Abstract
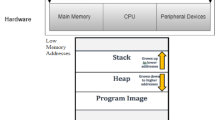
This article contributes to the field of operating-systems verification. It presents a formalization of virtual memory that extends to memory-mapped devices. Our formalization consists of a stack of three detailed formal memory models: physical memory (i.e., RAM), physically-addressable memory-mapped devices (including their respective side effects, access and alignment requirements), and page-table based virtual memory. Each model is formally shown to satisfy the plain-memory specification, a memory abstraction that enables efficient reasoning for type-correct programs. This stack of memory models was developed in an attempt to verify Nova, the Robin micro-hypervisor. It is a key component of our verification environment for operating-system kernels based on the interactive theorem prover PVS.
Similar content being viewed by others
References
Alkassar, E., Hillebrand, M.A., Leinenbach, D., Schirmer, N.W., Starostin, A.: The Verisoft approach to systems verification. In: Shankar, N., Woodcock, J. (eds.) Verified Software: Theories, Tools, Experiments Second International Conference, VSTTE 2008, Toronto, Canada, October 6–9, 2008, Proceedings. Lecture Notes in Computer Science, Toronto, Canada, vol. 5295, pp. 209–224. Springer, New York (2008)
Bevier, W.R.: Kit: a study in operating system verification. IEEE Trans. Softw. Eng. 15(11), 1382–1396 (1989)
Beyer, S., Jacobi, C., Kroening, D., Leinenbach, D., Paul, W.: Putting it all together: Formal verification of the VAMP. Int. J. Softw. Tools Technol. Transf. 8(4–5), 411–430 (2006)
Science Applications International Corporation: Green Hills Software INTEGRITY-178B Separation Kernel security target, ver. 1.0 (2008). Available from http://www.niap-ccevs.org/cc-scheme/st/st_vid10119-st.pdf. Retrieved February 11, 2009
Daum, M., Dörrenbächer, J., Wolff, B., Schmidt, M.: A verification approach for system-level concurrent programs. In: Woodcock, J., Shankar, N. (eds.) Verified Software: Theories, Tools, Experiments. Second International Conference, VSTTE 2008, Toronto, Canada, October 6–9, 2008, Proceedings. Lecture Notes in Computer Science, Toronto, Canada, vol. 5295, pp. 161–176. Springer, New York (2008)
Daum, M., Dörrenbächer, J., Bogan, S.: Model stack for the pervasive verification of a microkernel-based operating system. In: Beckert, B., Klein, G. (eds.) 5th International Verification Workshop (VERIFY’08). CEUR Workshop Proceedings, vol. 372, pp. 56–70. CEUR-WS.org (2008)
Hillebrand, M., In der Rieden, T., Paul, W.J.: Dealing with I/O devices in the context of pervasive system verification. In: 23nd IEEE International Conference on Computer Design: VLSI in Computers and Processors (ICCD 2005), 2-5 October 2005, San Jose, CA, USA, Proceedings, pp. 309–316. IEEE (2005)
Hillebrand, M.A., Paul W.J.: On the architecture of system verification environments. In: Yorav, K. (ed.) Hardware and Software: Verification and Testing, Third International Haifa Verification Conference, HVC 2007, Haifa, Israel, October 23–25, 2007, Proceedings. Lecture Notes in Computer Science, vol. 4899, pp. 153–168. Springer, New York (2008)
Hohmuth, M., Tews, H.: The semantics of C+ + data types: Towards verifying low-level system components. In: Basin, D., Wolff, B. (eds.) 16th International Conference on Theorem Proving in Higher Order Logics (TPHOLs 2003). Emerging Trends Proceedings, pp. 127–144. Institut für Informatik, Universität Freiburg (2003). Technical report no. 187
Hohmuth, M., Tews, H.: The VFiasco approach for a verified operating system. In: 2nd ECOOP Workshop on Programming Languages and Operating Systems (ECOOP-PLOS), Glasgow, UK (2005)
Härtig, H., Hohmuth, M., Feske, N., Helmuth, C., Lackorzynski, A., Mehnert, F., Peter M.: The Nizza secure-system architecture. In: First International Conference on Collaborative Computing: Networking, Applications and Worksharing, San Jose, California, USA (2005)
Huisman, M., Jacobs, B.: Java program verification via a Hoare logic with abrupt termination. In: Maibaum, T. (ed.) Fundamental Approaches to Software Engineering. Lecture Notes in Computer Science, vol. 1783, pp. 284–303. Springer, Berlin (2000)
IBM Systems: Virtualization, ver. 2, release 1 (2005). Available from http://publib.boulder.ibm.com/infocenter/eserver/v1r2/topic/eicay/eicay.pdf. Retrieved December 18, 2008
Intel Corporation, Denver, Colorado: Intel 64 and IA-32 Architectures Software Developer’s Manual (2007). Order Number: 25366[5-9]-023US
Intel Corporation: TLBs, Paging-Structure Caches, and Their Invalidation (2008). Application note 317080-002
ISO/IEC JTC1/SC22/WG21 C+ + Standards Committee: Programming Languages—C+ + (1998). ISO/IEC 14882:1998
Klein, G.: Operating system verification—an overview. Technical report NRL-955, NICTA, Sydney, Australia (2008)
Kolanski, R.: A logic for virtual memory. Electr. Notes Theor. Comput. Sci. 217 61–77 (2008)
Kolanski, R., Klein, G.: Mapped separation logic. In: Woodcock, J., Shankar, N. (eds.) Proceedings of VSTTE 2008—Verified Software: Theories, Tools and Experiments. Lecture Notes in Computer Science, vol. 5295, pp. 15–29. Toronto, Canada, Springer (2008). ISBN:978-3-540-87872-8
Norrish, M.: C formalised in HOL. Technical report UCAM-CL-TR-453. Computer Laboratory, University of Cambridge (1998)
Owre, S., Rajan, S., Rushby, J.M., Shankar, N., Srivas, M.: PVS: Combining specification, proof checking, and model checking. In: Alur, R., Henzinger, T.A. (eds.) Computer Aided Verification. Lecture Notes in Computer Science, vol. 1102, pp. 411–414. Springer, Berlin (1996)
Robin: Open robust infrastructures. Project webpage http://robin.tudos.org (2006)
Schirmer, N.: Verification of sequential imperative programs in Isabelle/HOL. PhD thesis, Technische Universität München (2006)
Tews, H.: Micro hypervisor verification: Possible approaches and relevant properties. In: NLUUG Voorjaarsconferentie 2007: Virtualisatie, pp. 96–109 (2007)
Tews, H., Weber, T., Völp, M.: A formal model of memory peculiarities for the verification of low-level operating-system code. In: Huuck, R., Klein, G.,Schlich, B. (eds.) Proceedings of the 3rd International Workshop on System Software Verification (SSV08). Electronic Notes in Theoretical Computer Science, vol. 217, pp. 79–96. Sydney (2008)
Tews, H., Weber, T., Poll, E., van Eekelen, M., van Rossum, P.: Formal Nova interface specification. Technical report ICIS–R08011, Radboud University Nijmegen (2008)
Tews, H., Weber, T., Völp, M., Poll, E., van Eekelen, M., van Rossum, P.: Nova micro–hypervisor verification. Technical report ICIS–R08012, Radboud University Nijmegen (2008)
Tuch, H.: Formal memory models for verifying C systems code. PhD thesis, University of NSW, Sydney 2052, Australia (2008)
Tuch, H.: Structured types and separation logic. Electr. Notes Theor. Comput. Sci. 217, 41–59 (2008)
Tuch, H., Klein, G.: A unified memory model for pointers. In: Sutcliffe, G., Voronkov, A. (eds.) 12th International Conference on Logic for Programming Artificial Intelligence and Reasoning (LPAR-12). Lecture Notes in Computer Science, vol. 3835, pp. 474–488. Jamaica (2005)
Tuch, H., Klein, G., Norrish, M.: Types, bytes, and separation logic. In: Hofmann, M., Felleisen, M. (eds.) Proc. 34th ACM SIGPLAN-SIGACT Symposium on Principles of Programming Languages (POPL’07), pp. 97–108. Nice, France (2007)
VFiasco: Verified Fiasco. Project webpage http://os.inf.tu-dresden.de/vfiasco (2001)
Völp, M., Courcambeck, S., Schwarz, C.: Final activity report. Robin project deliverable D.8, Technische Universität Dresden, Germany (2008)
Walker, B.J., Kemmerer, R.A., Popek, G.J.: Specification and verification of the UCLA Unix security kernel. Commun. ACM 23(2), 118–131 (1980)
Author information
Authors and Affiliations
Corresponding author
Additional information
This work has been supported by the European Union through PASR grant 104600.
Rights and permissions
About this article
Cite this article
Tews, H., Völp, M. & Weber, T. Formal Memory Models for the Verification of Low-Level Operating-System Code. J Autom Reasoning 42, 189–227 (2009). https://doi.org/10.1007/s10817-009-9122-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10817-009-9122-0