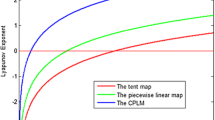
Abstract
In recent years, various chaos-based image encryption algorithms have been proposed to meet the growing demand for real-time secure image transmission. However, chaotic system that is the core component of chaos-based cryptosystem usually degrades under finite computing precision, causing many security issues. In this paper, a novel cryptosystem with analog-digital hybrid chaotic model is proposed. Firstly, the analog Chen chaotic system and the digital Logistic map are adopted to depict the capability of the hybrid model, in which analog system is used to perturb digital system. Dynamic analyses demonstrate that the hybrid method has better complexity, larger chaotic parameter range and good ability to counteract dynamical degradation. The chaos-based key streams generated by the perturbed Logistic map are more suitable for image encryption. Secondly, a parameter selection mechanism is introduced to increase security. The state variables of Chen chaotic system and cipher image are involved in parameter selection process to dynamically change the parameter of the perturbed Logistic map. The involvement of cipher image makes the key streams relevant to plain image and can resist known/chosen-plaintext attacks. Performance, security and comparison analyses indicate that this cryptosystem has high security, low time complexity, and ability to resist common attacks.














Similar content being viewed by others
References
Abdulla A (2015) Exploiting similarities between secret and cover images for improved embedding efficiency and security in digital steganography. Dissertation, University of Buckingham. http://bear.buckingham.ac.uk/149/
Alawida M, Samsudin A, Sen Teh J, Alkhawaldeh RS (2019) A new hybrid digital chaotic system with applications in image encryption. Signal Process 160:45–58. https://doi.org/10.1016/j.sigpro.2019.02.016
Alawida M, Samsudin A, Sen Teh J (2019) Enhancing unimodal digital chaotic maps through hybridization. Nonlinear Dyn 96:601–613
Alvarez G, Li SJ (2009) Cryptanalyzing a nonlinear chaotic algorithm (NCA) for image encryption. Commun Nonlinear Sci Numer Simul 14:3743–3749. https://doi.org/10.1016/j.cnsns.2009.02.033
Arroyo D, Li CQ, Li SJ, Alvarez G, Halang WA (2009) Cryptanalysis of an image encryption scheme based on a new total shuffling algorithm. Chaos Solitons Fract 41:2613–2616. https://doi.org/10.1016/j.chaos.2008.09.051
Arroyo D, Diaz J, Rodriguez FB (2013) Cryptanalysis of a one round chaos-based substitution permutation network. Signal Process 93:1358–1364
Biswas MR, Alam KMR, Tamura S, Morimoto Y (2019) A technique for DNA cryptography based on dynamic mechanisms. J Inf Secur Appl 48:102363. https://doi.org/10.1016/j.jisa.2019.102363
Bouhous A, Kemih K (2018) Novel encryption method based on optical time-delay chaotic system and a wavelet for data transmission. Opt Laser Technol 108:162–169. https://doi.org/10.1016/j.optlastec.2018.06.052
Chai XL, Gan ZH, Chen YR, Zhang YS (2017) A visually secure image encryption scheme based on compressive sensing. Signal Process 134:35–51. https://doi.org/10.1016/j.sigpro.2016.11.016
Chang CC, Hwang MS, Chen TS (2001) A new encryption algorithm for image cryptosystems. J Syst Softw 58:83–91. https://doi.org/10.1016/s0164-1212(01)00029-2
Chen JX, Zhu ZL, Fu C, Yu H, Zhang LB (2015) A fast chaos-based image encryption scheme with a dynamic state variables selection mechanism. Commun Nonlinear Sci Numer Simul 20:846–860. https://doi.org/10.1016/j.cnsns.2014.06.032
Chen C, Sun KH, He SB (2020) An improved image encryption algorithm with finite computing precision. Signal Process 168:107340. https://doi.org/10.1016/j.sigpro.2019.107340
Dorgham O, Al-Rahamneh B, Almomani A, Al-Hadidi M, Khatatneh KF (2018) Enhancing the security of exchanging and storing DICOM medical images on the cloud. Int J Cloud Appl Comput 8(1):154–172
Fu C, Wen ZK, Zhu ZL, Yu H (2016) A security improved image encryption scheme based on chaotic baker map and hyperchaotic Lorenz system. Int J Comput Sci Eng 12:113–123
Gao XJ (2019) Enhancing Ikeda time delay system by breaking the symmetry of sine nonlinearity. Complexity 2019:1–14
Gong LH, Wu RQ, Zhou RN (2020) A new 4D chaotic system with coexisting hidden chaotic attractors. Int J Bifurcat Chaos 30(10):2050142. https://doi.org/10.1142/S0218127420501424
Hanis S, Amutha R (2018) Double image compression and encryption scheme using logistic mapped convolution and cellular automata. Multimed Tools Appl 77:6897–6912. https://doi.org/10.1007/s11042-017-4606-0
Hu HP, Deng YS, Liu LF (2014) Counteracting the dynamical degradation of digital chaos via hybrid control. Commun Nonlinear Sci Numer Simul 19:1970–1984. https://doi.org/10.1016/j.cnsns.2013.10.031
Jallouli O, El Assad S, Chetto M, Lozi R, Caragata D (2015) A novel chaotic generator based on weakly-coupled discrete skewtent maps. International Conference for Internet Technology and Secured Transactions, pp 38–43
Jeng FG, Huang WL, Chen TH (2015) Cryptanalysis and improvement of two hyper-chaos-based image encryption schemes. Signal Process Image Commun 34:45–51. https://doi.org/10.1016/j.image.2015.03.003
Khan JS, Ahmad J (2019) Chaos based efficient selective image encryption. Multidimens Syst Signal Process 30:943–961. https://doi.org/10.1007/s11045-018-0589-x
Kumar A (2019) Design of secure image fusion technique using cloud for privacy-preserving and copyright protection. Int J Cloud Appl Comput 9(3):22–36
Lan RS, He JW, Wang SH, Gu TL, Luo XN (2018) Integrated chaotic systems for image encryption. Signal Process 147:133–145. https://doi.org/10.1016/j.sigpro.2018.01.026
Li CQ, Li SJ, Chen GR, Halang WA (2009) Cryptanalysis of an image encryption scheme based on a compound chaotic sequence. Image Vis Comput 27:1035–1039. https://doi.org/10.1016/j.imavis.2008.09.004
Li CH, Luo GC, Qin K, Li CB (2017) An image encryption scheme based on chaotic tent map. Nonlinear Dyn 87:127–133
Li CL, Li HM, Li FD, Wei DQ, Yang XB, Zhang J (2018) Multiple-image encryption by using robust chaotic map in wavelet transform domain. Optik 171:277–286. https://doi.org/10.1016/j.ijleo.2018.06.029
Li CQ, Lin DD, Lü JH, Hao F (2018) Cryptanalyzing an image encryption algorithm based on autoblocking and electrocardiography. IEEE Multimed 25:46–56
Lin CY, Prangjarote P, Kang LW, Huang WL, Chen TH (2012) Joint fingerprinting and decryption with noise-resistant for vector quantization images. Signal Process 92:2159–2171. https://doi.org/10.1016/j.sigpro.2012.02.002
Liu LF, Lin J, Miao SX, Liu BC (2017) A double perturbation method for reducing dynamical degradation of the digital baker map. Int J Bifurc Chaos 27:1750103. https://doi.org/10.1142/S0218127417501036
Mamta, Gupta BB (2019) An efficient KP design framework of attribute-based searchable encryption for user level revocation in cloud. Concurr Comp Pract E 32(18):e5291. https://doi.org/10.1002/cpe.5291
Melkemi KE, Golea NEH (2019) ROI-based fragile watermarking for medical image tamper detection. Int J High Perform Comput Netw 13(2):199–210
Özkaynak F (2018) Brief review on application of nonlinear dynamics in image encryption. Nonlinear Dyn 92:305–313
Paar C, Pelzl J (2009) Understanding cryptography: a textbook for students and practitioners. Springer, Berlin, Heidelberg
Pareek NK, Patidar V, Sud KK (2013) Diffusion–substitution based gray image encryption scheme. Digit Signal Process 23:894–901. https://doi.org/10.1016/j.dsp.2013.01.005
Ping P, Wu JJ, Mao YC, Feng X, Fan JY (2019) Design of image cipher using life-like cellular automata and chaotic map. Signal Process 150:233–247. https://doi.org/10.1016/j.sigpro.2018.04.018
Skrobek A (2007) Cryptanalysis of chaotic stream cipher. Phys Lett A 363:84–90
Som S, Dutta S, Singha R, Kotal A, Palit S (2015) Confusion and diffusion of color images with multiple chaotic maps and chaos-based pseudorandom binary number generator. Nonlinear Dyn 80:615–627
Su YR, Wo Y, Han G (2019) Reversible cellular automata image encryption for similarity search. Signal Process Commun 72:134–147. https://doi.org/10.1016/j.image.2018.12.008
Tang JY, Yu ZN, Liu LF (2019) A delay coupling method to reduce the dynamical degradation of digital chaotic maps and its application for image encryption. Multimed Tools Appl 78:24765–24788. https://doi.org/10.1007/s11042-019-7602-8
Teng L, Wang XY (2012) A bit-level image encryption algorithm based on spatiotemporal chaotic system and self-adaptive. Opt Commun 285:4048–4054. https://doi.org/10.1016/j.optcom.2012.06.004
Tong XJ, Wang Z, Zhang M, Liu Y, Xu H, Ma J (2015) An image encryption algorithm based on the perturbed high-dimensional chaotic map. Nonlinear Dyn 80:1493–1508
Wang Y, Luo LY, Xie Q, Tian HJ, Yang HQ (2009) A fast stream cipher based on spatiotemporal Chaos. 2009 International Symposium on Information Engineering and Electronic Commerce, pp 418-422
Wang Y, Wong KW, Liao XF, Chen GR (2011) A new chaos-based fast image encryption algorithm. Appl Soft Comput 11:514–522. https://doi.org/10.1016/j.asoc.2009.12.011
Wang CF, Fan CL, Feng K, Huang X, Ding Q (2018) Analysis of the time series generated by a new high-dimensional discrete chaotic system. Complexity 2018:9818520
Wang XY, Wang Y, Zhu XQ, Luo C (2020) A novel chaotic algorithm for image encryption utilizing one-time pad based on pixel level and DNA level. Opt Lasers Eng 125:105851. https://doi.org/10.1016/j.optlaseng.2019.105851
Wheeler DD, Matthews RAJ (1991) Supercomputer investigations of a chaotic encryption algorithm. Cryptologia 15:140–152. https://doi.org/10.1080/0161-119191865821
Wu Y, Noonan JP, Agaian S (2011) NPCR and UACI randomness tests for image encryption. Cyber J Multidiscip J Sci Technol J Sel Areas Telecommun:31–38
Yang FF, Mou J, Yan HZ, Hu JH (2019) Dynamical analysis of a novel complex chaotic system and application in image diffusion. IEEE Access 7:118188–118202
Ye GD, Huang XL (2017) An efficient symmetric image encryption algorithm based on an intertwining logistic map. Neurocomputing 251:45–53. https://doi.org/10.1016/j.neucom.2017.04.016
Ye HS, Zhou RN, Gong LH (2020) Multi-image compression-encryption scheme based on quaternion discrete fractional Hartley transform and improved pixel adaptive diffusion. Signal Process 175:107652. https://doi.org/10.1016/j.sigpro.2020.107652
Yu CY, Li JZ, Li X, Ren XC, Gupta BB (2018) Four-image encryption scheme based on quaternion Fresnel transform, chaos and computer generated hologram. Multimed Tools Appl 77(4):4585–4608. https://doi.org/10.1007/s11042-017-4637-6
Yu SS, Zhou RN, Gong LH, Zhe N (2020) Optical image encryption algorithm based on phase-truncated short-time fractional Fourier transform and hyper-chaotic system. Opt Lasers Eng 124:105816. https://doi.org/10.1016/j.optlaseng.2019.105816
Zheng J, Hu HP, Xia X (2018) Applications of symbolic dynamics in counteracting the dynamical degradation of digital chaos. Nonlinear Dyn 94:1535–1546. https://doi.org/10.1007/s11071-018-4440-6
Zhou ZL, Mu Y (2019) Visual vocabulary tree-based partial-duplicate image retrieval for coverless image steganography. Int J High Perform Comput Netw 14(3):333
Zhou YC, Hua ZY, Pun CM, Chen CLP (2014) Cascade chaotic system with applications. IEEE Trans Cybern 45:2001–2012
Zhou RN, Hua TX, Gong LH, Pei DJ, Liao QH (2015) Quantum image encryption based on generalized Arnold transform and double random-phase encoding. Quantum Inf Process 14(4):1193–1213. https://doi.org/10.1007/s11128-015-0926-z
Zhu ZL, Zhang W, Wong KW, Yu H (2011) A chaos-based symmetric image encryption scheme using a bit-level permutation. Inf Sci 181:1171–1186. https://doi.org/10.1016/j.ins.2010.11.009
Acknowledgements
This work was supported by the National Key R&D Program of China [grant number 2017YFB0802000]; and the Cryptography Theoretical Research of National Cryptography Development Fund [grant number MMJJ20170109]; and the Key R&D Program of Hubei Province [grant number 2020BAB104].
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zheng, J., Hu, H. A symmetric image encryption scheme based on hybrid analog-digital chaotic system and parameter selection mechanism. Multimed Tools Appl 80, 20883–20905 (2021). https://doi.org/10.1007/s11042-021-10751-0
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-021-10751-0