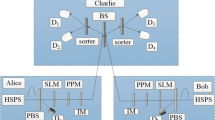
Abstract
Decoy state method is widely used in practical quantum key distribution (QKD) systems to substantially extend the secure communication distance. Detector efficiency mismatch (DEM), which exists between practical detectors, effects the security of practical QKD systems seriously. Security of single photon QKD with DEM has been analyzed. However, estimate of the phase error rate still remains difficult in practice. Here, using a simple equivalent detection model, the mutual information between legitimate users and the eavesdropper for single photon state in QKD with DEM is analyzed. Then we improve the security analysis to cover the situation of weak coherent QKD with DEM. A general theory of the decoy state QKD with DEM is proposed to calculate the lower bound of count rate and the upper bound of error rate of single photon state signals. The numerical simulations show that secure key can also be generated, but the existing of DEM will reduce the secure key of practical decoy state QKD systems. The experiment parameter related security bound of DEM is also given out.
Graphical abstract

Similar content being viewed by others
References
C.H. Bennett, G. Brassard, Quantum cryptography: Public key distribution and coin tossing, in Proceedings of IEEE International Conference on Computers, Systems and Signal Processing, New York (1984), Vol. 175
B. Huttner, N. Imoto, N. Gisin, T. Mor, Phys. Rev. A 51, 1863 (1995)
V. Makarov, D.R. Hjelme, J. Mod. Opt. 52, 691 (2005)
V. Makarov, A. Anisimov, J. Skaar, Phys. Rev. A 74, 022313 (2006)
V. Makarov, J. Skaar, Quantum Inf. Comput. 8, 622 (2008)
B. Qi, C.-H.F. Fung, H.-K. Lo, X.F. Ma, Quantum. Inf. Comput. 7, 73 (2007)
Y. Zhao, C.-H.F. Fung, B. Qi, C. Chen, H.-K. Lo, Phys. Rev. A 78, 042333 (2008)
N. Gisin, S. Fasel, B. Kraus, H. Zbinden, G. Ribordy, Phys. Rev A 73, 022320 (2006)
N. Jain et al., New J. Phys. 16, 123030 (2014)
H. Weier et al., New J. Phys. 13, 073024 (2011)
C. Wiechers et al., New J. Phys. 13, 013043 (2011)
C.-H.F. Fung, B. Qi, K. Tamaki, H.-K. Lo, Phys. Rev. A 75, 032314 (2007)
F. Xu, B. Qi, H.-K. Lo, New J. Phys. 12, 113026 (2010)
A. Lamas-Linares, C. Kurtsiefer, J. Opt. Express 15, 9388 (2007)
W.-L. Wang, M. Gao, Z. Ma, J. Phys. A: Math. Theor. 46, 455301 (2013)
L. Lydersen et al., Nat. Photonics 4, 686 (2010a)
L. Lydersen et al., Opt. Express 18, 27938 (2010b)
S. Sauge, L. Lydersen, A. Anisimov, J. Skaar, V. Makarov, Opt. Express 19, 23590 (2011)
V. Makarov, New J. Phys. 11, 065003 (2009)
L. Lydersen, M.K. Akhlaghi, A.H. Majedi, J. Skaar, V. Makarov, New J. Phys. 13, 113042 (2011)
H.-W. Li et al., Phys. Rev. A 84, 062308 (2011)
S.-H. Sun, M.-S. Jiang, L.-M. Liang, Phys. Rev. A 83, 062331 (2011)
S.-H. Sun, M. Gao, M.-S. Jiang, C.-Y. Li, L.-M. Liang, Phys. Rev. A 85, 032304 (2012)
W.-T. Liu, S.-H. Sun, L.-M. Liang, J.-M. Yuan, Phys. Rev. A 83, 042326 (2011)
Y.-L. Tang et al., Phys. Rev. A 88, 22308 (2013)
S.-H. Sun, M.-S. Jiang, X.-C. Ma, C.-Y. Li, L.-M. Liang, Sci. Rep. 4 (2014)
W.Y. Hwang, Phys. Rev. Lett. 91, 057901 (2003)
H.-K. Lo, X.-F. Ma, K. Chen, Phys. Rev. Lett. 94, 230504 (2005)
X.-B. Wang, Phys. Rev. Lett. 94, 230503 (2005)
B. Qi, C.H. Fung, H.-K. Lo, X.-F. Ma, Quantum Inf. Comput. 7, 73 (2007)
N. Jain et al., Phys. Rev. Lett. 107, 110501 (2011)
Y.Y. Fei, X.-D. Meng, M. Gao, H. Wang, Z. Ma, Sci. Rep. 8 (2018)
C.-H.F. Fung, K. Tamaki, B. Qi, H.-K. Lo, X.F. Ma, Quantum Inf. Comput. 9, 131 (2009)
L. Lydersen, J. Skaar, Quantum Inf. Comput. 10, 60 (2010)
O. Marøy, L. Lydersen, J. Skaar, Phys. Rev. A 82, 032337 (2010)
P.M. Nielsen et al., J. Mod. Optics 48, 1921 2001
H.-K. Lo, M. Curty, B. Qi, Phys. Rev. Lett. 108, 130503 (2012)
T.F.D. Silva, G.C.D. Amaral, G.B. Xavier, G.P. Temporó, J.P.V.D. Weid, IEEE J. Sel. Top. Quantum Electron. 21, 167 (2014)
N. Gisin, G. Ribordy, W. Tittel, H. Zbinden, J. Rev. Mod. Phys. 74, 145 (2002)
N. Lütkenhaus, A. Shields, New J. Phys. 11, 045005 (2009)
V. Scarani et al., Rev. Mod. Phys. 81, 1301 (2009)
D. Gottesman, H.-K. Lo, N. Lutkenhaus, J. Preskill, Security of quantum key distribution with imperfect devices, in Proceedings International Symposium on IEEE on Information Theory 2004. ISIT 2004 (2004), p. 136
I. Csiszàr, J. Korner, IEEE Trans. Inf. Theory 24, 339 (1978)
U.M. Maurer, IEEE Trans. Inf. Theory 39, 733 (1993)
X.-F. Ma, B. Qi, Y. Zhao, H.-K. Lo, Phys. Rev. A 72, 012326 (2005)
C. Gobby, Z.-L. Yuan, A.J. Shields, Appl. Phys. Lett. 84, 3762 (2004)
Y.-Y. Fei, M. Gao, W.-L. Wang, C.-B. Li, Z. Ma, Phys. Rev. A 91, 052305 (2015)
Author information
Authors and Affiliations
Corresponding authors
Rights and permissions
About this article
Cite this article
Fei, Yy., Meng, Xd., Gao, M. et al. Practical decoy state quantum key distribution with detector efficiency mismatch. Eur. Phys. J. D 72, 107 (2018). https://doi.org/10.1140/epjd/e2018-90110-3
Received:
Revised:
Published:
DOI: https://doi.org/10.1140/epjd/e2018-90110-3