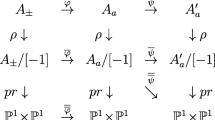Abstract
For a large class of functions \(f:\mathbb {F}_q\rightarrow E(\mathbb {F}_q)\) to the group of points of an elliptic curve \(E/\mathbb {F}_q\) (typically obtained from certain algebraic correspondences between E and \(\mathbb {P}^1\)), Farashahi et al. (Math Comput 82(281):491–512, 2013) established that the map \((u,v)\mapsto f(u)+f(v)\) is regular, in the sense that for a uniformly random choice of \((u,v)\in \mathbb {F}_q^2\), the elliptic curve point \(f(u)+f(v)\) is close to uniformly distributed in \(E(\mathbb {F}_q)\). This result has several applications in cryptography, mainly to the construction of elliptic curve-valued hash functions and to the “Elligator Squared” technique by Tibouchi (in: Christin and Safavi-Naini (eds) Financial cryptography. LNCS, vol 8437, pp 139–156. Springer, Heidelberg, 2014) for representating uniform points on elliptic curves as close to uniform bitstrings. In this paper, we improve upon Farashahi et al.’s character sum estimates in two ways: we show that regularity can also be obtained for a function of the form \((u,v)\mapsto f(u)+g(v)\) where g has a much smaller domain than \(\mathbb {F}_q\), and we prove that the functions f considered by Farashahi et al. also satisfy requisite bounds when restricted to large intervals inside \(\mathbb {F}_q\). These improved estimates can be used to obtain more efficient hash function constructions, as well as much shorter “Elligator Squared” bitstring representations.
Similar content being viewed by others
Notes
An interval in a not necessarily prime finite field \(\mathbb {F}_q\) is any subset of the form \(H + x[m,\dots ,m+k]\) where H is an additive subgroup of \(\mathbb {F}_q\), x an element of \(\mathbb {F}_q\), and m, k non negative integers (see [21, §4]) with \(k<p\).
An alternate definition frequently found in the literature differs from this one by a constant factor 1 / 2. That constant factor is irrelevant for our purposes.
For this to be well-defined, we of course need a family of random variables on increasingly large sets \(S_q\). Usual abuses of language apply.
References
Aranha D.F., Fouque P., Qian C., Tibouchi M., Zapalowicz J.: Binary Elligator Squared. In: Joux A., Youssef A.M. (eds.) SAC. LNCS, vol. 8781, pp. 20–37. Springer, Heidelberg (2014).
Bernstein D.J., Hamburg M., Krasnova A., Lange T.: Elligator: elliptic-curve points indistinguishable from uniform random strings. In: Sadeghi A., Gligor V.D., Yung M. (eds.) ACM CCS’13, pp. 967–980. ACM, New York (2013).
Boneh D., Franklin M.K.: Identity-based encryption from the Weil pairing. In: Kilian J. (ed.) CRYPTO. LNCS, vol. 2139, pp. 213–229. Springer, Berlin (2001).
Brier E., Coron J.S., Icart T., Madore D., Randriam H., Tibouchi M.: Efficient indifferentiable hashing into ordinary elliptic curves. In: Rabin T. (ed.) CRYPTO. LNCS, vol. 6223, pp. 237–254. Springer, Berlin (2010).
Castro F.N., Moreno C.J.: Mixed exponential sums over finite fields. Proc. Am. Math. Soc. 128(9), 2529–2537 (2000).
Cochrane T.: On a trigonometric inequality of Vinogradov. J. Number Theory 26(1), 9–16 (1987).
Cochrane T., Peral J.C.: An asymptotic formula for a trigonometric sum of Vinogradov. J. Number Theory 91(1), 1–19 (2001).
Couveignes J.M., Kammerer J.-G.: The geometry of flex tangents to a cubic curve and its parameterizations. J. Symb. Comput. 47(3), 266–281 (2012).
Couveignes J.M., Lercier R.: The geometry of some parameterizations and encodings. Adv. Math. Commun. 8(4), 437–458 (2014).
Farashahi R.R.: Hashing into Hessian curves. In: Nitaj A., Pointcheval D. (eds.) AFRICACRYPT. LNCS, vol. 6737, pp. 278–289. Springer, Heidelberg (2011).
Farashahi R.R., Shparlinski I.E., Voloch J.F.: On hashing into elliptic curves. J. Math. Cryptol. 3, 353–360 (2010).
Farashahi R.R., Fouque P.-A., Shparlinski I., Tibouchi M., Voloch J.F.: Indifferentiable deterministic hashing to elliptic and hyperelliptic curves. Math. Comput. 82(281), 491–512 (2013).
Fouque P.-A., Tibouchi M.: Deterministic encoding and hashing to odd hyperelliptic curves. In: Joye M., Miyaji A., Otsuka A. (eds.) Pairing. LNCS, vol. 6487, pp. 265–277. Springer, Berlin (2010).
Fouque P.-A., Tibouchi M.: Estimating the size of the image of deterministic hash functions to elliptic curves. In: Abdalla M., Barreto P.S.L.M. (eds.) LATINCRYPT. LNCS, vol. 6212 , pp. 81–91. Springer, Heidelberg (2010).
Fouque P.A., Tibouchi M.: Indifferentiable hashing to Barreto-Naehrig curves. In: Hevia A., Neven G. (eds.) LATINCRYPT. LNCS, vol. 7533, pp. 1–17. Springer, Heidelerg (2012).
Fried M.D.: Global construction of general exceptional covers. In: Mullen G.L., Shiue P.J. (eds.) Finite Fields: Theory, Applications, and Algorithms. Contemporary Mathematics, vol. 168, pp. 69–100. American Mathematical Society, Providence (1994).
Fouque P.-A., Joux A., Tibouchi M.: Injective encodings to elliptic curves. In: Boyd C., Simpson L. (eds.) ACISP. LNCS, vol. 7959, pp. 203–218. Springer, Heidelberg (2013).
Icart T.: How to hash into elliptic curves. In: Halevi S. (ed.) CRYPTO. LNCS, vol. 5677, pp. 303–316. Springer, Heidelberg (2009).
Iwaniec H., Kowalski E.: Analytic Number Theory, vol. 53. American Mathematical Society Colloquium Publications; American Mathematical Society, Providence (2004).
Kammerer J., Lercier R., Renault G.: Encoding points on hyperelliptic curves over finite fields in deterministic polynomial time. In: Joye M., Miyaji A., Otsuka A. (eds.) Pairing-Based Cryptography—Pairing 2010. Lecture Notes in Computer Science, vol. 6487, pp. 278–297. Springer, Heidelberg (2010).
Kohel D.R., Shparlinski I.: On exponential sums and group generators for elliptic curves over finite fields. In: Bosma W. (ed.) ANTS. LNCS, vol. 1838, pp. 395–404. Springer, Heidelberg (2000).
Lidl R., Niederreiter H.: Finite fields. Encyclopedia of Mathematics and Its Applications, vol. 20. Cambridge University Press, Cambridge, second edition, With a foreword by P. M. Cohn (1997).
Maurer U., Renner R., Holenstein C.: Indifferentiability, impossibility results on reductions, and applications to the random oracle methodology. In: Naor M. (ed.) TCC. LNCS, vol. 2951, pp. 21–39. Springer, Heidelberg (2004).
Peral J.C.: On a sum of Vinogradov. Colloquium Math. 60, 225–232 (1990).
Perel’muter G.I.: Estimation of a sum along an algebraic curve. Mat. Zametki 5, 373–380 (1969).
Rosen M.: Number Theory in Function Fields. Graduate Texts in Mathematics, vol. 210. Springer, New York (2002).
Sato H., Hakuta K.: An efficient method of generating rational points on elliptic curves. J. Math. Ind. 1(A), 33–44 (2009).
Shallue A., van de Woestijne C.: Construction of rational points on elliptic curves over finite fields. In: Hess F., Pauli S., Pohst M.E. (eds.) ANTS. LNCS, vol. 4076, pp. 510–524. Springer, Heidelberg (2006).
Skałba M.: Points on elliptic curves over finite fields. Acta Arith. 117, 293–301 (2005).
Tibouchi M.: Elligator Squared: Uniform points on elliptic curves of prime order as uniform random strings. In: Christin N., Safavi-Naini R. (eds.) Financial Cryptography. LNCS, vol. 8437, pp. 139–156. Springer, Heidelberg (2014).
Tibouchi M.: Impossibility of surjective Icart-like encodings. In: Chow S.S.M., Liu J.K., Hui L.C.K., Yiu S. (eds.) ProvSec. LNCS, vol. 8782, pp. 29–39. Springer, Heidelberg (2014).
Ulas M.: Rational points on certain hyperelliptic curves over finite fields. Bull. Pol. Acad. Sci. Math. 55(2), 97–104 (2007).
Acknowledgments
We are grateful to Igor Shparlinski for fruitful comments and discussions, and to anonymous reviewers for numerous useful comments.
Author information
Authors and Affiliations
Corresponding author
Additional information
This is one of several papers published in Designs, Codes and Cryptography comprising the “Special Issue on Coding and Cryptography”.
Rights and permissions
About this article
Cite this article
Tibouchi, M., Kim, T. Improved elliptic curve hashing and point representation. Des. Codes Cryptogr. 82, 161–177 (2017). https://doi.org/10.1007/s10623-016-0288-2
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10623-016-0288-2