Abstract
The previous contribution uses the k-means procedure to create clusters. It converts into a chain route when the threshold content goes beyond the energy of the devices in the system. The information transmitter fuel includes the power of the machine circuitry and the magnitude of facts communication and blowout. The vibrancy helps in communication circuitry. The knowledge packages ship to the destination. The architecture has two stages. The groups form during the clustering stage. The Optimal CBR method uses the k-means procedure to construct groups. It selects the cluster head based on the Euclidean length and device fuel. The verge posted by the group head to the individual set associates is the characteristic weight above which the machine transmits the data to the head. When two-thirds of the devices are lifeless, the instruments use the greedy procedure to construct a chain-like multiple-hop methodology to reach the base station. A beacon transmission is sent by the base station to the active devices in the chaining stage (when the energy of the nodes is lower). The base station creates the path using multiple-hop chain routing and the greedy technique. The devices send the notification to the base station using the chain track. The proposed work increases security by 9.67% when transmitting data and by 11.38% (device getting compromised).
You have full access to this open access chapter, Download chapter PDF
Similar content being viewed by others
Keywords
Introduction
Sensors (Ambika 2020, 2021) are tiny devices deployed to accumulate information from an object of interest. The number of sensor hubs in a detector organization is higher than the number of devices in an impromptu organization. Sensing element hubs are inclined to disappointment. The geography of a sensor network changes much of the time. Sensor hubs fundamentally utilize a transmission correspondence worldview, while most impromptu organizations depend on the money-to-point interchanges. Sensor hubs are restricted in power, computational limits, and memory. Detector hubs might not have worldwide recognizable proof (ID) given the measure of upward and countless tiny devices.
Smart sensors with actuators make Internet of Things (Ambika 2019; Dian et al. 2020). The idea of the Internet is to associate PC gadgets changing to a bunch of associates. It encompasses things of human residing space, like home apparatuses, machines, transportation, business capacity, products, etc. The quantity in the living space is more than the quantity of the total populace. Research continues to make these things speak with one another using the Internet. The correspondence among these things alludes to the Internet of Things.
The recommendation (Jothikumar et al. 2021) uses a k-means algorithm. It converts into a chain route when the threshold content goes beyond the energy of the devices in the system. The information transmitter fuel includes the power of the machine circuitry and the magnitude of facts communication and blowout. The vibrancy helps in communication circuitry. The knowledge packages ship to the destination. The architecture has two stages. The groups form during the clustering stage. The Optimal CBR method uses the k-means procedure to construct groups. It selects the cluster head based on the Euclidean length and device fuel. The verge posted by the group head to the individual set associates is the characteristic weight above which the machine transmits the data to the head. When two-thirds of the devices are lifeless, the instruments use the greedy procedure to construct a chain-like multiple-hop methodology to reach the base station. A beacon transmission is sent by the base station to the active devices in the chaining stage (when the energy of the nodes is lower). The base station creates the path using multiple-hop chain routing and the greedy technique. The devices (Nagaraj 2021) send the notification to the base station using the chain track.
The suggestion employs a hashing methodology. The base station broadcasts to the public for every session. The devices generate the hash codes for the sensed data and create the outcome using the public key. This methodology secures the devices and data during transmission.
The contribution of the work:
-
The devices send the notification to the base station using the chain track. The suggestion employs a hashing methodology.
-
The base station broadcasts to the public for every session.
-
The devices develop the hash codes for the sensed information and generate the outcome using the public key.
-
The proposed work increases security by 9.67% when transmitting data and 11.38% details when the device is compromised.
The work is divided into sections. Literature survey is summarized in segment 2. IoT-based wireless network is detailed in division 3. Different kinds of attacks in IoT are explained in section “Different Types of Attacks”. Importance of 5G is briefed in segment 5. Background is discussed in section “Background”. The proposed work is detailed in division 7. Analysis of work is detailed in section “Analysis of the proposal”. The work concludes in section “Conclusion”.
Literature Survey
The following sections briefs the contribution made by various authors. The recommendation (Jothikumar et al. 2021) uses a k-means algorithm. It converts into a chain route when the threshold content goes beyond the energy of the devices in the system. The information transmitter fuel includes the power of the machine circuitry and the magnitude of facts communication and blowout. The vibrancy helps in communication circuitry. The knowledge packages ship to the destination. The architecture has two stages. The groups form during the clustering stage. The Optimal CBR method uses the k-means procedure to construct groups. It selects the cluster head based on the Euclidean length and device fuel. The verge posted by the group head to the individual set associates is the characteristic weight above which the machine transmits the data to the head. The instruments use the greedy procedure to construct a chain-like multiple-hop methodology to reach the base station When two-thirds of the devices are lifeless. A beacon transmission is sent by the base station to the active devices in the chaining stage (when the energy of the nodes is lower). The base station creates the path using multiple-hop chain routing and the greedy technique. The devices send the notification to the base station using the chain track.
It is M2M traffic mode (Fu et al. 2018). It further develops traffic adjusting strategies. This model is reasonable in speaking to the current promising mass of gadgets. 3GPP has made a record 3GPP TR 37.868, which gives a way to deal with demonstrating M2M traffic in the LTE organization. The existing traffic models depict a fixed arbitrary process. It has a limited time stretch. M2M gadgets produce traffic. This approach offers two traffic models and double crosses intervals. The first model portrays the ordinary condition of the organization, where each M2M gadget for 60 s communicates one message. The subsequent model shows the condition of the expanded network load. This heap prompts the mass enactment of M2M gadgets.
WSN (Fu et al. 2018) can work at 900 MHz/2.4 GHz to help the 5 GHz, recurrence groups. The concentrator contains associate WSN pointing to the 5G versatile interchanges world. The methodology develops the framework execution. It uses the UAV as a transfer station. SINK UAV BS improves on the framework model. The concentrator communicates a sign to the BS with one UAV as the hand-off. This framework model can more readily uncover the connection between the place of the UAV-based hand-off and the framework energy consumption. The limited transmission distance between the Base station and the concentrator can limit the sending force of the concentrator. The ideal flight path is not set in stone by AI.
The organization (Lynggaard and Skouby 2015) contains an assortment of homes furnished with IoT. It deals with administration like lighting, warming, security, and theater setups for its users. These IoT gadgets interconnect with the home organization, which associates with the web cloud services. The network interconnects the brilliant homes and interfaces using cloud administrations that consume the enormous information produced by the home IoT. The IoT gadgets create a tremendous measure of data to be handled by the city CoT administrations. It contains an assortment of associated sensor hub bunches where each gathering ends in a sensor end gadget. These end gadgets speak with a switching hub which thus courses correspondence through the network.
The gridlock situation (Sachan et al. 2021) is an examination of two D2D correspondence modes. The work distinguishes the hubs with lesser responsibilities from the previous information saved in the control unit of the base station. The controlling unit has every one of the subtleties of commitment in a specific gadget. It very well may be distinguished what hubs are with a lesser burden. It infers that such notes are moving next to zero data. The hubs with low loads can be worked at lower communication power levels all at once and additionally works on the SINR because of diminished by and large impedance in the framework and further develops the battery duration of the portable hubs. The encompassing hubs have a lesser burden at a specific time. There will be proficient correspondence while decreasing the impedance.
The work (Sekaran et al. 2021) is an integrated spectrum selection and spectrum access using a greedy and AI-based framework to allow the forthcoming and subsequent demands on 5G and beyond to be presented. A fractional Knapsack Greedy-based strategy is introduced, and Lagrange Hyperplane-based approach is utilized to realize the AI-based strategies for spectrum selection and spectrum allocation for IoT-enabled sensor networks. This framework is called Fractional Knapsack and Lagrange Hyperplane Spectrum Access (FK-LHSA). The First Fractional Knapsack Multi-band spectrum selection (FKMSS) model is designed along with an energy consumption model to optimize channel or spectrum throughput. A Lagrange Hyperplane (LH) spectrum access model minimizes spectrum access delay and improves access accuracy. The simulation results show that the proposed FKM and LH model can effectively reduce the spectrum access delay (along with the improvement of throughput and spectrum access accuracy).
The proposal (Shin and Kwon 2020) cures security weaknesses in light of the framework engineering in WSNs for 5G-coordinated IoT. The proposed conspire parts into five stages. The framework arrangement stage incorporates the statement of the framework boundaries and entryway and sensor hub enrollment before sending. The client enrollment stage starts when a client sends a solicitation message for enlistment to the confirmation server over a secure channel. The user needs to get to the WSN responsible for the entryway the accompanying advances perform with the client, verification server, and passage over a public channel. With the assistance of the verification server, the client and passage commonly validate one another and lay out a typical meeting key for future correspondence. The client can acquire the tangible information progressively from the WSN that matches entrance honors. The key and biometric update stage permits a client to refresh the secret key and biometrics without connection with the validation server. The messages communicate over a channel in the entrance honor update stage.
It is an energy harvest Markovian battery model (Mahmoud et al. 2017) of 100 states, which addresses the fuel of the optional client, and infers the throughput while considering detecting a power error reap CRWSN. The energy reaps supplementary client can send bundles on the channel Whenever the pipeline is passive. The auxiliary client neglects to communicate information when the channel is inactive because erroneous detection prompts throughput corruption. The throughput improves the fruitful transmission boundaries. The conditions address a restricted battery limit. It is a non-complete M/M/1 model of the energy gather CR-WSN model because of the inconsistent worth of the primary state. The progress of the states relies upon the entrance likelihood. It views that there is general information at the optional client to send. The range states change in light of the traffic of the essential client. The range state stays unaltered by involving a client with probability or travels to sit with the likelihood in the past schedule opening.
IoT-Based Wireless Networks
The IoT is reconciliation and correspondence between clever devices. IoT's incomparability contributes to new advancements and applications. Such detectors and actuators collaborate with different handsets, microcontroller gadgets, and conventions for the correspondence of control and sensor information. Such constant modules communicate detected information to the unified storehouses. In contrast with traditional wired or remote systems administration frameworks, the highlights of IoT using remote advances are unique as the number of specialized gadgets is very high. Figure 10.2 is the representation of the same.
Different Types of Attacks
Taxonomy of threats in IoT (Krishna et al. 2021)
K-nearest Neighbor algorithm (Pacheco et al. 2021)
The following are the different security concerns:
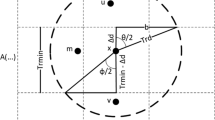
(Fig. 10.1).
Perception Layer
-
Eavesdropping (Khattak et al. 2019)—Assailants can sniff the traffic produced by IoT information stream to accumulate client's data by setting up comparable IoT gadgets.
-
Malicious Data Injection (Alromih et al. 2018)—Bogus sensor information infusion is a type of assault where the sensor information utilized in IoT applications is produced or altered for malevolent purposes.
-
Sybil Attack (Mishra et al. 2018)—The noxious hubs in this can have numerous personalities of a veritable hub by either imitating it or with a phony character through duplication.
-
Disclosure of Critical Information (Zhang Et Al. 2017)—Sensors utilized in IoT devices can reveal delicate data, for example, passwords, secret keys, charge card certifications, etc. These subtleties disregard client security or fabricate an information base for future assaults.
-
Side-Channel Attacks (Kumar et al. 2017)—The aggressor assembles data and plays out the figuring out cycle to gather the encryption accreditations of an IoT gadget while the encryption interaction is in progress. This data is not gathered from plaintext or ciphertext during the encryption cycle. Side-channel goes after the utilization of information to gain the key the gadget utilizes.
-
Malicious Data Injection (Alromih et al. 2018)—Assailants exploit defects in correspondence conventions to embed information into the organization. The gateway will mess with the data expected to control the gadget on the off chance. The infusion assault might bring about code execution or framework control from a remote place.
-
Node cloning (Khattak et al. 2019)—For unapproved purposes, the gadgets can be effectively fashioned and recreated. It is called the cloning of hubs.
-
Exhaustion attack (Aarika et al. 2020)—Depletion is a spot assault. It is associated with deactivation attacks. It decreases the size of the organization and eliminates hubs for all time from the organization.
Abstraction Layer
-
Illegal access (Alramadhan and Sha 2017)—The unlawful access and vindictive difference in information might emerge when handling delicate information.
-
Man-in-the-Middle—A framework (Navas et al. 2018) tunes in on rush hour gridlock between a savvy gadget and an entryway. All traffic steers utilizing the assailant's PC using the ARP harming procedure
-
Spoofing—To start a caricaturing assault (Mohammadnia and Slimane 2020), an aggressor can imitate a node. A transmission could record utilizing a convenient per user.
-
Threat to communication protocols (Failed 2017)—OSI layered convention engineering and the actual layer encryption aren't supported. It requires extra security techniques in the upper layers.
-
Tag cloning—The attack (Dimitriou 2005) can mimic.
-
Denial-of-Service (DoS)—It is a kind of assault (Liang et al. 2016) where a gadget or application is malevolently denied typical activity.
-
DDoS—Any IoT gadget, organization, or programming system could be closed somewhere around a disseminated forswearing of administration (DoS) assault (Zhang and Green 2015), delivering the assistance out of reach to its shoppers.
-
Traffic analysis—Invaders (Hafeez et al. 2019) distinguish the base station, close by hubs, or bunch heads to uphold forswearing of administration assault or bundle listening in.
-
Sleep deprivation—The forswearing of a rest assault (Brun et al. 2018) on a battery-fueled gadget will bring about energy consumption.
Network Layer
-
Hello flood (Srinivas and Manivannan 2020)—The hubs in the organization decipher a welcome message coming from the inside and imprint it as a correspondence course.
-
Sinkhole (Pundir et al. 2020)—By utilizing this methodology, an aggressor compromises an organization's focal hub and supersedes to deliver it inaccessible.
-
Blackhole—Assuming that the noxious hub encounters a Blackhole assault (Sahay et al. 2018), it will drop all bundles experienced.
-
Traffic Analysis—The assailant investigates the traffic and saves a duplicate for later use in this assault.
-
Wormhole—This organization's assault (Pongle and Chavan 2015) would catch traffic in one area and divert it to another.
-
Selective forwarding—An aggressor dispatches an assault (Hariri et al. 2019) by entering an organization and dropping parcels.
-
RPL exploit (Airehrour et al. 2019)—The angry hubs can try to divert ways when information is moved.
-
Transport Layer
-
Desynchronization—Desynchronizing the transmissions between two hubs permits an aggressor to break real connections between them
-
Session hijacking (Humaira et al. 2020)—The aggressor takes the meeting ID and professes to be the genuine client to assume control over a client's Internet-based meeting
Computing Layer
-
Malicious Attack (Ahmed et al. 2018)—As laborers in the organization download vindictive programming programs from the Internet, there is a decent opportunity for the machine to get hacked. The malware would spread across the organization, putting the entire organization under its impact.
-
SQL injection (Uwagbole et al. 2017)—SQL infusion is a web security blemish that permits an assailant to interfere with a web application's data set inquiries. It allows an aggressor to get to the data that they wouldn't ordinarily have the option to recover.
-
Illegal Access (Deebak et al. 2019)—If IoT contraptions don't have an expected design, the whole organization is harmed. The organizations utilizing cloud-based registering to need unlimited authority over their organizations, which requires designing and safeguarding their cloud arrangements on security controls given by their cloud specialist co-ops.
-
Storage Attack—The programmers will dial back the movement of the gadget as they utilize the distributed storage assets.
-
Access Attack—An unapproved individual or foe accesses the IoT network here of assault.
-
Software modification (Wurster et al. 2005)—An IoT gadget can be undermined by altering its product or firmware by utilizing physical or remote admittance to make unapproved moves.
Operation Layer
-
Illegal Intervention—Even though cloud specialist co-ops are engaged in determinedly developing APIs and points of interaction, this blast has stretched out security perils connected with them.
-
Unauthorized Access (Failed 2013)—Whenever varied clients can adjust the plans of various sections of the IoT systems, synchronous execution of arrangement changes and synchronous adjusting of course of action records prompts unpredictable system status.
Application Layer
-
Malicious code—Pernicious codes or focused on malware can undoubtedly take advantage of the weaknesses of IoT widgets through the Internet, which permits programmers to think twice about gadgets.
-
Software Modification—The assailant will want to reinvent IoT gadgets remotely. This action could bring about the IoT network being hacked.
-
Data tampering (Huang et al. 2021)—During an assault of this kind, the data on the end gadget is distorted by an assailant.
-
Cross-site script (Failed 2006)—It is a procedure aggressors use to embed vindictive code into a trusted site.
-
Identity Thefts—IoT frameworks manage a lot of individual and touchy data. This information can be taken.
-
Virus attack—The target of these assaults is to break the classification of the framework. The gamble of these assaults is fundamentally higher for cell phones, sinks, or entryways in IoT organizations.
-
Spyware attack (Wazid et al. 2013)—Introduced on IoT gadgets without assent, spyware is an established program that gathers data.
-
Code Injection (Ray and Ligatti 2012)—Assailants ordinarily utilize the most straightforward method for breaking into a device or organization. Assuming the gadget is imperiled to resentful contents and confusion, it is the primary mark for an aggressor.
-
Intersection (Berthold and Langos 2002)—Whenever a framework's trustworthiness is compromised, there is a high gamble of well-being and security dangers.
-
Brute force attack (Knudsen and Robshaw 2011)—A power assault includes deliberately trying and speculating each conceivable passphrase or secret key blend to get sufficiently close to the framework.
Importance of 5G
The Internet of Things (Lee et al. 2017) is a unique paradigm that gives users access to wireless communication networks and artificial intelligence technology and is thought to be relevant to a wide range of disciplines and applications. The development of fifth-generation cellular network technology opens up the possibility of deploying vast sensors in the IoT and processing massive data, testing communications, and data mining capabilities.
The confluence of the Internet, intelligence, and objects is the 5G IIoT paradigm (Mavromoustakis 2016). Traditional IoT is a paradigm that integrates large network connection entities and encompasses the Internet and things. An intelligent individual combines intellect and objects. It creates high-functioning agents or gadgets to fulfill complex applications such as object identification.
The advancement of fifth era (5G) networks is more promptly available as a significant driver of the development of IoT applications. New applications and plans of action later on IoT require new execution standards such as enormous availability, security, dependability, the inclusion of remote correspondence, super low idleness, throughput, super solid, et al. for an immense number of IoT gadgets. The developing Long-Term Evolution (LTE) and 5G innovations are supposed to give new availability connection points to the future IoT applications (To meet these prerequisites).
Background
K-Nearest Neighbor (Sun and Huang 2010) is one of the complex Machine Learning calculations of the Supervised Learning procedure. It accepts the similitude between the new case/information and accessible cases into the classification. It stores every one of the accessible information and orders another information point in light of the comparability. It tends to group into a good suite class by utilizing the KNN algorithm. It can be utilized for Regression as well concerning Classification. It is a non-parametric calculation and implies it makes no presumption on the information. It stores the dataset and plays out an activity on the dataset. KNN calculation at the preparation stage keeps the dataset. It orders that information into a classification after getting new information. Figure 10.2 portrays the same. The steps are as follows:
Step-1: Select the number K of the neighbors.
Step-2: Calculate the Euclidean distance of K number of neighbors.
Step-3: Take the K closest neighbors according to the determined Euclidean distance.
Step-4: Among these k neighbors, count the quantity of the elements in every classification.
Step-5: Assign the new information focusing on that classification for which the quantity of the neighbor is most extreme.
Step-6: Our model is prepared.
Mathematical Explanation for Euclidean Distance
The distance between two points we should subtract the dimensions of each coordinate by each other, sum them all, apply power of two then square root it. Let the points be A and B. let the coordinates of A be (a1, a2) and B is (b1, b2)
Proposed Work
The previous contribution (Jothikumar et al. 2021) uses k-means procedure to create clusters. It converts into chain route when the threshold content goes beyond the energy of the devices in the system. The information transmitter fuel includes the power of the machine circuitry and the magnitude of facts communication and blowout. The vibrancy helps in communication circuitry. The knowledge packages ship to the destination. The architecture has two stages. The groups form during the clustering stage. The Optimal CBR method uses the k-means procedure to construct groups. It selects the cluster head based on the Euclidean length and devices fuel. The verge posted by the group head to the individual set associates is the characteristic weight above which the machine transmits the data to the head. When two-thirds of the devices are lifeless, the instruments use the greedy procedure to construct a chain-like multiple-hop methodology to reach the base station. A beacon transmission is sent by the base station to the active devices in the chaining stage (when the energy of the nodes is lower). The base station creates the path using multiple-hop chain routing and the greedy technique. The devices send the notification to the base station using the chain track.
The contribution is the improvement of the previous suggestion. The dataset is generated in the trial state. The sink node generates a public key and dispatches it to the other devices in the network. The devices create the hash code using sensed data. The code is used with the public key to generate the final outcome. The methodology secures the data from the hackers. The base station uses KNN algorithm to segregate the data into groups. The method detects the security breach at an early stage.
Assumptions
-
The nodes are assumed to be static by nature. They are deployed to track an object of interest. The same is communicated to the devices before deployment.
-
The IoT device is designated base station.
-
The nodes are embedded with a set of algorithms and credentials before deployment.
-
The nodes use multi-hop methodology to transmit messages to the base station (IoT device) or the predestined location.
-
The cluster heads communicate with the store nodes after authenticating themselves.
-
The base station broadcast the public key to its network.
Creating Trial Data Sets
-
The nodes after deployment are into trial state, where the trial readings are gathered from the nodes. This creates the trial dataset. This dataset is stored in the base station for reference.
-
It generates hash code and the same is used along with public key to generate the final outcome.
-
It uses KNN algorithm to classify the data sets into subsets (Table 10.1).
Transmitting the Messages
-
The nodes sense the environment and generate the hash code. The public key is used to generate the final outcome.
-
Any new value is recognized at an early stage.
Analysis of the Proposal
The previous architecture (Jothikumar et al. 2021) has two stages. The groups form during the clustering stage. The Optimal CBR method uses the k-means procedure to construct groups. It selects the cluster head based on the Euclidean length and devices fuel. The verge posted by the group head to the individual set associates is the characteristic weight above which the machine transmits the data to the head. When two-thirds of the devices are lifeless, the instruments use the greedy procedure to construct a chain-like multiple-hop methodology to reach the base station. A beacon transmission is sent by the base station to the active devices in the chaining stage (when the energy of the nodes is lower). The base station creates the path using multiple-hop chain routing and the greedy technique. The devices send the notification to the base station using the chain track.
A hashing computation (Pieprzyk 1993) is a cryptographic hash work. A numerical calculation maps information (of erratic size) to a hash of proper size. A hash work calculation intends to be a one-way work, infeasible to modify. Nonetheless, as of late, a few hashing calculations have been compromised.
A public key (Ambika and Raju 2010) encodes a message with the authenticity of a computerized signature. It joins a relating private key. It is known exclusively to its proprietor. Public keys are accessible from a declaration authority, which issues advanced testaments that demonstrate the proprietor's character and contain the proprietor's public key. Public keys utilize irregular calculations. It matches the shared key with a related private key. A public key is given to any individual with whom a singular need to convey, through a private key has a place with the singular it was made for and isn't shared. The public key is commonly put away on a public key foundation server and scrambles information safely before being sent on the web.
The suggestion employs a hashing methodology. The base station broadcasts public for every session. The devices generate the hash codes for the sensed data and generate the outcome using the public key. This methodology secures the data in the devices and data during transmission. The work is simulated using Python. Table 10.2 portrays the simulation parameters used in the proposal. In simulation, we have considered temperature as the parameter.
Security
The IoT is where the Internet meets the actual world. The new aspect of protection ought to be explored as the going after danger moves from controlling data to controlling incitation. The worldview makes many worries over the securing information, benefits, and, surprisingly, the whole IoT framework. The attributes like secrecy, uprightness, verification, approval, accessibility, and protection should be guaranteed for the IoT framework to ensure security in IoT. The confidential data are necessary to be secured. Hence different kinds of security measures (Varshney et al. 2019; Sharma et al. 1286) are to be adopted. The proposed work increases security by 9.67% compared with previous work (Jothikumar et al. 2021). The same is represented in Fig. 10.3.
The nodes will get compromised, if the devices are not able to defend themselves. Sensors are cheap devices. Hence protection is a must. The proposal generates hash codes, followed by the generation of outcome based on the public key. If the adversary captures the nodes, it will not be able to figure out anything out of it. The data in the devices are 11.38% secure compared to Jothikumar et al. (2021). Figure 10.4 represents the same.
Conclusion
Smart sensors and actuators work together and send data to IoT devices. These devices communicate over a common platform. The instruments use 5G Internet facility to communicate with other devices or same/different caliber. The recommendation uses k-means algorithm. It converts into chain route when the threshold content goes beyond the energy of the devices in the system. The information transmitter fuel includes the power of the machine circuitry and the magnitude of facts communication and blowout. The vibrancy helps in communication circuitry. The knowledge packages ship to the destination. The architecture has two stages. The groups form during the clustering stage. The Optimal CBR method uses the k-means procedure to construct groups. It selects the cluster head based on the Euclidean length and devices fuel. The verge posted by the group head to the individual set associates is the characteristic weight above which the machine transmits the data to the head. When two-thirds of the devices are lifeless, the instruments use the greedy procedure to construct a chain-like multiple-hop methodology to reach the base station. A beacon transmission is sent by the base station to the active devices in the chaining stage (when the energy of the nodes is lower). The base station creates the path using multiple-hop chain routing and the greedy technique. The devices send the notification to the base station using the chain track. The suggestion employs a hashing methodology. The base station broadcasts public for every session. The devices generate the hash codes for the sensed data and generate the outcome using the public key. This methodology secures the data in the devices and data during transmission. The proposed work increases security by 9.67% when transmitting data and 11.38% data when the device is compromised.
References
Aarika K, Bouhlal M, Abdelouahid RA, Elfilali S, Benlahmar E (2020) Perception layer security in the internet of things. In: The 17th international conference on mobile systems and pervasive computing (MobiSPC), the 15th international conference on future networks and communications (FNC);The 10th international conference on sustainable energy information technology, Leuven, Belgium
Andy S, Rahardjo B, Hanindhito B (2017) Attack scenarios and security analysis of MQTT communication protocol in IoT system. In: 4th international conference on electrical engineering, computer science and informatics (EECSI), Yogyakarta, Indonesia
Ahmed A, Latif R, Latif S, Abbas H, Khan FA (2018) Malicious insiders attack in IoT based multi-cloud e-healthcare environment: a systematic literature review. Multimed Tools Appl 77(17):21947–21965
Airehrour D, Gutierrez JA, Ray SK (2019) SecTrust-RPL: a secure trust-aware RPL routing protocol for Internet of Things. Futur Gener Comput Syst 93:860–876
Alramadhan M, Sha K (2017) An overview of access control mechanisms for internet of things. In: 26th international conference on computer communication and networks (ICCCN), Vancouver, BC, Canada
Alromih A, Al-Rodhaan M, Tian Y (2018) A randomized watermarking technique for detecting malicious data injection attacks in heterogeneous wireless sensor networks for internet of things applications. Sensors 18(12):4346
Ambika N (2020) SYSLOC: hybrid key generation in sensor network. In: Handbook of wireless sensor networks: issues and challenges in current scenario's. advances in intelligent systems and computing, vol 1132. Springer, Cham, pp 325–347
Ambika N (2019) Energy-perceptive authentication in virtual private networks using GPS data. In: Security, privacy and trust in the IoT environment. Springer, Cham, pp 25–38
Ambika N (2021) Wearable sensors for smart societies: a survey. In: Green technological innovation for sustainable smart societies. Springer, Cham, pp 21–37
Ambika N, Raju GT (2010) Figment authentication scheme in wireless sensor network. In: Security technology, disaster recovery and business continuity, Jeju Island, Korea, Springer, pp 220–223
Berthold O, Langos H (2002) Dummy traffic against long term intersection attacks. In: International workshop on privacy enhancing technologies, Cambridge, UK
Brun O, Yin Y, Gelenbe E, Kadioglu YM, Augusto-Gonzalez J, Ramos M (2018) Deep learning with dense random neural networks for detecting attacks against IoT-connected home environments. In: International ISCIS security workshop, London, UK
Bulashenko A, Piltyay S, Polishchuk A, Bulashenko O (2020) New traffic model of M2M technology in 5G wireless sensor networks. In: 2nd international conference on advanced trends in information theory (ATIT), Kyiv, Ukraine
Deebak BD, Al-Turjman F, Aloqaily M, Alfandi O (2019) An authentic-based privacy preservation protocol for smart e-healthcare systems in IoT. IEEE Access 7:135632–135649
Dian FJ, Vahidnia R, Rahmati A (2020) Wearables and the Internet of Things (IoT), applications, opportunities, and challenges: a Survey. IEEE Access 8:69200–69211
Dimitriou T (2005) A lightweight RFID protocol to protect against traceability and cloning attacks. In: First international conference on security and privacy for emerging areas in communications networks (SECURECOMM'05), Athens, Greece
Fu S, Zhao L, Su Z, Jian X (2018) UAV based relay for wireless sensor networks in 5G systems. Sensors 18(8):2413
Gardašević G, Katzis K, Bajić D, Berbakov L (2020) Emerging wireless sensor networks and Internet of Things technologies—foundations of smart healthcare. Sensors 20(13):3619
Hafeez I, Antikainen M, Tarkoma S (2019) Protecting IoT-environments against traffic analysis attacks with traffic morphing. In: IEEE international conference on pervasive computing and communications workshops (PerCom Workshops), Kyoto, Japan
Hariri A, Giannelos N, Arief B (2019) Selective forwarding attack on iot home security kits. In: Computer security, Cham. Springer, pp 360–373
Hassan WH (2019) Current research on Internet of Things (IoT) security: a a survey. Comput Netw 148:283–294
Huang DW, Liu W, Bi J (2021) Data tampering attacks diagnosis in dynamic wireless sensor networks. Comput Commun 172:84–92
Humaira F, Luva IMSSA, Rahman MB (2020) A secure framework for IoT smart home by resolving session Hijacking. Global J Comp Sci Technol 20(2):1–13
Jothikumar C, Ramana K, Chakravarthy VD, Singh S, Ra IH (2021) An efficient routing approach to maximize the lifetime of IoT-based wireless sensor networks in 5G and beyond. Mobile Inf Syst 1–11
Kirda E, Kruegel C, Vigna G, Jovanovic N (2006) Noxes: a client-side solution for mitigating cross-site scripting attacks. In: ACM symposium on applied computing, Dijon France
Khattak HA, Shah MA, Khan S, Ali I, Imran M (2019) Perception layer security in Internet of Things. Futur Gener Comput Syst 100:144–164
Khattak HA, Shah MA, Khan S, Ali I, Imran M (2019) Perception layer security in Internet of Things. Future Gener Comput Syst 100:144–164
Knudsen LR, Robshaw MJ (2011) Brute force attacks. In: The block cipher companion. Springer, Berlin, Heidelberg, pp 95–108
Krishna R, Priyadarshini A, Jha A, Appasani B, Srinivasulu A, Bizon N (2021) State-of-the-art review on IoT threats and attacks: taxonomy, challenges and solutions. Sustainability 13:9463
Kumar S, Sahoo S, Mahapatra A, Swain AK, Mahapatra KK (2017) Security enhancements to system on chip devices for IoT perception layer. In: IEEE international symposium on nanoelectronic and information systems (iNIS), Bhopal, India
Lee SK, Bae M, Kim H (2017) Future of IoT networks: a survey. Appl Sci 7(10):1072
Liang L, Zheng K, Sheng Q, Huang X (2016) A denial of service attack method for an iot system. In: 8th international conference on information technology in medicine and education (ITME), Fuzhou, China
Lynggaard P, Skouby KE (2015) Deploying 5G-technologies in smart city and smart home wireless sensor networks with interferences. Wirel Pers Commun 81(4):1399–1413
Mahmoud HH, ElAttar HM, Saafan A, ElBadawy H (2017) Optimal operational parameters for 5G energy harvesting cognitive wireless sensor networks. IETE Tech Rev 34(sup1):62–72
Mavromoustakis CX, Mastorakis G, Mongay JM (2016) Internet of Things (IoT) in 5G mobile technologies, vol 8, Springer, Switzerland
Mishra AK, Tripathy AK, Puthal D, Yang LT (2018) Analytical model for sybil attack phases in internet of things. IEEE Internet Things J 6(1):379–387
Mohammadnia H, Slimane SB (2020) IoT-NETZ: Practical spoofing attack mitigation approach in SDWN network. In: Seventh international conference on software defined systems (SDS), Paris, France
Muslukhov I, Boshmaf Y, Kuo C, Lester J, Beznosov K (2013) Know your enemy: the risk of unauthorized access in smartphones by insiders. In: 15th international conference on Human-computer interaction with mobile devices and services, Munich Germany
Nagaraj A (2021) Introduction to sensors in IoT and cloud computing applications. Bentham Science Publishers, UAE
Navas RE, Bouder HL, Cuppens N, Cuppens F, Papadopoulos GZ (2018) Do not trust your neighbors! A small IoT platform illustrating a man-in-the-middle attack. In: International conference on ad-hoc networks and wireless, Saint-Malo, France
Pacheco A, Junior J, Ruiz-Armenteros A, Henriques R (2021) Assessment of k-nearest neighbor and random forest classifiers for mapping forest fire areas in central Portugal using landsat-8, sentinel-2, and terra imagery. Remote Sens 13:1345
Pieprzyk JSB (1993) Design of hashing algorithms. Springer, Berlin, Heidelberg
Pongle P, Chavan G (2015) Real time intrusion and wormhole attack detection in internet of things. Int J Comput Appl 121(9):0975–8887
Pundir S, Wazid M, Singh DP, Das AK, Rodrigues JJPC, Park Y (2020) Designing efficient sinkhole attack detection mechanism in edge-based IoT deployment. Sensors 20(5):1300
Ray D, Ligatti J (2012) Defining code-injection attacks. Acm Sigplan Notices 47(1):179–190
Sachan S, Sharma R, Sehgal A (2021) SINR based energy optimization schemes for 5G vehicular sensor networks. Wirel Pers Commun 1–21 (2021)
Sahay R, Geethakumari G, Mitra B, Thejas V (2018) Exponential smoothing based approach for detection of blackhole attacks in IoT. In: IEEE international conference on advanced networks and telecommunications systems (ANTS), Indore, India
Sekaran R, Goddumarri SN, Kallam S, Ramachandran M, Patan R, Gupta D (2021) 5G integrated spectrum selection and spectrum access using AI-based frame work for IoT based sensor networks. Comput Netw 186:107649
Sharma M, Bhushan B, Khamparia A (2021) Securing Internet of Things: attacks, countermeasures and open challenges. In: Emerging technologies in data mining and information security. Advances in intelligent systems and computing, vol 1286. Singapore, Springer, pp 873–885
Shin S, Kwon T (2020) A privacy-preserving authentication, authorization, and key agreement scheme for wireless sensor networks in 5G-integrated Internet of Things. IEEE Access 8:67555–67571
Srinivas TAS, Manivannan SS (2020) Prevention of hello flood attack in IoT using combination of deep learning with improved rider optimization algorithm. Comput Commun 163:162–175
Sun S, Huang R (2010) An adaptive k-nearest neighbor algorithm. In: Seventh international conference on fuzzy systems and knowledge discovery, Yantai, China
Tilwari V, Dimyati K, Hindia M, Mohmed Noor Izam T, Amiri I (2020) EMBLR: a high-performance optimal routing approach for D2D communications in large-scale IoT 5G network. Symmetry 12:438
Uwagbole SO, Buchanan WJ, Fan L (2017) Applied machine learning predictive analytics to SQL injection attack detection and prevention. In: IFIP/IEEE symposium on integrated network and service management (IM), Lisbon, Portugal
Varshney T, Sharma N, Kaushik I, Bhushan B (2019) Architectural model of security threats & their countermeasures in IoT. In: International conference on computing, communication, and intelligent systems (ICCCIS), Greater Noida, India
Wazid M, Katal A, Goudar RH, Singh DP, Tyagi A, Sharma R, Bhakuni P (2013) A framework for detection and prevention of novel keylogger spyware attacks. In: 7th international conference on intelligent systems and control (ISCO), Coimbatore, India
Wurster G, Van Oorschot PC, Somayaji A (2005) A generic attack on checksumming-based software tamper resistance. In: IEEE symposium on security and privacy (S&P'05), Oakland, CA, USA
Zhang C, Green R (2015) Communication security in internet of thing: preventive measure and avoid DDoS attack over IoT network. In: 18th symposium on communications & networking, VA, USA
Zhang G, Kou L, Zhang L, Liu C, Da Q, Sun J (2017) A new digital watermarking method for data integrity protection in the perception layer of IoT. Secur Commun Netw 1–13
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Open Access This chapter is licensed under the terms of the Creative Commons Attribution 4.0 International License (http://creativecommons.org/licenses/by/4.0/), which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons license and indicate if changes were made.
The images or other third party material in this chapter are included in the chapter's Creative Commons license, unless indicated otherwise in a credit line to the material. If material is not included in the chapter's Creative Commons license and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder.
Copyright information
© 2023 The Author(s)
About this chapter
Cite this chapter
Ambika, N. (2023). Securing the IoT-Based Wireless Sensor Networks in 5G and Beyond. In: Bhushan, B., Sharma, S.K., Kumar, R., Priyadarshini, I. (eds) 5G and Beyond. Springer Tracts in Electrical and Electronics Engineering. Springer, Singapore. https://doi.org/10.1007/978-981-99-3668-7_10
Download citation
DOI: https://doi.org/10.1007/978-981-99-3668-7_10
Published:
Publisher Name: Springer, Singapore
Print ISBN: 978-981-99-3667-0
Online ISBN: 978-981-99-3668-7
eBook Packages: EngineeringEngineering (R0)