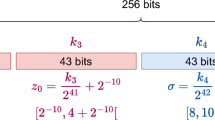
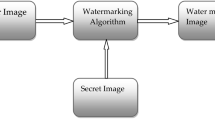
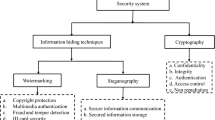
Abstract
Optimization techniques are used in watermarking algorithms to balance the trade-off between the two mutually conflicting parameters-imperceptibility and robustness. Differential Evolution (DE) with Rotational Cross over (RCO), namely DE-RCO, is employed in the proposed algorithm to improve the convergence of optimization. The DE-RCO provides a watermarking scheme with the highest robustness preserving the transparency. The watermark encoding and decoding carried in the transform domain with a hybrid combination of Schur Factorization (SF) and Singular Value Decomposition (SVD). Two-fold security provided with the Digital Signature (DS) generation and B-test. The DS is concealed in the watermarked image for authentication purpose of freeing the algorithm from the false-positive problem. When the signature passed through the insecure channel, it may corrupt and lead to the failure of the A-test, even the correct watermark given at the extraction leading to the false-negative problem. B-test is conducted to free the algorithm from a false negative problem. An enhanced authentication framework designed and implemented to make the algorithm free from the false-positive and false-negative issues using DS and the hash generated by Gaussian Hermite Moments (GHMs). The experimental results compared with the related existing watermarking schemes demonstrate that the proposed scheme exhibit strong robustness to attacks, invisible and highly secure against false-positive and false-negative problems.

























Similar content being viewed by others
References
Ahmed F, Siyal MY, Abbas VU (2010) A secure and robust hash-based scheme for image authentication. Signal Process 90(5):1456–1470
Ali M, Ahn CW, Pant M (2014) A robust image watermarking technique using SVD and Differential Evolution in DCT domain. Optik-Int J Light Electron Opt 125(1):428–434
Ali M, Ahn CW, Pant M, Siarry P (2015) An image watermarking scheme in wavelet domain with optimized compensation of singular value decomposition via artificial bee colony. Inf Sci 301:44–60
Ali M (2018) An optimal image watermarking approach through cuckoo search algorithm in wavelet domain. Int J Syst Assur Eng Manag 9(3):602–611
Al-Haj AM (ed.) (2010) Advanced techniques in multimedia watermarking: image, video and audio applications: image, video and audio applications. IGI Global
Ansari IA, Pant M (2017) Multipurpose image watermarking in the domain of DWT based on SVD and ABC. Pattern Recognit Lett 94:228–236
Araghi TK, Manaf AA, Araghi SK (2018) A secure blind discrete wavelet transform based watermarking scheme using two-level singular value decomposition. Expert Syst Appl 112:208–228
Aslantas V (2008) A singular-value decomposition-based image watermarking using genetic algorithm. AEU-Int J Electron Commun 62(5):386–394
Aslantas V, Dogan AL, Ozturk S (2008) DWT-SVD based image watermarking using particle swarm optimizer. In: 2008 IEEE International conference on multimedia and expo. IEEE, pp 241–244
Aung A, Ng BP, Rahardja S (2011) A robust watermarking scheme using sequency-ordered complex Hadamard transform. J Signal Process Syst 64 (3):319–333
Bamal R, Kasana SS (2019) Dual hybrid medical watermarking using walsh-slantlet transform. Multimedia Tools Appl 78(13):17899–17927
Berger CE, de Koeijer JA, Glas W, Madhuizen HT (2006) Color separation in forensic image processing. J Forensic Sci 51(1):100–102
Cox I, Miller M, Bloom J, Fridrich J, Kalker T (2007) Digital watermarking and steganography. Morgan Kaufmann, San Mateo
Delp E J III, Wong PW (2003) Security and watermarking of multimedia contents V. In: Security and watermarking of multimedia contents V, vol 5020
Deng LB, Wang S, Qiao LY (2017) DE-RCO: rotating crossover operator with multiangle searching strategy for adaptive differential evolution. IEEE Access 6:2970–2983
Flusser J, Zitova B, Suk T (2009) Moments and moment invariants in pattern recognition. Wiley, New York
Gonzales RC, Woods RE (1992) Digital image processing. Reading, Mass: Addison-Wesley, 518–524
Grycuk R, Gabryel M, Nowicki R, Scherer R (2016) Content-based image retrieval optimization by Differential Evolution. In: 2016 IEEE congress on evolutionary computation (CEC). IEEE, pp 86–93
Henderson N, Sacco WF, Barufatti NE, Ali MM (2010) Calculation of critical points of thermodynamic mixtures with Differential Evolution algorithms. Ind Eng Chem Res 49(4):1872–1882
Hill DL, Batchelor PG, Holden M, Hawkes DJ (2001) Medical image registration. Phys Med Biol 46(3):R1
Horng SJ, Rosiyadi D, Fan P, Wang X, Khan MK, Pan Y (2011) An efficient copyright protection scheme for e-government document images. In: IEEE MultiMedia
Horng SJ, Rosiyadi D, Fan P, Wang X, Khan MK (2014) An adaptive watermarking scheme for e-government document images. Multimed Tools Appl 72(3):3085–3103
Hosny KM, Khedr YM, Khedr WI, Mohamed ER (2018) Robust image hashing using exact Gaussian–Hermite moments. IET Image Process 12 (12):2178–2185
Hsu LY, Hu HT, Chang YH (2018) An improvement of embedding color watermarks in color images based on schur decomposition. In: 2018 41st international conference on telecommunications and signal processing (TSP). IEEE, pp 1–5
ITU R (2002) Methodology for the subjective assessment of the quality of television pictures. Recommendation ITU-R BT. 500-11
Jayalakshmi M, Merchant SN, Desai UB (2006) Digital watermarking in contourlet domain. In: 18th International conference on pattern recognition (ICPR’06), vol 3. IEEE, pp 861–864
Kozat SS, Venkatesan R, Mihçak MK (2004) Robust perceptual image hashing via matrix invariants. In: 2004 International conference on image processing, 2004. ICIP’04, vol 5. IEEE
Lin WH, Horng SJ, Kao TW, Fan P, Lee CL, Pan Y (2008) An efficient watermarking method based on significant difference of wavelet coefficient quantization. IEEE Trans Multimed 10(5):746–757
Lin WH, Horng SJ, Kao TW, Chen RJ, Chen YH, Lee CL, Terano T (2009) Image copyright protection with forward error correction. Expert Syst Appl 36(9):11888–11894
Loukhaoukha K (2013) Image watermarking algorithm based on multi-objective ant colony optimization and singular value decomposition in wavelet domain. J Optim 2013:1–10
Meenakshi K, Bethel GB (2014) Design and simulation of Constant bit rate compressor using fuzzy logic. In: 2014 First international conference on networks & soft computing (ICNSC2014). IEEE, pp 309–313
Meenakshi K, Rao CS, Prasad KS (2014) A robust watermarking scheme based Walsh-Hadamard transform and SVD using ZIG ZAG scanning. In: 2014 International conference on information technology. IEEE, pp 167–172
Meenakshi K, Srinivasa Rao C, Satya Prasad K (2014) A scene based video watermarking using slant transform. IETE J Res 60(4):276–287
Meenakshi K, Prasad KS, Rao CS (2017) Development of low-complexity video watermarking with conjugate symmetric sequency–complex Hadamard transform. IEEE Commun Lett 21(8):1779–1782
Meenakshi K, Swaraja K, Kora P, Ch UK (2019) Texture feature based oblivious watermarking with slant transform using fuzzy logic. In: 2019 IEEE 5th international conference for convergence in technology (I2CT). IEEE, pp 1–5
Meenakshi K, Padmavathi Kora DK (2019) Video watermarking with curvelet transform. Int J Innov Technol Explor Eng (IJITEE), ISSN 2278–3075
Mohan BC, Srinivaskumar S, Chatterji BN (2008) A robust digital image watermarking scheme using singular value decomposition (SVD), dither quantization and edge detection. J ICGST-GVIP 8:17–23
Monga V (2005) Perpetually based methods for robust image hashing
Meenakshi K, Swaraja K, Kora P (2019) A robust DCT-SVD based video watermarking using zigzag scanning. In: Soft computing and signal processing. Springer, Singapore, pp 477–485
Nilchi ARN, Taheri A (2008) A new robust digital image watermarking technique based on the Discrete Cosine Transform and Neural Network. In: 2008 International symposium on biometrics and security technologies. IEEE, pp 1–7
Ramanjaneyulu K, Rajarajeswari K (2012) Wavelet-based oblivious image watermarking scheme using genetic algorithm. IET Image Process 6 (4):364–373
Saxena N, Mishra KK, Tripathi A (2018) DWT-SVD-based color image watermarking using dynamic-PSO. In: Advances in computer and computational sciences. Springer, Singapore, pp 343–351
Sequeira A, Kundur D (2001) Communication and information theory in watermarking: a survey. In: Multimedia systems and applications IV, vol 4518. International Society for Optics and Photonics, pp 216–227
Su Q, Yuan Z, Liu D (2018) An approximate Schur decomposition-based spatial domain color image watermarking method. IEEE Access 7:4358–4370
Swaraja K (2018) Medical image region based watermarking for secured telemedicine. Multimed Tools Appl 77(21):28249–28280
Swaraja K, Meenakshi K, Kora P (2020) An optimized blind dual medical image watermarking framework for tamper localization and content authentication in secured telemedicine. Biomed Signal Process Control 55:101665
Swaraja K, Madhaveelatha Y, Reddy VSK (2014) A pristine digital video watermarking in H. 264 compressed domain. In: 2014 IEEE International conference on computational intelligence and computing research. IEEE, pp 1–4
Tang Z, Huang L, Zhang X, Lao H (2016) Robust image hashing based on color vector angle and canny operator. AEU-Int J Electron Commun 70 (6):833–841
Vali MH, Aghagolzadeh A, Baleghi Y (2018) Optimized watermarking technique using self-adaptive Differential Evolution based on redundant discrete wavelet transform and singular value decomposition. Expert Syst Appl 114:296–312
Wolfe SJ (1980) A characterization of Lévy probability distribution functions on Euclidean spaces. J Multivar Anal 10(3):379–384
Yu F, Li Y, Wei B, Kuang L (2016) Interactive differential evolution for user-oriented image retrieval system. Soft Comput 20(2):449–463
Zhao Y, Wang S, Feng G, Tang Z (2010) A robust image hashing method based on Zernike moments. J Comput Inf Syst 6(3):717–725
Zheng F, Zecchin AC, Simpson AR (2013) Self-adaptive differential evolution algorithm applied to water distribution system optimization. J Comput Civil Eng 27(2):148–158
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Meenakshi, K., Swaraja, K. & Kora, P. A hybrid matrix factorization technique to free the watermarking scheme from false positive and negative problems. Multimed Tools Appl 79, 29865–29900 (2020). https://doi.org/10.1007/s11042-020-09250-5
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-020-09250-5