Abstract
Simultaneous transmission and reflection reconfigurable intelligent surface (Star-RIS) has been recently introduced as one of the hopeful technologies in future communications. In this work, we investigate a beamforming design for Star-RIS-assisted secure wireless communications with two practical protocols, namely energy splitting (ES) and mode switching (MS). We assume that our transceivers are not ideal and have residual hardware impairments that lead to distortion noise. We aim to maximize the total secrecy rate by optimizing the beamforming in BS and Star-RIS under the limitation of transmission power consumption. The proposed non-convex optimization problem is solved via successive convex approximation and alternating optimization.
Similar content being viewed by others
1 Introduction
Recently, reconfigurable intelligent surface (RIS) is a potential technique to create dynamic and adaptable wireless radio propagation [1,2,3,4,5]. The low-cost RIS structure comprises multiple passive elements, which are smaller in size than the wavelength of the signal. RIS can be set up at critical sites such as building exteriors and highway poles, advertising displays, and car windows [6,7,8,9]. Every passive element of RIS can dynamically modify channels, either constructively or destructively, by changing the amplitude and phase shift of the radiated signal. So, RIS makes the wireless environment intelligent. In other words, by properly designing optimal RIS coefficients, signal beams can be configured to achieve diverse goals, including increasing the throughput of specific terminals, eliminating interference from other devices, or mitigating information leakage to potential eavesdroppers [10,11,12,13]. Considering the mentioned features of RIS result overcoming signal attenuation, more energy efficiency, improving spectral efficiency and data rates, and flexibility in network design, which is particularly valuable in dynamic environments with changing user requirements and network conditions.
A recently introduced type of RIS, the simultaneous transmission and reflection RIS (Star-RIS), has been announced. It can make full spatial coverage by simultaneously reflecting signals in front of the Star-RIS and transmitting behind it. In other words, the incoming signal is divided into two components referred to as the transmitted and reflected signals. So, Star-RIS can overcome the conventional RIS limitation, which achieves only half-space coverage because of the reflecting signal. Also, simultaneous control of transmitted and reflected signals enables more degrees-of-freedom than conventional RIS [14,15,16,17,18,19].
However, the security of wireless networks is a significant aspect. RIS can enhance the secrecy performance by dynamically adjusting wireless channels due to emitting waves constructively or destructively in proportion to system goals such as reducing leakage of information to eavesdroppers and enhancing the security rate [20,21,22,23,24]. The authors in [25] studied Star-RIS and UAV assisted secure communication in which optimized transmission beamforming vector consists of information and artificial noise components, RIS phase shift, and UAV trajectory to maximize the total secrecy rate. Existing work in [26] studied a secure communication system based on Star-RIS and AN. [27] investigated a Star-RIS-aided NOMA secure communication to guarantee full space secure transmission based on ES, MS, and TS. The authors in [28] investigated beamforming for Star-RIS-aided uplink NOMA secrecy communication by considering imperfect CSI for eavesdroppers and show performance improvement with the aide of Star-RIS compared to conventional RIS. The existing work in [29] studied secure communication assisted by Star-RIS-aided SWIPT and RSMA techniques. Also, a secure NOMA communication aided by Star-RIS, is studied in [30,31,32,33].
In practical scenarios, physical transceivers experience inherent hardware impairments, which cause distortions in both transmitted and received signals, with the ratio proportional to the transmitted and received signal power, unlike receiver noise, which is only added to the received signal and is independent of the signal. [34, 35]. Based on research findings, the distortion noise is modeled as an additive Gaussian distribution with variance proportional to the signal power [36]. In [37, 38], the authors studied the RSMA-assisted MIMO Star-RIS communication system while considering hardware impairments. [39] investigated the ergodic achievable rate of an uplink NOMA communication system with the assistance of Star-RIS by considering imperfect CSI and transceiver hardware impairments. The author in [40] investigated Star-RIS NOMA downlink communication under phase error and transceiver hardware impairment.
As shown in Table 1, few works have been devoted to Star-RIS assisted communication under hardware impairments [37,38,39,40,41]. The existing work in [37] investigates RSMA in MIMO RIS communication system and assumes that the transceivers may suffer from hardware imperfections such as I/Q imbalance, which arise due to mismatches in amplitude and phase between the in-phase and quadrature components transformation. It demonstrates that Star-RIS with MS improves the fairness rate, outperforming regular RIS. Also, the authors in [38] studied the spectral efficiency of a MIMO broadcast channel with transceiver I/Q imbalance and showed that Star-RIS outperforms RIS in fairness rate based on ES and MS protocols. [37, 38] proposed an optimization solution via majorization and minimization approaches and did not demonstrate the impact of the number of RIS elements and BS antennas on the performance. Authors in [39] have studied NOMA uplink communication assisted by Star-RIS. Firstly, they estimated the equivalent channel from user to BS using the LMMSE and then theoretically calculated ergodic sum rate by considering channel estimation errors and hardware impairments. They demonstrate saturation of the channel estimation and the ergodic sum rate by increasing transmit power due to distortion noise caused by hardware impairments. In [40], the ergodic rate behavior of Star-RIS assisted NOMA communications is evaluated based on MS protocol for Star-RIS under phase error and hardware impairment. It shows the degrading impact of hardware impairment on the ergodic sum rate and performance improvement by increasing transmission power and the number of RIS elements. The existing work in [41] minimized transmitted power consumption by optimizing active and passive beamforming in a symbiotic radio communication assisted by active Star-RIS under hardware impairments.
As a result of the above discussions based on Table 1, although the efforts in [37,38,39,40,41] studied the Star-RIS Communication under hardware impairments, the critical issue of secrecy communication has not been analyzed yet and remains an open issue. Also, none of them investigated the downlink achievable rate in the presence of Gaussian distortion noise for hardware impairment. We optimize active and passive beamforming based on Star-RIS ES and MS protocols to maximize the total secrecy rate under the constraints of limited transmission power consumption and hardware imperfections of BS and legitimate users. The proposed non-convex problem is solved by alternating optimization methods with semi-definite relaxation, successive convex approximation, penalty concave–convex procedure techniques, and slack variables. Our results show that Star-RIS outperforms conventional RIS and No-RIS in terms of performance. Between Star-RIS protocols, ES has higher performance than MS. The total secrecy rate increases by increasing the number of Star-RIS elements and BS antennas, but it saturates due to distortion noise caused by hardware impairments. A higher transceiver hardware impairment level leads to decreasing SSR, and the impact of receiver hardware impairment level is higher than transmitter hardware impairment level to decrease the SSR.
Notation: This paper uses the following mathematical notations and symbols. Boldface uppercase and lowercase demonstrate matrices and vectors, respectively. We use \({{\textbf{X}}^\mathrm{{*}}}\), \({{\textbf{X}}^\mathrm{{T}}}\), \({{\textbf{X}}^\mathrm{{H}}}\), \(\left\| {\textbf{X}} \right\| _2^2\) to represent conjugate, transpose, hermitian, and Frobenius norm of \({\textbf{X}}\), respectively. \(\mathrm{{Diag}}({\textbf{x}})\) demonstrates a diagonal matrix that \({\textbf{x}}\) is on its main diagonal. \(\mathrm{{diag}}({\textbf{X}})\) is a vector consists of main diagonal of \({\textbf{X}}\). \({\widetilde{Diag}}({\mathbf{X}})\) is a diagonal matrix with diagonal elements the same as the \(\textbf{X}\). \({[{\textbf{x}}]_m}\) is the \({m_{th}}\) element of vector \({\textbf{x}}\). \({\textbf{X}}\mathop \succ \limits _ - 0\) shows a positive semi-definite matrix. \({{\mathbb {C}}^{M \times N}}\) denotes complex value matrices space. \({{\mathcal {C}}}{{\mathcal {N}}}(\mu ,{\hspace{0.55542pt}} {\sigma ^2})\) shows complex Gaussian random variables with mean of \(\mu\) and variance of \({\sigma ^2}\).
2 Methods/experimental
The first part of this section explains the studied system model, and the second and third parts demonstrate the channel and signal model. Then, we explain the problem formulation for ES protocol and solve the problem for MS protocol. At the end of this part, we propose convergence and complexity analysis.
2.1 System model
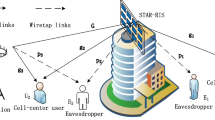
As shown in Fig. 1 , we study a Star-RIS assisted secure communications consisting of an N-antenna transmitter, a Star-RIS with M elements, two single-antenna eavesdroppers, and two legitimate receivers. Star-RIS has established two separate spaces within the spatial vicinity of itself. The initial space, denoted as the ’R space’, is where the reflected signal from RIS is directed back into the same space as the incident signal and the opposite space, referred to as ’T space’, away from the incident signal source and the transmitter. Star-RIS concurrently can serve both ’T’ and ’R’ spaces. The receiver and eavesdropper in the i-th space are the i-th receiver and i-th eavesdropper. Every element of Star-RIS transmits and reflects signal \({p_m} = \sqrt{\beta _m^p} {e^{j\phi _m^p}}{s_m}\), based on changing amplitude and phase shift of incident signal (\({s_m}\)), which \(\sqrt{\beta _m^p} \in [0,1]\) and \(\phi _m^p \in [0,2\pi )\) are the amplitude and phase shift of the m-th element of Star-RIS, \(p = r\) and \(p = t\) specify reflection or transmission mode. It should be noted that the \(\phi _m^r\) and \(\phi _m^t\) in each element are independent of each other, but \(\sqrt{\beta _m^r}\) and \(\sqrt{\beta _m^t}\) due to the conservation of energy principle should satisfy \({\left| {{t_m}} \right| ^2} + {\left| {{r_m}} \right| ^2} = {\left| {{s_m}} \right| ^2}\) that leads to \(\beta _m^r + \beta _m^t = 1\), which means that the total energy of the radiated signal on an element should be equal to the sum of the energies of signals in both T and R modes [42].
We employ ES and MS in the proposed problem. In ES, each element should operate in both T and R modes, and the ratio of transmitted energy at mode T to mode R is \(\beta _m^t:\beta _m^r\). So, the ES mode has the highest degree of freedom among other methods due to design transmission and reflection coefficients simultaneously, which are modeled as
where \(p = r\) and \(p = t\) specify the reflection or transmission coefficient, respectively, and \(\phi _m^p \in [0,2\pi )\), \(\sqrt{\beta _m^p} \in [0,1]\), \(\beta _m^t + \beta _m^r = 1\), \(m \in M \buildrel \Delta \over = \{ \mathrm{{1}},\mathrm{{2}},\ldots ,\mathrm{{M}}\}\) [43].
In MS mode, all elements of Star-RIS form two sets of \({M_t}\) and \({M_r}\) elements work in T and R modes, respectively, where \({M_t} + {M_r} = M\). In other words, MS mode is a particular case of ES mode with binary amplitude of the coefficients, which leads to lower degrees of freedom than ES. The MS transmission and reflection coefficients are modeled as
where \(p = r\) and \(p = t\) specify the reflection and transmission coefficient, respectively, and \(\phi _m^p \in [0,2\pi )\), \(\sqrt{\beta _m^p} \in \{ 0,1\}\), \(m \in M \buildrel \Delta \over = \{ \mathrm{{1}},\mathrm{{2}},\ldots ,\mathrm{{M}}\}\) [43].
2.2 Channel model
Let \(\textbf{h}_i^H \in {{\mathbb {C}}^{1 \times N}}\), \(\textbf{g}_i^H \in {{\mathbb {C}}^{1 \times N}}\), \(\textbf{v}_i^\mathrm{{H}} \in {{\mathbb {C}}^{1 \times M}}\), \(\textbf{r}_i^\mathrm{{H}} \in {{\mathbb {C}}^{1 \times M}}\), and \({\textbf{G}} \in {{\mathbb {C}}^{M \times N}}\) denote the channels corresponding to communication paths from BS to i-th legitimate receiver, BS to i-th eavesdropper, RIS to i-th legitimate receiver, RIS to i-th eavesdropper, and BS to RIS, respectively, where \(i \in \{ t,r\}\). It is assumed that the perfect CSI of these links is known at the BS, and all channels are independent quasi-static block fading. Let, \(\textbf{h}_i\), and \({\textbf{g}}_i\) are Rayleigh fading, \(\textbf{G}\), \({\textbf{v}}_i\), and \({\textbf{r}}_i\) follow Rician distribution with Rician factor k, in which \({{\textbf{G}}^{\text{{LoS}}}}\), \({{\textbf{v}}_i^{\text{{LoS}}}}\) and \({{\textbf{r}}_i^{\text{{LoS}}}}\) are modeled by the product of steering vector of receiver and transmitter in each channel while \({\textbf{v}}_i^\mathrm{{NLoS}}\), \({\textbf{r}}_i^\mathrm{{NLoS}}\), \({\textbf{G}^\mathrm{{NLoS}}}\) follow Rayleigh distribution. These channels are expressed as
Where, \({\rho _0}\) is the path loss at the reference distance of 1 m. The symbols \({d_{BS - RIS}}\), \({d_{RIS - U_i}}\), \({d_{RIS - E_i}}\), \({d_{BS - U_i}}\), and \({d_{BS - E_i}}\) indicate distances between BS and RIS, RIS and i-th user, RIS and i-th eavesdropper, BS and i-th user, BS and i-th eavesdropper, respectively. \(\alpha \ge 2\) represents the path loss exponent.
2.3 Signal model
The BS simultaneously broadcasts the signal to Star-RIS and two legitimate users, placed in reflection and transmission regions where an eavesdropper attempts to wiretap the signal in each region. Furthermore, Star-RIS conveys signals to legitimate users. Since, in a practical scenario, the transmitter and receiver experience inherent hardware impairments, we suppose that BS and legitimate receivers suffer from residual hardware impairments. We consider direct and indirect links from BS to legitimate receivers, and eavesdroppers. Let \(s\sim {{\mathcal {C}}}{{\mathcal {N}}}(0,{\hspace{0.55542pt}} 1)\) as the transmitted signal, \({\textbf{w}} \in {{\mathbb {C}}^{N \times 1}}\) as active beamforming vector, \({{\textbf{m}}_T} \in {{\mathbb {C}}^{N \times 1}}\) as independent Gaussian transmit distortion noise with power distortion \({{\textbf{m}}_T} \sim {{\mathcal {C}}}{{\mathcal {N}}}(0,{\mu _t}{\widetilde{Diag}}({\textbf{w}}{{\textbf{w}}^H}))\) by ratio of \({\mu _t} \ge 0\) to transmitted signal power due to BS hardware impairment. So, BS transmits the signal as below
then received baseband signals at legitimate users and eavesdroppers are calculated as below
where \({m_i}\) is an independent Gaussian distortion noise at i-th legal receiver with distribution of \({{\mathcal {C}}}{{\mathcal {N}}}(0,{\mu _r}\{ |{y_i} - {m_i}{|^2}\} )\) by the ratio of \({\mu _r} \ge 0\) to received signal power. The additive white Gaussian noises (AWGN) at each receiver and eavesdropper are represented by \({n_i}\), and \({n_{{e_i}}}\), respectively, with mean of zero and variance of \(\sigma _i^2\) and \(\sigma _e^2\) where \({n_i}\sim {{\mathcal {C}}}{{\mathcal {N}}}(0,{\hspace{0.55542pt}} \sigma _i^2)\) and \({n_{{e_i}}}\sim {{\mathcal {C}}}{{\mathcal {N}}}(0,{\hspace{0.55542pt}} \sigma _e^2)\).
BS feeds back Star-RIS’s coefficients to the RIS controller through dedicated feedback channels. Let \({{\varvec{\theta }}_i} = diag({{\mathbf {\Phi }}_i}) \in {{\mathbb {C}}^{M \times 1}}\) and convert to \({{\varvec{\theta }}_i} = [{{\varvec{\theta }}_i};1] \in {{\mathbb {C}}^{(M + 1) \times 1}}\), then the equivalent channels from RIS to users and eavesdroppers i.e. \(\{{{\textbf{H}}_i}, {{\textbf{F}}_i}\} \in {{\mathbb {C}}^{(M + 1) \times N}}\) are formulated by
then the Eqs. 9 and 10 can be rewritten as below
then, the data rate that can be attained at user i is modeled as
with using \({y^H}{\widetilde{\mathrm{{Diag}}}}(x{x^H})y = {x^H}{\widetilde{\mathrm{{Diag}}}}(y{y^H})x\), Eq. 15 is rewritten as below
and the data rate that can be attained at Eve i is provided by
2.4 Problem formulation
In this part, we design optimized active beamforming and transmission and reflection beamforming based on ES protocol to maximize the total secrecy rate under the impact of transmitter and legitimate receivers hardware impairments subject to limited transmission power. Our objective is to solve the subsequent problem mathematically
Constraint 18b denotes the limited transmission power consumption, and constraint 18c is added due to the ES coefficient. Problem 18 is not-convex due to non-concave objective function 18a and non-convex ES coefficient constraint 18c.
To solve problem 18, the SCA method is implemented, which converges to a local solution [44] and alternating optimization that converts the proposed problem into convex sub-problems, which is solved via conventional optimization tools like CVX. So, we solve the proposed problem based on optimizing \({\textbf{w}}\) and \({{\varvec{\theta }}_i}\) in an iterative manner. We implement alternating optimization based on auxiliary variables, first-order Taylor approximation, and the equality Eq. 19 to reformulate the proposed problem into a convex problem. We implement sequential rank-one constraint relaxation (SROCR) for decoupling the hardly coupled variables and non-convex rank one Star-RIS coefficients constraint. For simplicity we solve the problem based on assuming \({\textbf{E}_i} = {{\varvec{\theta }}_i}{\varvec{\theta }}_i^H\) where \({\textbf{E}_i} \in {{\mathbb {C}}^{(M + 1) \times (M + 1)}}\), and also we use Eq. 19 in our solution.
For solving problem 18, the first step toward converting Eq. 18a into concave form is using auxiliary variables \({{\textbf{P}}_i} = [{p_{1,i}},{p_{2,i}},{p_{3,i}},{p_{4,i}}]\) as below [36]
so that, \(\sum \limits _{i = r,t} {({R_i}} - {R_{{e_i}}}) \ge \sum \limits _{i = r,t} {({p_{1,i}}} - {p_{2,i}} - {p_{3,i}} + {p_{4,i}})\).
For optimizing problem based on \({\textbf{w}}\) with given \({{\textbf{E}} _i}\), we introduce an auxiliary variable \({{\textbf{r}}_{f,i}} = [{r_{f,i,1}},{r_{f,i,2}},{r_{f,i,3}},{r_{f,i,4}}]\), so that the equivalent of Eq. 20a is given below [36]
the equivalent of Eq. 20b is given below
the equivalent of Eq. 20c is given below
the equivalent of Eq. 20d is given below
The Eqs. 21a, 22b, 23b, and 24a are convex but the Eqs. 21b, 22a, 23a, and 24b are concave. By using the first-order Taylor approximation and equality 19, the non-convex equations are, respectively, equivalent as below
where \({{\textbf{A}}_{1,i}} = (1 + {\mu _r}){\textbf{H}}_i^H{{\textbf{E}}_i}{{\textbf{H}}_i} + {\mu _t}(1 + {\mu _r}){\widetilde{\mathrm{{Diag}}}}({\textbf{H}}_i^H{{\textbf{E}}_i}{{\textbf{H}}_i})\) and \({{\textbf{A}}_{2,i}} = {\mu _t}{\widetilde{\mathrm{{Diag}}}}({\textbf{F}}_i^H{{\textbf{E}}_i}{{\textbf{F}}_i})\), and \({\textbf{w}}^n\) is obtained at iteration n. Please refer to Appendix 1 for the proof of Eqs. (25) and (28). The optimization problem 18 for optimizing \({\textbf{w}}\) by fixing \({{\textbf{E}} _i}\) is reformulated as
For optimizing the problem based on \({\textbf{E} _i}\) where \({\textbf{E}_i} = {{\varvec{\theta }}_i}{\varvec{\theta }}_i^H\) with given \({\textbf{w}}\), we use semi-definite relaxation (SDR). The subproblem of optimizing \({\textbf{E} _i}\) by fixing \({\textbf{w}}\) is proposed as
We introduce an auxiliary variable \({{\textbf{r}}_{e,i}} = [{r_{e,i,1}},{r_{e,i,2}},{r_{e,i,3}},{r_{e,i,4}}]\), so that the equivalent of Eq. 20a is given below
the equivalent of Eq. 20b is given below
the equivalent of Eq. 20c is given below
the equivalent of Eq. 20d is given below
where \({{\textbf{B}}_1} = (1 + {\mu _r}){{\textbf{H}}_i}{\textbf{w}}{{\textbf{w}}^H}{\textbf{H}}_i^H + {\mu _t}(1 + {\mu _r}){{\textbf{H}}_i}{\widetilde{\mathrm{{Diag}}}}({\textbf{w}}{{\textbf{w}}^H}){\textbf{H}}_i^H\), \({{\textbf{B}}_2} = {\mu _r}{{\textbf{H}}_i}{\textbf{w}}{{\textbf{w}}^H}{\textbf{H}}_i^H + (1 + {\mu _r}){\mu _t}{{\textbf{H}}_i}{\widetilde{\mathrm{{Diag}}}}({\textbf{w}}{{\textbf{w}}^H}){\textbf{H}}_i^H\), \({{\textbf{B}}_3} = {\mu _t}{{\textbf{F}}_i}{\widetilde{\mathrm{{Diag}}}}({\textbf{w}}{{\textbf{w}}^H}){\textbf{F}}_i^H + {{\textbf{F}}_i}{\textbf{w}}{{\textbf{w}}^H}{\textbf{F}}_i^H\) and \({{\textbf{B}}_4} = {\mu _t}{{\textbf{F}}_i}{\widetilde{\mathrm{{Diag}}}}({\textbf{w}}{{\textbf{w}}^H}){\textbf{F}}_i^H\).
We approximate the non-convex constraints 32a and 33a based on the first-order Taylor approximation as below
The rank-one constraint 30b is relaxed by implementing sequential rank-one constraint relaxation (SROCR) as below,
where \({\mathrm{{\varepsilon }}_{\max }}({{\textbf{E}}_i})\) represents maximum eigenvalue of \({\textbf{E}}_i\), and \({\mathrm{{\varepsilon }}^{[l]}} \in [0,1]\) is relaxation parameter in \(\mathrm{{l}}\)-th iteration. Since the maximum eigenvalue of a rank-one matrix is equal to the trace of that matrix, so \({\mathrm{{\varepsilon }}^{[l]}} = 1\) means that the matrix is rank one but \({\mathrm{{\varepsilon }}^{[l]}} = 0\) leads to dropped rank-one constraint. \({\mathrm{{\varepsilon }}_{\max }}({{\textbf{E}}_i})\) is approximated by the following
where \(e_{\max }^H({\textbf{E}}_i^{[l]})\) denotes the largest eigenvector associated with the maximum eigenvalue of \({\textbf{E}}_i^{[l]}\). It should be noted that \({\mathrm{{\varepsilon }}^{[l]}}\) can be updated with the following formula in each iteration
where \({\Delta ^l}\) is the step size. So finally, the optimization subproblem of optimizing \({{\textbf{E}}_i}\) by fixing \({\textbf{w}}\) is reformulated as
Finally, we proposed iterative Algorithm 1 to solve problem (18) for ES protocol. This algorithm involves an alternating optimization of active beamforming in problem (29) and passive beamforming in problem (40). Hear, \(\mathrm{{\varepsilon }}_i\) denotes the rank-one relaxation parameter mentioned in Eq. (35).
2.5 Investigating MS
Compared to energy splitting mode, for mode switching (MS), with given \({{\textbf{E}}_i}\), the optimization of transmitter beamforming vector \({\textbf{w}}\) is the same as ES mode while in optimization of passive beamforming \({{\textbf{E}}_i}\) with given \({\textbf{w}}\), transmission and reflection coefficients are always between 0 and 1, so constraint \(\beta _m^i - {(\beta _m^i)^2} \ge 0\) always holds but the equality holds in MS mode that \(\beta _m^i\) is only 0 or 1. So the optimization problem with given \({\textbf{w}}\) has non-convex binary constraints, and to tackle these non-convex binary terms, we add a penalty term to the objective function based on the Eq. 41
Since the objective function should be maximum, the penalty term is non-concave due to \({(\beta _m^i)^2}\). By using \(\beta _m^{i,n}\), which is calculated in the last iteration of the SCA algorithm, based on the first-order Taylor approximation, the lower bound for Eq. 41 is obtained as below [45, 46]
In addition, the equivalent of \(\beta _m^i\) is \({\textbf{E}}_{m,m}^i\). So, the optimization problem in MS mode is given below
Where \(\mathrm{{\chi }} > 0\) is a penalty factor that imposes a penalty to the objective function. We should notice that, unlike ES protocol, in MS protocol, we use an outer loop to guarantee binary STAR-RIS coefficients with predefined accuracy \(\varepsilon _\mathrm{{{out}}}\). In the outer loop, we increase the penalty factor proportionally by \(\kappa \ge 1\) in each iteration, when \(\mathrm{{\chi }} \rightarrow + \infty\), the solution of problem 43 is satisfied the equality constraint 41 [42, 47].
Finally, we develop two-layer iterative algorithm (2) to tackle problem (18) in MS protocol. In the inner layer, we alternatively optimize active beamforming in problem (29) and passive beamforming in problem (43). In the outer layer, we ensure the binary MS Star-RIS coefficients meet the predefined accuracy \({\varepsilon _\mathrm{{{out}}}} > 0\).
2.6 Convergence analysis
The convergence behavior of the implemented solution is guaranteed based on the following details. Since the optimization problem 18 is solved based on the alternating manner and SCA, and also due to non-decreasing objective function 18a in each iteration while having a finite upper bound for objective function due to limited transmission power, i.e., constraint 18b, therefor the convergence of AO algorithm is ensured. So, let \({R_{secure}}({\textbf{w}}_i^k,{\textbf{E}}_i^k)\), \({R_{secure}}({\textbf{w}}_i^{k+1},{\textbf{E}}_i^k)\), \({R_{secure}}({\textbf{w}}_i^{k+1},{\textbf{E}}_i^{k+1})\) represent the objective of 18 and 29 and 40, respectively, then we have the following inequality
so due to bounded objective function, \(R_{\textrm{secure}}({{\textbf{w}}_i^k},{{\textbf{E}}_i^k})\) is converged to an optimal point limit \(R_{secure}({{\textbf{w}}_i^\mathrm{{{opt}}}},{{\textbf{E}}_i^\mathrm{{{opt}}}})\) [48, 49].
2.7 Complexity analysis
The complexity of SOCP active beamforming (29) is \(\mathcal {O}(N^3)\) [36], and the complexity of SDP passive beamforming (40), and (43) is \(\mathcal {O}(M^{3.5})\) [50], Thus, the overall complexity of Algorithm 1 for ES protocol is \(\mathcal {O}(I_l(N^3+M^{3.5}))\), where \(I_l\) represents the iteration number needed for convergence. The total complexity of Algorithm (2) for MS is \(\mathcal {O}(I_\mathrm{{{out}}}I_{in}(N^3+M^{3.5}))\), where \(I_\mathrm{{{out}}}\) and \(I_{in}\) representing the iteration numbers of the outer and inner layers required for convergence.
3 Results and discussion
The advantages of deploying Star-RIS in the proposed secure wireless communications system are evaluated in this section. We assume that users are at (50 m,2 m) and (50 m, -2 m), and eavesdroppers are at (45 m,2 m) and (45 m, -2 m). We compare the performance of Star-RIS with M elements and No-RIS system, and conventional RIS that contains two reflection and transmission surfaces, each one with M/2 elements. For more details, the simulation parameters are written in Table 2.
In Fig. 2, we plot total secrecy rate versus transmitted power consumption across all deployments of RIS. Since Star-RIS simultaneously reflects and transmits signals, it has more degrees of freedom than conventional RIS, which results in higher performance for Star-RIS than conventional RIS and No-RIS systems. Also, we demonstrate the performance of the No-RIS system, which has the lowest performance since RIS and Star-RIS can create dynamic and adaptable wireless radio propagation. In the two operating protocols of Star-RIS, ES mode has higher performance than MS due to more degrees of freedom. It should be noted that the secrecy rate trends to an upper bound with increasing maximum transmission power due to distortion noise.
The SSR versus the number of RIS elements is shown in Fig. 3. It can be observed that RIS can obtain more signal power and enable beamforming with more elements. Hence, the sum secrecy rate improves with increasing M. It should be noted that hardware impairment degrades the sum secrecy rate due to distortion noise. So, the SSR saturates for hardware impairment by an increase in M. Also, in curves with more transmit power, it can be observed that SSR reaches the saturation and largest value with the lower number of RIS elements since the transceiver hardware impairments are power dependent. Also, Star-RIS outperforms conventional RIS due to more degrees of freedom. Among ES and MS modes in Star-RIS, ES has better performance due to the continuous altitude of RIS coefficients in contrast to MS, which can operate with a binary altitude of coefficients. This figure validates the impact of optimization over passive beamforming vectors, which refers to both transmission and reflection.
The SSR versus number of BS antennas is shown in Fig. 4, where \(p_\mathrm{{{Max}}}=15dBm\), and \(M=16\). Since more antennas in BS enable higher active beamforming gain, the total secrecy rate increases for all methods, but, increasing transmitter or receiver hardware impairment levels, i.e., \(\mu _t\) or \(\mu _r\) leads to a decrease in sum secrecy rate. In each deployment method, the SSR with simulation parameters \(\mu _t = 0.05, \mu _r= 0.01\) has higher performance than with \(\mu _t = 0.01, \mu _r= 0.05\) since the receiver distortion noise power is larger than the transmit distortion noise. Also, similar to the previous figure, Star-RIS outperforms conventional RIS (CRIS) and No-RIS systems. ES has the highest performance, and the No-RIS scenario has the lowest performance. This figure confirms the impact of active beamforming optimization. So, the effect of optimizing joint active and passive beamforming together is confirmed in Figs. 4 and 3.
Figure 5 shows the SSR versus the receiver and transmitter hardware impairment level (i.e., \(\mu _r\) and \(\mu _t\)). Since more hardware impairment levels in BS and legitimate receivers result in more distortion noise, it leads BS to use some of available transmission power for compensating the hardware impairments, and hence sum secrecy rate of legitimate users decreases with increasing \(\mu _r\) and \(\mu _t\).
It should be noted that with large \(\mu\), distortion noise in equation 16 becomes noticeable with respect to receiver noise. Also, the algorithm with more degrees of freedom receives more distortion noise, so the distortion noise in ES is larger than in the MS and conventional RIS, respectively. Due to these two reasons, and based on equation 16, with large \(\mu\), three algorithms perform the same, But with small \(\mu\), ES outperforms MS, and MS outperforms conventional RIS. So, finally, ES, MS, and conventional algorithms gradually perform the same when the hardware impairment levels increase.
4 Conclusion
This paper investigates robust beamforming designs for secure MISO downlink communication systems aided by Star-RIS under residual transceiver hardware impairments that lead to distortion noise. We aimed to maximize the total secrecy rate subject to limited power consumption by optimizing beamforming at BS and Star-RIS with two practical protocols named ES and MS. Based on our simulation results, Star-RIS outperforms conventional RIS and No-RIS systems in terms of performance. In Star-RIS, the ES performs better than MS. The total secrecy rate increases with more Star-RIS elements and BS antennas, but residual transceiver hardware impairment reduces SSR. It should be noted that the impact of the receiver hardware impairment level is higher than the transmitter hardware impairment level. Our results show that the sum secrecy rate trends to an upper bound with increasing maximum transmission power and number of RIS elements due to distortion noise.
Availability of data and materials
Not applicable.
Abbreviations
- AN:
-
Artificial noise
- AO:
-
Alternating optimization
- BS:
-
Base station
- CSI:
-
Channel state information
- ES:
-
Energy splitting
- LMMSE:
-
Linear minimum mean square error
- MS:
-
Mode switching
- NOMA:
-
Non orthogonal multiple access
- RIS:
-
Reconfigurable intelligent surface
- RSMA:
-
Rate splitting multiple access
- SCA:
-
Successive convex approximation
- SDP:
-
Semidefinite programming
- SDR:
-
Semidefinite relaxation
- SOCP:
-
Second order cone programming
- SROCR:
-
Sequential rank-one constraint relaxation
- SSR:
-
Sum secrecy rate
- Star-RIS:
-
Simultaneously transmission and reflection RIS
- TS:
-
Time switching
- UAV:
-
Unmanned aerial vehicle
References
Q. Wu, S. Zhang, B. Zheng, C. You, R. Zhang, Intelligent reflecting surface-aided wireless communications: a tutorial. IEEE Trans. Commun. 69(5), 3313–3351 (2021)
M.A. Alves, G. Fraidenraich, R.C. Ferreira, F.A. De Figueiredo, E.R. De Lima, Multiple-antenna weibull-fading wireless communications enhanced by reconfigurable intelligent surfaces. IEEE Access. 11, 107218–107236 (2023)
Y. Yang, Y. Hu, M.C. Gursoy, Energy efficiency of RIS-assisted NOMA-based MEC networks in the finite blocklength regime. IEEE Trans. Commun. 72(4), 2275–2291 (2023)
X. Yuan, W. Li, Y. Hu, A. Schmeink, in 2022 International Symposium on Wireless Communication Systems (ISWCS) (IEEE, 2022), pp. 1–6
H.M. Hariz, S. Sheikhzadeh, N. Mokari, M.R. Javan, B. Abbasi-Arand, E.A. Jorswieck, Ai-based radio resource management and trajectory design for PD-NOMA communication in IRS-UAV assisted networks. arXiv preprint arXiv:2111.03869 (2021)
A.S. De Sena, D. Carrillo, F. Fang, P.H. Nardelli, D.B. Da Costa, U.S. Dias, Z. Ding, C.B. Papadias, W. Saad, What role do intelligent reflecting surfaces play in multi-antenna non-orthogonal multiple access? IEEE Wirel. Commun. 27(5), 24–31 (2020)
Y. Ai, A. Felipe, L. Kong, M. Cheffena, S. Chatzinotas, B. Ottersten, Secure vehicular communications through reconfigurable intelligent surfaces. IEEE Trans. Veh. Technol. 70(7), 7272–7276 (2021)
L. Hu, C. Sun, G. Li, A. Hu, D.W.K. Ng, Reconfigurable intelligent surface-aided secret key generation in multi-cell systems. arXiv preprint arXiv:2303.12455 (2023)
Y. Xu, B. Gu, Z. Gao, D. Li, Q. Wu, C. Yuen, Applying RIS in multi-user SWIPT-WPCN systems: a robust and environmentally-friendly design. IEEE Trans. Cognit. Commun. Netw. 10(1), 209–222 (2023)
X. Liu, Y. Liu, Y. Chen, H.V. Poor, Ris enhanced massive non-orthogonal multiple access networks: deployment and passive beamforming design. IEEE J. Sel. Areas Commun. 39(4), 1057–1071 (2020)
Y. Lu, Y. Jiang, L. Zhang, M. Bennis, D. Niyato, X. You, in ICC 2023-IEEE International Conference on Communications (IEEE, 2023), pp. 5370–5376
H. Kim, H. Chen, M.F. Keskin, Y. Ge, K. Keykhosravi, G.C. Alexandropoulos, S. Kim, H. Wymeersch, Ris-enabled and access-point-free simultaneous radio localization and mapping. IEEE Trans. Wirel. Commun. (2023)
E. Björnson, H. Wymeersch, B. Matthiesen, P. Popovski, L. Sanguinetti, E. de Carvalho, Reconfigurable intelligent surfaces: a signal processing perspective with wireless applications. IEEE Signal Process. Mag. 39(2), 135–158 (2022)
Y. Liu, X. Mu, J. Xu, R. Schober, Y. Hao, H.V. Poor, L. Hanzo, Star: simultaneous transmission and reflection for 360° coverage by intelligent surfaces. IEEE Wirel. Commun. 28(6), 102–109 (2021)
J. Xu, Y. Liu, X. Mu, O.A. Dobre, Star-RIS: simultaneous transmitting and reflecting reconfigurable intelligent surfaces. IEEE Commun. Lett. 25(9), 3134–3138 (2021)
W. Yan, W. Hao, G. Sun, C. Huang, Q. Wu, Wideband beamforming for Star-RIS-assisted THZ communications with three-side beam split. arXiv preprint arXiv:2310.13933 (2023)
S. Huang, W. Wang, R. Jiang, X. Wang, Z. Fei, C. Huang, J. Li, S. Ren, X. Li, H. Dang, Average sum-rate maximization for coupled phase-shift Star-RIS enhanced multi-user miso-OFDM system. IEEE Trans. Commun. 72(3), 1457–1473 (2023)
H. Xiao, X. Hu, A. Li, W. Wang, Z. Su, K.K. Wong, K. Yang, Star-RIS enhanced joint physical layer security and covert communications for multi-antenna mmWave systems. arXiv preprint arXiv:2307.08043 (2023)
A. Papazafeiropoulos, L.N. Tran, Z. Abdullah, P. Kourtessis, S. Chatzinotas, Achievable rate of a Star-RIS assisted massive mimo system under spatially-correlated channels. IEEE Trans. Wirel. Commun. 23(2), 1550–1564 (2023)
S. Xu, C. Liu, H. Wang, M. Qian, J. Li, On secrecy performance analysis of multi-antenna Star-RIS-assisted downlink NOMA systems. EURASIP J. Adv. Signal Process. 2022(1), 118 (2022)
S.P. Le, H.N. Nguyen, N.T. Nguyen, C.H. Van, A.T. Le, M. Voznak, Physical layer security analysis of IRS-based downlink and uplink NOMA networks. EURASIP J. Wirel. Commun. Netw. 2023(1), 105 (2023)
S.R. Shahcheragh, K. Mohamed-pour, Active and passive beamforming for secure wireless communication via Star-RIS under imperfect CSI. in 31st International Conference on Electrical Engineering (ICEE 2023) pp. 981–986 (2023)
M. Ragheb, A. Kuhestani, S.M.S. Hemami, Joint beamforming and artificial noise design in secure millimeter-wave communications with the aid of intelligent reflecting surfaces. J. Iran. Assoc. Electric. Electron. Eng. 19(3), 55–62 (2022)
M. Rihan, A. Zappone, S. Buzzi, Robust RIS-assisted mimo communication-radar coexistence: joint beamforming and waveform design. IEEE Trans. Commun. 71(11), 6647–6661 (2023)
Y. Wen, G. Chen, S. Fang, M. Wen, S. Tomasin, M. Di Renzo, Ris-assisted UAV secure communications with artificial noise-aware trajectory design against multiple colluding curious users. IEEE Trans. Inform. Forensics Sec. 19, 3064–3076 (2024)
Y. Han, N. Li, Y. Liu, T. Zhang, X. Tao, Artificial noise aided secure NOMA communications in Star-RIS networks. IEEE Wirel. Commun. Lett. 11(6), 1191–1195 (2022)
W. Wang, W. Ni, H. Tian, Z. Yang, C. Huang, K.K. Wong, Safeguarding NOMA networks via reconfigurable dual-functional surface under imperfect CSI. IEEE J. Select. Top. Signal Process. 16(5), 950–966 (2022)
Z. Zhang, J. Chen, Y. Liu, Q. Wu, B. He, L. Yang, On the secrecy design of Star-RIS assisted uplink NOMA networks. IEEE Trans. Wirel. Commun. 21(12), 11207–11221 (2022)
H.R. Hashempour, H. Bastami, M. Moradikia, S.A. Zekavat, H. Behroozi, A.L. Swindlehurst, Secure swipt in Star-RIS aided downlink miso rate-splitting multiple access networks. arXiv preprint arXiv:2211.09081 (2022)
X. Li, Y. Zheng, M. Zeng, Y. Liu, O.A. Dobre, Enhancing secrecy performance for Star-RIS NOMA networks. IEEE Trans. Veh. Technol. 72(2), 2684–2688 (2022)
H. Jia, L. Ma, S. Valaee, Star-RIS enabled downlink secure NOMA network under imperfect CSI of eavesdroppers. IEEE Commun. Lett. 27(3), 802–806 (2023)
S. Xu, C. Liu, H. Wang, M. Qian, J. Li, Star-RIS-assisted scheme for enhancing physical layer security in NOMA systems. IET Commun. 16(19), 2328–2342 (2022)
Y. Liu, K. Huang, X. Sun, J. Yang, J. Zhao, Secure wireless communications for Star-RIS-assisted millimetre-wave NOMA uplink networks. IET Commun. 17(9), 1127–1139 (2023)
H. Shen, W. Xu, S. Gong, C. Zhao, D.W.K. Ng, Beamforming optimization for IRS-aided communications with transceiver hardware impairments. IEEE Trans. Commun. 69(2), 1214–1227 (2020)
Y. Liu, E. Liu, R. Wang, B. Lu, Z. Han, Beamforming design and performance evaluation for reconfigurable intelligent surface assisted wireless communication systems with non-ideal hardware. arXiv preprint arXiv:2006.00664 (2020)
G. Zhou, C. Pan, H. Ren, K. Wang, Z. Peng, Secure wireless communication in RIS-aided miso system with hardware impairments. IEEE Wirel. Commun. Lett. 10(6), 1309–1313 (2021)
M. Soleymani, I. Santamaria, E.A. Jorswieck, Rate splitting in mimo RIS-assisted systems with hardware impairments and improper signaling. IEEE Trans. Veh. Technol. 72(4), 4580–4597 (2022)
M. Soleymani, I. Santamaria, E. Jorswieck, Noma-based improper signaling for mimo Star-RIS-assisted broadcast channels with hardware impairments. arXiv preprint arXiv:2308.02696 (2023)
Q. Li, M. El-Hajjar, Y. Sun, I. Hemadeh, A. Shojaeifard, Y. Liu, L. Hanzo, Achievable rate analysis of the Star-RIS aided NOMA uplink in the face of imperfect CSI and hardware impairments. IEEE Trans. Commun. 71(10), 6100–6114 (2023)
W. Khalid, M.A.U. Rehman, T. Van Chien, H. Yu, in 2023 International Conference on Artificial Intelligence in Information and Communication (ICAIIC) (IEEE, 2023), pp. 654–656
C. Zhou, B. Lyu, S. Gong, C. You, Active Star-RIS assisted symbiotic radio communications under hardware impairments. IEEE Commun. Lett. (2023)
X. Mu, Y. Liu, L. Guo, J. Lin, R. Schober, Simultaneously transmitting and reflecting (star) RIS aided wireless communications. IEEE Trans. Wirel. Commun. 21(5), 3083–3098 (2021)
H. Niu, Z. Chu, F. Zhou, Z. Zhu, Simultaneous transmission and reflection reconfigurable intelligent surface assisted secrecy miso networks. IEEE Commun. Lett. 25(11), 3498–3502 (2021)
D.T. Ngo, S. Khakurel, T. Le-Ngoc, Joint subchannel assignment and power allocation for OFDMA femtocell networks. IEEE Trans. Wirel. Commun. 13(1), 342–355 (2013)
N. Zhang, Y. Liu, X. Mu, W. Wang, A. Huang, Queue-aware Star-RIS assisted NOMA communication systems. IEEE Trans. Wirel. Commun. 23(5), 4786–4801 (2023)
W. Ni, Y. Liu, Y.C. Eldar, Z. Yang, H. Tian, Star-RIS enabled heterogeneous networks: Ubiquitous NOMA communication and pervasive federated learning. arXiv e-prints pp. arXiv–2106 (2021)
B. Shi, Y. Wang, D. Li, W. Cai, J. Lin, S. Zhang, W. Shi, S. Yan, F. Shu, Star-RIS-UAV-aided coordinated multipoint cellular system for multi-user networks. Drones 7(6), 403 (2023)
J. Zuo, Y. Liu, Z. Ding, L. Song, H.V. Poor, Joint design for simultaneously transmitting and reflecting (star) RIS assisted NOMA systems. IEEE Trans. Wireless Commun. 22(1), 611–626 (2022)
Y. Sun, K. An, J. Luo, Y. Zhu, G. Zheng, S. Chatzinotas, Intelligent reflecting surface enhanced secure transmission against both jamming and eavesdropping attacks. IEEE Trans. Veh. Technol. 70(10), 11017–11022 (2021)
Z.Q. Luo, W.K. Ma, A.M.C. So, Y. Ye, S. Zhang, Semidefinite relaxation of quadratic optimization problems. IEEE Signal Process. Mag. 27(3), 20–34 (2010)
Acknowledgements
Not applicable.
Funding
This work is funded by Springer Nature to support the lowest income countries.
Author information
Authors and Affiliations
Contributions
This work is part of Seyedeh Reyhane Shahcheragh’s Ph.D. thesis. All authors have contributed to this research work, read and approved the final manuscript.
Corresponding author
Ethics declarations
Competing interests
The authors declare that they have no competing interests.
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Appendix 1
Appendix 1
Proof of equation (25) and (28)
Let v be a complex scaler variable. We have the first-order Taylor inequality
for any fixed point \(v^{(n)}\). By knowing that \({\textbf{E}}_i={\varvec{\theta }}_i{\varvec{\theta }}^H_i\), for optimizing problem based on \(\textbf{w}\), we replace v and \(v^{(n)}\) in (25) with \({\varvec{\theta }}_i^H{{\textbf{H}}_i}{{\textbf{w}}}\) and \({\varvec{\theta }}_i^H{{\textbf{H}}_i}{{\textbf{w}}^{(n)}}\), and also with \(\mathrm{{Diag}}({\varvec{\theta }}_i^H{{\textbf{H}}_i}){{\textbf{w}}}\) and \(\mathrm{{Diag}}({\varvec{\theta }}_i^H{{\textbf{H}}_i}){{\textbf{w}}^{(n)}}\), so, we have
Based on above explanation, we can obtain (25), and with similar mathematical, (28) is obtained.
Rights and permissions
Open Access This article is licensed under a Creative Commons Attribution 4.0 International License, which permits use, sharing, adaptation, distribution and reproduction in any medium or format, as long as you give appropriate credit to the original author(s) and the source, provide a link to the Creative Commons licence, and indicate if changes were made. The images or other third party material in this article are included in the article’s Creative Commons licence, unless indicated otherwise in a credit line to the material. If material is not included in the article’s Creative Commons licence and your intended use is not permitted by statutory regulation or exceeds the permitted use, you will need to obtain permission directly from the copyright holder. To view a copy of this licence, visit http://creativecommons.org/licenses/by/4.0/.
About this article
Cite this article
Shahcheragh, S.R., Mohamed-Pour, K. Beamforming design for Star-RIS assisted secure wireless communication system under hardware impairments. J Wireless Com Network 2024, 59 (2024). https://doi.org/10.1186/s13638-024-02389-x
Received:
Accepted:
Published:
DOI: https://doi.org/10.1186/s13638-024-02389-x