Abstract
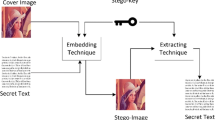
The advantage of spatial domain image steganography techniques is their capacity to embed high payloads of data by directly modifying image pixels. While these techniques have a high-embedding capacity, they often create visual and statistical distortion in smoother regions. Most existing edge steganography techniques divide an image into blocks and insert data by processing the blocks in a linear order, but these method also has multiple drawbacks. First, if the selected block has an insufficient number of edge pixels, it may result in multiple blocks being processed. Second, at high embedding rates, the method creates severe distortion as multiple message bits are hidden in edge pixels and surrounding non-edge pixels without analyzing the statistical dependencies and correlation of pixels, compromising data security. The aim of the proposed method is to construct a Block-wise Edge Adaptive Steganography Scheme (BEASS) using textured regions, particularly edges and surrounding pixels. This scheme dynamically chooses the region to embed messages using a local complexity measure of Standard Deviation. It offers high payload, minimal distortion embedding by hiding three message bits into edge pixels using the minimal Mean Square Error to determine the embedding capacity of neighboring non-edge pixels within the block to preserve the statistical dependencies. The practical merit of this approach was validated and compared with existing algorithms, and experimental results find that the proposed method surpasses IQM tests, achieves a high PSNR of61\(\sim \)65, proves to be robust against kurtosis and skewness distortion, resists histogram attack, RS steganalysis and high dimensional ensemble classifier at 80% block modifications.











Similar content being viewed by others
References
Cheddad A, Condell J, Curran K, Mc Kevitt P (2010) Digital image steganography: Survey and analysis of current methods. Signal Process 90:727–752
Bai J, Chang C-C, Nguyen S, Zhu C, Liu Y (2017) A high payload steganographic algorithm based on edge detection. Displays, pp 46
Bassil Y (2012) Image Steganography based on a Parameterized Canny Edge Detection Algorithm. Int J Comput Appl 60(4):55–40
Li B, He J, Huang J, Shi YQ (2011) A survey on image steganography and steganalysis. Journal of Information Hiding and Multimedia Signal Processing 2(2):142–172
Chakraborty S, Jalal A, Bhatnagar C (2017) LSB Based non blind predictive edge adaptive image steganography. Multimedia Tools and Applications 76:7973–7987
Chan C-K, Cheng LM (2004) Hiding data in images by simple LSB substitution. Pattern Recogn 37 :469–474
Chandramouli R, Memon N (2001) Analysis of LSB based image steganography techniques. IEEE 3:1019–1022
Fawcett T (2004) ROC Graphs: notes and practical considerations for researchers. Mach Learn 31:1–38
Ferzli R, Girija L, Ali W (2010) Efficient implementation of kurtosis based no reference image sharpness metric. Proceedings of SPIE-The International Society for Optical Engineering, pp 7532
Fridrich J, Goljan M (2002) Practical steganalysis of digital Images-State of the art. Proceedings of SPIE-The International Society for Optical Engineering: pp 1–13
Al-Dmour H, Al-Ani A (2015) A steganography embedding method based on edge identification and XOR coding. Expert Syst Appl, 46(C)
Hempstalk K (2006) Hiding Behind Corners: Using Edges in Images for Better Steganography
Leng H-S, Tseng H-W (2014) High-payload block-based data hiding scheme using hybrid edge detector with minimal distortion. IET Image Process 8:647–654
Islam S, Modi M, Gupta P (2014) Edge-based image steganography. EURASIP Journal on Information Security, pp 8
Kodovsky J, Fridrich J (2011) Steganalysis in high dimensions: Fusing classifiers built on random subspaces. Proceedings of SPIE-The International Society for Optical Engineering, pp 7880
Jung K-H (2018) Comparative Histogram Analysis of LSB-based Image Steganography. WSEAS Transactions on Systems and Control 13:103–112
Ker A (2005) Steganalysis of LSB matching in grayscale images. Signal Processing Letters IEEE 12:441–444
Kodovsky J, Fridrich J, Holub V (2012) Ensemble classifiers for steganalysis of digital media. IEEE Transactions on Information Forensics and Security 7(2):432–444
Koo H, Cho N (2013) Skew estimation of natural images based on a salient line detector. J Electron Imaging 22(1):013020(1)–013020(6)
Sanjeev K, Amarpal S, Manoh K (2019) Information hiding with adaptive steganography based on Novel Fuzzy edge identification. Elsevier Defense Technology 15:162–169
Laishram D, Tuithung T (2018) A survey on digital image steganography: current trends and challenges. SSRN Electronic Journal, 10.2139/ssrn.3171494
Lee YK, Chen L-H (2000) High capacity image steganography model. Vision Image and Signal Processing IEE Proceedings 147:288–294
Liao X, Yu Y, Li B, Li Z, Qin Z (2020) A new payload partition strategy in color image steganography. IEEE Transactions on Circuits and Systems for Video Technology 30(3):685–696
Luo W, Huang F, Huang J (2010) Edge adaptive image steganography based on LSB matching revisited. IEEE Transactions on Information Forensics and Security 5:201–214
Mielikainen J (2006) LSB Matching revisited. Signal Processing Letters IEEE 13:285–287
Pevný T, Bas P, Fridrich J (2010) Steganalysis by subtractive pixel adjacency matrix. IEEE Transactions on Information Forensics and Security 5 (2):142–172
Subhedar M, Mankar V (2014) Current status and key issues in image steganography: a survey. Computer Science Review, pp 95–113
Cheng W-J, Chang C-C, Le T (2010) High payload steganography mechanism using hybrid edge detector. Expert Syst Appl 37:3292–3301
Yang C-H, Weng C-Y, Wang S-J, Sun H-M (2008) Adaptive data hiding in edge areas of images with spatial LSB domain systems. Information Forensics and Security IEEE Transactions 3(2):488–497
Liu Y, Cheng MM, Bian J, Zhang LJ, Peng T, Cao Y (2018) Semantic edge detection with diverse deep supervision. ArXiv Computer Science, arXiv:1804.02864
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Laishram, D., Tuithung, T. A novel minimal distortion-based edge adaptive image steganography scheme using local complexity. Multimed Tools Appl 80, 831–854 (2021). https://doi.org/10.1007/s11042-020-09519-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09519-9