Abstract
We design a laboratory experiment in which an interested third party endowed with private information sends a public message to two conflicting players, who then make their choices. We find that third-party communication is not strategic. Nevertheless, a hawkish message by a third party makes hawkish behavior more likely while a dovish message makes it less likely. Moreover, how subjects respond to the message is largely unaffected by the third party’s incentives. We argue that our results are consistent with a focal point interpretation in the spirit of Schelling.

Similar content being viewed by others
Change history
11 April 2017
An erratum to this article has been published.
Notes
Ethnic conflict between the Tutsi and the Hutu continues to this day and played a major role in contributing to the Rwandan genocide (Mamdani 2014).
In a discussion of British colonial policy in India, Stewart (1951) quotes Brigadier John Coke as follows: “Our endeavor should be to uphold in full force the (fortunate for us) separation which exists between different religions and races, and not to endeavor to amalgamate them. Divide et empera should be the principle of the Indian Government.”
President Obama, in a 2010 address to the Parliament of India, has said: “I am mindful that I might not be standing before you today, as President of the United States, had it not been for Gandhi and the message he shared with America and the world.” President Jimmy Carter called Martin Luther King, Jr. “the conscience of his generation.”
We find other evidence against third party social preferences. Exploiting the observation that communication is uninformative, we derive equilibrium predictions about the effect of social preferences in both of our treatments. All else equal, social preferences toward the third party should lead to more hawkish behavior in the presence of a provocateur and less hawkish behavior in the presence of a peacemaker, compared to the baseline conflict game. While the presence of a peacemaker made hawkish behavior less likely, the presence of the provocateur had no effect on the likelihood of conflict. Moreover, even in the presence of social preferences, uninformative communication is disregarded in equilibrium. This is not what we observe in the data.
“[...] a third player with a payoff structure of his own who is given an influential role through his control over communication.” Schelling (1980, p. 144)
The control in McAdams and Nadler (2005) is a symmetric Hawk-Dove game with complete information which has two pure strategy Nash equilibria: (Hawk, Dove) and (Dove, Hawk). Their treatments are: (1) spinning a wheel which selects (Hawk, Dove) or (Dove, Hawk) with 50–50 chance in front of the subjects; (2) using an additional subject, called the leader, who opens an envelope containing a recommendation to either play (Hawk, Dove) or (Dove, Hawk); (3) same as (2) but with the leader publicly chosen as the highest scorer in a test.
In the experiment, the software approximated costs up to 3 decimal digits.
Does a country possess weapons of mass destruction? How much political will does a country have to engage in a conflict?
Baliga and Sjöström (2012) show that it is without loss of generality to assume that the third party’s message space contains only two messages, one of which makes Player 2 more likely to be hawkish.
The public nature of communication is crucial. If the provocateur communicated privately with each player, communication would necessarily be uninformative. To see this, first note that the provocateur would always send to Player 2 the message that maximizes the probability that Player 2 will choose the dovish action, which is commonly known to be the provocateur’s most preferred action by that player. As a result, private communication with Player 2 will be uninformative. Consequently, Player 1 will also ignore the provocateur’s message.
Recall that a babbling equilibrium always exists in cheap talk games.
Intuitively, when \(c_1\) is very high or very low, Player 1 has a strictly dominant strategy, and the provocateur cannot influence Player 1’s behavior. He will therefore send the message that is more likely to induce Player 2 to choose the dovish action. When \(c_1\) is in some intermediate range, the provocateur can potentially affect Player 1’s behavior. Note that he would only want to affect this behavior in the direction of being more hawkish. In this intermediate range, the provocateur will thus use his public announcement to induce Player 1 to be hawkish by provoking Player 2. As actions are strategic complements, an increase in the probability that Player 2 is hawkish will indeed lead Player 1 to best respond with a more hawkish stance.
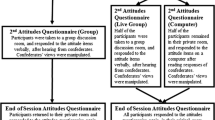
While we do not analyze behavior in the “two player after provocateur” and “two player after peacemaker” conditions, we collected this data to guarantee both consistency in the description of the experiment to the different subjects and also comparable earnings. In particular, participants in the sessions where the two player condition came first were told that the experiment will have a second half.
Specifically, the instructions stated: “We will provide you with instructions for the second part at the end of the first part of the experiment.”
The quiz tested the subjects’ understanding of the experiment with eight questions for the two player baseline and ten questions for the provocateur and peacemaker treatments. The quiz was administered only at the beginning of the first part of each session. For the second part of each session, subjects were given the new instructions with additional time to read them but no additional quiz. All the instructions for the experiment can be found in the Online Appendix.
\(n=1\) without a third party and \(n=2\) when a third party is present. This formulation makes the natural assumption that players care for their opponents’ payoffs equally.
As explained in detail in Sect. 4.1, we find that provocateurs do not communicate strategically.
Average earnings amounted to approximately 14 US dollars per subject at the time of the experiment. The minimum wage in Mexico is small, about 70 pesos per day. For a better reference point, consider that a 15km Uber ride from the house of one of the authors to the airport cost around 80 pesos at the time of the experiment.
Recall from the previous section that both uninformative equilibrium with social preferences and informative equilibrium without social preferences predict that the introduction of a provocateur increases the incidence of hawkish behavior.
In every instance the results of a Fisher’s exact test are reported in the text, the results are robust to estimating a logit regression with session clustered errors. I.e., none of our results rely on assuming that the observations are independent at the subject-decision level.
This is true regardless of whether we use independent, clustered, or boostrapped standard errors. We also get non-significant coefficients if we pool the first and second half of the data.
I.e., we get qualitatively and quantitatively similar results if we use a logit model with subject-level random effects or bootstrapped standard errors.
Role switching, which occurs in our experiment, has been shown to decrease social preferences in trust games (see, e.g., Burks et al. 2003). However, it cannot explain why behavior in each of the experimental conditions is consistent with social preferences of Player 1 and Player 2 toward each other.
Controlling for costs, we find that the latter P-value becomes statistically significant (\(P<0.01\)); the other statistical comparisons across Player 1 and Player 2 remain qualitatively similar to those reported in the preceding paragraph. We also find that Result 3 holds separately for Player 1 and Player 2. That is, if we look at the effect of the dovish message sender’s identity separately for Player 1 and Player 2, we find no significant effects (\(P>0.1\) in both cases). We discuss other robustness checks in Sect. 4.3 below.
Recall from Sect. 3 that the peacemaker’s message has no effect on behavior in equilibrium.
Charness (2000) employs a complete information version of the stag hunt game and finds that when one of the players sends a message before the actions are chosen, senders tend to send the dovish message most of the time and, conditional on receiving the dovish message, choose the dovish action with very high probability.
A player is a coordination type when his cost is between 10 and 85, in which case the hawkish action is a best response to a hawkish action and similarly for the dovish action.
The probability that a player is a coordination type is \(\approx\)0.789\(\left( =\frac{85-10}{95}\right)\) in all treatments of our experiment.
Similarly, a strategy that does not depend on Player 3’s observed costs might have appeared less biased than a strategy that does.
To the extent we observe treatment effects, these effects are insignificant.
Following experience with the two player game, subjects in the role of Player 1 and Player 2 did worse than predicted in the presence of the provocateur (\(P<0.1\)) and better than predicted in the presence of the peacemaker (\(P<0.01\)).
Recall that subjects were less hawkish than predicted in every treatment of the experiment.
References
Baliga, S., & Sjöström, T. (2012). The strategy of manipulating conflict. The American Economic Review, 102(6), 2897–2922.
Bland, J., & Nikiforakis, N. (2015). Coordination with third-party externalities. European Economic Review, 80, 1–15.
Blume, A., DeJong, D. V., Kim, Y. G., & Sprinkle, G. B. (2001). Evolution of communication with partial common interest. Games and Economic Behavior, 37, 79–120.
Brandts, J., & MacLeod, W. B. (1995). Equilibrium selection in experimental games with recommended play. Games and Economic Behavior, 11(1), 36–63.
Burks, S. V., Carpenter, J. P., & Verhoogen, E. (2003). Playing both roles in the trust game. Journal of Economic Behavior & Organization, 51(2), 195–216.
Cason, T. N., & Sharma, T. (2007). Recommended play and correlated equilibria: An experimental study. Economic Theory, 33(1), 11–27.
Charness, G. (2000). Self-serving cheap talk: A test of Aumann’s conjecture. Games and Economic Behavior, 33, 177–194.
Charness, G., & Rabin, M. (2002). Understanding social preferences with simple tests. Quarterly Journal of Economics, 177, 817–869.
Cooper, D., & Kagel, J. H. (2003). Lessons learned: Generalizing learning across games. The American Economic Review, 93(2), 202–207.
Fehr, E., & Schmidt, K. M. (1999). A theory of fairness, competition, and cooperation. Quarterly Journal of Economics, 114, 817–868.
Fischbacher, U. (2007). z-Tree: Zurich toolbox for ready-made economic experiments. Experimental Economics, 10, 171–178.
Galbiati, R., & Vertova, P. (2008). Obligations and cooperative behaviour in public good games. Games and Economic Behavior, 64(1), 146–170.
Levine, D. K. (1998). Modeling altruism and spitefulness in experiments. Review of Economic Dynamics, 1(3), 593–622.
Mamdani, M. (2014). When victims become killers: Colonialism, nativism, and the genocide in Rwanda. Princeton, NJ: Princeton University Press.
McAdams, R. H., & Nadler, J. (2005). Testing the focal point theory of legal compliance: The effect of third-party expression in an experimental hawk/dove game. Journal of Empirical Legal Studies, 2(1), 87–123.
Rankin, F. W., Van Huyck, J. B., & Battalio, R. C. (2000). Strategic similarity and emergent conventions: Evidence from similar stag hunt games. Games and Economic Behavior, 32(2), 315–337.
Rick, S., & Weber, R. A. (2010). Meaningful learning and transfer of learning in games played repeatedly without feedback. Games and Economic Behavior, 68, 716–730.
Schelling, T. C. (1980). The strategy of conflict. Cambridge, MA: Harvard University Press.
Stewart, N. (1951). Divide and rule: British policy in indian history. Science and Society, 15(1), 49–57.
Van Huyck, J. B., Gillette, A. B., & Battalio, R. C. (1992). Credible assignments in coordination games. Games and Economic Behavior, 4(4), 606–626.
Author information
Authors and Affiliations
Corresponding author
Additional information
The original version of this article was revised.
Piotr Evdokimov acknowledges the financial support of the Asociación Mexicana de Cultura A.C. Both authors thank the seminar participants at ITAM, Andrei Gomberg, Ryan Oprea, the editor, and two anonymous referees for useful comments.
An erratum to this article is available at https://doi.org/10.1007/s10683-017-9525-4.
Electronic supplementary material
Below is the link to the electronic supplementary material.
Rights and permissions
About this article
Cite this article
Evdokimov, P., Garfagnini, U. Third-party manipulation of conflict: an experiment. Exp Econ 21, 27–49 (2018). https://doi.org/10.1007/s10683-017-9523-6
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10683-017-9523-6