Abstract
In this work we investigate the problem of simultaneous privacy and integrity protection in cryptographic circuits. We consider a white-box scenario with a powerful, yet limited attacker. A concise metric for the level of probing and fault security is introduced, which is directly related to the capabilities of a realistic attacker. In order to investigate the interrelation of probing and fault security we introduce a common mathematical framework based on the formalism of information and coding theory. The framework unifies the known linear masking schemes. We proof a central theorem about the properties of linear codes which leads to optimal secret sharing schemes. These schemes provide the lower bound for the number of masks needed to counteract an attacker with a given strength. The new formalism reveals an intriguing duality principle between the problems of probing and fault security, and provides a unified view on privacy and integrity protection using error detecting codes. Finally, we introduce a new class of linear tamper-resistant codes. These are eligible to preserve security against an attacker mounting simultaneous probing and fault attacks.

Similar content being viewed by others
References
Anderson RJ, Kuhn MG (1996) Tamper resistance—a cautionary note. In: Second USENIX workshop on electronic commerce, pp 1–11
Barak B, Goldreich O, Impagliazzo R, Rudich S, Sahai A, Vadhan S, Yang K (2001) On the (im)possibility of obfuscating programs (extended abstract). In: Kilian J (ed) Advances in cryptology—CRYPTO 2001—21st annual international cryptology conference. Santa Barbara, California, USA, 19–23 Aug 2001. Proceedings, Lecture Notes in Computer Science, vol 2139. Springer, Berlin, pp 1–18
Biham E, Shamir A (1997) Differential fault analysis of secret key cryptosystems. In: Kaliski BS Jr (ed) Advances in cryptology—CRYPTO ’97, 17th annual international cryptology conference, Santa Barbara, California, USA, 17–21 Aug 1997. Proceedings, Lecture Notes in Computer Science, vol 1294. Springer, Berlin, pp 513–525
Boit C, Schlangen R, Kerst U, Lundquist T (2008) Physical techniques for Chip-backside IC debug in nanotechnologies. IEEE Des Test Comput 25(3):250–257
Boneh D, DeMillo RA, Lipton RJ (2001) On the importance of eliminating errors in cryptographic computations. J Cryptol 14(2):101–119
Chari S, Jutla CS, Rao JR, Rohatgi P (1999) Towards sound approaches to counteract power-analysis attacks. In: Wiener MJ (ed) Advances in cryptology—CRYPTO ’99, 19th annual international cryptology conference, Santa Barbara, California, USA, 15–19 Aug 1999. Proceedings, Lecture Notes in Computer Science, vol 1666. Springer, Berlin, pp 398–412
Cover TM, Thomas JA (2006) Elements of information theory. Wiley series in telecommunications and signal processing, 2nd edn. Wiley-Interscience, New York. ISBN 0-471-24195-4
Gennaro R, Lysyanskaya A, Malkin T, Micali S, Rabin T (2004) Algorithmic tamper-proof (ATP) security: theoretical foundations for security against hardware tampering. In: Naor M (ed) Theory of cryptography. First theory of cryptography conference, TCC 2004, Cambridge, MA, USA, 19–21 Feb 2004. Proceedings, Lecture Notes in Computer Science, vol 2951. Springer, Berlin, pp 258–277
Gössel M, Ocheretny V, Sogomonyan E, Marienfeld D (2008) New methods of concurrent checking. Frontiers in Electronic Testing, FRET, vol 42. Springer, Berlin
Handschuh H, Paillier P, Stern J (1999) Probing attacks on tamper-resistant devices. In: Koç ÇK, Paar C (eds) Cryptographic hardware and embedded systems—CHES’99. First international workshop, Worcester, MA, USA, 12–13 Aug 1999. Proceedings, Lecture Notes in Computer Science, vol 1717. Springer, Berlin, pp 303–315
Hsiao MY (1970) A class of optimal minimum odd-weight-column SEC-DED codes. IBM J Res Develop 14:395–401
Ishai Y, Prabhakaran M, Sahai A, Wagner D (2006) Private circuits II: keeping secrets in tamperable circuits. In: Vaudenay S (ed) Advances in cryptology—EUROCRYPT 2006, 25th annual international conference on the theory and applications of cryptographic techniques, St. Petersburg, Russia, May 28–June 1, 2006. Proceedings, Lecture Notes in Computer Science, vol 4004. Springer, Berlin, pp 308–327
Ishai Y, Sahai A, Wagner D (2003) Private circuits: securing hardware against probing attacks. In: Boneh D (ed) Advances in cryptology—CRYPTO 2003, 23rd annual international cryptology conference, Santa Barbara, California, USA, 17–21 Aug 2003. Proceedings, Lecture Notes in Computer Science, vol 2729. Springer, Berlin, pp 463–481
Kocher PC, Jaffe J, Jun B (1999) Differential power analysis. In: Wiener M (ed) Advances in cryptology—CRYPTO ’99, 19th annual international cryptology conference, Santa Barbara, California, USA, 15–19 Aug 1999. Proceedings, Lecture Notes in Computer Science, vol 1666. Springer, Berlin, pp 388–397
MacWilliams FJ, Sloane NJA (2006) The theory of error-correcting codes, Mathematical Library, vol 16, 12th edn. North-Holland, Amsterdam. ISBN 0-444-85193-3
Mangard S, Oswald E, Popp T (2007) Power analysis attacks—revealing the secrets of smart cards. Springer, Berlin. ISBN 0-387-30857-1
Massey JL (1993) Minimal codewords and secret sharing. In: Proceedings of the 6th joint Swedish–Russian international workshop on information theory, pp 276–279
Messerges TS (2000) Securing the AES finalists against power analysis attacks. In: Schneier B (ed) Fast software encryption, 7th International workshop, FSE 2000, New York, NY, USA, 10–12 April 2000. Proceedings, Lecture Notes in Computer Science, vol 1978. Springer, Berlin, pp 150–164
Micali S, Reyzin L (2004) Physically observable cryptography (extended abstract). In: Naor M (ed) Theory of cryptography. First theory of cryptography conference, TCC 2004, Cambridge, MA, USA, 19–21 Feb 2004. Proceedings, Lecture Notes in Computer Science, vol 2951. Springer, Berlin, pp 278–296
Schmidt J-M, Kim CH (2009) A probing attack on AES. In: Chung K-I, Sohn K, Yung M (eds) Information security applications: 9th international workshop, WISA 2008, Jeju Island, Korea, September 23–25, 2008, Revised selected papers. Lecture Notes in Computer Science, vol 5379. Springer, Berlin, pp 256–265
Shannon CL (1949) Communication theory of secrecy systems. Bell Syst Tech J 28:656–715
Siegenthaler T (1984) Correlation-immunity of nonlinear combining functions for cryptographic applications. IEEE Trans Inf Theory 30(5):776–780
Skorobogatov SP, Anderson RJ (2003) Optical fault induction attacks. In: Kaliski BS Jr, Koç ÇK, Paar C (eds) Cryptographic hardware and embedded systems—CHES 2002, 4th international workshop, Redwood Shores, CA, USA, 13–15 August 2002, Revised papers. Lecture Notes in Computer Science, vol 2523. Springer, Berlin, pp 2–12
Vernam GS (1919) (AT&T Bell Labs). Secret signaling system. United States Patent 1,310,719, 22 July 1919, filed 13 Sept 1918
Author information
Authors and Affiliations
Corresponding author
Additional information
Responsible Editor: K. Chakrabarty
Appendices
Appendix A: Example for OPS(7,4;2) Masking Scheme
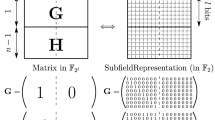
A number of s = 3 mask bits provides probing security PS(2) for data words of length k = 4. The canonical probing matrix in the OPS(7,4;2) masking scheme is a [7, 4, 3] Hamming code.
In explicit terms, the corresponding generator matrix (2) induces the masking scheme
Appendix B: Example for OPS(16,11;3) Masking Scheme
A number of s = 5 mask bits can provide probing security PS(3) for data words of length k = 11. The canonical probing matrix in the OPS(16,11;3) masking scheme is a [16, 11, 4] Hsiao code [11].
Appendix C: Example for OPS(17,9;4) Masking Scheme
The [17, 9, 5] quadratic residue code, cf. [15], generates an OPS(17,9;4) masking scheme. Using the generator polynomial x 8 + x 5 + x 4 + x 3 + 1 the following canonical probing matrix is obtained.
Appendix D: Example for OTR(7,4,1;2,2) Tamper Resistant Code
To achieve a forcing security of order 2, FRS(2), we start with the parity check matrix of a [7, 4, 3] Hamming code. The distance of this code is d min = 3 and the number of redundancy bits is r = n − k = 3.
As given by Table 1 a number of s = 3 masks bits is required to achieve PS(2) for an OPS code of length n = 7. Hence a maximum of j = k − s = 1 information bits can be protected. The canonical generator matrix can be easily constructed by applying elementary row operations:
It is immediate that any two columns in the probing matrix (lower part of G) are linearly independent. Hence this OTR code is PS(2).
Appendix E: Example for OTR(16,11,6;3,3) Tamper Resistant Code
In this nontrivial example we use a minimum weight Hsiao code (d min = 4) of length n = 16 and dimension k = 11 as a starting point to achieve FRS(3),
From Table 1 we see that s = 5 masks are necessary to secure n = 16 bits against a probing attack of order 3. Applying elementary row operations the generator matrix of an equivalent PS(3)-secure code can be constructed:
This OTR code can secure j = k − s = 6 bits of information simultaneously against FRA(3) and PA(3) attacks.
Rights and permissions
About this article
Cite this article
Gammel, B.M., Mangard, S. On the Duality of Probing and Fault Attacks. J Electron Test 26, 483–493 (2010). https://doi.org/10.1007/s10836-010-5160-0
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10836-010-5160-0