Abstract
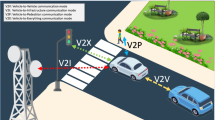
The rapid advancements in computer systems and wireless sensor networks (WSNs) motivate many intelligent transportation systems (ITSs) applications in smart cities, such as vehicular ad hoc networks (VANETs). The WSN supports data exchange between mobile vehicles and servers to provide effective traffic control and smooth service for VANET users. However, the vehicle environment still faces many challenges. One of the VANET concerns is the privacy and security of data flows from heterogeneous systems. Therefore, we suggest a Provably Online/Offline Signcryption (POOSC) protocol for vehicular communication in VANET to preserve data confidentiality and ciphertext unforgeability. In this architecture, the transmitter registered in the Identity-Based Cryptosystems (IBC) environment can safely and efficiently communicate with the receiver in the Public-Key Infrastructure (PKI) environment despite the limitations and challenges of heterogeneous systems. In a Random Oracle Model (ROM), we show that our protocol is safe against Indistinguishability-Adaptive Chosen-Ciphertext Attacks (IND-CCA2) under the Computational Diffie–Hellman (CDH) assumption and Existential Unforgeability-Adaptive Chosen Message Attacks (EUF-CMA) under the Discret-Logarithm (DL) assumption. Moreover, the POOSC protocol overcomes the certificate authority burden. Besides, we designed the POOSC protocol with a free pairing that achieves low computation cost and better scalability for VANET environments. The POOSC effectively meets non-repudiation, integrity, and authentication in a logically single step.









Similar content being viewed by others
References
Ali I, Lawrence T, Li F (2020) An efficient identity-based signature scheme without bilinear pairing for vehicle-to-vehicle communication in VANETs. J Syst Architect 103:101692
Ali I, Lawrence T, Omala AA, Li F (2020) An efficient hybrid signcryption scheme with conditional privacy-preservation for heterogeneous vehicular communication in VANETs. IEEE Trans Veh Technol 69(10):11266–11280
Bansal U, Kar J, Ali I, Naik K (2022) ID-CEPPA: identity-based computationally efficient privacy-preserving authentication scheme for vehicle-to-vehicle communications. J Syst Archit 102387
Chatterjee T, Karmakar R, Kaddoum G, Chattopadhyay S, Chakraborty S (2022) A survey of VANET/V2X routing from the perspective of non-learning-and learning-based approaches. IEEE Access 10:23022–23050
Cui J, Wei L, Zhang J, Xu Y, Zhong H (2018) An efficient message-authentication scheme based on edge computing for vehicular ad hoc networks. IEEE Trans Intell Transp Syst 20(5):1621–1632
Elkhalil A, Elhabob R, Eltayieb N et al (2021) An efficient signcryption of heterogeneous systems for internet of vehicles. J Syst Archit 113:101885
Elkhalil A, Zhang J, Elhabob R (2021) An efficient heterogeneous blockchain-based online/offline signcryption systems for internet of vehicles. Clust Comput 24(3):2051–2068
Gao H, Liu C, Li Y, Yang X (2020) V2VR: reliable hybrid-network-oriented V2V data transmission and routing considering RSUS and connectivity probability. IEEE Trans Intell Transp Syst 22(6):3533–3546
Gura N, Patel A, Wander A, Eberle H, Shantz SC (2004) Comparing elliptic curve cryptography and RSA on 8-bit CPUs. In: International workshop on cryptographic hardware and embedded systems. Springer, pp 119–132
Hemalatha R et al (2021) A survey: security challenges of VANET and their current solution. Turkish J ComputMath Educ (TURCOMAT) 12(2):1239–1244
Huang Q, Yue W, He Y, Yang Y (2018) Secure identity-based data sharing and profile matching for mobile healthcare social networks in cloud computing. IEEE Access 6:36584–36594
Janani V, Manikandan M (2018) Efficient trust management with Bayesian-evidence theorem to secure public key infrastructure-based mobile ad hoc networks. EURASIP J Wirel Commun Netw 2018(1):1–27
Jin C, Chen G, Yu C, Shan J, Zhao J, Jin Y (2018) An efficient heterogeneous signcryption for smart grid. PLoS ONE 13(12):e0208311
Khan S, Sharma I, Aslam M, Khan MZ, Khan S (2021) Security challenges of location privacy in VANETs and state-of-the-art solutions: a survey. Future Internet 13(4):96
Kumar A, Bansal M, et al (2017) A review on VANET security attacks and their countermeasure. In: 2017 4th international conference on signal processing, computing and control (ISPCC). IEEE, pp 580–585
Kumar S, Singh V (2021) A review of digital signature and hash function based approach for secure routing in VANET. In: 2021 International conference on artificial intelligence and smart systems (ICAIS). IEEE, pp 1301–1305
Li F, Han Y, Jin C (2016) Practical access control for sensor networks in the context of the internet of things. Comput Commun 89:154–164
Li F, Han Y, Jin C (2016) Practical signcryption for secure communication of wireless sensor networks. Wirel Pers Commun 89(4):1391–1412
Li F, Zheng Z, Jin C (2016) Secure and efficient data transmission in the internet of things. Telecommun Syst 62(1):111–122
Li Y, Qi Y, Lu L (2017) Secure and efficient V2V communications for heterogeneous vehicle ad hoc networks. In: 2017 International conference on networking and network applications (NaNA). IEEE, pp 93–99
Li Y, Wang C, Zhang Y, Niu S (2016) Privacy-preserving multi-receiver signcryption scheme for heterogeneous systems. Secur Commun Netw 9(17):4574–4584
Liang S, Cheng J, Zhang J (2020) Research on data load balancing technology of massive storage system for wearable devices. Digit Commun Netw
Liu J, Li J, Zhang L, Dai F, Zhang Y, Meng X, Shen J (2018) Secure intelligent traffic light control using fog computing. Futur Gener Comput Syst 78:817–824
Liu X, Wang Z, Ye Y, Li F (2020) An efficient and practical certificateless signcryption scheme for wireless body area networks. Comput Commun 162:169–178
Luckshetty A, Dontal S, Tangade S, Manvi SS (2016) A survey: comparative study of applications, attacks, security and privacy in VANETs. In: 2016 International conference on communication and signal processing (ICCSP). IEEE, pp 1594–1598
Manvi SS, Tangade S (2017) A survey on authentication schemes in VANETs for secured communication. Veh Commun 9:19–30
Maurya AK, Das AK, Jamal SS, Giri D (2021) Secure user authentication mechanism for IoT-enabled wireless sensor networks based on multiple bloom filters. J Syst Archit 120:102296
Mundhe P, Verma S, Venkatesan S (2021) A comprehensive survey on authentication and privacy-preserving schemes in VANETs. Comput Sci Rev 41:100411
Omala AA, Mbandu AS, Mutiria KD, Jin C, Li F (2018) Provably secure heterogeneous access control scheme for wireless body area network. J Med Syst 42(6):1–14
Saeed MES, Liu Q, Tian G, Gao B, Li F (2018) HOOSC: heterogeneous online/offline signcryption for the internet of things. Wirel Netw 24(8):3141–3160
Shamir A (1984) Identity-based cryptosystems and signature schemes. In: Workshop on the theory and application of cryptographic techniques. Springer, pp 47–53
Shao Z, Gao Y (2014) A provably secure signature scheme based on factoring and discrete logarithms. Appl Math Inf Sci 8(4):1553
Shim KA (2014) S2DRP: secure implementations of distributed reprogramming protocol for wireless sensor networks. Ad Hoc Netw 19:1–8
Shim KA, Lee YR, Park CM (2013) EIBAS: an efficient identity-based broadcast authentication scheme in wireless sensor networks. Ad Hoc Netw 11(1):182–189
Sudarsono A, Yuliana M, Darwito HA (2017) A secure data sharing using identity-based encryption scheme for e-healthcare system. In: 2017 3rd International conference on science in information technology (ICSITech). IEEE, pp 429–434
Ullah I, Alomari A, Ul Amin N, Khan MA, Khattak H (2019) An energy efficient and formally secured certificate-based signcryption for wireless body area networks with the internet of things. Electronics 8(10):1171
Wang L, Kuo GSG (2012) Mathematical modeling for network selection in heterogeneous wireless networks—a tutorial. IEEE Commun Surv Tutor 15(1):271–292
Zhang B, Jia Z, Zhao C (2018) An efficient certificateless generalized signcryption scheme. Secur Commun Netw
Zhang W, Wang N, Li L, Wei T (2022) Joint compressing and partitioning of CNNs for fast edge-cloud collaborative intelligence for IoT. J Syst Archit 102461
Zhou F, Li Y, Ding Y (2019) Practical V2I secure communication schemes for heterogeneous VANETs. Appl Sci 9(15):3131
Zhou Y, Yang B, Zhang W (2016) Provably secure and efficient certificateless generalized signcryption. Chin J Comput 39(3):543–551
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Elkhalil, A., zhang, J., Elhabob, R. et al. POOSC: Provably online/offline signcryption scheme for vehicular communication in VANETs. Computing 105, 2539–2561 (2023). https://doi.org/10.1007/s00607-023-01196-4
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00607-023-01196-4