Abstract
We study the complexity of the Distributed Constraint Satisfaction Problem (DCSP) on a synchronous, anonymous network from a theoretical standpoint. In this setting, variables and constraints are controlled by agents which communicate with each other by sending messages through fixed communication channels. Our results endorse the well-known fact from classical CSPs that the complexity of fixed-template computational problems depends on the template’s invariance under certain operations. Specifically, we show that DCSP(Γ) is polynomial-time tractable if and only if Γ is invariant under symmetric polymorphisms of all arities. Otherwise, there are no algorithms that solve DCSP(Γ) in finite time. We also show that the same condition holds for the search variant of DCSP. Collaterally, our results unveil a feature of the processes’ neighbourhood in a distributed network, its iterated degree, which plays a major role in the analysis. We explore this notion establishing a tight connection with the basic linear programming relaxation of a CSP.
Similar content being viewed by others
Avoid common mistakes on your manuscript.
1 Introduction
The Constraint Satisfaction Problem (CSP) consists of a collection of variables and a collection of constraints where each constraint specifies the valid combinations of values that can be taken simultaneously by the variables in its scope. The goal is to decide if there exists an assignment of the elements of a domain to the variables which satisfies all constraints. The CSP is a very rich mathematical framework that is widely used both as a fruitful paradigm for theoretical research, and as a powerful tool for applications in AI, such as scheduling and planning [19, 23].
While, in its full generality, the finite-domain CSP is known to be NP-complete, applying specific restrictions on the instances can yield tractable subclasses of the problem. One of the most studied approaches consists in requiring that, in each constraint, the set of allowed combinations for its values be drawn from a prescribed set Γ, usually called the constraint language or the template. Thanks to the proof of the CSP dichotomy conjecture obtained separately in [10] and [30], which culminated a decades-long research program, it is possible to determine the complexity (P or NP-complete) of each family of CSPs, CSP(Γ), which is obtained by fixing Γ. This proof confirmed that the complexity of the constraint satisfaction problem is deeply tied to certain algebraic properties of the constraint language. Specifically, it depends on whether or not the constraint language is invariant under certain operations known as its polymorphisms. The polymorphisms of a constraint language enforce a symmetry on the space of solutions of a CSP instance that can possibly be exploited by an algorithm. This connection with algebra is also present in our work.
We study the computational complexity of the distributed counterpart of CSP, which is known as DCSP. This was introduced by Yokoo et al. [27] as a formal framework for the study of cooperative distributed problem solving. In particular, we consider a deterministic, synchronous, anonymous network of agents controlling variables and constraints, and we study the complexity of message passing algorithms on this network. A number of practical applications can be encoded in the DCSP model, for instance resource allocation tasks in wireless networks, routing, networking, and mobile technologies (see for instance [7, 11]).
We notice that this framework is general enough to encompass some simple Graph Neural Network architectures (see for example [15, 22]). In particular, when training a GNN to classify graphs, it is customary that the GNN network ignores the node label when updating its feature vector. This is, in fact, essential as otherwise there would be no way to apply the network trained on a given graph to another one. However, whereas in all variants of GNNs the computation is limited to a reduced number of operations over feature vectors, in the DCSP model the computation at each node is governed by an arbitrary algorithm. GNNs have a wide range of applications including molecule classification or image classification (see [6] for example). Recently, GNNs have been deployed to solve CSPs [24].
While there are a variety of well-performing distributed algorithms for constraint satisfaction and optimisation (see for instance [12, 21, 29]), the theoretical aspects of distributed complexity are to date not well understood. In this paper we initiate the study of the complexity of DCSP parametrized by the constraint language, obtaining a complete characterization of its tractable classes. More specifically, building on the connection between the CSP and algebra, we show that for any finite constraint language Γ, the decision problem for DCSP(Γ) is tractable whenever Γ is invariant under symmetric polymorphisms of all arities, where an operation is symmetric if its result does not depend on the order of its arguments. Otherwise, there are no message passing algorithms that solve DCSP(Γ). Collaterally, we show that the same holds for the search problem for DCSP.
Our work begins with the identification of a feature of the nodes in a distributed network, its iterated degree, which plays a major role in how messages are transmitted in the network. The iterated degree is an extension of the similar concept introduced in the study of the isomorphism problem which turns out to have a variety of alternative characterizations in terms of fractional isomorphisms, the Weisfeiler-Leman test, and definability with counting logics (see [15]). It turns out that, due to the network anonymity, in every distributed algorithm all equivalent agents (with respect to iterated degree) must necessarily behave identically at each round. A similar phenomenon has been observed independently in the context of GNNs in [22, 25] leading to further study in [3].
We use this fact to show that, under the absence of symmetric polymorphisms of any arity in Γ, it is always possible to construct two instances of DCSP(Γ), one satisfiable and the other unsatisfiable, that cannot be distinguished by any message passing algorithm in an anonymous network.
On the other hand, invariance under symmetric polymorphisms is connected with the basic linear programming relaxation of a CSP instance. More precisely, if Γ has symmetric polymorphisms of all arities then one can decide the satisfiability of every instance of CSP(Γ) by checking whether its basic linear programming relaxation is feasible (see for instance [5]). Whereas it is not clear how to directly use this fact to obtain a distributed algorithm for DCSP(Γ), it can be applied to establish a structure theorem that unveils a simple yet surprising structure in the solution space of every satisfiable instance in DCSP(Γ): it must contain a solution that assigns the same value to all variables that have the same iterated degree. The proof of the structure theorem uses the weighted majority algorithm, a weight update method that is widely used in optimisation and machine learning applications (see [2]). The structure theorem is key in the proof of the positive results as it allows to run an adapted variant of the jpq-consistency algorithm [18] that overcomes the absence of unique identifiers for the variables, by using instead their iterated degree.
This paper is organised as follows. In Section 2 we introduce some definitions and technical concepts about the DCSP model. In Section 3 we present the basic LP relaxation for CSPs and we show its connection to the symmetry on the solution space, culminating in the statement of the structure theorem. Section 4 is dedicated to the proof of the dichotomy theorem for the complexity of DCSP, with the hardness results in Section 4.1, the details of the distributed algorithm for tractable languages in Section 4.2, and its extension to the search problem in Section 4.3. Finally, in the Conclusion we discuss some directions into which our work could be extended.
2 Preliminaries
Constraint Satisfaction Problems
An instance I of the finite-domain Constraint Satisfaction Problem (CSP) is a triple (X,D,C) where X is a set of variables, D is a finite set called the domain, and C is a set of constraints where a constraint c ∈ C is a pair (s,R) where \(R \subseteq D^{k}\) is a relation over D of positive integer arity k, and s is a tuple of k variables, known as the scope of c. We use arity(⋅) to denote the arity of a relation, tuple, or constraint and we write x ∈ c for any variable x in the scope of c. An assignmentν : X → D is said to be satisfying if for all constraints c = (s,R) ∈ C we have ν(s) ∈ R, where ν is applied to s coordinate-wise. Usually we denote the number of variables by n and the number of constraints by m.
Let Γ be a set of relations over some finite domain D, and let CSP(Γ) denote the set of CSP instances with all constraint relations lying in Γ. In this context, Γ is known as the constraint language. Throughout this paper, we will assume that Γ is always finite. Then, the decision problem for CSP(Γ) is the problem of deciding whether a satisfying assignment exists for an instance I ∈CSP(Γ). The search problem for CSP(Γ) is the problem of deciding whether a satisfying assignment exists and, if it does, to find one such assignment.
The Distributed Model
We consider the DCSP model of [27] with some small modifications. The basic idea is to assign the task of solving a constraint satisfaction problem to a multi-agent system. In the original model, which assumes that all constraints are binary [28, 29], the assumption is that each variable is controlled by an agent, and two agents can communicate with one another if and only if they share a constraint. Here we deviate slightly from the original model to allow for non-binary constraints and we assume that both variables and constraints are controlled by distributed agents in the network. An instance [12] of the Distributed Constraint Satisfaction Problem (DCSP) is a tuple (A,X,D,C,α), where X, D, and C are as in the classical CSP, A is a finite set of agents, and α : X ∪ C → A is a surjective function which assigns the control of each variable x ∈ X and each constraint c ∈ C to an agent α(x), α(c) respectively. For the purpose of this paper, we assume that there are exactly n + m agents, and therefore each agent controls exactly one variable or one constraint. Under this assumption, there is a one-to-one correspondence between instances of CSP and DCSP, and thus we shall switch freely between them, while maintaining the distinction between agents and their controlled variables and constraints for clarity when discussing distributed algorithms.
Distributed Networks and Message Passing
We now present some fundamental concepts relating to the message-passing paradigm for distributed networks. For a general introduction to distributed algorithms, we refer the reader to [13]. A distributed system consists of a finite set of agents or processes, which are connected through communication channels to form a network. Any process in the network can perform events of three kinds: send, receive and internal. Send and receive events are self-explanatory, as they denote the sending or receiving of a message over a communication channel. Any kind of local computation performed at the process level, as well as state changes and decisions, are classified as internal events.
We assume a fully synchronous communication model, meaning that the send event at a process a and the corresponding receive event at a process a′ can be considered de facto as a unique event, with no time delay. As a whole, a synchronous system proceeds in rounds, where at each round a process can perform some internal computation and then send messages to and receive messages from its neighbours. A round needs to terminate at every process before the next round begins. Note that while for simplicity we assume a synchronous network, all our algorithms can be adapted to asynchronous systems by applying a simple synchronizer. Nonetheless, we point out that our negative results rely on the network operating in synchronous rounds.
We make the fundamental assumption that the network is anonymous, meaning that variables, constraints and agents do not have IDs. For practical purposes, we still refer to variables and constraints with names (such as xi, ci), however these cannot be communicated through the channels. The assumption of anonymity can have various practical justifications: the processes may actually lack the hardware to have an ID, or they may be unable to reveal their ID due to security or privacy concerns. For instance, the basic architecture of GNNs is anonymous. This is a very desirable property as it allows to deploy GNNs in different networks than those in which they were trained.
We assume that all the processes run locally the same deterministic algorithm, therefore IDs cannot be created and deadlocks cannot be broken by for instance flipping a random coin. Hence, the lack of IDs makes the processes essentially indistinguishable from one another - except, as we will see later, for the structure of their neighbourhood in the network.
Leader election is a procedure by which the processes in a network select a single process to be the leader in a distributed way. If a leader is elected, then she can, for instance, dictate the output to the other processes. Moreover, all the information about the instance can be gathered to the leader, which if the network had unique IDs, would be sufficient to solve the CSP locally at the leader. It is a well-known result that there does not exist a terminating deterministic algorithm to elect a leader in an anonymous ring [1]. Therefore, the assumptions of anonymity and determinism ensure that the DCSP model is intrinsically different from the (centralised) CSP framework, and open up the way for establishing novel, non-trivial complexity results. We remark that while considerable effort has been put into characterizing under what conditions an anonymous network is able to elect a leader [8, 26] or compute relations [9], our work focuses on characterizing the complexity of the DCSP as parametrised by the constraint language. Therefore, all of our algorithms work regardless of the topology of the network, and hence regardless of whether or not a leader can be elected.
The encoding of a DCSP instance into the message passing framework is straightforward. The processes correspond to the agents of the network, and there is a labelled communication channel between a variable agent α(x) and a constraint agent α(c) if and only if x ∈ c. More formally, the Factor Graph [12] GI of an instance I = (X,D,C) of CSP is the undirected bipartite graph with vertex set X ∪ C and edge set {{x,c}∣x ∈ c}. Each edge in GI that is incident to a variable x and a constraint c where c = (s,R) has a label ℓ{x,c} = (S,R) for S = {i∣s[i] = x}, where for a tuple t, t[i] denotes the ith entry of t.Footnote 1 Then, the message passing network corresponds to the factor graph where every node (variable or constraint) is replaced by their associated agent and every edge by a communication channel of the same label. Note that between any two agents there is at most one channel. If privacy is a concern, we point out that labeling channels does not reveal any more information about the processes than what is strictly necessary for the problem instance to be well defined. It is easy to prove (see Appendix B) that in the case that all relations are binary, the original model where only variables are controlled by agents is equivalent to our model.
We say that I is connected if GI is connected in the standard graph-theoretic sense. Unless explicitly stated we only consider instances whose factor graph consists of a unique connected component.
At the start of an algorithm, a process only has access to very limited information. All processes know the total number n of variables in the CSP instance, the total number m of constraints, the labels of the communication channels that they are incident to in the network, and naturally whether they are controlling a variable or a constraint. During a run of the algorithm a process can acquire further knowledge from the messages that it receives from its neighbours. We assume that at any time each process is in one of a set of states, a subset of which are terminating states. When it enters a terminating state, a process performs no more send or internal events, and all receive events are disregarded. The local algorithm is then a deterministic function which determines the process’s next state, and the messages it will send to its neighbours. The output of such function only depends on the process’s current knowledge (including the messages it has received so far), and on its state. We allow processes to send different messages through different channels. However, since processes can only distinguish the channels based on their labels, identical messages must be sent through channels with identical labels. Note that the power of the model would not decrease if only one message was allowed to be passed through all the channels, since a process can simulate sending a separate message through each channel by tagging each message with the label of the desired channel and concatenating them in a unique string. This, however, comes at the cost of increased message size. Moreover, if a process needs to broadcast multiple messages, these can be concatenated into one. We say that an algorithm terminates when all processes are in a terminating state. For a precise formalisation of the definition of distributed algorithm, see Appendix A.
We say that a distributed algorithm solves an instance I of DCSP if the algorithm terminates and at termination every process correctly outputs that I is satisfiable if it is, and that it is not satisfiable otherwise. Moreover, we consider the search version of DCSP, denoted DCSP-Search. In the search version, if the input instance I is satisfiable, at termination every variable process α(x) must additionally specify a value ν(x) ∈ D such that ν : X → D is a satisfying assignment. For every constraint language Γ, we denote by DCSP(Γ) and DCSP-Search(Γ) the restrictions of DCSP and DCSP-Search, respectively, to instances containing only constraint relations from Γ.
In terms of algorithmic complexity, there are a number of measures that can be of interest. Time complexity, which is our primary concern, corresponds to the total amount of time required for the algorithm to terminate, including the time needed for internal events. This is closely related to the number of rounds of the algorithm, which is another measure that we are concerned with. Message complexity and bit complexity measure the total number of messages and bits exchanged respectively. These can be bounded easily from the maximum size of a message.
Iterated Degree and Degree Sequence
We present a number of concepts from graph theory that carry over to CSPs. Their adaptation to DCSPs is straightforward in all cases. In an undirected graph G, the degree of a vertex v is the number of edges incident at v. The zeroth iterated degree of v is equal to its degree. For k ≥ 1, the kth iterated degree of v is the multiset of (k − 1)th degrees of v’s neighbours in G. The kth iterated degree sequence of a graph is the multiset of kth iterated degrees of its vertices.
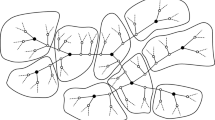
Example 1
In the context of graph theory the colour refinement algorithm, which calculates the iterated degree sequence of a graph, is often used as a simple heuristic for the graph isomorphism problem. If two graphs are isomorphic then they must have the same iterated degree sequence, but the opposite is not true (see for example Fig. 1).
We extend the notion of iterated degree to CSPs as follows. Consider the labelled factor graph GI of an instance I described in the previous paragraph. In what follows it will be convenient to allow instances I with a disconnected factor graph GI. Let v be a node of GI and denote its neighbourhood in the factor graph by N(v). The (zeroth) degree, denoted δ0(v), of a node in the factor graph is simply a symbol that distinguishes variables from constraints: we set δ0(x) = ‘●’ for all x ∈ X and \(\delta _{0}(c)=\text {`}\blacktriangle \text {'}\) for all c ∈ C. The kth iterated degreeFootnote 2 (k ≥ 1) of a node v is defined as δk(v) = {{(ℓ{v,w},δk− 1(w))∣w ∈ N(v)}}, where the notation {{…}} stands for multiset. We write \(v \sim ^{k}_{\delta } v^{\prime }\) if \(\delta _{k}(v)=\delta _{k}(v^{\prime })\), and simply \(v \sim _{\delta } v^{\prime }\) if \(v \sim ^{k}_{\delta } v^{\prime }\) for all k ≥ 0. In this case, we say that v and \(v^{\prime }\) are iterated degree equivalent. It can be shown (see the following proposition) that as k increases, the partition induced by \(\sim _{\delta }^{k}\) gets more refined, and indeed it reaches a fixed point for some k ≤ 2n where n = |X|.
Proposition 1
Let I = (A,X,D,C,α) be an instance of DCSP(Γ) and let \(v,v^{\prime } \in X \cup C\). Let k ≥ 2n where n = |X|. Then, \(v \sim _{\delta }^{k} v^{\prime }\) implies \(v \sim _{\delta } v^{\prime }\).
Proof
We start by showing that for all non-negative integers \(k,k^{\prime }\) with \(k \leq k^{\prime }\), the partition induced by \(\sim _{\delta }^{k^{\prime }}\) on X ∪ C is at least as refined as the partition induced by \(\sim _{\delta }^{k}\). The proof goes by induction. Let \(v,v^{\prime }\) be arbitrary nodes in GI. Clearly if \(\delta _{0}(v) \neq \delta _{0}(v^{\prime })\), then \(\delta _{k}(v) \neq \delta _{k}(v^{\prime })\) for all \(k \in \mathbb {N}\), so in particular \(\delta _{1}(v) \neq \delta _{1}(v^{\prime })\). Now assume that for all \(v,v^{\prime } \in X \cup C\), \(\delta _{k}(v) = \delta _{k}(v^{\prime })\) implies \(\delta _{k-1}(v) = \delta _{k-1}(v^{\prime })\). Then it is a clear consequence of the definition of δk that \(\delta _{k+1}(v) = \delta _{k+1}(v^{\prime }) \implies \delta _{k}(v) = \delta _{k}(v^{\prime })\) for all \(v,v^{\prime } \in X \cup C\) too as required.
Now it remains to show that if \(v \sim _{\delta }^{2n} v^{\prime }\), then \(v \sim _{\delta }^{k} v^{\prime }\) for all k ≥ 2n. The result is immediate if we replace 2n by n + m. To achieve 2n we use the fact that the factor graph is bipartite. Denote by Pk and Qk the partitions induced by \(\sim _{\delta }^{k}\) on X and C respectively and note that if Pk− 2 = Pk then (Pk,Qk) is a fixed point. We notice that Pk− 2 = Pk must occur for some k ≤ 2n and we are done. □
The notion of iterated degree is strikingly relevant in our work as it captures what it means for two processes in a network to be indistinguishable. This implies that no distributed algorithm can differentiate between two iterated degree equivalent nodes, as we illustrate in the following result.
Proposition 2
Let I = (A,X,D,C,α) be an instance of DCSP(Γ) whose factor graph is not necessarily connected and consider two nodes \(v,v^{\prime }\) in GI. Then, \(v \sim _{\delta } v^{\prime }\) if and only if any terminating decision algorithm over I outputs the same decision at α(v) and \(\alpha (v^{\prime })\). Furthermore, if \(v,v^{\prime }\in X\) and I is satisfiable, then any terminating search algorithm outputs the same values \(\nu (v) = \nu (v^{\prime })\) at α(v) and \(\alpha (v^{\prime })\).
Proof
(⇒). At the beginning of the algorithm, all processes are in the same state. Let v be a node in the factor graph of I, and denote by \({s_{t}^{v}}\) the message broadcast at time t by α(v) to its neighbours. For any two nodes v, \(v^{\prime }\), \(\delta _{1}(v) = \delta _{1}(v^{\prime })\) is equivalent to v and \(v^{\prime }\) having the same initial knowledge – that is, v and \(v^{\prime }\) are either both variables or both constraints and their adjacent channels have the same multiset of labels. This means that the first internal and send events are the same at α(v) and at \(\alpha (v^{\prime })\), hence \({s_{1}^{v}}=s_{1}^{v^{\prime }}\). Then, it is easy to see by induction that \(\delta _{t}(v)= \delta _{t}(v^{\prime }) \implies {s_{t}^{v}}=s_{t}^{v^{\prime }}\), which in turn implies that
This implies that at any time t, α(v) and \(\alpha (v^{\prime })\) send and receive the same messages, so they have the same knowledge and hence the internal events at α(v) and \(\alpha (v^{\prime })\) are the same at all time. In particular, if the algorithm terminates, then the terminating state is the same at α(v) and \(\alpha (v^{\prime })\), and therefore the decision and, in case of search, the value of ν at α(v) and \(\alpha (v^{\prime })\) are the same.
(⇐). Consider the algorithm that calculates the iterated degree at each node (we detail the procedure in the proof of Theorem 15). If \(v \not \sim _{\delta } v^{\prime }\), then we can find an algorithm that on the basis of the iterated degree gives different outputs at α(v) and \(\alpha (v^{\prime })\). □
Example 2
Let \({\Gamma }=\{\neq _{\mathbb {B}}\}\) where \(\neq _{\mathbb {B}}\) is the inequality relation on the Boolean domain \(\mathbb {B}=\{0,1\}\), that is, \(\neq _{\mathbb {B}} \ = \{(0,1),(1,0)\}\). Let I be an instance of DCSP(Γ) with variables {x1,…,xn} and constraints \(((x_{1},x_{2}),\neq _{\mathbb {B}}), ((x_{2},x_{3}),\neq _{\mathbb {B}}), \ldots , ((x_{n},x_{1}),\neq _{\mathbb {B}})\). That is, I can be seen as a directed ring. If n is even, then clearly I is satisfiable. Therefore, if there was a distributed algorithm that solved the search version of DCSP(Γ), any two agents controlling two consecutive variables xi, xi+ 1 should output at termination a partial assignment ν for their controlled variable such that ν(xi)≠ν(xi+ 1). But it is easy to see that all variable agents in I have the same iterated degree, and so by Proposition 2, such an algorithm cannot exist.
The following is a direct consequence of Proposition 2. We say that two instances I and \(I^{\prime }\) have the same iterated degree sequence if there exists a bijection γ between the nodes of GI and the nodes of \(G_{I^{\prime }}\) such that for every k ≥ 0 and every node v of GI, the kth degree of v in I is equal to the kth degree of γ(v) in \(I^{\prime }\). We note that in this case, if we construct the (disconnected) instance \(I\cup I^{\prime }\) containing all the variables and constraints in I and \(I^{\prime }\), then \(v\sim _{\delta } \gamma (v)\) for every node v of GI. Hence the result below follows.
Corollary 3
Let \(I,I^{\prime } \in \text {DCSP}({\Gamma })\) have the same iterated degree sequence. Then with both inputs any terminating decision algorithm will report the same decision.
Example 3
Let \({\Gamma }=\{\neq _{\mathbb {B}}\}\) be as in Example 2 and consider the two instances pictured in Fig. 1 (where nodes represent variables and edges represent constraints). By Corollary 3, any terminating decision algorithm will report the same decision on both instances. However, one of the instances is satisfiable and the other is not, so there cannot be a distributed algorithm that solves DCSP(Γ).
Polymorphisms
Let R be a k-ary relation over a finite domain D. An ℓ-ary polymorphism of R is an operation f : Dℓ → D such that the coordinate-wise application of f to any set of ℓ tuples from R gives a tuple in R. More precisely, for any t1,…,tℓ ∈ R, we have that (f(t1[1],…,tℓ[1]),…,f(t1[k],…,tℓ[k])) ∈ R. We say that a function f is a polymorphism of a constraint language Γ if f is a polymorphism of all relations R ∈Γ. Equivalently, we say that Γ is invariant under f. The set of polymorphisms of a constraint language Γ will be denoted by Pol(Γ). There is a particular construction of a CSP instance that is closely related to the clone of polymorphisms of the corresponding constraint language. Let Γ be a constraint language over a finite domain D. For any positive integer r, the indicator problem of order r for Γ is the instance I = (X,D,C) ∈CSP(Γ) where X = Dr and C contains for every relation R ∈Γ and for every \(\mathbf {t}_{1},\dots ,\mathbf {t}_{r}\in R\), the constraint (s,R) where \(\mathbf {s}[i]=(\mathbf {t}_{1}[i],\dots ,\mathbf {t}_{r}[i])\) for every \(i\in \{1,\dots ,arity(R)\}\). It follows easily that for every \(\nu :D^{r}\rightarrow D\), ν satisfies I if and only if ν is a polymorphism of Γ.
An ℓ-ary operation f is said to be symmetric if for all x1,…,xℓ and for all permutations σ of \(\{1,\dots ,\ell \}\) we have that f(x1,…,xℓ) = f(xσ(1),…,xσ(ℓ)).
Example 4
Once again let \(\neq _{\mathbb {B}}\) be as in Example 2. It is easy to see that the ternary minority operation f given by f(x,y,z) = x ⊕ y ⊕ z is a polymorphism of \(\neq _{\mathbb {B}}\). On the other hand, one can show that \(\neq _{\mathbb {B}}\) does not have symmetric polymorphisms of arity 2. In particular, let t1 = (0,1) and t2 = (1,0). Since a symmetric binary operation f needs to satisfy f(0,1) = f(1,0), the coordinate-wise application of f to t1,t2 would yield a reflexive tuple, which cannot possibly belong to \(\neq _{\mathbb {B}}\).
Our work unveils a novel structure in the space of solutions of a CSP instance that is deeply connected to the symmetry of its polymorphisms. In particular, Pol(Γ) containing symmetric polymorphisms of all arities is equivalent to the existence of a satisfying assignment to every satisfiable instance of CSP(Γ) that preserves the partition induced by \(\sim _{\delta }\). This is the main result of Section 3.
pp and efpp definability
We conclude this section by presenting a notion of definability for relations that is closely associated to polymorphisms. A relation \(R \subseteq D^{k}\) is said to be primitive positive definable, most commonly shortened to pp-definable, from a constraint language Γ over the same domain D if there exists a pair \(((x_{1},\dots ,x_{k}),I)\) with I = (X,D,C) an instance of CSP(Γ ∪{eqD}) where eqD = {(d,d)∣d ∈ D} is the equality relation, and \(x_{1},\dots ,x_{k}\) are distinct variables in X such that for every tuple t ∈ Dk
A constraint language \({\Gamma }^{\prime }\) is pp-definable from Γ if all the relations in \({\Gamma }^{\prime }\) can be pp-defined from Γ. The following complexity reduction between CSP classes is well known.
Theorem 4 (see 4)
Let Γ, \({\Gamma }^{\prime }\) be finite constraint languages. If Γ pp-defines \({\Gamma }^{\prime }\), then \(\text {CSP}({\Gamma }^{\prime })\) is log-space reducible to CSP(Γ).
However, in the distributed setting, allowing equality introduces a few technical difficulties. Fortunately, this obstacle could be overcome by considering a more restricted notion of pp-definability which, following [17], we shall call efpp-definability, where equality is not allowed. More precisely, we shall say that a relation R is equality-free primitive positive definable (efpp-definable, for short) from Γ if it is pp-definable and, in addition, the instance I witnessing the pp-definition belongs to CSP(Γ). That is, we are not allowed to use the equality relation in the instance, unless, of course, it belongs already to Γ. Then, we have:
Proposition 5
Let Γ, \({\Gamma }^{\prime }\) be finite constraint languages, and assume that \({\Gamma }^{\prime }\) is efpp-definable from Γ. If DCSP(Γ) is solvable in polynomial time (resp. finite time) then so is \(\text {DCSP}({\Gamma }^{\prime })\).
Proof
Given an algorithm Alg that solves DCSP(Γ) we can design a new algorithm \(\operatorname {Alg}^{\prime }\) for \(\text {DCSP}({\Gamma }^{\prime })\) that given an instance \(I^{\prime }=(A^{\prime },X^{\prime },D,C^{\prime },\alpha ^{\prime })\) of \(\text {DCSP}({\Gamma }^{\prime })\) simulates the execution of Alg with the instance I = (A,X,D,C,α) of DCSP(Γ) defined as follows. For every constraint \(c=((s_{1},\dots ,s_{k}),R)\) in \(C^{\prime }\), consider the pair \(((x_{1},\dots ,x_{k}),I_{R})\) defining R over Γ and replace constraint c by the instance Ic (meaning all its variables and constraints) obtained from IR by renaming the variables so that xi = si for every 1 ≤ i ≤ k and the rest of variables in Ic are fresh. Note that IR (and hence Ic) does not contain equalities. Then α is defined such that it agrees with \(\alpha ^{\prime }\) over \(X^{\prime }\) and, as usual, every variable and constraint in I is controlled by a different agent.
The simulation is as follows. At each round, for every \(x\in X^{\prime }\), \(\alpha ^{\prime }(x)\) simulates the execution of α(x) as in Alg, and for every \(c\in C^{\prime }\), \(\alpha ^{\prime }(c)\) simulates the execution of all constraints and fresh variables in Ic. We note that no new communication channels need to be created as this simulation is done internally by \(\alpha ^{\prime }(c)\). The transmission of messages can be also easily simulated for every pair of neighbours α(x) and α(c) in I. In fact, if \(x\not \in X^{\prime }\), then both α(x) and α(c) are simulated by the same agent \(\alpha ^{\prime }(c)\) in \(I^{\prime }\) (and, hence, no communication is required). Otherwise, if \(x\in X^{\prime }\), α(x) is simulated by \(\alpha ^{\prime }(x)\) and α(c) is simulated by some neighbour \(\alpha ^{\prime }(c^{\prime })\) of α(x). □
Remark 6
We note here that for every r ≥ 1, the indicator problem of order r for Γ constitutes an efpp-definition of the |D|r-ary relation U encoding the set of all polymorphisms of arity r. It then follows from Proposition 5 that if DCSP(Γ) is solvable in finite time then so is DCSP({U}).
3 Basic Linear Programming Relaxation
For any CSP instance I = (X,D,C) there is a LP relaxation (usually called basic LP relaxation, see for example [20]) denoted BLP(I), which is defined as follows. It has a variable v(x,d) for each x ∈ X and d ∈ D, and a variable v(c,t) for each c ∈ C and t ∈ R where R is the constraint relation of c. All variables must take values in the range [0,1]. The value of v(x,d) is interpreted as the probability that v is assigned to d. Similarly, the value of v(c,t) is interpreted as the probability that the scope of c is assigned component-wise to the tuple t. In this paper we only deal with a feasibility problem (that is, there is no objective function). The variables are restricted by the following equations:
where we denote the relation and scope of a constraint c by Rc and sc respectively. We say that BLP decides CSP(Γ) if for every instance I ∈CSP(Γ), I is satisfiable whenever BLP(I) is feasible. We will use the following well-known result.
Theorem 7 (see [20])
If Γ has symmetric polymorphisms of all arities, then BLP decides CSP(Γ). Moreover, if I ∈CSP(Γ) is satisfiable then it has a solution ν such that for all \(x,x^{\prime }\) with \(v(x,d) = v(x^{\prime },d)\) for all d ∈ D, we have \(\nu (x)=\nu (x^{\prime })\).
Proof
It is clear that if there is no feasible solution to BLP(I), then I is not satisfiable, regardless of the polymorphisms of Γ. So let Γ be such that Pol(Γ) contains symmetric polymorphisms of all arities and let I be an instance of CSP(Γ) such that BLP(I) is feasible. We can assume that there exists some natural number n such that in the feasible solution to BLP(I), all variables take rational values of the form \(\frac {r}{n}\) for some integer r. That is, for all x ∈ X, d ∈ D, c ∈ C and t ∈ Rc (where Rc is the relation of c) there exist corresponding integers such that
Let f be a symmetric polymorphism of Γ of arity n. For every x ∈ X we shall denote by fx the value of f when applied to an n-tuple where each d ∈ D appears exactly r(x,d) times. We claim that the assignment ν : X → D given by ν(x) = fx satisfies I. To see this, consider an arbitrary constraint c = (s,R). Denote by \(\mathbf {t}^{\prime }\) the tuple obtained by applying f coordinate-wise to n tuples t1,…,tn chosen as follows: each tuple t ∈ R is chosen exactly r(c,t) times. Clearly \(\mathbf {t}^{\prime } \in R\) since f is a polymorphism of R. So, to show that c is satisfied by ν, it is enough to show that \(\nu (\mathbf {s}[i]) = \mathbf {t}^{\prime }[i]\). Now, \(\mathbf {t}^{\prime }[i]\) is the result of applying f to the set of the ith elements of t1,…,tn. But any d ∈ D occurs in t1[i],…,tn[i] exactly \({\sum }_{\mathbf {t}[i]=d} r(c,\mathbf {t}) = n \cdot v(\mathbf {s}[i],d) = r(\mathbf {s}[i],d)\) times, and so, given that f is symmetric, we have
as required. □
The following theorem reveals a useful structure inside the solutions of the BLP.
Theorem 8
Let I = (X,D,C) be an instance of CSP(Γ) such that BLP(I) is feasible. Then, BLP(I) has a feasible solution such that for every \(x,x^{\prime }\in X\) with \(x\sim _{\delta } x^{\prime }\) and every d ∈ D, \(v(x,d)=v(x^{\prime },d)\).
Proof
We start by rewriting the program in the form
by replacing every equality a = b by the inequalities a ≥ b and − a ≥−b.
It will be convenient to index the rows and columns of B not using positive integers. Let us start with the columns. Each column is associated to a variable of BLP(I), i.e, a variable of the form v(x,d), x ∈ X,d ∈ D or v(c,t),c ∈ C,t ∈ Rc. In the first case, we index the corresponding column with the pair (x,d) whereas in the second case we index it with the pair (c,t), and we denote by V the set of all such indices.
Now, let us turn our attention to the rows. Every equation in (1) gives rise to two rows that we shall index with (x,+) and (x,−). Similarly, every equation in (2) also gives rise to two rows that we shall index with (c,i,d,+) and (c,i,d,−). Let us denote by W the set of all indexes for rows.
We shall see later how to define an oracle which, given a probability W-vector p (i.e, a vector p with non-negative entries such that the sum of all its entries is 1), outputs a vector v which is a solution to the weaker problem
if one exists, or correctly states that no such vectors exist otherwise. Note that if a solution exists to (3), then it is necessarily also a solution to (4), while the opposite is not true in general.
For every w ∈ W, let us denote by Bw the row corresponding to w. If w = (x,+) then, since the vector returned by the oracle satisfies v ∈ [0,1]V it follows easily that Bwv −b[w] ∈ [− 1,|D|]. Similarly, if w = (c,i,d,+) then \(B_{w}\mathbf {v}-\mathbf {b}[w]\in [-1,\max \limits _{R \in {\Gamma }}|R|]\). It follows that by setting ℓ = 1 and \(\rho =\max \limits \{|D|,\max \limits _{R \in {\Gamma }}|R|\}\) any such oracle-given vector v satisfies the following condition: there is a fixed subset \(J \subseteq W\) (consisting precisely of the positive rows) such that
□
Such an oracle is known as a (ℓ,ρ)-bounded oracle. Then we have:
Theorem 9 (2)
Let ε > 0 be an arbitrary error parameter. Suppose that there exists an (ℓ,ρ)-bounded oracle for the feasibility problem (4). Assume that \(\ell \geq \frac {\varepsilon }{2}\). Then there exists an algorithm which either finds v such that Bv ≥b − ε whenever such v exists, or correctly concludes that no such v exists otherwise. Such algorithm makes \(\mathcal {O}(\ell \rho \log (|W|) / \varepsilon ^{2})\) calls to the oracle.
The algorithm that Theorem 9 refers to is Multiplicative Weight Update (MWU), a well-known technique that is widely used in optimisation and machine learning. MWU was discovered independently by researchers of different communities; for a survey of its different variants we refer the reader to [2]. The version that is relevant to our paper is described in Algorithm 1. Recall that the algorithm assumes that there is a feasible solution.

We shall see that if we choose the oracle O wisely then for every \(x, x^{\prime } \in X\) with \(x \sim _{\delta } x^{\prime }\) and every d ∈ D, the solution returned by the MWU algorithm assigns the same value to v(x,d) and \(v(x^{\prime },d)\).
To see this we need some more notation. We note that \(\sim _{\delta }\) induces in a natural way an equivalence relation \(\sim _{V}\) on V. In particular, we have that \(v,v^{\prime }\in V\) are \(\sim _{V}\)-related if v = (x,d) and \(v^{\prime }=(x^{\prime },d)\) where \(x\sim _{\delta } x^{\prime }\) and d ∈ D, or v = (c,t) and \(v^{\prime }=(c^{\prime },\mathbf {t})\) where \(c\sim _{\delta } c^{\prime }\) and t ∈ Rc (note that, necessarily, \(R_{c}=R_{c^{\prime }}\)). Similarly \(\sim _{\delta }\) induces an equivalence relation, denoted \(\sim _{W}\), on W. More specifically, we have that \(w,w^{\prime }\in W\) are \(\sim _{W}\)-related if w = (x,s) and \(w^{\prime }=(x^{\prime },s)\) where \(x\sim _{\delta } x^{\prime }\) and s ∈{+,−} or w = (c,i,d,s) and \(w^{\prime }=(c^{\prime },i,d,s)\) where \(c\sim _{\delta } c^{\prime }\), \(i\in \{1,\dots ,arity(c)\}\), d ∈ D, and s ∈{+,−}.
Now, we say that a V -vector v is \(\sim _{V}\)-preserving if \(\mathbf {v}[v]=\mathbf {v}[v^{\prime }]\) whenever \(v\sim _{V} v^{\prime }\) and we similarly define \(\sim _{W}\)-preserving W -vectors. So it is enough to show that there exists some oracle O that guarantees that at each iteration t of the WMU algorithm, v(t) is \(\sim _{V}\)-preserving. To this end we need the following easy properties.
Claim 1
For all \(\sim _{V}\)-preserving V-vectors v and for all \(\sim _{W}\)-preserving W-vectors w, we have that
-
1.
Bv is \(\sim _{W}\)-preserving;
-
2.
wTB is \(\sim _{V}\)-preserving.
Proof Proof of Claim
1. We include only the proof of (2) as the proof of (1) is analogous and, indeed, simpler. Let v := wTB. An easy computation shows that
where we write Cx to denote the set of all constraints in C where x appears in the scope, and
It is immediate to see that, if w is \(\sim _{W}\)-preserving, then \(\mathbf {v}(c,\mathbf {t})=\mathbf {v}(c^{\prime },\mathbf {t})\) whenever \(c\sim _{\delta } c^{\prime }\). Let us show that \(\mathbf {v}(x,d)=\mathbf {v}(x^{\prime },d)\) whenever \(x\sim _{\delta } x^{\prime }\). Since w is \(\sim _{W}\)-preserving we have that \(\mathbf {w}(x,s)=\mathbf {w}(x^{\prime },s)\) for s ∈{+,−} and hence we only need to show that \(\varphi _{x}(C_{x})=\varphi _{x^{\prime }}(C_{x^{\prime }})\) where φx(Cx) is a shorthand for
and \(\varphi _{x^{\prime }}(C_{x^{\prime }})\) is defined analogously.
Now, for every R ∈Γ, every \(S \subseteq \{1,\dots ,arity(R)\}\), and every class [c] of equivalent constraints, let Cx,R,S,[c] be the set of constraints in Cx that belong to [c], whose constraint relation is R, and whose scope s satisfies the following: (i ∈ S) ⇔s[i] = x for every \(i\in \{1,\dots ,arity(R)\}\). Note that since Cx and \(C_{x^{\prime }}\) can be partitioned as the union of sets of this form it is only necessary to show that \(\varphi _{x}(C_{x,R,S,[c]})=\varphi _{x^{\prime }}(C_{x^{\prime },R,S,[c]})\) for every choice of R, S, and [c]. To see this it is enough to note that \(|C_{x,R,S,[c]}|=|C_{x^{\prime },R,S,[c]}|\) (because \(x\sim _{\delta } x^{\prime }\)) and that, since w is \(\sim _{W}\)-preserving, for every constraint \(c^{\prime }\in [c]\) and every choice of d, i, and s, we have \(\mathbf {w}(c^{\prime },i,d,s)=\mathbf {w}(c,i,d,s)\). □
Proof
Now, consider the oracle O that, given a W-vector p, returns the V-vector v defined as v[v] = 1 if pTB[v] is positive and v[v] = 0 otherwise. Since v maximizes pTBv under the restriction v ∈ [0,1]V it follows that v satisfies (4). Furthermore, it is easy to see that if p is \(\sim _{W}\)-preserving then v is \(\sim _{V}\)-preserving.
Now, note that by definition both w(1) - which is an all-ones W-vector - and b are \(\sim _{W}\)-preserving. It follows easily by induction that for each t, v(t) is \(\sim _{V}\)-preserving and w(t) is \(\sim _{W}\)-preserving. Hence, if we call algorithm WMU iteratively with \(T\rightarrow \infty \) we obtain in the limit a feasible solution satisfying the conditions of the statement. We note here that, although we have not included explicitly any inequalities requiring that all the variables in BLP(I) take values in the range [0,1], this is guaranteed by the fact that all the entries of the vector returned by O are in the range [0,1]. This concludes the proof of Theorem 8. □
We finalize the section by presenting the theorem on the structure of the solution space of CSP instances.
Theorem 10
Let Γ be a finite constraint language. The following are equivalent:
-
1.
Γ has symmetric polymorphisms of all arities.
-
2.
For all satisfiable instances I = (X,D,C) ∈CSP(Γ) there exists a satisfying assignment ν : X → D such that for all pairs of variables \(x,x^{\prime } \in X\), if \(x \sim _{\delta } x^{\prime }\) then \(\nu (x)=\nu (x^{\prime })\).
Proof
(1)⇒ (2). Let I be a satisfiable instance of CSP(Γ), where Γ has symmetric polymorphisms of all arities. Consider the solution of BLP(I) given by Theorem 8 and note that it satisfies \(v(x,d)=v(x^{\prime },d)\) for all \(x \sim _{\delta } x^{\prime }\) and all d ∈ D. Then, by Theorem 7, I has a solution ν which satisfies \(\nu (x)=\nu (x^{\prime })\) for all \(x \sim _{\delta } x^{\prime }\).
(2)⇒ (1). Let Γ satisfy (2) and let r ≥ 1. We shall prove that Γ has a symmetric polymorphism of arity r. Let I = (X,D,C) be the indicator problem of order r. Recall that every solution to I corresponds to an r-ary polymorphism of Γ, and hence the indicator problem is always satisfiable since for instance the projection to the first coordinate is a polymorphism of Γ. Let ν be a solution of the indicator problem which satisfies condition (2). It is easy to show by induction that for every tuple \((t_{1}.\dots ,t_{r})\in D^{r}\), every permutation σ of \(\{1,\dots ,r\}\) and every k ≥ 0, \((t_{1},\dots ,t_{r})\sim _{\delta }^{k} (t_{\sigma (1)},\dots ,t_{\sigma (r)})\) which implies that \(\nu (t_{1},\dots ,t_{r})=\nu (t_{\sigma (1)},\dots ,t_{\sigma (r)})\). We conclude that ν is symmetric as required. □
4 The Complexity of DCSP
The primary goal of this section is to prove the main theorem of this paper, namely, the dichotomy theorem for tractability of DCSP(Γ), which we now state.
Theorem 11
DCSP(Γ) is solvable in polynomial time if and only if Pol(Γ) contains symmetric polymorphisms of all arities. Otherwise, DCSP(Γ) cannot be solved in finite time.
We show hardness of constraint languages that do not have symmetric polymorphisms of all arities in Section 4.1 and tractability of the remaining languages in Section 4.2. In addition, in Section 4.3 we extend the decision algorithm so that, additionally, it also provides a solution to the search problem. Hence we have:
Theorem 12
DCSP-Search(Γ) is solvable in polynomial time if and only if Pol(Γ) contains symmetric polymorphisms of all arities. Otherwise, DCSP-Search(Γ) cannot be solved in finite time.
4.1 Intractable Languages
In this section we focus on intractable languages, that is, the hardness part of Theorem 11.
Theorem 13
Let Γ be a constraint language on a finite domain D. If Pol(Γ) does not contain symmetric operations of all arities, then there is no algorithm that solves DCSP(Γ) in finite time.
Schematically, the proof goes as follows. Assume that Γ does not have symmetric polymorphisms of some arity r. Consider the relation U defined by the set of solutions of the indicator problem of order r. It can be shown that if DCSP(Γ) is solvable in polynomial (or finite) time then so is DCSP({U}). Then, we show that there always exist two connected instances of DCSP({U}), of which one is satisfiable and the other one is not, that have the same iterated degree sequence. Therefore, any algorithm will return the same output on both instances, meaning that one of these outputs is wrong. Before embarking on the proof we state the following useful combinatorial lemma.
Lemma 14
Let 0 < k < d be positive integers. If n is a large enough multiple of k, then there exists a collection \(\mathbb {S}\) of nk k-element subsets of \(\{0,1,\dots ,kn-1\}\) satisfying the following properties:
-
(a)
\(\mathbb {S}\) contains every k-element subset of \(\{0,\dots ,d-1\}\)
-
(b)
Every element of \(\{0,1,\dots ,kn-1\}\) appears in the same number of sets of \(\mathbb {S}\).
-
(c)
If k ≥ 2, the k-uniform hypergraph with vertex set given by \(\{0,1,\dots ,kn-1\}\) and edge set given by \(\mathbb {S}\) is connected.
Proof
If k = 1 we can just define \(\mathbb {S}\) to be the set containing all singletons in \(\{0,1,\dots ,kn-1\}\) so we can assume that k ≥ 2. Pick some n that is a multiple of k and consider the subsets of \({\{0,1,\dots ,kn-1\}}\). We say that one such set is bad if S = S + i mod kn for some i≠ 0, and good otherwise where the right-hand side of the equation is a shorthand for the set {s + i mod kn∣s ∈ S}. The following facts hold. □
Claim 2
If \(n>\frac {2(d-1)}{k}\), then all subsets of \(\{0,\dots ,d-1\}\) are good.
Proof Proof of Claim
2. Let \(S \subseteq \{0,\dots ,d-1\}\) and assume that S is bad. Then, there exists i such that S = S + i mod kn. Denote by sm the smallest element of S. Then, we need sm + i ∈ S, which implies that i ≤ d − 1. On the other hand, kn + sm = x + i for some x ∈ S, implying that kn + sm ≤ 2(d − 1) < kn, a contradiction. □
Claim 3
There are at least nk good sets.
Proof Proof of Claim
3. Let S be a bad set and let 0 < i < kn be minimal such that S = S + i. We note that S is fully determined by S ∩ [0,i − 1] and i. Now, we observe that since 0 < i, it follows that |S ∩ [0,i − 1]|≤ k/2 and, hence, there are at most ik/2 ≤ (kn)k/2 choices for S ∩ [0,i − 1]. If s ∈ S and S is bad it follows that s + j ⋅ i mod kn ∈ S for every integer j. Since S has k elements it follows that i ⋅ j = kn for some j ≤ k. Hence, we have at most k choices for i. Hence, in total we have at most O(nk/2) bad sets. This implies that there are at least \(\binom {kn}{k}-O(n^{k/2})\) good sets, which is at least nk for n large enough.
Therefore, consider the collection of good k-element subsets of \(\{0,1,\dots ,kn-1\}\). We say that two sets S, \(S^{\prime }\) are related if \(S=S^{\prime }+i \mod {kn}\) for some i≠ 0. Note that, since we are only considering good sets, every class of related sets has exactly kn members and, hence, there are at least nk/kn many classes. Also it is immediate that every class of related sets satisfies condition (b).
Hence, to construct \(\mathbb {S}\) we just need to remove some of the classes of good sets so that we end up having exactly nk/kn classes, which corresponds to nk sets. We have to keep all the classes containing one of the sets of condition (b), which is always possible if we pick n large enough so that \(\binom {d}{k} \leq n^{k}\).
It only remains to show that the hypergraph with vertex set \(\{0,1,\dots ,kn-1\}\) and edge set \(\mathbb {S}\) is connected. To do this it is sufficient to show that each \(i \in \{0,1,\dots ,kn-1\}\) is connected to, say, vertex 0 by a walk. This is immediate to see as, for instance, \(S_{0}=\{0,1,\ldots ,k-1\} \in \mathbb {S}\) (because \(S_{0} \subseteq \{0,1,\dots ,d-1\}\)) and therefore \(S_{i} :=S_{0} +i \in \mathbb {S}\) for all \(i \in \{0,1,\dots ,kn-1\}\), hence, the sets S0,S1,…,Si−k+ 1 witness that 0 and i are connected. □
Proof Proof of Theorem 13
Assume that Pol(Γ) does not contain symmetric polymorphisms of arity r ≥ 2. Fix any arbitrary order \(\mathbf {t}_{1}, \ldots , \mathbf {t}_{|D|^{r}}\) on the tuples of Dr and consider the relation U defined as
This is, U is the set of solutions of the indicator problem of order r. Given that U is efpp-definable from Γ, it follows from Proposition 5 and Remark 6 that if DCSP({U}) is not solvable in finite time then neither is DCSP(Γ).
Partition Dr into equivalence classes where two tuples \(\mathbf {t},\mathbf {t}^{\prime }\in D^{r}\) are related, denoted \(\mathbf {t}\equiv \mathbf {t}^{\prime }\), if there exists some permutation σ on {1,…,r} such that \(\mathbf {t}^{\prime }[i]=\mathbf {t}[\sigma (i)]\) for every i ∈{1,…,r}. We shall use \(D^{r}_{\equiv }\) to refer to the collection of classes and [t]≡ to refer to the class of tuple t. For every t ∈ Dr, define \(k_{[\mathbf {t}]_{\equiv }}\) to be the number of tuples in [t]≡. Then we can choose an integer n large enough such that for every t ∈ Dr, n is a multiple of \(k_{[\mathbf {t}]_{\equiv }}\), and n satisfies Lemma 14 for \(k=k_{[\mathbf {t}]_{\equiv }}\) and \(d=k_{[\mathbf {t}]_{\equiv }} \cdot |D|\). Notice that since Pol(Γ) does not contain symmetric polymorphisms of all arities, we must have that |D|≥ 2, and hence there is some \([\mathbf {t}]_{\equiv } \in D^{r}_{\equiv }\) such that \(k_{[\mathbf {t}]_{\equiv }}\geq 2\).
We are now ready to construct two instances I1 and I2 of DCSP({U}), which are indistinguishable with respect to their iterated degree sequence, but differ with regards to satisfiability. The two instances have the same set of variables, defined to be \(\bigcup _{[\mathbf {t}]_{\equiv }\in D^{r}_{\equiv }} V_{[\mathbf {t}]_{\equiv }}\) where \(V_{[\mathbf {t}]_{\equiv }}=\{v_{[\mathbf {t}]_{\equiv }}^{i} \mid 0\leq i< k_{[\mathbf {t}]_{\equiv }} n\}\) is a set of \(k_{[\mathbf {t}]_{\equiv }}n\) distinct variables.
We start by constructing the constraints of the unsatisfiable instance I1, which we will do in two stages. First, for every class [t]≡, let \(\mathbb {S}_{[\mathbf {t}]_{\equiv }}\) be the collection of \(n^{k_{[\mathbf {t}]_{\equiv }}}\) sets of cardinality \(k_{[\mathbf {t}]_{\equiv }}\) given by Lemma 14, as before with \(d=k_{[\mathbf {t}]_{\equiv }}\cdot |D|\) and \(k=k_{[\mathbf {t}]_{\equiv }}\). Note that each set in \(\mathbb {S}_{[\mathbf {t}]_{\equiv }}\) defines naturally a subset of \(V_{[\mathbf {t}]_{\equiv }}\) so we shall abuse notation and assume that \(\mathbb {S}_{[\mathbf {t}]_{\equiv }}\) is a collection of subsets of \(V_{[\mathbf {t}]_{\equiv }}\).
To simplify notation it will be convenient to use \(\mathbb {S}\) as a shorthand for the indexed family \(\{\mathbb {S}_{[\mathbf {t}]_{\equiv }} \mid {[\mathbf {t}]_{\equiv }}\in D^{r}_{\equiv }\}\). Now let S be \(\{S_{[\mathbf {t}]_{\equiv }} \mid {[\mathbf {t}]_{\equiv }}\in D^{r}_{\equiv }\}\) satisfying \(S_{[\mathbf {t}]_{\equiv }}\in \mathbb {S}_{[\mathbf {t}]_{\equiv }}\) for every \({[\mathbf {t}]_{\equiv }}\in D^{r}_{\equiv }\). We associate to S the constraint (s,U) where the scope s is constructed as follows. Before defining s we need some preparation. Recall that every coordinate of U, and hence of s, is associated to a tuple t ∈ Dr, so we can talk of the class [t]≡ to which each coordinate belongs. In particular, there are \(k_{[\mathbf {t}]_{\equiv }}\) coordinates in s of class [t]≡. Hence, by fixing some arbitrary ordering we can use \(\mathbf {s}_{[\mathbf {t}]_{\equiv }}^{i}\), \(i=1,\dots ,k_{[\mathbf {t}]_{\equiv }}\) to refer to the coordinates in s of class [t]≡. Then, informally, \(S_{[\mathbf {t}]_{\equiv }}\) describes which variables from \(v^{0}_{[\mathbf {t}]_{\equiv }},\dots ,v^{k_{[\mathbf {t}]_{\equiv }}n-1}_{[\mathbf {t}]_{\equiv }}\) to use in order to fill coordinates \(\mathbf {s}_{[\mathbf {t}]_{\equiv }}^{i}\), \(i=1,\dots ,k_{[\mathbf {t}]_{\equiv }}\). Formally, for every \([\mathbf {t}]_{\equiv }\in D^{r}_{\equiv }\) and each \(i=1,\dots ,k_{[\mathbf {t}]_{\equiv }}\), \(\mathbf {s}_{[\mathbf {t}]_{\equiv }}^{i}\) is assigned to the ith element in \(S_{[\mathbf {t}]_{\equiv }}\) in increasing order.
We add such a constraint for each of the \({\Pi }_{[\mathbf {t}]_{\equiv } \in D^{r}_{\equiv }} n^{k_{[\mathbf {t}]_{\equiv }}} = n^{(|D|^{r})}\) possible choices for S. Therefore, after the first stage we have exactly \(n^{(|D|^{r})}\) constraints.
In the second stage we add more constraints which will yield the particular symmetry of I1. Note that every permutation σ on \(\{1,\dots ,r\}\) induces a permutation \(\sigma ^{\prime }\) on the coordinates of U in a natural way. Specifically, if coordinate i of U is associated to tuple ti, then \(\sigma ^{\prime }(i)=j\) where \(\mathbf {t}_{j}=(\mathbf {t}_{i}[\sigma (1)],\dots ,\mathbf {t}_{i}[\sigma (r)])\). Then, in the second stage, for each permutation σ on {1,…,r} and for every constraint (s,U) added in the first stage we add the constraint \((\mathbf {s}^{\prime },U )\) where for every 1 ≤ i ≤|D|r, \(\mathbf {s}^{\prime }[i]=\mathbf {s}[\sigma ^{\prime }(i)]\). Therefore, after the second stage we have a total of \(m=r!\cdot n^{(|D|^{r})}\) constraints as needed.
We now turn to I2. The constraints are constructed in a similar way, but instead of using the family \(\mathbb {S}\) in the first stage, we use a different family \(\mathbb {S}^{\prime }\). In particular, for each class [t]≡, \(\mathbb {S}^{\prime }_{[\mathbf {t}]_{\equiv }}\) is obtained by partitioning \(V_{[\mathbf {t}]_{\equiv }}\) in \(k_{[\mathbf {t}]_{\equiv }}\) blocks of consecutive elements, so that each block has exactly n elements. Then, \(\mathbb {S}^{\prime }_{[\mathbf {t}]_{\equiv }}\) contains the \(n^{k_{[\mathbf {t}]_{\equiv }}}\) sets that can be obtained by selecting one element from each block. The second stage is done exactly as in I1.
We need to show that I1 and I2 are connected. Notice that in both instances each constraint (s,U) spans all subsets \(V_{[\mathbf {t}]_{\equiv }}\), so in both cases it is sufficient to prove that the subgraph of the factor graph induced by the constraint set together with one of these subsets \(V_{[\mathbf {t}]_{\equiv }}\) is connected. Pick any t ∈ Dr with \(k_{[\mathbf {t}]_{\equiv }}\geq 2\). Then, from part 14 of Lemma 14, the hypergraph \((V_{[\mathbf {t}]_{\equiv }}, \mathbb {S}_{[\mathbf {t}]_{\equiv }})\) is connected, and since for every \(S_{[\mathbf {t}]_{\equiv }} \in \mathbb {S}_{[\mathbf {t}]_{\equiv }}\) there is some constraint in I1 that all the variables in \(S_{[\mathbf {t}]_{\equiv }}\) participate in, \(V_{[\mathbf {t}]_{\equiv }}\) satisfies the aforementioned connectedness condition in I1, meaning that I1 is connected. As for I2, the reasoning is the same except that we are left to show that whenever \(k_{[\mathbf {t}]_{\equiv }}\geq 2\), the hypergraph with vertex set \(\{0,1,\dots ,kn-1\}\) and edge set \(\mathbb {S}^{\prime }\) is connected. This is immediate as by construction of \(\mathbb {S}^{\prime }\), any two vertices in \(\{0,1,\dots ,kn-1\}\) either belong to two separate blocks, in which case they share an edge, or they belong to the same block, in which case they both share an edge with any other vertex in any other block. □
Claim 4
I1 and I2 have the same iterated degree sequence.
Proof Proof of Claim
4. Let \([\mathbf {t}]_{\equiv } \in D^{r}_{\equiv }\). First, we observe that in both instances after the first stage, every variable of \(V_{[\mathbf {t}]_{\equiv }}\) appears in the same number of constraints. More specifically, every variable in \(V_{[\mathbf {t}]_{\equiv }}\) appears in an n-fraction of the constraints added in stage 1. In the case of instance I1 this is due to the fact that \(\mathbb {S}_{[\mathbf {t}]_{\equiv }}\) satisfies condition 14 in Lemma 14 and in instance I2 this follows from the fact that \(\mathbb {S}^{\prime }_{[\mathbf {t}]_{\equiv }}\) contains all possible sets obtained by choosing an element within each one of the blocks of size n. After the second stage (in both I1 and I2 since the second stage is common) every variable in \(V_{[\mathbf {t}]_{\equiv }}\) still participates in an n-fraction of the total number of constraints. In addition, it follows easily that the positions of the scope in which a variable in \(V_{[\mathbf {t}]_{\equiv }}\) participates distribute evenly among the \(k_{[\mathbf {t}]_{\equiv }}\) positions associated to t. That is, in both instances, we have that for every \([\mathbf {t}]_{\equiv }\in D^{r}_{\equiv }\), every variable \(x\in V_{[\mathbf {t}]_{\equiv }}\), and every position i associated to [t]≡ there are exactly \(\frac {m}{n k_{[\mathbf {t}]_{\equiv }}}\) constraints in which x appears at position i of the scope, where \(m = r! \cdot n^{|D|^{r}}\). Using this fact it is very easy to prove that I1 and I2 have the same iterated degree sequence. Formally, one could show by induction on k that for every \([\mathbf {t}]_{\equiv }\in D^{r}_{\equiv }\) and \(x_{1},x_{2}\in V_{[\mathbf {t}]_{\equiv }}\), \(\delta _{k}^{I_{1}}(x_{1})=\delta _{k}^{I_{2}}(x_{2})\) and that for any two constraints c1,c2 in I1 and I2 respectively \(\delta _{k}^{I_{1}}(c_{1})=\delta _{k}^{I_{2}}(c_{2})\). Here we are using \(\delta _{k}^{I_{1}}(\cdot )\) and \(\delta _{k}^{I_{2}}(\cdot )\) to denote the kth degree of a node in the factor graphs of I1 and I2 respectively. □
Claim 5
Instance I1 is unsatisfiable while instance I2 is satisfiable.
Proof Proof of Claim
5. We start by showing that I1 is not satisfiable. Assume by contradiction that I1 has a satisfying assignment ν. For each class [t]≡, consider the values given by ν to the first d variables \(v_{0},\dots ,v_{d-1}\) in \(V_{[\mathbf {t}]_{\equiv }}\). Since \(d=k_{[\mathbf {t}]_{\equiv }} \cdot |D|\), it follows by the pigeon-hole principle that at least \(k_{[\mathbf {t}]_{\equiv }}\) of these variables are assigned by ν to the same value of D. Let \(S_{[\mathbf {t}]_{\equiv }}\) be a subset of \(V_{[\mathbf {t}]_{\equiv }}\) containing \(k_{[\mathbf {t}]_{\equiv }}\) of these variables (we know that this subset belongs to \(\mathbb {S}_{[\mathbf {t}]_{\equiv }}\) by condition 14 of Lemma 14). Now consider the constraint (s,U) in I1 associated to \(S:=\{S_{[\mathbf {t}]_{\equiv }} \mid {[\mathbf {t}]_{\equiv }\in D^{r}_{\equiv }}\}\), which belongs to I1. If ν is a solution to I1, then the restriction of ν to s corresponds to an r-ary polymorphism of Γ. But ν assigns the same value to any two related tuples \(\mathbf {t} \equiv \mathbf {t}^{\prime }\), which implies that ν is symmetric, a contradiction.
We now turn our focus to I2. Let f be any r-ary polymorphism of Γ (for example the ith (1 ≤ i ≤ r) projection operation defined as \(f(x_{1},\dots ,x_{r})=x_{i}\)). We shall construct a solution ν of I2 in the following way. Recall that in the definition of I2 we have partitioned the elements of \(V_{[\mathbf {t}]_{\equiv }}\) in \(k_{[\mathbf {t}]_{\equiv }}\) consecutive blocks. In the first stage, all the elements in each block are placed in the same coordinate of U. So, if \(\mathbf {t}_{1},\dots ,\mathbf {t}_{|D|^{r}}\) are the tuples associated to coordinates \(1,\dots ,|D|^{r}\) and hence blocks \(1,\dots ,|D|^{r}\) respectively, then we only need that all variables in the ith block are assigned to f(ti) to satisfy all constraints added in the first stage. This assignment also satisfies the constraints added in the second stage, because if f is an r-ary polymorphism of Γ, then for every permutation σ on \(\{1,\dots ,r\}\), the operation g defined as \(g(x_{1},\dots ,x_{r})= f(x_{\sigma (1)},\dots ,x_{\sigma (r)})\) is also a polymorphism of Γ. □
Proof
To sum up, we constructed two connected instances I1 and I2, the latter of which is satisfiable while the former is not, which have the same iterated degree sequence. It follows from Corollary 3 that any distributed algorithm will give the same output on both instances, meaning that no algorithm can solve DCSP({U}). As anticipated at the beginning of the proof then it follows that there are also no algorithms that solve DCSP(Γ). □
4.2 Tractable Languages
In this section we turn our attention to the tractable case. In particular we shall show the following:
Theorem 15
Let Γ be a constraint language that is invariant under symmetric polymorphisms of all arities. Then there is an algorithm Alg that solves DCSP(Γ). The total running time, number of rounds, and maximum message size of Alg are, respectively, \(\mathcal {O}(n^{3}m\log n)\), \(\mathcal {O}(n^{2})\), and \(\mathcal {O}(m\log n)\) where n and m are the number of variables and constraints, respectively, of the input instance.
Note that this implies the “if” part of Theorem 11. Alg is composed of two phases. In the first phase, a distributed version of the colour refinement algorithm allows every process to calculate its iterated degree. Then, thanks to Theorem 10 we can use the degree of a variable as its ID for the second phase, implying that a distributed adapted version of the jpq-consistency algorithm [18] where messages are tagged with a process’s iterated degree solves the decision problem for Γ.
Distributed Colour Refinement
Let I = (A,X,D,C,α) be an instance of DCSP(Γ) and let n = |X| and m = |C|. There is a very natural way to calculate an agent’s iterated degree in a distributed way, both for variables and for constraints. This is a mere adaptation of the 1-dimensional Weisfeiler-Leman algorithm, also known as colour refinement, an algorithm that partitions the vertices of a graph into classes by iteratively distinguishing them on the basis of their degree (see for example [15, 16]). The algorithm proceeds in rounds. At round k = 0, each agent α(v) for v ∈ X ∪ C computes δ0(v) and broadcasts it to all its neighbours. At round k > 0, each agent α(v) knows the (k − 1)th degrees of its neighbours which it had received in the previous round, uses them to compute δk(v), and broadcasts it to its neighbours. If k = 2n then for every \(x,x^{\prime }\in X\) satisfying \(x\sim ^{k}_{\delta } x^{\prime }\) we have that \(x\sim _{\delta } x^{\prime }\), which implies that we can essentially regard the kth iterated degree as the unique common ID for all variables that are iterated degree equivalent. Then in 2n rounds each agent α(v) can compute \(\delta _{\infty }(v)\), where we use \(\delta _{\infty }\) as a shorthand for δ2n. As we described it, the distributed colour refinement algorithm is not particularly efficient in terms of message complexity. Although this is not necessary to achieve polynomial time, we can reduce the space required to encode \(\delta _{\infty }(v)\).
Lemma 16
Let \(s_{\max \limits }\) denote the size of the encoding of \(\delta _{\infty }(v)\). A modified version of the distributed colour refinement algorithm that runs over \(\mathcal {O}(n^{2})\) rounds achieves \(s_{\max \limits } = \mathcal {O}(\log n)\). The time at each round and the maximum size of a message are both bounded above by \(\mathcal {O}(m s_{max})\).
Proof
We describe a variation of the distributed colour refinement algorithm that achieves the required bounds. After computing the kth degree and before proceeding to compute the (k + 1)th degree, all agents broadcast their kth degree to their neighbours. At the next round, every agent broadcasts all the kth degrees received (removing repetitions) to its neighbours so that in 2n rounds every agent has received a complete list of all the kth degrees of all nodes. Every agent α(v) orders all kth degrees (this can easily be done in such a way that all agents produce the same order), and sets δk(v) to be the rank of its own degree in the order. Then it proceeds to send out this new encoding of δk(v) and to calculate δk+ 1(v) accordingly.
In this way, we have \(s_{\max \limits }=\mathcal {O}(\log (n+m))=\mathcal {O}(\log n)\). Note that the total number of rounds of this algorithm is \(\mathcal {O}(n^{2})\) and that, provided every set of degrees is stored as an ordered array, the cost of each computation done locally by an agent at a given round is bounded above by the size, \(\mathcal {O}((n+m)s_{\max \limits })=\mathcal {O}(ms_{\max \limits })\), of the largest message sent. Note that in order to obtain these bounds we have used the standard facts that any instance of CSP over a fixed finite constraint language Γ is such that \(m = \mathcal {O}(n^{r})\) and \(n = \mathcal {O}(rm)\), where r is the largest arity of a relation in Γ. □
As we will see, the price of an increase in the number of rounds (from n to n2) is compensated by the effect of \(s_{\max \limits }\) on both time complexity and the size of the messages.
The Distributed Consistency Algorithm
It is well known that if a constraint language Γ has symmetric operations of all arities then it satisfies the so-called bounded width property (see [5]). We avoid introducing the formal definition of bounded width as it is not needed in our results and refer the reader to [5] for reference. Informally, a constraint language Γ has bounded width if CSP(Γ) can be solved by a local consistency algorithm. This is a large class of problems which includes many languages that are not solvable by BLP, such as for instance the Boolean inequality relation \(\neq _{\mathbb {B}}\) of Example 2. Now, it has been shown in [18] that if Γ has bounded width and I ∈CSP(Γ) satisfies a combinatorial condition called jpq-consistency, then I has a solution. Instead of stating literally the result in [18] we shall state a weaker version that uses a different notion of consistency, more suitable to the model of distributed computation introduced in the paper.
A set system S is a subset of X × D. We shall use Sx to denote the set {d ∈ D∣(x,d) ∈ S}. A walk of length ℓ (in instance I) is any sequence \(x_{0}c_{0}{\dots } c_{\ell -1}x_{\ell }\) where \(x_{0},\dots ,x_{\ell }\) are variables, \(c_{0},\dots ,c_{\ell -1}\) are constraints, and xi,xi+ 1 ∈ ci for every 0 ≤ i < ℓ. Note that walks are precisely the walks in the factor graph GI (in the standard graph-theoretic sense) starting and finishing in X.
Let S be a set system, p be a walk, and \(B\subseteq S_{x}\) where x is the starting node of p. The propagation of B via p under S, denoted B +Sp, is the subset of D defined inductively on the length ℓ of p as follows. If ℓ = 0 then B +Sp = B. Otherwise, \(p=p^{\prime }c_{\ell -1}x_{\ell }\) where \(p^{\prime }\) is a walk of length ℓ − 1 ending at xℓ− 1. Let cℓ− 1 = (s,R). Then we define B +Sp to contain all e ∈ D such that there exists \(d\in B +_{S} p^{\prime }\) and t ∈ R such that for every 1 ≤ i ≤ arity(R), t[i] satisfies the following conditions:
-
1.
t[i] ∈ Ss[i],
-
2.
if s[i] = xℓ− 1 then t[i] = d, and
-
3.
if s[i] = xℓ then t[i] = e.
We are now ready to state the result from [18] that we shall use.
Theorem 17 (follows from 18)
Let I be an instance of CSP(Γ) where Γ has bounded width and let S be a set system such that Sx≠∅ for every x ∈ X and such that for every walk p starting and finishing at the same node x and for every d ∈ Sx, d belongs to {d} +Sp. Then I is satisfiable.
Our goal is to design a distributed algorithm that either correctly determines that an instance I is unsatisfiable, or produces a set system S verifying the conditions of Theorem 17. This is not possible in general due to the fact that agents are anonymous and hence a hypothetical algorithm that would generate a walk in a distributed way would be unable to determine if the initial and end nodes are the same. However, thanks to the structure established by Theorem 10, this difficulty can be overcome when Γ has symmetric polymorphisms of all arities because, essentially, the iterated degree of a node can act as its unique identifier. To make this intuition precise we will need to introduce a few more definitions.
We say that a pair (x,d) ∈ S is S-supported if for every walk p starting at x and finishing at a node y with \(x \sim _{\delta } y\), we have that {d} +Sp contains d.
Remark 18
We note that if (x,d) ∈ S is not S-supported and \(p=x_{0}c_{0}{\dots } x_{\ell }\) is a walk of minimal length among all walks witnessing that (x,d) is not S-supported then ℓ ≤ n2|D|. Indeed if we let \(B_{i}=\{d\}+x_{0}c_{0}{\dots } x_{i}\), \(i=0,\dots ,\ell \) then we have that (xi,Bi)≠(xj,Bj) for every 0 ≤ i < j ≤ ℓ, since otherwise the shorter walk \(x_{0}c_{0}{\dots } x_{i}c_{j}{\dots } x_{\ell }\) would contradict the minimality of p. Since there are n choices for each xi and 2|D| choices for Bi, the bound follows.
We say that a set system S is safe if for every solution ν ∈ I we have
Then, we have
Lemma 19
Let S be a safe set system and let (x,d) ∈ S be a pair that is not S-supported. Then S ∖{(x,d)} is safe.
Proof
Let ν be any solution in I satisfying ν(y) = ν(z) for every y,z ∈ X with \(y \sim _{\delta } z\) and let \(p=x_{0}c_{0}{\dots } x_{\ell }\) be any walk in S witnessing that (x,d) is not S-supported, (i.e, p is such that x0 = x, \(x_{0} \sim _{\delta } x_{\ell }\), and d∉{d} +Sp). Since S is safe we have that ν(y) ∈ Sy for every y ∈ X. It remains to see that ν(x)≠d, so that the safety condition remains unaltered when (x,d) is removed. First, it follows easily by induction that for every 1 ≤ i ≤ ℓ, ν(xi) ∈{ν(x)} +Spi where \(p_{i}=x_{0}c_{0}{\dots } x_{i}\). Then, since ν(xℓ) ∈{ν(x)} +Sp, ν(x) = ν(xℓ), and d∉{d} +Sp, it follows that ν(x)≠d. □
Our distributed consistency algorithm (that is, the second phase of Alg) works as follows. Every variable agent α(x) maintains a set \(S_{x} \subseteq D\) in such a way that the set system S is guaranteed to be safe at all times. As a result of an iterative process S is modified. We shall use Si to denote the content of S at the ith iteration, where an iteration is, in turn, a loop of \(T=2n(2^{|D|}+1)=\mathcal {O}(n)\) consecutive rounds. The rationale behind this exact value will be made clear later. Initially, \({S_{x}^{0}}\) is set to D for every x ∈ X. At iteration i for i ≥ 1, Si is obtained by removing all the elements in Si− 1 that are not Si− 1-supported. Then, in at most \(n|D|=\mathcal {O}(n)\) iterations we shall obtain a fixed point \(S^{\infty }\).
The key observation is that when Γ has symmetric polymorphisms of all arities, the satisfiability of I can be determined from \(S^{\infty }\). Indeed, if \(S^{\infty }_{x}=\emptyset \) for some x ∈ X then we can conclude from the fact that \(S^{\infty }\) is safe and Theorem 10 that I has no solution. Otherwise, \(S^{\infty }\) satisfies the conditions of Theorem 17 and, hence, I is satisfiable.
It remains to see how to compute Si+ 1 from Si. In an initial preparation step for every iteration, every variable agent α(x) sends \({S^{i}_{x}}\) to all its neighbours. To compute Si+ 1 the algorithm proceeds in rounds. All the messages sent are sets containing triplets of the form \((\delta _{\infty },d,B)\) where d ∈ D, \(B\subseteq D\), and \(\delta _{\infty }\) is the iterated degree of some variable x ∈ X. It follows from the fact that there are at most n possibilities for the degree of a variable that the size of each message is \(\mathcal {O}(ns_{\max \limits })\).
The agents controlling variables and constraints alternate. That is, variables perform internal and send events at even rounds and receive messages at odd rounds, while constraints perform internal and send events at odd rounds and receive messages at even rounds. More specifically, in round j = 0 of iteration i, every variable agent α(x) sends to its neighbours the message M containing all triplets of the form \((\delta _{\infty }(x),d,\{d\})\) with \(d\in {S^{i}_{x}}\). At round 2j for j > 0, α(x) computes M = M1 ∪⋯ ∪ Mr where \(M_{1},\dots ,M_{r}\) are the messages it received at the end of round 2j − 1. Subsequently, for every triplet \((\delta _{\infty },d,B)\in M\) with \(\delta _{\infty }=\delta _{\infty }(x)\) and d∉B, α(x) marks d as ‘not Si-supported’. Finally, it sends message M to all its neighbours. This computation can be done in time \(\mathcal {O}(rns_{\max \limits })=\mathcal {O}(mns_{\max \limits })\) provided that each message is stored as an ordered array.
In round 2j + 1, every constraint agent α(c) computes from the messages Mx (received from each neighbour α(x) in the previous round) the set \(M^{\prime }_{x}\), which contains for every variable y ∈ c and every \((\delta _{\infty },d,B)\) in My, the triplet \((\delta _{\infty },d,B+_{S^{i}} p)\) where p = ycx. Finally, it sends to each neighbour α(x) the corresponding message \(M^{\prime }_{x}\). Note that while α(c) doesn’t know the address of α(x) specifically, knowing the label of the channel that connects them is sufficient to calculate \(M^{\prime }_{x}\) correctly and send the message accordingly. Moreover, for given y and x, α(c) can compute \(B+_{S^{i}} p\) in \(\mathcal {O}(1)\) time as α(c) knows both \({S^{i}_{y}}\) and \({S^{i}_{x}}\). Hence, since the arity of the relations is fixed (as Γ is fixed) the total running time at iteration 2j + 1 of a constraint agent α(c) is \(\mathcal {O}(ns_{\max \limits })\).
Now it is immediate to show by induction that for every j ≥ 0, every x ∈ X and c ∈ C with x ∈ c the message sent by α(x) to α(c) at the end of round 2j is precisely
and the message sent by α(c) to α(x) at the end of round 2j + 1 is precisely
By Remark 18 only 2n2|D| = T − 2n iterations are needed to identify all elements in Si that are not Si-supported. Hence, after exactly T − 2n rounds every variable agent α(x) computes \(S^{i+1}_{x}\) by removing all the elements in Si that are marked as “not Si-supported”. If \(S_{x}^{i+1} = \emptyset \), then α(x) initiates a wave, which is propagated by all its neighbours, broadcasting that an inconsistency was detected. In this case, in at most 2n additional rounds all agents can correctly declare that I is unsatisfiable. Otherwise, a new iteration begins.
To sum up, the distributed consistency algorithm consists of \(\mathcal {O}(n)\) iterations consisting, each, of \(\mathcal {O}(n)\) rounds where the total running time for internal events at a given round is \(\mathcal {O}(mns_{\max \limits })\) and the maximum size of each message transmitted is \(\mathcal {O}(ns_{\max \limits })\). Together with the bounds given by Lemma 16 for the distributed colour refinement phase, this completes the proof of Theorem 15.
4.3 The Search Algorithm
We conclude by presenting the proof of Theorem 12. The hardness part follows immediately from Theorem 11 as the search problem is as difficult as the decision problem. For the positive result we shall present an adaptation of the algorithm solving the decision version. Let I be an instance of DCSP-Search(Γ) where Γ contains symmetric polymorphisms of all arities. In what follows we shall use intensively the fact that Pol(Γ) is closed under composition. Let \(J\subseteq D\) be minimal with the property that f(D) = J for some unary polymorphism f in Pol(Γ). It is fairly standard to show that for every r ≥ 0 there is a r-ary symmetric operation g in Pol(Γ) such that \(g(x,\dots ,x)=x\) for every x ∈ J. Indeed, let f satisfy f(D) = J and let \(g^{\prime }\) be any r-ary symmetric polymorphism in Pol(Γ). Then the unary operation h defined by \(h(x)=f\circ g^{\prime }(x,\dots ,x)\) is a unary polymorphism of Γ. By the choice of f we have \(h(D)\subseteq J\). We note that h(J) = J since otherwise h2 would contradict the minimality of f. Consequently, h restricted to J is a (partial) isomorphism, and so h− 1 preserves all relations of Γ restricted to the subdomain J. Hence, the r-ary operation g defined as \(g=h^{-1}\circ f \circ g^{\prime }\) satisfies the claim. This implies that if we enlarge the constraint language by adding all singletons {d}, d ∈ J, the resulting constraint language, which we shall denote by \({\Gamma }^{\prime }\), still has symmetric polymorphisms of all arities. For convenience we also include D in \({\Gamma }^{\prime }\).
The algorithm has two phases. In the first phase it runs the decision algorithm to determine whether the instance is satisfiable. As a byproduct, every variable agent α(x) has computed its iterated degree \(\delta _{\infty }(x)\) and knows as well its rank in a prescribed ordering of all variable degrees \(\delta _{\infty }^{1},\dots ,\delta _{\infty }^{r}\), r ≤ n. This (partial) order will be used to coordinate between the agents. An i-agent, 1 ≤ i ≤ r is any agent α(x) with \(\delta _{\infty }(x)=\delta ^{i}_{\infty }\). We also assume a fixed ordering on the elements in D. If the instance is unsatisfiable nothing else remains to be done so from now on we shall assume that the instance is satisfiable.
In the second phase the algorithm searches for a solution. Every variable agent α(x) maintains a set \(F_{x}\subseteq D\) with the property that there is a solution ν that falls within the set system F, i.e, such that ν(x) ∈ Fx for every x ∈ X. Initially every agent α(x) sets Fx = D so it is only necessary to make sure that this condition is preserved during the execution of the algorithm. The second phase contains two nested loops. The outer loop has r iterations and the inner loop consists of at most |D| iterations so that we shall use iteration (i,d) to indicate the run of the algorithm at the \(i=1,\dots ,r\) iteration of the outer loop and at the iteration d of the inner loop.
At the beginning of iteration (i,d) every variable agent α(x) defines \(S_{x} \subseteq D\) to be Sx = {d} whenever α(x) is an i-agent and Sx = Fx elsewhere. Then it runs the distributed consistency algorithm starting at S obtaining a fixed point \(S^{\infty }\). We note that since all initial sets Sx belong to \({\Gamma }^{\prime }\) and \({\Gamma }^{\prime }\) contains symmetric polymorphisms of all arities then the obtained fixed point \(S^{\infty }\) correctly determines whether there exists a solution ν that falls within S. Then every i-agent α(x) checks whether \(S^{\infty }_{x}=\emptyset \). In case of positive answer nothing else is done and round (i,d) finishes. Otherwise, there must be a solution ν that falls within S, so α(x) sets Fx to {d} and starts a wave to indicate to all processes that the ith iteration of the outer loop is finished and that the next iteration of the outer loop can start. When the r iterations of the outer loop have been completed the set system F contains only singletons. The assignment that sets every variable x ∈ X to the only element in Fx is necessarily a solution. This concludes the proof of Theorem 12.
5 Conclusion
We analysed the complexity of the distributed constraint satisfaction problem on a synchronous, anonymous network parametrised by the constraint language. We showed that, depending on the polymorphisms of Γ, DCSP(Γ) is either solvable in polynomial time, or not solvable altogether. A number of natural open questions arise in this context. For instance, it is not clear whether asynchronous networks are strictly more powerful than their synchronous counterpart. Moreover, it would be interesting to explore the role of allowing agents to make random choices - provided this is not used to create and share unique IDs.
In the spirit of [14], one could consider characterizing the structural restrictions on tractable distributed CSPs, or in other words, determining which classes of networks are tractable in the DCSP framework, regardless of the constraint language. The starting point for this analysis could be the work on fibrations by Boldi et al. (see for example [8, 9]). In particular, we propose the question of establishing a connection between the universal fibration of a graph and its iterated degree sequence.
Notes
For mathematical clarity, we label edges with the relation itself. However, in algorithmic applications, every relation can be substituted with a corresponding symbol.
We remark that the notions of degree and iterated degree are well-defined concepts in graph theory. We borrow this terminology to refer to the analogous concepts in CSPs.
References
Angluin, D.: Local and Global Properties in Networks of Processors (Extended Abstract). In: Miller, R.E., Ginsburg, S., Burkhard, W.A., Lipton, R.J. (eds.) Proceedings of the 12th Annual ACM Symposium on Theory of Computing. April 28-30, 1980, Los Angeles, California, USA, pp. 82–93. ACM (1980)
Arora, S., Hazan, E., Kale, S.: The Multiplicative Weights Update Method: a meta-Algorithm and Applications. Theory Comput. 8(1), 121–164 (2012)
Barceló, P., Kostylev, E., Monet, M., Pérez, J., Reutter, J.L., Silva, J.P.: The Logical Expressiveness of Graph Neural Networks. In: 8th International Conference on Learning Representations, ICLR 2020 Addis Ababa, Ethiopia. April 26-30, 2020. OpenReview.net (2020)
Barto, L.: The constraint satisfaction problem and universal algebra. Bull. Symb. Log. 21(3), 319–337 (2015)
Barto, L., Krokhin, A.A., Willard, R.: Polymorphisms, and how to use them. In: Krokhin, A.A., Zivný, S. (eds.) The Constraint Satisfaction Problem: Complexity and Approximability, vol. 7 of Dagstuhl Follow-Ups. pp. 1–44. Schloss Dagstuhl - Leibniz-Zentrum für Informatik (2017)
Battaglia, P.W., Hamrick, J.B., Bapst, V., Sanchez-Gonzalez, A., Flores Zambaldi, V., Malinowski, M., Tacchetti, A., Raposo, D., Santoro, A., Faulkner, R., Gülçehre, C., Francis Song, H., Ballard, A.J., Gilmer, J., Dahl, G.E., Vaswani, A., Allen, K.R., Nash, C., Langston, V., Dyer, C., Heess, N., Wierstra, D., Kohli, P., Botvinick, M., Vinyals, O., Li, Y., Pascanu, R.: Relational inductive biases, deep learning, and graph networks. CoRR, abs/1806.01261 (2018)
Bejar, R., Krishnamachari, B., Gomes, Carla, G., Selman, B.: Distributed constraint satisfaction in a wireless sensor tracking system. In: Workshop on distributed constraint reasoning, international joint conference on artificial intelligence. vol. 4 (2001)
Boldi, P., Shammah, S., Vigna, S., Codenotti, B., Gemmell, P., Simon, J.: Symmetry breaking in anonymous networks: Characterizations. In: Fourth israel symposium on theory of computing and systems, ISTCS 1996, Jerusalem, Israel. June 10-12, 1996, Proceedings. pp. 16–26. IEEE Computer Society (1996)
Boldi, P., Vigna, S.: An effective characterization of computability in anonymous networks. In: Welch, J.L. (ed.) Distributed computing, 15th international conference, DISC 2001, Lisbon, Portugal. October 3-5, 2001, Proceedings. vol. 2180 of Lecture Notes in Computer Science, pp. 33–47. Springer (2001)
Bulatov, A.A.: A Dichotomy theorem for nonuniform csps. In: Chris Umans (ed.) 58th IEEE Annual Symposium on Foundations of Computer Science, FOCS, Berkeley, CA, USA, October 15-17, 2017, pp. 319–330. IEEE, Computer Society (2017)
Duffy, K.R., Bordenave, C., Leith, D.J.: Decentralized Constraint Satisfaction. IEEE/ACM Trans. Netw. 21(4), 1298–1308 (2013)
Fioretto, F., Pontelli, E., Yeoh, W.: Distributed constraint optimization problems and applications: A survey. J. Artif. Intell. Res. 61, 623–698 (2018)
Fokkink, W.: Distributed algorithms: An intuitive approach MIT Press (2013)
Grohe, M.: The Complexity of homomorphism and constraint satisfaction problems seen from the Other side. J. ACM 54(1), 1:1–1:24 (2007)
Grohe, M.: word2vec, node2vec, Graph2vec, x2vec: Towards a Theory of Vector Embeddings of Structured data. In: Dan Suciu, Yufei Tao, and Zhewei Wei, editors, Proceedings of the 39th ACM SIGMOD-SIGACT-SIGAI Symposium on Principles of Database Systems, PODS 2020, Portland, OR, USA, June 14-19, 2020. pp. 1–16. ACM (2020)
Martin Grohe, M., Kersting, K., Mladenov, M., Schweitzer, P.: Color refinement and its applications. Van den Broeck, G.; Kersting, K.; Natarajan, S (2017)
Jonsson, P., Lagerkvist, V., Nordh, G., Zanuttini, B.: Strong partial clones and the time complexity of SAT problems. J. Comput. Syst. Sci. 84, 52–78 (2017)
Kozik, M.: Solving CSPs using weak local consistency. SIAM J. Comput. 50(4), 1263–1286 (2021)
Krokhin, A.A., živný, S. (eds.): Editors. The Constraint Satisfaction Problem: Complexity and Approximability. vol. 7 of Dagstuhl Follow-Ups Schloss Dagstuhl - Leibniz-Zentrum für Informatik (2017)
Kun, G., O’donnell, R., Tamaki, S., Yoshida, Y., Zhou, Y.: Linear programming, width-1 csps, and robust satisfaction. In: Goldwasser, S. (ed.) Innovations in Theoretical Computer Science 2012, Cambridge, MA, USA, January 8-10, 2012, pp. 484–495. ACM (2012)
Meisels, A.: Distributed Search by Constrained Agents - Algorithms, Performance, Communication. Advanced Information and Knowledge Processing. Springer (2008)
Morris, C., Ritzert, M., Fey, M., Hamilton, W.-L., Lenssen, J.-E., Rattan, G., Grohe, M.: Weisfeiler and Leman go Neural: Higher-order graph neural networks. In: The Thirty-Third AAAI Conference on Artificial Intelligence, AAAI 2019, The Thirty-First Innovative Applications of Artificial Intelligence Conference, IAAI 2019, The Ninth AAAI Symposium on Educational Advances in Artificial Intelligence, EAAI 2019, Honolulu, Hawaii, USA, January 27 - February 1, 2019, pp. 4602–4609. AAAI Press (2019)
Rossi, F., Van Beek, P., Walsh, T. (eds.): Handbook of constraint programming. Vol. 2 of Foundations of Artificial Intelligence. Elsevier (2006)
Toenshoff, J., Ritzert, M., Wolf, H., Grohe, M.: RUN-CSP: Unsupervised learning of message passing networks for binary constraint satisfaction problems. CoRR, abs/1909.08387 (2019)
Xu, K., Hu, W., Leskovec, J., Jegelka, S.: How powerful are graph neural networks?. In: 7th International conference on learning representations, ICLR 2019, New Orleans, LA, USA, May 6-9, 2019. OpenReview.net (2019)
Yamashita, M., Kameda, T.: Computing on an anonymous network. In: Dolev, D. (ed.) Proceedings of the Seventh Annual ACM Symposium on Principles of Distributed Computing, Toronto, Ontario, Canada. August 15-17 1988. pp. 117–130. ACM (1988)
Yokoo, M., Durfee, E.H., Ishida. T., Kuwabara, K.: Distributed constraint satisfaction for formalizing distributed problem solving. In: Proceedings of the 12th International conference on distributed computing systems, Yokohama, Japan. June 9-12 1992. pp. 614–621. IEEE Computer Society (1992)
Yokoo, M., Durfee, E.H., Ishida, T., Kuwabara, K.: The distributed constraint satisfaction problem: Formalization and algorithms. IEEE Trans. Knowl. Data Eng. 10(5), 673–685 (1998)
Yokoo, M., Hirayama, K.: Algorithms for distributed constraint satisfaction: A review. Auton. Agents Multi Agent Syst. 3(2), 185–207 (2000)
Zhuk, D.: Berkeley, CA, USA, October 15-17, 2017. pp. 331–342. IEEE, Computer Society. In: Umans, C. (ed.) 58th IEEE Annual symposium on foundations of computer science, FOCS (2017)
Acknowledgements
We would like to thank Gergely Neu for useful discussions on the weighted majority algorithm.
Funding
Open Access funding provided thanks to the CRUE-CSIC agreement with Springer Nature.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This article belongs to the Topical Collection: Theoretical Aspects of Computer Science (STACS 2021) Guest Editors: Markus Bläser and Benjamin Monmege
The project that gave rise to these results received the support of a fellowship from “la Caixa” Foundation (ID 100010434). The fellowship code is LCF/BQ/DI18/11660056. This project has received funding from the European Union’s Horizon 2020 research and innovation programme under the Marie Sk lodowska-Curie grant agreement No. 713673.
Victor Dalmau was supported by MICCIN grants TIN2016-76573-C2-1P and PID2019-109137GB-C22.
Appendices
Appendix A:: The Distributed Formalism
In this section we formalize the definition of the distributed system model which was used throughout the paper. Note that for simplicity, here we describe a distributed system which only allows message broadcast (as opposed to allowing different messages to be sent through channels with different labels). Nonetheless, as pointed out in Section 2, this does not decrease the expressive power of the system.
Let \(\mathbb {N}\) denote the set of positive integers and \(\mathbb {N}_{0} := \mathbb {N} \cup \{0\}\). For a (possibly infinite) set S, we use \(\mathbb {N}_{0}^{S}\) (as an extension of the power set notation 2S) to denote the set of all multisets containing just elements from S. Let Σ be a finite alphabet. A message is a finite string of symbols from Σ, that is, an element of Σ∗. A process (also called an agent) is a 7-tuple (Σ,Λ,L,Q,qo,Qf,F) where Λ is a finite set known as the memory alphabet, L is a finite set of labels, Q is a finite set of states, q0 ∈ Q is the initial state, \(Q_{f} \subseteq Q\) denotes the subset of terminal states, and F is a Turing-computable function
which takes as input the current state, the memory tape, and the multiset of labelled messages received at the previous round, and outputs a new state, an updated memory tape, and a message to be broadcast to the process’s neighbours. We require that terminal states are fixed points of F in the sense that for all q ∈ Qf, λ ∈Λ∗, and \(M \in \mathbb {N}_{0}^{L \times {\Sigma }^{*}}\) it holds that
where ε ∈Σ∗ denotes the empty string. An output of the function F – that is, a triplet c = (q,λ,s) ∈ Q ×Λ∗×Σ∗ – is called a configuration of the process.
In this paper, a message-passing network is an edge-labelled graph whose vertex set is a set of identical processes and where the label set of the network corresponds to the label set of the processes. The neighbourhood of a process i in the network is denoted N(i). Given a message-passing network G with vertex set [p], a run of F over G with initial memory \(({\lambda ^{1}_{0}},\ldots ,{\lambda ^{p}_{0}})\) is a collection of p sequences of configurations \({c^{i}_{0}},{c^{i}_{1}},{c^{i}_{2}} \ldots \), i ∈ [p] where \({c^{i}_{t}}=({q^{i}_{t}},{\lambda ^{i}_{t}}, {s^{i}_{t}})\), such that \({q^{i}_{0}}=q_{0}\) is the initial state, \({s^{i}_{0}} = \varepsilon \) is the empty string, and for all t ≥ 0 and all i ∈ [p], \((q^{i}_{t+1}, \lambda ^{i}_{t+1}, s^{i}_{t+1}) = F({q^{i}_{t}},{\lambda ^{i}_{t}},{M^{i}_{t}})\), where \({M^{i}_{t}} = \{\{(\ell _{\{i,j\}},{s^{j}_{t}}) \mid j \in N(i)\}\}\) and ℓ{i,j}∈ L denotes the label of edge {i,j}. A run is said to be terminating if there exists some integer T such that, for each i ∈ [p], \({q^{i}_{T}} \in Q_{f}\) (and hence, by definition of F, \({q^{i}_{t}}={q^{i}_{T}}\) for all t > T). The output of the run is the set of terminal memory tapes \({\lambda ^{i}_{T}}\), i ∈ [p].
We point out that, while for convenience we define runs to be infinite sequences of configurations, for all practical purposes one can assume that a process effectively halts as soon as it reaches a terminating state.
Notice that, given p identical processes, a run of the algorithm is fully determined by the connectivity and labels of the network, and by the choice of initial memory \({\lambda ^{i}_{0}}\) for each of the p processes. This is generally fairly limited as each process acquires new information via message passing. It could, for instance, contain the processes’ unique identifiers if these were available (this is clearly not the case for anonymous networks like the one that we address in this paper). In the case of the DCSP message passing network, the connectivity is as described in Section 2. In particular, the network is bipartite and each edge with its corresponding label describes how a variable participates in a constraint. The initial memory is limited to the numbers n and m of variables and constraints respectively in the DCSP instance, and to a bit which specifies if the process is controlling a variable or a constraint. In particular, it contains no identifier nor any other information about the input instance. Moreover, in the case of DCSP the function F can depend on the constraint language, since this is fixed, but not on the specifics of the input instance. Finally, we remark that while F does not depend explicitly on the round t, this can be stored and updated in the process’s memory, and the messages can even be tagged with a time stamp if this is needed for synchronization purposes, for example, due to hardware issues.
Appendix B:: Binary Structures
Throughout the paper, we assumed that both variables and constraints are controlled by agents in a distributed network (in this section, we will refer to this as model 1). However, when all the constraint relations in Γ are binary it is also valid and, indeed, more common to assume that only variables are controlled by agents, and there is a communication channel between any two variable agents α(x) and \(\alpha (x^{\prime })\) whenever x and \(x^{\prime }\) share a constraint (model 2) which is labelled with the constraint relation and the direction of the constraint.
It is very easy to see that in the binary case both models are equivalent. Indeed, for every CSP instance (X,D,C), let (A1,X,D,C,α1) and (A2,X,D,C,α2) be the associated DCSP instances in model 1 and 2 respectively. It is easy to see that every algorithm in model 2 can be easily simulated by an algorithm in model 1. In particular, it is only necessary that at round 2j every variable agent α1(x) replicates the jth round of α2(x) (while every constraint agent α1(c) remains idle). Then, round 2j + 1 is used to replicate the messages sent at round j. That is, whenever α2(x) sends a message to a neighbour \(\alpha _{2}(x^{\prime })\) at round j, α1(x) sends a message to α1(c) at round 2j, where c is the constraint shared by x and \(x^{\prime }\). At round 2j + 1 then α1(c) forwards the message to \(\alpha _{1}(x^{\prime })\).
Similarly, any algorithm in model 1 can be replicated in model 2. In this case, at a given round j, every agent α2(x) simulates the internal computation done at round j by α1(x) and all its neighbours.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Butti, S., Dalmau, V. The Complexity of the Distributed Constraint Satisfaction Problem. Theory Comput Syst (2022). https://doi.org/10.1007/s00224-022-10091-y
Accepted:
Published:
DOI: https://doi.org/10.1007/s00224-022-10091-y