioukas, D., Verikoukis, C., & Skianis, C. (2014). Capacity maximization through energy-aware multi-mode relaying. Springer Wireless Personal Communications, 74(1), 83–99.
Musavian, L., Aïssa, S., & Lambotharan, S. (2010). Effective capacity for interference and delay constrained cognitive radio relay channels. IEEE Transactions on Wireless Communications, 9(5), 1698–1707.
Xu, Yi, & Wang, W. (2013). Wireless mesh network in smart grid: Modeling and analysis for time critical communications. IEEE Transactions on Wireless Communications, 12(7), 3360–3371.
Sun, H., Nallanathan, A., Tan, Bo, Thompson, J. S., Jiang, J., & Poor, H. V. (2012). Relaying technologies for smart grid communications. IEEE Wireless Communications, 19(6), 52–59.
Niyato, D., & Wang, P. (2012). Cooperative transmission for meter data collection in smart grid. IEEE Commuications Magazine, 50(4), 90–97.
Dong, L., Yousefi’zadeh, H., & Jafarkhani, H. (2011). Cooperative jamming and power allocation for wireless relay networks in presence of eavesdropper. IEEE International Conference on Communications (pp. 1–5).
Kong, J., Hong, X., & Gerla, M. (2003). A new set of passive routing attacks in mobile ad hoc networks. IEEE Military Communications Conference, 2, 796–801.
Deng, H., Li, W., & Agrawal, D. P. (2002). Routing security in wireless ad hoc networks. IEEE Communications Magazine, 40(10), 70–75.
Khodakarami, H., & Lahouti, F. (2012). Link adaptation with untrusted relay assignment: Design and performance analysis. Arxiv.
Zou, Y., Wang, X., & Shen, W. (2013). Optimal relay selection for physical-layer security in cooperative wireless networks. IEEE Journal on Selected Areas in Communications, 31(10), 2099–2111.
Huang, J., Mukherjee, A., & Swindlehurst, A. L. (2013). Secure communication via an untrusted non-regenerative relay in fading channels. IEEE Transactions on Signal Processing, 61(10), 2536–2550.
Bassily, R., & Ulukus, S. (2013). Deaf cooperation and relay selection strategies for secure communication in multiple relay networks. IEEE Transactions on Signal Processing, 61(6), 1544–1554.
Li, J., Petropulu, A. P., & Weber, S. (2011). On cooperative relaying schemes for wireless physical layer security. IEEE Transactions on Signal Processing, 59(10), 4985–4997.
Xu, W., Ma, K., Trappe, W., & Zhang, Y. (2006). Jamming sensor networks: attack and defense strategies. IEEE Networks, 20(3), 41–47.
Krikidis, I. (2010). Opportunistic relay selection for cooperative networks with secrecy constraints. IET Communications, 4(15), 1787–1791.
Ding, Z., Leung, K. K., Goeckel, D. L., & Towsley, D. (2011). Opportunistic relaying for secrecy communications: Cooperative jamming vs. relay chatting. IEEE Transactions on Wireless Communications, 10(6), 1725–1729.
Chen, G., Tian, Z., Gong, Y., Chen, Z., & Chambers, J. (2014). Max-ratio relay selection in secure buffer-aided cooperative wireless networks. IEEE Transactions on Information Forensics and Security, 9(4), 719–729.
Krikidis, I., Charalambous, T., & Thompson, J. S. (2012). Buffer-aided relay selection for cooperative diversity systems without delay constraints. IEEE Transactions on Wireless Communications, 11, 1957–1967.
Nomikos, N., Charalambous, T., Krikidis, I., Vouyioukas, D., & Johansson M. (2014). Hybrid cooperation through full-duplex opportunistic relaying and max-link relay selection with transmit power adaptation. In IEEE International Conference on Communications.
Ikhlef, A., Michalopoulos, D. S., & Schober, R. (2012). Max-max relay selection for relays with buffers. IEEE Transactions on Wireless Communications, 11, 1124–1135.
Nomikos, N., Vouyioukas, D., Charalambous, T., Krikidis, I., Makris, P., Skoutas, D. N., Johansson, M., & Skianis, C. (2013). Joint relay-pair selection for buffer-aided successive opportunistic relaying. Wiley-Blackwell Transactions on Emerging Telecommunications Technologies. doi:10.1002/ett.2718.
El Gamal, A., Mammen, J., Prabhakar, B., & Shah, D. (2006). Optimal throughput-delay scaling in wireless networks—Part II: Constant-size packets. IEEE Transactions on Information Theory, 52(11), 5111–5116.
3GPP TR 36.814 v. 9.0.0. (2010). Technical specification group radio access network; evolved universal terrestrial radio access (E-UTRA); Further advancements for E-UTRA physical layer aspects.
Krikidis, I., Thompson, J. S., & McLaughlin, S. (2009). Relay selection for secure cooperative networks with jamming. IEEE Transactions on Wireless Communications, 8(10), 5003–5011.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Nomikos, N., Nieto, A., Makris, P. et al. Relay selection for secure 5G green communications. Telecommun Syst 59, 169–187 (2015). https://doi.org/10.1007/s11235-014-9890-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11235-014-9890-7