Abstract
Two protocols of quantum key agreement (QKA) that solely use Bell state and Bell measurement are proposed. The first protocol of QKA proposed here is designed for two-party QKA, whereas the second protocol is designed for multi-party QKA. The proposed protocols are also generalized to implement QKA using a set of multi-partite entangled states (e.g., 4-qubit cluster state and \(\Omega \) state). Security of these protocols arises from the monogamy of entanglement. This is in contrast to the existing protocols of QKA where security arises from the use of non-orthogonal state (non-commutativity principle). Further, it is shown that all the quantum systems that are useful for implementation of quantum dialogue and most of the protocols of secure direct quantum communication can be modified to implement protocols of QKA.
Similar content being viewed by others
Notes
Here subscripts A, B, C denote Alice, Bob, and Charlie, respectively.
In the stabilizer formalism of quantum error correction Pauli group is frequently used (see Section 10.5.1 of [32]). It is usually defined as \(G_{1}=\left\{ \pm I,\pm iI,\pm \sigma _{x},\pm i\sigma _{x},\pm \sigma _{y},\pm i\sigma _{y},\pm \sigma _{z},\pm i\sigma _{z}\right\} ,\) where \(\sigma _{i}\) is a Pauli matrix. The inclusion of \(\pm 1\) and \(\pm i\) ensures that \(G_{1}\) is closed under standard matrix multiplication, but the effect of \(\sigma _{i},\,-\sigma _{i},\, i\sigma _{i}\), and \(-i\sigma _{i}\) on a quantum state is the same. So in [33], we redefined the multiplication operation for two elements of the group in such a way that global phase is ignored from the product of matrices. This is consistent with the quantum mechanics and it gives us a modified Pauli group \(G_{1}=\{I,\,\sigma _{x},\, i\sigma _{y},\,\sigma _{z}\}=\{I,\, X,\, iY,\, Z\}.\)
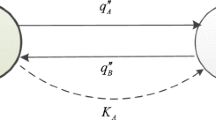
In \(\mathrm{PP^{GV}}\)Alice does not need to disclose her key \(K_{A}\). Everything else is the same and as a consequence \(b=2n,\, q=4n\) and \(c=n\) with \(c\) being the number of bits in the message or key that is transmitted.
References
Bennett, C.H., Brassed, G.: Quantum cryptography: public key distribution and coin tossing. In: Proceedings of the IEEE International Conference on Computers, Systems, and Signal Processing, Bangalore, India, pp. 175–179 (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67, 661–663 (1991)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68, 3121–3124 (1992)
Goldenberg, L., Vaidman, L.: Quantum cryptography based on orthogonal states. Phys. Rev. Lett. 75, 1239–1243 (1995)
Boström, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002)
Lucamarini, M., Mancini, S.: Secure deterministic communication without entanglement. Phys. Rev. Lett. 94, 140501 (2005)
Shukla, C., Pathak, A.: Hierarchical quantum communication. Phys. Lett. A 377, 1337–1344 (2013)
Zhou, N., Zeng, G., Xiong, J.: Quantum key agreement protocol. Electron. Lett. 40, 1149–1150 (2004)
Chong, S.-K., Hwang, T.: Quantum key agreement protocol based on BB84. Optic Commun. 283, 1192–1195 (2010)
Yin, X.-R., Ma, W.-P., Liu, W.-Y.: Three-party quantum key agreement with two-photon entanglement. Int. J. Theor. Phys. 52, 3915–3921 (2013)
Gisin, N., Renner, R., Wolf, S.: classical and quantum key agreement: Is there a classical analog to bound entanglement? Algorithmica 34, 389–412 (2002)
Dijk, M. v., Koppelaar, A.: Quantum key agreement. In: Proceedings of IEEE International Symposium on Information Theory, IEEE, pp. 350–350 (1998)
Tsai, C.W., Hwang, T.: On “Quantum key agreement protocol”, Technical Report, C-S-I-E, NCKU. Taiwan, R.O.C. (2009)
Tsai, C.W., Chong S.K., Hwang, T.: Comment on quantum key agreement protocol with maximally entangled states. In: Proceedings of the 20th Cryptology and Information Security Conference (CISC 2010), pp. 210–213. National Chiao Tung University, Hsinchu, Taiwan, 27–28 May (2010)
Chong, S.-K., Tsai, C.W., Hwang, T.: Improvement on “Quantum key agreement protocol with maximally entangled states”. Int. J. Theor. Phys. 50, 1793–1802 (2011)
Liu, B., Gao, F., Huang, W., Wen, Q.-Y.: Multiparty quantum key agreement with single particles. Quantum Info. Process. 12, 1797–1805 (2013)
Sun, Z., Zhang, C., Wang, B., Li, Q., Long, D.: Improvement on “multiparty quantum key agreement with single particles”. Quantum Inf. Process. 12, 3411–3420 (2013)
Shi, R.-H., Zhong, H.: Multi-party quantum key agreement with Bell states and Bell measurements. Quantum Inf. Process. 12, 921–932 (2013)
Huang, W., Wen, Q.-Y., Liu, B., Su Q., Gao, F.: Cryptanalysis of a multi-party quantum key agreement protocol with single particles, arXiv:1308.2777 (quant-ph)
Diffie, W., Hellman, M.: New directions in cryptography. IEEE Trans. Inf. Theory 22, 644–654 (1976)
Simon, B.-W., Menezes, A.: Authenticated Diffe-Hellman key agreement protocols in selected areas in cryptography. Springer, Berlin Heidelberg (1999)
Victor, S.: Lower bounds for discrete logarithms and related problems. In Advances in Cryptology-EUROCRYPT’97, pp. 256–266. Springer, Berlin Heidelberg (1997)
Shor, P.W.: Polynomial-time algorithms for prime factorization and discrete logarithms on a quantum computer. SIAM J. Comput. 26, 1484–1509 (1997)
Hsueh, C.C., Chen, C.Y.: Quantum key agreement protocol with maximally entangled states. In: Proceedings of the 14th Information Security Conference, National Taiwan University of Science and Technology, Taipei, pp. 236–242 (2004)
Noh, T.-G.: Counterfactual quantum cryptography. Phys. Rev. Lett. 103, 230501 (2009)
Shukla, C., Pathak, A., Srikanth, R.: Beyond the Goldenberg-Vaidman protocol: secure and efficient quantum communication using arbitrary, orthogonal, multi-particle quantum states. Int. J. Quantum Inf. 10, 1241009 (2012)
Yadav, P.,Srikanth R., Pathak, A.: Generalization of the Goldenberg-Vaidman QKD protocol, arXiv:1209.4304 (quant-ph)
Avella, A., Brida, G., Degiovanni, I.P., Genovese, M., Gramegna, M., Traina, P.: Experimental quantum-cryptography scheme based on orthogonal states. Phys. Rev. A 82, 062309 (2010)
Ren, M., Wu, G., Wu, E., Zeng, H.: Experimental demonstration of counterfactual quantum key distribution. Laser Phys. 21, 755–760 (2011)
Brida, G., Cavanna, A., Degiovanni, I.P., Genovese, M., Traina, P.: Experimental realization of counterfactual quantum cryptography. Laser Phys. Lett. 9, 247–252 (2012)
Liu, Yang, et al.: Experimental demonstration of counterfactual quantum communication. Phys. Rev. Lett. 109, 030501 (2012)
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Information. Cambridge University Press, New Delhi (2008)
Shukla, C., Kothari, V., Banerjee, A., Pathak, A.: On the group-theoretic structure of a class of quantum dialogue protocols. Phys. Lett. A 377, 518–527 (2013)
Deng, F.-G., Long, G.L., Liu, X.-S.: Two-step quantum direct communication protocol using the Einstein-Podolsky-Rosen pair block. Phys. Rev. A 68, 042317 (2003)
Cai, Q.-Y., Li, B.-W.: Improving the capacity of the Boström-Felbinger protocol. Phys. Rev. A 69, 054301 (2004)
Pathak, A.: Elements of quantum computation and quantum communication. CRC Press, Boca Raton, USA (2013)
An, N.B.: Quantum dialogue. Phys. Lett. A 328, 6 (2004)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85, 5635–5638 (2000)
Acknowledgments
AP thanks Department of Science and Technology (DST), India for support provided through the DST project No. SR/S2/LOP-0012/2010 and he also acknowledges the supports received from the projects CZ.1.05/2.1.00/03.0058 and CZ.1.07/2.3.00/20.0017 of the Ministry of Education, Youth and Sports of the Czech Republic.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Shukla, C., Alam, N. & Pathak, A. Protocols of quantum key agreement solely using Bell states and Bell measurement. Quantum Inf Process 13, 2391–2405 (2014). https://doi.org/10.1007/s11128-014-0784-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11128-014-0784-0