Abstract
Duality quantum computing is a new mode of a quantum computer to simulate a moving quantum computer passing through a multi-slit. It exploits the particle wave duality property for computing. A quantum computer with n qubits and a qudit simulates a moving quantum computer with n qubits passing through a d-slit. Duality quantum computing can realize an arbitrary sum of unitaries and therefore a general quantum operator, which is called a generalized quantum gate. All linear bounded operators can be realized by the generalized quantum gates, and unitary operators are just the extreme points of the set of generalized quantum gates. Duality quantum computing provides flexibility and a clear physical picture in designing quantum algorithms, and serves as a powerful bridge between quantum and classical algorithms. In this paper, after a brief review of the theory of duality quantum computing, we will concentrate on the applications of duality quantum computing in simulations of Hamiltonian systems. We will show that duality quantum computing can efficiently simulate quantum systems by providing descriptions of the recent efficient quantum simulation algorithm of Childs and Wiebe (Quantum Inf Comput 12(11–12):901–924, 2012) for the fast simulation of quantum systems with a sparse Hamiltonian, and the quantum simulation algorithm by Berry et al. (Phys Rev Lett 114:090502, 2015), which provides exponential improvement in precision for simulating systems with a sparse Hamiltonian.



Similar content being viewed by others
References
Brandt, H.E., Myers, J.M., Lomonaco Jr., S.J.: Aspects of entangled translucent eavesdropping in quantum cryptography. Phys. Rev. A. 56, 4456 (1997)
Myers, J.M., Brandt, H.E.: Converting a positive operator-valued measure to a design for a measuring instrument on the laboratory bench. Meas. Sci. Technol. 8, 1222 (1997)
Brandt, H.E.: Qubit devices and the issue of quantum decoherence. Prog. Quant. Eletron. 22, 257–370 (1999)
Brandt, H.E.: Positive operator valued measure in quantum information processing. Am. J. Phys. 67, 434–439 (1999)
Brandt, H.E.: Secrecy capacity in the four-state protocol of quantum key distribution. J. Math. Phys. 43, 4526–4530 (2002)
Brandt, H.E.: Quantum-cryptographic entangling probe. Phys. Rev. A. 71, 042312 (2005)
Brandt, H.E.: Quantum computational geodesics. J. Mod. Opt. 56, 2112–2117 (2009)
Brandt, H.E.: Geodesic derivative in quantum circuit complexity analysis. J. Mod. Opt. 57, 1972–1978 (2010)
Brandt, H.E.: Aspects of the Riemannian geometry of quantum computation. Int. J. Mod. Phys. B. 26, 1243004 (2012)
Long, G.L.: General quantum interference principle and duality computer. Commun. Theor. Phys. 45, 825–844 (2006); Also see arXiv:quant-ph/0512120. It was briefly mentioned in an abstract (5111–53) (Tracking No. FN03-FN02-32) submitted to SPIE conference Fluctuations and Noise in Photonics and Quantum Optics in 18 Oct 2002
Gudder, S.: Mathematical theory of duality quantum computers. Quantum Inf. Process. 6, 37–48 (2007)
Long, G.L.: Mathematical theory of the duality computer in the density matrix formalism. Quantum Inf. Process. 6(1), 49–54 (2007)
Zou, X.F., Qiu, D.W., Wu, L.H., Li, L.J., Li, L.Z.: On mathematical theory of the duality computers. Quantum Inf. Process. 8, 37–50 (2009)
Cui, J.X., Zhou, T., Long, G.L.: Density matrix formalism of duality quantum computer and the solution of zero-wave-function paradox. Quantum Inf. Process. 11, 317–323 (2012)
Long, G.L.: Duality quantum computing and duality quantum information processing. Int. J. Theor. Phys. 50, 1305–1318 (2011)
Long, G.L., Liu, Y.: Duality computing in quantum computers. Commun. Theor. Phys. 50, 1303–1306 (2008)
Long, G.L., Liu, Y., Wang, C.: Allowable generalized quantum gates. Commun. Theor. Phys. 51, 65–67 (2009)
Cao, H.X., Li, L., Chen, Z.L., Zhang, Y., Guo, Z.H.: Restricted allowable generalized quantum gates. Chin. Sci. Bull. 55, 2122–2125 (2010)
Wang, Y.Q., Du, H.K., Dou, Y.N.: Note on generalized quantum gates and quantum operations. Int. J. Theor. Phys. 47, 2268–2278 (2008)
Gudder, S.: Duality quantum computers and quantum operations. Int. J. Theor. Phys. 47, 268–279 (2008). http://www.math.du.edu/data/preprints/m0611.pdf
Du, H.K., Wang, Y.Q., Xu, J.L.: Applications of the generalized Lders theorem. J. Math. Phys. 49, 013507 (2008)
Zhang, Y., Cao, H.X., Li, L.: Realization of allowable qeneralized quantum gates. Sci. China Phys. Mech. Astron. 53, 1878–1883 (2010)
Long, G.L., Liu, Y.: Duality quantum computing. Front. Comput. Sci. 2, 167–178 (2008)
Long, G.L., Liu, Y.: General principle of quantum interference and the duality quantum computer. Rep. Prog. Phys. 28, 410–431 (2008). (in Chinese)
Li, C.Y., Li, J.L.: Allowable generalized quantum gates using nonlinear quantum optics. Commun. Theor. Phys. 53, 75–77 (2010)
Liu, Y., Zhang, W.H., Zhang, C.L., Long, G.L.: Quantum computation with nonlinear optics. Commun. Theor. Phys. 49, 107–110 (2008)
Wang, W.Y., Shang, B., Wang, C., Long, G.L.: Prime factorization in the duality computer. Commun. Theor. Phys. 47, 471–473 (2007)
Chen, Z.L., Cao, H.X.: A note on the extreme points of positive quantum operations. Int. J. Theor. Phys. 48, 1669–1671 (2010)
Hao, L., Liu, D., Long, G.L.: An N/4 fixed-point duality quantum search algorithm. Sci. China Phys. Mech. Astron. 53, 1765–1768 (2010)
Liu, Y.: Deleting a marked state in quantum database in a duality computing mode. Chin. Sci. Bull. 58, 2927–2931 (2013)
Hao, L., Liu, D., Long, G.L.: An N4 fixed-point duality quantum search algorithm. Sci. China Phys. Mech. Astron. 53, 1765–1768 (2010)
Cui, J.X., Zhou, T., Long, G.L.: An optimal expression of a Kraus operator as a linear combination of unitary matrices. J. Phys. A Math. Theor. 45, 444011 (2012)
Liu, Y., Cui, J.X.: Realization of Kraus operators and POVM measurements using a duality quantum computer. Chin. Sci. Bull. 59, 2298–2301 (2014)
Cao, H.X., Chen, Z.L., Guo, Z.H., et al.: Complex duality quantum computers acting on pure and mixed states. Sci. China Phys. Mech. Astron. 55, 2452–2462 (2012)
Cao, H.X., Long, G.L., Guo, Z.H., et al.: Mathematical theory of generalized duality quantum computers acting on vector-states. Int. J. Theor. Phys. 52, 1751–1767 (2013)
Li, C.Y., Li, J.L.: Allowable generalized quantum gates using nonlinear quantum optics. Commun. Theor. Phys. 53, 75–77 (2010)
Wu, Z.Q., Zhang, S.F., Zhu, C.X.: Remarks on generalized quantum gates. Hacettepe J. Math. Stat. 43, 451–460 (2014)
Chen, L., Cao, H.X., Meng, H.X.: Generalized duality quantum computers acting on mixed states. Quantum Inf. Process. (2015). doi:10.1007/s11128-015-1112-z
Hao, L., Long, G.L.: Experimental implementation of a fixed-point duality quantum search algorithm in the nuclear magnetic resonance quantum system. Sci. China Phys. Mech. Astron. 54, 936–941 (2011)
Zheng, C., Hao, L., Long, G.L.: Observation of a fast evolution in a parity-time–symmetric system. Philos. Trans. R. Soc. A Math. Phys. Eng. Sci. 371, 20120053 (2013)
Aaronson, S.: Quantum computing, postselection, and probabilistic polynomial-time. Proc. R. Soc. Lond. A Math. Phys. Eng. Sci. 461, 3473–3482 (2005)
Childs, A.M., Wiebe, N.: Hamiltonian simulation using linear combinations of unitary operations. Quantum Inf. Comput. 12(11–12), 901–924 (2012)
Berry, D.W., Childs, A.M., Cleve, R., Kothari, R., Somma, R.D.: Simulating Hamiltonian dynamics with a truncated Taylor series. Phys. Rev. Lett. 114, 090502 (2015)
Wootters, W.K., Zurek, W.H.: A single quantum cannot be cloned. Nature 299, 802–803 (1982)
Dieks, D.: Communication by EPR devices. Phys. Lett. A 92, 271–272 (1982)
Yao, S., Liang, H., Gui-Lu, L.: Why can we copy classical information? Chin. Phys. Lett. 28, 010306 (2011)
Feynman, R.P.: Simulating physics with computers. Int. J. Theor. Phys. 21, 467 (1982)
Benioff, P.: The computer as a physical system: a microscopic quantum mechanical Hamiltonian model of computers as represented by Turing machines. J. Stat. Phys. 22, 563–591 (1980)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26, 1484–1509 (1997)
Grover, L.K.: Quantum mechanics helps in searching for a needle in a haystack. Phys. Rev. Lett. 79, 325–328 (1997)
Long, G.L.: Grover algorithm with zero theoretical failure rate. Phys. Rev. A 64, 022307 (2001)
Toyama, F.M., van Dijk, W., Nogami, Y.: Quantum search with certainty based on modified Grover algorithms: optimum choice of parameters. Quantum Inf. Proc. 12, 1897–1914 (2013)
Lloyd, S.: Universal quantum simulators. Science 273, 1073 (1996)
Lu, Y., Feng, G.R., Li, Y.S., Long, G.L.: Experimental digital quantum simulation of temporal-spatial dynamics of interacting fermion system. Sci. Bull. 60, 241–248 (2015)
Sornborger, A.T.: Quantum simulation of tunneling in small systems. Sci. Rep. 2, 597 (2012)
Childs, A.M., Cleve, R., Deotto, E., Farhi, E., Gutmann, S., Spielman, D.A.: Exponential algorithmic speedup by quantum walk. In: Proceedings of the 35th ACM Symposium on Theory of Computing, pp. 59–68 (2003)
Aharonov, D., Ta-Shma, A.: Adiabatic quantum state generation and statistical zero knowledge. In: Proceedings of the 35th ACM Symposium on Theory of Computing, pp. 20–29 (2003)
Feng, G.R., Xu, G.F., Long, G.L.: Experimental realization of nonadiabatic holonomic quantum computation. Phys. Rev. Lett. 110, 190501 (2013)
Feng, G.R., Lu, Y., Hao, L., Zhang, F.H., Long, G.L.: Experimental simulation of quantum tunneling in small systems. Sci. Rep. 3, 2232 (2013)
Suzuki, M.: General theory of fractal path integrals with applications to many-body theories and statistical physics. J. Math. Phys. 32, 400 (1991)
Blanes, S., Casas, F., Ros, J.: Extrapolation of symplectic integrators. Celest. Mech. Dyn. Astr. 75, 149 (1999)
Berry, D.W., Childs, A.M., Cleve, R., Kothari, R., Somma, R.D.: Proceedings of the 46th Annual ACM Symposium on Theory of Computing, New York, pp. 283–292. ACM Press, New York (2014)
Shor, P.W.: Why haven’t more quantum algorithms been found? J. ACM (JACM) 50, 87–90 (2003)
Ray, P., Chakrabarti, B.K., Chakrabarti, A.: Sherrington–Kirkpatrick model in a transverse field: absence of replica symmetry breaking due to quantum fluctuations. Phys. Rev. B. 39, 11828 (1989)
Kadowaki, T., Nishimori, H.: Quantum annealing in the transverse Ising model. Phys. Rev. E. 58, 53555363 (1998)
Das, A., Chakrabarti, B.K.: Colloquium: quantum annealing and analog quantum computation. Rev. Mod. Phys. 80, 1061 (2008)
Denchev, V. S., Boixo, S., Isakov, S. V., Ding, N., Babbush, R., Smelyanskiy, V., Neven, H.: What is the computational value of finite range tunneling? arXiv preprint arXiv:1512.02206 (2015)
Johnson, M.W., Amin, M.H.S., Gildert, S., Lanting, T., Hamze, F., Dickson, N., Chapple, E.M.: Quantum annealing with manufactured spins. Nature 473, 194–198 (2011)
Acknowledgments
This work was supported by the National Basic Research Program of China (2015CB921002), the National Natural Science Foundation of China Grant Nos. 11175094 and 91221205. Wei is supported by the Fund of Key Laboratory (9140C75010215ZK65001).
Author information
Authors and Affiliations
Corresponding author
Additional information
Project supported by the National Natural Science Foundation of China (Grant Nos. 11175094 and 91221205), the National Basic Research Program of China (2015CB921002).
Appendices
Appendix 1: An example of the Childs–Wiebe algorithm in duality quantum computing
Suppose we want to realize the quantum simulation with \(k=1,\ell _q= q \), then
where \(\ell _q \) \((q\in \lbrace 1,k+1=2\rbrace )\) represent distinct natural numbers and \(\sum _{q=1}^{k+1} C_q=1\), \((C_1,\ldots ,C_{k+1} \in R)\). When \(k=1,\ell _q= q \),
and
For convenient, let \(r=1\), put \( -1 \) into \( S_1(t) \). The duality quantum gate in this case is
where \(U_{1}=-S_1(t)\), \(U_{2}=S_1(t/2)^{2} \).
The QWD is simulated by the unitary operation V and the QWC is simulated by unitary operation W respectively,
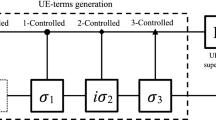
The simulation procedure in the duality quantum computing formalism is illustrated in Fig. 4. Starting from the initial state is \( |0\rangle |\varPsi \rangle \). First, the QWD operation V is performed on the auxiliary qubit, and this transforms the auxiliary qubit through the following transformation,
Quantum circuit of the Childs–Wiebe algorithm in duality quantum computing when \(k=1,\ell _q= q \). \(|\varPsi \rangle \) denotes the initial state of duality quantum computer, and auxiliary qubit is in the \(|0\rangle \) state. The squares represent unitary operations and the circles represent the state of the controlling qubit. Unitary operations \(U_{1}\), \(U_{2}\) are activated only when the auxiliary qubit is \(|0\rangle \) and \(|1\rangle \), respectively
Then we perform the auxiliary qubits \( |0\rangle \) controlled operation \( U_{1} \) and \( U_{2} \) on the computer. We have
We perform the QWC operations W on the state \(\frac{1}{\sqrt{5}}|0\rangle +\frac{2}{\sqrt{5}}|1\rangle \). We have the following
The total process can be described as:
So, the probability of the auxiliary state \( |0\rangle \) being detected is \( \Vert \frac{3}{5}|0\rangle (\frac{1}{3} U_{1} + \frac{4}{3} U_{2})|\varPsi \rangle \Vert ^{2}\), which is the successful probability of the algorithm. Considering the simple case that Hamiltonian has two terms, namely \( m=2 \).
Then \( S_1(t)=\mathrm{e}^{-iH_{1}t}\mathrm{e}^{-2iH_{2}t}\mathrm{e}^{-iH_{1}t}\) and \(S_1(t/2)^{2}=\mathrm{e}^{-iH_{1}t/2}\mathrm{e}^{-iH_{2}t}\mathrm{e}^{-iH_{1}t}\mathrm{e}^{-iH_{2}t}\mathrm{e}^{-iH_{1}t/2}\). In this case, setting \( t=1 \), the probability of implementing U(t) on the target state \( |\varPsi \rangle \) successfully is
where \(P_{f} \) is the failure probability. If the algorithm fails, one can simply restart from the initial state and repeat the process again. The probability of success after 5 repetitions is \(1-(P_{f})^5\approx 0.98\).
Appendix 2: An example of the BCCKS algorithm in duality quantum computing
Suppose \(K=2\), \(L= 2 \), \( H=(\alpha _{1}H_{1}+\alpha _{2}H_{2}) \), then
For convenient, let \(r=1\), put \( -i \) into H , ignore the normalized constant. We only care about the first column in the matrice for the QWD operations, thus we have
where X can be an arbitrary element satisfying the condition that the matrix \( V^{F} \) is unitary. After implementing the first unitary operations \( V^{F} \) in the \( |0\rangle ^{2} \) part of the initial state, we get \(|00\rangle +\sqrt{(\alpha _{1}+\alpha _{2})t}|10\rangle +\frac{(\alpha _{1}+\alpha _{2})t}{\sqrt{2}}|11\rangle \). After implementing the second unitary operations \( V^{S} \) on two \( |0\rangle _{L} \) part of initial state, we get two same states \( \sqrt{\alpha _{1}}|0\rangle +\sqrt{\alpha _{2}}|1\rangle \).
Quantum circuit of the BCCKS algorithm in duality quantum computing when \(K = 2;L = 2 \). In Part a of Fig. 5, \(|\varPsi \rangle \) is the initial state of duality quantum computer and there are 2 numbers of \(|0\rangle \) auxiliary controlling qubits and 2 numbers of 2 level \( |0\rangle \) auxiliary controlling qudits. Unitary operations \(U_{0}\) are activated only when the qubit and qudit holds the respective values indicated in circles. Part b of Fig. 5 is to illustrate that each unitary operation \(U_{0}\) is composed of \( H_{1}\) and \( H_{2}\)
We perform the 2 level auxiliary qudit \( |0\rangle _{2} \) and 2 auxiliary qubits \( |00\rangle \) controlled operations \( U_{j} \) on the computer. We change the state into
Setting \( W^{F} =(V^{F} )^{\dagger }\), \(W^{S}=( V^{S})^{\dagger } \) and performing the QWC operations \( W^{F} \)and \(W^{S} \) on the state \(|{1^k0^{K-k}}\rangle \) and \(|\ell \rangle \), respectively. We focus our attention on the terms with the L level auxiliary qudit being in state \( |0\rangle _{L} \) and K auxiliary qubits being in state \( |0\rangle ^{K} \). We have the following
Denoting the state orthogonal to \(|00\rangle |0\rangle |0\rangle |\varPsi \rangle \) as \( |\varPhi \rangle \), the total process can be described as:
where \( s=1+t(\alpha _{1}+\alpha _{2})/r+t^{2}(\alpha _{1}+\alpha _{2}))^{2}/2r^{2} \). So, the probability of detecting the auxiliary state \(|00\rangle |0\rangle |0\rangle \) is \( P_{s} \), where \(P_{s}=\parallel (1+ t(\alpha _{1}H_{1}+\alpha _{2}H_{2})+\frac{t^{2}}{2}(\alpha _{1}H_{1}+\alpha _{2}H_{2})^{2}) |\varPsi \rangle \parallel ^{2}/{s^{2}}\). Namely the probability of implementing U on the target state \( |\varPsi \rangle \) successfully is \( P_{s} \). If the order of Taylor series K is large enough and \((\alpha _{1}+\alpha _{2})t=\ln 2 \), then \(\sqrt{ P_{s}} \approx 1/s\approx 1/2, \arcsin \beta =\arcsin (1/s)\approx \pi /6\). The error is bounded in the tolerant range. By using the obvious amplitude amplification procedure once, we have \( \sin 3\beta \approx 1 \). Now, the probability of detecting the auxiliary state \( |00\rangle |0\rangle |0\rangle \) is almost \( 100 \%\). Namely, we have deterministically implemented U on the target state \(|\varPsi \rangle \).
Rights and permissions
About this article
Cite this article
Wei, SJ., Long, GL. Duality quantum computer and the efficient quantum simulations. Quantum Inf Process 15, 1189–1212 (2016). https://doi.org/10.1007/s11128-016-1263-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-016-1263-6