Abstract
In this paper, a novel multi-party quantum private comparison protocol with a semi-honest third party (TP) is proposed based on the entanglement swapping of d-level cat states and d-level Bell states. Here, TP is allowed to misbehave on his own, but will not conspire with any party. In our protocol, n parties employ unitary operations to encode their private secrets and can compare the equality of their private secrets within one time execution of the protocol. Our protocol can withstand both the outside attacks and the participant attacks on the condition that none of the QKD methods is adopted to generate keys for security. One party cannot obtain other parties’ secrets except for the case that their secrets are identical. The semi-honest TP cannot learn any information about these parties’ secrets except the end comparison result on whether all private secrets from n parties are equal.
Similar content being viewed by others
References
Bennett, C.H., Brassard, G.: Quantum cryptography: public-key distribution and coin tossing. Proc. IEEE Int. Conf. Comput. Syst. Signal Process. 560, 175–179 (1984)
Ekert, A.K.: Quantum cryptography based on Bell’s theorem. Phys. Rev. Lett. 67(6), 661–663 (1991)
Bennett, C.H.: Quantum cryptography using any two nonorthogonal states. Phys. Rev. Lett. 68(21), 3121 (1992)
Cabello, A.: Quantum key distribution in the Holevo limit. Phys. Rev. Lett. 85, 5635 (2000)
Shih, H.C., Lee, K.C., Hwang, T.: New efficient three-party quantum key distribution protocols. IEEE J. Sel. Top. Quantum Electron. 15(6), 1602–1606 (2009)
Long, G.L., Liu, X.S.: Theoretically efficient high-capacity quantum-key-distribution scheme. Phys. Rev. A 65, 032302 (2002)
Bostrom, K., Felbinger, T.: Deterministic secure direct communication using entanglement. Phys. Rev. Lett. 89, 187902 (2002)
Chong, S.K., Hwang, T.: The enhancement of three-party simultaneous quantum secure direct communication scheme with EPR pairs. Opt. Commun. 284(1), 515–518 (2011)
Bouwmeester, D., Pan, J.W., Mattle, K., Eibl, M., Weinfurter, H., Zeilinger, A.: Experimental quantum teleportation. Nature 390(6660), 575–579 (1997)
Zhang, Z.J., Liu, Y.M., Man, Z.X.: Many-agent controlled teleportation of multi-qubit quantum information via quantum entanglement swapping. Commun. Theor. Phys. 44(5), 847–849 (2005)
Yin, X.F., Liu, Y.M., Zhang, Z.Y., Zhang, W., Zhang, Z.J.: Perfect teleportation of an arbitrary three-qubit state with the highly entangled six-qubit genuine state. Sci. China Phys. Mech. Astron. 53(11), 2059–2063 (2010)
Yao, A.C.: Protocols for secure computations. In: Proceedings of 23rd IEEE Symposium on Foundations of Computer Science (FOCS’ 82), p. 160. Washington, DC (1982)
Boudot, F., Schoenmakers, B., Traor’e, J.: A fair and efficient solution to the socialist millionaires’problem. Discret. Appl. Math. 111(1–2), 23–36 (2001)
Lo, H.K.: Insecurity of quantum secure computations. Phys. Rev. A 56(2), 1154–1162 (1997)
Yang, Y.G., Wen, Q.Y.: An efficient two-party quantum private comparison protocol with decoy photons and two-photon entanglement. J. Phys. A Math. Theor. 42, 055305 (2009)
Chen, X.B., Xu, G., Niu, X.X., Wen, Q.Y., Yang, Y.X.: An efficient protocol for the private comparison of equal information based on the triplet entangled state and single-particle measurement. Opt. Commun. 283, 1561 (2010)
Lin, J., Tseng, H.Y., Hwang, T.: Intercept–resend attacks on Chen et al’.s quantum private comparison protocol and the improvements. Opt. Commun. 284, 2412–2414 (2011)
Yang, Y.G., Gao, W.F., Wen, Q.Y.: Secure quantum private comparison. Phys. Scr. 80, 065002 (2009)
Liu, W., Wang, Y.B., Cui, W.: Quantum private comparison protocol based on Bell entangled states. Commun. Theor. Phys. 57, 583–588 (2012)
Yang, Y.G., Xia, J., Jia, X., Shi, L., Zhang, H.: New quantum private comparison protocol without entanglement. Int. J. Quantum Inf. 10, 1250065 (2012)
Chen, X.B., Su, Y., Niu, X.X., Yang, Y.X.: Efficient and feasible quantum private comparison of equality against the collective amplitude damping noise. Quantum Inf. Process. 13, 101–112 (2014)
Liu, B., Gao, F., Jia, H.Y., Huang, W., Zhang, W.W., Wen, Q.Y.: Efficient quantum private comparison employing single photons and collective detection. Quantum Inf. Process. 12, 887–897 (2013)
Zi, W., Guo, F.Z., Luo, Y., Cao, S.H., Wen, Q.Y.: Quantum private comparison protocol with the random rotation. Int. J. Theor. Phys. 52, 3212–3219 (2013)
Tseng, H.Y., Lin, J., Hwang, T.: New quantum private comparison protocol using EPR pairs. Quantum Inf. Process. 11, 373–384 (2012)
Wang, C., Xu, G., Yang, Y.X.: Cryptanalysis and improvements for the quantum private comparison protocol using EPR pairs. Int. J. Quantum Inf. 11, 1350039 (2013)
Yang, Y.G., Xia, J., Jia, X., Zhang, H.: Comment on quantum private comparison protocols with a semi-honest third party. Quantum Inf. Process. 12, 877–885 (2013)
Zhang, W.W., Zhang, K.J.: Cryptanalysis and improvement of the quantum private comparison protocol with semi-honest third party. Quantum Inf. Process. 12, 1981–1990 (2013)
Li, Y.B., Ma, Y.J., Xu, S.W., Huang, W., Zhang, Y.S.: Quantum private comparison based on phase encoding of single photons. Int. J. Theor. Phys. 53, 3191–3200 (2014)
Liu, X.T., Zhang, B., Wang, J., Tang, C.J., Zhao, J.J.: Differential phase shift quantum private comparison. Quantum Inf. Process. 13, 71–84 (2014)
Liu, W., Wang, Y.B.: Quantum private comparison based on GHZ entangled states. Int. J. Theor. Phys. 51, 3596–3604 (2012)
Li, J., Zhou, H.F., Jia, L., Zhang, T.T.: An efficient protocol for the private comparison of equal information based on four-particle entangled W state and Bell entangled states swapping. Int. J. Theor. Phys. 53(7), 2167–2176 (2014)
Liu, W., Wang, Y.B., Jiang, Z.T.: An efficient protocol for the quantum private comparison of equality with W state. Opt. Commun. 284, 3160–3163 (2011)
Zhang, W.W., Li, D., Li, Y.B.: Quantum private comparison protocol with W States. Int. J. Theor. Phys. 53(5), 1723–1729 (2014)
Ji, Z.X., Ye, T.Y.: Quantum private comparison of equal information based on highly entangled six-qubit genuine state. Commun. Theor. Phys. 65, 711–715 (2016)
Sun, Z.W., Long, D.Y.: Quantum private comparison protocol based on cluster states. Int. J. Theor. Phys. 52, 212–218 (2013)
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z.: A protocol for the quantum private comparison of equality with \(\chi \)-type state. Int. J. Theor. Phys. 51, 69–77 (2012)
Liu, W., Wang, Y.B., Jiang, Z.T., Cao, Y.Z., Cui, W.: New quantum private comparison protocol using \(\chi \)-type state. Int. J. Theor. Phys. 51, 1953–1960 (2012)
Lin, S., Guo, G.D., Liu, X.F.: Quantum private comparison of equality with \(\chi \)-type entangled states. Int. J. Theor. Phys. 52, 4185–4194 (2013)
Chang, Y.J., Tsai, C.W., Hwang, T.: Multi-user private comparison protocol using GHZ class states. Quantum Inf. Process. 12, 1077–1088 (2013)
Liu, W., Wang, Y.B., Wang, X.M.: Multi-party quantum private comparison protocol using \(d\)-dimensional basis states without entanglement swapping. Int. J. Theor. Phys. 53, 1085–1091 (2014)
Wang, Q.L., Sun, H.X., Huang, W.: Multi-party quantum private comparison protocol with \(n\)-level entangled states. Quantum Inf. Process. 13, 2375–2389 (2014)
Cerf, N.J.: Pauli cloning of a quantum bit. Phys. Rev. Lett. 84, 4497 (2000)
Cerf, N.J.: Asymmetric quantum cloning in any dimension. J. Mod. Opt. 47(2–3), 187–209 (2000)
Cerf, N.J.: Asymmetric quantum cloning machines. Acta Phys. Slov. 48(3), 115 (1998)
Karimipour, V., Bahraminasab, A., Bagherinezhad, S.: Entanglement swapping of generalized cat states and secret sharing. Phys. Rev. A 65, 042320 (2002)
Li, C.Y., Zhou, H.Y., Wang, Y., Deng, F.G.: Secure quantum key distribution network with Bell states and local unitary operations. Chin. Phys. Lett. 22(5), 1049 (2005)
Li, C.Y., Li, X.H., Deng, F.G., Zhou, P., Liang, Y.J., Zhou, H.Y.: Efficient quantum cryptography network without entanglement and quantum memory. Chin. Phys. Lett. 23(11), 2896 (2006)
Chen, Y., Man, Z.X., Xia, Y.J.: Quantum bidirectional secure direct communication via entanglement swapping. Chin. Phys. Lett. 24(1), 19 (2007)
Ye, T.Y., Jiang, L.Z.: Improvement of controlled bidirectional quantum direct communication using a GHZ state. Chin. Phys. Lett. 30(4), 040305 (2013)
Cai, Q.Y.: Eavesdropping on the two-way quantum communication protocols with invisible photons. Phys. Lett. A 351(1–2), 23–25 (2006)
Gisin, N., Ribordy, G., Tittel, W., Zbinden, H.: Quantum cryptography. Rev. Mod. Phys. 74(1), 145–195 (2002)
Deng, F.G., Zhou, P., Li, X.H., Li, C.Y., Zhou, H.Y.: Robustness of two-way quantum communication protocols against Trojan horse attack (2005). arXiv: quant-ph/0508168
Li, X.H., Deng, F.G., Zhou, H.Y.: Improving the security of secure direct communication based on the secret transmitting order of particles. Phys. Rev. A 74, 054302 (2006)
Gao, F., Qin, S.J., Wen, Q.Y., Zhu, F.C.: A simple participant attack on the Bradler–Dusek protocol. Quantum Inf. Comput. 7, 329 (2007)
Gao, F., Wen, Q.Y., Zhu, F.C.: Comment on:“quantum exam” [Phys Lett A 350(2006) 174]. Phys. Lett. A 360(6), 748–750 (2007)
Guo, F.Z., Qin, S.J., Gao, F., Lin, S., Wen, Q.Y., Zhu, F.C.: Participant attack on a kind of MQSS schemes based on entanglement swapping. Eur. Phys. J. D 56(3), 445–448 (2010)
Qin, S.J., Gao, F., Wen, Q.Y., Zhu, F.C.: Cryptanalysis of the Hillery–Buzek–Berthiaume quantum secret-sharing protocol. Phys. Rev. A 76(6), 062324 (2007)
Lin, J., Hwang, T.: An enhancement on Shi et al’.s multiparty quantum secret sharing protocol. Opt. Commun. 284(5), 1468–1471 (2011)
Chen, J.H., Lee, K.C., Hwang, T.: The enhancement of Zhou et al.’s quantum secret sharing protocol. Int. J. Mod. Phys. C 20(10), 1531–1535 (1999)
Acknowledgements
The authors would like to thank the anonymous reviewers for their valuable comments that help enhancing the quality of this paper. Funding by the National Natural Science Foundation of China (Grant Nos. 61402407 and 11375152) is gratefully acknowledged.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflicts of interest
The authors declare that they have no conflict of interest.
Appendix
Appendix
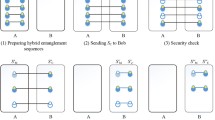
Graphical description of entanglement swapping between one d-level n-particle cat state and one d-level Bell state (Here, one d-level n-particle cat state is depicted by a line with n nodes on it where the first node is solid and other nodes are empty. And one d-level Bell state is depicted by a line with two nodes on it where one node is solid and the other node is empty)
Rights and permissions
About this article
Cite this article
Zhao-Xu, J., Tian-Yu, Y. Multi-party quantum private comparison based on the entanglement swapping of d-level cat states and d-level Bell states. Quantum Inf Process 16, 177 (2017). https://doi.org/10.1007/s11128-017-1628-5
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11128-017-1628-5