Abstract
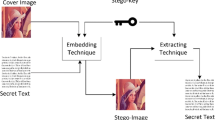
In spatial domain image steganography, Least Significant Bits (LSB) of cover image pixels are used to embed a secret message due to minimal distortion and higher payload capacity. In this paper, we have introduced an exclusive-OR (XOR) based encoding of encrypted secret message bits using varying higher-order pixel intensity bits. Encoding and LSB embedding is done block-wise by dividing the cover image into a number of blocks. The secret message is first encrypted using symmetric key cryptography and then encoded those encrypted bits by XORing them with randomly selected higher-order pixel bis of the cover image to obscure the secret bits further. Next, an inversion technique is applied to the encoded bits block-wise to keep the LSB bit changes to a minimum. The stego-key consists of the symmetric encryption key and the encode-key containing parameter settings such as the number_of_blocks, starting_block, start_pixel_offset, block_selection_rule, etc. This stego-key is shared prior to the actual communication using public-key cryptography to ensure the key’s authenticity and integrity. The extraction process does not require the cover image; the stego-image and the stego-key are sufficient. Experimental results show the visual imperceptibility along with improved image quality metrics such as Mean Square Error (MSE), Peak Signal to Noise Ratio (PSNR), Normalized Cross-Correlation (NCC), and Structural Similarity (SSIM) index in comparison to other well-known techniques. The average PSNR value remains above 51dB, even with 90% of the capacity utilized. The proposed scheme successfully eludes many standard steganalysis attacks such as histogram-based analysis (PDH), chi-square based embed probability test, Regular and Singular groups (RS) analysis, sample pair test, etc. on the tested stego-images.






Similar content being viewed by others
References
Abdulla AA, Sellahewa H, Jassim SA (2019) Improving embedding efficiency for digital steganography by exploiting similarities between secret and cover images. Multimed Tools Appl 78(13):17799–17823
Al-Dmour H, Al-Ani A (2016) A steganography embedding method based on edge identification and xor coding. Expert Syst Appl 46:293–306
Al-Nofaie SMA, Gutub AAA (2020) Utilizing pseudo-spaces to improve arabic text steganography for multimedia data communications. Multimed Tools Appl 79(1–2):19–67. https://doi.org/10.1007/s11042-019-08025-x
Bharti SS, Gupta M, Agarwal S (2019) A novel approach for audio steganography by processing of amplitudes and signs of secret audio separately. Multimed Tools Appl 78(16):23179–23201
Bhuiyan T, Sarower AH, Karim MR, Hassan MM (2019) An image steganography algorithm using lsb replacement through xor substitution. In: 2019 International conference on information and communications technology (ICOIACT). IEEE, pp 44–49
Biswas R, Bandyapadhay SK (2020) Random selection based GA optimization in 2D-DCT domain color image steganography. Multimed Tools Appl 79:7101–7120. https://doi.org/10.1007/s11042-019-08497-x
Boehm B (2014) Stegexpose-a tool for detecting lsb steganography. arXiv:1409.1556
Chan CK, Cheng LM (2004) Hiding data in images by simple lsb substitution. Pattern Recognit 37(3):469–474
Chang CC, Tseng HW (2009) Data hiding in images by hybrid lsb substitution. In: Third international conference on multimedia and ubiquitous engineering (MUE’09). IEEE, pp 360–363
Dalal M, Juneja M (2019) A robust and imperceptible steganography technique for sd and hd videos. Multimed Tools Appl 78(5):5769–5789. https://doi.org/10.1007/s11042-018-6093-3
Datta B, Mukherjee U, Bandyopadhyay SK (2016) Lsb layer independent robust steganography using binary addition. Procedia Comput Sci 85:425–432
Dumitrescu S, Wu X, Memon N (2002) On steganalysis of random lsb embedding in continuous-tone images. In: Proceedings. International conference on image processing, vol 3. IEEE, pp 641–644
Dumitrescu S, Wu X, Wang Z (2002) Detection of lsb steganography via sample pair analysis. In: International workshop on information hiding. Springer, pp 355–372
Farwa S, Bibi N, Muhammad N (2020) An efficient image encryption scheme using Fresnelet transform and elliptic curve based scrambling. Multimed Tools Appl 79:28225–28238. https://doi.org/10.1007/s11042-020-09324-4
Fridrich J, Goljan M, Du R (2001) Detecting lsb steganography in color, and gray-scale images. IEEE Multimed 8(4):22–28
Ganguly NM, Paul G, Saha SK, Burman D (2020) A pvd based high capacity steganography algorithm with embedding in non-sequential position. Multimed Tools Appl 79:13449–13479. https://doi.org/10.1007/s11042-019-08178-9
Kahn D (1996) The history of steganography. In: International workshop on information hiding. Springer, pp 1–5
Kang S, Park H, Park JI (2020) Combining LSB embedding with modified Octa-PVD embedding. Multimed Tools Appl 79:21155–21175. https://doi.org/10.1007/s11042-020-08925-3
Kharrazi M, Sencar HT, Memon N (2006) Improving steganalysis by fusion techniques: a case study with image steganography. In: Transactions on data hiding and multimedia security I. Springer, pp 123–137
Kuznetsov A, Smirnov O, Onikiychuk A, Makushenko T, Anisimova O, Arischenko A (2020) Adaptive pseudo-random sequence generation for spread spectrum image steganography. In: 2020 IEEE 11th international conference on dependable systems, services and technologies (DESSERT). IEEE, pp 161–165
Laishram D, Tuithung T (2021) A novel minimal distortion-based edge adaptive image steganography scheme using local complexity. Multimed Tools Appl 80:831–854. https://doi.org/10.1007/s11042-020-09519-9
Mahato S, Yadav DK, Khan DA (2017) Personal characters to bits mapping using Dot Pattern Character Encoding Scheme (DPCES). J King Saud Univ-Comput Inf Sci 32(2):197–207. https://doi.org/10.1016/j.jksuci.2017.08.003. http://www.sciencedirect.com/science/article/pii/S1319157817301568
Maji G, Mandal S (2019) Secure and robust image steganography using a reference image as key. Int J Innov Technol Explor Eng (IJITEE) 8(7):2828–2839
Maji G, Mandal S (2020) A forward email based high capacity text steganography technique using a randomized and indexed word dictionary. Multimed Tools Appl 1–21. https://doi.org/10.1007/s11042-020-09329-z
Maji G, Mandal S, Sen S, Debnath NC (2018) Dual image based lsb steganography. In: 2nd International conference on recent advances in signal processing, telecommunications & computing (SigTelCom). IEEE, pp 61–66
Maji G, Mandal S, Debnath NC, Sen S (2019) Pixel value difference based image steganography with one time pad encryption. In: 2019 IEEE 17th international conference on industrial informatics (INDIN), vol 1. IEEE, pp 1358–1363
Maji G, Mandal S, Sen S (2020) Dual image-based dictionary encoded data hiding in spatial domain. Int J Inf Secur Privacy (IJISP) 14(2):83–101
Mandal PC, Mukherjee I, Chatterji BN (2021) High capacity reversible and secured data hiding in images using interpolation and difference expansion technique. Multimed Tools Appl 80:3623–3644. https://doi.org/10.1007/s11042-020-09341-3
Maniriho P, Ahmad T (2019) Information hiding scheme for digital images using difference expansion and modulus function. J King Saud Univ-Comput Inf Sci 31(3):335–347
Muhammad N, Bibi N, Mahmood Z, Akram T, Naqvi SR (2017) Reversible integer wavelet transform for blind image hiding method. PloS One 12(5):e0176979
Muhammad N, Bibi N, Qasim I, Jahangir A, Mahmood Z (2018) Digital watermarking using hall property image decomposition method. Pattern Anal Appl 21(4):997–1012
Mukherjee S, Sanyal G (2020) Image steganography with N-puzzle encryption. Multimed Tools Appl 79:29951–29975. https://doi.org/10.1007/s11042-020-09522-0
Sahu AK, Swain G (2019) High fidelity based reversible data hiding using modified lsb matching and pixel difference. J King Saud Univ-Comput Inf Sci
Setiadi DRIM (2019) Payload enhancement on least significant bit image steganography using edge area dilation. Int J Electron Telecommun 65 (2):287–292
Setyono A et al (2019) Securing and hiding secret message in image using xor transposition encryption and lsb method. IOP Publishing, vol 1196, p 012039
Sy Shen, Huang L h, Ss Y u (2018) A novel adaptive data hiding based on improved emd and interpolation. Multimed Tools Appl 77(10):12563–12579
Singh S (2020) Adaptive PVD and LSB based high capacity data hiding scheme. Multimed Tools Appl 79:18815–18837. https://doi.org/10.1007/s11042-020-08745-5
Singh S, Siddiqui TJ (2018) Transform domain techniques for image steganography. In: Computer vision: concepts, methodologies, tools, and applications. IGI Global, pp 170–186
Singh L, Singh A, Singh P (2020) Secure data hiding techniques: a survey. Multimed Tools Appl 79(23):15901–15921
Stanley CA (2005) Pairs of values and the chi-squared attack. Department of Mathematics, Iowa State University
Thakur S, Singh AK, Ghrera SP, Elhoseny M (2019) Multi-layer security of medical data through watermarking and chaotic encryption for tele-health applications. Multimed Tools Appl 78(3):3457–3470
Trithemius J, McLean A (1982) The steganographia of Johannes Trithemius. Magnum Opus Hermetic Sourceworks
Wang Z, Bovik AC, Sheikh HR, Simoncelli EP (2004) Image quality assessment: from error visibility to structural similarity. IEEE Trans Image Process 13(4):600–612
Wang J, Cheng M, Wu P, Chen B (2019) A survey on digital image steganography. J Inf Hiding Privacy Protect 1(2):87–93. https://doi.org/10.32604/jihpp.2019.07189
Westfeld A, Pfitzmann A (1999) Attacks on steganographic systems. In: International workshop on information hiding. Springer, pp 61–76
Wu DC, Tsai WH (2003) A steganographic method for images by pixel-value differencing. Pattern Recognit Lett 24(9-10):1613–1626
Younus ZS, Hussain MK (2019) Image steganography using exploiting modification direction for compressed encrypted data. J King Saud Univ-Comput Inf Sci
Zhang X, Wang S (2004) Vulnerability of pixel-value differencing steganography to histogram analysis and modification for enhanced security. Pattern Recognit Lett 25(3):331–339
Zhang X, Long J, Wang Z, Cheng H (2015) Lossless and reversible data hiding in encrypted images with public-key cryptography. IEEE Trans Circuits Syst Video Technol 26(9):1622–1631
Acknowledgments
This research did not receive any specific grant from funding agencies in the public, commercial, or not-for-profit sectors.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare no conflict of interest.
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Maji, G., Mandal, S. & Sen, S. Cover independent image steganography in spatial domain using higher order pixel bits. Multimed Tools Appl 80, 15977–16006 (2021). https://doi.org/10.1007/s11042-020-10298-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-10298-6