Abstract
We define metrics and measures to characterize the ratio of accessible quantum entanglement for complex network failures in the quantum Internet. A complex network failure models a situation in the quantum Internet in which a set of quantum nodes and a set of entangled connections become unavailable. A complex failure can cover a quantum memory failure, a physical link failure, an eavesdropping activity, or any other random physical failure scenarios. Here, we define the terms such as entanglement accessibility ratio, cumulative probability of entanglement accessibility ratio, probabilistic reduction of entanglement accessibility ratio, domain entanglement accessibility ratio, and occurrence coefficient. The proposed methods can be applied to an arbitrary topology quantum network to extract relevant statistics and to handle the quantum network failure scenarios in the quantum Internet.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
As quantum computers evolve significantly [2,3,4,5,6,7,8,9,10,11], there arises a fundamental need for a communication network that provides unconditionally secure communication and all the network functions of the traditional Internet. This network structure is the quantum Internet [12,13,14,15,16,17]. The availability of quantum entanglement is a crucial aspect in any global-scale quantum Internet. The quantum Internet refers to a set of connected heterogeneous quantum communication networks realized by quantum nodes and channels (such as optical fibers or wireless optical quantum channels in the physical layer) [18,19,20,21,22,23,24]. The quantum Internet also integrates a set of classical auxiliary communication channels to transmit auxiliary classical-side information between the quantum nodes. The quantum Internet is modeled as a global-scale quantum communication network composed of quantum subnetworks and networking components. The core network of the quantum Internet is assumed to be an entangled network structure [12, 25,26,27,28,29,30,31,32,33,34,35,36,37,38,39], which is a communication network in which the quantum nodes are connected by entangled connections. An entangled connection refers to a shared entangled system (i.e., a Bell state for qubit systems to connect two quantum nodes) between the quantum nodes. In an unentangled network structure, the quantum nodes are not necessarily connected by entanglement [40, 41], and the communication between the nodes is realized in a point-to-point setting. This setting does not allow quantum communication over arbitrary distances, and an unentangled network structure can mostly be used for establishing a point-to-point quantum key distribution (QKD) [1, 42] between the quantum nodes. These short distances can be extended to longer distances by the utilization of free-space quantum channels [12, 42]. However, this solution is auxiliary, since it can be used only at some specific points of the unentangled network structure. Therefore, it does not represent an adequate and fundamental answer to the problem of long-distance quantum communication. Consequently, in an unentangled network structure, the multi-hop settings are weak for experimental, long-distance and global-scale quantum communication. On the other hand, the entangled network structure allows the parties to establish multi-hop entanglement, multi-hop QKD, high-precision sensor networks, advanced distributed computations and cryptographic functions, advanced quantum protocols, and, more importantly, the distribution of quantum entanglement over arbitrary (unlimited, in theory) distances [12]. As an important corollary, an entangled network structure provides a strong experimental basis for realizing a global-scale quantum communication network, the quantum Internet.
In the entangled network structure of the quantum Internet, the entangled connections form entangled paths. Entanglement between a distant source and a target node is established through several intermediate repeater nodes [12, 25, 26, 43, 44]. The level of entanglement (i.e., the level of an entangled connection) is defined as the number of nodes (i.e., the hop distance between entangled nodes) spanned by the shared entanglement, whose range is extended by the basic operation of entanglement swapping (entanglement extension). The entangled connections have several relevant attributes, the most important of which are the fidelity of entanglement and the entanglement throughput. The throughput of an entangled connection is measured as the number of entangled states per second at a given fidelity, which provides a useful metric on the basis of which further relevant metrics can be built.
Here we define measures to characterize the ratio of accessible quantum entanglement in case of complex network failures [45,46,47,48] in the quantum Internet. A complex network failure models a network situation in which a set of quantum nodes and a set of entangled connections become unavailable because of an (unknown) reason. A complex failure, therefore, can cover a set of practical failure reasons: a quantum memory failure situation in which a set of nodes and connections become unavailable, quantum node and connection failure scenarios, physical-link failures, or an eavesdropping activity. Specifically, a complex failure event is modeled by a network domain that is referred to as a complex failure domain. In our model, a failure domain has an abstracted center point and a given length radius [47, 48]. This domain approach allows us to describe the probability that a given node or entangled connection (i.e., a given network element) is affected by a failure in the function of the given network element’s distance from the abstracted center point of the complex failure domain.
The entanglement accessibility ratio of a given quantum network is based on the metric of the given entangled connection’s entanglement throughput. Each entangled connection is further verified by a given condition that puts a lower bound on the entanglement throughput. The entanglement accessibility ratio measures the successful accessible entanglement at a given lower bound condition for parallel complex failures in the quantum network.
We also define the cumulative probability of entanglement accessibility ratio that quantifies the cumulative probability of all complex failure events’ occurrence for which the entanglement accessibility ratio exceeds a given lower bound.
We also quantify the probability that the total entanglement accessibility ratio in the quantum network is reduced to at most a particular ratio after a complex failure. Particularly, this parameter is referred as the probabilistic reduction of entanglement accessibility ratio.
To describe the impacts of a given complex failure on the ratio of accessible entanglement, we define the domain entanglement accessibility ratio, which quantifies the accessible entanglement ratio after a complex failure in a particular domain in a function of the radius of the given failure domain.
We define the occurrence coefficient of an entanglement accessibility ratio (occurrence ratio) at a complex failure domain, which is measured by the ratio of the number of occurrence of a given entanglement accessibility ratio in the network after a complex failure event and the total number of occurrences of all entanglement accessibility ratios after a complex failure event.
We show that the defined measures can be extracted from the occurrence ratio, and therefore, it is enough to determine the occurrence coefficient to derive the other metrics. We propose an algorithm to determine the occurrence coefficient from the empirical quantities of the quantum network that are directly observable in the analyzed network setting. In particular, the defined entanglement accessibility measures can be derived in a purely empirical way by extracting relevant statistics from the analyzed quantum network.
The proposed protocol is not dependent from the actual physical implementation; therefore, it can be applied in the heterogeneous network structure and network components of the quantum Internet. (The protocol can also be applied in the quantum Internet at the utilization of magnetic field in the perturbation method [49,50,51] (kind of Zeeman effect [52]) in the physical layer,Footnote 1 or in electromagnetic field-based [54, 55] scenarios in the network components.)
The novel contributions of our manuscript are as follows:
- 1.
We define measures to characterize the accessible quantum entanglement in case of complex network failures in the quantum Internet.
- 2.
We define the terms such as entanglement accessibility ratio, cumulative probability of entanglement accessibility ratio, probabilistic reduction of entanglement accessibility ratio, and occurrence coefficient.
- 3.
We show that the defined measures can be extracted from the occurrence ratio, and therefore, it is enough to determine the occurrence coefficient to derive the other metrics.
- 4.
We propose an algorithm to determine the occurrence coefficient from the empirical quantities of the quantum network that are directly observable in the analyzed network setting of the quantum Internet.
- 5.
The entanglement accessibility measures can be derived in a purely empirical way by extracting relevant statistics from the quantum Internet.
This paper is organized as follows: In Sect. 2, the related works are summarized. In Sect. 3, some preliminaries are introduced. Section 4 defines the entanglement accessibility measures. Section 5 discusses the occurrence coefficient and defines an algorithm for the empirical evaluation of the measures. In Sect. 6, a numerical evaluation is proposed. Finally, Sect. 7 concludes the paper.
2 Related works
In this section, we review some recent results connected to the establishment of the experimental quantum Internet.
A technical roadmap on the experimental development of the quantum Internet has been provided in [15]. The roadmap is connected to the Quantum Internet Research Group (QIRG) [56], which group is formulated and supported by an international researcher background and collaboration. The authors of [15] address some important capability milestones for the realization of a global-scale quantum Internet. The technical roadmap also addresses important future engineering problems brought up by the quantum Internet, such as the development of a standardized architectural framework for the quantum Internet, standardization and protocols of the quantum Internet, application programming interface (API) for the quantum Internet, and the definition of the application level of the quantum Internet [1].
In a quantum Internet scenario, entanglement purification is a procedure that takes two imperfect systems \(\sigma _{1} \) and \(\sigma _{2} \) with initial fidelity \(F_0<1\) and outputs a higher-fidelity density \(\rho \) such that \(F\left( \rho \right) >F_0\). In [57], the authors propose novel physical approaches to assess and optimize entanglement purification schemes. The proposed solutions provide an optimization framework of practical entanglement purification.
In [58], the authors defined a method for deterministic delivery of quantum entanglement on a quantum network. The results allow us to realize entanglement distribution across multiple remote quantum nodes in a quantum Internet setting.
In [59], a satellite-to-ground QKD system over 1200 km has been demonstrated. The proposed model integrated a low-Earth-orbit satellite with decoy-state QKD. The reported key rate of the protocol was above the kHz key rate over a distance up to 1200 km. The work has a relevance for an experimental quantum Internet, since the results also allow us to realize high-efficiency long-distance QKD in a global quantum Internet setting.
In [60], the authors demonstrated the quantum teleportation of independent single-photon qubits over 1400 km. Since an experimental realization of a global-scale quantum Internet requires the application of quantum teleportation over long distances, the proposed results represent a fundamental of any experimental quantum Internet. In [61], the authors demonstrated quantum teleportation with high-fidelity values between remote single-atom quantum memories.
Some other recent results connected to the development of an experimental global-scale quantum Internet are as follows. In [62], the authors demonstrated the Bell inequality violation using electron spins separated by 1.3 km. In [63], the authors demonstrated modular entanglement of atomic qubits using photons and phonons. The quantum repeaters are fundamental networking elements of any experimental quantum Internet. The quantum repeaters are used in the entanglement distribution process to generate quantum entanglement between distant senders and receivers. The quantum repeaters also realize the entanglement purification and the entanglement swapping (entanglement extension) procedures. For an experimental realization of quantum repeaters based on atomic ensembles and linear optics, see [64].
Since quantum channels also have a fundamental role in the quantum Internet, we suggest the review paper of [65] and also the work of [66], for some specialized applications of quantum channels. For a review on some recent results of quantum computing technology, we suggest [67]. For some recent services developed for the quantum Internet, we suggest [68,69,70,71,72,73,74,75,76,77].
Some other related topics are as follows: The works [25, 26, 40, 43, 65, 68,69,70] are related to the utilization of entanglement for long-distance quantum communications and for a global-scale quantum Internet and also to the various aspects of quantum networks in a quantum Internet setting.
For some fundamental works on quantum machine learning, see [78,79,80,81]; on quantum Shannon theory, see [65, 66, 82,83,84,85,86]; on quantum computing, see [87, 88]; for schemes for reducing decoherence in quantum memory, see [89]; for quantum network coding, see [90,91,92,93]; for transformation of multipartite pure states, see [94]; for multistage entanglement swapping, see [95]; and for optical microcavities and photonic channels for quantum communication, see [96].
For some important works on the experimental implementations of quantum repeaters, entanglement purification, and entanglement distribution, see [95, 97,98,99,100,101,102,103,104,105,106,107,108,109,110].
3 Preliminaries
3.1 Entanglement fidelity
The aim of the entanglement distribution procedure is to establish a d-dimensional entangled system between the distant points A and B, through the intermediate quantum repeater nodes. Let \(d=2\), and let \({\left| \beta _{00} \right\rangle } \) be the target entangled system A and B, \({\left| \beta _{00} \right\rangle } =\frac{1}{\sqrt{2} } \left( {\left| 00 \right\rangle } +{\left| 11 \right\rangle } \right) ,\) subject to be generated. At a particular density \(\sigma \) generated between A and B, the fidelity of \(\sigma \) is evaluated as
Without loss of generality, an aim of a practical entanglement distribution is to reach \(F\ge 0.98\) in (1) for a given \(\sigma \) [12,13,14, 25, 26, 43, 65, 68].
3.2 Entangled network structure
Let V refer to the nodes of an entangled quantum network N, which consists of a transmitter node \(A\in V\), a receiver node \(B\in V\), and quantum repeater nodes \(R_{i} \in V\), \(i=1,\ldots ,q\). Let \(E=\left\{ E_{j} \right\} \), \(j=1,\ldots ,m\) refer to a set of edges (an edge refers to an entangled connection in a graph representation) between the nodes of V, where each \(E_{j} \) identifies an \(\mathrm{L}_{l} \)-level entanglement, \(l=1,\ldots ,r\), between quantum nodes \(x_{j} \) and \(y_{j} \) of edge \(E_{j} \), respectively. Let \(N=\left( V,\mathrm{{\mathcal S}}\right) \) be an actual quantum network with \(\left| V\right| \) nodes and a set \(\mathrm{{\mathcal S}}\) of entangled connections. An \(\mathrm{L}_{l} \)-level, \(l=1,\ldots ,r\), entangled connection \(E_{\mathrm{L}_{l} } \left( x,y\right) \), refers to the shared entanglement between a source node x and a target node y, with hop distance
since the entanglement swapping (extension) procedure doubles the span of the entangled pair in each step. This architecture is also referred to as the doubling architecture [12, 25, 26, 43].
For a particular \(\mathrm{L}_{l} \)-level entangled connection \(E_{\mathrm{L}_{l} } \left( x,y\right) \) with hop distance (2), there are \(d\left( x,y\right) _{\mathrm{L}_{l} } -1\) intermediate nodes between the quantum nodes x and y.
3.3 Entanglement purification and entanglement throughput
Entanglement purification is a probabilistic procedure that creates a higher-fidelity entangled system from two low-fidelity Bell states. The entanglement purification procedure yields a Bell state with an increased entanglement fidelity \(F'\),
where \(F_{in} \) is the fidelity of the imperfect input Bell pairs. The purification requires the use of two-way classical communications [12,13,14, 25, 26, 43, 65, 68].
Let \(B_{F} (E_{\mathrm{L}_{l} }^{i})\) refer to the entanglement throughput of a given \(\mathrm{L}_{l} \) entangled connection \(E_{\mathrm{L}_{l} }^{i} \) measured in the number of d-dimensional entangled states established over \(E_{\mathrm{L}_{l} }^{i} \) per sec at a particular fidelity F (dimension of a qubit system is \(d=2\)) [12,13,14, 25, 26, 43, 65, 68].
For any entangled connection \(E_{\mathrm{L}_{l} }^{i} \), a condition c should be satisfied as
where \({{B}}_{F}^{\text {*}}( E_{{{\text {L}}_{l}}}^{i})\) is a critical lower bound on the entanglement throughput at a particular fidelity F of a given \(E_{{{\text {L}}_{l}}}^{i}\), i.e., \({{B}_{F}}( E_{{{\text {L}}_{l}}}^{i})\) of a particular \(E_{{{\text {L}}_{l}}}^{i}\) has to be at least \({B}_{F}^{\text {*}}( E_{{{\text {L}}_{l}}}^{i})\).
4 Model description
In this section, we define the terms and metrics for entanglement accessibility in the quantum Internet.
4.1 Failure identifications in the quantum internet
Let \(\mathrm{{\mathcal R}}_{f} \) refer to a complex failure domain that models a set of quantum nodes \(V\left( \mathrm{{\mathcal R}}_{f} \right) \) and a set of entangled connections \(\mathrm{{\mathcal S}}\left( \mathrm{{\mathcal R}}_{f} \right) \) in a particular network domain [47, 48], whose nodes and entangled connections are affected by a complex failure f (complex—randomly affects both nodes and connections). Note that while \(\mathrm{{\mathcal S}}\left( \mathrm{{\mathcal R}}_{f} \right) \) refers to the set of local entangled connections within the failure domain \(\mathrm{{\mathcal R}}_{f}\), E refers to the entangled connections of the global quantum network N; therefore, \(\mathcal {S}\left( {{\mathcal {R}}_{f}} \right) \) is a subset of E,
and
also holds.
An f complex failure event is identified by the entanglement throughput of an ith \(\mathrm{L}_{l} \)-level entangled connection \(E_{\mathrm{L}_{l} }^{i} \) as
where \({B}_{F}^{\text {*}}( E_{{{\text {L}}_{l}}}^{i})\) is a critical lower bound on the entanglement throughput.
In the \(c_{\mathrm{{\mathcal R}}_{f} } \) center of \(\mathrm{{\mathcal R}}_{f} \), for all entangled connections of the set \(\mathrm{{\mathcal S}}\left( \mathrm{{\mathcal R}}_{f} \right) \) of \(\mathrm{{\mathcal R}}_{f} \),
and therefore, the probability \(\Pr \left( f\right) \) that an event f occurs at \(c_{\mathrm{{\mathcal R}}_{f} } \) for all elements of \(\mathrm{{\mathcal S}}\left( \mathrm{{\mathcal R}}_{f} \right) \) is
As the distance d from the center of \(\mathrm{{\mathcal R}}_{f} \) increases, the complex failure probability \(\Pr \left( f\right) \) decreases, e.g.,
Let \(c_{\mathrm{{\mathcal R}}_{f} } \) be the center of domain \(\mathrm{{\mathcal R}}_{f} \), and let \(r_{\mathrm{{\mathcal R}}_{f} } \) be the radius of \(\mathrm{{\mathcal R}}_{f} \) defined as in terms of the hop distance of an abstracted shortest entangled path \(\mathcal {P}\) in \(\mathrm{{\mathcal R}}_{f} \), as
where \(x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \in \mathrm{{\mathcal R}}_{f} \) is the nearest affected quantum node to \(c_{\mathrm{{\mathcal R}}_{f} } \), \(y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \in \mathrm{{\mathcal R}}_{f} \) is the farthest affected quantum node from \(c_{\mathrm{{\mathcal R}}_{f} } \), while \(\mathcal {P}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \) is an abstracted shortest entangled path between \(x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \) and \(y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \), with a hop distance \(d\left( \mathrm{{\mathcal P}}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \right) \), as
where \(x'_{i} \left( c_{\mathrm{{\mathcal R}}_{f} } \right) \), \(i=1,\ldots ,m\) are intermediate quantum nodes between \(x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \) and \(y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \) on the entangled path \(\mathrm{{\mathcal P}}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \).
Thus, (11) can be rewritten via (12). Then, assuming a doubling architecture on \(\mathcal {P}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \) between \(x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \) and \(y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \) in \(\mathrm{{\mathcal R}}_{f}\), the radius in (11) is yielded as
where \(l\left( E\left( x,y \right) \right) \) identifies the level of the entangled connection \({{E}_{{{\text {L}}_{l}}}}\left( x,y \right) \).
The probability of (10) is derived further as follows. At a given random \(c_{\mathrm{{\mathcal R}}_{f} } \) and \(r_{\mathrm{{\mathcal R}}_{f} } \), the probability that a given element (e.g., node or connection) i is affected [47] by the complex failure f is defined as
where \(d_{i,c_{\mathrm{{\mathcal R}}_{f} } } \) is the distance of element i from the center \(c_{\mathrm{{\mathcal R}}_{f} } \) of complex failure domain \(\mathrm{{\mathcal R}}_{f} \).
4.2 Entanglement accessibility ratio
Let \(\mathrm{{\mathcal S}}^{\mathrm{*}} \) refer to those entangled connections of N for which the condition c [see (4)] holds after a complex failure f. Let \(\Phi ^{c} \left( f\right) \) be a random variable that quantifies the ratio of total entanglement throughput in a complex failure event at a given c [see (4)]. This quantity is referred as the entanglement accessibility ratio (EAR) after a complex failure f and identified by the ratio of total entanglement throughput after a complex failure f of N and the total entanglement throughput without a failure event [47] at a given lower bound condition (4) as
where \(\left| \mathrm{{\mathcal S}}\right| \) is the number of connections in the set \(\mathrm{{\mathcal S}}\) of N, and \(\left| \mathrm{{\mathcal S}}^{\mathrm{*}} \right| \) is the cardinality of connection set \(\mathrm{{\mathcal S}}^{\mathrm{*}} \) after a failure f occurs in \(\mathrm{{\mathcal R}}_{f} \).
4.3 Cumulative probability of entanglement accessibility ratio
Let x be a critical lower bound on the entanglement accessibility ratio of \(\Phi ^{c} \left( f\right) \) [see (15)] at a given condition c and a complex failure f. A \(\sigma \left( \Phi ^{c} \left( f\right) \right) \) cumulative probability of all complex failure events’ occurrence for which the yielding ratio \(\Phi ^{c} \left( f\right) \) at a given c is at least x [see (15)],
is referred to as the cumulative probability of entanglement accessibility ratio (CP-EAR) \(\sigma ^{c} \left( \Phi ^{c} \left( f\right) \right) \), defined as
where \(\zeta ^{c} \left( \Phi ^{c} \left( f\right) \right) \) is the cumulative distribution function of \(\Phi ^{c} \left( f\right) \) at a condition c.
The \(\xi ^{c} \left( \Phi ^{c} \left( f\right) \right) \) probability density function (PDF) of ratio
after a complex failure f is therefore
4.4 Probabilistic reduction of entanglement accessibility ratio
Assume that the \(\zeta ^{c} \left( \Phi ^{c} \left( f\right) \right) \) cumulative distribution function of \(\Phi ^{c} \left( f\right) \) at a condition c is given as
Using (20), the probabilistic reduction of entanglement accessibility ratio (PR-EAR) \(\Omega ^{c} \left( \Phi ^{c} \left( f\right) \right) \) at a given ratio x, condition c, and probability q is defined as
As follows, the PR-EAR parameter \(\Omega ^{c} \left( x\right) \) in (21) quantifies the probability q that the total entanglement accessibility ratio is reduced to at most ratio x after a complex failure f.
4.5 Domain-dependent entanglement accessibility ratio
The \(\Lambda ^{x} \left( r\right) \) domain-dependent entanglement accessibility ratio (DD-EAR) quantifies the \(\Phi ^{c} \left( f\right) \) accessible entanglement ratio after a complex failure f in a particular domain \(\mathrm{{\mathcal R}}_{f} \) in a function of the radius \(r_{\mathrm{{\mathcal R}}_{f} } \) of \(\mathrm{{\mathcal R}}_{f} \) as
where \(\varphi \left( \Phi ^{c} \left( f\right) ,r_{\mathrm{{\mathcal R}}_{f} } \right) \) is the PDF of ratio \(\Phi ^{c} \left( f\right) \) at an \(r_{\mathrm{{\mathcal R}}_{f} } \)-radius length complex failure domain \(\mathrm{{\mathcal R}}_{f} \), defined as
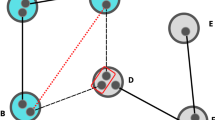
A complex network failure situation of a quantum repeater network N with failure domain \(\mathrm{{\mathcal R}}_{f} \) is illustrated in Fig. 1. A complex failure f is associated with domain \(\mathrm{{\mathcal R}}_{f} \), \(f=1,\ldots ,m\). In the center \(c_{\mathrm{{\mathcal R}}_{f} } \) of the \(\mathrm{{\mathcal R}}_{f} \), for all \(E_{\mathrm{L}_{l} }^{i} \) connections \(B_{F} (E_{\mathrm{L}_{l} }^{i})=0\), and \(\Pr \left( f\right) =1\). As the distance d from the center of \(\mathrm{{\mathcal R}}_{f} \) increases, the failure probability decreases, e.g., \(\Pr \left( f\right) <1\). The condition \(c:B_{F} (E_{\mathrm{L}_{l} }^{i})\ge B_{F}^{\mathrm{*}} (E_{\mathrm{L}_{l} }^{i})\) holds for \(\forall i\), where \(B_{F}^{\mathrm{*}} (E_{\mathrm{L}_{l} }^{i})\) is a critical lower bound on an ith \(\mathrm{L}_{l} \)-level entangled connection \(E_{\mathrm{L}_{l} }^{i} \), for the established entangled connections of N,
An f complex network failure scenario in a quantum Internet setting. A complex failure defines a domain \(\mathrm{{\mathcal R}}_{f} \) (depicted by the gray-line circle) with a random radius \(r_{\mathrm{{\mathcal R}}_{f} } \) and center \(c_{\mathrm{{\mathcal R}}_{f} } \), and with a set of affected quantum nodes (depicted by dark gray nodes) and entangled connections (depicted by dashed red lines) between a source (A) quantum node and a target (B) quantum node (the affected network components are depicted by the gray cloud)
5 Evaluation of entanglement accessibility
In this section, first, we define a coefficient that describes the occurrence of a given entanglement accessibility ratio after a multiple complex failure scenario. Then, we propose an empirical method to determine the occurrence coefficient from the observable quantities of a particular quantum network of the quantum Internet.
5.1 Occurrence coefficient
Let \(Q\left( \Phi ^{c} \left( f\right) \right) \) refer to the occurrence coefficient of a particular \(\Phi ^{c} \left( f\right) \) entanglement accessibility ratio at a complex failure domain \(\mathrm{{\mathcal R}}_{f} \) in N, defined as
where \(\mathrm{{\mathcal N}}\left( \Phi ^{c} \left( f\right) \right) \) is the number of occurrence of a given entanglement accessibility ratio \(\Phi ^{c} \left( f\right) \) in N after a failure f, while \(\mathrm{{\mathcal N}}\left( \mathrm{{\mathcal A}}^{c} \left( f\right) \right) \) quantifies the total number of occurrences of all accessible ratios \(\mathrm{{\mathcal A}}^{c} \left( f\right) \) in N after a failure f.
Extending (24) to all the m complex failure domains \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \) yields
where \(Q^{\left( f=i\right) } \left( \Phi ^{c} \left( f\right) \right) \) quantifies the occurrence of ratio \(\Phi ^{c} \left( f\right) \) via (24) for an ith domain \(\mathrm{{\mathcal R}}_{f=i} \).
In the function of \(Q^\mathrm{tot}(N)\), the quantities of (17), (21), and (22) can be derived as follows.
For an m-domain setting with domains \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \), \(\sigma ^{c} \left( \Phi ^{c} \left( f\right) \right) \) can be derived from the function \(Q^\mathrm{tot}(N)\) as
while \(\Omega ^{c} \left( \Phi ^{c} \left( f\right) \right) \) at \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \) is
At a particular failure domain radius \(r_{\mathrm{{\mathcal R}}_{f} } \) of a given \(\mathrm{{\mathcal R}}_{f} \), let
where \(\xi ^{c} \left( \Phi ^{c} \left( f\right) \right) \) as shown in (19).
For all domains \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \), (28) extends to
where \(\tilde{Q}^{\left( f=i\right) } \left( \Phi ^{c} \left( f\right) ,r_{\mathrm{{\mathcal R}}_{f} } \right) \) quantifies the occurrence of ratio \(\Phi ^{c} \left( f\right) \) for an ith domain \(\mathrm{{\mathcal R}}_{f=i} \) via a particular radius \(r_{\mathrm{{\mathcal R}}_{f} } \) using (28). Then \(\Lambda ^{x} \left( r_{\mathrm{{\mathcal R}}_{f} } \right) \) in a \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \) scenario is expressed as
Therefore, (26) to (30) follow that the entanglement accessibility ratios can be determined via the occurrence coefficient \(\tilde{Q}^\mathrm{tot} \left( \Phi ^{c} \left( f\right) ,r_{\mathrm{{\mathcal R}}_{f} } \right) \).
To find this quantity at a given network N empirically, we propose an algorithm as follows.
5.2 Empirical evaluation of occurrence coefficient
We propose an algorithm, \(\mathrm{{\mathcal A}}_{Q\left( \Phi ^{c} \left( f\right) \right) } \), for the empirical determination of the O-EAR coefficient \(Q\left( \Phi ^{c} \left( f\right) \right) \) [see (24)] at a complex failure domain \(\mathrm{{\mathcal R}}_{f} \) scenario and then the evaluation of \(Q^\mathrm{tot}(N)\) [see (25)] by the extended analysis of all domains \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \). Some preliminary definitions are as follows.
5.2.1 Definitions
To describe the topology of N, let \(I_{N} \) be the node-to-node incidence matrix of N, and let \(\tilde{I}_{N} \) refer to a temporal incidence matrix for the iteration steps of the algorithm.
Each \(L_{i} \)-level entangled connection is characterized by a particular entanglement throughput rate \(B_{F} (E_{\mathrm{L}_{l} }^{i})\), which are used to determine the \(A\left( \mathrm{{\mathcal S}}\right) \) total accessible entanglement at a connection set \(\mathrm{{\mathcal S}}\) at no failure as
Then, let \(A_{\rho ,U_{k} } \) and \(B_{\rho ,U_{k} } \) be the source and target quantum nodes of a demand \(\rho \) associated with user \(U_{k} \), \(k=1,\ldots ,K\), where K is the number of users. Then, let \(D\left( \rho \left( \mathrm{{\mathcal S}}'\right) \right) \) be the total required entanglement by a demand \(\rho \) as
f \(\rho \left( \mathrm{{\mathcal S}}'\right) \) refers to the connection set \(\mathrm{{\mathcal S}}'\) of \(\rho \).
For a given demand \(\rho _{i} \), let
quantify the total required entanglement of demand \(\rho _{i} \) with connection set \(\mathrm{{\mathcal S}}'_{i} \) along entangled connections traversed by respective paths \(\mathrm{{\mathcal P}}\left( N\right) \) in N.
Let
identify a set of g demands with both end nodes \(A_{\rho \in \mho , U_{k} } \) and \(B_{\rho \in \mho ,U_{k} } \) not affected by a complex failure f.
Assuming that a complex failure f with a domain \(\mathrm{{\mathcal R}}_{f} \) occurs in N, the total accessible entanglement after a complex failure f is
where \(\mathrm{{\mathcal S}}^{\mathrm{*}} \) is the connection set of N after the failure.
The center \(c_{\mathrm{{\mathcal R}}_{f} } \) of a domain \(\mathrm{{\mathcal R}}_{f} \) and the corresponding radius length \(r_{\mathrm{{\mathcal R}}_{f} } \) of \(\mathrm{{\mathcal R}}_{f} \) are modeled as uniformly distributed random continuous variables [47].
At a given \(\hat{B}_{F} (E_{\mathrm{L}_{l} }^{i})\) upper bound on the entanglement throughput of \(E_{\mathrm{L}_{l} }^{i} \), the remaining accessible entanglement throughput is defined as
where \(B_{F} (E_{\mathrm{L}_{l} }^{i})\) refers to a current rate.
Let \(R_{f} \left( N\right) \) quantify the empirical estimate of entanglement accessible ratio \(\Phi ^{c} \left( f\right) \) [see (15)] after a complex failure f in a given quantum network N, as
where \(A\left( \mathrm{{\mathcal S}}^{\mathrm{*}} \right) \) is defined in (35), while \(A\left( \mathrm{{\mathcal S}}\right) \) is given by (31). Therefore, \(R_{f} \left( N\right) \) provides an estimation of \(Q\left( \Phi ^{c} \left( f\right) \right) \) from the empirical values of (35) and (31) as
5.2.2 Algorithm
The \(\mathrm{{\mathcal A}}_{Q\left( \Phi ^{c} \left( f\right) \right) } \) algorithm aims to determine the empirical estimation of the occurrence function \(Q\left( \Phi ^{c} \left( f\right) \right) \).
The algorithm \(\mathrm{{\mathcal A}}_{Q\left( \Phi ^{c} \left( f\right) \right) } \) for a \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \) multiple complex failure scenario is given in Algorithm 1.

5.3 Description
A brief description of the \(\mathrm{{\mathcal A}}_{Q\left( \Phi ^{c} \left( f\right) \right) } \) method is as follows. In steps 1 and 2, some initializations are performed for further calculations. Steps 3 to 5 derive the ratio \(R_{f} \left( N\right) \approx \Phi ^{c} \left( f\right) \) of accessible entanglement at a given failure domain \(\mathrm{{\mathcal R}}_{f} \). The steps aim to determine the ratio of total accessible entanglement in a given complex domain failure scenario. For each demand that has unaffected end nodes, a path searching is performed to find the shortest alternate path \(\dot{\mathrm{{\mathcal P}}}_{i} \) for all demands \(\rho _{i} \) to serve requirement \(D\left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) of a given \(\rho _{i} \). If an alternate path exists but the entangled connections of the path are not able to serve the required entanglement \(D\left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \), then a new shortest path \(\ddot{\mathrm{{\mathcal P}}}_{i} \) is determined. The calculations are performed for all demands that are present with a nonzero required entanglement in the network. In step 6, the iteration is extended for the evaluation of all failure domains \(\mathrm{{\mathcal R}}_{f=1} ,\ldots ,\mathrm{{\mathcal R}}_{f=m} \).
5.3.1 Step 1
In step 1, a temporal incidence matrix \(\tilde{I}_{N} \) is initialized by \(I_{N} \), and the value of the total accessible entanglement via set \(\mathrm{{\mathcal S}}^{\mathrm{*}} \) after a complex failure f is set to zero, \(A\left( \mathrm{{\mathcal S}}^{\mathrm{*}} \right) =0\), where \(A\left( \mathrm{{\mathcal S}}^{\mathrm{*}} \right) \) is defined in (35). To identify the set of quantum nodes affected by f, for all nodes their corresponding probability \(\Pr (d_{i,c_{\mathrm{{\mathcal R}}_{f} } })\) is determined via (14) in a function of distance \(d_{i,c_{\mathrm{{\mathcal R}}_{f} } } \) node i from center \(c_{\mathrm{{\mathcal R}}_{f} } \) of \(\mathrm{{\mathcal R}}_{f} \). Then to distinguish the unusable connections after f has occurred for all connections for which condition c does not hold [see (4)], set the corresponding elements of \(\tilde{I}_{N} \) to 0.
5.3.2 Step 2
In step 2, for all entangled connections of \(\mathrm{{\mathcal S}}^{\mathrm{*}} \), the amount of the utilizable throughput rate is set to a maximum of the given entangled connection \(E_{\mathrm{L}_{l} }^{i} \), \(F(E_{\mathrm{L}_{l} }^{i})=\hat{B}_{F} (E_{\mathrm{L}_{l} }^{i})\), where \(\hat{B}_{F} (E_{\mathrm{L}_{l} }^{i})\), the upper bound on the throughput of an entangled connection \(E_{\mathrm{L}_{l} }^{i} \), and \(F(E_{\mathrm{L}_{l} }^{i})\) are given by (36). Initialize a set \(\mho =\left\{ \rho _{1} ,\ldots ,\rho _{g} \right\} \) of demands with both end nodes \(A_{\rho \in \mho ,U_{k} } \) and \(B_{\rho \in \mho ,U_{k} } \) not affected by f as given by (34). The quantity of \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) [see (33)], which describes the required total entanglement by demand \(\rho _{i} \) with connection set \(\mathrm{{\mathcal S}}'_{i} \) along entangled connections traversed by respective paths \(\mathrm{{\mathcal P}}\left( N\right) \) in N, is set to the amount of the total entanglement required for \(\rho _{i} \), \(D\left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) [see (32)]. As a final substep, determine the shortest path \(\dot{\mathrm{{\mathcal P}}}_{i} \) for \(\rho _{i} \) by using the temporarily incidence matrix \(\tilde{I}_{N} \) as characterized in step 1.
5.3.3 Step 3
In step 3, some computations are performed for the demands \(\rho _{i} \) of set \(\mho \), whose demands are not affected by the failure. The value of the total accessible entanglement via connection set \(\mathrm{{\mathcal S}}'_{i} \) of a given demand \(\rho _{i} \) after a complex failure f, \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \) [see (31)], is set to the minimal amount of utilizable throughput rate of \(\dot{\mathrm{{\mathcal P}}}_{i} \); thus,
From step 2, it follows that \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \) will be equal to the maximal entanglement rate of that entangled connection, which yields the min–max optimization
After this substep, the relation of \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) and \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \) is verified, and the next steps are selected based on it. If the value of the required total entanglement \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) of demand \(\rho _{i} \) along entangled connections traversed by respective paths \(\mathrm{{\mathcal P}}\left( N\right) \) in N does not exceed \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \), the value of the total accessible entanglement of demand \(\rho _{i} \) after a complex failure f, then \(A\left( \mathrm{{\mathcal S}}^{\mathrm{*}} \right) \) value of total accessible entanglement via connection set \(\mathrm{{\mathcal S}}^{\mathrm{*}} \) after a complex failure f is increased by \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \). Conversely, if \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) exceeds \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \), then \(A\left( \mathrm{{\mathcal S}}^{\mathrm{*}} \right) \) is increased by \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \). As the value of \(A\left( \mathrm{{\mathcal S}}^{\mathrm{*}} \right) \) is determined, depending on the relation of \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) and \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \), the value of the required total entanglement \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) is either decreased by \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) or by \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \). This substep therefore yields \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) =0\) if \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \le A\left( \mathrm{{\mathcal S}}'_{i} \right) \), but results in \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) =D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) -A\left( \mathrm{{\mathcal S}}'_{i} \right) \) if \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) >A\left( \mathrm{{\mathcal S}}'_{i} \right) \). Depending on the relation of \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) and \(A\left( \mathrm{{\mathcal S}}'_{i} \right) \), a final computation is also performed in this step. For each entangled connection traversed by the shortest path \(\dot{\mathrm{{\mathcal P}}}_{i} \), the amount of remaining utilizable entanglement throughput is decreased as \(F(E_{\mathrm{L}_{l} }^{i})=F(E_{\mathrm{L}_{l} }^{i})-D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) if \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \le A\left( \mathrm{{\mathcal S}}'_{i} \right) \), and \(F(E_{\mathrm{L}_{l} }^{i})=F(E_{\mathrm{L}_{l} }^{i})-A\left( \mathrm{{\mathcal S}}'_{i} \right) \) if \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) >A\left( \mathrm{{\mathcal S}}'_{i} \right) \) holds.
5.3.4 Step 4
In step 4, a set \(\lambda \) of demands is determined via condition \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) >0\). It follows that some demanded entanglement cannot be served fully; thus, in this step, the entanglement assigned to the demands should be increased as much as possible. These demands are still associated with a nonzero required entanglement ratio in the network, and therefore, these queries should be processed. This step focuses on the service of these demands via the corresponding calculations that are similar to the calculations of step 3. The \(A\left( \mathrm{{\mathcal S}}^{\mathrm{*}} \right) \) value is increased by a given X, which is a given ratio of the maximum of the total accessible entanglement throughput of the entangled connections of the next shortest path \(\ddot{\mathrm{{\mathcal P}}}_{i} \). Then, the value of \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) \) is decreased by ratio X.
5.3.5 Step 5
In step 5, all demands are served until there is no nonzero required entanglement present in the network. All demands are served if \(D^{\mathrm{{\mathcal P}}\left( N\right) } \left( \rho _{i} \left( \mathrm{{\mathcal S}}'_{i} \right) \right) =0\) for all \(\rho _{i} \). The serving process of demands also stops if there is no next shortest path \(\ddot{\mathrm{{\mathcal P}}}_{i} \) in the network; therefore, \(\ddot{\mathrm{{\mathcal P}}}_{i} =\emptyset \) holds. Finally, the empirical estimation of the ratio of accessible entanglement after a failure is determined as \(R_{f} \left( N\right) ={A\left( { {\mathcal S}}^{\mathrm{*}} \right) /A\left( {{\mathcal S}}\right) } \) [see (37)]. The estimation of \(Q\left( R_{f} \left( N\right) \right) \) [see (24)] uses the empirical value of \(A\left( {{\mathcal S}}^{\mathrm{*}} \right) \) after a complex failure f via connection set \(\mathrm{{\mathcal S}}^{\mathrm{*}} \), and also the empirical value of the \(A\left( \mathrm{{\mathcal S}}\right) \) via connection set \(\mathrm{{\mathcal S}}\). Using the resulting estimate \(R_{f} \left( N\right) \) in (37), \(Q\left( R_{f} \left( N\right) \right) \) can be determined via the estimation in (38).
5.3.6 Step 6
Finally, step 6 extends the results for all the m failure events occurring in N to determine \(Q^\mathrm{tot}(N)\) [see (25)].
5.4 Computational complexity
The computational complexity of algorithm \(\mathrm{{\mathcal A}}_{Q\left( \Phi ^{c} \left( f\right) \right) } \) depends on the complexity of the searching method applied in steps 3 and 4 to compute the shortest paths. Using a base-graph method [68,69,70] to determine the shortest path with respect to the entanglement throughput metric, the complexity of the method is at most \(\mathrm{{\mathcal O}}\left( \log n\right) ^{2} \), where n is the size of a k-dimensional n-sized base graph \(G^{k} \) of N.
5.5 Nonlinear optimization for the control observable
A non-stochastic regulation (NSR) [111,112,113] nonlinear optimization method can be defined within the proposed scheme to yield an estimation of the occurrence coefficient (control observable), in the following manner.
Let \(Q\left( \Phi ^{c} \left( f\right) \right) \) be an actual occurrence ratio at a particular f in N subject to be estimated, and let
be the noisy empirical vector of the \(R_{f} \left( N\right) \), \(f=1,\ldots ,m\) noisy quantities associated with the m failure domains \(\mathrm{{\mathcal R}}_{1} ,\ldots ,\mathrm{{\mathcal R}}_{m} \).
In the optimization model, it is assumed that the empirical statistical information obtainable from the quantum network is noisy. Let \(\varDelta \) be a noise vector associated with the estimation error, such that
where \(\vec {Q}^\mathrm{tot} \left( N\right) \) is the vector as
Then, the \(\left\langle Q^\mathrm{tot} \left( N\right) \right\rangle \) estimate of \(Q^\mathrm{tot} \left( N\right) \) yielded via an NSR optimization [111,112,113] is as
where \(\omega \) is an unknown regularization parameter, \(\xi \) is a linear operator, \(\vec {d}\) is a matrix, as
where \(d\left( f\right) \) is a deterministic exponential function
where \(\delta \) is an unknown regularization parameter, such that from (46)
where \(Q\left( \Phi ^{c} \left( f\right) \right) \) is as
where \(\alpha \) and \(\gamma \) are unknown regularization parameters, \(\varphi \left( \varDelta \right) \) is a process that represents the noise of the empirical estimation, \(K_{\varDelta } \) is the covariance matrix of the noise \(\varDelta \) included in the empirical vector \(\vec {R} \left( N\right) \), \(\gamma \) is a regularization parameter, \(\vec {Q}'^\mathrm{tot} \left( N\right) \) is the derivative of \(\vec {Q}^\mathrm{tot} \left( N\right) \), and \(\otimes \) is the convolution operator.
To determine the formula of (44), the estimation of the unknown parameters \(\omega \) in (44), \(\delta \) in (46), and \(\alpha \), \(\gamma \) in (48), is as follows. An \(\mathrm{{\mathcal L}}\) Laplace approximation of a marginal likelihood [113, 114] can be derived to evaluate the estimations of the unknown parameters at a particular \(\vec {R} \left( N\right) \) [see (42)], as
where \(F_{\mathrm{{\mathcal L}}} \left( \vec {R} \left( N\right) \right) \) is a probability function, as
where \(\Lambda \left( \vec {Q}^\mathrm{tot} \left( N\right) \right) \in \mathrm{{\mathbb {R}}}^{\Omega _{\mathrm{{\mathcal L}}} } \) is an approximation of \(\vec {Q}^\mathrm{tot} \left( N\right) \), \(\Omega _{\mathrm{{\mathcal L}}} \) is the order of approximation, and \(\Upsilon \) is defined as
where \(\mathrm{{\mathcal H}}^{-1} \) is the inverse of a Hessian \(\mathrm{{\mathcal H}}\).
As follows, the unknown parameters can be evaluated from the noisy empirical vector (42); therefore, the \(\left\langle Q^\mathrm{tot} \left( N\right) \right\rangle \) estimate of \(Q^\mathrm{tot} \left( N\right) \) can be determined via the formula of (44).
5.6 Entropy rate on a Lie group
The entropy rate [115] in the protocol can be formalized using the Lie algebra theory [116,117,118], in the following manner.
At a given \(Q\left( \Phi ^{c} \left( f\right) \right) \) at a particular failure domain \(\mathrm{{\mathcal R}}_{f} \), let
be a group function on the \(n=2\)-dimensional Lie group \(\mathrm{SE}\left( n\right) =\mathrm{SE}\left( 2\right) \), defined as
where c is a constant set to \(c=0\), while \(X_{1} ,X_{2} \) and \(X_{3} \) are basis matrices for the Lie algebra [117, 118] \(\mathrm{SE}\left( 2\right) \), as
Then, let
be a PDF that characterizes the distribution of the group function \(G_{f} \) at a given f.
For (55), the Lie derivative \(X'_{i} \varphi _{f} \), \(i=1,2,3\), is defined as
where \(\varphi \left( G_{f} \circ e^{fX_{i} } \right) \) is a PDF of \(\left( G_{f} \circ e^{fX_{i} } \right) \), \(e^{fX_{i} } \) is a matrix exponential, and \(\circ \) is the matrix multiplication operator.
Then, the \(S\left( \varphi _{f} \right) \) entropy rate at (55) on a Lie group \({\mathrm{SE}}\left( 2\right) \) is yielded as
while the \(S'\left( \varphi \right) \) change of the entropy rate of (57) is as
Applying the derivations for the m failure domains \(\mathrm{{\mathcal R}}_{f} \) , \(f=1,\ldots ,m\), the \(S_{\Sigma } \left( \varphi \right) \) total entropy rate is
while \(S'_{\Sigma } \left( \varphi \right) \) the derivative of \(S_{\Sigma } \left( \varphi \right) \) is as
6 Numerical evaluation
The numerical evaluation serves illustration purposes in random quantum network settings. As future work, our aim is to utilize an advanced network simulation framework [119].
6.1 CP-EAR and PR-EAR
In this subsection, the CP-EAR and PR-EAR coefficients are illustrated.
The analysis assumes \(f=1,\ldots ,100\) failure domains in random quantum network scenarios \(N_{s} \), \(s=1,2\), such that distribution of \(\Pr \left( f\right) \)-s is drawn from a \(\mathrm{{\mathcal U}}\) uniform distribution, \(\left\{ \Pr \left( f\right) \right\} _{f=1}^{100} \in \mathrm{{\mathcal U}}\).
The distributions of the \(\sigma ^{c} \left( \Phi ^{c} \left( f\right) \right) \) coefficient for random quantum network scenarios \(N_{s} \), \(s=1,2\), in function of x, \(\Phi ^{c} \left( f\right) \ge x\), are depicted in Fig. 2a, b. The corresponding \(\Omega ^{c} \left( \Phi ^{c} \left( f\right) \right) \) values of \(N_{s} \), \(s=1,2\), in function of q, \(q=\Pr \left( f\right) \), are depicted in Fig. 2c, d.
The CP-EAR coefficient (a, b), and the PR-EAR coefficient (c, d). a A distribution of the \(\sigma ^{c} \left( \Phi ^{c} \left( f\right) \right) \) coefficient for a random network scenario \(N_{s} \), \(s=1\), in function of x, \(\Phi ^{c} \left( f\right) \ge x\), \(f=1,\ldots ,100\). b A distribution of the \(\sigma ^{c} \left( \Phi ^{c} \left( f\right) \right) \) coefficient for a random network scenario \(N_{s} \), \(s=2\), in function of x, \(\Phi ^{c} \left( f\right) \ge x\), \(f=1,\ldots ,100\). c Distribution of \(\Omega ^{c} \left( \Phi ^{c} \left( f\right) \right) \) in function of q, \(q=\Pr \left( f\right) \), for \(N_{1} \). d Distribution of \(\Omega ^{c} \left( \Phi ^{c} \left( f\right) \right) \) in function of q, \(q=\Pr \left( f\right) \), for \(N_{2} \)
6.2 DD-EAR
In this subsection, the DD-EAR coefficient is illustrated for random quantum network scenarios \(N_{s} \), \(s=1,2\), with \(f=1,\ldots ,100\).
The distribution of the \(\Phi ^{c} \left( f\right) \) and \(\varphi \left( \Phi ^{c} \left( f\right) ,r_{\mathrm{{\mathcal R}}_{f} } \right) \) coefficients of \(\Lambda ^{x} \left( r_{\mathrm{{\mathcal R}}_{f} } \right) \), and the resulting \(\Lambda ^{x} \left( r_{\mathrm{{\mathcal R}}_{f} } \right) \) in function of the normalized hop distance \(0\le \zeta \left( d\left( \mathrm{{\mathcal P}}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \right) \right) \le 1\),
where \(\mathrm{{\mathcal P}}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \) is a shortest entangled path between \(x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \) and \(y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \) in \(\mathrm{{\mathcal R}}_{f} \), while \(d\left( \mathrm{{\mathcal P}}^{*} \left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \right) \) is an upper bound on \(d\left( \mathrm{{\mathcal P}}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \right) \) in \(\mathrm{{\mathcal R}}_{f} \), for random quantum network scenarios \(N_{s} \), \(s=1,2\) are depicted in Fig. 3.
The DD-EAR coefficient. The distribution of \(\Phi ^{c} \left( f\right) \), \(\varphi \left( \Phi ^{c} \left( f\right) ,r_{\mathrm{{\mathcal R}}_{f} } \right) \), and \(\Lambda ^{x} \left( r_{\mathrm{{\mathcal R}}_{f} } \right) \), at random quantum network scenarios \(N_{s} \), \(s=1,2\), with \(f=1,\ldots ,100\). a A distribution of \(\varphi \left( \Phi ^{c} \left( f\right) ,r_{\mathrm{{\mathcal R}}_{f} } \right) \) at \(N_{1} \), \(f=1,\ldots ,100\). b A distribution of \(\Phi ^{c} \left( f\right) \) at \(N_{1} \), \(f=1,\ldots ,100\). c Distribution of \(\Lambda ^{x} \left( r_{\mathrm{{\mathcal R}}_{f} } \right) \) in function of a normalized hop distance \(\zeta \left( d\left( \mathrm{{\mathcal P}}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \right) \right) \) at \(N_{1} \), \(f=1,\ldots ,100\). d A distribution of \(\varphi \left( \Phi ^{c} \left( f\right) ,r_{\mathrm{{\mathcal R}}_{f} } \right) \) at \(N_{2} \), \(f=1,\ldots ,100\). e A distribution of \(\Phi ^{c} \left( f\right) \) at \(N_{2} \), \(f=1,\ldots ,100\). f Distribution of \(\Lambda ^{x} \left( r_{\mathrm{{\mathcal R}}_{f} } \right) \) in function of a normalized hop distance \(\zeta \left( d\left( \mathrm{{\mathcal P}}\left( x\left( c_{\mathrm{{\mathcal R}}_{f} } \right) ,y\left( c_{\mathrm{{\mathcal R}}_{f} } \right) \right) \right) \right) \) at \(N_{2} \), \(f=1,\ldots ,100\)
7 Conclusions
Here, we defined entanglement accessibility measures to evaluate the ratio of accessible quantum entanglement at complex failure events in the quantum Internet. A complex failure is modeled by a complex failure domain, which identifies a set of quantum nodes and entangled connections affected by that failure. We introduced the terms such as entanglement accessibility ratio and occurrence coefficient to characterize the availability of entanglement in a multiple failure setting. We proposed an algorithm to derive the occurrence coefficient via an empirical estimation observable from the evaluated parameters of the analyzed quantum network. The defined metrics and algorithm can be applied efficiently in experimental quantum Internet scenarios.
Notes
At a constant magnetic field perturbation, the evolution operator is diagonal. Even when the magnetic field depends only on time and not on space, the exact perturbation unitary evolution operator remains diagonal. The quantum system can be disturbed by perturbing it with electric, magnetic, or electromagnetic radiation, and hence, the system becomes excited and changes its state. Magnetic field-based protocol design here is more complex because a 1-D (dimensional) magnetic field will not act on a 1-D charged particle. (From the Lorentz law [53], \(\left( qV\times B \right) \bot V\), where q is the charge of the particle, V is the velocity, and B is the magnetic field.) Note, a charged particle can also be excited in a 3-D box with a 3-D control magnetic field. Another possible extension to this problem is to consider a particle in a 3-D box perturbed by a vector electric field and a vector magnetic field [54, 55].
Abbreviations
- API:
-
Application programming interface
- CP-EAR:
-
Cumulative probability of entanglement accessibility ratio
- EAR:
-
Entanglement accessibility ratio
- O-EAR:
-
Occurrence of entanglement accessibility ratio
- PDF:
-
Probability density function
- PR-EAR:
-
Probabilistic reduction of entanglement accessibility ratio
- QKD:
-
Quantum key distribution
- DD-EAR:
-
Domain-dependent entanglement accessibility ratio
References
Gyongyosi, L., Bacsardi, L., Imre, S.: A survey on quantum key distribution. Infocom. J. XI 2, 14–21 (2019)
Preskill, J.: Quantum computing in the NISQ era and beyond. Quantum 2, 79 (2018)
Arute, F., et al.: Quantum supremacy using a programmable superconducting processor. Nature 574, 7779 (2019). https://doi.org/10.1038/s41586-019-1666-5
Harrow, A.W., Montanaro, A.: Quantum computational supremacy. Nature 549, 203–209 (2017)
Aaronson, S., Chen, L.: Complexity-theoretic foundations of quantum supremacy experiments. In: Proceedings of the 32nd Computational Complexity Conference, CCC’17, pp. 22:1–22:67 (2017)
Farhi, E., Goldstone, J., Gutmann, S., Neven, H.: Quantum algorithms for fixed qubit architectures. arXiv:1703.06199v1 (2017)
Alexeev, Y. et al.: Quantum computer systems for scientific discovery. arXiv:1912.07577 (2019)
Loncar, M., et al.: Development of quantum interconnects for next-generation information technologies. arXiv:1912.06642 (2019)
Farhi, E., Neven, H.: Classification with quantum neural networks on near term processors. arXiv:1802.06002v1 (2018)
Ajagekar, A., Humble, T., You, F.: Quantum computing based hybrid solution strategies for large-scale discrete-continuous optimization problems. Comput. Chem. Eng. 132, 106630 (2020)
Foxen, B. et al.: Demonstrating a continuous set of two-qubit gates for near-term quantum algorithms. arXiv:2001.08343 (2020)
Van Meter, R.: Quantum Networking. Wiley, Hoboken. ISBN 1118648927, 9781118648926 (2014)
Lloyd, S., Shapiro, J.H., Wong, F.N.C., Kumar, P., Shahriar, S.M., Yuen, H.P.: Infrastructure for the quantum Internet. ACM SIGCOMM Comput. Commun. Rev. 34, 9–20 (2004)
Kimble, H.J.: The quantum Internet. Nature 453, 1023–1030 (2008)
Wehner, S., Elkouss, D., Hanson, R.: Quantum internet: a vision for the road ahead. Science 362, 6412 (2018)
Pirandola, S., Braunstein, S.L.: Unite to build a quantum internet. Nature 532, 169–171 (2016)
Pirandola, S.: End-to-end capacities of a quantum communication network. Commun. Phys. 2, 51 (2019)
Caleffi, M.: End-to-end entanglement rate: toward a quantum route metric. In: 2017 IEEE GLOBECOM. (2018) https://doi.org/10.1109/GLOCOMW.2017.8269080
Caleffi, M.: Optimal routing for quantum networks. IEEE Access 5, 22299–22312 (2017). https://doi.org/10.1109/ACCESS.2017.2763325
Caleffi, M., Cacciapuoti, A.S., Bianchi, G.: Quantum internet: from communication to distributed computing. arXiv:1805.04360 (2018)
Castelvecchi, D.: The quantum internet has arrived. Nature 554, 7692 (2018)
Cacciapuoti, A.S., Caleffi, M., Tafuri, F., Cataliotti, F.S., Gherardini, S., Bianchi, G.: Quantum internet: networking challenges in distributed quantum computing. arXiv:1810.08421 (2018)
Laurenza, R., Pirandola, S.: General bounds for sender-receiver capacities in multipoint quantum communications. Phys. Rev. A 96, 032318 (2017)
Kok, P., Munro, W.J., Nemoto, K., Ralph, T.C., Dowling, J.P., Milburn, G.J.: Linear optical quantum computing with photonic qubits. Rev. Mod. Phys. 79, 135–174 (2007)
Van Meter, R., Ladd, T.D., Munro, W.J., Nemoto, K.: System design for a long-line quantum repeater. IEEE/ACM Trans. Netw. 17(3), 1002–1013 (2009)
Van Meter, R., Satoh, T., Ladd, T.D., Munro, W.J., Nemoto, K.: Path selection for quantum repeater networks. Netw. Sci. 3(1–4), 82–95 (2013)
Chakraborty, K., Rozpedeky, F., Dahlbergz, A., Wehner, S.: Distributed routing in a quantum internet. arXiv:1907.11630v1 (2019)
Khatri, S., Matyas, C.T., Siddiqui, A.U., Dowling, J.P.: Practical figures of merit and thresholds for entanglement distribution in quantum networks. Phys. Rev. Res. 1, 023032 (2019)
Kozlowski, W., Wehner, S.: Towards large-scale quantum networks. In: Proceedings of the sixth annual ACM international conference on nanoscale computing and communication, Dublin, Ireland. arXiv:1909.08396 (2019)
Pathumsoot, P., Matsuo, T., Satoh, T., Hajdusek, M., Suwanna, S., Van Meter, R.: Modeling of measurement-based quantum network coding on IBMQ devices. arXiv:1910.00815v1 (2019)
Pal, S., Batra, P., Paterek, T., Mahesh, T. S.: Experimental localisation of quantum entanglement through monitored classical mediator. arXiv:1909.11030v1 (2019)
Pirandola, S.: Bounds for multi-end communication over quantum networks. Quantum Sci. Technol. 4, 045006 (2019)
Pirandola, S. et al.: Advances in quantum cryptography. arXiv:1906.01645 (2019)
Miguel-Ramiro, J., Dur, W.: Delocalized information in quantum networks. arXiv:1912.12935v1 (2019)
Pirker, A., Dur, W.: A quantum network stack and protocols for reliable entanglement-based networks. arXiv:1810.03556v1 (2018)
Tanjung, K. et al.: Probing quantum features of photosynthetic organisms. npj Quantum Inf. 4, 60 (2018)
Tanjung, K., et al.: Revealing nonclassicality of inaccessible objects. Phys. Rev. Lett. 119, 120402 (2017)
Gyongyosi, L., Imre, S.: Optimizing high-efficiency quantum memory with quantum machine learning for near-term quantum devices. Sci. Rep. (2020). https://doi.org/10.1038/s41598-019-56689-0
Gyongyosi, L., Imre, S.: Theory of noise-scaled stability bounds and entanglement rate maximization in the quantum internet. Sci. Rep. (2020). https://doi.org/10.1038/s41598-020-58200-6
Pirandola, S., Laurenza, R., Ottaviani, C., Banchi, L.: Fundamental limits of repeaterless quantum communications. Nat. Commun. (2017). https://doi.org/10.1038/ncomms15043
Muralidharan, S., Kim, J., Lutkenhaus, N., Lukin, M.D., Jiang, L.: Ultrafast and fault-tolerant quantum communication across long distances. Phys. Rev. Lett. 112, 250501 (2014)
Bacsardi, L.: On the way to quantum-based satellite communication. IEEE Commun. Mag. 51(08), 50–55 (2013)
Van Meter, R., Devitt, S.J.: Local and distributed quantum computation. IEEE Comput. 49(9), 31–42 (2016)
Pirandola, S.: Capacities of repeater-assisted quantum communications. arXiv:1601.00966 (2016)
Leepila, R., Oki, E., Kishi, N.: Scheme to find k disjoint paths in multi-cost networks. IEEE ICC 2011, (2011)
Leepila, R.: Routing schemes for survivable and energy-efficient networks. PhD Thesis, Department of Information and Communication Engineering, The University of Electro-Communications (2014)
Rak, J.: Resilient Routing in Communication Networks. Springer, Berlin (2015)
Rak, J.: k-penalty: A novel approach to find k-disjoint paths with differentiated path costs. IEEE Commun. Lett. 14(4), 354–356 (2010)
Mathew, K. T.: Perturbation Theory. Encyclopedia of RF and Microwave Engineering. Wiley, Hoboken. ISBN: 9780471270539. Online ISBN: 9780471654506. (2005) https://doi.org/10.1002/0471654507
Frasca, M.: A strongly perturbed quantum system is a semiclassical system. Proc. R. Soc. A 463, 2085 (2007). https://doi.org/10.1098/rspa.2007.1879
Sulejmanpasic, T., Unsal, M.: Aspects of perturbation theory in quantum mechanics: the BenderWuMathematica package. Comput. Phys. Commun. 228, 273–289 (2018). https://doi.org/10.1016/j.cpc.2017.11.018
Tokura, Y., van der Wiel, W.G., Obata, T., Tarucha, S.: Coherent single electron spin control in a slanting Zeeman field. Phys. Rev. Lett. 96, 047202 (2006)
Jha, D.K.: Text Book Of Vector Dynamics. Discovery Publishing House, New Delhi. ISBN 8183560016, 9788183560016 (2005)
Bethe, H.A., Schwinger, J.: Perturbation theory for cavities. N.D.R.C. RPT. D1-117, Cornell University. (2017). arXiv:1705.02433. https://doi.org/10.1002/lpor.201700113
Lalanne, P., Yan, W., Vynck, K., Sauvan, C., Hugonin, J.-P.: Light interaction with photonic and plasmonic resonances. Laser Photon. Rev. 12(5), 1700113 (2018). https://doi.org/10.1002/lpor.201700113. arXiv:1705.02433
Quantum Internet Research Group (QIRG). https://datatracker.ietf.org/rg/qirg/about/ (2018)
Rozpedek, F., Schiet, T., Thinh, L., Elkouss, D., Doherty, A., Wehner, S.: Optimizing practical entanglement distillation. Phys. Rev. A 97, 062333 (2018)
Humphreys, P., et al.: Deterministic delivery of remote entanglement on a quantum network. Nature 558, 268–273 (2018)
Liao, S.-K., et al.: Satellite-to-ground quantum key distribution. Nature 549, 43–47 (2017)
Ren, J.-G., et al.: Ground-to-satellite quantum teleportation. Nature 549, 70–73 (2017)
Noelleke, C., et al.: Efficient teleportation between remote single-atom quantum memories. Phys. Rev. Lett. 110, 140403 (2013)
Hensen, B., et al.: Loophole-free Bell inequality violation using electron spins separated by 1.3 kilometres. Nature 526, 682–686 (2015)
Hucul, D., et al.: Modular entanglement of atomic qubits using photons and phonons. Nat. Phys. 11(1), 37 (2015)
Sangouard, N., et al.: Quantum repeaters based on atomic ensembles and linear optics. Rev. Mod. Phys. 83, 33 (2011)
Gyongyosi, L., Imre, S., Nguyen, H.V.: A survey on quantum channel capacities. IEEE Commun. Surv. Tutor. (2018). https://doi.org/10.1109/COMST.2017.2786748
Pirandola, S., Braunstein, S.L., Laurenza, R., Ottaviani, C., Cope, T.P.W., Spedalieri, G., Banchi, L.: Theory of channel simulation and bounds for private communication. Quantum Sci. Technol. 3, 035009 (2018)
Gyongyosi, L., Imre, S.: A survey on quantum computing technology. Comput. Sci. Rev. 1, 1 (2018). https://doi.org/10.1016/j.Cosrev.2018.11.002
Gyongyosi, L., Imre, S.: Decentralized base-graph routing for the quantum internet. Phys. Rev. A (2018). https://doi.org/10.1103/PhysRevA.98.022310
Gyongyosi, L., Imre, S.: Dynamic topology resilience for quantum networks. In: Proceedings of SPIE 10547, Advances in Photonics of Quantum Computing, Memory, and Communication XI, 105470Z. (2018) https://doi.org/10.1117/12.2288707
Gyongyosi, L., Imre, S.: Topology adaption for the quantum internet. Quantum Inf. Process 17, 295 (2018). https://doi.org/10.1007/s11128-018-2064-x
Gyongyosi, L., Imre, S.: Entanglement access control for the quantum internet. Quantum Inf. Process 18, 107 (2019). https://doi.org/10.1007/s11128-019-2226-5
Gyongyosi, L., Imre, S.: Opportunistic entanglement distribution for the quantum internet. Sci. Rep. (2019). https://doi.org/10.1038/s41598-019-38495-w
Gyongyosi, L., Imre, S.: Adaptive routing for quantum memory failures in the quantum internet. Quantum Inf. Process 18, 52 (2019). https://doi.org/10.1007/s11128-018-2153-x
Gyongyosi, L., Imre, S.: Multilayer optimization for the quantum internet. Sci. Rep. (2018). https://doi.org/10.1038/s41598-018-30957-x
Gyongyosi, L., Imre, S.: Entanglement availability differentiation service for the quantum internet. Sci. Rep. (2018). https://doi.org/10.1038/s41598-018-28801-3)
Gyongyosi, L., Imre, S.: Entanglement-gradient routing for quantum networks. Sci. Rep. 1, 1 (2017). https://doi.org/10.1038/s41598-017-14394-w
Gyongyosi, L., Imre, S.: A Poisson model for entanglement optimization in the quantum internet. Quantum Inf. Process 18, 233 (2019). https://doi.org/10.1007/s11128-019-2335-1
Biamonte, J., et al.: Quantum machine learning. Nature 549, 195–202 (2017)
Lloyd, S., Mohseni, M., Rebentrost, P.: Quantum algorithms for supervised and unsupervised machine learning. arXiv:1307.0411 (2013)
Lloyd, S., Weedbrook, C.: Quantum generative adversarial learning. Phys. Rev. Lett. 121, 040502 (2018). arXiv:1804.09139
Sheng, Y.B., Zhou, L.: Distributed secure quantum machine learning. Sci. Bull. 62, 1025–1029 (2017)
Imre, S., Gyongyosi, L.: Advanced Quantum Communications–An Engineering Approach. Wiley, New Jersey (2013)
Petz, D.: Quantum Information Theory and Quantum Statistics. Springer, Heidelberg (2008)
Lloyd, S.: Capacity of the noisy quantum channel. Phys. Rev. A 55, 1613–1622 (1997)
Gisin, N., Thew, R.: Quantum communication. Nat. Photon. 1, 165–171 (2007)
Leung, D., Oppenheim, J., Winter, A.: IEEE Trans. Inf. Theory 56, 3478–90 (2010)
Lloyd, S., Mohseni, M., Rebentrost, P.: Quantum principal component analysis. Nat. Phys. 10, 631 (2014)
Lloyd, S.: The universe as quantum computer. In: Zenil, H. (ed.) A computable universe: understanding and exploring nature as computation. World Scientific, Singapore (2013). arXiv:1312.4455v1
Shor, P.W.: Scheme for reducing decoherence in quantum computer memory. Phys. Rev. A 52, R2493–R2496 (1995)
Kobayashi, H., Le Gall, F., Nishimura, H., Rotteler, M.: General Scheme for Perfect Quantum Network Coding with Free Classical Communication. Lecture Notes in Computer Science (Automata, Languages and Programming SE-52 vol. 5555). pp. 622–633. Springer, Berlin (2009)
Hayashi, M.: Prior entanglement between senders enables perfect quantum network coding with modification. Phys. Rev. A 76, 040301(R) (2007)
Hayashi, M., Iwama, K., Nishimura, H., Raymond, R., Yamashita, S.: Quantum Network Coding. Lecture Notes in Computer Science (STACS 2007 SE52 vol. 4393) Thomas, W., Weil, P. (eds.). Springer, Berlin (2007)
Kobayashi, H., Le Gall, F., Nishimura, H., Rotteler, M.: Perfect quantum network communication protocol based on classical network coding. In: Proceedings of 2010 IEEE International Symposium on Information Theory (ISIT), pp. 2686–2690 (2010)
Chen, L., Hayashi, M.: Multicopy and stochastic transformation of multipartite pure states. Phys. Rev. A 83(2), 022331 (2011)
Goebel, A.M., Wagenknecht, G., Zhang, Q., Chen, Y., Chen, K., Schmiedmayer, J., Pan, J.W.: Multistage entanglement swapping. Phys. Rev. Lett. 101, 080403 (2008)
Xiao, Y.F., Gong, Q.: Optical microcavity: from fundamental physics to functional photonics devices. Sci. Bull. 61, 185–186 (2016)
Chou, C., Laurat, J., Deng, H., Choi, K.S., de Riedmatten, H., Felinto, D., Kimble, H.J.: Functional quantum nodes for entanglement distribution over scalable quantum networks. Science 316(5829), 1316–1320 (2007)
Yuan, Z., Chen, Y., Zhao, B., Chen, S., Schmiedmayer, J., Pan, J.W.: Experimental demonstration of a BDCZ quantum repeater node. Nature 454, 1098–1101 (2008)
Schoute, E., Mancinska, L., Islam, T., Kerenidis, I., Wehner, S.: Shortcuts to quantum network routing. arXiv:1610.05238 (2016)
Zhang, W., et al.: Quantum secure direct communication with quantum memory. Phys. Rev. Lett. 118, 220501 (2017)
Enk, S.J., Cirac, J.I., Zoller, P.: Photonic channels for quantum communication. Science 279, 205–208 (1998)
Briegel, H.J., Dur, W., Cirac, J.I., Zoller, P.: Quantum repeaters: the role of imperfect local operations in quantum communication. Phys. Rev. Lett. 81, 5932–5935 (1998)
Dur, W., Briegel, H.J., Cirac, J.I., Zoller, P.: Quantum repeaters based on entanglement purification. Phys. Rev. A 59, 169–181 (1999)
Duan, L.M., Lukin, M.D., Cirac, J.I., Zoller, P.: Long-distance quantum communication with atomic ensembles and linear optics. Nature 414, 413–418 (2001)
Van Loock, P., Ladd, T.D., Sanaka, K., Yamaguchi, F., Nemoto, K., Munro, W.J., Yamamoto, Y.: Hybrid quantum repeater using bright coherent light. Phys. Rev. Lett. 96, 240501 (2006)
Zhao, B., Chen, Z.B., Chen, Y.A., Schmiedmayer, J., Pan, J.W.: Robust creation of entanglement between remote memory qubits. Phys. Rev. Lett. 98, 240502 (2007)
Simon, C., de Riedmatten, H., Afzelius, M., Sangouard, N., Zbinden, H., Gisin, N.: Quantum repeaters with photon pair sources and multimode memories. Phys. Rev. Lett. 98, 190503 (2007)
Tittel, W., Afzelius, M., Chaneliere, T., Cone, R.L., Kroll, S., Moiseev, S.A., Sellars, M.: Photon-echo quantum memory in solid state systems. Laser Photon. Rev. 4, 244–267 (2009)
Sangouard, N., Dubessy, R., Simon, C.: Quantum repeaters based on single trapped ions. Phys. Rev. A 79, 042340 (2009)
Dur, W., Briegel, H.J.: Entanglement purification and quantum error correction. Rep. Prog. Phys 70, 1381–1424 (2007)
Khorasani, S.: Operator approach in nonlinear stochastic open quantum physics. arXiv:1908.05189 (2019)
Ahlgren, A., et al.: Perfusion quantification by model-free arterial spin labeling using nonlinear stochastic regularization deconvolution. Mag. Reson. Med. 70, 1470–1480 (2013)
Zanderigo, F., Bertoldo, A., Pillonetto, G., Cobelli, A.C.: Nonlinear stochastic regularization to characterize tissue residue function in bolus-tracking MRI: assessment and comparison with SVD, block-circulant SVD, and Tikhonov. IEEE Trans. Biomed. Eng. 56, 1287–1297 (2009)
Bell, B.M., Pillonetto, G.: Estimating parameters and stochastic functions of one variable using nonlinear measurement models. Inverse Probl. 20, 627–646 (2004)
Bowen, L.: Examples in the entropy theory of countable group actions. Ergod. Theory Dyn. Syst. (2019). https://doi.org/10.1017/etds.2019.18
de Saxce, G.: Link between lie group statistical mechanics and thermodynamics of continua. Entropy 18, 254 (2016). https://doi.org/10.3390/e18070254
Chirikjian, G.S.: Information-theoretic inequalities un unimodular lie groups. J. Geom. Mech. 2(2), 119–158 (2010). https://doi.org/10.3934/jgm.2010.2.119
Chirikjian, G.S.: Information theory on lie groups and mobile robotics applications. In: Processing of the 2010 IEEE International Conference on Robotics and Automation, Anchorage, Alaska, USA (2010). https://doi.org/10.1109/ROBOT.2010.5509791
SimulaQron. http://www.simulaqron.org/ (2019)
Acknowledgements
Open access funding provided by Budapest University of Technology and Economics (BME). The research reported in this paper has been supported by the Hungarian Academy of Sciences (MTA Premium Postdoctoral Research Program 2019), by the National Research, Development and Innovation Fund (TUDFO/51757/2019-ITM, Thematic Excellence Program), by the National Research Development and Innovation Office of Hungary (Project No. 2017-1.2.1-NKP-2017-00001), by the Hungarian Scientific Research Fund - OTKA K- 112125 and in part by the BME Artificial Intelligence FIKP grant of EMMI (Budapest University of Technology, BME FIKP-MI/SC).
Author information
Authors and Affiliations
Contributions
LGY designed the protocol and wrote the manuscript. LGY and SI analyzed the results. All authors reviewed the manuscript.
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
L. Gyongyosi: Parts of this work were presented in [1].
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Gyongyosi, L., Imre, S. Entanglement accessibility measures for the quantum Internet. Quantum Inf Process 19, 115 (2020). https://doi.org/10.1007/s11128-020-2605-y
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-020-2605-y