Abstract
In this paper, we develop task offloading and resource allocation scheme for unmanned aerial vehicle (UAV)-assisted mobile edge computing (MEC) system with channel estimation errors over Rician fading channels. The objective is to maximize the system utility with constrained network stability, transmit power, and data arrival rate. We consider a general multi-user UAV-assisted MEC system based on frequency division multiple access (FDMA), and we assume that the computation tasks are split into separate tasks and offloaded to the server for computing. We study stochastic computational resource management based on the Lyapunov optimization algorithm. The optimal transmit power and bandwidth allocation for computation offloading are obtained alternately, and the optimal computation task admission at each time slot and the optimal value of the auxiliary variable are derived. Simulation results verify the effectiveness of the proposed scheme in the paper and evaluate the influence of various parameters to the system performance.
Similar content being viewed by others
1 Introduction
With the emergence of various typical applications, e.g., virtual/augmented reality, vehicle networks, online games, and smart transportation, the user equipments (UEs) generate massive computation-intensive and delay-sensitive data tasks that need to be processed within a short time [1, 2]. The emerging applications, finite battery lives, and limited computation capacities pose more great challenges and more strict requirements on the quality of computation experience. In the future wireless communications, millions of portable devices will be installed around the base station [3–5]. Therefore, novel techniques have to be proposed to meet explosive computing needs and the growing demand for computing quality.
Mobile edge computing (MEC) and unmanned aerial vehicle (UAV) are two key promoters of 5G; both academia and industry have given sufficient attention in them currently. MEC has become as an effective solution to help UE deal with these computation-intensive tasks. Meanwhile, unmanned aerial vehicle-assisted MEC has attracted lots of research attention due to UAV’s mobility, flexibility, and maneuverability. Among the possible applications, the UAV-assisted MEC is especially important in disaster rescue and emergency response, which are in the absence of available terrestrial infrastructures [6–8].
Different from traditional cloud computing systems with long latency for data exchange, MEC enables an innovative architecture which aims to tackle conventional drawbacks by providing computation capabilities. A large number of computationally intensive tasks generated by mobile devices are offloaded to the MEC server, which can greatly increase the speed of data execution, and reduce execution costs and consumption. In recent years, there are some research papers about MEC systems. The authors derived local optimal scheme in [9] for a single user MEC system and aimed at minimizing local execution energy consumption. This framework was further developed in [10] and comprised a set of policies for controlling CPU cycles. The authors designed distributed computation offloading for solving both energy-and-latency minimization problems and investigated the execution cost minimization problem in effective MEC system [11, 12]. Considering the latency constraints of UE and the tradeoff between different resources, energy consumption minimization optimization was provided in computing systems [13–16]. In [16], the authors investigated heterogeneous network with multicore MEC server. The authors in [17] solved resource allocation stochastic optimization problem within data offloading. The energy consumption and delay constraint with respect to average queue length were investigated in [18]. Wang et al. [19] considered the total revenue of the network within content caching and formed an optimization problem. The authors designed a novel network of a multi-user scenario for optimizing user equipment data offloading and utilized the failure probability notion for the latency minimization problem [20, 21]. Optimal offloading schemes are obviously important to MEC, but some assumptions proposed by the current research have some limitations which assumed that the channel state information (CSI) is perfect and without considering randomness of data arrival.
The studies about UAV-enabled wireless communications have received more and more attention from scholars. Compared with conventional terrestrial communications, it is a potential technology for communication systems and novel network infrastructure in 5G systems due to its underlying applications in communication scenarios. UAV-assisted communication systems have some significant performance and advantages, such as cost savings, fast mobility, and higher line-of-sight (LoS) link probability between the UAV and the user. As a result, UAVs can be used as temporary relay nodes and temporary data hotspot area to establish fast and timely communication links, and can be quickly distributed to mobile users on the edge in a round flight attitude, carrying data offloaded from UEs to improve energy efficiency (EE). When terrestrial infrastructures are damaged or communication traffics are congested, UAVs equipped with computation capability can be quickly deployed as aerial computation servers to meet the temporary and unexpected demands.
The authors in [22] jointly optimized the UAV’s trajectory and transmit power for covert communications in terms of maximizing the average covert transmission rate. The authors in [23] investigated an energy-efficient UAV-aided cellular network and maximized the EE by jointly optimizing resource allocation and trajectory. It is foreseeable that the UAV-supported infrastructure in the application of MEC systems is worthy of study [24, 25]. UAV-supported MEC wireless-powered system with the computing rate maximization problems under the constraints of energy-harvesting and the UAV’s speed was proposed in [25]. The authors utilized UAV as energy transmitters to power ground mobile users and considered both two computing offloading modes. In [26], the authors studied the difference between the offloading of video data processed to a MEC server and the local execution of task data onboard UAVs. As a hypothetical use case for the platform, the authors demonstrated how to use UAVs for crowd surveillance based on facial recognition. In order to improve the MEC-UAV computing performance, Jeong et al. [27] designed a resource allocation scheme aimed at minimizing the total amount of mobile energy consumption, while meeting the service quality requirements of the offloaded mobile application. To achieve fair performance among users, the authors considered a multi-UAV system and put forward the joint power allocation [28, 29]. The author in [30] took ultra-reliable UAV as the research object, combined with relay communication to analyze the location optimization of the UAV and optimized the task block length with the constraint of delay. Path planning is an important part for UAV-aided MEC system [31, 32], and combining UAV with other technologies is also a research hotspot. In [33], the authors presented the optimization of the joint beamforming mechanism and UAV-assisted power allocation design aimed at maximizing the rate to improve the performance of the relay system. Based on the premise of increasing the service range of UAVs, the best deployment strategies of them were proposed. Then, the types of targets that can be served by UAVs were classified and investigated to maximize the number of flexible service and types of ground users [34–36].
In this paper, UAV-assisted MEC system with channel estimation errors over Rician fading channels is developed. We consider task offloading and resource allocation, and an online computational resource management using the Lyapunov optimization algorithm for multi-user MEC-UAV systems based on frequency division multiple access (FDMA) is proposed. We assume that the computing tasks that arrive at the mobile device are split into separate tasks, so that each device can offload it to the server for computing. We formulate the system utility maximization problem, subject to transmit power, data arrival rate, and network stability constraint under channel estimation error over Rician fading channels. Specifically, we can also derive the optimal amount of data reached by the mobile user at each time slot and the optimal value of the auxiliary variable and determine the optimal transmit power and bandwidth allocation for offloaded computing. Numerical results verify the correctness of the theoretical analysis and the effectiveness of the scheme proposed in the paper and prove the influence of various parameters on the system performance.
The rest of this paper is as follows. The methods and system model are introduced in Sections 2 and 3, respectively. The system utility maximization problem is formulated in Section 4. Computing data offloading and computational resource management based on the Lyapunov optimization algorithm are proposed in Section 5. Section 6 shows the simulation results, and we conclude this paper in Section 7.
2 Methods/experimental
We consider UAV-assisted multi-user MEC system with channel estimation error over Rician fading channels. The task offloading, power allocation, and bandwidth allocation are developed. An online computational resource management using the Lyapunov optimization algorithm based on FDMA for solving the system utility maximization problem is studied, subject to transmit power, data arrival rate, and network stability constraint. Specifically, we update the backlog of the data queue for UE as Qi(t) and the length of the task data for the server as C(t). The time-average system throughput in the long term is equal to \({\sum \nolimits }_{i\in U}{\overline {{{d}_{i}}}}\). With the assistance of the Lyapunov optimization technique, the complicated stochastic problem is transformed into continuous static optimization problems. The optimal data admission di(t)∗, the optimal value of the auxiliary variable δi(t)∗, and the optimal transmit power allocation pi(t)∗ and optimal bandwidth allocation αi(t)∗ are determined.
3 System model
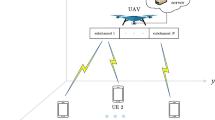
As shown in Fig. 1, we consider that the channels between UAV and UEs are line-of-sight channels and assume that the flight altitude of the UAV is fixed as a constant H(H>0). The system available bandwidth is WHz, and all UEs are equipped with single antenna. We denote the sets of UEs as U={1, 2, …, N}. Time is slotted and time slot length is τ. A three-dimensional (3D) Cartesian coordinate system is adopted. The UEs are distributed randomly each with a location ri=(xi,yi,0),∀i∈U. The UAV is located at position rv=(x,y,H). Specifically, dv,i is the distance between the UAV and UE, given by:
The UAV at a sufficiently high altitude is likely to establish LoS links with the ground UEs and also experiences small-scale fading due to rich scattering. Therefore, the channel between each UE and the UAV can be modeled as \({{h}_{i}}=\sqrt {\frac {{{h}_{0}}}{d_{v,i}^{2}}}{{h}_{r}}\) [10], where \({{{h}_{0}}}/{d_{v,i}^{2}}\;\) is the large-scale average channel power gain and h0 denotes the channel power gain at a reference distance d0=1 m. hr is the small-scale fading coefficient.
Due to the existence of the LoS path, the small-scale fading can be modeled by the Rician fading as follows:
where hl denotes the deterministic LoS channel component and hs is a zero-mean unit-variance circularly symmetric complex Gaussian (CSCG) random variable which denotes the random scattered component. k denotes the Rician factor.
We assume that hl and k are perfectly known at UAV. hs is estimated at receiver with minimum mean square error estimation and modeled as:
where \({{\hat {h}}_{s}}\) denotes the estimation of hs, and \({{\tilde {h}}_{s}}\) denotes the estimation error. \({{\hat {h}}_{s}}\) and \({{\tilde {h}}_{s}}\) are CSCG random variables with zero means and variances \(1-{{\tilde {\sigma }}^{2}},{{\tilde {\sigma }}^{2}}\), respectively. \({{\tilde {\sigma }}^{2}}\) is the estimation error variance, and the channel state information is perfect when \({{\tilde {\sigma }}^{2}}\text {=}0\).
Let \({{\hat {h}}_{r}}=\sqrt {\frac {k}{k+1}}{{h}_{l}}+\sqrt {\frac {1}{k+1}}{{\hat {h}}_{s}}\) [6], then \({{\tilde {h}}_{r}}=\sqrt {\frac {1}{k+1}}{{\tilde {h}}_{s}}\). Thus, we can get the received signal:
where pi(t) denotes the transmitting power of UE. N0 is the noise power spectral density. αi(t) is the proportion of bandwidth allocated to the ith user equipment and should satisfy:
The SNR can be given as:
With the Shannon theorem, the uplink capacity of ith UE in time slot t under imperfect CSI is:
Next, we will give computation task queueing models. Let Ai(t) (bits) denote the arrival data of UE at time slot t and with the maximum \(A_{i}^{\max }\). We assume that the task data arriving at each UE is following the Poisson distribution and the average data arrival rate is Amax, Ai(t)=τAmax. The UE may only allow part of data denoted by di(t) (bits) to arrive at time slot t and 0≤di(t)≤Ai(t). Let Qi(t) be the backlog of the data queue at ith UE, and it is updated as:
where \(B_{i}^{u}(t)\) denotes the amount of computing data tasks offloaded from the ith UE to MEC server and \(B_{i}^{u}(t)\text {=}\tau {{R}_{i}}(t)\).
The MEC server can execute one bit of computation task with Li CPU cycles. We denote \(f_{i}^{\mathrm {s}}(t)\) as server’s CPU-cycle frequency with the maximum \(f_{i}^{\max }\). The amount of data tasks actually offloaded from the UE to the MEC server is \(c_{i}^{m}(t)\) and \(c_{i}^{m}(t)=\min \{{{Q}_{i}}(t),B_{i}^{u}(t)\}\). The MEC server will store the data that has not been processed in the queue for subsequent processing. The length of the task data on the server side can be updated:
where \(F(t)=\tau \frac {f_{i}^{s}(t)}{{{L}_{i}}}\) denotes the amount of task queue that the server can execute at time slot t.
4 Problem formulation
The objective problem is maximizing the system utility while satisfying transmit power, data arrival rate, and network stability constraint under imperfect channel estimation over Rician fading. Thus, the system utility can be defined as:
where
defines the time average of stochastic process di(t). Particularly, \(\Phi (\overline {\mathbf {d}})\) is a concave logarithmic function. The total data admission \({\sum \nolimits }_{i\in U}{\overline {{{d}_{i}}}}\) is equal to the time-average system throughput in the long term [5].
We formulate the utility maximization problem P as:
where C1 is the constraint of data task arrival which ensures that the admitted data will not exceed the total amount of data arrived. C2 is the transmit power constraint, and C3 is the proportion of bandwidth constraint, respectively. Constraint C4 guarantees the stability of all queues.
As the description above, we can identify that P is a stochastic optimization problem as the arrived computation tasks and the queue backlogs are highly stochastic and unpredictable. Moreover, there are several variables including the optimal transmit power allocation and optimal bandwidth allocation for computation offloading, and the optimal computation task data admission at each time slot to be determined which are difficult to solve using generic optimization algorithm. Therefore, with the help of the Lyapunov optimization technique, this stochastic optimization problem can be resolved efficiently. The Lyapunov optimization is able to transform the complicated stochastic problem into continuous static optimization problems and eliminate time coupling of variables [35].
5 Online joint optimization algorithm
We use the Lyapunov optimization theory to equivalently reformulate problem P as P1:
where δi is the auxiliary variable. We define a device-specific virtual queue Gi(t), and we can reformulate C5 with the stability. It can be updated by:
Therefore, P1 can be rewritten as P2:
Next, we define a perturbed Lyapunov function of P2:
We define Δ(t) as the conditional Lyapunov drift:
where Θ(t)=[C(t),Qi(t),Gi(t),∀i∈U]. So we can get a drift-plus-penalty function as follows:
where V≥0 is a varied control parameter to achieve the tradeoff between the system utility and queue stability.
Lemma 1
For any queue backlogs and actions, ΔV(t) is upper bounded by:
where
Proof
Please see Appendix 1.
According to Lemma 1, we have converted the optimization problem P2 to solve for the minimum value of the right side (RHS) at each time slot. Therefore, the original stochastic optimization problem P1 has been transformed into solving continuous instantaneous static optimization problems. Decomposing (19) into several sub-problems:
□
Based on the above analysis, we can get the online joint optimization algorithm for di(t)∗, δi(t)∗,pi(t)∗, and αi(t)∗ of this paper, as summarized in Algorithm 1. In what follows, we will give the details about the optimization algorithm.

5.1 Optimal data admission
We find that the third and fifth terms of ΔVRHS(t) contain the task data arrival admission di(t). The decoupled sub-problem of minimizing data admission can be written as:
Thus, the optimal data admission decision can be given by:
5.2 Optimal auxiliary parameter
Due to the fact that the second and fifth terms of ΔVRHS(t) involve the auxiliary parameter δi(t), thus, the sub-problem of optimizing the auxiliary variable is given by:
We take the first order derivative with respect to δi(t), and we get \(\frac {\partial f\left ({{\delta }_{i}}(t) \right)}{\partial {{\delta }_{i}}(t)}={{G}_{i}}(t)-\frac {V}{\left (1+{{\delta }_{i}}(t) \right)\ln 2}\). Then, taking the second order derivative with respect to δi(t), \(\frac {{{\partial }^{2}}f\left ({{\delta }_{i}}(t) \right)}{{{\partial }^{2}}{{\delta }_{i}}(t)}=\frac {V}{{{\left (1+{{\delta }_{i}}(t) \right)}^{2}}\ln 2}\ge 0\). Since the objective function is convex, we make \(\frac {\partial f\left ({{\delta }_{i}}(t) \right)}{\partial {{\delta }_{i}}(t)}=0\). Thus, the optimal auxiliary parameter δi(t) is given as follows:
5.3 Optimal transmit power allocation and optimal bandwidth allocation
The third and fourth terms of ΔVRHS(t) involve the transmit power pi(t) and the bandwidth proportion αi(t); thus, the sub-problem is:
We define a new set for UE with:
and then the rest of UEs is defined as \({{\mathcal {U}}^{c}}(t)=U\backslash {{\mathcal {U}}^{s}}(t)\). As the bandwidth allocation cannot be zero, we assign a minimum value σ to αi(t). The sub-problem is transformed:
5.3.1 Optimal transmit power allocation
For a fixed proportion of bandwidth \(\left \{ {{\alpha }_{i}}(t), i\in {{\mathcal {U}}^{c}}(t) \right \}\), the optimal transmit power allocation optimization problem can be obtained:
Taking the first derivative of Ri(t) with respect to pi(t) we can get when Qi(t)≤C(t), the term [C(t)−Qi(t)]τRi(t) increases with the increasing of pi(t). Thus, the optimal transmit power is given by pi(t)∗=0. When Qi(t)≥C(t), the term [C(t)−Qi(t)]τRi(t) is non-increasing with pi(t); therefore, \({{p}_{i}}{{(t)}^{*}}=p_{i}^{\max }\) is the optimal transmit power. Intuitively, this means that only when the number of tasks in the task queue area of the user terminal is greater than the number of executable tasks in the task buffer of the MEC server, the computation tasks will be offloaded.
5.3.2 Optimal bandwidth allocation
For a fixed transmit power allocation \(\left \{ {{p}_{i}}(t), i\in {{\mathcal {U}}^{c}}(t) \right \}\), the bandwidth allocation can be obtained by solving the following problem:
We can find from (30) that the bandwidth allocation is more challenging as the αi(t) is coupled among different UEs. The Lagrange multiplier method is a classical analysis method for solving the extremum of a function under constraint conditions. It can transform the optimization problem containing constraints into an unconstrained problem.
According to the above, we can get the Lagrange function as follows:
where λ(t)≥0 is the Lagrange multiplier.
Based on the Karush-Kuhn-Tucker (KKT) conditions, we can get the following equation set:
Based on the above, if pi(t)h0=0, we define αi(t)=σ and there is no bandwidth allocation in this special case. If not, we can get that \(\frac {\mathrm {d}{{R}_{i}}(t)}{\mathrm {d}{{\alpha }_{i}}(t)}\) is inversely proportional to αi(t) and \(\underset {{{\alpha }_{i}}(t)\to +\infty }{\mathop {\lim }}\,\frac {\mathrm {d}{{R}_{i}}(t)}{\mathrm {d}{{\alpha }_{i}}(t)}=0,\underset {{{\alpha }_{i}}(t)\to {{0}^{+}}}{\mathop {\lim }}\,\frac {\mathrm {d}{{R}_{i}}(t)}{\mathrm {d}{{\alpha }_{i}}(t)}=+\infty \). Therefore, we can derive λ∗(t) over [λl(t),λu(t)] by the bisection search:
When \(\lambda (t)\text {=}\tilde {\lambda }(t)\), we define that \({{\mathcal {A}}_{i}}\left (\tilde {\lambda }(t) \right)\) is the root of \(\left [ C(t)-{{Q}_{i}}(t) \right ]\tau \frac {\mathrm {d}{{R}_{i}}(t)}{\mathrm {d}{{\alpha }_{i}}(t)}+\tilde {\lambda }(t)=0\). Therefore, we can further get the following equation set:
From the analysis above, the optimal bandwidth allocation is \(\alpha _{i}^{*}(t)={{\mathcal {A}}_{i}}\left ({{\lambda }^{*}}(t) \right)\) and the optimal Lagrangian multiplier λ∗(t) should satisfy:
As a summary, the procedure of the optimal bandwidth allocation \(\alpha _{i}^{*}(t)\) is summarized in Algorithm 2. Moreover, we can analyze the computation complexity of proposed algorithm, which is mainly from the optimization for bandwidth allocation. Given a solution accuracy ε1>0, ε2>0, the complexity of bisection method for λ∗(t) is \(\mathcal {O}(\log (1/{{\varepsilon }_{1}}))\) and the complexity for solving \({{\mathcal {A}}_{i}}(\tilde {\lambda }(t))\) is \(\mathcal {O}(\log (1/{{\varepsilon }_{2}}))\). For each iteration, the resource allocation complexity is \(\mathcal {O}(N)\). Therefore, the total computation complexity for our proposed optimization algorithm is \(\mathcal {O}(N\log (1/{{\varepsilon }_{1}})\log (1/{{\varepsilon }_{2}}))\).

5.4 Algorithm performance analysis
In this section, we will provide the gap between the optimal system utility achieved by the proposed online algorithm and the optimal value of the original problem, and give the bound of time-average queue length. We introduce the following theorem.
Theorem 1
Supposing there is a positive constant ξ, the proposed online algorithm has the following properties for any control parameter V≥0:
(a) The gap between the Φ∗ and Φopt is less than D/V, i.e.,
where Φ∗ is the optimal system utility achieved by the proposed online algorithm. Φopt is the optimum of system utility for problem P.
(b) The time-average queue length is upper bounded by:
Proof
Please see Appendix 2. □
Remark 1
The proposed algorithm optimizes and updates the transmit power allocation and bandwidth allocation alternately, which will converge to the optimal solution of problem P.
Theorem 1 shows that there exists a [O(1/V),O(V)] tradeoff between system utility and queue backlog (or the delay). According to Little’s law, the delay is proportional to the time-averaged queue length [35]. We can find that with the increase of V, the utility Φ∗ can gradually get closer to the optimum Φopt. In addition, the average queue length will grow linearly as shown in (41).
6 Simulation results and discussions
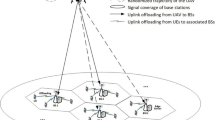
In this section, simulation results are presented to evaluate the effectiveness of proposed scheme and the effect of various parameters to system performance. We assume the height of the UAV is H=50 m. Unless otherwise stated, the simulation parameters are listed in Table 1. Mobile devices are located randomly at an equal distance of 150 m from the MEC server, and the position of UAV is at rv=[0,0,50]. The simulation scenarios of UAV-assisted MEC system are illustrated in Fig. 2. For the sake of simplicity, the unit of system throughput and the average queue length shown is “bits.” The corresponding simulation results are illustrated in Figs. 3, 4, 5, 6 and 7.
In Fig. 3, the results of the system throughput versus control parameter V under different channel estimation error \({{\tilde {\sigma }}^{2}}\) are shown. Based on the results, we find that the system throughput increases rapidly with the control parameter V and then starts to stabilize with the increasing of V. As the control parameter, V plays a tradeoff role in system throughput and queue length (or delay) so that the resources can be utilized more effectively. When V is less than a certain value, the system resources are allocated according to the existing mechanism. With the continuous increasing of V, the existence of estimation errors affects the change of transmit rate. But V controls the system throughput to remain stable for ensuring the effective queue arrival, and the data queue can be timely processed.
Furthermore, based on different estimation error variances, it is shown that the system throughput with smaller estimation error variance even \({{\tilde {\sigma }}^{2}}=0\) is higher than that with greater estimation error variance \({{\tilde {\sigma }}^{2}}=0.1\). The main reason is that the transmission rate is a decreasing function of the estimation error variance. Therefore, a large estimation error variance results in a small transmission rate and then reduces the system throughput and the system utility. This result also proves that the scheme is very effective for maximizing system utility under the premise of satisfying the long-term auxiliary parameter constraints.
In Fig. 4, the time-averaged queue length versus varied control parameter V under different estimation error variances is compared. The results illustrate that the time-averaged queue length is an increasing function with respect to control parameter V. Moreover, with an increasing of estimation error variance, the average queue length increases and the average system utility and throughput decreases which proves the long-term average queue stability and matches the results from Fig. 3. The time required for data transmission increases with the length of the queue. In other words, the CPU frequency of the server is much higher than the frequency required to provide data computing services for mobile devices under these circumstances and many computing resources provided by the server are wasted; these resources can be reallocated by other UEs.
Figure 5 gives the effect of average data arrival rate on system throughput under different estimation errors. It can be obviously observed that the system throughput increases as average data arrival rate Amax increases. When the estimation error variance is \({{\tilde {\sigma }}^{2}}=0\), the system throughput is much greater than that with \({{\tilde {\sigma }}^{2}}=0.1\). This follows the fact that the system throughput and utility is dominated by transmit rate which is decreasing with respect to estimation error under the same data arrival rate for a large control parameter V.
From Fig. 6, the average queue length versus the average data arrival rate under different estimation error variances is found. As illustrated in Fig. 6, the increasing in the average data arrival rate Amax will cause an increase in the average queue length on the user side, as expected. This is because as the average data arrival rate continues to increase, the corresponding transmission power and rate will also increase. In order to maintain the finite value of each user’s queue length while satisfying the queue length constraint, the system cannot transmit enough data tasks under the transmit power constraints that specifies UE transmit power and network stability, which results in a long backlog of data queues on the user side.
In order to evaluate the superiority of proposed optimization algorithm, we considered the existence of estimation error \({{\tilde {\sigma }}^{2}}=0.1\) and compare the time-averaged achievable rate under the proposed scheme, the equal power allocation scheme, and the equal bandwidth allocation scheme in Fig. 7. It is shown that the performance of our proposed scheme is superior to the other two allocation schemes. In addition, it also illustrates the significance of dynamic resource allocation to obtain a higher transmission rate during computation offloading in the case of task random arrival and the presence of estimation errors.
7 Conclusion
This paper developed task offloading and resource allocation scheme for UAV-enabled mobile edge computing system and considered the channel estimation error over Rician fading channels. The system utility maximization problem is formulated, subject to data arrival rate, transmit power, and network stability constraint. The computation task data can be divided into independent small tasks to facilitate the server’s computing. An online computational resource management using the Lyapunov optimization algorithm for multi-user MEC systems is considered. Based on the above, we obtain the optimal task data admission strategy for mobile devices and the optimal expression of the auxiliary variables based on the data arrival and determine the optimal transmit power and bandwidth allocation alternately. Simulation results verify the correctness and the effectiveness of the proposed scheme in the paper and validate the influence of various parameters to the system performance.
8 Appendix 1
For any a,b,c≥0, there holds
(max[a−b, 0]+c)2≤a2+b2+c2+2a(c−b). Therefore, we take squares on both sides of (8), (9), and (14):
Substituting (42)–(44) into (18), we can get the upper bound of D in Lemma 1:
Then, we replace all the expectations with the maximum of each variables and yield:
where \(R_{i}^{\max }\) and Fmax are the maximum of capacity Ri(t) and the amount of task queue F(t), respectively.
9 Appendix 2
From formula (19), we can get the minimum upper bound of ΔV(t):
where π is any feasible control policy for problem P. For θ>0, there exists at least one π∗
Plugging (48) into (47) and then taking a limit as θ→0 yields:
By taking expectation and using telescoping sums over {0,1,…,T−1}, we get:
Dividing (50) by VT, taking T→∞, and neglecting non-negative terms when appropriate, we can obtain:
Due to \({{\Phi }^{*}}\ge \frac {1}{T}\underset {T\to \infty }{\mathop {\lim }}\,{\sum \nolimits }_{t=0}^{T-1}{\mathbb {E}[\Phi (\delta (t))]}\) [5], we can get \({{\Phi }^{opt}}-{{\Phi }^{*}}\le \frac {D}{V}\).
Similarly, the proof about \(\underset {T\to \infty }{\mathop {\lim }}\,\frac {1}{T}{\sum \nolimits }_{t=0}^{T-1}{{\sum \nolimits }_{i=1}^{N}{{{Q}_{i}}(t)}}\le \frac {D+V({{\Phi }^{opt}-{\Phi }^{*}})}{\xi }\) can be found in [35].
Availability of data and materials
All the data and programs in this paper are available from the corresponding author on reasonable request.
Abbreviations
- UAV:
-
Unmanned aerial vehicle
- MEC:
-
Mobile edge computing
- FDMA:
-
Frequency division multiple access
- UE:
-
User equipment
- CSI:
-
Channel state information
- LOS:
-
Line-of-sight
- EE:
-
Energy efficiency
References
B. P. Rimal, D. P. Van, M. Maier, Mobile edge computing empowered fiber-wireless access networks in the 5G era. IEEE Commun. Mag.55(2), 192–200 (2017).
S. Wang, X. Zhang, Y. Zhang, et al., A survey on mobile edge networks: convergence of computing, caching and communications. IEEE Access. 5:, 6757–6779 (2017).
M. Chiang, T. Zhang, Fog and IoT: an overview of research opportunities. IEEE Internet Things J.3(6), 854–864 (2016).
A. U. R. Khan, M. Othman, S. A. Madani, et al., A survey of mobile cloud computing application models. IEEE Commun. Surv. Tutor.16(1), 393–413 (2014).
X. C. Lyu, W. Ni, H. Tian, et al., Optimal schedule of mobile edge computing for internet of things using partial information. IEEE J. Sel. Areas Commun.35(11), 2606–2615 (2017).
Q. H. Song, S. Jin, F. C. Zheng, in 2018 IEEE 87th Vehicular Technology Conference (VTC Spring). Joint power allocation and beamforming for UAV-enabled relaying systems with channel estimation errors (IEEE, 2018), pp. 1–5. https://doi.org/10.1109/VTCSpring.2018.8417734.
M. N. Nguyen, L. D. Nguyen, T. Q. Duong, H. D. Tuan, Real-time optimal resource allocation for embedded UAV communication systems. IEEE Wirel. Commun. Lett.8(1), 225–228 (2019).
J. Xia, Cache-aided mobile edge computing for b5g wireless communication networks. EURASIP J. Wirel. Commun. Netw.PP(99), 1–5 (2019).
W. Zhang, Y. Wen, K. Guan, D. Kilper, H. Luo, D. O. Wu, Energy-optimal mobile cloud computing under stochastic wireless channel. IEEE Trans. Wirel. Commun.12(9), 4569–4581 (2013).
C. You, R. Zhang, 3D trajectory optimization in Rician fading for UAV-enabled data harvesting. IEEE Trans. Wirel. Commun.18(6), 3192–3207 (2019).
X. Chen, L. Jiao, W. Li, X. Fu, Efficient multi-user computation offloading for mobile-edge cloud computing. IEEE Trans. Netw.24(5), 2795–2808 (2016).
Y. Mao, J. Zhang, S. H. Song, K. B. Letaief, Stochastic joint radio and computational resource management for multi-user mobile-edge computing systems. IEEE Trans. Wirel. Commun.16(9), 5994–6009 (2017).
S. Sardellitti, G. Scutari, S. Barbarossa, Joint optimization of radio and computational resources for multicell mobile-edge computing. IEEE Trans. Signal Inf. Process. Netw.1(2), 89–103 (2015).
O. Munoz, A. Pascual-Iserte, J. Vidal, Optimization of radio and computational resources for energy efficiency in latency-constrained application offloading. IEEE Trans. Veh. Technol.64(10), 4738–4755 (2015).
X. Cao, F. Wang, J. Xu, R. Zhang, S. Cui, Joint computation and communication cooperation for energy-efficient mobile edge computing. IEEE Internet Things J. 6(3), 4188–4200 (2019).
J. Zhao, Q. Li, Y. Gong, K. Zhang, Computation offloading and resource allocation for cloud assisted mobile edge computing in vehicular networks. IEEE Trans. Veh. Technol. 68(8), 7944–7956 (2019).
J. Kwak, Y. Kim, J. Lee, S. Chong, Dream: dynamic resource and task allocation for energy minimization in mobile cloud systems. IEEE J. Sel. Areas Commun.33(12), 2510–2523 (2015).
S. Mao, S. Leng, S. Maharjan, Y. Zhang, Energy efficiency and delay tradeoff for wireless powered mobile-edge computing systems with multi-access schemes. IEEE Trans. Wirel. Commun.19(3), 1855–1867 (2020).
C. Wang, C. Liang, F. R. Yu, Q. Chen, L. Tang, Computation offloading and resource allocation in wireless cellular networks with mobile edge computing. IEEE Trans. Wirel. Commun.16(8), 4924–4938 (2017).
C. G. Li, H. J. Yang, F. Sun, J. M. Cioffi, L. X. Yang, Multiuser overhearing for cooperative two-way multiantenna relays. IEEE Trans. Veh. Technol.65(5), 3796–3802 (2016).
J. Liu, Q. Zhang, Offloading schemes in mobile edge computing for ultra-reliable low latency communications. IEEE Access. 6:, 12825–12837 (2018).
X. B. Zhou, S. H. Yan, J. Hu, J. Sun, J. Li, F. Shu, Joint optimization of a UAV′s trajectory and transmit power for covert communications. IEEE Trans. Signal Process.67(16), 4276–4290 (2019).
M. Hua, Y. Wang, C. G. Li, Energy-efficient optimization for UAV-aided cellular offloading. IEEE Wirel. Commun. Letters.8(3), 769–772 (2019).
Y. Zeng, R. Zhang, T. J. Lim, Wireless communications with unmanned aerial vehicles: opportunities and challenges. IEEE Commun. Mag.54(5), 36–42 (2016).
F. H. Zhou, Y. P. Wu, R. Q. Y. Hu, et al., Computation rate maximization in UAV-enabled wireless-powered mobile-edge computing systems. IEEE J. Sel. Areas Commun.36(9), 1927–1941 (2018).
N. H. Motlagh, M. Bagaa, T. Taleb, UAV-based IoT platform: a crowd surveillance use case. IEEE Commun. Mag.55(2), 128–134 (2017).
S. Jeong, O. Simeone, J. Kang, Mobile edge computing via a UAV-mounted cloudlet: optimization of bit allocation and path planning. IEEE Trans. Veh. Technol.67(3), 2049–2063 (2018).
C. G. Li, F. Sun, J. M. Cioffi, L. X. Yang, Energy efficient MIMO relay transmissions via joint power allocations. IEEE Trans. Circ. Syst.61(7), 531–535 (2014).
Q. Wu, Y. Zeng, R. Zhang, Joint trajectory and communication design for multi-UAV enabled wireless networks. IEEE Trans. Wirel. Commun.17(3), 2109–2121 (2018).
C. Pan, H. Ren, Y. Deng, M. Elkashlan, A. Nallanathan, Joint blocklength and location optimization for URLLC-enabled UAV relay systems. IEEE Commun. Lett.23(3), 498–501 (2019).
Q. Liu, L. Shi, L. L. Sun, J. Li, M. Ding, F. Shu, Path planning for UAV-mounted mobile edge computing with deep reinforcement learning. IEEE Trans. Veh. Technol.69(5), 5723–5728 (2020).
Y. Qian, F. Wang, J. Li, L. Shi, K. Cai, F. Shu, User association and path planning for UAV-aided mobile edge computing with energy restriction. IEEE Wirel. Commun. Lett.8(5), 1312–1315 (2019).
J. Xu, Y. Zeng, R. Zhang, UAV-enabled wireless power transfer: trajectory design and energy optimization. IEEE Trans. Wirel. Commun.17(8), 5092–5106 (2018).
M. Alzenad, A. El-Keyi, H. Yanikomeroglu, 3-D placement of an unmanned aerial vehicle base station for maximum coverage of users with different QoS requirements. IEEE Wirel. Commun. Lett.7(1), 38–41 (2018).
M. J. Neely, Stochastic Network Optimization with Application to Communication and Queueing Systems (Morgan and Claypool, San Rafael, 2010).
C. G. Li, S. L. Zhang, P. Liu, F. Sun, Overhearing protocol design exploiting inter-cell interference in cooperative green networks. IEEE Trans. Veh. Technol.65(1), 441–446 (2016).
Funding
This work was supported in part by the National Natural Science Foundation of China (61571225, 61571224), in part by the Open Research Fund Key Laboratory of Wireless Sensor Network and Communication of Chinese Academy of Sciences (2017006), in part by the Postgraduate Research and Practice Innovation Program of Jiangsu Province (KYCX19 _0191), and in part by the Open Research Fund of Nanjing University of Aeronautics and Astronautics (KFJJ20190409).
Author information
Authors and Affiliations
Contributions
GW was the writer of this paper. XY gave crucial directions and modified this manuscript. GW proposed the main idea and analyzed it. FX and GW made the simulation tests. GW, XY, FX, and JC assisted in the review of this manuscript. All authors read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Wang, G., Yu, X., Xu, F. et al. Task offloading and resource allocation for UAV-assisted mobile edge computing with imperfect channel estimation over Rician fading channels. J Wireless Com Network 2020, 169 (2020). https://doi.org/10.1186/s13638-020-01780-8
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13638-020-01780-8