Abstract
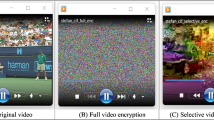
Since the COVID-19 pandemic, telemedicine or non-face-to-face medicine has increased significantly. In practice, various types of medical images are essential to achieve effective telemedicine. Medical image encryption algorithms play an irreplaceable role in the fast and secure transmission and storage of these medical images. However, most of the existing medical image encryption algorithms are full encryption algorithms, which are inefficient and time-consuming, so they are not suitable for emergency medical scenarios. To improve the efficiency of encryption, a small number of works have focused on partial or selective encryption algorithms for medical images, in which different levels of encryption strategies were adopted for different information content regions of medical images. However, these encryption algorithms have inadequate security more or less. In this paper, based on the Logistic map, we designed an improved variable dimension map. Then, an encryption algorithm for medical images was proposed based on it. This algorithm has two modes: (1) full encryption mode and (2) semi-full encryption mode, which can better adapt to different medical scenarios, respectively. In full encryption mode, all pixels of medical images are encrypted by using the confusion-diffusion structure. In semi-full encryption mode, the region of interest of medical images is extracted. The confusion was first adopted to encrypt the region of interest, and then, the diffusion was adopted to encrypt the entire image. In addition, no matter which encryption mode is used, the algorithm provides the function of medical image integrity verification. The proposed algorithm was simulated and analyzed to evaluate its effectiveness. The results show that in semi-full encryption mode, the algorithm has good security performance and lower time consumption; while in full encryption mode, the algorithm has better security performance and is acceptable in time.
Graphical Abstract






















Similar content being viewed by others
References
Abd El-Latif AA, Abd-El-Atty B, Talha M (2017) Robust encryption of quantum medical images. IEEE Access 6:1073–1081. https://doi.org/10.1109/ACCESS.2017.2777869
Abdmouleh MK, Khalfallah A, Bouhlel MS (2017) A novel selective encryption DWT-based algorithm for medical image. In: 2017 14th International Conference on Computer Graphics, Imaging and Visualization, Marrakesh, Morocco, pp 79–84. https://doi.org/10.1109/CGiV.2017.10
Abdulbaqi AS, Obaid AJ, Mohammed AH (2021) ECG signals recruitment to implement a new technique for medical image encryption. J Discret Math Sci Crypt 24(6):1663–1673. https://doi.org/10.1080/09720529.2021.1884378
Akkasaligar PT, Biradar S (2020) Selective medical image encryption using DNA cryptography. Inf Secur J: Glob Perspect 29(2):91–101. https://doi.org/10.1080/19393555.2020.1718248
Alvarez G, Li S (2006) Some basic cryptographic requirements for chaos-based cryptosystems. Int J Bifurcation Chaos 16(08):2129–2151
Aouissaoui I, Bakir T, Sakly A (2021) Robustly correlated key-medical image for DNA-chaos based encryption. IET Image Proc 15(12):2770–2786. https://doi.org/10.1049/ipr2.12261
Arumugham S, Rajagopalan S, Bosco J, Rayappan B, Amirtharajan R (2018) Networked medical data sharing on secure medium–a web publishing mode for DICOM viewer with three layer authentication. J Biomed Inform 86:90–105. https://doi.org/10.1016/j.jbi.2018.08.010
Arunkumar S, Subramaniyaswamy V, Vijayakumar V, Chilamkurti N, Logesh R (2019) SVD-based robust image steganographic scheme using RIWT and DCT for secure transmission of medical images. Measurement 139:426–437. https://doi.org/10.1016/j.measurement.2019.02.069
Balasamy K, Suganyadevi S (2021) A fuzzy based ROI selection for encryption and watermarking in medical image using DWT and SVD. Multimed Tools Appl 80:7167–7186
Banday SA, Pandit MK (2021) Texture maps and chaotic maps framework for secure medical image transmission. Multimed Tools Appl 80(12):17667–17683
Banu SA, Amirtharajan R (2020) A robust medical image encryption in dual domain : chaos-DNA-IWT combined approach. Med Biol Eng Compu 58(7):1445–1458
Barik RC, Changder S (2021) A novel and efficient amino acid codon based medical image encryption scheme colligating multiple chaotic maps. Multimed Tools Appl 80:10723–10760
Belazi A, Talha M, Kharbech S, Xiang W (2019) Novel medical image encryption scheme based on chaos and DNA encoding. IEEE Access 7:36667–36681. https://doi.org/10.1109/ACCESS.2019.2906292
Chen M, Ma G, Tang C, Lei Z (2020) Generalized optical encryption framework based on shearlets for medical image. Opt Lasers Eng 128:106026. https://doi.org/10.1016/j.optlaseng.2020.106026
Chen X, Hu C-J (2017) Medical image encryption based on multiple chaotic mapping and wavelet transform. Biomed Res 28(20):8834–8837
Chen X, Hu C (2017) Adaptive medical image encryption algorithm based on multiple chaotic mapping. Saudi J Biol Sci 24(8):1821–1827. https://doi.org/10.1016/j.sjbs.2017.11.023
Dagadu JC, Li J, Aboagye EO (2019) Medical image encryption based on hybrid chaotic DNA diffusion. Wireless Pers Commun 108(1):591–612. https://doi.org/10.1007/s11277-019-06420-z
Dai Y, Wang H, Wang Y (2016) Chaotic medical image encryption algorithm based on bit-plane decomposition. Int J Pattern Recognit Artif Intell 30(4):1657001. https://doi.org/10.1142/S0218001416570019
Dai Y, Wang H, Zhou Z, Jin Z (2016) Research on medical image encryption in telemedicine systems. Technol Health Care 24(s2):S435–S442. https://doi.org/10.3233/THC-161166
Deb S, Bhuyan B (2021) Chaos-based medical image encryption scheme using special nonlinear filtering function based LFSR. Multimed Tools Appl 80(13):19803–19826
Elhoseny M, Shankar K, Lakshmanaprabu SK, Maseleno A, Arunkumar N (2020) Hybrid optimization with cryptography encryption for medical image security in Internet of Things. Neural Comput Appl 32:10979–10993. https://doi.org/10.1007/s00521-018-3801-x
Fridrich J (1998) Symmetric ciphers based on two-dimensional chaotic maps. Int J Bifurc Chaos 8(6):1259–1284
Fu C, Meng W, Zhan Y, Zhu Z, Lau FC, Chi KT, Ma H (2013) An efficient and secure medical image protection scheme based on chaotic maps. Comput Biol Med 43(8):1000–1010
Ge J (2020) Alcencryption : A secure and efficient algorithm for medical. IEEE Sig Process Lett 125(3):1083–1100. https://doi.org/10.32604/cmes.2020.013039
Göreke V (2023) A novel method based on Wiener filter for denoising Poisson noise from medical X-Ray images. Biomed Sig Process Control 79:104031
Grebogi C, Ott E, Yorke JA (1983) Crises, sudden changes in chaotic attractors, and transient chaos. Physica D 7(1–3):181–200
Gupta R, Pachauri R, Singh AK (2018) An effective approach of secured medical image transmission using encryption method. Mol Cell Biomech 15(2):63. https://doi.org/10.3970/mcb.2018.00114
Hafsa A, Gafsi M, Malek J, Machhout M (2021) FPGA implementation of improved security approach for medical image encryption and decryption. Sci Program 2021:1–20
Hua Z, Yi S, Zhou Y (2018) Medical image encryption using high-speed scrambling and pixel adaptive diffusion. Sig Process 144:134–144. https://doi.org/10.1016/j.sigpro.2017.10.004
Ismail SM, Said LA, Radwan AG, Madian AH, Abu-elyazeed MF (2018) Generalized double-humped logistic map-based medical image encryption. J Adv Res 10:85–98. https://doi.org/10.1016/j.jare.2018.01.009
ISO 27799:2016(en) Health informatics — Information security management in health using ISO/IEC 27002, 2016. https://www.iso.org/standard/62777.html
Jain K, Aji A, Krishnan P (2021) Medical image encryption scheme using multiple chaotic maps. Pattern Recogn Lett 152:356–364. https://doi.org/10.1016/j.patrec.2021.10.033
Jain M, Choudhary RC, Kumar A (2016) Secure medical image steganography with RSA cryptography using decision tree. In: 2016 2nd International Conference on Contemporary Computing and Informatics (IC3I), pp 291–295. https://doi.org/10.1109/IC3I.2016.7917977
Janani T, Brindha M (2021) A secure medical image transmission scheme aided by quantum representation. J Inf Secur Appl 59:102832. https://doi.org/10.1016/j.jisa.2021.102832
Jiao G, Peng X, Duan K (2019) Image encryption with the cross diffusion of two chaotic maps. KSII Trans Internet Inf Syst (TIIS) 13(2):1064–1079
Jiao G, Zhou S, Li L, Zou Y (2019) Hybrid chaotic encryption algorithm for securing dicom systems. Int J Performability Eng 15(5):1436–1444. https://doi.org/10.23940/ijpe.19.05.p20.14361444
Kamal ST, Hosny KM, Member S, Elgindy TM, Darwish MM, Fouda MM (2021) A new image encryption algorithm for grey and color medical images. IEEE Access 9:37855–37865
Kanso A, Ghebleh M (2015) An efficient and robust image encryption scheme for medical applications. Commun Nonlinear Sci Numer Simul 24(1–3):98–116. https://doi.org/10.1016/j.cnsns.2014.12.005
Khashan OA, Alshaikh M (2020) Edge-based lightweight selective encryption scheme for digital medical images. Multimed Tools Appl 79(35):26369–26388
Khond S, Vijayakumar B (2019) Secure medical image processing using chaos and DNA encryption enhanced using reversible data hiding. Int J Eng Adv Technol (IJEAT) 8(6S):1062–1067. https://doi.org/10.35940/ijeat.F1202.0886S19
Krishnan KS, Suhaila S, Raja SP (2022) A novel medical image encryption using Rössler system. Intell Autom Soft Comput 33(2):1081–1101. https://doi.org/10.32604/iasc.2022.024023
Kumar CV, Natarajan V, Poonguzhali P (2015) Secured patient information transmission using reversible watermarking and DNA encrytion for medical images. Appl Math Sci 9(48):2381–2391
Kumar M, Gupta P (2021) A new medical image encryption algorithm based on the 1D logistic map associated with pseudo-random numbers. Multimed Tools Appl 80(12):18941–18967
Kumar S, Panna B, Kumar R (2019) Medical image encryption using fractional discrete cosine transform with chaotic function. Med Biol Eng Compu 57(11):2517–2533
Li S, Zhao L, Yang N (2021) Medical image encryption based on 2d zigzag confusion and dynamic diffusion. Secur Commun Netw 2021:6624809
Lima JB, Madeiro F, Sales FJR (2015) Encryption of medical images based on the cosine number transform. Sig Process : Image Commun 35:1–8. https://doi.org/10.1016/j.image.2015.03.005
Lin C, Wu J, Chen P, Lai H, Li C, Kuo C, Pai N (2021) Intelligent symmetric cryptography with chaotic map and quantum based key generator for medical images infosecurity. IEEE Access 9:118624–118639. https://doi.org/10.1109/ACCESS.2021.3107608
Liu J, Li J, Cheng J, Ma J, Sadiq N, Han B, Geng Q, Ai Y (2019) A novel robust watermarking algorithm for encrypted medical image based on DTCWT-DCT and chaotic map. Comput Mater Continua 61(2):889–910. https://doi.org/10.32604/cmc.2019.06034
Liu S, Liu L, Pang M (2021) Encryption method and security analysis of medical images based on stream cipher enhanced logical mapping. Technol Health Care 29(S1):185–193. https://doi.org/10.3233/THC-218019
Manikandan N, Muthaiah R, Teekaraman Y, Kuppusamy R, Radhakrishnan A (2021) A novel random error approximate adder-based lightweight medical image encryption scheme for secure remote monitoring of health data. Secur Commun Netw 2021:1–14
Manikandan V, Amirtharajan R (2021) On dual encryption with RC6 and combined logistic tent map for grayscale and DICOM. Multimed Tools Appl 80(15):23511–23540
Manikandan V, Amirtharajan R (2022) A simple embed over encryption scheme for DICOM images using Bülban map. Med Biol Eng Compu 60(3):701–717. https://doi.org/10.1007/s11517-021-02499-4
Masood F, Driss M, Boulila W, Ahmad J, Rehman SU, Jan SU, Qayyum A, Buchanan WJ (2022) A lightweight chaos-based medical image encryption scheme using random shuffling and XOR operations. Wirel Pers Commun 127(2):1405–1432. https://doi.org/10.1007/s11277-021-08584-z
Mishra P, Bhaya C, Pal AK, Singh AK (2023) A medical image cryptosystem using bit-level diffusion with DNA coding. J Ambient Intell Humaniz Comput 14(3):1731–1752. https://doi.org/10.1007/s12652-021-03410-7
Mortajez S, Tahmasbi M, Zarei J, Jamshidnezhad A (2020) A novel chaotic encryption scheme based on efficient secret keys and confusion technique for confidential of DICOM images. Inform Med Unlocked 20:100396. https://doi.org/10.1016/j.imu.2020.100396
Muthu JS, Murali P (2022) A novel DICOM image encryption with JSMP map. Optik 251(2022):168416. https://doi.org/10.1016/j.ijleo.2021.168416
Nita SL, Mihailescu MI (2022) Hash functions. In: Cryptography and cryptanalysis in java. Apress, pp 101–112. https://doi.org/10.1007/978-1-4842-8105-5_8
Norcen R, Podesser M, Pommer A, Schmidt H-P, Uhl A (2003) Confidential storage and transmission of medical image data. Comput Biol Med 33(3):277–292. https://doi.org/10.1016/S0010-4825(02)00094-X
Noura M, Noura H, Chehab A, Mansour MM, Sleem L, Couturier R (2018) A dynamic approach for a lightweight and secure cipher for medical images. Multimed Tools Appl 77(23):31397–31426
Prabhavathi K, Sathisha C, Ravikumar K (2017) Region of interest based selective medical image encryption using multi chaotic system. In: 2017 International Conference on Electrical, Electronics, Communication, Computer, and Optimization Techniques (ICEECCOT), pp 1–5
Praveenkumar P, Devi NK, Ravichandran D, Avila J, Thenmozhi K, Rayappan JBB, Amirtharajan R (2018) Transreceiving of encrypted medical image-a cognitive approach. Multimed Tools Appl 77(7):8393–8418. https://doi.org/10.1007/s11042-017-4741-7
PRC Cryptography Law art (2019) The 14th Meeting of the Standing Committee of the Thirteenth National People’s. http://www.npc.gov.cn/englishnpc/c23934/202009/dfb74a30d80b4a2bb5c19678b89a4a14.shtml
Qasim KR, Qasim SS (2020) Encrypt medical image using Csalsa20 stream algorithm. Medico-Legal Update 20(3):1248–1256
Rahmatullah B, Noble JA (2014) Anatomical object detection in fetal ultrasound: computer-expert agreements. In: Pham TD, Ichikawa K, Oyama-Higa M, Coomans D, Jiang X (eds) Biomedical informatics and technology. ACBIT 2013. Communications in computer and information science. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-642-54121-6_18
Raja S (2018) Secured medical image compression using DES encryption technique in Bandelet multiscale transform. Int J Wavelets Multiresolut Inf Process 16(04):1850028. https://doi.org/10.1142/S0219691318500285
Raja S (2019) Multiscale transform-based secured joint efficient medical image compression-encryption using symmetric key cryptography and ebcot encoding technique. Int J Wavelets Multiresolut Inf Process 17(05):1950034. https://doi.org/10.1142/S0219691319500346
Rajendran S, Krithivasan K, Doraipandian M (2021) A novel cross cosine map based medical image cryptosystem using dynamic bit-level diffusion. Multimed Tools Appl 80(16):24221–24243
Ravichandran D, Praveenkumar P, Rayappan JBB, Amirtharajan R (2016) Chaos based crossover and mutation for securing DICOM image. Comput Biol Med 72:170–184. https://doi.org/10.1016/j.compbiomed.2016.03.020
Ravichandran D, Praveenkumar P, Rayappan JBB, Amirtharajan R (2017) DNA chaos blend to secure medical privacy. IEEE Trans Nanobiosci 16(8):850–858
Reyad O, Hamed K, Karar ME (2020) Hash-enhanced elliptic curve bit-string generator for medical image encryption. J Intell Fuzzy Syst 39(5):7795–7806. https://doi.org/10.3233/JIFS-201146
Sasikaladevi N, Geetha K, Revathi A (2019) EMOTE – Multilayered encryption system for protecting medical images based on binary curve. J King Saud Univ - Comput Inf Sci 32(10):1215. https://doi.org/10.1016/j.jksuci.2019.01.014
Selvi CT, Amudha J, Sudhakar R (2021) A modified salp swarm algorithm (SSA) combined with a chaotic coupled map lattices (CML) approach for the secured encryption and compression of medical images during data transmission. Biomed Sig Process Control 66:102465. https://doi.org/10.1016/j.bspc.2021.102465
Shafique A, Ahmed J, Rehman MUR, Hazzazi MM (2021) Noise-resistant image encryption scheme for medical images in the chaos and wavelet domain. IEEE Access 9:59108–59130. https://doi.org/10.1109/ACCESS.2021.3071535
Shahzadi R, Anwar SM, Qamar F, Ali M, Rodrigues JJPC (2019) Chaos based enhanced RC5 algorithm for security and integrity of clinical images in remote health monitoring. IEEE Access 7:52858–52870. https://doi.org/10.1109/ACCESS.2019.2909554
Shankar K, Elhoseny M, Dhiravida E, Lakshmanaprabu SK, Wu W (2018) An efficient optimal key based chaos function for medical image security. IEEE Access 6:77145–77154. https://doi.org/10.1109/ACCESS.2018.2874026
Singh LD, Singh KM (2017) Medical image encryption based on improved ElGamal encryption technique. Optik - Int J Light Electron Opt 147:88–102. https://doi.org/10.1016/j.ijleo.2017.08.028
Song W, Fu C, Zheng Y, Cao L, Tie M (2021) A practical medical image cryptosystem with parallel acceleration. J Ambient Intell Humaniz Comput 14(8):9853–9867. https://doi.org/10.1007/s12652-021-03643-6
Stalin S, Maheshwary P, Shukla PK, Maheshwari M, Gour B, Khare A (2019) Fast and secure medical image encryption based on non linear 4D logistic map and DNA sequences (NL4DLM_DNA). J Med Syst 43(8):267
Summary of the HIPAA Security Rule (2021) Available: https://www.hhs.gov/hipaa/for-professionals/security/laws-regulations/index.html
Tamilselvi R, Ravindran G (2015) Comparison of encryption efficiency in DICOM images based on radon and block transform. Int J ChemTech Res 8(6):843–846
Tanveer SR, Alam KR, Morimoto Y (2022) A multi-stage chaotic encryption technique for medical image. Information Security Journal: A Global Perspective 31(6):657–675
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber J: Multidiscip J Sci Technol J Sel Areas Telecommun (JSAT) 1(2):31–38
Yadav A, Saini B, Verma VK, Pal V (2021) A joint medical image compression and encryption using AMBTC and hybrid chaotic system. J Discret Math Sci Crypt 24(8):2233–2244. https://doi.org/10.1080/09720529.2021.2011102
Yang Y, Xiao X, Cai X, Zhang W (2019) A secure and high visual-quality framework for medical images by contrast-enhancement reversible data hiding and homomorphic encryption. IEEE Access 7:96900–96911
Ye C, Xiong Z, Ding Y, Zhang X, Wang G, Xu F (2015) Joint fingerprinting/encryption for medical image security. Int J Secur Its Appl 9(1):409–418
Zhang B, Rahmatullah B, Wang SL, Liu Z (2023) A plain-image correlative semi-selective medical image encryption algorithm using enhanced 2D-logistic map. Multimed Tools Appl 82(10):15735–15762
Zhang B, Rahmatullah B, Wang SL, Zaidan A, Zaidan B, Liu P (2023) A review of research on medical image confidentiality related technology coherent taxonomy, motivations, open challenges and recommendations. Multimed Tools Appl 82(14):21867–21906
Zhang L, Zhu Z, Yang B, Liu W, Zhu H, Zou M (2015) Cryptanalysis and improvement of an efficient and secure medical image protection scheme. Math Probl Eng 2015:913476
Zhang L, Zhu Z, Yang B, Liu W, Zhu H, Zou M (2015) Medical image encryption and compression scheme using compressive sensing and pixel swapping based permutation approach. Math Probl Eng 2015:940638
Zhou J, Li J, Di X (2020) A novel lossless medical image encryption scheme based on game theory with optimized ROI parameters and hidden ROI position. IEEE Access 8:122210–122228. https://doi.org/10.1109/ACCESS.2020.3007550
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Competing interests
The authors declare no competing interests.
Additional information
Publisher's note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Springer Nature or its licensor (e.g. a society or other partner) holds exclusive rights to this article under a publishing agreement with the author(s) or other rightsholder(s); author self-archiving of the accepted manuscript version of this article is solely governed by the terms of such publishing agreement and applicable law.
About this article
Cite this article
Zhang, B., Rahmatullah, B., Wang, S.L. et al. A variable dimensional chaotic map-based medical image encryption algorithm with multi-mode. Med Biol Eng Comput 61, 2971–3002 (2023). https://doi.org/10.1007/s11517-023-02874-3
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11517-023-02874-3