Abstract
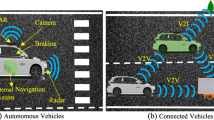
In the rapid growth of automated transportation systems Vehicle to Infrastructure (V2I) communication is growing in significance to guarantee the effectiveness, security, and dependability of contemporary road networks. Sensitive data is exchanged during V2I communication, making strong authentication procedures essential to preventing fraudulent activity and potential security risks. This paper suggests an enhanced authentication technique in order to overcome the drawbacks of the current V2I communication security protocols. To improve the overall strength of the authentication procedure, proposed methodology combines cutting-edge cryptographic methods with creative security controls. To address the dynamic and resource-constrained nature of vehicle networks, the suggested approach focuses on striking a compromise between security, efficiency, and scalability. Large-scale deployment of cellular communications networks, such LTE-V2X and 5G NR, together with the Vehicle to Everything (V2X) architecture intended to facilitate vehicle communications. They could ensure adequate performance (latency, bandwidth, packet loss) and a stable geographic distribution. This paper suggests a safe authentication method for 5G-based V2X communication in this situation. In order to meet security needs, this paper proposes lightweight cryptography techniques to ensure an elevated level of security in the vehicle-to-vehicle infrastructure of mobile communication. Additionally it supports vehicles in obtaining all keys and data from RSU other cars or the network safely. It validates proposal utilizing the Automated Validation of Internet Security Protocols and Applications (AVISPA) tool to achieve the security goals. The EAP-IKEv2 protocol is used to establish a secure communication with the assistance of the HLPSL language and SPAN, a security protocol animator for AVISPA. By reusing IKEv2's encryption and payloads, EAP-IKEv2 is an adaptable EAP technique that allows for the facilitation of symmetric and asymmetric authentication as well as their combination. With the aim of establishing IPsec security associations, this EAP technique offers the security advantages associated with IKEv2 authentication and key agreement without requiring the exchange of messages in pairs using Diffie-Hellman. It assess the performance based on operational cost, time complexity, and space complexity, showing that proposed model has a lower computational cost.










Similar content being viewed by others
Data availability
The dataset generated and analyzed during the current study are available from the corresponding author on reasonable request.
References
Yang L, Han J, Zhang Y. An efficient authentication scheme for security and privacy preservation in V2I communications. In: 2017 IEEE 28th Annual International Symposium on Personal, Indoor, and Mobile Radio Communications (PIMRC). IEEE; 2017. pp. 1–6.
Jiang W, Li F, Lin D, Bertino E. A mutual authentication scheme for vehicular ad hoc networks. IEEE Trans Inf Forensics Secur. 2015;10(12):2681–91.
Liu Y, Wang L, Chen HH. A lightweight and secure authentication protocol for V2I communication. IEEE Trans Veh Technol. 2014;63(2):907–19.
Ali I, Chen Y, Faisal M, Li M. Efficient and provably secure schemes for vehicular ad-hoc networks. In: Heterogeneous Cloud Computing and Security: Second International Conference. Springer; 2013. pp. 199–212.
Li X, Ma J, Wang W, Xiong Y, Zhang J. A novel smart card and dynamic ID based remote user authentication scheme for vehicular ad hoc networks. J Netw Comput Appl. 2013;36(5):1365–71.
Wang B, Zhang G, Gong Y. A secure authentication scheme for vehicular ad-hoc networks based on certificates. In: 2012 IEEE International Conference on Green Computing and Communications (GreenCom). IEEE; 2012. pp. 548–552.
Zhang Q, Cheng L, Lu R, Yang B. A secure and efficient authentication scheme for vehicular ad hoc networks. IEEE Trans Veh Technol. 2010;59(1):293–300.
Yu W, Zhang Y, Wang W, Gao X. A lightweight authentication scheme for vehicular ad hoc networks. In: 2010 Fifth International Conference on Mobile Ad-hoc and Sensor Networks (MSN). IEEE; 2010. pp. 436–441.
Zhang C, Lin X, Lu R, Ho PH. An efficient and secure authentication scheme for VANETs. In: 2009 IEEE Wireless Communications and Networking Conference. IEEE; 2009, pp. 1–6.
Zhang Y, Wang W, Yu W, Zhang H. A lightweight authentication scheme for VANETs. In: 2009 IEEE Vehicular Networking Conference. IEEE; 2009. pp. 1–5.
Zhang Y, Liu L, Han J, Lu Y. A lightweight and secure authentication scheme based on ECC for V2I communication. In: 2018 IEEE International Conference on Communications (ICC). IEEE; 2018. pp. 1–6.
Liang X, Wang L, Hu X, Wang Z. A privacy-preserving authentication scheme for V2I communication based on blockchain. IEEE Trans Intell Transp Syst. 2020;21(1):252–61.
Zhang J, Li F, Lin Q, Liu J. A secure and efficient authentication scheme for V2I communication based on certificate revocation list and identity-based signature. IEEE Trans Veh Technol. 2020;69(6):5996–6008.
Chen S, Wang X, Zhang Q, Wang J. A secure and efficient authentication scheme for V2I communication based on lightweight elliptic curve cryptography. IEEE Access. 2020;8:183303–15.
Li Z, Zhang W, Zhang J, Wang C. A privacy-preserving and efficient authentication scheme for V2I communication based on blockchain and attribute-based signature. IEEE Trans Ind Inform. 2021;17(11):7950–61.
Liu T, Zhang M, Choo KR. A lightweight and secure authentication scheme for V2I communication based on bilinear pairing. IEEE Trans Inf Forensics Secur. 2020;15(11):3493–504.
He J, Zhang Q, Wang J, Liu M. A secure and efficient authentication scheme for V2I communication based on blockchain and quantum password. IEEE Trans Ind Inform. 2022;18(11):7566–77.
Zhang Y, Wang X, Liu L, Han J. A lightweight and secure authentication scheme based on post-quantum cryptography for V2I communication. IEEE Access. 2022;10:57030–42.
Li S, Li F, Li Z, Jin H. A secure and privacy-preserving authentication scheme for V2I communication based on blockchain and lightweight attribute-based signature. IEEE Trans Veh Technol. 2022;71(8):8193–206.
Wang S, Hu Y, Hu W. A secure and efficient authentication scheme for V2I communication based on lightweight lattice-based cryptography. IEEE Trans Veh Technol. 2021;70(10):9991–10003.
Acknowledgement
The authors acknowledged the REVA University in Bengaluru, India and MINDA Corporation Limited, Bangalore, India for their valuable contributions to the research efforts through the provision of supportive facilities.
Author information
Authors and Affiliations
Contributions
This research endeavor was made possible by the collaboration and contributions of all authors.
Corresponding author
Ethics declarations
Conflict of interest
No conflict of interest.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article is part of the topical collection “Advances in Computational Approaches for Image Processing, Wireless Networks, Cloud Applications and Network Security” guest edited by P. Raviraj, Maode Ma and Roopashree H R.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Suresh, D., Joshi, P.V., Parandkar, P. et al. An Improved Authentication Scheme for V2I Communication. SN COMPUT. SCI. 5, 535 (2024). https://doi.org/10.1007/s42979-024-02865-7
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s42979-024-02865-7