Abstract
Fog computing is an emerging research domain to provide computational services such as data transmission, application processing and storage mechanism. Fog computing consists of a set of fog server machines used to communicate with the mobile user in the edge network. Fog is introduced in cloud computing to meet data and communication needs for Internet of Things (IoT) devices. However, the vital challenges in this system are job scheduling, which is solved by examining the makespan, minimizing energy depletion and proper resource allocation. In this paper, we introduced a reinforced strategy Dynamic Opposition Learning based Social Spider Optimization (DOLSSO) Algorithm to enhance individual superiority and schedule workflow in Fog computing. The extensive experiments were conducted using the FogSim simulator to generate the dataset and an energy-efficient open-source tool utilized to model and simulate resource management in fog computing. The performance of the formulated model is ratified using two test cases. The proposed algorithm attained the optimized schedule with minimized cost function concerning the CPU processing period and assigned memory. Our simulation outcomes show the efficacy of the introduced technique in handling job scheduling issues, and the results are contrasted with five existing metaheuristic techniques. The results show that the proposed method achieves 10% - 15% better CPU utilization and 5%-10% less energy consumption than the other techniques.
Similar content being viewed by others
Introduction
The everyday needs of society are facilitated using cloud computing [1]. Cloud computing system uses master-slave infrastructure among service providers. The client users access cloud computing on-demand to access the service using “pay-as-you-go” [2]. Cloud services are assessed anywhere at any time through the internet. Besides their benefit, cloud computing consumes high latency and higher network bandwidth, since data centers are available far from the client user. A novel architecture is to integrate fog computing in the cloud environment to eradicate the above-said issue. The idea of fog computing extends direct communication among edge nodes of the network [3]. Fog computing network consists of fog servers with a wireless communication device, data storage memory and computational unit [4]. The energy-efficient resource utilization plays a significant role in this network. Therefore, any deviation in cloud data might result in a substantial change in energy consumption, affecting starvation. This situation can be eradicated by efficiently scheduling the jobs into the fog server. But it is observed that dynamic job scheduling is tricky due to complicated task flow and perplexing issues [5].
Job scheduling problem (JSP) is an NP-hard combinatorial optimization problem due to various numbers of all feasible solutions is t!pm where t denotes the count of jobs/tasks, and pm specifies the total count of physical machines. Individual jobs deal with the unique operation sequence. The main aim of job scheduling is to reduce the response time and maximise the company’s revenue. However, the JSP suffers two main challenges: choosing an adequate facility and determining the best order of operations to reduce the makespan. Several researchers have contributed to solving job scheduling using mathematical models, namely exact, heuristic and meta-heuristic approaches. Firstly, Exact strategies like the dynamic approach, branch and bound method, and component and price approaches are adequate to solve the small-scale problem and to provide optimal solutions. However, these exact approaches are time-consuming and suffer to solve large-scale real-time issues. The minor JSPs problems can be optimally solved using the CPLEX application [6].
In the real-time, most JSPs are large scale and generic mathematical models cannot guarantee optimal solutions. Still, they can provide near-optimal solutions concerning colossal time consumption. Recent research has used meta-heuristic algorithms, namely evolutionary algorithm and swarm intelligence algorithm, to solve the JSPs problem. A hybrid Genetic algorithm [7] was utilized to minimize the maximum completion time. However, the model fails to provide the optimal solution due to poor convergence. The multi-objective artificial bee colony algorithm [8] was introduced to address the multi-objectives, assignment vector, job permutation and machine speed selection. The Pareto archive particle swarm optimization algorithm [9] combines the Crowing distance-based archive and mutation process to handle the JSP issues. Due to the method’s limited exploration ability, it becomes stuck in local optima. In [10], the ant colony method was used to overcome the problems with flexible job shops. The outcomes demonstrate that the strategy produces superior results to the compared algorithms.
The hybrid genetic and cuckoo search technique devised by Singh Satyendra et al. [11] produces better results in small-scale instances but falls short in medium- and large-scale ones. Wang et al. [12] used hybrid discrete differential evolution to handle task scheduling challenges and reduce the maximum turnover time. However, the algorithm is significantly more complicated because of the problem with the solution update. Lu et al. [13] suggested a cellular grey wolf optimisation to reduce cycle time in blocking flow shops. To strengthen the search process by adding new control factors, the author of [14] recently presented hybrid whale optimization with the Levy flight and DE algorithm. They also used the technique to shorten the JSP problem’s turnaround time. The spotted hyena optimizer was devised to address the discrete work sequence difficulties [5]. Atay et al. [15] suggested a clonal selection algorithm to address the JSP difficulties. The proposed approach yields superior results in terms of reducing completion time.
The main objective of the flower pollination algorithm [16] is to shorten the time complexity of task sequence issues. The author in [17] introduced the bi-objective optimization technique to lower the makespan and cost factors. The author also used the goal programming method to submit multi-objective task sequence assignments in cloud-fog computing [18]. The simulation results offer superior outcomes in terms of access level control, deadline measures, and service delay times. A modified pigeon-inspired optimization technique [19] was applied to deal with job sequence issues. The results of the experiment outperform the compared algorithms. However, due to the complexity of the algorithms, task assignment takes a lengthy time.
Social Spider Optimization (SSO) technique is a recently introduced swarm intelligence algorithm that mimics the social conduct of a spider. The technique deliberates the working principle of spiders concerning the biotic actions of cooperative groups. The SSO approach segregates the total population into numerous search agents, namely male and female spiders and adequately processes the specialized operators for each search agent. These operators aid the algorithm in trade-off the search process towards finding the optimal solutions. Initially, SSO was introduced to handle global optimization problems [20]. In later work, some researchers modified the generic SSO algorithm to solve binary optimization problems, namely clustering and classifications [21]. Further, the generic SSO algorithm has been utilized for several complex problems, namely constraint optimization problems [22], load balancing in a grid environment [23], clustering analysis [24], and multi-level thresholding problems [25].
The major highlights of this work are stated as follows;
-
Our proposed technique integrates the dynamic opposition-based learning technique into the social spider algorithm to enhance the exploration capability and to maximize the convergence rate.
-
This novel DOLSSO technique handles job scheduling issues in cloud environments. It enhances the diversity of scheduling solutions and reduces the local optimal struck.
-
Extensive experimentation was conducted using FogSim with two different test scenarios to validate the efficacy of the proposed system in handling the job scheduling problem.
-
The solution quality of the proposed algorithm is compared with five recent state-of-art meta-heuristic algorithms.
-
The results show that the proposed method achieves 10% - 15% better CPU utilization and 5%-10% less energy consumption than the other techniques.
The rest of the article is structured as Literature work section deliberates existing works in the literature on fog computing infrastructure for handling scheduling problems. The JSP in FOG computing section discusses the system prototype and Proposed methodology section presents the problem definition and shows a representation of the SSO algorithm to solve job scheduling problems, and Experimental analysis section illustrates the simulation analysis. Finally, Conclusion section concludes the work with its outcome and future directions.
Literature work
The scheduling issue is the sharing of present resources concerning the count of tasks/jobs. The JSP is a significant problem and complex, like the scheduling problem. The job scheduling problem on a heterogeneous system is considered an NP complex problem [26]. Graph partitioning strategy is adapted to balance the load in fog computing infrastructure [27]. The authors used dynamic graph partitioning for load balancing and cloud automation technology for building virtual machines. Data stream processing [28] is implemented in fog computing with QoS aware scheduler, and it will monitor incoming and outgoing data for node utilization and inter-node communication. Load balancing in fog computing creates an issue with the quality of experience [29]. The authors proposed a reduced task scheduling algorithm to process load balancing in fog computing. Based on the scheduling process, resources are allocated to serve fog nodes called small cells. Van den Boss et al. [30] focus on the cost-efficiently schedule based on deadline constraint heuristic on public and private clouds. The budget constraint schedule is implemented in the cloud environment and is based on the advantage of comparative methodology. This algorithm suits extensive scale networks due to its higher complexity [31].
In a standard JSP problem, there is the job block which determines the tasks and a block of physical systems with its resources [32]. In JSP, the general strategy is to process each job in the sequence of physical machines with the allocated resource constraints. However, allotted resource constraints are not sufficient in real-world situations. Economic factors and globalization force the IT industries to sustain by modifying single-standard facilities into multi-facility production. Hence, several researchers have started to perform their research on JSP, which is a much more perplexing problem and schedule jobs by minimizing production cost and computational time [33].
Based on recent research works, it is examined that several researchers have worked on single objective constraints such as reducing makespan. Further, in multi-objective restrictions such as reducing makespan, increasing workload, and overall power utilization of companies). Hongtao Tang et al. [34] introduced hybrid teaching and learning-based approach to solving the scattered and casting job scheduling issue. The author presented a three-layer coding method and five neighbourhood formations to handle the local search process in the algorithm. A real-time casting enterprise case study evaluates the algorithm’s performance. The observed results are compared with the six state-of-art metaheuristic algorithms to prove their efficacy. Hui Li et al. [35] proposed a hybrid differential evolution algorithm to tackle adaptable work planning by reevaluating tasks and job priority limitations. Chromosome encryption and decryption strategy are introduced to handle the real-time constraints and to attain a high-quality initial population. Further, genetic operators with self-adjusting conditions are incorporated to widen the search regions and increase the convergence rate.
SSO algorithm is a recently proposed metaheuristic algorithm that works based on the working principle of the social spider. Erik et al. [22] proposed an SSO algorithm to solve global continuous optimization problems. A robust clustering approach using SSO with a chaotic technique was presented in 2018 [36]. The literature review discussed above deliberates that few works are carried out to solve JSPs in fog computing using meta-heuristic techniques. In addition, none of the researchers has utilized the SSO algorithm in literature to handle the JSP issue. Hence, we introduced a novel discrete SSO to run JSP, and the outcome specifies that DOLSSO has attained a better result than existing methods.
The JSP in FOG computing
In this section, the overview of JSP is discussed with the set of jobs, sequences and challenges in JSP. Later, the system design for fog computing infrastructure is illustrated. In addition, the mathematical formulation of large-scale JSP is represented.
The overview of JSP
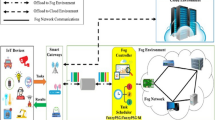
JSP is considered a significant scheduling issue that needs to process the sequence of jobs on the system or server by considering the number of constraints and objectives. A \(\mathcal{n}\times \ell\) JSP can be expressed as a set of \(\mathcal{n}\) jobs \(\psi =\left\{{\psi}_1,{\psi}_2,\dots, {\psi}_{\mathcal{n}}\right\}\) that is executed on a set of fog servers Υ = {Υ1, Υ2, …, Υℓ}. Each task ψi is expressed by order of \({\mathcal{n}}_i\) process \({P}_{ij}\left(j=1,2,\dots, {\mathcal{n}}_i\right)\) to be processed in a sequence completion order of jobs in a scheduled list. The challenge of JSP is to identify the adequate server for each process (known as Server selection) and the process execution order on the server (known as process ordering). According to the constraints of server election and job execution on one or more servers. The JSP is classified into three major classifications: JSP, partial-JSP and total-JSP. In JSP, the jobs are executed only on one elected server, whereas partial-JSP jobs can be performed on one or more partial machines. Finally, total-JSP is hugely flexible and can be implemented on any number of servers, as shown in Fig. 1.
System design
Fog computing infrastructure consists of \(\mathcal{n}\) number of the fog server machine. In our architecture, the cloud administrator is responsible for partitioning ψ job into T tasks. The decomposition of employment into the scheme is based on the number of available Fog server machines. We propose an SSO algorithm executed by the cloud administrator to ensure optimal scheduling in the Fog server.
Job scheduling is represented by a Directed Weight Graph (DWG); DWG is a weighted-node directed graph denoted by DWG = (T, E, F, μ, δ). T represents a set of tasks to be performed, and E indicates data dependencies among tasks. Let cloud consist of Υ set of Fog server, Υ = {Υ1, Υ2, …, Υℓ}. There are \(\mathcal{n}\) jobs submitted to schedule and executed by the Fog server. The jobs are portioned into tasks, and each assignment is apportioned to one fog server to schedule. Let Job ψ be partitioned into tasks and represented as \(\psi =\left\{{\psi}_1,{\psi}_2,\dots, {\psi}_{\mathcal{n}}\right\}\), where \(\mathcal{n}=\mid \textrm{Y}\mid .E\) represents the set of edges among nodes in T.
Definition 1
In DWG, assume any task can be processed on any Fog server machine in the formulated architecture. The numeral of edges in the graph is denoted by |E| ⊆ |Υ| × |T|. Each task Ti is processed on the Fog server machine concerning task execution time and allocated memory to process, and it is represented as, \({T}_i=\left[\begin{array}{c}{\mu}_i\\ {}{\delta}_i\end{array}\right]\). The CPU execution time of the task Ti on Fog, server is represented as μi. δi is used to represent allocated memory for the task Ti to perform.
Definition 2
In DWG, input for the graph is assigned using the Initialization Matrix (IG) IG = (Υi, j)n ∗ n. The initialization matrix consists of i task to be executed on j fog server machine. The element in the initialization matrix is one if the job is assigned to the fog server or else it is 0, and it can be represented as Υi, j ∈ 0, 1.
The objective of job scheduling is minimizing the total cost of execution time on processing tasks and, thus Optimal Scheduled Matrix (OG) is given as \({O}_G={\left(\begin{array}{c}{\textrm{Y}}_{i,j}\end{array}\right)}_{n\ast n}\).
The mathematical formulation of large-scale JSP
This section discusses the mathematical formulation of the large-scale job scheduling problem. Large-scale JSP is an extension of JSP in the number of jobs and machines. Therefore, Large scale JSP consists of the same mathematical model of JSPs. The constraints and objective functions of large-scale JSP are mathematically modelled and given as follows.
-
1)
Once the ith job of jth the task is assigned to the ℓth server, it cannot be interrupted until it completes its execution. Then, the Pij is computed as an additive of its initial time and handling time.
where, Cijℓ, Sijℓ and Eijℓ are denoted as culmination time, initial time and handling time of the jth task of the ith job Pij on server ℓ, respectively.
-
2)
The initial time of the ith job of jth task Pij on the server, ℓ is calculated based on the peak period of the earlier task μ on the server and the peak time of the earlier task.
-
3)
Server ℓ closes down when the last jobs are completed its execution.
where, Ψℓ denotes the shutdown time of the server ℓ, ϑ indicates the end job on sever ℓ, Ψϑℓ represents the peak time of the previous job on server ℓ.
-
4)
Some set of limitations on the server for the execution of the process. Thus, the constraints are specified below.
where n and m indicate the sequence of jobs and servers, respectively. Cωℓ, Eωℓ specifies the culmination time and handling time of job ω on server ℓ, Υ determines the sizeable positive integer. χiωℓ denotes the handling sequence priority of job i and job ω on server ℓ. If job i Is executed on the server ℓ then χiωℓ ∈ 1, otherwise 0.
-
5)
A single server suffers from handling more than one operation simultaneously.
where, Τijωtℓ denoted as whether the ith job of the jth task Pij is handled earlier than the tth task of the ωth job Pωt on server ℓ, if it is executed, then 1; otherwise, 0. Υij ∩ Υωt indicates the vacant server set that can able to handle the tasks Pij and Pωt simultaneously.
-
6)
When the task has numerous operations on a similar job, it is essential to process through the determined order.
where, φi denotes the numeral tasks of job i.
-
7)
When the server is scheduled, then the entire jobs can access at the initial time (S = 0)
-
8)
For each job, one server can be chosen for its execution.
where βijℓ represented as whether the server ℓ handles the job Pij, one deliberates the process is executing, 0 determines the process is not completed.
The objective of the JSP optimization problem incorporates max culmination time, max server load, min execution cost, etc. This work utilizes the max culmination time to ensure the proposed algorithm’s efficacy, which can be mathematically modelled as follows.
where Makespan denotes the max culmination time of all servers, it is the initial specification to calculate the handling efficacy. Ψℓ is mathematically expressed as.
Proposed methodology
This section discusses the overview of generic social spider optimization algorithm, the dynamic opposite learning concept and the formulation of the proposed algorithm.
Overview of social spider optimization algorithm
SSO algorithm mimics the foraging actions of vibration sense. The source of food is another social spider or prey on the web. The direction of the food source is erudite using vibration sense. The spider denotes a feasible solution in the SSO algorithm, and the web indicates search space. SSO consists of male and female agents; the female numeral individual is more significant than the male individual. The numeral female individual (Nf) and male individuals (Nm) are calculated using
where rand denotes the arbitrary function within the range of [0,1]; Np denotes the numeral populations; each spider receives weight Wi in population, Φ using fitness calculation. The weight was calculated using
The vibration sense Va, b on the web received by spider a and sent by spider b. da, b is the Euclidean distance, which can be calculated using
The cooperative behaviour of female agents is calculated using
where x, y, z, rl, rand are arbitrary values between [0,1], γ is the threshold value, t is the iteration number for nearest spider c, d. The cooperative behaviour of male agents is calculated using
where, \(\frac{\sum_{e=1}^{N_m}{m}_e(o).{W}_{N_{f+h}}}{\sum_{e=1}^{N_m}.{W}_{N_{f+h}}}\) denotes the weighted mean for the male population.

The dominant male and female agents are used for mating within radius r can be calculated using
where \({ub}_j^{high}\) and \({lb}_j^{low}\) are the upper and lower confines of the problem. The SSO algorithm is presented in algorithm 1.
Dynamic opposite learning method
The dynamic opposite learning method (DOL) is an extension of the opposition-based learning (OBL) method that is proposed by Xu et al. [37]. However, the OBL method can improve the quality of the algorithm towards optimal concerning the exploration of search space. But, determining the opposite position from the current situation is imminent. DOL is familiarized to advance the solution quality by eliminating the local optimal struck to eradicate the issue. The DOL is moreover similar to OBL by changing the opposite number Xo with Xro (i.e., Xro = rand . Xo, rand ∈ [0, 1]). The stable pursuit region can be modified into an unstable pursuit region trademarking the active change concerning arbitrary number.
Assumption
Let α denoted as the lower bound of the individual, λ denotes the upper bound of the individual. For instance, Xro, α and λ consist of two cases, namely Xro ∈ [α, λ] and Xro ∉ [α, λ]. The individual Xro, Xo and X consist of three associations such as 1) Xro between Xo and X 2) Xro is larger than Xo and 3) Xro is minimum than X.
The dynamic opposite number Xdo can be regenerated when Xdo ∉ [α, λ]. At the same time, if Xro is exceed the upper and lower bound due to the below Eq. (21).
The mathematical model of DOL concerning the dynamic opposite number and the active opposite point is expressed as follows.
Dynamic opposite value
It is considered to determine the step-by-step process of DOL. The mathematical model of Xdo can be expressed in Eq. (22).
where, r1 and r2 denoted as arbitrary values with the bound of [0,1]; z indicates the learning weight value; X represented as the actual number with the range of [α, λ].
Dynamic opposite point: The expansion of positive contradictory value in the various dimensional search point. The mathematical model of the active opposite end can be expressed in Eq. (24).
where, D determines the D-dimensional space that incorporates various possible individuals; X specifies the present individual with D-dimensional space (i.e., X = {X1, X2, …, XD} are limited to upper (i.e., λ = {λ1, λ2, …, λD} and lower α = {α1, α2, …, αD} bound; r3 and r4 are indicates the arbitrary values with the range of [0,1].
The DOL method is incorporated into the beginning and rehearsal of the SSO population. In the initialization process, the opposite population Φdo is generated by the population Φ (i.e., Φdo ∪ Φ). Then, the fitness of the population Φdo ∪ Φ is computed and picks the half set of individuals to the population ΦS. In the generation process, if the hopping process gratifies, it produces the Φdo by ΦS and process the whole population as Φdo ∪ ΦS, then compute the fitness of Φdo ∪ ΦS and repeat the process until the process completes. If the solution of Φdo, ΦS and Φ exceeds the boundary, then regenerate the individual within the upper and lower limit.
DOL-based SSO algorithm
In this part, we proposed a novel variant of SSO, namely DOLSSO, to enhance the standard SSO algorithm to handle the precocity that constantly riddles several optimization techniques.
Population initialization based on DOL
The opposite solutions based on DOL are generated from the set of the first half of present individuals. The DOL population is processed with the SSO population initialization method. The mathematical model is expressed as follows.
where, Φij indicates the jth dimension of ith the solution in population created by SSO, r1, i and r2, i are two arbitrary values within the range of [0,1], λj and αj specifies the upper and lower boundary of jth dimension of ith solution \({\Phi}_{ij}^{do}\), determines the opposite individual of Φij. The DOL population initialization \({\Phi}_{ij}^{do}\) should satisfy the boundary region as per Eq. (27).
where RN indicates the arbitrary values within the limit of [αj, λj].
Generation hopping based on DOL
DOL iteration hopping is analogous to the DOL population initialization process. This DOL iteration hopping strategy can be processed into whole generation to aid the algorithm to eradicate from local optimal struck. The hopping rate of the DOL method is represented by δ ∈ [0, 1] to determine the probability of the technique according to the hop rate. If the arbitrary value produced is minimal than the hopping rate factor δ, DOL process the hopping action. The mathematical model of the hopping process is expressed as follows.
where z denotes the learning weight that differs concerning various scenarios and conditions, r3, i and r4, i are the two arbitrary values within the range of [0,1].
DOLSSO algorithm
As discussed earlier, DOLSSO is the modified version of SSO that includes the DOL method in standard SSO. The SSO algorithm is given in algorithm 1, and the DOL method is discussed in Dynamic opposite learning method section. The procedure of DOLSSO is presented in algorithm 2, and the workflow of DOLSSO is sketched in Fig. 2.

Decoding and encoding for JSP
A wide variety of strategies are available to encode and decode the JSP. Gao et al. [38] introduced one of the most popular strategies, including server selection and process ordering vectors. Although the strategy provides better results for some scenarios, its representation of individuals increases memory utilisation. In this work, we utilized the encoding and decoding strategy from the reference [37].
Exploration and exploitation analysis
We utilized the hopping rate factor (δ) in the proposed system to trade off the exploration and exploitation process. The individual that satisfies the hopping element then the current individual will undergo the exploration process using the DOL method. Otherwise, the individual utilizes the SSO method to exploit the search space. Therefore, we use δ with the fixed values of 0.5 to determine the solution update process. The DOLSSO algorithm initiates with a set of random solutions. At each generation, search individuals update their positions concerning randomly selected search agents, or the best individual found so far. Depending on the hopping factor δ, the proposed algorithm can switch between the exploration and exploitation processes. Finally, the DOLSSO is terminated by the fulfilment of a stop criterion.
Experimental analysis
The experimentation setup and evaluation of results are performed to ensure the effectiveness of the projected system. Later, the obtained outcome of the introduced model is compared with five state-of-art existing metaheuristic algorithms. We have utilized the FogSim simulator in this scheduling to generate the dataset. An energy-efficient open-source tool is used for modelling and simulating resource management in fog/edge computing. The FogSim is integrated with CloudSim to deal with the actions between fog computing environments. In CloudSim, different parameters, like data centres, use communication processes for transmission.
Parameter settings
The performance of the SSO algorithm on solving job scheduling is coded using FogSim with CloudSim under Windows 10 on an Intel i5 processor with 3.4GHz and 16GB RAM. The empirical result is compared with other state-of-art metaheuristic algorithms, namely Social Spider Optimization (SSO) [22], grasshopper optimization algorithm (GOA) [39], Salp swarm algorithm (SSA) [40], Grey Wolf Optimization (GWO) [41], and Whale Optimization Algorithm (WOA) [42]. For all experimentation algorithms, the population size, maximum iterations and number of runs are fixed as 60, 100 and 20, respectively. The simulation parameters utilized for this experimentation is illustrated in Table 1.
Result analysis
The dataset is generated with the aid of a FogSim-based simulation tool. All the proposed and compared algorithms are iterated for 100 epochs for each test case with varying tasks, and obtained results are graphically plotted. Further, we experimented on two test cases concerning the number of processors and fog nodes. For the first case, the number of processors varies from 4, 8, 12, 16, 20, and 24 with 20, 40, 80, 160, 320 and 400 tasks, respectively. Each task is allocated to an adequate number of fog servers, and processing orders are determined by solution representation as specified in DOL-based SSO algorithm section. For the second case, the number of fog nodes varies from 5, 10, 15 and 20 with respect to different jobs.
Case 1: experimentation based on the number of processors
In the first case, we have created varying numbers of processors with various tasks. The experimentation results are measured, and the introduced model is contrasted with five metaheuristic algorithms: GOA, SSA, GWO, WOA and SSO. Figure 3 determines the average resource utilization concerning the number of processors. Figure 3 shows that the proposed DOL-SSP algorithm provides better than GOA, SSA, GWO, WOA and SSO. The standard SSA algorithm competes with the proposed algorithm but fails during iterations. At the same time, the proposed DOL-SSO algorithm utilizes the processors effectively by allocating adequate tasks to the available machines. GWO and WOA algorithm provides moreover similar results in resource utilization. Overall, average resource utilization by DOLSSO was improved on average by 12% more than the standard SSA algorithm.
The average energy depletion ratio concerning the number of processors is represented in Fig. 4. In this experimentation, achieving a lower energy consumption ratio specifies the algorithm hoards the energy and provides better performance. Based on Fig. 4, we noticed that the introduced model gives significant outcomes to all numbers of processors except eight processors compared to other algorithms. Moreover, GWO and SSA provide similar results and attain more energy consumption ratio, which offers less performance than the proposed method. The standard SSO algorithm and the proposed algorithm achieve the same results due to the random initialization of populations. Also, several ways consume more energy than the proposed algorithm. Though the proposed algorithm attains the same output in 8 processors, the resources are more effectively utilized than the standard SSO algorithm.
Case 2: experimentation based on the number of fog nodes
The efficacy of the proposed model on fog computing scenarios is validated by varying fog nodes from 5 to 20 with a varying number of jobs. CPU clock rate and allocated memory for heterogeneous nodes are taken from [43]. We have considered four cases of fog nodes; the maximum number of iterations is 8000 in all test cases with 20 runs. The introduced model is contrasted with five existing metaheuristic algorithms like GOA, SSA, GWO, WOA and SSO. For evaluation, two performance metrics are utilized: execution time and allocated memory for jobs with respect to completion time. Once the server is distributed with a specific number of jobs, it is locked until it completes its execution. The experimentation of execution time for various jobs concerning fog nodes is observed in Table 2. The execution time for jobs is illustrated in Fig. 5. The table and Fig. 5 clearly show that the introduced model provides improved results concerning minimum execution time than the other compared algorithms.
The allocated memory for jobs concerning the number of fog nodes is observed in Table 2. The pictorial representation of allocated memory for jobs is illustrated in Fig. 6. As observed from the results, Table 3 and Fig. 6 specifies that the concert of the DOLSSO method outperforms well than compared algorithms. The maximum allocated memory concerning 20 fog nodes for various determined jobs attained by DOLSSO (2.6 GB) is lesser than the standard SSO (2.9 GB). In addition, allocated memory for jobs achieved by GWO (2.8 GB) and SSO (2.9 GB) are closer. Based on the experimentation results, incorporating the DOL strategy into SSO improves performance by eradicating local optimal struck and a better convergence rate.
Conclusion
In the last few years, fog computing has given great attention to researchers, industrialists and the community due to its computational services. We addressed the job scheduling issue in the fog computing setting with reduced CPU time utilization and memory usage. This work introduces a novel version of the SSO method by incorporating the dynamic opposition learning (DOL) approach, namely the DOLSSO algorithm. The proposed model enriches the solution quality by eradicating the local optimal struck and boosting the convergence rate towards the optimal solution. The experimentation is carried out in the FogSim simulation tool with two different scenarios. The first scenario pacts with several processors concerning the number of tasks, and the second test case deals with the number of fog nodes concerning the number of jobs. The proposed infrastructure guarantees the execution of the data request and satisfies mobile users effectively using the DOLSSO algorithm. The empirical result shows the algorithm’s effectiveness in obtaining an optimal schedule in a Fog computing environment. The results show that the proposed method achieves ~ 10% - 15% better CPU utilization and ~ 5%-10% less energy consumption than other algorithms. Further, this work can be extended to handle the multi-objective flexible job scheduling issue by incorporating self-adaptive parameters into the DOLSSO algorithm.
Availability of data and materials
The data that support the findings of this study are available from the first author upon reasonable request.
References
Buyya R, Yeo CS, Venugopal S, Broberg J, Brandic I (2009) Cloud computing and emerging IT platforms: vision, hype, and reality for delivering computing as the 5th utility. Futur Gener Comput Syst 25(6):599–616
Eleyan A, Eleyan D (2015) Forensic process as a service (FPaaS) for cloud computing. In: Intelligence and security informatics conference (EISIC), 2015 European. IEEE, pp 157–160
The Network.Cisco Delivers Vision of Fog Computing to Accelerate Value from Billions of Connected Devices. http://newsroom.cisco.com/press-release-content?articleId=1334100.M
Deng R, Rongxing L, Lai C, Luan TH, Liang H (2016) Optimal workload allocation in fog-cloud computing toward balanced delay and power consumption. IEEE Internet Things J 3(6):1171–1181
Şahman MA (2021) A discrete spotted hyena optimizer for solving distributed job shop scheduling problems. Appl Soft Comput 106:107349
Naderi B, Azab A (2014) Modeling and heuristics for scheduling of distributed job shops. Expert Syst Appl 41(17):7754–7763
Gao J, Chen R (2011) A hybrid genetic algorithm for the distributed permutation flowshop scheduling problem. Int J Comput Intell Syst 4(4):497–508
Xie J, Gao L, Pan Q-k, Fatih Tasgetiren M (2019) An effective multi-objective artificial bee colony algorithm for energy efficient distributed job shop scheduling. Proc Manufact 39:1194–1203
Lei D (2008) Pareto archive particle swarm optimization for multi-objective fuzzy job shop scheduling problems. Int J Adv Manuf Technol 37(1):157–165
Rossi A, Dini G (2007) Flexible job-shop scheduling with routing flexibility and separable setup times using ant colony optimisation method. Robot Comput Integr Manuf 23(5):503–516
Singh S, Kurmi J, Tiwari SP (2015) A hybrid genetic and cuckoo search algorithm for job scheduling. Int J Sci Res Publ 5(6):1–4
Wang L, Pan Q-K, Suganthan PN, Wang W-H, Wang Y-M (2010) A novel hybrid discrete differential evolution algorithm for blocking flow shop scheduling problems. Comput Oper Res 37(3):509–520
Lu C, Gao L, Pan Q, Li X, Zheng J (2019) A multi-objective cellular grey wolf optimizer for hybrid flowshop scheduling problem considering noise pollution. Appl Soft Comput 75:728–749
Liu M, Yao X, Li Y (2020) Hybrid whale optimization algorithm enhanced with Lévy flight and differential evolution for job shop scheduling problems. Appl Soft Comput 87:105954
Atay Y, Kodaz H (2014) Implementation of CSA with clone-mutation mechanism to the JSSP. Int J Mach Learn Comput 4(1):6
Bezdan T, Zivkovic M, Antonijevic M, Zivkovic T, Bacanin N (2021) Enhanced flower pollination algorithm for task scheduling in cloud computing environment. In: Machine learning for predictive analysis. Springer, Singapore, pp 163–171
Yadav AM, Tripathi KN, Sharma SC (2022) A bi-objective task scheduling approach in fog computing using hybrid fireworks algorithm. J Supercomput 78(3):4236–4260
Najafizadeh A, Salajegheh A, Rahmani AM, Sahafi A (2022) Multi-objective task scheduling in cloud-fog computing using goal programming approach. Clust Comput 25(1):141–165
Wu X, Shen X, Zhao N, Shaomin W (2020) An improved discrete pigeon-inspired optimisation algorithm for flexible job shop scheduling problem. Int J Bio-Inspir Comput 16(3):181–194
Cuevas E, Cienfuegos M, Zaldívar D, Pérez-Cisneros M (2013) A swarm optimization algorithm inspired in the behavior of the social-spider. Expert Syst Appl 40(16):6374–6384
Baş E, Ülker E (2020) A binary social spider algorithm for continuous optimization task. Soft Comput 24(17):12953–12979
Cuevas E, Cienfuegos M (2014) A new algorithm inspired in the behavior of the social-spider for constrained optimization. Expert Syst Appl 41(2):412–425
Mahato DP, Singh RS (2018) On maximizing reliability of grid transaction processing system considering balanced task allocation using social spider optimization. Swarm Evol Comput 38:202–217
Zhou Y, Zhou Y, Luo Q, Abdel-Basset M (2017) A simplex method-based social spider optimization algorithm for clustering analysis. Eng Appl Artif Intell 64:67–82
Ouadfel S, Taleb-Ahmed A (2016) Social spiders’ optimization and flower pollination algorithm for multi-level image thresholding: a performance study. Expert Syst Appl 55:566–584
Shao Z, Zhuge Q, Xue C, Sha EH-M (2005) Efficient assignment and scheduling for heterogeneous dsp systems. IEEE Trans Parallel Distrib Syst 16(6):516–525
Ningning S, Chao G, Xingshuo A, Qiang Z (2016) Fog computing dynamic load balancing mechanism based on graph repartitioning. China Commun 13(3):156–164
Cardellini V, Grassi V, Presti FL, Nardelli M (2015) On QoS-aware scheduling of data stream applications over fog computing infrastructures. In: Computers and communication (ISCC), 2015 IEEE symposium on. IEEE, Larnaca, p 271–76.
Oueis J, Strinati EC, Barbarossa S (2015) The fog balancing: load distribution for small cell cloud computing. In: Vehicular technology conference (VTC spring), 2015 IEEE 81st. IEEE, Glasgow, p 1–6.
den Bossche V, Ruben KV, Broeckhove J (2011) Cost-efficient scheduling heuristics for deadline constrained workloads on hybrid clouds. In: Cloud computing technology and science (CloudCom), 2011 IEEE third international conference on. IEEE, Athens, p 320–27.
Zeng L, Veeravalli B, Li X (2012) Scalestar: budget conscious scheduling precedence-constrained many-task workflow applications in cloud. In: Advanced information networking and applications (AINA), 2012 IEEE 26th international conference on. IEEE, Fukuoka, p 534–41.
Fleming PJ, Zalzala AMS (editor) (1997) Genetic algorithms in engineering systems. Institution of Electrical Engineers, Herts
Naderi B, Azab A (2015) An improved model and novel simulated annealing for distributed job shop problems. Int J Adv Manuf Technol 81(1):693–703
Tang H, Fang B, Liu R, Li Y, Guo S (2022) A hybrid teaching and learning-based optimization algorithm for distributed sand-casting job-shop scheduling problem. Appl Soft Comput 120:108694
Li H, Wang X, Peng J (2022) A hybrid differential evolution algorithm for flexible job shop scheduling with outsourcing operations and job priority constraints, Expert Systems with Applications, p 117182, ISSN 0957-4174. https://doi.org/10.1016/j.eswa.2022.117182
Aggarwal S, Chatterjee P, Bhagat RP, Purbey KK, Nanda SJ (2018) A social spider optimization algorithm with chaotic initialization for robust clustering. Proc Comput Sci 143:450–457
Xu Y, Yang Z, Li X, Kang H, Yang X (2020) Dynamic opposite learning enhanced teaching–learning-based optimization. Knowl-Based Syst 5(188):104966
Zhang G, Gao L, Shi Y (2011) An effective genetic algorithm for the flexible job-shop scheduling problem. Expert Syst Appl 38(4):3563–3573
Saremi S, Mirjalili S, Lewis A (2017) Grasshopper optimisation algorithm: theory and application. Adv Eng Softw 105:30–47
Mirjalili S, Gandomi AH, Mirjalili SZ, Saremi S, Faris H, Mirjalili SM (2017) Salp swarm algorithm: a bio-inspired optimizer for engineering design problems. Adv Eng Softw 114:163–191
Natesan G, Chokkalingam A (2019) Task scheduling in heterogeneous cloud environment using mean grey wolf optimization algorithm. ICT Express 5(2):110–114
Jiang T, Zhang C, Zhu H, Jiuchun G, Deng G (2018) Energy-efficient scheduling for a job shop using an improved whale optimization algorithm. Mathematics 6(11):220
Bitam S, Zeadally S, Mellouk A (2017) Fog computing job scheduling optimization based on bees swarm. Enterp Inf Syst 12,(4):1–25.
Acknowledgements
This research was supported by the Taif University Researchers Supporting Project number (TURSP-2020/231), Taif University, Taif, Saudi Arabia.
Funding
Researchers Supporting Project number (TURSP-2020/231), Taif University, Taif, Saudi Arabia.
Author information
Authors and Affiliations
Contributions
Conceptualization - Kuppusamy P; methodology- Kuppusamy P, N. Marline Joys Kumari; validation- Rajakumar Ramalingam, Mamoon Rashid, Abdul Rehman Javed; formal analysis- Wael Y. Alghamdi, Hashem Alyami; writing—original draft preparation- Kuppusamy P; writing—review and editing- Mamoon Rashid, Abdul Rehman Javed; supervision- Rajakumar Ramalingam; funding acquisition- Wael Y. Alghamdi. All authors have read and agreed to the submitted version of the manuscript.
Corresponding author
Ethics declarations
Ethics approval and consent to participate
Not applicable.
Competing interests
The authors declare no conflict of interest.
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article's Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article's Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Kuppusamy, P., Kumari, N.M.J., Alghamdi, W.Y. et al. Job scheduling problem in fog-cloud-based environment using reinforced social spider optimization. J Cloud Comp 11, 99 (2022). https://doi.org/10.1186/s13677-022-00380-9
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13677-022-00380-9