Abstract
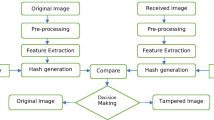
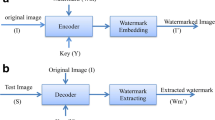
The accumulating and proliferating of the internet has increased ten folds from the year 2010 to 2020 according to the Ericsson report [58]. This trend is further increasing, making the transmission of multimedia much easier. However, the impetuous growth of data breaches and manipulations in multimedia has become a matter of concern. In such a scenario the main concern is the security of multimedia data besides protecting its integrity and authenticity. In this work, a new approach utilizing hashing and watermarking has been proposed for tamper detection and localization of digital images. At first, the original cover image is segmented into 4 × 4 non-overlapping blocks. For each 4 × 4 block, Discrete Cosine Transform (DCT) is applied to extract the DC coefficients. Further, a hash is generated from these coefficients using the SHA-256 hash function. The original cover image is Arnold Transformed and then segmented into 4 × 4 blocks to embed the extracted hash (16 bits in each block). Afterward, Inverse Arnold Transform is applied to obtain the watermarked image. The proposed approach is found to be resistant to different image processing attacks, copy-paste attacks, and copy-move attacks. Moreover, the average PSNR value of 51.16 dB along with the average SSIM value of 0.9965 has been reported for the presented scheme that is higher compared to already existing schemes. Also, the average FPR value for random tampering is found to be 4.6986 that is better compared to the state-of-the-art technique. The scheme can detect and localize the tamper more efficiently compared to the existing schemes making it a competent contender for the said purpose.













Similar content being viewed by others
References
Azeroual A, Karim A. Real-time image tamper localization based on fragile watermarking and Faber-Schauder wavelet. AEU Int J Electron Commun. 2017;79:207–18.
Gull S, Mansour RF, Aljehane NO, Parah SA. A self-embedding technique for tamper detection and localization of medical images for smart-health. Multimed Tools Appl. 2021;80(19):29939–64.
Singh K. Data Hiding: Current Trends, Innovation and Potential Challenges. ACM Trans Multimed Comput Commun Appl 16, 3s, Article 101 2021;16. https://doi.org/10.1145/3382772
Gull S, Parah SA, Khan M. Reversible data hiding exploiting Huffman encoding with dual images for IoMT based healthcare. Comput Commun. 2020;163:134–49.
Anand A, Singh AK. Cloud based secure watermarking using IWT-Schur-RSVD with fuzzy inference system for smart healthcare applications. Sustain Cities Soc. 2021;75:103398, ISSN 2210–6707. https://doi.org/10.1016/j.scs.2021.103398.
Feng B, et al. A novel semi-fragile digital watermarking scheme for scrambled image authentication and restoration. Mob Netw Appl. 2020;25:82–94. https://doi.org/10.1007/s11036-018-1186-9.
Hurieb ESB, Gutub AA. Enhancing Medical Data Security via Combining Elliptic Curve Cryptography with 1-LSB and 2-LSB Image Steganography. Int J Comput Sci Netw Secur (IJCSNS). 2020;20(12):232–41.
Singh OP, Singh AK. A robust information hiding algorithm based on lossless encryption and NSCT-HD-SVD. Mach Vis Appl. 2021;32:101. https://doi.org/10.1007/s00138-021-01227-0.
Mahto DK, Sing AK. A survey of color image watermarking: State-of-the-art and research directions. Comput Electr Eng. 2021;93:107255, ISSN 0045–7906. https://doi.org/10.1016/j.compeleceng.2021.107255
Gutub AA. Regulating Watermarking Semi-Authentication of Multimedia Audio via Counting-Based Secret Sharing. Pamukkale Univ J Eng Sci. 2021.
Fan M, Wang H. An enhanced fragile watermarking scheme to digital image protection and selfrecovery. Signal Process Image Commun. 2018;66:19–29. https://doi.org/10.1016/j.image.2018.04.003.
Qin C, et al. Self-embedding fragile watermarking based on reference-data interleaving and adaptive selection of embedding mode. Inf Sci. 2016;373:233–50.
Gutub AA, Al-Shaarani F. Efficient Implementation of Multi-image Secret Hiding Based on LSB and DWT Steganography Comparison. Arab J Sci Eng. 2020;45:2631–44. https://doi.org/10.1007/s13369-020-04413-w.
Norah A, Gutub AA. Simulating Light-Weight-Cryptography Implementation for IoT Healthcare Data Security Applications. Int J E Health Medical Commun. 2019;10:1–15.
Qin C, et al. Fragile image watermarking with pixel-wise recovery based on overlapping embedding strategy. Signal Process. 2017;138:280–93.
Hurrah NN, et al. Dual watermarking framework for privacy protection and content authentication of multimedia. Futur Gener Comput Syst. 2018. https://doi.org/10.1016/j.future02018.12.036.
Gong X, et al. A secure image authentication scheme based on dual fragile watermark. Multimedia Tools and Applications. 2020;79(25):18071–88.
Hussan M, et al. Tamper Detection and Self-Recovery of Medical Imagery for Smart Health. Arab J Sci Eng. 2021;1–17. https://doi.org/10.1007/s13369-020-05135-9AJSE-D-20-03588R1.
Hassan FS, Gutub AA. Efficient Image Reversible Data Hiding Technique Based on Interpolation Optimization. Arab J Sci Eng (AJSE). 2021;46(9):8441–56.
Zhang X, Yangyang X, Zhongmeng Z. Self-embedding fragile watermarking based on DCT and fast fractal coding. Multimed Tools Appl. 2015;74(15):5767–86.
Loan NA, et al. Secure and robust digital image watermarking using coefficient differencing and chaotic encryption. IEEE Access. 2018;6:19876–97.
Hong W, Chen M, Chen TS. An efficient reversible image authentication method using improved PVO and LSB substitution techniques. Signal Process Image Commun. 2017;58:111–22.
Nazari M, Sharif A, Mollaeefar M. An improved method for digital image fragile watermarking based on chaotic maps. Multimed Tools Appl. 2017;76(15):16107–23.
Singh AK, Kumar B, Singh G, Mohan A. Robust and secure multiple watermarking technique for application in tele-ophthalmology. In: Med Image Watermarking, Springer. 2017;159–173.
Pandey R, Singh AK, Kumar B, Mohan A. Iris based secure NROI multiple eye image watermarking for teleophthalmology. Multimed Tools Appl. 2016;75(22):14381–97.
Kunhu A, Al-Ahmad H, Mansoori SA. A reversible watermarking scheme for ownership protection and authentication of medical images. In: 2017 Int Conf Electr Comput Technol Appl (ICECTA). 2017;1–4.
Trivedy S, Pal AK. A logistic map-based fragile watermarking scheme of digital images with tamper detection. Iran J Sci Technol Trans Electr Eng. 2017;41(2):103–13.
Hurrah NN, Parah SA, Sheikh JA. Embedding in medical images: an efficient scheme for authentication and tamper localization. Multimed Tools Appl. 2020;79:21441–70. https://doi.org/10.1007/s11042-020-08988-2.
Hassan FS, Gutub AA. Improving data hiding within colour images using hue component of HSV colour space. CAAI Transact Intel Technol. 2021.
Li Z, et al. Rank-Constrained Spectral Clustering With Flexible Embedding. IEEE Transact Neural Netw Learn Syst. 2018;29(12):6073–82. https://doi.org/10.1109/TNNLS.2018.2817538.
Li Z, et al. Dynamic Affinity Graph Construction for Spectral Clustering Using Multiple Features. IEEE Transact Neural Netw Learn Syst. 2018;29(12):6323–32. https://doi.org/10.1109/TNNLS.2018.2829867.
Lin PL, Hsieh CK, Huang PW. A hierarchical digital watermarking method for image tamper detection and recovery. Pattern Recogn. 2005;38(12):2519–29. https://doi.org/10.1016/j.patcog.2005.02.007.
Shehab A, et al. Secure and robust fragile watermarking scheme for medical images. IEEE Access. 2018;6:10269–78.
Singh D, Singh SK. Effective self-embedding watermarking scheme for image tampered detection and localization with recovery capability. J Vis Commun Image Represent. 2016;38:775–89.
Naskar R, Chakraborty RS. A generalized tamper localization approach for reversible watermarking algorithms. ACM Trans Multimed Comput Commun Appl. 2013;9(3), 19:1–19:22.
Hsu CS, Tu SF. Image tamper detection and recovery using adaptive embedding rules. Measurement. 2016;88:287–96. https://doi.org/10.1016/j.measurement.2016.03.053.
Tiwari A, Sharma M, Tamrakar RK. Watermarking based image authentication and tamper detection algorithm using vector quantization approach. AEU Int J Electron Commun. 2017;78:114–23.
Rajput V, Ansari IA. Image tamper detection and self-recovery using multiple median watermarking. Multimed Tools Appl. 2019. https://doi.org/10.1007/s11042-019-07971-w.
Cao F, An B, Wang J, Ye D, Wang H. Hierarchical recovery for tampered images based onwatermark self-embedding. Displays. 2017;46:52–60.
Sarreshtedari S, Akhaee MA. A source-channel coding approach to digital image protection and self-recovery. IEEE Trans Image Process. 2015;24(7):2266–77.
Zhao X, Bateman P, Ho AT. Image authentication using active water marking and passive forensics techniques. In: Analysis M, editor. Process Commun. Springer-Verlag, Berlin: Heidelberg. 2011;139–83.
Lee TY, Lin SD. Dual watermark for image tamper detection and recovery. Pattern Recognit. 2008;41(11):3497–506.
Huang SC, Jiang CF. A color image authentication and recovery method using block truncation code embedding. J Mar Sci Technol. 2012;20(1):49–55.
Chuang JC, Hu YC. An adaptive image authentication scheme for vector quantization compressed image. J Vis Commun Image Represent. 2011;22(5):440–9.
He H, Zhang J, Tai HM. A wavelet-based fragile watermarking scheme for secure image authentication. In international workshop on digital watermarking Springer, Berlin, Heidelberg 2006;422- 432.
Lu H, Shen R, Chung FL. Fragile watermarking scheme for image authentication. Electron Lett. 2003;39(12):898–900.
Peng Y, Niu X, Fu L, Yin Z. Image authentication scheme based on reversible fragile watermarking with two images. J Inf Secur Appl. 2018;40:236–46.
Gull S, Loan NA, Parah SA. An efficient watermarking technique for tamper detection and localization of medical images. J Ambient Intell Humaniz Comput. 2018;2018:1799–808. https://doi.org/10.1007/s12652-018-1158-8.
Singh P, Agarwal S. A self-recoverable dual watermarking scheme for copyright protection and integrity verification. Multimed Tools Appl. 2017;76(5):6389–428.
Ansari IA, Pant M, Ahn CW. SVD based fragile watermarking scheme for tamper localization and self-recovery. Int J Mach Learn Cybern. 2016;7(6):1225–39.
Bravo-Solorio S, Calderon F, Li CT, Nandi AK. Fast fragile watermark embedding and iterative mechanism with high self-restoration performance. Digital Signal Process. 2018;73:83–92.
Parah SA, et al. Information hiding inmedical images: a robust medical image watermarking system forE-healthcare. Multimed Tools Appl. 2017;76(8):10599–633.
Eswaraiah R, Reddy ES. Medical image watermarking technique for accuratetamper detection in ROI and exact recovery of ROI. Int J Telemed Appl. 2014;2014:13.
Bhalerao S, Ansari IA, Kumar AA. Secure image watermarking for tamper detection and localization. J Ambient Intell Humaniz Comput. 2020;12:1057–68. https://doi.org/10.1007/s12652-020-02135-3.
Prasad S, Pal AK. A tamper detection suitable fragile watermarking scheme based on novel payload embedding strategy. Multimed Tools Appl. 2020;79:1673–705. https://doi.org/10.1007/s11042-019-08144-5.
L University. UCID Image Dataset. http://homepages.lboro.ac.uk/cogs/datasets/ucid/data/ucid.v2.tar.gz. (Accessed: 24 Aug, 2020).
Kodak image dataset. http://r0k.us/graphics/kodak. (Accessed: 7 june 2021).
https://www.ericsson.com/en/press-releases/2020/6/ericsson-mobility-report---june-2020. (Accessed: 23 Aug 2021).
Jan A, et al. Secure data transmission in IOTs based on CLOG edge detection. Future Geeration Comput Syst. 121:59–73. (Accessed: 8 April 2021).
Funding
This work is not supported by any funding.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Informed consent
NA.
Conflicts of interest
The authors do not have any conflict of interest.
Research involving human participants and/or animals
NA.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Hussan, M., Parah, S.A., Jan, A. et al. Hash-based image watermarking technique for tamper detection and localization. Health Technol. 12, 385–400 (2022). https://doi.org/10.1007/s12553-021-00632-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12553-021-00632-9