Abstract
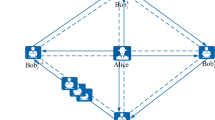
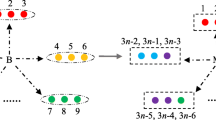
A quantum secret sharing scheme with identity authentication is proposed. By leveraging the measurement correlation of the GHZ states, conjugate measurement bases (X-basis and Y-basis) and bitwise XOR operation, the secret message sender, Alice, can authenticate the identities of other participants, namely Bob and Charlie. Once quantum identity authentication is established, Alice encrypts the secret message by mapping it into a local unitary operation on the GHZ particles based on the pre-agreed coding rules. With the entanglement swapping feature of GHZ states, Bob and Charlie can decode Alice’s secret message by utilizing Bell-basis measurement. The proposed scheme is characterized by its simple operation, high transmission efficiency and quantum bit utilization. Additionally, it demonstrates resilience against various common attacks, including interception retransmission attack, identity impersonation attack, denial of service attack, entangle-and-measure attack.
Similar content being viewed by others
References
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979). https://doi.org/10.1145/359168.359176
Hillery, M., Buzek, V., Berthiaume, A.: Quantum secret sharing. Phys. Rev. A 59(3), 1829–1834 (1999). https://doi.org/10.1103/PhysRevA.59.1829
Karlsson, A., Koashi, M., Imoto, N.: Quantum entanglement for secret sharing and secret splitting. Phys. Rev. A 59(1), 162–168 (1999). https://doi.org/10.1103/PhysRevA.59.162
Xiao, L., Lu Long, G., Deng, F.-G., Pan, J.-W.: Efficient multiparty quantum-secret-sharing schemes. Phys. Rev. A 69, 052307 (2004). https://doi.org/10.1103/PhysRevA.69.052307
Lin, S., Wen, Q.-Y., Qin, S.-J., Zhu, F.-C.: Multiparty quantum secret sharing with collective eavesdropping-check. Opt. Commun. 282(22), 4455–4459 (2009). https://doi.org/10.1016/j.optcom.2009.07.053
Abulkasim H, Hamad, S., Khalifa, A., El Bahnasy, K.: Quantum secret sharing with identity authentication based on bell states. Int. J. Quantum Inf. 15(4) (2017). https://doi.org/10.1142/S021974991750023X
Qin, H., Tang, W.K.S., Tso, R.: Three-party quantum secret sharing based on d-dimensional bell state. Modern Phys. Lett. B 33(3) (2019). https://doi.org/10.1142/S0217984919500234
Wang, T.-Y., Wang, X.-X., Cai, X.-Q., Wei, C.-Y., Zhang, R.-L.: Analysis of efficient and secure dynamic quantum secret sharing protocol based on bell states. Quantum Inf. Process. 20(1) (2021). https://doi.org/10.1007/s11128-020-02916-x
Shi, R.-H.: Useful equations about bell states and their applications to quantum secret sharing. IEEE Commun. Lett. 24(2), 386–390 (2020). https://doi.org/10.1109/LCOMM.2019.2954134
Liu, M.-H.: Multiparty quantum secret sharing protocol using bell particle. Computer and Modernization 0(4), 55–58 (2014)
Samadder Chaudhury, S.: A quantum evolving secret sharing scheme. Int. J. Theor. Phys. 59(12), 3936–3950 (2020). https://doi.org/10.1007/s10773-020-04644-5
Yin-Ju, L.: Quantum secret sharing via cavity qed. Int. J. Theor. Phys. 59(10), 3324–3328 (2020). https://doi.org/10.1007/s10773-020-04591-1
Song, X., Liu, Y., Xiao, M., Deng, H., Yang, S.: A verifiable (t, n) threshold quantum state sharing scheme on ibm quantum cloud platform. Quantum Inf. Process. 19(9), 337 (2020). https://doi.org/10.1007/s11128-020-02846-8
Shi, R.-H., Li, Y.-F.: Quantum secret permutating protocol. IEEE Trans. Comput. 72(5), 1223–1235 (2023). https://doi.org/10.1109/TC.2022.3207121
Ye, C.-Q., Ye, T.-Y.: Circular semi-quantum secret sharing using single particles*. Commun. Theor. Phys. 70(6), 661 (2018). https://doi.org/10.1088/0253-6102/70/6/661
Chen, Y., Ye, T.-Y.: Semiquantum secret sharing by using \(\chi \)-type states. Eur. Phys. J. Plus 137(12), 1331 (2022). https://doi.org/10.1140/epjp/s13360-022-03521-w
Li, Q., Chan, W.H., Long, D.-Y.: Semiquantum secret sharing using entangled states. Phys. Rev. A 82(2), 022303 (2010)
Wang, J., Zhang, S., Zhang, Q., Tang, C.-J.: Semiquantum secret sharing using two-particle entangled state. Int. J. Quantum Inf. 10(05), 1250050 (2012)
Li, L., Qiu, D., Mateus, P.: Quantum secret sharing with classical bobs. J. Phys. A Math. Theor. 46(4), 045304 (2013)
Tsai, C.-W., Yang, C.-W., Lee, N.-Y.: Semi-quantum secret sharing protocol using w-state. Modern Phys. Lett. A 34(27), 1950213 (2019)
Shor, P.: Algorithms for quantum computation - discrete logarithms and factoring. In: Goldwasser, S. (ed.) 35TH Annual symposium on foundations ot computer science, proceedings. Annual symposium on foundations of computer science, pp. 124–134. IEEE, Computer Soc Press, 10662 LOS VAQUEROS CIRCLE, LOS ALAMITOS, CA 90720 (1994)
Yang, Y.-G., Liu, X.-X., Gao, S., Chen, X.-B., Li, D., Zhou, Y.-H., Shi, W.-M.: A stronger participant attack on the measurement-device-independent protocol for deterministic quantum secret sharing. Quantum Inf. Process. 20(7) (2021). https://doi.org/10.1007/s11128-021-03141-w
Qin, S.-J., Gao, F., Wen, Q.-Y., Zhu, F.-C.: Cryptanalysis of the hillery-bužek -berthiaume quantum secret-sharing protocol. Phys. Rev. A 76, 062324 (2007). https://doi.org/10.1103/PhysRevA.76.062324
Gao, F., Qin, S.-J., Wen, Q.-Y., Zhu, F.-C.: A simple participant attack on the brádler-dušek protocol. Quantum Info. Comput. 7(4), 329–334 (2007)
Crépeau, C., Salvail, L.: Quantum oblivious mutual identification. In: Guillou, L.C., Quisquater, J.-J. (eds.) Advances in Cryptology – EUROCRYPT ’95, pp. 133–146. Springer, Berlin, Heidelberg (1995)
Mihara, T.: Quantum identification schemes with entanglements. Phys. Rev. A 65(5, A) (2002). https://doi.org/10.1103/PhysRevA.65.052326
Li, X., Barnum, H.: Quantum authentication using entangled states. Int. J. Found Comput. Sci. 15(04), 609–617 (2004). https://doi.org/10.1142/S0129054104002649
Jian, W., Quan, Z., Chao-Jing, T.: Multiparty simultaneous quantum identity authentication based on entanglement swapping. Chin. Phys. Lett. 23(9), 2360–2363 (2006)
Zhang, Z., Zeng, G., Zhou, N., Xiong, J.: Quantum identity authentication based on ping-pong technique for photons. Phys. Lett. A 356(3), 199–205 (2006). https://doi.org/10.1016/j.physleta.2006.03.048
Zheng, X.-y., Long, Y.-x.: Controlled quantum secure direct communication with authentication protocol based on five-particle cluster state and classical xor operation. Quantum Inf. Process. 18(5) (2019). https://doi.org/10.1007/s11128-019-2239-0
Kang, M.-S., Heo, J., Hong, C.-H., Yang, H.-J., Han, S.-W., Moon, S.: Controlled mutual quantum entity authentication with an untrusted third party. Quantum Inf. Process 17(7) (2018). https://doi.org/10.1007/s11128-018-1927-5
Zhang, S., Chen, Z.-K., Shi, R.-H., Liang, F.-Y.: A novel quantum identity authentication based on bell states. Int. J. Theor. Phys. 59(1), 236–249 (2020). https://doi.org/10.1007/s10773-019-04319-w
Jiang, S., Zhou, R.-G., Hu, W.: Semi-quantum mutual identity authentication using bell states. Int. J. Theor. Phys. 60(9), 3353–3362 (2021). https://doi.org/10.1007/s10773-021-04911-z
Lou, X., Wang, S., Ren, S., Zan, H., Xu, X.: Quantum identity authentication scheme based on quantum walks on graphs with ibm quantum cloud platform. Int. J. Theor. Phys. 61(2) (2022). https://doi.org/10.1007/s10773-022-04986-2
Jian, L., Wang, Y., Chen, G., Zhou, Y., Liu, S.: Quantum identity authentication using a hadamard gate based on a ghz state. J Phys. B-Atomic Molecular and Opt. Phys. 56(7) (2023). https://doi.org/10.1088/1361-6455/acbd27
Musanna, F., Kumar, S.: Quantum secret sharing using ghz state qubit positioning and selective qubits strategy with simulation analysis. Int. J. Theor. Phys. 61(10) (2022). https://doi.org/10.1007/s10773-022-05237-0
Hwang, T., Hwang, C.-C., Li, C.-M.: Multiparty quantum secret sharing based on ghz states. Phys. Scr. 83(4) (2011). https://doi.org/10.1088/0031-8949/83/04/045004
Xu, Y., Li, Z., Liu, T., Zhu, H.: Multi-party quantum secret sharing protocol based on ghz states entanglement swapping. Int. J. Theor. Phys. 61(3) (2022). https://doi.org/10.1007/s10773-022-05081-2
Fu-Guo, D., Ping, Z., Xi-Han, L., Chun-Yan, L., Hong-Yu, Z.: Efficient multiparty quantum secret sharing with greenberger-horne-zeilinger states. Chin. Phys. Lett. 23(5), 1084 (2006). https://doi.org/10.1088/0256-307X/23/5/006
Acknowledgements
This work was supported by National Natural Science Foundation of China (Grant No. 61871120), and the Natural Science Foundation of Jiangsu Province, China (Grant Nos. BK20191259 and BK20220804)
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhong, J., Ruan, B. & Liu, Z. Quantum Secret Sharing with Identity Authentication Based on GHZ States Entanglement Swapping. Int J Theor Phys 62, 266 (2023). https://doi.org/10.1007/s10773-023-05455-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s10773-023-05455-0