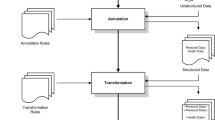
Medical image processing methods and algorithms, developed by researchers, need to be validated and tested. Test data would ideally be real clinical data especially that clinical data is varied and exists in large volumes. Nowadays, clinical data is accessible electronically and has important value for researchers. However, the usage of clinical data for research purposes should respect data confidentiality, patient right to privacy, and patient consent. In fact, clinical data is nominative given that it contains information about the patient such as name, age, and identification number. Evidently, clinical data needs to be de-identified to be exported to research databases. However, the same patient is usually followed during a long period of time. The disease progression and the diagnostic evolution represent extremely valuable information for researchers as well. Our objective is to build a research database from de-identified clinical data while enabling the data set to be easily incremented by exporting new pseudonymous data, acquired over a long period of time. Pseudonymization is data de-identification, such that data belonging to an individual in the clinical environment still belong to the same individual in the de-identified research version. In this paper, we explore various software architectures to enable the implementation of an imaging research database that can be incremented in time. We also evaluate their security and discuss their security pitfalls. As most imaging data accessible electronically is available with the digital imaging and communication in medicine (DICOM) standard, we propose a de-identification scheme that closely follows DICOM recommendations. Our work can be used to enable electronic health record (EHR) secondary usage such as public surveillance and research, while maintaining patient confidentiality.




Similar content being viewed by others
References
YC Chiang TS Hsu S Kuo CJ Liau DW Wang (2003) ArticleTitlePreserving confidentiality when sharing medical database with the Cellsecu system Int J Med Inf 71 IssueID1 17–23 Occurrence Handle10.1016/S1386-5056(03)00030-3
A Ohrn L Ohno-Machado (1999) ArticleTitleUsing Boolean reasoning to anonymize databases Artif Intell Med 15 IssueID3 235–254 Occurrence Handle10206109 Occurrence Handle10.1016/S0933-3657(98)00056-6 Occurrence Handle1:STN:280:DyaK1M3itV2msg%3D%3D
Hundepool A, Willenborg L: μ- and τ-ARGUS: software for statistical disclosure control. Proc. Third International Seminar on Statistical Confidentiality. Bled, 1996
L Sweeney (1998) Datafly: a system for providing anonymity in medical data TY Lin S Qian (Eds) Database Security XI: Status and Prospects Chapman and Hall New York
L Ohno-Machado PSP Silveira S Vinterbo (2004) ArticleTitleProtecting patient privacy by quantifiable control of disclosures in disseminated databases Int J Med Inf 73 IssueID7-8 599–606 Occurrence Handle10.1016/j.ijmedinf.2004.05.002
Digital Imaging and Communications in Medicine (DICOM), Supplement 55: Attribute Level Confidentiality (including De-identification), National Electrical Manufacturers Association, 2002
Schneier B: Applied Cryptography Second Edition: protocols, algorithms, and source code in C, John Wiley, 1996
Radiology, IHE Technical Framework, http://www.ihe.net
IT Infrastructure, IHE Technical Framework, http://www. ihe.net
K Pommerening M Reng (2004) Secondary use of the electronic health record via pseudonymisation L Bos S Laxminarayan A Marsh (Eds) Medical Care Compunetics 1 IOS Press Amsterdam 441–446
M Peyraviana A Roginskya A Kshemkalyanib (1998) ArticleTitleOn probabilities of hash value matches Comput Secur 17 IssueID2 171–174 Occurrence Handle10.1016/S0167-4048(97)82016-0
Klein DV: ‘Foiling the Cracker’: A Survey of, and Implications to, Password Security. Proceedings of the USENIX UNIX Security Workshop, 1990, pp 5–14
Feldmeier DC, Karn, PR: UNIX Password Security-Ten Years Later. Advances in cryptology-CRYPTO ’89 Proceedings, Springer, Berlin Heidelberg New York 1990, pp 44–63
Acknowledgments
This work was supported by the Natural Sciences and Engineering Research Council of Canada.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Noumeir, R., Lemay, A. & Lina, JM. Pseudonymization of Radiology Data for Research Purposes. J Digit Imaging 20, 284–295 (2007). https://doi.org/10.1007/s10278-006-1051-4
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10278-006-1051-4