Abstract
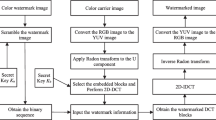
This paper presents a copyright protection and integrity verification watermarking scheme for color images. It uses the extracted features of the host image to generate a watermark, which is then embedded in the host image to produce a watermarked image. We have inserted the watermark in the frequency domain using discrete cosine transform. The choice of the positions of the watermark bits depends on a preprocessing study on the original and compressed–decompressed image. Then, we have implemented a blind detection algorithm. In order to counter rotation and cropping attacks, our scheme adopts Speeded-Up Robust Feature to locate invariant key points. The latter are extracted from the original image and used as part of the keys of our scheme to resynchronize only watermarked image altered by rotation and cropping. The robustness and integrity of our method are tested by executing Stirmark 3.1 attacks to the watermarked images. The experimental results show that our method affords a high level of imperceptibility and robustness against JPEG compression, unique and double Stirmark attacks.












Similar content being viewed by others
References
F.W. Alsaade, Watermarking for content integrity and ownership control of medical images. J. Artif. Intell. (2016). https://doi.org/10.3923/jai.2017.32.41
R.A.A.K. Bhullar, D. Dangwal, S. Kumar, A zero-watermarking scheme using discrete wavelet transform. Procedia Comput. Sci. 70, 603–609 (2015)
S. Bekkouch, K.M. Faraoun, Robust and reversible image watermarking scheme using combined DCT-DWT-SVD transforms. J. Inf. Process. Syst. 11, 406–420 (2015)
H. Bay, A. Ess, T. Tuytelaars, L. Gool, SURF: Speeded up robust features. Comput. Vis. Image Underst. (CVIU) 110(3), 346–359 (2008)
M.K. Baby, A. Madhu, Watermarking based biomedical image integrity control with DCT lossless compression. Int. J. Adv. Sci. Technol. Eng. Manag. Sci. 3, 297–303 (2017)
W.C. Chen, Y. Xiong, J. Gao, N. Gelfand, R. Grzeszczuk, Efficient extraction of robust image features on mobile devices, in 6th IEEE and ACM International Symposium on Mixed and Augmented Reality, ISMAR, pp. 287–288 (2007)
M. Charfeddine, M. El’arbi, C.B. Amar, A new DCT audio watermarking scheme based on preliminary MP3 study. Multimed. Tools Appl. 70, 1521–1557 (2012)
W.J. Chen, R.W. Xiaolong, W.T. Meng, Affine correction based image watermarking robust to geometric attacks. Int. Conf. Parallel Distrib. Comput. Appl. Technol. (2016). https://doi.org/10.1109/PDCAT.2016.45
L. Dong, Y. Zhang, X. Shi, On feature-based sar image registration: appropriate feature and retrieval algorithm. Adv. Remote Sens. Technol. Coast. Environ. Disasters Infrastruct. (2018). https://doi.org/10.5772/intechopen.81665
G. Ertugrul, S. Ozturk, A novel hash function based fragile watermarking method for image integrity. Multimed. Tools Appl. 78, 17701–17718 (2019)
W.K. ElSaid, Watermarking digital artworks. Int. J. Comput. Appl. 125, 0975–8887 (2015)
M.C. Hernandez, A.C.H. Garcia-Ugalde, M.N. Miyatake, H.P. Meana, Copyright protection of color imaging using robust-encoded watermarking. Radioengineering 24, 240–251 (2015)
G. Jianting, P. Zheng, J. Huang, Secure watermarking scheme against watermark attacks in the encrypted domain. J. Vis. Commun. Image Represent. 24, 125–135 (2015)
F. Kurniawan, M.S. Khalil, M.K. Khan, Y.M. Alginahi, Exploiting digital watermarking to preserve integrity of the digital Holy Quran images. Int. Conf. Adv. Inf. Technol. Holy Quran Sci. (2013). https://doi.org/10.1109/NOORIC.2013.18
M. Kutter, F. Petitcolas, A fair benchmark for image watermarking systems. SPIE Conf. Secur. Watermarking Multimed. Contents 33657, 226–239 (1999)
S. Kamble, S. Agarwal, V.K. Shrivastava, V. Maheshkar, DCT based texture watermarking using GLCM. Int. Adv. Comput. Conf. (2010). https://doi.org/10.1109/IADCC.2010.5423014
C. Ling, O.U. Rehman, Watermarking for Image Authentication (Springer, Basel, 2015), pp. 43–73. https://doi.org/10.1007/978-3-319-13156-6_2
L. Laouamer, O. Tayan, A Semi-blind robust DCT watermarking approach for sensitive text images. Arab. J. Sci. Eng. 40, 1097–1109 (2015)
LIGM, Laboratoire d’Informatique Gaspard -Monge. http://igm.univmlv.fr/~incerti/IMAGES/PPM.htm. Accessed April 2018
M. Moosazadeh, G. Ekbatanifard, Robust image watermarking algorithm using DCT coefficients relation in YCoCg-R color space, in Eighth International Conference on Information and Knowledge Technology (IKT) (Hamedan, Iran, 2016), pp. 263–267
M. Nasrin, B.E. Khoo, Robust blind image watermarking scheme based on redundant discrete wavelet transform and singular value decomposition. AEU Int. J. Electron. Commun. 37, 102–112 (2013)
A.M. Osman, E.A.A. Osman, R. Row, Invisible digital image watermarking in spatial domain with random localization. Int. J. Eng. Innov. Technol. (IJEIT) 2, 227-231231 (2012)
W.C. Peng, X. Wang, Z.Q. Xia, C. Zhang, X.J. Chen, Geometrically resilient color image zero-watermarking algorithm based on quaternion exponent moments. J. Vis. Commun. Image Represent. 41, 247–259 (2016)
S .R. Priyanka, S. Maheshkar, Robust multiple composite watermarking using LSB technique, in Proceedings of the 5th International Conference on Frontiers in Intelligent Computing: Theory and Applications, Advances in Intelligent Systems and Computing, pp. 209–217 (2017). https://doi.org/10.1007/978-981-10-3153-3_21
A. Roy, A.K. Maiti, K. Ghosh, A perception based color image adaptive watermarking scheme in YCbCr space. Int. Conf. Signal Process. Integr. Netw. (2015). https://doi.org/10.1109/SPIN.2015.7095399
S. Roy, A.K. Pal, An indirect watermark hiding in discrete cosine transform-singular value decomposition domain for copyright protection. R. Soc. Open Sci. (2017). https://doi.org/10.1098/rsos.170326
Reading Al Quran. http://readingalquran.com/alquran.php?part=30, Accessed April 2018
A. Singh, J. Nigam, R. Thakur, R. Gupta, A. Kumar, Wavelet based robust watermarking technique for integrity control in medical images. Int. Conf. Micro-Electron. Telecommun. Eng. (2016). https://doi.org/10.1109/ICMETE.2016.103
S.H. Soleymani, A.H. Taherinia, A.H. Mohajerzadeh, A blind robust watermarking method based on Arnold Cat map and amplified pseudo-noise strings with weak correlation. J. Vis. Commun. Image Represent. (2018). arXiv:1804.11240v1. Accessed 19 Jan 2020
N. Tarhouni, M. Charfddine, C.B. Amar, A New Robust and Blind Image Watermarking Scheme In Frequency Domain Based On Optimal Blocks Selection, Int. Conf. Cent. Eur. Comput. Graph. Vis. Comput. Vis. (2018). https://doi.org/10.24132/CSRN.2018.2802.11
N. Tiwari, Sharmilaand, Digital watermarking applications, parameter measures and techniques. Int. J. Comput. Sci. Netw. Secur. 17, 184–194 (2017)
H. Tian, Y. Zhao, R. Ni, L. Qin, X. Li, LDFT-based watermarking resilient to local desynchronization attacks. IEEE Trans. Cybern. (2013). https://doi.org/10.1109/TCYB.2013.2245415
C. Wang, Y. Zhang, X. Zhou, Robust image watermarking algorithm based on ASIFT against geometric attacks. Appl. Sci. (2018). https://doi.org/10.3390/app8030410
H. Zhang, C. Wang, X. Zhou, Fragile watermarking for image authentication using the characteristic of SVD. Algorithms (2017). https://doi.org/10.3390/a10010027
Y. Zhang, C. Wang, X. Zhou, RST resilient watermarking scheme based on DWT-SVD and scale-invariant feature transform. Algorithms (2017). https://doi.org/10.3390/a10020041
Acknowledgements
The research leading to these results received funding from the Tunisian Ministry of Higher Education and Scientific Research under the Grant Agreement Number LR11ES48
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Tarhouni, N., Charfeddine, M. & Ben Amar, C. Novel and Robust Image Watermarking for Copyright Protection and Integrity Control. Circuits Syst Signal Process 39, 5059–5103 (2020). https://doi.org/10.1007/s00034-020-01401-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00034-020-01401-1