Abstract
This work introduces XMSS-T, a new stateful hash-based signature scheme with tight security. Previous hash-based signatures are facing a loss of security, linear in performance parameters such as the total tree height. Our new scheme can achieve the same security level but using hash functions with a smaller output length, which immediately leads to a smaller signature size. The same techniques also apply directly to the recent stateless hash-based signature scheme SPHINCS (Eurocrypt 2015), and the signature size is reduced as well.
Being a little more specific and technical, the tight security stems from new multi-target notions of hash-function properties which we define and analyze. We show precise complexity for breaking these security properties under both classical and quantum generic attacks, thus establishing a reliable estimate for the quantum security of XMSS-T. Especially, we prove quantum query complexity tailored for cryptographic applications, which overcome some limitations of standard techniques in quantum query complexity such as they usually only consider worst-case complexity. Our proof techniques may be useful elsewhere.
We also implement XMSS-T and compare its performance to that of XMSS (PQCrypto 2011), the most recent stateful hash-based signature scheme before our work.
Full version of this paper including missing proofs is available at: http://ia.cr/2015/1256. This work was supported by European Commission through the ICT program under contract ICT-645622 (PQCRYPTO). Part of this work was done while the first author was visiting IQC. F.S. acknowledges support by Cryptoworks21, Canada’s NSERC and ORF.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
- Post-quantum cryptography
- Hash-based signatures
- Hash function security
- Multi-target attacks
- Quantum query complexity
1 Introduction
Hash-based signatures are considered the most promising post-quantum alternative to existing schemes RSA and ECDSA which are vulnerable to quantum attacks. This is especially because the security of cryptographic hash functions has been well understood under intensive scrutinization. In addition, there are exact reductionist proofs relating the hardness of breaking the schemes to the hardness of breaking security properties of the hash functions used in the schemes. This allows precise estimation on the security of specific parameter sets.
Traditionally, the security of hash-based signature schemes was related to collision-resistance of the used hash function. In recent years several works focused on basing security on milder assumptions [5, 11, 12, 15, 20, 22], such as second-preimage resistance and one-wayness. There are two fundamental reasons driving this trend. On the one hand, the attacks against the collision-resistance of SHA1 and MD5 motivated researchers to develop collision-resilient signature schemes [19, 26]. On the other hand, collision resistance is subject to birthday attacks while (second-)preimage resistance is not. Hence, to reach a security level of \(\lambda \) bits, a hash function with \(n = 2\lambda \) bit digests is needed if collision resistance is required whereas for (second-)preimage resistance only \(n = \lambda \) bit digests are needed. Halving the output size of the used hash function immediately halves the signature and key sizes of hash-based signatures.
Multi-target Attacks. The above statement is only half the truth because it bears on the implicit assumption that a hash function is used only once. Clearly, for many cryptographic constructions this is not the case. Consider for example preimage resistance (aka. one-wayness). For many cryptographic constructions, an adversary will be able to learn a magnitude of function values and security breach may occur once he finds a preimage for just one of them. More specifically, suppose that a hash function with n bit outputs is used d times in a cryptographic construction. If it suffices to invert the hash function on any one out of the d outputs to break the security of the scheme, then the attack complexity is downgraded to \(\mathcal {O}(2^n / d\)) instead of \(\mathcal {O}(2^n)\). Intuitively this is because every input value that an adversary tries has probability \(d/2^n\) of being a solution instead of \(1/2^n\), if we treat the hash function as a random function. For theoretical (asymptotic) security this worries nobody as d is normally at most polynomial in n. However, when choosing parameters in practice this can easily cause serious consequences.
This issue is indeed very pertinent to hash-based signatures. Consider for example the hash-based signature scheme XMSS [12] and its multi-tree version \(\text {XMSS}^{MT}\) [22] (see Sect. 4) with parameters that allow to use a keypair for a virtually unlimited amount of signatures (e.g. a total tree height of \(h=60\)). In this case, an attacker can learn about \(2^{66}\) images under the same hash function and will succeed in forging a signature if he finds a single preimage for any one of the \(2^{66}\) values. Consequently, to achieve for example security of 256 bits one cannot use a 256 bit hash function but has to use one with output length 322. This does not only imply the use of a hash function with a bigger output length (and hence a slowdown), it also increases the signature size by roughly \(25\,\%\).
This Work. In this work we introduce a new hash-based signature scheme XMSS-T that is not vulnerable to multi-target attacks. Towards this end, we propose two new multi-target notions for preimage and second-preimage resistance. We then analyze the generic security of hash functions with regard to these new properties against classical and quantum adversaries, proving upper and lower bounds on the query complexity of generic attacks. More specifically, the first type of notions (single-function multi-target) models a notion that is implicitly used by recent collision-resilient hash-based signature schemes like XMSS, \(\text {XMSS} ^{MT}\) and SPHINCS [5, 12, 22]. In these notions, an adversary \(\mathcal {A}\) receives p target values and a random function from the hash function family. Then, \(\mathcal {A}\) is asked to find a preimage (or second-preimage, respectively) for one of the target values under the given function. We prove that compared to standard (second-)preimage resistance, the query complexity of generic attacks drops by a factor p for classical and \(\sqrt{p}\) for quantum adversaries. Then we introduce multi-function multi-target notions of preimage and second-preimage resistance. For these notions, \(\mathcal {A}\) is given multiple pairs of function and target value, drawn independently at random. It is now \(\mathcal {A}\) ’s goal to find a preimage (or second-preimage, respectively) for one of the target values under the associated function. We prove that in this case the query complexity of generic attacks is exactly the same as for the standard (single-function, single-target) notions.
Given that multi-function multi-target notions are as hard as the standard notions of preimage and second-preimage resistance we construct a new hash-based signature scheme with security based on these new notions. As the basic construction follows that of XMSS, we call the new scheme XMSS-T, indicating XMSS with tightened security. While XMSS looses in the bit security an amount linear in several parameters including the total tree height, XMSS-T looses only two bits, independent of any parameters. The differences between \(\text {XMSS}^{MT}\) and XMSS-T are a different hash tree and one-time signature scheme construction such that the security can be based on the multi-target multi-function properties. The basic change is that for every hash function call within a hash tree or a hash chain, a different hash function key and different bitmasks are used. Note that XMSS-T is stateful and it may be not suitable in some practical use cases. The good news is that we can make similar changes to the stateless hash-based signature scheme SPHINCS easily. Roughly speaking, it amounts to replacing the used hash trees and one-time signatures by the ones described in this work.
Finally, we present an implementation of XMSS-T and compare it to XMSS and \(\text {XMSS}^{MT}\). We show that the applied changes only have marginal performance implications (a factor 3 loss in speed for all algorithms). Our code is available at https://joostrijneveld.nl/papers/multitarget_xmss.
Remarks on Proving Quantum Generic Security. At first sight the tasks of breaking the various security properties for hash functions seem similar to some standard problems studied in quantum query complexity. However due to some limitations, existing results such as techniques for proving quantum query lower bounds [2, 3] cannot be applied directly. For example, there are famous works showing upper and lower bounds on finding collisions in r-to-1 functions [1, 9]. Nonetheless, random functions, whose properties our work studies, are very unlikely to be r-to-1. More generally, quantum query complexity usually considers worst-case complexity only, whereas in cryptographic settings we care about average-case complexity. Another issue is that, as observed by Zhandry [29], quantum query lower bounds often have implications about quantum algorithms with high success probability only. For cryptographic applications however, an attacker with small but noticeable chance of breaking a scheme is still relevant. Therefore, a complete lower bound would be bounding the success probability of any algorithm making a specified number of queries. It might be possible to find fixes by digging into existing works, the situation is yet unclear. We expect that techniques developed in this work can find useful in other cryptographic settings as well.
Organization. We introduce and discuss the new security notions for hash function families in Sect. 2, where detailed analysis for quantum generic security is presented in Section 3. In Sect. 4 we present XMSS-T and discuss its security in Sect. 5. Finally, we present our implementation results in Sect. 6.
Notation. We write \(x \mathop {\longleftarrow }\limits ^{\$}\mathcal {X}\) if x is randomly chosen from the set \(\mathcal {X}\) using the uniform distribution. We further write \(\log \) for \(\log _2\). We denote the uniform distribution over bit strings of length n by \(\mathcal {U}_{n}\). We write \(m = \text {poly}\left( n\right) \) to denote that m is a function, polynomial in n. We call a function \(\epsilon (n) : \mathbb {N}\rightarrow [0,1]\) negligible and write \(\epsilon (n) = \mathrm{negl} {\left( n\right) }\) if for any \(c \in \mathbb {N}, c > 0\) there exists a \(n_c \in \mathbb {N}\) s.th. \(\epsilon (n) < n^{-c}\) for all \(n > n_c\).
2 New Security Notions for Hash Function Families
In this section, we recall some known and define several new security notions for (hash) function families and discuss their security against both classical and quantum generic attacks. In the following we restrict ourselves to function families that operate on bit strings and have a fixed input size, as this is the case in our constructions. However, the definitions are the same for the more general case. In the following let \(n\in \mathbb {N}\) be the security parameter, \(m=\text {poly}\left( n\right) ,k =\text {poly}\left( n\right) \), and \(\mathcal {H} _n = \{\textsc {H} _K: \{0,1\}^{m} \rightarrow \{0,1\}^n\}_{K \in \{0,1\}^k}\) be a family of functions. We say a function family \(\mathcal {H} _n\) is efficient if there exists a probabilistic polynomial time (PPT) algorithm that evaluates \(\textsc {H} _K(M)\) for any \(M \in \{0,1\}^m\) and \(K \in \{0,1\}^k\). We require all used functions to be efficient, unless we state otherwise. For hash-based signatures we are mainly interested in functions with \(m,k \ge n\). However, we try to keep our results as general as possible and make it explicit whenever we are relying on \(m,k \ge n\).
2.1 Defining the Security Notions
Preimage-Resistance (OW). Let’s revisit the standard notion of preimage resistance (a.k.a. one-wayness). We define the success probability of an adversary \(\mathcal {A}\) against the preimage resistance of a hash function family \(\mathcal {H} _n\) as
Single-Function, Multi-target Preimage Resistance ( SM-OW ). We now define the success probability of an adversary against \({\textsc {sm-ow}}\). This is the basic multi-target notion of preimage resistance implicitly used by previous collision resilient hash-based signature schemes like XMSS. We show in Sect. 3 that this notion is significantly easier to attack than standard preimage resistance. The definition takes another parameter p defining the number of targets.
Multi-Function, Multi-target Preimage Resistance (MM-OW). Next we define the success probability of an adversary \(\mathcal {A}\) against \({\textsc {mm-ow}}\). This is the notion we are aiming for with XMSS-T as it is as hard to break as standard preimage resistance, as we will show below. Again the definition is parameterized by the number of targets:
The difference between these two new definitions is that for \({\textsc {sm-ow}}\) all targets are for the same function while for \({\textsc {mm-ow}}\) each target has an associated random function from the family. We decided that \(\mathcal {A}\) has to output the associated index i in case of \({\textsc {mm-ow}}\) as otherwise any reduction would have to search for i and \(\mathcal {A}\) knows i for any attack that does better than guessing.
Second-Preimage Resistance ( SPR ). After presenting the multi-target notions for one-wayness, we now turn to second-preimage resistance. We start revisiting the standard notion of second-preimage resistance. We define the success probability of an adversary \(\mathcal {A}\) against the second-preimage resistance (\({\textsc {spr}})\) of a hash function family \(\mathcal {H} _n\) as
Note that in this definition the adversary is not promised to receive an M that actually has a second-preimage. Hence, especially for families \(\mathcal {H} _n\) with \(m = n\), i.e. same size of domain and co-domain, the adversaries success probability is largely influenced by the probability that a random M actually has a second-preimage.
Single-Function, Multi-target Second-Preimage Resistance ( SM-SPR ). As for one-wayness, we define two multi-target notions: single-function multi-target second-preimage resistance (\({\textsc {sm-spr}}\)) and multi-function multi-target second-preimage resistance (\({\textsc {mm-spr}}\)). The first one (\({\textsc {sm-spr}}\)) is the notion implicitly used in XMSS. The latter is the notion we aim for with XMSS-T that is as hard to break as standard second-preimage resistance, as we will prove below. We start defining the success probability of an adversary against \({\textsc {sm-spr}}\). The definition again takes another parameter p defining the number of targets:
Multi-function, Multi-target Second-Preimage Resistance ( MM-SPR ). Next we define the success probability of an adversary \(\mathcal {A}\) against \({\textsc {mm-spr}}\). Again the definition is parameterized by the number of targets:
Extended Target Collision Resistance ( E TCR ). In [19] Halevi and Krawczyk introduced extended target collision resistance (eTCR) as a hash function property that is close to target collision resistance. In the classical target-collision resistance game, the adversary is allowed to choose a target message M. Afterwards he learns a function (by learning a key K) and has to find a collision for the M under this function \(\textsc {H} _K\). While the setup of the eTCR game is exactly the same, the adversary wins if he can present a new message \(M'\) and a (possibly new) key \(K'\) such that \(\textsc {H} _K(M) = \textsc {H} _{K'}(M')\). Formally, the success probability of an adversary \(\mathcal {A} =(\mathcal {A} _1,\mathcal {A} _2)\), where \(\mathcal {A} _1\) and \(\mathcal {A} _2\) have shared memory, against \({\textsc {eTCR}}\) is defined as follows:
Multi-target Extended Target Collision Resistance ( M-E TCR ). We can also define a multi target version (\({\textsc {eTCR}}\) is inherently multi function anyway). To keep the definition readable we use a challenge oracle \(\mathsf {Box}(\cdot )\) that on input of a message outputs a uniformly random function key. This oracle models the ability of \(\mathcal {A} \) to adaptively obtain p eTCR challenges for the same function family. We denote by \((M_i, K_i)\) the ith query-answer pair of \(\mathsf {Box}(\cdot )\). The success probability of an adversary \(\mathcal {A} \) against m-eTCR that makes no more than p queries to \(\mathsf {Box}(\cdot )\) is defined as:
2.2 Generic Security
To determine secure parameters for hash function families or constructions based on them, their security against generic attacks is analyzed. Generic attacks show which security level is achievable at all for a given property as they do not take any possibly existing function specific weaknesses into account. A hash function family is considered broken if the security level for one property is (significantly) lower than the generic security.
Classical Generic Security. The standard way to analyze the complexity of generic attacks against a security property of hash function families is analyzing the success probability of an adversary \(\mathcal {A}\) against a random function family to which it is given black box access. The classical security is well understood in the literature. The security of the new notions we defined can be easily established as well. For completeness, we give brief justifications in Appendix A. Table 1 summarizes the classical and quantum generic security.
Quantum Generic Security. When we analyze the properties of hash functions under generic quantum attacks, we treat any hash function as a random function and the adversary can issue quantum superposition queries to the function. Namely, we are essentially working under the quantum random-oracle model [6]. When there are multiple functions, we assume they are independent random functions and the adversary can query them jointly in superposition. Namely, queries in the form of
are permittedFootnote 1. This choice is meant to capture the fact that in reality all hash functions are public, and a quantum adversary can certainly evaluate them jointly in superposition. This is in contrast to the classical setting, where each query must specify an index, and hence the adversary only gets one value of one function per query. One can define a similar model in the quantum setting (i.e., each query must specify one and only one function index K) and study all the security properties therein. We stress that this model seems weaker than the one we choose, and in particular our lower bounds results are hence stronger. Namely, they hold against stronger quantum attacks. It is an interesting theoretical question as to determining whether the two models are indeed different.
We prove our results regarding quantum generic security in Sect. 3. Our findings are summarized in Table 1. Please note that the constant hidden in the \(\varTheta \) is small, i.e. 16 for the lower bounds.
3 Analyzing Quantum Generic Security
In the following we establish the generic security of hash function families against quantum attacks on the defined properties. For each security property, we give attacks and analyze their success probabilities. All attacks are based on Grover’s quantum search algorithm, but we will need to analyze the complexity for random problem instances. More importantly, we establish matching lower bounds for all cases. The proofs of lower bounds follow a unified structure. Specifically, we first define a family of distributional search problems and bound the success probability of quantum algorithms against these problems. Then, we reduce various instances of the search problem to the task of breaking each of the security properties we care about. The hardness of the distributional search problems hence implies the generic security of hash functions for these security properties.
3.1 Toolbox
(Generalized) Grover’s Quantum Search Algorithm. One of the most useful algorithmic tools in quantum computing is Grover’s quantum search algorithm and its many generalizations (e.g., [7, 8, 10, 18] to name a few). Here we just need a simple version for searching a universe with multiple marked items. We state it in the following Lemma.
Lemma 1
Let \(f:\mathcal {X}\rightarrow \{0,1\}\) be an oracle function and let \(\mathcal {X}_f = \{x\in \mathcal {X}: f(x) =1\}\). Then there is a quantum algorithm \({\textsc {QSearch}}\) with q queries that finds an \(x\in \mathcal {X}_f\) with success probability \(\varOmega (q^2\frac{|\mathcal {X}_f|}{|X|})\).
Most of the attacks we describe later will apply QSearch in a straightforward way. However, since our problem instances are generated randomly, we will need to give a new analysis of the average-case performance.
A Hard Average-Case Search Problem. It is well known that Grover’s search algorithm is also optimal [4]. Namely, adopting notations from Lemma 1, any q-query algorithm can find a marked item with probability at most \(O(q^2 \frac{|X_f|}{|X|})\). However since the security notions we defined all refer to average-case problems, the worst-case lower bound of Grover’s search is not very useful. Here we introduce a distributional search problem, and prove a stringent hardness result.
Definition 1
Let \(\mathcal {F}:=\left\{ f: \{0,1\}^m \rightarrow \{0,1\}\right\} \) be the collection of all boolean functions on \(\{0,1\}^m\). Let \(\lambda \in [0,1]\) and \(\varepsilon >0\). Define a family of distributions \(D_\lambda \) on \(\mathcal {F} \) such that \(f\leftarrow _R D_\lambda \) satisfies
for any \(x\in \{0,1\}^m\).
We define Avg-Search \(_\lambda \) to be the problem that given oracle access to \(f\leftarrow D_\lambda \), finds an x such that \(f(x)=1\). For any quantum algorithm \(\mathcal {A}\) that makes q queries, we define
Theorem 1
\( \mathsf{Succ}_{\lambda }^q(\mathcal {A}) \le 8 \lambda (q+1)^2\) holds for any quantum algorithm \(\mathcal {A} \) with q queries.
Note that this theorem matches the intuitive argument that for \(f\leftarrow D_\lambda \), there are \(2^m \lambda \) marked items on average and hence any quantum algorithm needs \(\varTheta (\sqrt{2^m/{(2^m\lambda )}}) = \varTheta (1/\sqrt{\lambda })\) queries. We defer its proof to the full version.
Simulating Random Functions. In our reductions to show lower bounds, we usually assume we have access to some random function \(f: \mathcal {X}\rightarrow \mathcal {Y}\). Ultimately, we will need to simulate f efficiently so that any algorithm with q queries cannot notice a difference. Fortunately, the following claim allows us to do so by sampling uniformly from a 2q-wise independent hash function family \(\mathcal {H} \).
Lemma 2
[28, Theorem 6.1] For any quantum adversary that makes no more than q queries to either a truly random function or a function drawn uniformly from \(\mathcal {H} \), the final states are identical.
There exists a vast literature on efficient constructions of t-wise independent hash functions. Interested readers are referred to, e.g., [14, 23, 24]. There is a technical subtlety though. Most constructions of \(\mathcal {H} \) consider output space \(\mathcal {Y}\) with size being a prime or a prime power. We need one with \(\mathcal {Y}= [N], N = 2^n-1\). A natural approach is to pick a prime \(M >> N\) and construct a 2q-wise independent family \(\mathcal {H} _0: \mathcal {X}\rightarrow [M]\). Then we would expect that \(\mathcal {H}: x\mapsto \mathcal {H} _0(x) \mod N\) will suffice for our purpose, modulo a tiny error. However we were unable to identify a rigorous proof in the literature for the correctness of this “mod” construction, especially with respect to quantum attacks. We give a formal proof in the full version.
Sometimes we need a random function f that excludes some output \(y \in \mathcal {Y}\). This is easy to realize as follows. We take a random function \(g: \mathcal {X}\rightarrow [k]\) where \(k = |\mathcal {Y}| - 1\). Then f(x) will be obtained by applying g on x and then mapping the outcome to \(\mathcal {Y}\backslash y\) according to some canonical isomorphism (e.g., any thing smaller than y remains unchanged, and anything else is incremented by 1.).
3.2 Hardness of Breaking the Security
We analyze in this section the hardness of generic quantum attacks on the various notions of hash functions. We give upper bounds on the success probabilities of any quantum adversary making at most q queries. Basically, we reduce \({{\mathsf{Avg}\text {-}\mathsf{Search}}} _\lambda \) with various \(\lambda \) to the task of breaking the security notion generically. The hardness of Avg-Search then implies the security against generic quantum attacks. The bounds for \({\textsc {ow}}\), \({\textsc {spr}}\) and their variants are given in Propositions 1 and 2. While the proofs are quite similar we have to deal with a restriction for the \({\textsc {ow}}\) notions that we did not figure out how to circumvent. Namely, we require that \(2^m \gg 2^n\) (e.g. \(m = 2n\)) and \(p \ll 2^n\), which is the case for most relevant hash function families. The complexity for \({\textsc {eTCR}}\) and \({\textsc {m-eTCR}}\) involves additional technical difficulty concerning programming a random oracle, and we analyze them in Proposition 3.
Proposition 1
Let \(m = cn\) for a positive real constant \(c > 1\) and \(p = o(n)\). For any quantum adversary with q queries, it holds that
The proof is given in the full version.
Proposition 2
For any quantum adversary with q queries, it holds that
We give the proof for \({\textsc {mm-spr}}\). The others can be proven analogously and are deferred to the full version.
Proof
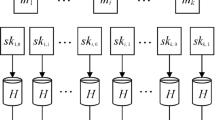
(Hardness of mm-spr ). Given an Avg-Search instance, we construct an instance of \({\textsc {mm-ow}} \) in Fig. 1:
Note that the way that f is generated ensures that each constructed \(\tilde{H}_i\) is distributed identically to a uniformly random function \(H:\{0,1\}^m\rightarrow \{0,1\}^n\). Therefore the output instance in the reduction is valid according to the definition Eq. 6. This implies that any q-query attacker solving \({\textsc {mm-spr}}\) will give rise to a 2q-query algorithm for \({{\mathsf{Avg}\text {-}\mathsf{Search}}} _\lambda \). As a consequence
follows by Theorem 1. We remark that, as mentioned in Sect. 3.1, \(\tilde{H}_i\) can be implemented efficiently.
Proposition 3
Let \(\varepsilon = 8 (q+1)^2/2^n\) and \(\delta = 4q^2/2^k\). For any quantum adversary with q queries, it holds that
To prove the proposition, we need a lemma that allows us to adaptively program a quantum random oracle. The proof follows standard techniques (see similar analyses for different scenarios in [16, 27]). Let \(\mathcal {A}\) be an arbitrary quantum algorithm and let \( H : \{0,1\}^m \times \{0,1\}^k \rightarrow \{0,1\}^n\) be a random function. Consider two games as follows:
-
Game \(G_0\): \(\mathcal {A}\) gets access to H. In phase 1, after making at most \(q_1\) queries to H, \(\mathcal {A}\) outputs a message \(M\in \{0,1\}^m\). Then a random \({\hat{K}}\in _R \{0,1\}^k\) is sampled and \(({\hat{K}},H_{\hat{K}}(M))\) is handed to \(\mathcal {A} \). \(\mathcal {A} \) continues to the second phase and makes at most \(q_2\) queries. \(\mathcal {A} \) outputs \(b\in \{0,1\}\) at the end.
-
Game \(G_1\): \(\mathcal {A}\) gets access to H. After making at most \(q_1\) queries to H, \(\mathcal {A}\) outputs a message \(M\in \{0,1\}^m\). Then a random \({\hat{K}}\in _R \{0,1\}^k\) is sampled as well as a random range element \(y\in _R \{0,1\}^n\). Program \(H_{\hat{K}}(M) = y\) and call the new oracle \(H'\). \(\mathcal {A} \) receives \(({\hat{K}}, y=H'_{\hat{K}}(M))\) and proceeds to the second phase. After making at most \(q_2\) queries, \(\mathcal {A} \) outputs \(b\in \{0,1\}\) at the end.
Lemma 3
\(\left| \Pr [\mathcal {A} (G_0) = 1] - \Pr [\mathcal {A} (G_1) = 1] \right| \le 2 \delta \), with \(\delta = 4 q^2 /2^k\).
The proof of the Lemma is described in the full version. Using the Lemma, we can prove Proposition 3.
Proof
(Proof of Proposition 3 ). We give a reduction from Avg-Search to breaking \({\textsc {eTCR}}\). Assume that there is \(\mathcal {A} \) that breaks \({\textsc {eTCR}}\) with probability \(\eta \). We construct an adversary \(\mathcal {A} '\) that solves Avg-Search with probability \(\eta - 2\delta \). Note that as long as \(\mathcal {A} \) does not notice that we reprogrammed H, its view would be identical to that of the standard \({\textsc {eTCR}}\) game, and by assumption \(\mathcal {A} \) wins with probability at least \(\eta \). By Lemma 3, reprogramming only incurs an additive error \(2\delta =4q^2/2^k\). We claim that \(\Pr [f(K^*,M^*) =1 ] \ge \eta - 2\delta \). But we know that the success probability of Avg-Search is at most \(\varepsilon :=8(q+1)^2/2^n\) by Theorem 1. Therefore \(\eta \le \varepsilon +2\delta \) and this proves Proposition 3. We can generalize the arguments above to the multi-target case easily.
3.3 Quantum Attacks
In this section, we apply quantum search algorithm QSearch to attack the various notions generically. In most cases, we get bounds on success probabilities matching the hardness results we have shown in Sect. 3.2.
Proposition 4
There exist quantum adversaries \(\mathcal {A} _1,\ldots , \mathcal {A} _8\) all of which making \(\varTheta (q)\) queries, such that
The proof is adapting standard analysis to the average case. We illustrate the basic idea by proving the case of preimage-resistance. The others are left to the full version.
Proof
(Quantum attack on ow ). We describe a O(q)-query attacker \(\mathcal {A} _1\) as follows. Given y and oracle access to H, \(\mathcal {A} _1\) will apply QSearch to search for x such that \(H(x)=y\). More specifically, \(\mathcal {A} _1\) constructs \(g_H: \{0,1\}^m \rightarrow \{0,1\}\) such that \(g_H(x)=1\) iff. \(H(x)=y\). Each evaluation on \(g_H\) can be realized efficiently by two queries to h. For any \(h \in \mathcal {H} \), let \(p_h:=\Pr _{H \leftarrow \mathcal {H}}[H=h]\) and let \(X_H = |H^{-1}(y)|\) be the random variable representing the preimage size of y. Then by Lemma 1 we can see that
In the last step we observe, by linearity of expectation, that
4 XMSS-T
The eXtended Merkle Signature Scheme (XMSS) was proposed by Buchmann, Dahmen, and Hülsing in [12]. The original proposal for XMSS essentially combines a collision-resilient version of the Winternitz one-time signature scheme (WOTS) from [11] with the collision-resilient hash tree construction from [15] and adds two different kinds of pseudorandom key generation, one leading an \({\textsc {{EU-CMA}}}\)-secure and one a forward-secure signature scheme. Under the name \(\text {XMSS}^{MT}\) Hülsing, Rausch, and Buchmann [22] later proposed a multi-tree version of XMSS.
In this work we introduce XMSS-T, XMSS with tightened security. In contrast to XMSS, XMSS-T avoids multi-target attacks. To this end, XMSS-T uses a new hash tree construction and a new WOTS variant WOTS-T. XMSS-T is based on \(\text {XMSS}^{MT}\). The main difference in the construction of \(\text {XMSS}^{MT}\) and XMSS-T is the use of independent function keys and bitmasks for every call to a hash function inside of the hash trees or WOTS-T. \(\text {XMSS}^{MT}\) used a single fixed key per function family and the same bitmask per internal tree level or chain position. The function keys and bitmasks used by XMSS-T are needed for verification. To keep the public key small these values are generated pseudorandomly, using a hash-based pseudorandom function family and a seed value that becomes part of the public key. In the following we describe XMSS-T.
Parameters. XMSS-T uses several parameters and several functions. The main security parameter is \(n\in \mathbb {N}\), the message digest length \(m \in \text {poly}\left( n\right) \). The functions include two keyed, short-input cryptographic hash functions \(\textsc {F}: \{0,1\}^n \times \{0,1\}^n\rightarrow \{0,1\}^n\) and \(\textsc {H}: \{0,1\}^{n}\times \{0,1\}^{2n}\rightarrow \{0,1\}^n\); one arbitrary-input randomized hash function \(\mathcal {H}:\{0,1\}^m\times \{0,1\}^*\rightarrow \{0,1\}^m\); and two ensembles of pseudorandom function families \(\mathcal {F} _n:\{0,1\}^n\times \{0,1\}^{*}\rightarrow \{0,1\}^n\), \(\mathcal {F} _m:\{0,1\}^n\times \{0,1\}^{*}\rightarrow \{0,1\}^m\), where we denote by \(\{0,1\}^*\) the ability to handle arbitrary input lengths up to some practical limit (e.g. \(2^{64}\) bits as in the case of the SHA family). Of course, these functions can all be built from a single cryptographic hash function, but the security analysis gets easier separating the functions according to the required properties.
XMSS-T uses a hyper-tree (a tree of trees) of total height \(h \in \mathbb {N}\), where h is a multiple of d and the hyper-tree consists of d layers of trees, each having height h / d. WOTS allows for a space-time trade-off using the Winternitz parameter \(w \in \mathbb {N}, w > 1\). The Winternitz parameter w and the length of the bit string that is signed \(\lambda \) determine \(\ell \) the number of function chains for WOTS:
The bit strings signed using WOTS are the m-bit message digests on the lowest layer and the n-bit root nodes of the layer below on all other layers.
As a running example we present concrete numbers for XMSS-T-256; the choices are explained in Sect. 6. For XMSS-T-256 we use \(n=256, m=316, h=60, d=3, w=16\) which leads to \(\ell _n=67\) and \(\ell _m=82\).
Addressing Scheme. XMSS-T requires an addressing scheme for hash function calls. Every addressing scheme that assigns to every call to either \(\textsc {F} \) or \(\textsc {H} \) within the virtual structure of a XMSS-T hyper-tree a unique address can be used (e.g. numbering all the calls in some order). We suggest to use a recursive addressing scheme that numbers sub-structures (e.g. a OTS key pair) inside a structure (e.g. a tree). The addressing scheme generates an address for a substructure, taking the address of the structure and appending the index of the substructure. For trees, which contain three different kinds of substructures (OTS key pairs, L-trees, and nodes), an additional identifier for the type of substructure is added. Below we assume that a function \(\textsc {GenAddr} (\mathbf {a} _s, index)\) exists that takes the address of the structure and the index of the substructure and outputs a unique address for this substructure within an XMSS-T key pair. The advantage of this addressing scheme is that it only uses information that is available when the hash call is executed.
The addressing scheme is publicly known and the same addresses can be used for all XMSS-T key pairs. The resulting addresses are used as inputs to PRF \(\mathcal {F} _n\) to pseudorandomly generate function keys and bitmasks.
WOTS-T. We now describe the new WOTS version. The construction differs from [20] in that it uses fresh keys and bitmasks for each hash function call. We denote the message length by \(\lambda \in \{n,m\}\) and to improve readability we write \(\ell , \ell _1\), and \(\ell _2\) instead of \(\ell _\lambda , \ell _{1,\lambda }\), and \(\ell _{2,\lambda }\). We include pseudorandom key generation, meaning that a seed value takes the place of a secret key in our description. We describe the algorithms as used by XMSS-T, hence, they take global secret and public information. For a standalone version, this information would have to be generated during key generation.
The difference between all WOTS variants is in the way the so called chaining function is constructed. WOTS-T uses the function \(\textsc {F}\) to construct the following chaining function:
Chaining Function \(c ^{i,j}(x,\mathbf {a} _\mathcal {C},\textsc {Seed})\) : On input of value \(x \in \{0,1\}^n\), iteration counter \(i \in \mathbb {N}\), start index \(j \in \mathbb {N}\), chain address \(\mathbf {a} _\mathcal {C} \), and (public) seed \(\textsc {Seed}\), the chaining function works the following way. In case \(i = 0\), \(c \) returns x, i.e., \(c ^{0,j}(x,\mathbf {a} _\mathcal {C},\textsc {Seed})=x\). For \(i>0\) we define \(c \) recursively as
where key \(k_{i,j} = \mathcal {F} _n(\textsc {Seed}, \textsc {GenAddr} (\mathbf {a} _\mathcal {C}, 2\cdot (j+i)))\) and bitmask \(r_{i,j} = \mathcal {F} _n(\textsc {Seed},\) \(\textsc {GenAddr} (\mathbf {a} _\mathcal {C}, 2\cdot (j+i)+1))\). I.e. in every round, the function first takes the bitwise xor of the previous value \(c ^{i-1,j}(x,\mathbf {a} _\mathcal {C},\textsc {Seed})\) and bitmask \(r_{i,j}\) and evaluates \(\textsc {F} \) with key \(k_{i,j}\) on the result.
Now we describe the three algorithms of WOTS-T.
Key Generation Algorithm \(((\mathsf {sk},\mathsf {pk})\longleftarrow \mathrm{WOTS} \text {.}\mathsf {kg} (\mathcal {S}, \mathbf {a} _\mathrm{OTS}, \textsc {Seed}))\) : On input of a global secret key seed \(\mathcal {S} \in \{0,1\}^n\) (used for every WOTS-T keypair within a XMSS-T keypair), the address of the WOTS-T keypair within a tree \(\mathbf {a} _\mathrm{OTS} \), and public seed \(\textsc {Seed}\), the key generation algorithm computes the internal secret key \(\mathsf {sk} = (\mathsf {sk} _1, \ldots , \mathsf {sk} _{\ell })\) as \(\mathsf {sk} _i \longleftarrow \mathcal {F} _n(\mathcal {S},\textsc {GenAddr} (\mathbf {a} _\mathrm{OTS}, i))\), i.e., the \(\ell \) n bit secret key elements are derived form the secret key seed using the address of the chain they are contained in. The public key \(\mathsf {pk} \) is computed as
where \(\mathbf {a} _{\mathcal {C} _i} = \textsc {GenAddr} (\mathbf {a} _\mathrm{OTS}, i)\). Note that \(\mathcal {S} \) requires less storage than \(\mathsf {sk} \); thus we generate \(\mathsf {sk} \) and \(\mathsf {pk} \) on the fly when necessary.
Signature Algorithm \((\sigma \longleftarrow \mathrm{WOTS} \text {.}\mathsf {sign} (M, \mathcal {S}, \mathbf {a} _\mathrm{OTS}, \textsc {Seed}))\) : On input of a \(\lambda \)-bit message M, the global secret key seed \(\mathcal {S} \in \{0,1\}^n\), the address of the WOTS-T keypair within a tree \(\mathbf {a} _\mathrm{OTS} \), and public seed \(\textsc {Seed}\), the signature algorithm first computes a base-w representation of M: \(M = (M_1 \ldots M_{\ell _1})\), \(M_i \in \{0,\ldots ,w-1\}\). That is, M is treated as the binary representation of a natural number x and then the w-ary representation of x is computed. Next it computes the checksum \(C = \sum _{i=1}^{\ell _1}(w-1-M_i)\) and its base w representation \(C = (C_1, \ldots , C_{\ell _2})\). The length of the base w representation of C is at most \(\ell _2\) since \(C \le \ell _1 (w-1)\). We set \(B = (b_{1}, \ldots , b_\ell ) = M \parallel C\), the concatenation of the base w representations of M and C. Then the internal secret key is generated using \(\mathsf {sk} _i \longleftarrow \mathcal {F} _n(\mathcal {S},\textsc {GenAddr} (\mathbf {a} _\mathrm{OTS}, i))\) the same way as during key generation. The signature is computed as
where \(\mathbf {a} _{\mathcal {C} _i} = \textsc {GenAddr} (\mathbf {a} _\mathrm{OTS}, i)\) as above.
Verification Algorithm \((\mathsf {pk} '\longleftarrow \mathrm{WOTS} \text {.}\mathsf {vf} (M, \sigma , \mathbf {a} _\mathrm{OTS}, \textsc {Seed}))\) : On input of a \(\lambda \)-bit message M, a signature \(\sigma \), the address of the WOTS-T keypair within a tree \(\mathbf {a} _\mathrm{OTS} \), and public seed \(\textsc {Seed}\), the verification algorithm first computes the \(b_i\), \(1 \le i \le \ell \) as described above. Then it returns:
A formally correct verification algorithm would compare \(\mathsf {pk} '\) to a given public key and output \(\mathsf {true}\) on equality and \(\mathsf {false}\) otherwise. In XMSS-T this comparison is delegated to the overall verification algorithm.
Binary Hash Trees. The central elements of a Merkle tree signature scheme are full binary hash trees. We use a new construction that allows multi-target-attack resilience. In XMSS-T, a binary hash tree of height h always has \(2^h\) leaves which are n bit strings \(L_i\), \(i \in [2^h-1]\). Each node \(N_{i,j}\), for \(0 < j \le h\), \(0\le i < 2^{h-j}\), of the tree stores an n-bit string. For the leaf nodes define \(N_{i,0}=L_i\). The values of the internal nodes \(N_{i,j}\) are computed as
where key \(k_{i,j} = \mathcal {F} _n(\textsc {Seed}, \textsc {GenAddr} (\mathbf {a} _\textsc {Tree}, 4\cdot (j+i)))\) and bitmask \(r_{i,j} = (\mathcal {F} _n(\textsc {Seed}, \textsc {GenAddr} (\mathbf {a} _\mathcal {C}, 4\cdot (j+i)+1)) \Vert \mathcal {F} _n(\textsc {Seed}, \textsc {GenAddr} (\mathbf {a} _\mathcal {C}, 4\cdot (j+i)+2)))\). We also denote the root as \(\textsc {Root} =N_{0,h}\).
An important notion is the authentication path \(\mathsf {Auth} _i = (\mathsf {A} _0, \ldots ,\mathsf {A} _{h-1})\) of a leaf \(L_{i}\) shown in Fig. 3. \(\mathsf {Auth} _i\) consists of all the sibling nodes of the nodes contained in the path from \(L_i\) to the root. For a discussion on how to compute authentication paths, see Sect. 6. Given a leaf \(L_{i}\) together with its authentication path \(\mathsf {Auth} _i\), the root of the tree can be computed using Algorithm 1.

L-Tree. In addition to the full binary trees above, we also use unbalanced binary trees called L-Trees as in [15]. These are exclusively used to hash WOTS-T public keys. The \(\ell _\lambda \) leaves of an L-Tree are the elements of a WOTS-T public key and the tree is constructed as described above but with one difference: A left node that has no right sibling is lifted to a higher level of the L-Tree until it becomes the right sibling of another node. Apart from this the computations work the same as for binary trees. The L-Trees have height \(\lceil \log \ell _\lambda \rceil \).
4.1 XMSS-T
Given all of the above we can finally describe the algorithms of the XMSS-T construction. An XMSS-T keypair completely defines a hyper-tree of height h that consists of d layers of trees of height h / d. Each of these trees looks as follows. The leaves of a tree are \(2^{h/d}\) L-Tree root nodes that each compress the public key of a WOTS-T key pair. Hence, a tree can be viewed as a key pair that can be used to sign \(2^{h/d}\) messages. The hyper-tree is structured into d layers. On layer \(d-1\) it has a single tree. On layer \(d-2\) it has \(2^{h/d}\) trees. The roots of these trees are signed using the WOTS-T key pairs of the tree on layer \(d-1\). In general, layer i consists of \(2^{(d-1-i)(h/d)}\) trees and the roots of these trees are signed using the WOTS-T key pairs of the trees on layer \(i+1\). Finally, on layer 0 the WOTS-T key pairs are used to sign the message digests.
To improve readability, we only give a functional description of the algorithms of XMSS-T. To obtain a practical scheme, this has to be combined with the distributed signature generation method from [22] which in turn makes use of the \(\textsc {BDS}\) algorithm [13] for efficient tree traversal.
Key Generation Algorithm \(((\mathsf {SK},\mathsf {PK})\longleftarrow \mathsf {kg} (1^n))\) : The key generation algorithm first samples two secret values \((\mathsf {SK} _1,\mathsf {SK} _2)\in \{0,1\}^n\times \{0,1\}^n\). The value \(\mathsf {SK} _1 = \mathcal {S} \) is the seed used for pseudorandom key generation in WOTS-T. The value \(\mathsf {SK} _2\) is used to generate pseudorandom values to randomize the message hash in \(\mathsf {sign}\). Also, the public seed \(\textsc {Seed} \mathop {\longleftarrow }\limits ^{\$}\{0,1\}^n\) is sampled as a uniform random value.
The remaining part of \(\mathsf {kg}\) consists of generating the root node of the tree on layer \(d-1\). Towards this end the WOTS-T key pairs for the single tree on layer \(d-1\) are generated using \(\mathsf {SK} _1\) as \(\mathcal {S} \). The ith leaf \(L_i\) of the tree is the root of an L-Tree that compresses \(\mathsf {pk} _i\). Finally, a binary hash tree is built using the constructed leaves and its root node becomes \(\mathsf {PK}_1\).
Besides the secret values and \(\textsc {Seed}\), the secret key also contains the index i of the next WOTS-T key pair to use for message signing. The index takes h bits and is initialized with the all 0 bit string. The XMSS-T secret key is \(\mathsf {SK} = (i=0^{h}, \mathsf {SK} _1,\mathsf {SK} _2,\textsc {Seed})\), the public key is \(\mathsf {PK}= (\mathsf {PK}_1,\textsc {Seed})\). \(\mathsf {kg}\) returns the key pair \(((\mathsf {SK} _1,\mathsf {SK} _2,\textsc {Seed}),(\mathsf {PK}_1,\textsc {Seed}))\).
Signature Algorithm \(((\varSigma , \mathsf {SK}) \longleftarrow \mathsf {sign} (M, \mathsf {SK}))\) : On input of a message \(M \in \{0,1\}^*\) and secret key \(\mathsf {SK} = (i, \mathsf {SK} _1,\mathsf {SK} _2,\textsc {Seed})\), \(\mathsf {sign}\) computes a randomized message digest \(D \in \{0,1\}^m\): First, a pseudorandom \(R\in \{0,1\}^m\) is computed as \(R\longleftarrow \mathcal {F} _m(\mathsf {SK} _2, M)\). Then, \(D \longleftarrow \mathcal {H} (R,M)\) is computed as the randomized hash of M using R as randomness. Note that signing is deterministic, i.e., we need no real randomness as all required ‘randomness’ is pseudorandomly generated using PRF \(\mathcal {F} _m\).
Given index i, the ith WOTS-T key pair on layer \(d=0\) is used to sign D. More specifically, this is the \(i_0\)th WOTS-T keypair in the \(i_0'\)th tree on layer 0, where \(i_0\) is given by the last h / d bits of i and \(i_0'\) by the remaining \((d-1)h/d\) bits of i. Next, the authentication path \(\mathsf {Auth} _{i_0}\) for the \(i_0\)th leaf of the \(i_0'\)th tree is computed as well as the root of that tree. Now, for every layer \(1 \le \delta \le d-1\) the same procedure is repeated with the difference that \(i = i_{\delta -1}'\) and the root computed on layer \(\delta -1\) is signed. So, to sign the root from layer \(\delta -1\), the \(i_\delta \)th WOTS-T keypair in the \(i_\delta '\)th tree on layer \(\delta \) is used, where \(i_\delta \) is given by the last h / d bits of \(i_{\delta -1}'\) and \(i_\delta '\) by the remaining \((d-1)h/d\) bits of \(i_{\delta -1}'\). Then the authentication path \(\mathsf {Auth} _{i_\delta }\) for the \(i_\delta \)th leaf of the \(i_\delta '\)th tree is computed as well as the root of that tree. The XMSS-T signature \(\varSigma =(i,R,\sigma _{\text {W},0},\mathsf {Auth} _{i_0}, \ldots , \sigma _{\text {W},d-1},\mathsf {Auth} _{i_{d-1}})\) contains the used index i, randomness R and one WOTS-T signature – authentication path pair \(\sigma _{\text {W},j},\mathsf {Auth} _{i_j}\), \(j\in [d-1]\) per layer.
Finally, \(\mathsf {sign}\) updates the secret key \(\mathsf {SK}\) setting \(i = i+1\) and outputs the pair\((\varSigma , \mathsf {SK})\).
Verification Algorithm \((b\longleftarrow \mathsf {vf} (M, \varSigma , \mathsf {PK}))\) : On input of a message \(M \in \{0,1\}^*\), a signature \(\varSigma \), and a public key \(\mathsf {PK}\), the algorithm computes the message digest \(D \longleftarrow \mathcal {H} (R,M)\) using the randomness R contained in the signature. Using i, the indices \(i_\delta , i_\delta '\) are computed for \(0 \le \delta \le d-1\). The message digest D and the \(\textsc {Seed}\) from \(\mathsf {PK}\) are used to compute the first WOTS-T public key \(\mathsf {pk} _{\text {W},0} \longleftarrow \mathrm{WOTS} \text {.}\mathsf {vf} (D, \sigma _{\text {W},0},\mathbf {a} _{\mathrm{OTS} _0}, \textsc {Seed})\), where \(\mathbf {a} _{\mathrm{OTS} _0}\) is the address of the \(i_0\)th WOTS-T keypair in the \(i_0'\)th tree on layer 0. An L-Tree is used to compute \(L_{i_0}\), the leaf corresponding to \(\mathsf {pk} _{\text {W},0} \). Then, the root \(\textsc {Root} _0\) of the respective tree is computed using Algorithm 1 with index \(i_0\), leaf \(L_{i_0}\) and authentication path \(\mathsf {Auth} _{i_0}\).
Then, this procedure gets repeated for layers 1 to \(d-1\) with the following two differences. First, on layer \(1\le \delta \le d-1\) the root of the previously processed tree \(\textsc {Root} _{\delta -1}\) is used to compute the WOTS-T public key \(\mathsf {pk} _{\text {W},\delta } \). Second, the leaf computed from \(\mathsf {pk} _{\text {W},\delta } \) using an L-Tree is \(L_{i_\delta }\). The result of the final repetition on layer \(d-1\) is a value \(\textsc {Root} _{d-1}\) for the root node of the single tree on the top layer. This value is compared to the first element of the public key, i.e., \(\mathsf {PK}_1 \mathop {=}\limits ^{?} \textsc {Root} _{d-1}\). If the comparison holds, \(\mathsf {vf}\) returns \(\mathsf {true}\), otherwise \(\mathsf {false}\).
5 Security
In the following we give a security reduction for XMSS-T. First, we review the required security definitions. Afterwards we give a security reduction for XMSS-T.
Existential Unforgeability Under Adaptive Chosen Message Attacks. The standard security notion for digital signature schemes is existential unforgeability under adaptive chosen message attacks (EU-CMA) [17] which is defined using the following experiment. By \({\textsc {Dss}}(1^n)\) we denote a signature scheme with security parameter n.

For the success probability of an adversary \(\mathcal {A} \) in the above experiment we write
A signature scheme is called \({\textsc {{EU-CMA}}}\)-secure if any PPT adversary has only negligible success probability:
Definition 2
( eu-cma ). Let \(n \in \mathbb {N}\), \({\textsc {Dss}}\) a digital signature scheme as defined above. We call \({\textsc {Dss}}\) \({\textsc {{EU-CMA}}}\)-secure if for all \(q,t = \text {poly}\left( n\right) \) the maximum success probability \({\mathrm {InSec}}^{{{\textsc {{eu-cma}}}}}\left( {{\textsc {Dss}}(1^n)}; {t,q} \right) \) of all possibly probabilistic adversaries \(\mathcal {A} \) running in time \(\le t\), making at most q queries to \(\mathsf {Sign}\) in the above experiment, is negligible in n:
To be precise, XMSS-T is a so-called key-evolving signature scheme which automatically updates the secret key after each signature. We capture this, assuming that the oracle \(\mathsf {sign} (\mathsf {sk},\cdot )\) in the above experiment replaces the secret key \(\mathsf {sk} \) after each signature with the one returned by \(\text {XMSS-T}.\mathsf {sign} \) and that it returns the empty string when \(i \ge 2^h\), i.e. when the maximum number of signatures were done.
Pseudorandom Function Families. In the following we give the missing definition for the properties of (hash) function families that we use, namely pseudorandomness. In our definition we use the definition of (hash) function families from Sect. 2. In the definition of the success probability of an adversary against pseudorandomness (\({\textsc {prf}}\)) the adversary gets black-box access to an oracle \(\mathsf {Box}\). \(\mathsf {Box}\) is either initialized with a function from \(\mathcal {H} _n\) or a function from the set \(\mathcal {G}(m,n)\) of all functions with domain \(\{0,1\}^m\) and range \(\{0,1\}^n\). The goal of the adversary is to distinguish both cases:
Using this success probability, we define a pseudorandom function family the following way.
Definition 3
( prf ). Let \(\mathcal {H} _n\) be defined as above. We call \(\mathcal {H} _n\) a pseudorandom function family, if it is efficient and for all \(t = \text {poly}\left( n\right) \) the maximum success probability \({\mathrm {InSec}}^{{{\textsc {prf}}}}\left( {\mathcal {H} _n}; {t} \right) \) of all possibly probabilistic adversaries \(\mathcal {A} \), running in time \(\le t\), is negligible in n:
5.1 Security Reduction
We now proof the security of XMSS-T. We will base the security of the core scheme on the multi-function multi-target second-preimage resistance of \(\textsc {F}, \textsc {H} \), the pseudorandomness of \(\mathcal {F} _n\), the multi-target extended target collision resistance of \(\mathcal {H} \) and a functional requirement on \(\textsc {F} \) defined below in the random oracle model. Please note that the random oracle model is only required to show that we can hand out the seed \(\textsc {Seed}\) used to generate the public function keys and bitmasks. Towards this end, we have to split the use of \(\mathcal {F} _n\) into two parts. Assume two functions \(\mathcal {F} _n^1\) and \(\mathcal {F} _n^2\). We assume \(\mathcal {F} _n^1\) is used in place of \(\mathcal {F} _n\) for pseudorandom (secret) key generation and generation of the message hash randomness. For \(\mathcal {F} _n^1\) we require standard model pseudorandomness. On the other hand, \(\mathcal {F} _n^2\) is used to replace \(\mathcal {F} _n\) when generating the hash keys \(k_{i,j}\) and bitmasks \(r_{i,j}\). In the proof, only \(\mathcal {F} _n^2\) is modeled as random oracle (using the concatenation of key and input as input to the RO).
As mentioned above we need an additional requirement on \(\textsc {F} \). Informally we require that every element in the image of \(\textsc {F} \) has at least two preimages, i.e.,
Please note that this requirement meets the expectation for a random function. This additional requirement is needed to not having to use the one-wayness of \(\textsc {F} \). If we had to use the one-wayness of \(\textsc {F} \), we still would have to guess the messages an adversary sends to the oracle. The reason is that plugging a challenge image into a chain means not knowing any previous value of the chain. Hence, we could not answer a query where the signature contains such a previous value of a chain. This would imply a security loss of roughly h bits. Given the above property we can instead extract a second preimage if \(\mathcal {A}\) inverts \(\textsc {F} \) with probability 1/2, loosing only 1 bit in the security level.
Now we got everything needed for the security reduction. We proof the following theorem:
Theorem 2
XMSS-T is existentially unforgeable under adaptive chosen message attacks with respect to the random oracle model if
-
\(\textsc {F}\) and \(\textsc {H}\) are multi-function multi-target second-preimage resistant function families,
-
\(\textsc {F}\) fulfills the requirement of Eq. 10,
-
\(\mathcal {F} _n^1, \mathcal {F} _m\) are pseudorandom function families,
-
\(\mathcal {F} _n^2\) is modeled as a random oracle, and
-
\(\mathcal {H} \) is an multi -target extend target collision resistant hash function family.
More specifically, the insecurity function \({\mathrm {InSec}}^{{{\textsc {{EU-CMA}}}}}\left( {\text {XMSS-T}}; {\xi ,2^h} \right) \) describing the maximum success probability over all adversaries running in time \(\le \xi \) against the \({\textsc {{EU-CMA}}}\) security of XMSS-T is bounded by
The general idea of the proof follows that of previous hash-based schemes. There are a few mutually exclusive cases what could have happened if an adversary succeeded. First, the attacker could have broken the m-eTCR property of \(\mathcal {H} \). This case is easily detected and can be handled in a straight-forward manner. Otherwise, the message digests have to differ. In this case the adversary has found a second preimage or a preimage for \(\textsc {F}\) or \(\textsc {H}\) with high probability. To extract a second preimage in this case, the reduction takes one \({\textsc {mm-spr}}\) challenge (M, K) per hash function call (\(\textsc {H}\) and \(\textsc {F}\)). Then, for this call the function is keyed with K and the bitmask is selected such that the input to the hash function is M. This means, if the input before the XOR with the bitmask is X, we use \(X \oplus M\) as bitmask. Then the RO is programmed such that it generates this bitmask and key for this hash function call. This programming is done adaptively, only when the adversary queries the RO for a value. Now, any second preimage in the scheme will be a valid solution for \({\textsc {mm-spr}}\) of either \(\textsc {H}\) or \(\textsc {F}\). The full proof can be found in Appendix B.
6 Implementation
In Sect. 4, we described XMSS-T, which builds on \(\text {XMSS}^{MT}\), altering the functions that are used to construct WOTS chains and hash trees. We now examine the cost of this change in terms of computation time. In order to measure the cost of the additional bitmasks and keys that are required for each application of the functions \(\textsc {F} \) and \(\textsc {H} \), we have implemented and benchmarked XMSS-T and \(\text {XMSS}^{MT}\). We use the \(\textsc {BDS}\) tree traversal algorithm [13] to speed up the authentication path computation, making the scheme practical.
We examine the scheme for two parameter configurations from the current Internet Draft for \(\text {XMSS}^{MT}\) [21], obtaining measurements for both a single-tree and a multi-tree set-up. For both settings, we use \(w = 16\) and \(m=n= 256\). For the first benchmark, we set \(h = 20, d = 1\). We use the same subtree height for the second configuration, setting \(h = 60, d = 3\) to construct three layers of subtrees with a height of twenty nodes each. We set \(k = 2\) as the BDS parameter for both parameter sets, we rely on the SHA 256 function to construct \(\textsc {F} \) and \(\textsc {H} \), and use ChaCha20 as the pseudorandom generator. These choices are also in accordance with [21]. For more parameter sets see [21].
For XMSS these parameters lead to a security level of 190 bits classical and 95 bits quantum for \(h=60\) (230 and 115 for \(h=20\)). Following the security analysis in the last section and the lower bounds in Sect. 2, these parameters have a security level of more than 256 bits classical, and 128 bits quantum (assuming that each hash query requires more than 4 bit operations) for XMSS-T (without the message digest). With the message digest we get approximately 190 bits classical and 95 bits quantum like for XMSS as \({\textsc {m-eTCR}}\) is still vulnerable to multi-target attacks. However, this can be fixed by increasing just the message digest size to \(m=276\) for \(h = 20\) and \(m=316\) for \(h=60\). With this change we get 256 bit classical and 128 bit quantum security. However, to get an insight into the effects of the changes made in XMSS-T, we decided to run the experiments for the exact same parameters (\(m= 256\)). For more benchmarks with different parameters see the full version.
To carry out these benchmarks, we have used a single core of an Intel Core i7-4770K CPU, running at 3.5 GHz, although the implementation was not optimized specifically for this platform.In the first setting, with \(h = 20\), we measure an average signing time of 12 488 458 clock cycles per signature for XMSS, and 34 862 033 clock cycles for XMSS-T. For the multi-tree version (\(h = 60\)), the scheme takes 13 014 401 clock cycles per signature for XMSS, and 37 025 552 cycles for XMSS-T.
This difference is quite significant. However, this was to be expected as the running time of the scheme is largely dominated by applications of \(\textsc {F} \) and \(\textsc {H} \) – precisely the functions that are changed for XMSS-T. For plain XMSS with the aforementioned parameters, these functions merely consist of calls to SHA-256 with inputs of 256 and 512 bits, respectively. Each of these inputs fits within the internal block size of SHA-256 (512 bits). When considering the Merkle-Damgård construction [25] that defines the structure of SHA-256, this implies a single application of the internal compression function. When transforming \(\textsc {F} \) and \(\textsc {H} \) into keyed hash functions, the input length increases. To ensure that the key and the input are in separate blocks, the key is prefixed with 256 zero-bits. This results in inputs of 768 and 1024 bits, respectively, implying the need for two blocks, as well as two applications of the compression function. The straight-forward calls to SHA-256 for \(\textsc {F} \) and \(\textsc {H} \) run in 1 072 and 1 924 cycles, while the keyed variants take 1 932 and 2 812 cycles, respectively.
A bigger factor weighing down \(\textsc {F} \) and \(\textsc {H} \) is the time needed to generate the keys and bitmasks pseudorandomly. Both these values require calls to the pseudorandom generator. For \(\textsc {F} \), we require two output blocks of 256 bits each; \(\textsc {H} \) requires three. At an expense of 560 cycles per output block, generating randomness for the masks and keys carries a significant cost.
Altogether, the experiments show that the tightened security comes at the cost of a factor less than 3 increase in the runtime.
Notes
- 1.
Alternatively, one can think of it as a global random function \((K,M)\mapsto O(K,M)\).
References
Aaronson, S., Shi, Y.: Quantum lower bounds for the collision and the element distinctness problems. J. ACM 51(4), 595–605 (2004)
Ambainis, A.: Quantum lower bounds by quantum arguments. J. Comput. Syst. Sci. 64(4), 750–767 (2002)
Beals, R., Buhrman, H., Cleve, R., Mosca, M., De Wolf, R.: Quantum lower bounds by polynomials. J. ACM 48(4), 778–797 (2001)
Bennett, C.H., Bernstein, E., Brassard, G., Vazirani, U.: Strengths and weaknesses of quantum computing. SIAM J. Comput. 26(5), 1510–1523 (1997)
Bernstein, D.J., Hopwood, D., Hülsing, A., Lange, T., Niederhagen, R., Papachristodoulou, L., Schneider, M., Schwabe, P., Wilcox-O’Hearn, Z.: SPHINCS: practical stateless hash-based signatures. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. LNCS, vol. 9056, pp. 368–397. Springer, Heidelberg (2015)
Boneh, D., Dagdelen, Ö., Fischlin, M., Lehmann, A., Schaffner, C., Zhandry, M.: Random oracles in a quantum world. In: Lee, D.H., Wang, X. (eds.) ASIACRYPT 2011. LNCS, vol. 7073, pp. 41–69. Springer, Heidelberg (2011)
Boyer, M., Brassard, G., Høyer, P., Tapp, A.: Tight bounds on quantum searching. arXiv preprint quant-ph/9605034 (1996)
Brassard, G., Hoyer, P., Mosca, M., Tapp, A.: Quantum amplitude amplification and estimation. Contemp. Math. 305, 53–74 (2002)
Brassard, G., Hoyer, P., Tapp, A.: Quantum algorithm for the collision problem. arXiv preprint quant-ph/9705002 (1997)
Brassard, G., Høyer, P., Tapp, A.: Quantum counting. In: Larsen, K.G., Skyum, S., Winskel, G. (eds.) ICALP 1998. LNCS, vol. 1443, pp. 820–831. Springer, Heidelberg (1998)
Buchmann, J., Dahmen, E., Ereth, S., Hülsing, A., Rückert, M.: On the security of the Winternitz one-time signature scheme. In: Nitaj, A., Pointcheval, D. (eds.) AFRICACRYPT 2011. LNCS, vol. 6737, pp. 363–378. Springer, Heidelberg (2011)
Buchmann, J., Dahmen, E., Hülsing, A.: XMSS - a practical forward secure signature scheme based on minimal security assumptions. In: Yang, B.-Y. (ed.) PQCrypto 2011. LNCS, vol. 7071, pp. 117–129. Springer, Heidelberg (2011)
Buchmann, J., Dahmen, E., Schneider, M.: Merkle tree traversal revisited. In: Buchmann, J., Ding, J. (eds.) PQCrypto 2008. LNCS, vol. 5299, pp. 63–78. Springer, Heidelberg (2008)
Carter, J.L., Wegman, M.N.: Universal classes of hash functions. In: Proceedings of the Ninth Annual ACM Symposium on Theory of Computing, pp. 106–112. ACM (1977)
Dahmen, E., Okeya, K., Takagi, T., Vuillaume, C.: Digital signatures out of second-preimage resistant hash functions. In: Buchmann, J., Ding, J. (eds.) PQCrypto 2008. LNCS, vol. 5299, pp. 109–123. Springer, Heidelberg (2008)
Eaton, E., Song, F.: Making existential-unforgeable signatures strongly unforgeable in the quantum random-oracle model. In: 10th Conference on the Theory of Quantum Computation, Communication and Cryptography, TQC 20–22 May 2015, Brussels, Belgium, pp. 147–162 (2015)
Goldwasser, S., Micali, S., Rivest, R.L.: A digital signature scheme secure against adaptive chosen-message attacks. SIAM J. Comput. 17(2), 281–308 (1988)
Grover, L.K.: A fast quantum mechanical algorithm for database search. In: Proceedings of the Twenty-Eighth Annual ACM Symposium on Theory of Computing, pp. 212–219. ACM (1996)
Halevi, S., Krawczyk, H.: Strengthening digital signatures via randomized hashing. In: Dwork, C. (ed.) CRYPTO 2006. LNCS, vol. 4117, pp. 41–59. Springer, Heidelberg (2006)
Hülsing, A.: W-OTS+ – shorter signatures for hash-based signature schemes. In: Youssef, A., Nitaj, A., Hassanien, A.E. (eds.) AFRICACRYPT 2013. LNCS, vol. 7918, pp. 173–188. Springer, Heidelberg (2013)
Hülsing, A., Butin, D., Gazdag, S., Mohaisen, A.: Xmss: extended hash-based signatures draft-irtf-cfrg-xmss-hash-based-signatures-01. Crypto Forum Research Group Internet-Draft (2015). https://tools.ietf.org/html/draft-irtf-cfrg-xmss-hash-based-signatures-01
Hülsing, A., Rausch, L., Buchmann, J.: Optimal parameters for XMSS\(^{\mathit{MT}}\). In: Cuzzocrea, A., Kittl, C., Simos, D.E., Weippl, E., Xu, L. (eds.) CD-ARES Workshops 2013. LNCS, vol. 8128, pp. 194–208. Springer, Heidelberg (2013)
Joffe, A., et al.: On a set of almost deterministic \( k \)-independent random variables. Ann. Probab. 2(1), 161–162 (1974)
Karloff, H., Mansour, Y.: On construction of k-wise independent random variables. In: Proceedings of the Twenty-Sixth Annual ACM Symposium on Theory of Computing, pp. 564–573. ACM (1994)
Merkle, R.C.: Secrecy, authentication, and public key systems. Ph.D thesis, Stanford University (1979)
Mironov, I.: Collision-resistant no more: hash-and-sign paradigm revisited. In: Yung, M., Dodis, Y., Kiayias, A., Malkin, T. (eds.) PKC 2006. LNCS, vol. 3958, pp. 140–156. Springer, Heidelberg (2006)
Unruh, D.: Quantum position verification in the random oracle model. In: Garay, J.A., Gennaro, R. (eds.) CRYPTO 2014, Part II. LNCS, vol. 8617, pp. 1–18. Springer, Heidelberg (2014)
Zhandry, M.: Secure identity-based encryption in the quantum random oracle model. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 758–775. Springer, Heidelberg (2012)
Zhandry, M.: A note on the quantum collision and set equality problems. Quantum Inf. Comput. 15(78), 557–567 (2015)
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Appendices
A Classical Generic Security
Preimage Resistance. For preimage resistance, analysis shows that the success probability of any classical \(\mathcal {A}\) that makes q queries to its oracle is
where the probability is taken over the internal coins of the oracle and the random choices of K and M. An attacker that makes no query but simply outputs a random domain element has success probability \(2^{-n}\) of hitting the target Y. An attacker that makes one query can verify the first guess. If that one did not hit Y he can make another guess which he now can not verify anymore. Together this gives a success probability of \(2/2^n\). Iterating this gives the above bound. Consequently, an attacker needs \(\mathcal {O}(2^n)\) queries to reach a success probability of at least 0.5.
Single-Function Multi-target Preimage Resistance. For \({\textsc {sm-ow}}\) a similar analysis shows a bound of
The reason is that the success probability of a single guess is now \(p/2^n\). Otherwise, the argument follows along the lines of the above argument. Consequently, the query complexity of a successful attack is \(\mathcal {O}(2^n/p)\). Please note, we also can get this result using a reduction from \({\textsc {ow}}\). In this case, we replace a random \(Y_i\) by the given Y from the \({\textsc {ow}}\) game. The reduction looses a factor 1/p.
Multi-function Multi-target Preimage Resistance. While the previous cases are more or less known results, for \({\textsc {mm-ow}}\) we are not aware of any such results. The difference to \({\textsc {sm-ow}}\) is that the adversary now basically plays p independent \({\textsc {ow}}\) games at once. In contrast to the \({\textsc {ow}}\) game \(\mathcal {A}\) can not use a query he made to attack \(Y_i\) for any other \(Y_j\) for \(j \ne i\). The reason is that different functions are associated to the different \(Y_i\). So, in the classical case we get a query bound of
The reason is that a guess has success probability \(1/2^n\). As one also has to guess \((K_i,Y_i)\), every verification query can only check if a given M fulfills \(Y_i = \textsc {H} _{K_i}(M)\) for a single i. Viewed differently, each query has to fix \(K_i\) in advance and outputs the associated \(Y_i\) only with probability \(2^{-n}\). Consequently, we get the same query bound \(\mathcal {O}(2^n)\) as for \({\textsc {ow}}\).
Second-Preimage Resistance. In the case of second-preimage resistance, the success probability of any \(\mathcal {A}\) that makes q queries to its oracle is
where the probability is taken over the internal coins of the oracle and the random choices of K and M. The bound can easily be derived following the analysis for one-wayness. Consequently, an attacker needs \(\mathcal {O}(2^n)\) queries to reach a success probability of at least 0.5.
Single-Function Multi-target Second-Preimage resistance. For \({\textsc {sm-spr}}\) a similar analysis shows a bound of
Again, the analysis follows along the lines of the respective analysis for \({\textsc {sm-ow}}\). Consequently, the query complexity of a successful attack is \(\mathcal {O}(2^n/p)\).
Multi-function Multi-target Preimage Resistance. While the previous cases are more or less known results, for \({\textsc {mm-spr}}\) we are not aware of any such results. The difference to \({\textsc {sm-spr}}\) is that the adversary now basically plays p independent \({\textsc {spr}}\) games at once. As for \({\textsc {mm-ow}}\), in the classical case, we get a query bound of
Again, the analysis follows along the lines of the respective analysis for \({\textsc {mm-ow}}\). Consequently, the query complexity of a successful attack is \(\mathcal {O}(2^n)\).
Extended Target Collision Resistance. For eTCR, analysis shows that the success probability of any adversary \(\mathcal {A}\) that makes no more than q queries to its oracle is
where the probability is taken over the internal coins of the oracle and the random choice of K.
Consider an arbitrary adversary \(\mathcal {A} =(\mathcal {A} _1,\mathcal {A} _2)\) attacking eTCR. \(A_1\) makes \(q_1\) queries and outputs a message M. Afterwards \(\mathcal {A} _2\) obtains K and makes \(q_2\) queries, with \(q_1+q_2 = q\). Without loss of generality, we assume that \(\mathcal {A} _1\) stores all his query results in the shared memory. When \(\mathcal {A} _2\) receives K, we can distinguish two mutually exclusive cases:
-
Case 1: \(\mathcal {A} _1\) already queried the oracle for \(\textsc {H} _K(M)\). To simplify analysis, we consider this a success for \(\mathcal {A}\). As K is a random key and \(\mathcal {A} _1\) made queries for no more than \(q_1\) different keys, this case occurs with probability
$$\begin{aligned} \epsilon _1 \le \frac{q_1}{2^k}. \end{aligned}$$ -
Case 2: \(\mathcal {A} _1\) did not query \(\textsc {H} _K(M)\) before. In this case, every query made by \(\mathcal {A} _1\) and every query made by \(\mathcal {A} _2\) has probability \(2^{-n}\) to hit \(\textsc {H} _K(M)\) and hence to be a solution. If \(\mathcal {A} _2\) does not find a solution using all query results, he can make another guess that has the same success probability as the queries before. Hence, the success probability in this case is exactly
$$\begin{aligned} \epsilon _2 = \frac{q_1+q_2}{2^n}. \end{aligned}$$
The sum of the two bounds \(\epsilon _1 + \epsilon _2\) takes its maximum for \(q_1 = q\). This gives the claimed bound. Note that the analysis for case 1 above is very rough and could be tightened (This is only a success if \(\mathcal {A} _1\) already found a pseudo-collision for (K, M)). However, in all relevant cases we know \(k \gtrsim n\) and hence tightening is of little use.
Multi-target- E TCR. Now, switching to \({\textsc {m-eTCR}}\) the complexities for the two cases change as follows: In both cases a factor of q is lost. In Case 1 this is caused by the fact that there are now q keys returned (over the game) that might hit a previously queried one. In Case 2 this is caused by the fact that each query works for all q targets (as in the case of \({\textsc {mm-spr}}\)). This leads to the bound
B Proof of Theorem 2
In the following we omit indices for the \({\textsc {mm-spr}}\) challenge pairs to preserve readability. Assume that there exists an adversary \(\mathcal {A}\) running in time \(\xi \) that breaks the \({\textsc {{EU-CMA}}}\) security of XMSS with probability \(\epsilon _\mathcal {A} \). In the following we will prove that \(\epsilon _\mathcal {A} \le {\mathrm {InSec}}^{{{\textsc {{EU-CMA}}}}}\left( {\text {XMSS-T}}; {\xi ,2^h} \right) \). First, consider the following two games:
-
Game 1. This is the original game.
-
Game 2. This is the same as Game 1 but instead of using random elements from \(\mathcal {F} _n^1\) and \(\mathcal {F} _m\) (by sampling \(\mathcal {S} \) and \(\mathsf {SK} _2\) from the key space), two truly random functions \(\textsc {G} _n:\{0,1\}^n\times \{0,1\}^{*}\rightarrow \{0,1\}^n\) and \(\textsc {G} _m:\{0,1\}^n\times \{0,1\}^{*}\rightarrow \{0,1\}^m\) are used.
The difference in the success probability of \(\mathcal {A}\) playing one of these games must be bound by \({\mathrm {InSec}}^{{{\textsc {prf}}}}\left( {\mathcal {F} _n^1}; {\xi } \right) +{\mathrm {InSec}}^{{{\textsc {prf}}}}\left( {\mathcal {F} _m}; {\xi } \right) \), otherwise we could use \(\mathcal {A}\) to distinguish \(\mathcal {F} _n^1\) or \(\mathcal {F} _m\) from a truly random function, breaking the pseudorandomness which would contradict the assumption. Hence, it suffices to analyze the success probability of \(\mathcal {A}\) in Game 2. Towards this end, we construct an oracle machine \(\mathcal {M} ^\mathcal {A} \) that breaks either the multi-function multi-target second-preimage resistance of \(\textsc {F}\) or of \(\textsc {H}\), or the extended target collision resistance of \(\mathcal {H} \). \(\mathcal {M} ^\mathcal {A} \) takes \(q_1\) challenge pairs \(\left\{ (K_i,M_i)\right\} _{1}^{{q_1}}\) for \(\textsc {F}\) and \(q_2\) challenge pairs \(\left\{ (K_i',M_i')\right\} _{1}^{{q_2}}\) for \(\textsc {H}\) where \(q_1\) (\(q_2\)) is the number of calls to \(\textsc {F}\) (\(\textsc {H}\)) for the XMSS-T key pair. Each of these challenge pairs gets associated with one specific call to \(\textsc {F}\) or \(\textsc {H}\) within the XMSS-T key pair.
\(\mathcal {M} ^\mathcal {A} \) first samples a random seed \(\textsc {Seed} \mathop {\longleftarrow }\limits ^{\$}\{0,1\}^n\). The XMSS-T public key \(\mathsf {PK}\)becomes \((\mathsf {PK}_1=\textsc {H} _{K_j'}(M_j'),\textsc {Seed})\) for \((K_j',M_j')\) – the pair associated with the call to \(\textsc {H}\) that computes the root. Now \(\mathcal {A}\) is run on this \(\mathsf {PK}\). When \(\mathcal {A}\) makes his ith query using some message \(\mathrm {Msg}_i\), \(\mathcal {M} ^\mathcal {A} \) first sends \(\mathrm {Msg}_i\) to the \({\textsc {m-eTCR}} \) challenger, receiving back a function key \(R_i\). Then it computes the message digest as \(D_i = \mathcal {H} (R_i,\mathrm {Msg}_i)\) and sets the signature index to i. The next steps are the same for each tree involved in the signature. First, \(\mathcal {M} ^\mathcal {A} \) computes the chain indices b. The \({\mathrm{WOTS}^+}\) signature is collected by selecting the challenge (K, M) for the \(b_j\)th call to \(\textsc {F} \) in the jth chain and computing the jth signature element as \(\textsc {F} _K(M)\). Similarly, the authentication path for the \({\mathrm{WOTS}^+}\) key pair is generated by figuring out the nodes that are required. Then, these nodes are calculated as \(\textsc {H} _K(M)\) where (K, M) is the challenge pair associated with the call to \(\textsc {H}\) that computes this authentication path node. The same is done for the root node. Afterwards, the whole procedure is repeated for the parent tree, until the top tree is done. Then the XMSS-T signature \(\varSigma _i\) is sent back to \(\mathcal {A}\).
If \(\mathcal {A}\) queries the RO, the RO is adaptively programmed such that it outputs the right bitmasks and keys. W.l.o.g., we assume that \(\mathcal {A}\) makes each query only once and stores the result. For any query \((X_1||X_2) \in \{0,1\}^n \times \{0,1\}^*\) where \(X_1 \ne \textsc {Seed} \) or \(X_2\) is no valid address of a bitmask or a key for a hash function call, the RO simply outputs a random value. Otherwise, assume for simplicity (again w.l.o.g.) that the adversary always queries the RO for the bitmask(s) and the key of a hash function call at once. Then the RO is programmed as follows: Assume (K, M) is the challenge pair for the associated hash call. If the address refers to the first hash call in a \({\mathrm{WOTS}^+}\) function chain, the start value of that chain is generated as \(X = \textsc {G} (\mathsf {SK} _1, \mathbf {a})\) where \(\mathbf {a} \) is the address of that function chain. Next, the RO is programmed to return bitmask \(r = X \oplus M\) and key K. If the address refers to a hash call in a \({\mathrm{WOTS}^+}\) function chain that is not the first in that chain, let \((K',M')\) be the challenge template associated with the previous hash call in that chain. Then the RO is programmed to return bitmask \(r = \textsc {F} _{K'}(M') \oplus M\) and key K. Finally, if the address refers to a hash call to \(\textsc {H}\), let \((K_1,M_1)\), \((K_2, M_2)\) be the challenge templates associated with the hash calls computing its two child nodes. Then the RO is programmed to return bitmask \(r = (\textsc {H} _{K_1}(M_1) \Vert \textsc {H} _{K_2}(M_2)) \oplus M\) and key K (Note that the challenge templates might be associated with calls to \(\textsc {F}\) if the address is associate with the computation of a node on level 1 in an L-tree. In this case \(\textsc {H}\) is replaced by \(\textsc {F}\) in the computation of r).
When \(\mathcal {A}\) outputs a forgery \((\mathrm {Msg}, \varSigma )\) with \(\varSigma = (i, R,\sigma _{\text {W},0},\mathsf {Auth} _{i_0}, \ldots , \sigma _{\text {W},d-1},\) \(\mathsf {Auth} _{i_{d-1}})\), \(\mathcal {M} ^\mathcal {A} \) runs the verification algorithm on \((\mathrm {Msg},\varSigma )\) and \((\varSigma _i, \mathrm {Msg}_i)\). If the forgery is invalid, \(\mathcal {M} ^\mathcal {A} \) returns \(\bot \). Otherwise, three mutually exclusive cases can occur. \(\mathcal {M} ^\mathcal {A} \) compares the values computed during the two verification runs in order of computation.
-
Case 1: If \(D = \mathcal {H} (R,\mathrm {Msg}) = \mathcal {H} (R_i,\mathrm {Msg}_i) = D_i\), i.e., if the digests of the ith query is the same as that of the forgery, \(\mathcal {M} ^\mathcal {A} \) broke m-eTCR and returns \((i,R,\mathrm {Msg})\). Hence, the probability that \(\mathcal {A}\) outputs a case 1 forgery must be upper bounded by \({\mathrm {InSec}}^{{{\textsc {m-eTCR}}}}\left( {\mathcal {H}}; {\xi } \right) \) per assumption.
If the digests are different, the corresponding \(b_i\) are also different and hence, parts of the data computed by the two verification runs must also differ. Now, \(\mathcal {M} ^\mathcal {A} \) only compares the computed \({\mathrm{WOTS}^+}\) public keys and the computed root values. By the pigeonhole principle, the signatures have to agree on one of these for the first time as they lead to the same root of the top tree.
-
Case 2: If the data generated verifying the two signatures first agrees on a \({\mathrm{WOTS}^+}\) public key, the message digests or the root nodes signed with this \({\mathrm{WOTS}^+}\) keypair where different. Hence, we got a \({\mathrm{WOTS}^+}\) forgery. In this case, by the construction of the checksum there must be one chain j in this \({\mathrm{WOTS}^+}\) keypair such that \(b_j < (b_j)_i\), i.e. the jth signature value of the forgery belongs to an earlier hash call than the one of the answer to the ith query. As both chains end in the same public key value, they most collide at the output of some call to \(\textsc {F}\). If this point is not the \((b_j)_i\)th call it has to be a later one. In this case, the input to the colliding call to \(\textsc {F}\) computed from the forgery is a second preimage for the challenge template associated with that call to \(\textsc {F}\) and \(\mathcal {M} ^\mathcal {A} \) outputs it, breaking \({\textsc {mm-spr}}\) of \(\textsc {F}\). Otherwise, the two chains collide on the output of the \((b_j)_i\)th call to \(\textsc {F}\), i.e., on \((\sigma _j)_i\), the jth value of the original signature. Let (K, M) be the challenge pair associated with the call to \(\textsc {F}\) that produced \((\sigma _j)_i\). According to Eq. 10, \((\sigma _j)_i\) has at least two preimages under \(\textsc {F} _k\). As \(\mathcal {A}\) has no information about the preimage, the value X that can be computed from the forgery and that leads \(f_K(X) = (\sigma _j)_i\) is unequal to M with at least probability 1/2. In that case, \(\mathcal {M} ^\mathcal {A} \) found a second preimage of M under \(\textsc {F} _K\) and outputs it. Otherwise it returns \(\bot \). Consequently, the probability that \(\mathcal {A}\) outputs a case 2 forgery must be upper bounded by \(2{\mathrm {InSec}}^{{{\textsc {mm-spr}}}}\left( {\textsc {F}}; {\xi } \right) \) per assumption.
-
Case 3: If the data generated verifying the two signatures first agrees on a root node, the \({\mathrm{WOTS}^+}\) public keys that are used to compute this root node have to differ. A third time by the pigeonhole principle, there must be one call to \(\textsc {H}\) between the \({\mathrm{WOTS}^+}\) public key and the root node where the output for the forgery and the correct signature agree for the first time. As the input data depends on previously computed outputs of \(\textsc {H}\) (or \(\textsc {F}\)), it must differ. Hence, for challenge pair (K, M), the input to this call to \(\textsc {H} _K\) is a second preimage for M, that \(\mathcal {M} ^\mathcal {A} \) returns breaking \({\textsc {mm-spr}}\) of \(\textsc {H}\). Hence, the probability that \(\mathcal {A}\) outputs a case 3 forgery must be upper bounded by \({\mathrm {InSec}}^{{{\textsc {mm-spr}}}}\left( {\textsc {H}}; {\xi } \right) \).
Combining the upper bounds from the three cases shows that the success probability \(\epsilon _\mathcal {A} \) of \(\mathcal {A}\) winning in Game 2 must be upper bounded by
Combining this with the result that the difference in \(\mathcal {A}\) ’s success probability between playing in Game 1 and playing in Game 2 must be upper bounded by \({\mathrm {InSec}}^{{{\textsc {prf}}}}\left( {\mathcal {F} _n^2}; {\xi } \right) \), we get the claimed bound on the success probability of any adversary \(\mathcal {A}\) running in time \(\xi \):
\(\square \)
Rights and permissions
Copyright information
© 2016 International Association for Cryptologic Research
About this paper
Cite this paper
Hülsing, A., Rijneveld, J., Song, F. (2016). Mitigating Multi-target Attacks in Hash-Based Signatures. In: Cheng, CM., Chung, KM., Persiano, G., Yang, BY. (eds) Public-Key Cryptography – PKC 2016. Lecture Notes in Computer Science(), vol 9614. Springer, Berlin, Heidelberg. https://doi.org/10.1007/978-3-662-49384-7_15
Download citation
DOI: https://doi.org/10.1007/978-3-662-49384-7_15
Published:
Publisher Name: Springer, Berlin, Heidelberg
Print ISBN: 978-3-662-49383-0
Online ISBN: 978-3-662-49384-7
eBook Packages: Computer ScienceComputer Science (R0)