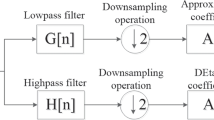
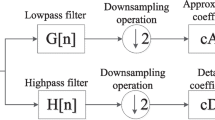
Abstract
More than ever, the practical and accurate watermarking technologies are called for the growing amount of exchanged digital image over the Internet. To protect the integrity and authenticity of digital image and to enhance the effect of tamper detection and restoration, we design and implement a semi-fragile watermark based on cat transformation, mostly used to locate tamper and recover for the transformed image and plain-image. The watermark which consists of two parts: the authentication watermark and recovery watermark, is embedded into the 2 least significant bit (LSB) of the pixel of the original image. The authentication watermark is calculated by the pixel value comparison and the parity check code, while the recovery watermark contains the average pixel value of the Torus image block. In the detection side, we use the hierarchy concept to locate the tamper in three layers and recover the attacked image in two layers. By using the hierarchy concept, this algorithm has another superiority that tamper can be detected on confused image. The experimental results show that our algorithm can accurately locate tamper and realize the content recovery and effectively prevent the vector quantization attack. Compared with other algorithms, this algorithm has better effect of tamper location and recovery.











Similar content being viewed by others
References
Cox IJ, Kilian J, Leighton FT, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
Cox I, Miller M, Bloom J, Fridrich J, Kalker T (2007) Digital watermarking and steganography. Morgan Kaufmann, Burlington
Song C, Sudirman S, Merabti M (2012) A robust region-adaptive dual image watermarking technique. J Vis Commun Image Represent 23(3):549–568
Barni M, Bartolini F (2004) Watermarking systems engineering: enabling digital assets security and other applications. Marcel Dekker, New York
Min W, Bede L (2003) Data hiding in image and video I Fundamental issues and solutions. IEEE Trans Image Process 12(6):685–695
Watson AB (1993) DCT Quantization matrices visually optimized for individual images. Proc SPIE Human Vis Vis Process Digit Display 9:202–216
Mohan BC, Kumar SS (2008) Robust digital watermarking scheme using contourlet transform. Int J Comput Sci Netw Security 8(2):43–51
Giakoumaki A, Pavlopoulos S, Koutouris D (2003) A medical image watermarking scheme based on wavelet transform. In: Proc 25th Annu Int Conf IEEE Eng Med Biol Soc, pp 856–859
Sadreazami H, Ahmad MO, Swamy MNS (2014) A study of multiplicative watermark detection in the contourlet domain using alpha-stable distributions. IEEE Trans Image Process 23(10):4348–4360
Karybali IG, Berberidis K (2006) Efficient spatial image watermarking via new perceptual masking and blind detection schemes. IEEE Trans Inf Forensics Security 1(2):256–274
Zeki AM, Manaf AA (2011) ISB Watermarking embedding: block based model. Inf Technol J 10(4):841–848
Emami MS, Sulong GB, Seliman SB (2012) An approximation approach for digital image owner identification using histogram intersection technique. Int J Innov Comput Inf Control 8(7):4605–4620
Wang Y, Pearmain A (2004) Blind image data hiding based on self reference. Pattern Recogn Lett 25 (15):1681–1689
Bhatnagar G, Wu QMJ, Raman B (2012) A new robust adjustable logo watermarking scheme. Comput Secur 31(1):40–58
Patra JC, Phua JE, Bornand C (2010) A novel DCT domain CRT-based watermarking scheme for image authentication surviving JPEG compression. Digit Signal Process 20(6):1597–1611
Su Q, Niu Y, Zou H, Liu X (2013) A blind dual color images watermarking based on singular value decomposition. Appl Math Comput 219(16):8455–8466
Su Q, Niu Y, Wang G, Jia S, Yue J (2014) Color image blind watermarking scheme based on QR decomposition. Signal Process 94:219–235
Zhu X, Ding J, Dong H, Hu K, Zhang X (2014) Normalized correlation-based quantization modulation for robust watermarking. IEEE Trans Multimedia 16(7):1888–1904
Horng S-J, Rosiyadi D, Li T, Takao T, Guo M, Khan MK (2013) A blind image copyright protection scheme for e-government. J Vis Commun Image Represent 24(7):1099–1105
Shen J-J, Hsu P-W (2007) A robust associative watermarking technique based on similarity diagrams. Pattern Recognit 40(4):1355–1367
Andalibi M, Chandler DM (2015) Digital image watermarking via adaptive logo texturization. IEEE Trans Image Processs 24(12):5060–5073
Barni M, Bartolini F, Piva A (2001) Improved wavelet-based watermarking through pixel-wise masking. IEEE Trans Image Process 10(5):783–791
Chang CS, Shen JJ (2017) Features classification forest: a novel development that is adaptable to robust blind watermarking techniques[J]. IEEE Transactions on Image Processing A Publication of the IEEE Signal Processing Society PP(99):1–1
Urvoy M, Goudia D, Autrusseau F (2014) Perceptual DFT watermarking with improved detection and robustness to geometrical distortions[J]. IEEE Trans Inf Forensics Secur 9(7):1108– 1119
Voloshynovskiy S, Pereira S, Pun T, Eggers JJ, Su JK (2001) Attacks on digital watermarks: classification, estimation based attacks, and benchmarks. IEEE Commun Mag 39(8):118–126
Blum L, Blum M, Shub M (1986) A Simple unpredictable pseudorandom number generator. SIAM J Comput 15(2):364–383
Celik MU (2002) Hierarchical watermarking for secure image authentication with localization [J]. IEEE Trans Image Process. 11(6):585–595
Wong PW, Memon N (2002) Secret and public key authentication schemes that resist vector quantization attack[A]. In: Proc of SPIE security and watermarking of multimedia[C]. San Jose, USA, pp 1593–1601
Hore A, Ziou D (2010) Image quality PSNR vs. SSIM[c]. In: International conference on pattern recognition, IEEE, 2366– 2369
Huang DZ, Chen ZG, Zhu CX (2008) Image spatial domain watermark algorithm based on general Arnold mapping and neural network[J]. Appl Res Comput 25(4):1144–1146
Shao L, Qin Z, Xingchen H (2007) Algorithm of spatial domain image watermark based on scrambling transformation of image[J]. Comput Eng 33(2):122–124
Celik MU, et al. (2002) Hierarchical watermarking for secure image authentication with localization. IEEE Transactions on Image Processing A Publication of the IEEE Signal Processing Society 11(6):585
Cox IJ, Kilian J, Leighton FT, et al. (1997) Secure spread spectrum watermarking for multimedia[J]. IEEE Transactions on Image Processing A Publication of the IEEE Signal Processing Society 6(12):1673–1687
Rota GC (1990) Geometrical methods in the theory of ordinary differential equations : V. I. Arnold, 2nd ed. Springer, 1988, 351 pp[J]. Adv Mater 80(2):269–269
Qiu T, Zhao A, Xia F, Si W, Wu. DO (2017) ROSE: Robustness strategy for scale-free wireless sensor networks. IEEE/ACM Trans Netw 25(5):2944–2959
Qiu T, Qiao R, Han M, Sangaiah AK, Lee I (2017) A lifetime-enhanced data collecting scheme for internet of things. IEEE Commun Mag 55(11):132–137
Qiu T, Zheng K, Han M, Philip Chen CL, Xu M (2017) A data-emergency-aware scheduling scheme for internet of things in smart cities. IEEE Transactions on Industrial Informatics. https://doi.org/10.1109/TII.2017.2763971
Guo C, Chen X, Jie YM, et al. (2017) Dynamic multi-phrase ranked search over encrypted data with symmetric searchable encryption. IEEE Transactions on Services Computing, published online. https://doi.org/10.1109/TSC.2017.2768045
Guo C, Luo NQ, Alam Bhuiyan MZ, et al. (2017) Key-aggregate authentication cryptosystem for data sharing in dynamic cloud storage. Future Generation Computer Systems, published online. https://doi.org/10.1016/j.future.2017.07.038
Guo C, Zhuang RH, Jie YM, et al. (2016) Fine-grained database field search using attribute-based encryption for E-Healthcare clouds. J Med Syst 40(11):235;1–235:8
Acknowledgements
This paper is supported by the National Science Foundation of China under grant No.61401060, 61501080, 61572095 and 61771090, the Fundamental Research Funds for the Central Universities’ under No. DUT16QY09, and the Social Science Foundation of Jiangxi Province, China No.15JY48.
Author information
Authors and Affiliations
Corresponding author
Additional information
A preliminary version of this paper appeared in Q-Shine 2017, 2017, December. This version includes a more detailed scheme and a concrete discussion, which was not included before.
Rights and permissions
About this article
Cite this article
Feng, B., Li, X., Jie, Y. et al. A Novel Semi-fragile Digital Watermarking Scheme for Scrambled Image Authentication and Restoration. Mobile Netw Appl 25, 82–94 (2020). https://doi.org/10.1007/s11036-018-1186-9
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11036-018-1186-9