Abstract
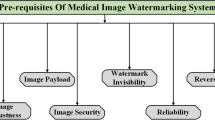
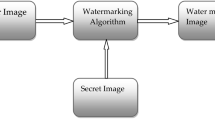
A hybrid robust lossless data hiding algorithm is proposed in this paper by using the Singular Value Decomposition (SVD) with Fast Walsh Transform (FWT) and Slantlet Transform (SLT) for image authentication. These transforms possess good energy compaction with distinct filtering, which leads to higher embedding capacity from 1.8 bit per pixel (bpp) up to 7.5bpp. In the proposed algorithm, Artificial Neural Network (ANN) is applied for region of interest (ROI) detection and two different watermarks are created. Embedding is done after applying FWH by changing the SVD coefficients and by changing the highest coefficients of SLT subbands. In dual hybrid embedding first watermark is the ROI and another watermark consists of three parts, i.e., patients’ personal details, unique biometric ID and the key for encryption. Comparison of the proposed algorithm is done with the existing watermarking techniques for analyzing the performance. Experiments are simulated on the proposed algorithm by casting numerous attacks for testing the visibility, robustness, security, authenticity, integrity and reversibility. The resultant outcome proves that the watermarked image has an improved imperceptibility with a high level of payload, low time complexity and high Peak Signal to Noise Ratio (PSNR) against the existing approaches.











Similar content being viewed by others
References
Acharya R, Bhat PS, Kumar S, Min LC (2003) Transmission and storage of medical images with patient information. Comput Biol Med 33(4):303–310
Acharya R, Niranjan UC, Iyengar SS, Kannathal N, Min LC (2004) Simultaneous storage of patient information with medical images in the frequency domain. Comput Methods Prog Biomed 76(1):13–19
Alattar AM (2004) Reversible watermark using the difference expansion of a generalized integer transform. IEEE transactions on image processing 13(8):1147–1156
Alvarez G, Li S, Hernandez L (2007) Analysis of security problems in a medical image encryption system. Comput Biol Med 37(3):424–427
Arsalan M, Malik SA, Khan A (2012) Intelligent reversible watermarking in integer wavelet domain for medical images. J Syst Softw 85(4):883–894
Bamal R, Kasana SS (2017) Slantlet based hybrid watermarking technique for medical images. Multimedia Tools and Applications 77:1–26
Bhatnagar G, Raman B (2009) Robust watermarking in multiresolution walsh-hadamard transform. In: IEEE international on advance computing conference 2009. IACC 2009. IEEE, pp 894–899
Biryukov A, Dunkelman O, Keller N, Khovratovich D, Shamir A (2010) Key recovery attacks of practical complexity on aes-256 variants with up to 10 rounds. In: Annual international conference on the theory and applications of cryptographic techniques. Springer, pp 299–319
Biryukov A, Khovratovich D, Nikolić I (2009) Distinguisher and related-key attack on the full aes-256. In: Advances in cryptology-CRYPTO 2009. Springer, pp 231–249
Cox IJ, Kilian J, Leighton FT, Shamoon T (1997) Secure spread spectrum watermarking for multimedia. IEEE Trans Image Process 6(12):1673–1687
da Silva PHF, Cruz RMS, Assuncao AGD (2010) Neuromodeling and natural optimization of nonlinear devices and circuits. System and Circuit Design for Biologically-Inspired Intelligent Learning, pp 1969067189
Fakhari P, Vahedi E, Lucas C (2011) Protecting patient privacy from unauthorized release of medical images using a bio-inspired wavelet-based watermarking approach. Digit Signal Process 21(3):433–446
Garcia-Hernandez JJ, Gomez-Flores W, Rubio-Loyola J (2016) Analysis of the impact of digital watermarking on computer-aided diagnosis in medical imaging. Comput Biol Med 68:37–48
Hykin S (1999) Neural networks: a comprehensive foundation. Printice-hall. Inc., New Jersey
Karaboga D, Basturk B (2007) A powerful and efficient algorithm for numerical function optimization: artificial bee colony (abc) algorithm. J Glob Optim 39(3):459–471
Lei B, Tan E-L, Chen S, Ni D, Wang T, Lei H (2014) Reversible watermarking scheme for medical image based on differential evolution. Expert Syst Appl 41(7):3178–3188
Li M, Poovendran R, Narayanan S (2005) Protecting patient privacy against unauthorized release of medical images in a group communication environment. Comput Med Imaging Graph 29(5):367–383
Naheed T, Usman I, Khan TM, Dar AH, Shafique MF (2014) Intelligent reversible watermarking technique in medical images using ga and pso. Optik-Int J Light Electron Opt 125(11):2515–2525
Rosenblatt F (1958) The perceptron: a probabilistic model for information storage and organization in the brain. Psychol Rev 65(6):386
Selesnick IW (1999) The slantlet transform. IEEE Trans Signal Process 47 (5):1304–1313
Shih FY, Wu Y-T (2005) Robust watermarking and compression for medical images based on genetic algorithms. Inf Sci 175(3):200–216
Shih FY, Zhong X (2016) High-capacity multiple regions of interest watermarking for medical images. Inf Sci 367:648–659
Thodi DM, Rodríguez JJ (2007) Expansion embedding techniques for reversible watermarking. IEEE Trans Image Process 16(3):721–730
Tian J (2003) Reversible data embedding using a difference expansion. IEEE Trans Circ Syst Video Technol 13(8):890–896
Tian Y, Tan T, Wang Y, Fang Y (2003) Do singular values contain adequate information for face recognition? Pattern Recogn 36(3):649–655
Wakatani A (2002) Digital watermarking for roi medical images by using compressed signature image. In: Proceedings of the 35th annual Hawaii international conference on system sciences 2002. HICSS. IEEE, pp 2043–2048
Wang Z-H, Lee C-F, Chang C-Y (2013) Histogram-shifting-imitated reversible data hiding. J Syst Softw 86(2):315–323
Wei JC, Kern GM (1989) Commonality analysis: a linear cell clustering algorithm for group technology. Int J Prod Res 27(12):2053–2062
Zain JM, Clarke M (2011) Reversible region of non-interest (roni) watermarking for authentication of dicom images. arXiv:1101.1603
Zhao Z, Luo H, Lu Z-M, Pan J-S (2011) Reversible data hiding based on multilevel histogram modification and sequential recovery. AEU-Int J Electron Commun 65(10):814–826
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Bamal, R., Kasana, S.S. Dual hybrid medical watermarking using walsh-slantlet transform. Multimed Tools Appl 78, 17899–17927 (2019). https://doi.org/10.1007/s11042-018-6820-9
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-018-6820-9