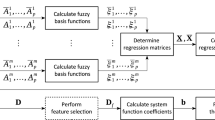
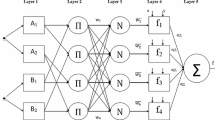
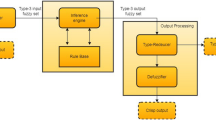
Abstract
Wireless sensor network (WSN) is employed in variety of applications ranging from agriculture to military. WSN is vulnerable to various security attacks, in which jamming attacks obstruct and disturb the exchange of information between sensor nodes in WSN by transmitting signals to jam legitimate transmission to cause a denial of service. Hence, it is essential to secure the sensor networks from jamming attacks. In this paper, two approaches: fuzzy inference system (FIS) and adaptive neuro-fuzzy inference system (ANFIS)-based jamming detection system are proposed for detecting the presence of jamming by computing two jamming detection metrics, namely, packet delivery ratio and received signal strength indicator. FIS approach is based on Takagi–Sugeno fuzzy logic which optimizes the jamming detection metrics. ANFIS approach combines fuzzy logic and learning ability of the neural network to optimize the metrics for detecting various types of jamming. The proposed approaches are compared with existing system and themselves. The simulation result shows that the proposed ANFIS approach detects the jamming attacks as high as true detection ratio.













Similar content being viewed by others
References
Abbasi AA, Younis M (2007) A survey on clustering algorithms for wireless sensor networks. Comput Commun 30(14–15):2826–2841
Akyildiz IF, Su W, Sankarasubramaniam Y, Cayirci E (2002) Wireless sensor networks: a survey. Comput Netw 38(4):393–422
Alrajeh NA, Khan S, Shams B (2013) Intrusion detection systems in wireless sensor networks: a review. Int J Distrib Sens Netw 2013:1–7
Azad P, Sharma V (2013) Cluster head selection in wireless sensor networks under fuzzy environment. ISRN Sens Netw 2013:1–8
Boyinbode O, Le H, Mbogho A, Takizawa M, Poliah R (2010) A survey on clustering algorithms for wireless sensor networks. In: Proceedings of the 13th international conference on network-based information systems, pp 358–364. https://doi.org/10.1109/nbis.2010.59
Cakiroglu M, Ozcerit AT (2008) Jamming detection mechanisms for wireless sensor networks. In: Proceedings of the 3rd international conference on scalable information systems, pp 4–6, June 2008
Chen J-S, Hong Z-W, Wang N-C, Jhuang S-H (2010) Efficient cluster head selection methods for wireless sensor networks. J Netw 5(8):964–970
Crosby GV, Pissinou N, Gadze J (2006) A framework for trust-based cluster head election in wireless sensor networks. In: Proceedings of 2nd IEEE workshop on dependability and security in sensor networks and systems, Columbia, pp 13–22
Devi R, Jha RK, Gupta A, Jain S, Kumar P (2017) Implementation of intrusion detection system using adaptive neuro-fuzzy inference system for 5G wireless communication network. Int J Electron Commun 74:94–106
Egbogah EE, Fapojuwo AO (2011) A survey of system architecture requirements for health care-based wireless sensor networks. Sensors 11:4875–4898
Fei H, Jiang M, Celentano L, Xiao Y (2008) Robust medical ad hoc sensor networks (MASN) with wavelet-based ECG data mining. Ad Hoc Netw 6(7):986–1012
Ferdous R, Muthukkumarasamy V, Sithirasenan E (2011) Trust-based cluster head selection algorithm for mobile ad hoc networks. In: IEEE 10th international conference on trust, security and privacy in computing and communications (TrustCom), Changsha, pp 589–596
Ganeshkumar P, Vijayakumar KP, Anandaraj M (2016) A novel jammer detection framework for cluster based wireless sensor networks. EURASIP J Wirel Commun Netw. https://doi.org/10.1186/s13638-016-0528-1
Hong S, Lim S, Song J (2011) Unified modeling language based analysis of security attacks in wireless sensor networks: a survey. KSII Trans Internet Inf Syst. https://doi.org/10.3837/tiis.2011.04.010
Hussain K, Abdullah AH, Iqbal S, Awan KM, Ahsan F (2013) Efficient cluster head selection algorithm for MANET. J Comput Netw Commun 2013:7
Jo M, Han L, Duy Tan N, Peter H (2015) A survey: energy exhausting attacks in MAC protocols in WBANs. Telecommun Syst 58(2):153–164. https://doi.org/10.1007/s11235-014-9897-0
Kang S, Lee S, Ahn S, An S (2012) Energy efficient topology control based on sociological cluster in wireless sensor networks. KSII Trans Internet Inf Syst 6(1):339–358
Kuila P, Jana PK (2012) Improved load balanced clustering algorithm for wireless sensor networks. Adv Comput Netw Secur 7135:399–404
Kumar D (2014) Performance analysis of energy efficient clustering protocol for maximizing lifetime of wireless sensor networks. IET Wirel Sens Syst 4(1):9–16
Liu X (2012) A survey on clustering routing protocols in wireless sensor networks. Sensors 12(8):11113–11153. https://doi.org/10.3390/s120811113
Liu X, Shi J (2012) Clustering routing algorithms in wireless sensor networks: an overview. KSII Trans Internet Inf Syst 6(7):1735–1755
Manju VC, Kumar MS (2012) Detection of jamming style DoS attack in wireless sensor network. In: Proceedings of second IEEE international conference on parallel distributed and grid computing (PDGC), pp 563–567
Mario S, Boris D, Srdjan C (2010) Detection of reactive jamming in sensor networks. ACM Trans Sens Netw. https://doi.org/10.1145/1824766.1824772
Mathur N, Glesk I, Buis A (2016) Comparison of adaptive neuro-fuzzy inference system (ANFIS) and Gaussian processes for machine learning (GPML) algorithms for the prediction of skin temperature in lower limb prostheses. Med Eng Phys 38(10):1083–1089
Misra S, Singh R, Rohith Mohan SV (2010) Information warfare-worthy jamming attack detection mechanism for wireless sensor networks using a fuzzy inference system. Sensors 10(4):3444–3479
Mo S, Chen H, Yinglong L (2011) Clustering-based routing for top-k querying in wireless sensor networks. EURASIP J Wirel Commun Netw 2011:73
Mokammel Haque M, Pathan A-SK, Hong CS, Huh E-N (2008) An asymmetric key-based security architecture for wireless sensor networks. KSII Trans Internet Inf Syst. https://doi.org/10.3837/tiis.2008.05.004
Paramasivan B, Kaliappan M (2014) Secure and fair cluster head selection protocol for enhancing security in mobile ad hoc networks. Sci World J 2014:1–6
Park S-J, Vedantham R, Sivakumar R, Akyildiz IF (2008) GARUDA: achieving effective reliability for downstream communication in wireless sensor networks. IEEE Trans Mob Comput 7(2):214–230
Rajshekhar Chalak A, Misra S, Obaidat MC (2010) A cluster-head selection algorithm for wireless sensor networks. In: 17th IEEE international conference on electronics, circuits, and systems ICECS, pp 130–133
Rani TP, Jayakumar C (2012) Survey on key pre distribution for security in wireless sensor networks. Adv Comput Sci Inf Technol Netw Commun 84:248–252. https://doi.org/10.1007/978-3-642-27299-8_26
Shi E, Perrig A (2004) Designing secure sensor networks. IEEE Wirel Commun 11(6):38–43
Shon T, Park Y (2009) A hybrid adaptive security framework for IEEE 802.15.4-based wireless sensor networks. KSII Trans Internet Inf Syst. https://doi.org/10.3837/tiis.2009.06.002
Siddhabathula K, Dong Q, Liu D, Wright M (2012) Fast jamming detection in sensor networks. In: Proceedings of IEEE international conference on communications, pp 934–938
Sikander G, Zafar MH, Raza A, Babar MI, Mahmud SA, Khan GM (2013) A survey of cluster based routing schemes for wireless sensor network. Smart Comput Rev 13(4):261–275
Singh SP, Sharma SC (2015) A survey on cluster based routing protocols in wireless sensor networks. Procedia Comput Sci 45:687–695
Vijayakumar KP, Ganeshkumar P, Anandaraj M (2015) A novel jamming detection technique in wireless sensor networks. KSII Trans Internet Inf Syst 9(10):4223–4249
Vijayakumar KP, Ganeshkumar P, Anandaraj M, Selvaraj K, Sivakumar P (2018) Fuzzy logic–based jamming detection algorithm for cluster based wireless sensor network. Int J Commun Syst 31:e3567. https://doi.org/10.1002/dac.3567
Wang XY, Wong A (2013) Multi-parametric clustering for sensor node coordination in cognitive wireless sensor networks. PLoS ONE. https://doi.org/10.1371/journal.pone.0053434
Xu W, Trappe W, Zhang Y, Wood T (2005) The feasibility of launching and detecting jamming attacks in wireless networks. In: Proceedings of the sixth ACM international symposium on mobile ad hoc networking and computing, pp 46–57, Nov 2005
Yadav RK, Kumar V, Kumar R (2015) A discrete particle swarm optimization based clustering algorithm for wireless sensor networks. Adv Intell Syst Comput 338:137–144
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Conflict of interest
The authors declare that they have no conflict of interest.
Human and animal rights
We have not performed any experiments which involve animals or humans.
Additional information
Communicated by P. Pandian.
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Vijayakumar, K.P., Pradeep Mohan Kumar, K., Kottilingam, K. et al. An adaptive neuro-fuzzy logic based jamming detection system in WSN. Soft Comput 23, 2655–2667 (2019). https://doi.org/10.1007/s00500-018-3636-5
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00500-018-3636-5