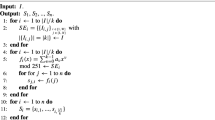Abstract
Shamir’s polynomial-based secret image sharing (SIS) scheme and visual secret sharing (VSS) also called visual cryptography scheme (VCS), are the primary branches in SIS. In traditional (k, n) threshold secret sharing, a secret image is fully (entirely) generated into n shadow images (shares) distributed to n associated participants. The secret image can be recovered by collecting any k or more shadow images. The previous SIS schemes dealt with the full secret image neglecting the possible situation that only part of the secret image needs protection. However, in some applications, only target part of the secret image may need to be protected while other parts may be not in a full image. In this paper, we consider the partial secret image sharing (PSIS) issue as well as propose a PSIS scheme for (n, n) threshold based on image inpainting and linear congruence (LC). First the target part is manually selected or marked in the color secret image. Second, the target part is automatically removed from the original secret image to obtain the same input cover images (unpainted shadow images). Third, the target secret part is generated into the pixels corresponding to shadow images by LC in the processing of shadow images texture synthesis (inpainting), so as to obtain the shadow images in a visually plausible way. As a result, the full secret image including the target secret part and other parts will be recovered losslessly by adding all the inpainted meaningful shadow images. Experiments are conducted to evaluate the efficiency of the proposed scheme.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
- Secret image sharing
- Partial secret image sharing
- Image inpainting
- Linear congruence
- Color image
- Lossless recovery
- Meaningful shadow images
1 Introduction
Through splitting the secret image into noise-like shadow images (also called shadows or shares), secret image sharing (SIS) distributes a secret image among multiple participants. The secret is recovered by collecting sufficient authorized participants(shadow images). SIS can be applied in not only information hiding, but also access control, authentication, watermarking, and transmitting passwords etc. Shamir’s polynomial-based scheme [1] and visual secret sharing (VSS) [2] also called visual cryptography scheme (VCS), are the primary branches in this field.
In Shamir’s original polynomial-based (k, n) threshold SIS [1], the secret image is generated into the constant coefficient of a random \((k-1)\)-degree polynomial to obtain n shadow images distributed to n associated participants. The secret image can be losslessly recovered by collecting any k or more shadow images based on Lagrange interpolation. Following Shamir’s scheme and utilizing all coefficients of the polynomial for embedding secret, Thien and Lin [3] reduced share size 1/k times to the secret image. The advantage of Shamir’s polynomial-based scheme [4,5,6] is lossless recovery. Shamir’s polynomial-based SIS requires more complicated computations, i.e., Lagrange interpolations, for reconstructing and known order of shares, although the scheme only needs k shares for recovering the distortion-less secret image.
In (k, n) threshold VSS [7,8,9,10,11,12,13], the generated n shadow images are printed onto transparencies and then distributed to n associated participants. The beauty of VSS is that, the secret image can be revealed by superposing any k or more shadow images and human visual system (HVS) with no cryptographic computation. Less than k shares will reveal nothing about the secret except the image size. Inspired by Naor and Shamir’s VSS work, the associated VSS physical properties and its problems are extensively studied, such as contrast [14], threshold [15], different formats [16], multiple secrets [6], noise-like patterns [11, 17,18,19,20], pixel expansion [8, 9, 21, 22] and so on [23, 24].
In most of the existing SIS schemes, the full (entire) secret image is directly generated into the shadow images. The previous SIS schemes dealt with the full secret image neglecting the possible situation that only part of the secret image may need protection. However, there are many examples that only part of the secret image may need to be protected while other parts may be not in the same image, such as improving part design, sensitive information in part of a image and so on. One possible scenario is described as follows. On the basis of multiple traditional design modules in a product, a company improves one module design of them, while the other modules continue to use the traditional original design. At this point for the overall design drawing of this product, the improved module is needed to be protected and the other original modules can be public. Due to business privacy and access control, this product design drawing is kept by the company’s n managers. Each manager can display the traditional modules in public display to facilitate the product introduction and other activities. In accordance with business needs, k or more managers together have the right to losslessly recover the full product design drawing including the improved module. In this scenario, we need protect target part of the secret image other than the full secret image as well as need access control with (k, n) threshold.
Thus, in some applications we may only need to encrypt part of the secret image rather than the full secret image for some reasons. However, the previous SIS schemes have not considered this issue. In order to deal with the partial secret image sharing (PSIS) issue, in this paper, we will introduce PSIS problem as well as propose a novel PSIS scheme for (n, n) threshold based on image inpainting [25, 26] and linear congruence (LC) [27], where (n, n) threshold is a special case of (k, n) threshold under \(k=n\). The target secret part of the color secret image is first manually selected and then automatically removed from the original color secret image to obtain the same input cover images (unpainted shadow images). Then, the target secret part is generated into the pixels corresponding to shadow images by LC in the processing of shadow images texture synthesis (inpainting), so as to obtain the shadow images in a way that looks reasonable to the human eye. As a result, the full secret image including the target secret part and the other parts will be recovered losslessly by adding all the inpainted meaningful shadow images. Experiments are conducted to evaluate the efficiency of the proposed scheme.
The rest of the paper is organized as follows. Section 2 introduces some basic requirements for the proposed scheme. In Sect. 3, the proposed scheme is presented in detail. Section 4 is devoted to experimental results. Finally, Sect. 5 concludes this paper.
2 Preliminaries
In this section, we give the PSIS problem description and some preliminaries as the basis for the proposed method. The original secret image S is shared among original total n shadow images, while the reconstructed secret image \( {S}' \) is reconstructed from t (\( k \le t \le n,t \in \mathrm{Z}^ + \)) shadow images.
2.1 Problem Definition
As show in Fig. 1, for the given secret image S in Fig. 1(a), Fig. 1(b) indicates the same input cover image C obtained by manually selecting and removing the target part from the original secret image S, where the notations of different parts and their edge are presented in Fig. 1(c). The region \(\varOmega \) is the target secret part (object), part \(\varPhi \) illustrates the untouched part, and \(\partial \varOmega \) denotes the edge of the 2 parts. Shadow images covered secret after sharing are denoted as \( S{C_i},i=1,2,...,n\) for (k, n) threshold.
The PSIS problem can be described as follows: From the selected target part \(\varOmega \) and the associated cover images \(C_1, C_2, \cdots C_{n}\), the PSIS scheme may generate n meaningful shadow images \( S{C_i},i=1,2,...,n\) distributed to n associated participants, where each shadow image looks like a nature image. When any k or more shadow images are collected, the full secret image including the secret target part can be reconstructed. Whereas even if infinite computational power is available, less than k shadow images will reveal nothing about the secret target part.
2.2 Linear Congruence
Equations (1) and (2) are the basic equations for LC secret sharing, by which (n, n) threshold secret sharing can be achieved, where P denotes a number larger than the biggest pixels value, \(x_i\) and y represent the i-th shared pixel and secret pixel, respectively. In Eq. (1), a one-to-many mapping between y and sum of all the x is established, so the secret value can be recovered losslessly with all the shared values. But there is no direct map relationship between secret value and less than k shared value, thus the method is secure. So Eq. (1) guarantees the feasibility of precise recovery and security for the proposed scheme. At the meanwhile, the condition in Eq. (2) ensures that no duplicate values exist in first n shared pixels.
Equation (3) is the basic equation for LC secret recovery. After removing the duplicate shared values, the rest of shared values \(x_{i_1},x_{i_2},\cdots ,x_{i_t}\) take part in the computation for the recovered secret value \(y'\) using Eq. (3).
Figure 2 indicates an example by directly applying LC method for (2, 2) threshold, where the input secret image is the same as Fig. 1. We can see that the secret target part can be reconstructed losslessly, while the corresponding the secret target parts of the shadow images are noise-like. In the revealing process of the secret image, it only needs to iterate t pixels and execute \(t - 1\) times addition operation and one time module operation to decode a secret pixel. Obviously, the time complexity is smaller. Hence, LC sharing idea is selected in our scheme as an SIS method.
2.3 Image Inpainting
Many image inpainting schemes were proposed in the literature, here Criminisi et al. approach [25, 26] will be applied in our scheme, which is researched widely. We will introduce Criminisi et al. image inpainting approach in detail. The keynote of it is the selection of patch priorities order in region-filling. The patch with the highest priority will be filled preferentially. The priorities will be renewed after every filling until the image is inpainted totally in the same manner. The main inpainting process includes:
-
1.
Select the part \(\varOmega \) to be inpainted, and \(\varOmega =S-\varPhi \).
-
2.
Determine the size of template window, denoted as \(\varPsi _p\), using image texture feature, where any \(p \in \partial \varOmega \) exhibits center of template window and the size of the window should be larger than the biggest texture element.
-
3.
Compute patch priorities by Eq. (4) which is defined as the product of the confidence term and data term.
$$\begin{aligned} W(p)=C(p)D(p) \end{aligned}$$(4)where C(p) and D(p) denote the confidence term and data term, respectively, defined as follows:
$$\begin{aligned} C(p) = \frac{{\sum \limits _{q \in \psi _p \cap \bar{\varOmega } } {C(q)} }}{{\left| {\psi _p } \right| }} \end{aligned}$$(5)$$\begin{aligned} D(p) = \frac{{\left| {\nabla S_p^ \bot \cdot n_p } \right| }}{a} \end{aligned}$$(6)where \(\left| {\psi _p } \right| \) indicates the area of \(\psi _p\) and a is a normalization factor. \(\nabla S_p^ \bot \) and \(n_p\) denote the isophote direction and the normal vector direction at point p, respectively.
The confidence term expresses the amount of reliable information contained in template window. The data term measures the difference between the isophote direction and the normal vector direction. In a word, we conclude that the template window includes more information and the difference between the isophote direction and the normal vector direction is less, the priority of the patch is higher.
-
4.
Find \(\hat{p}\) using Eq. (7) and the most matching block \(\psi _{\hat{q}} \in \varPhi \) in the source image using template window according to Eq. (8), where the evaluation standard is the Sum of Squared Differences (SSD). Finally, the most matching block replaces the patch of current window.
$$\begin{aligned} \hat{p} = \mathop {\arg \;\max }\limits _{p \in \partial \varOmega } W(p) \end{aligned}$$(7)$$\begin{aligned} \hat{q} = \mathop {\arg \;\min }\limits _{q \in \varPhi } d(\psi _{\hat{p}} ,\psi _q ) \end{aligned}$$(8) -
5.
Renew the confidence terms after each filling process \(C(q) = C(\hat{p})\) for any \(q \in \psi _{\hat{p}} \cap \varOmega \).
-
6.
Repeat steps 3–5 until the image is inpainted completely.
Taking as an example, the inpainted image by Criminisi et al. approach is presented in Fig. 3. We can see that another visually plausible image is obtained, thus image inpainting will be applied in the proposed scheme to achieve meaningful shadow images.
An example of the inpainted image from Fig. 1(b) by Criminisi et al.’s approach
3 The Proposed PSIS Scheme
Here, in order to deal with the PSIS issue, in this paper, we propose a novel PSIS scheme for (n, n) threshold based on image inpainting and LC. We present the proposed PSIS scheme based on the original secret image S and the selected secret target part \(\varOmega \), resulting in n output meaningful shadow images \(SC_1,SC_2, \cdots SC_n \). Our generation steps are described in Algorithm 1.

In step 2 of our Algorithm, each shadow image has its own order (highest priority) in which the filling proceeds, i.e., \(\hat{p_i}\). Aiming to inpaint synchronously, among the n candidate orders, the highest priority is selected again in Step 3 as the applied order for all the n shadow images inpainting.
After the most matching block replaces the patch of the current window in Step 4, the secret block of the current window corresponding to the secret target part will be generated into the n shadow images corresponding blocks based on LC sharing in Steps 5–6. Thus, the modified patches of the current window will be the basis for next inpainting processing so that the target secret pixel is encoded into the pixels corresponding to shadow images in the processing of shadow images inpainting. As a result, meaningful shadow images may be achieved in a visually plausible way.
The secret recovery of the proposed scheme is the same as LC method according to Eq. (3) by all the n shadow images.
4 Experimental Results and Analyses
In this section, experiments and analyses are conducted to evaluate the effectiveness of the proposed method. In the experiments, the same example as shown in Fig. 1 will be employed as the input color secret image, with size of 512 \( \times \) 384.
Simulation result by the proposed PSIS scheme is presented in Fig. 4 for (4, 4) threshold, where Fig. 4(a) \( - \) (d) show the generated four shadow images \(SC_1, SC_2, SC_3, SC_4\) and the recovered results by two or more shadow images are presented in Fig. 4(e) \( - \) (o). Here “+” indicates addition and module operation as in LC. The shadow images corresponding to the secret target part are meaningful in a way that looks reasonable to the human eye, although little artifact appears in the shadow images due to the modification of the shadow images blocks for secret block generation based on LC sharing in Steps 5–6 of our Algorithm. We can see that the secret target part can be reconstructed losslessly when all the four shares are collected. The recovering results by less than four shadow images cannot recovery the secret while secret leakage appears especially for the edge of the selected secret target part, which also may be caused by the modification of the shadow images blocks in Steps 5–6 of our Algorithm. In the revealing process of the secret image, it only needs to execute one time addition operation and one time module operation to decode a secret pixel so that the recovery computation complexity is simple. Decreasing the artifacts and threshold extension will be our future work.
Additional (3, 3) threshold simulation result is illustrated in Fig. 5, we can conclude similar results as the previous simulation except for a little more artifact in the shadow image, which is caused by LC sharing feature.
Based on the above results we can conclude that:
-
1.
The target part is successfully inpainted into visually plausible shadow image.
-
2.
Each shadow image is meaningful in a way that looks reasonable to the human eye, while Every single shadow image can not disclose the secret image.
-
3.
When \( t < n\) shadow images are collected, we cannot recovery the secret although secret leakage appears.
-
4.
When \( t=n \) shadow images are recovered by only addition and module operation, the secret image including the secret target part could be recovered losslessly.
-
5.
An acceptable the partial secret image sharing (PSIS) for (n, n) threshold is achieved in our scheme.
5 Conclusion
This paper considered the new partial secret image sharing (PSIS) issue as well as proposed a novel PSIS scheme for (n, n) threshold based on image inpainting and linear congruence (LC) secret sharing method. Experiments showed that the output inpainted shadow images are meaningful, and the full secret image including the target secret part and other parts can be recovered losslessly by addition. Decreasing the artifacts and threshold extension will be our future work.
References
Shamir, A.: How to share a secret. Commun. ACM 22(11), 612–613 (1979)
Naor, M., Shamir, A.: Visual cryptography. In: De Santis, A. (ed.) EUROCRYPT 1994. LNCS, vol. 950, pp. 1–12. Springer, Heidelberg (1995). https://doi.org/10.1007/BFb0053419
Thien, C.C., Lin, J.C.: Secret image sharing. Comput. Graph. 26(5), 765–770 (2002)
Lin, S.J., Lin, J.C.: VCPSS: A two-in-one two-decoding-options image sharing method combining visual cryptography (vc) and polynomial-style sharing (pss) approaches. Pattern Recogn. 40(12), 3652–3666 (2007)
Yang, C.N., Ciou, C.B.: Image secret sharing method with two-decoding-options: Lossless recovery and previewing capability. Image Vis. Comput. 28(12), 1600–1610 (2010)
Li, P., Ma, P.J., Su, X.H., Yang, C.N.: Improvements of a two-in-one image secret sharing scheme based on gray mixing model. J. Vis. Commun. Image Represent. 23(3), 441–453 (2012)
Yan, X., Wang, S., El-Latif, A.A.A., Niu, X.: Visual secret sharing based on random grids with abilities of AND and XOR lossless recovery. Multimedia Tools Appl., 1–22 (2013)
Yang, C.N.: New visual secret sharing schemes using probabilistic method. Pattern Recognit. Lett. 25(4), 481–494 (2004)
Cimato, S., De Prisco, R., De Santis, A.: Probabilistic visual cryptography schemes. Comput. J. 49(1), 97–107 (2006)
Wang, D., Zhang, L., Ma, N., Li, X.: Two secret sharing schemes based on boolean operations. Pattern Recognit. 40(10), 2776–2785 (2007)
Wang, Z., Arce, G.R., Di Crescenzo, G.: Halftone visual cryptography via error diffusion. IEEE Trans. Inf. Forensics Security. 4(3), 383–396 (2009)
Weir, J., Yan, W.Q.: A comprehensive study of visual cryptography. In: Shi, Y.Q. (ed.) Transactions on Data Hiding and Multimedia Security V. LNCS, vol. 6010, pp. 70–105. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-14298-7_5
Yang, C.N., Sun, L.Z., Yan, X., Kim, C.: Design a new visual cryptography for human-verifiable authentication in accessing a database. J. Real-Time Image Proc. 12(2), 483–494 (2016)
Wu, X., Sun, W.: Improving the visual quality of random grid-based visual secret sharing. Sig. Process. 93(5), 977–995 (2013)
Yan, X., Wang, S., Niu, X.: Threshold construction from specific cases in visual cryptography without the pixel expansion. Sig. Process. 105, 389–398 (2014)
Luo, H., Yu, F., Pan, J.S., Lu, Z.M.: Robust and progressive color image visual secret sharing cooperated with data hiding. In: Eighth International Conference on Intelligent Systems Design and Applications, ISDA 2008, vol. 3, Kaohsiung, Taiwan, IEEE, pp. 431–436. IEEE (2008)
Yan, X., Wang, S., Niu, X., Yang, C.N.: Generalized random grids-based threshold visual cryptography with meaningful shares. Sig. Process. 109, 317–333 (2015)
Zhou, Z., Arce, G.R., Di Crescenzo, G.: Halftone visual cryptography. IEEE Trans. Image Process. 15(8), 2441–2453 (2006)
Liu, F., Wu, C.: Embedded extended visual cryptography schemes. IEEE Trans. Inf. Forensics Secur. 6(2), 307–322 (2011)
Yan, X., Wang, S., Niu, X., Yang, C.N.: Halftone visual cryptography with minimum auxiliary black pixels and uniform image quality. Digit. Signal Proc. 38, 53–65 (2015)
Guo, T., Liu, F., Wu, C.: Threshold visual secret sharing by random grids with improved contrast. J. Syst. Softw. 86(8), 2094–2109 (2013)
Fu, Z., Yu, B.: Visual cryptography and random grids schemes. In: Shi, Y.Q., Kim, H.-J., Pérez-González, F. (eds.) IWDW 2013. LNCS, vol. 8389, pp. 109–122. Springer, Heidelberg (2014). https://doi.org/10.1007/978-3-662-43886-2_8
Ateniese, G., Blundo, C., De Santis, A., Stinson, D.R.: Visual cryptography for general access structures. Inf. Comput. 129(2), 86–106 (1996)
Li, P., Yang, C.N., Wu, C.C., Kong, Q., Ma, Y.: Essential secret image sharing scheme with different importance of shadows. J. Vis. Commun. Image Represent. 24(7), 1106–1114 (2013)
Criminisi, A., Perez, P., Toyama, K.: Region filling and object removal by exemplar-based image inpainting. IEEE Trans. Image Process. 13(9), 1200–12 (2004). A Publication of the IEEE Signal Processing Society
Shen, W., Song, X., Niu, X.: Hiding traces of image inpainting. Res. J. Appl. Sci. Eng. Technol. 4(23), 4962–4968 (2012)
Liu, L., Lu, Y., Yan, X., Wan, S.: A progressive threshold secret image sharing with meaningful shares for gray-scale image. In: 2016 12th International Conference on Mobile Ad-Hoc and Sensor Networks (MSN), pp. 380–385. IEEE (2016)
Acknowledgement
This work is supported by the National Natural Science Foundation of China (Grant Number: 61602491).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Yan, X. et al. (2017). Partial Secret Image Sharing for (n, n) Threshold Based on Image Inpainting. In: Zhao, Y., Kong, X., Taubman, D. (eds) Image and Graphics. ICIG 2017. Lecture Notes in Computer Science(), vol 10668. Springer, Cham. https://doi.org/10.1007/978-3-319-71598-8_47
Download citation
DOI: https://doi.org/10.1007/978-3-319-71598-8_47
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-71597-1
Online ISBN: 978-3-319-71598-8
eBook Packages: Computer ScienceComputer Science (R0)